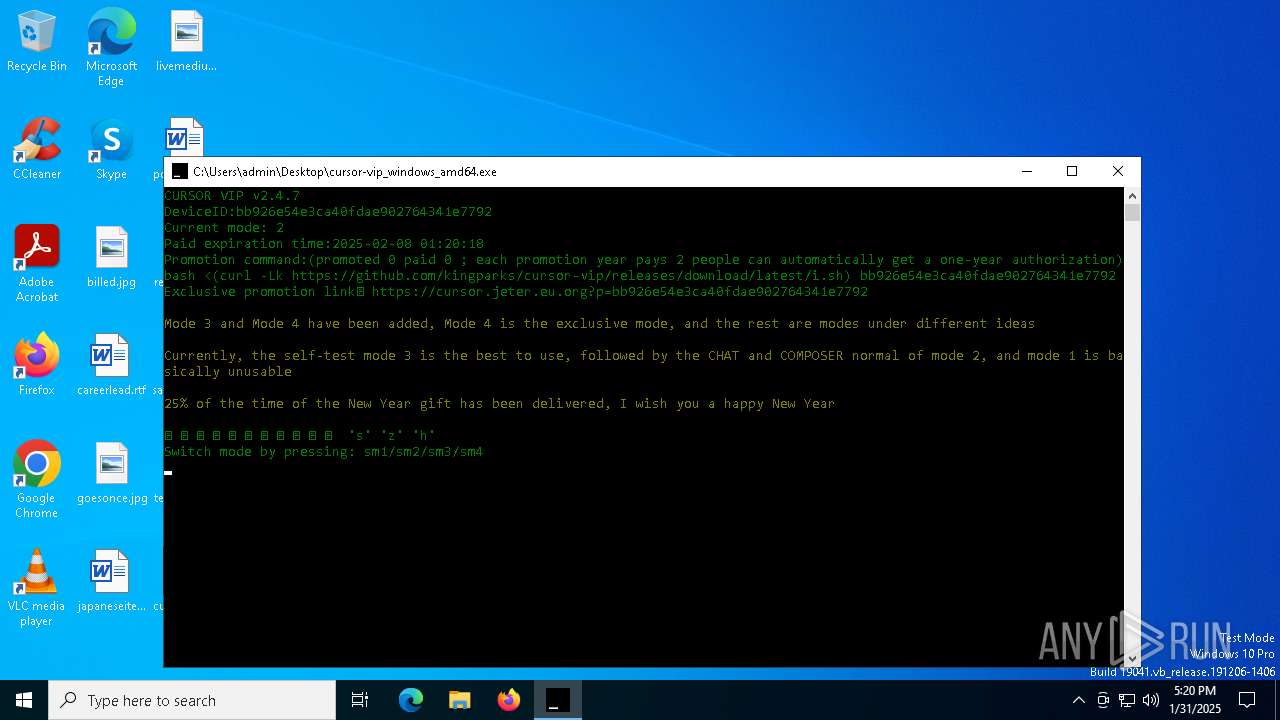
| download: | /kingparks/cursor-vip/releases/download/latest/cursor-vip_windows_amd64.exe |
| Full analysis: | https://app.any.run/tasks/266ddfcc-4447-436d-9406-47bc4039a487 |
| Verdict: | Malicious activity |
| Analysis date: | January 31, 2025, 17:19:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 9 sections |
| MD5: | BA0EF9C8A17A2D74E69D0FDC16F5997D |
| SHA1: | FF1CD2914DCD257381A7D792748C2F5CAA8B47B8 |
| SHA256: | 3BA2CE5EADB71ED9F39F0AC92402137FFF7C6C471E69649CFAFEB81138C30FAD |
| SSDEEP: | 98304:iIGI4qThGHFKDCP6XO91aOhMOCsXQU0DP6n7KytOHD9wfuBC7KOKhq5+ywtlhRZo:Ni |
MALICIOUS
No malicious indicators.SUSPICIOUS
There is functionality for taking screenshot (YARA)
- cursor-vip_windows_amd64.exe (PID: 5728)
- cursor-vip_windows_amd64.exe (PID: 2804)
Starts POWERSHELL.EXE for commands execution
- cursor-vip_windows_amd64.exe (PID: 5728)
- cursor-vip_windows_amd64.exe (PID: 2804)
- cursor-vip_windows_amd64.exe (PID: 3420)
Uses TASKKILL.EXE to kill process
- cursor-vip_windows_amd64.exe (PID: 5728)
- cursor-vip_windows_amd64.exe (PID: 2804)
- cursor-vip_windows_amd64.exe (PID: 3420)
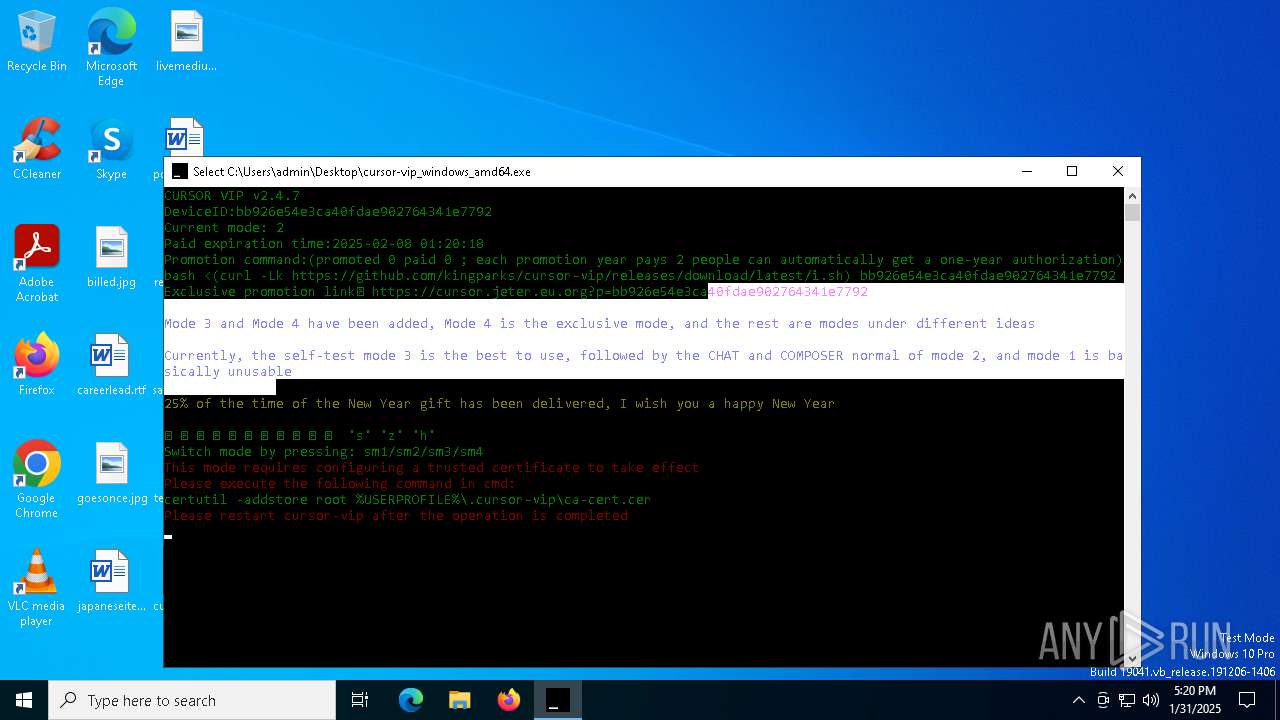
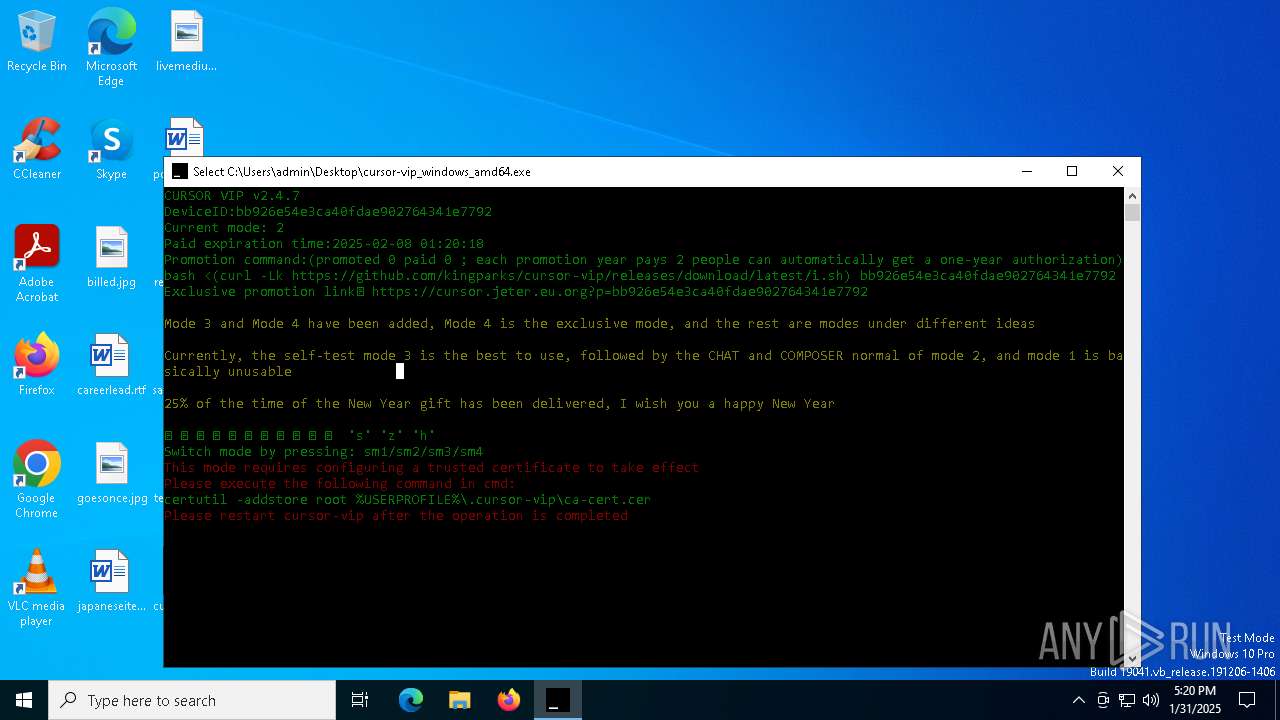
Adds/modifies Windows certificates
- certutil.exe (PID: 1740)
Executable content was dropped or overwritten
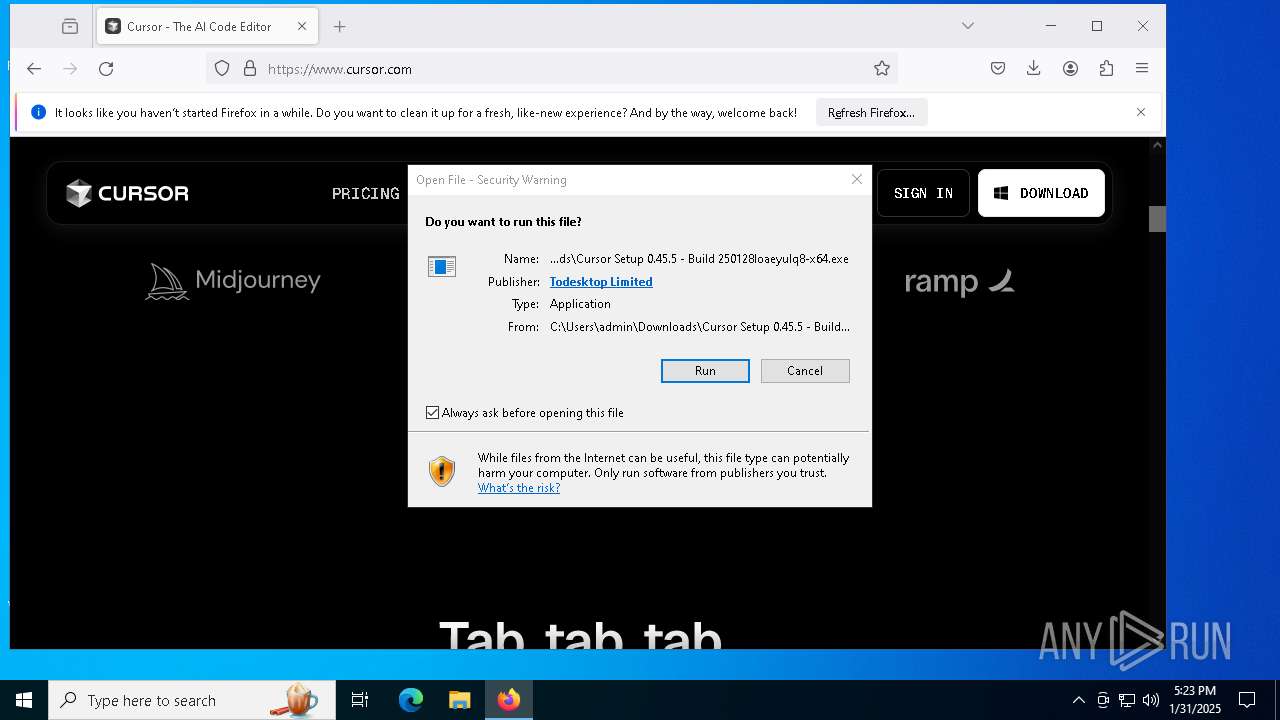
- Cursor Setup 0.45.5 - Build 250128loaeyulq8-x64.exe (PID: 1016)
The process creates files with name similar to system file names
- Cursor Setup 0.45.5 - Build 250128loaeyulq8-x64.exe (PID: 1016)
Malware-specific behavior (creating "System.dll" in Temp)
- Cursor Setup 0.45.5 - Build 250128loaeyulq8-x64.exe (PID: 1016)
Drops 7-zip archiver for unpacking
- Cursor Setup 0.45.5 - Build 250128loaeyulq8-x64.exe (PID: 1016)
Get information on the list of running processes
- cmd.exe (PID: 7140)
- Cursor Setup 0.45.5 - Build 250128loaeyulq8-x64.exe (PID: 1016)
Starts CMD.EXE for commands execution
- Cursor Setup 0.45.5 - Build 250128loaeyulq8-x64.exe (PID: 1016)
INFO
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5064)
- cursor-vip_windows_amd64.exe (PID: 5728)
- cursor-vip_windows_amd64.exe (PID: 2804)
- cursor-vip_windows_amd64.exe (PID: 3420)
Drops encrypted JS script (Microsoft Script Encoder)
- cursor-vip_windows_amd64.exe (PID: 5728)
- cursor-vip_windows_amd64.exe (PID: 2804)
- cursor-vip_windows_amd64.exe (PID: 3420)
Checks supported languages
- cursor-vip_windows_amd64.exe (PID: 5728)
- cursor-vip_windows_amd64.exe (PID: 2804)
- SearchApp.exe (PID: 5064)
- cursor-vip_windows_amd64.exe (PID: 3420)
- Cursor Setup 0.45.5 - Build 250128loaeyulq8-x64.exe (PID: 1016)
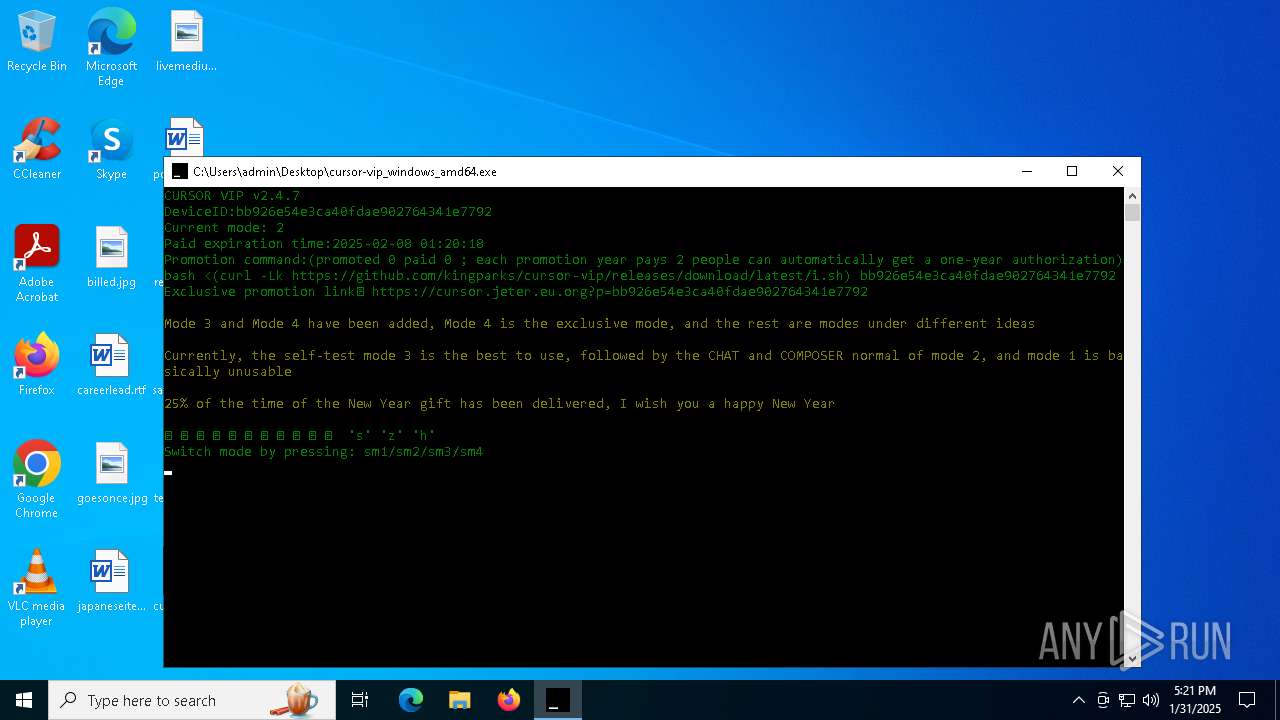
Detects GO elliptic curve encryption (YARA)
- cursor-vip_windows_amd64.exe (PID: 5728)
- cursor-vip_windows_amd64.exe (PID: 2804)
Application based on Golang
- cursor-vip_windows_amd64.exe (PID: 5728)
- cursor-vip_windows_amd64.exe (PID: 2804)
Reads the software policy settings
- SearchApp.exe (PID: 5064)
- cursor-vip_windows_amd64.exe (PID: 5728)
- cursor-vip_windows_amd64.exe (PID: 2804)
- cursor-vip_windows_amd64.exe (PID: 3420)
Reads the computer name
- cursor-vip_windows_amd64.exe (PID: 5728)
- cursor-vip_windows_amd64.exe (PID: 2804)
- cursor-vip_windows_amd64.exe (PID: 3420)
Manual execution by a user
- cursor-vip_windows_amd64.exe (PID: 2804)
- cmd.exe (PID: 4576)
- cmd.exe (PID: 2452)
- cursor-vip_windows_amd64.exe (PID: 3420)
- firefox.exe (PID: 4648)
Process checks computer location settings
- SearchApp.exe (PID: 5064)
Application launched itself
- firefox.exe (PID: 4648)
- firefox.exe (PID: 3900)
Executable content was dropped or overwritten
- firefox.exe (PID: 3900)
The sample compiled with english language support
- firefox.exe (PID: 3900)
- Cursor Setup 0.45.5 - Build 250128loaeyulq8-x64.exe (PID: 1016)
Create files in a temporary directory
- Cursor Setup 0.45.5 - Build 250128loaeyulq8-x64.exe (PID: 1016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 3 |
| CodeSize: | 5879296 |
| InitializedDataSize: | 552960 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6e1c0 |
| OSVersion: | 6.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows command line |
Total processes
163
Monitored processes
37
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2716 -childID 3 -isForBrowser -prefsHandle 2616 -prefMapHandle 5008 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1428 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {ed45798a-a919-4b4d-b412-9108c199fbcc} 3900 "\\.\pipe\gecko-crash-server-pipe.3900" 19af3f33850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1016 | "C:\Users\admin\Downloads\Cursor Setup 0.45.5 - Build 250128loaeyulq8-x64.exe" | C:\Users\admin\Downloads\Cursor Setup 0.45.5 - Build 250128loaeyulq8-x64.exe | firefox.exe | ||||||||||||
User: admin Company: Cursor AI, Inc. Integrity Level: MEDIUM Description: Cursor is an AI-first coding environment. Version: 250128loaeyulq8 Modules
| |||||||||||||||
| 1220 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1356 | powershell "Get-Culture | select -exp Name" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cursor-vip_windows_amd64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1740 | certutil -addstore root C:\Users\admin\.cursor-vip\ca-cert.cer | C:\Windows\System32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2076 | powershell "Get-Culture | select -exp Name" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cursor-vip_windows_amd64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2160 | taskkill /IM Cursor.exe /F | C:\Windows\System32\taskkill.exe | — | cursor-vip_windows_amd64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2452 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
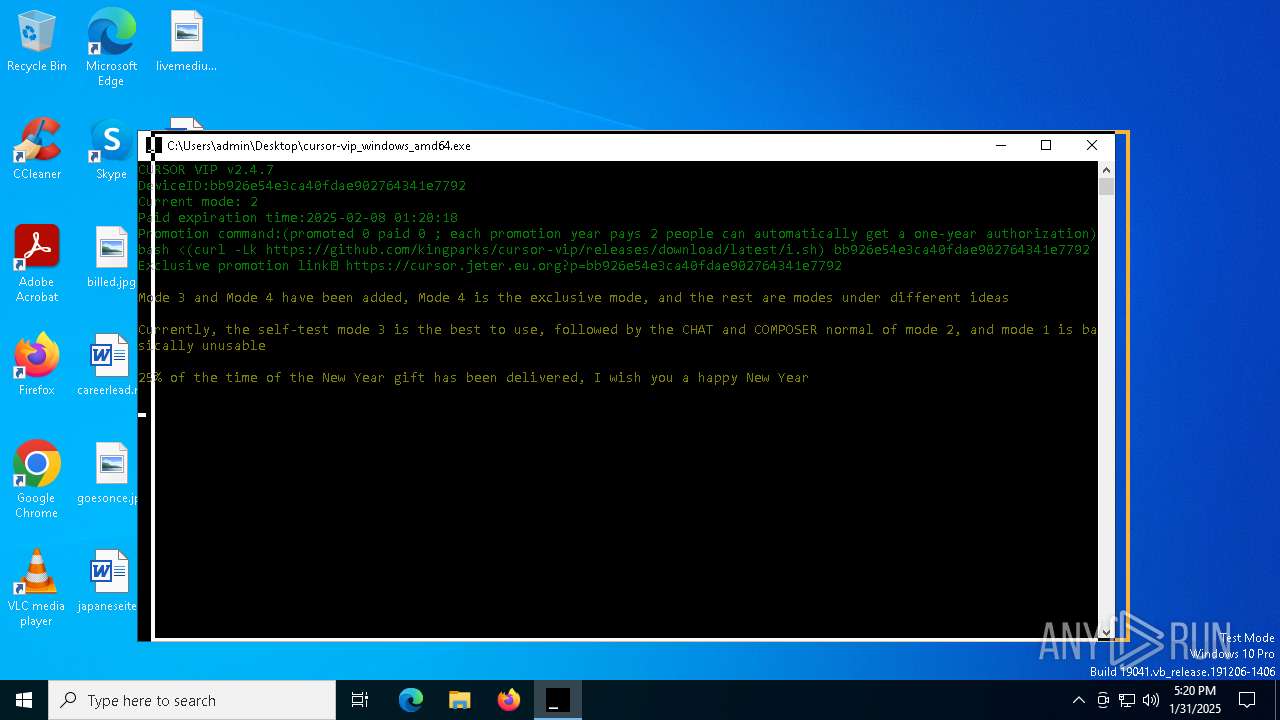
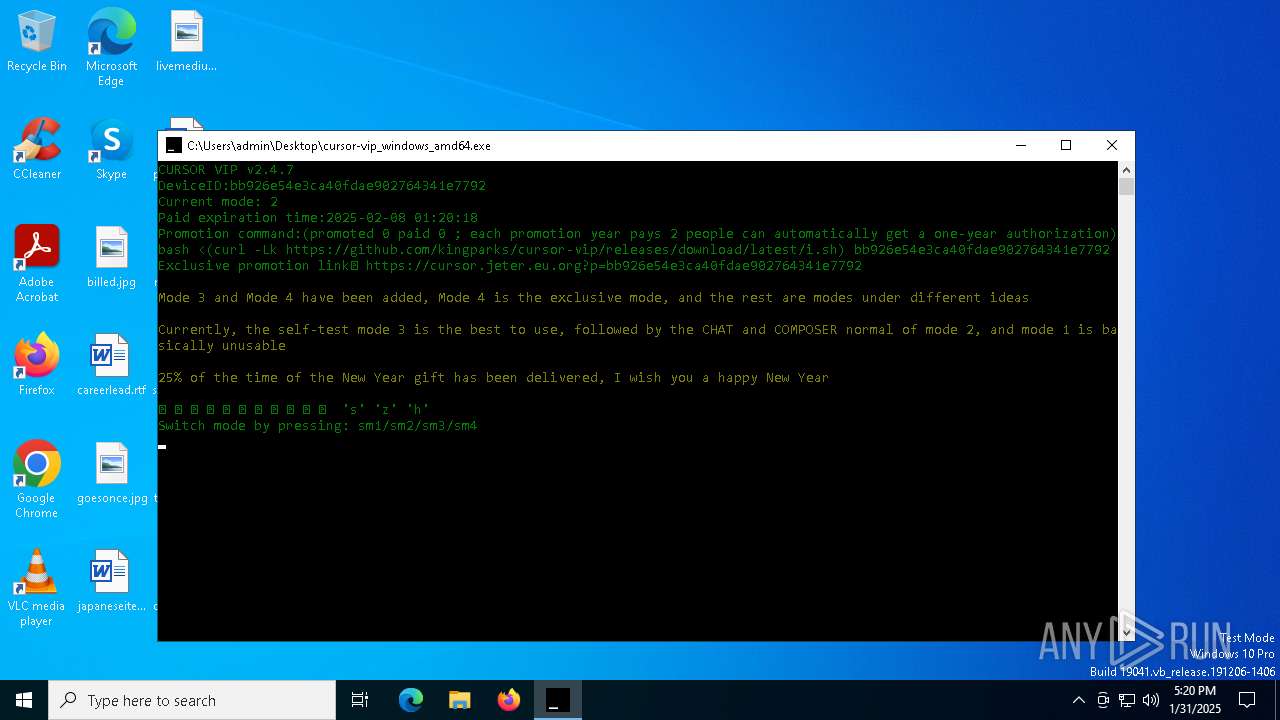
| 2804 | "C:\Users\admin\Desktop\cursor-vip_windows_amd64.exe" | C:\Users\admin\Desktop\cursor-vip_windows_amd64.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3040 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4820 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4576 -prefMapHandle 4596 -prefsLen 36588 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {0a33adef-c867-4c11-9965-f0c021525123} 3900 "\\.\pipe\gecko-crash-server-pipe.3900" 19af510ef10 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
Total events
47 792
Read events
47 692
Write events
97
Delete events
3
Modification events
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | DynamicText |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | DynamicTextTruncated |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\Internet Explorer\DOMStorage\bing.com |
| Operation: | write | Name: | Total |
Value: 50111 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\DynamicSearchBox |
| Operation: | write | Name: | TelemetryID |
Value: 0000438135640474DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\DynamicSearchBox |
| Operation: | write | Name: | TelemetryID |
Value: 00008AEB2B640474DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\Internet Explorer\DOMStorage\bing.com |
| Operation: | write | Name: | Total |
Value: 50667 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\Internet Explorer\DOMStorage\bing.com |
| Operation: | write | Name: | Total |
Value: 929 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\SOFTWARE\Microsoft\Speech_OneCore\Isolated\A1hdl50UVDh2ZbG324Nx-6fZgntcGnHOs5kHLdmaJYE\HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech_OneCore\Recognizers |
| Operation: | write | Name: | DefaultTokenId |
Value: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Speech_OneCore\Recognizers\Tokens\MS-1033-110-WINMO-DNN | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | IsMSACloudSearchEnabled |
Value: 0 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | IsAADCloudSearchEnabled |
Value: 0 | |||
Executable files
7
Suspicious files
606
Text files
350
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1356 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4ojubidq.rzb.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\Internet Explorer\DOMStore\ZWUI0EBX\www.bing[1].xml | text | |
MD5:AF4C8595E0140D249A475A80C296B470 | SHA256:1EBE02E9AA0D7A09108B69C62FD580282530F2A693EE2BA808656B9EBB2D5ED2 | |||
| 1356 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lr5rp4k1.mvu.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5728 | cursor-vip_windows_amd64.exe | C:\Users\admin\.cursor-vip\cursor-vip.pid | text | |
MD5:80B618EBCAC7AA97A6DAC2BA65CB7E36 | SHA256:015DD044EE9F809CDF83B19270E5ECA74ECE7684050FC3EB545B7734CBBFF52F | |||
| 5728 | cursor-vip_windows_amd64.exe | C:\Users\admin\.cursor-vip\i-need-to-trust-ca-cert.pem | text | |
MD5:5123888F35778F4A9E31F1DD32122C16 | SHA256:80F7E8858EDDCB45648FA9FB66730A9BC2D8350EB9415345675877993E85D89A | |||
| 1356 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:5D9226D4BA058405C4C840CE35F9E53A | SHA256:26F89F88CADE10C4ED93D864977876C6E13847E1036CDAD27BDB3B539C9DB450 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:E785F8C5B094E1EBFCFFC225DC2D7661 | SHA256:A381A568E13A03ADC7276A7327DFB7E658AEF7ACC3336EA7B9D700BC3DF2A7B4 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:4576A9EEC235D01185E3A55AF77732A4 | SHA256:A135BF635F73DAEC819E8BE68D08D44CBC161632CDF9907D885044E4C1193963 | |||
| 5728 | cursor-vip_windows_amd64.exe | C:\Users\admin\.cursor-vip\ca.pem | text | |
MD5:3CA699EA523468B0FC09A67F0AB84D94 | SHA256:8BB1CF32065E5DAEFAFCB3C4AFF4B5AFA26326A3BA397B25D89A9E87CCF21CBA | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\Init[1].htm | html | |
MD5:802DFEE92BE6128A94DE553C00A61717 | SHA256:2E35213D0B087451126CA2A419FA7CBFF6F0041E2871402473AFFF5D8FA76ED7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
119
DNS requests
140
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2160 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2160 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3692 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
3900 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
3900 | firefox.exe | POST | 200 | 2.16.202.114:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
3900 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
3900 | firefox.exe | POST | 200 | 95.101.54.122:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1684 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.21.65.153:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5728 | cursor-vip_windows_amd64.exe | 104.21.11.16:443 | cursor.jeter.eu.org | CLOUDFLARENET | — | unknown |
1076 | svchost.exe | 23.212.90.82:443 | go.microsoft.com | AKAMAI-AS | MX | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
cursor.jeter.eu.org |
| unknown |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |