| URL: | https://tinyurl.com/sw2pfpr9 |
| Full analysis: | https://app.any.run/tasks/a012bae1-a093-45f0-9798-5e67b191ca51 |
| Verdict: | Suspicious activity |
| Analysis date: | May 12, 2023, 04:50:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 2E46D9DFD0FB74E36749E3B670ADC577 |
| SHA1: | EC3C0D674E25F4D0680ED51E285AFE89932DEF42 |
| SHA256: | 3BA2C630838A1839DC7606EE0B1A3599CA3E85B367B84AB01FE0A3577563C80E |
| SSDEEP: | 3:N8EzLdINSXTcn:2EndmkTcn |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Create files in a temporary directory
- iexplore.exe (PID: 3768)
- iexplore.exe (PID: 3316)
Application launched itself
- iexplore.exe (PID: 3316)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3316 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://tinyurl.com/sw2pfpr9" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3768 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3316 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
35 714
Read events
35 492
Write events
218
Delete events
4
Modification events
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3316) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
2
Suspicious files
56
Text files
48
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3316 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:60E3CAB7482457E16687E22ED7012D68 | SHA256:D63959FBC05F4B391F6E88729812C2316DD178E36D998893805F1D19A3D3EDAB | |||
| 3316 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3316 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\F0Z23QXX.txt | text | |
MD5:FDB304B10DA81DB0E69DCF4A282EDE07 | SHA256:D5A8918EA722A038C57AD485BA64C8F0FCE5C630F01F76E744B0C26F92F53F18 | |||
| 3768 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 3768 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\bootstrap.min[1].css | text | |
MD5:450FC463B8B1A349DF717056FBB3E078 | SHA256:2C0F3DCFE93D7E380C290FE4AB838ED8CADFF1596D62697F5444BE460D1F876D | |||
| 3768 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\sw2pfpr9[1].htm | html | |
MD5:B322AA530508ED4B91BCB7E30287D3F7 | SHA256:ADF0AE6FAB5A5AD4EEBBBE3EEA47456CF258E44F28E45C603F2BE6E7F56A1EFC | |||
| 3768 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\c5d76fe02e00a83f31f7d53f20ed5a90[1].jpg | image | |
MD5:C5D76FE02E00A83F31F7D53F20ED5A90 | SHA256:1280727EC8FBDB680DF884B919E60C5B717AA2792AC939F67E717274A3632683 | |||
| 3316 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:BC78FBF119F317E3C904A09845575122 | SHA256:F87AEB8099C9A03C4845FAD91F44D4B4921AFF58A2D2A5873E9E8B65EB3512CC | |||
| 3316 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3316 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\imagestore\f7ruq93\imagestore.dat | binary | |
MD5:E9AF3FF8DD3A444BEBFF6AA24EFEC86E | SHA256:9BE198CB8E65CF49EABADAEDE6162371C6F45A559D0BF7ACB5C945459D0E6542 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
41
DNS requests
21
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3316 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3768 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?316f883f5ff4d0ca | US | compressed | 4.70 Kb | whitelisted |
3768 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?66ca256166adf5c3 | US | compressed | 4.70 Kb | whitelisted |
3768 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
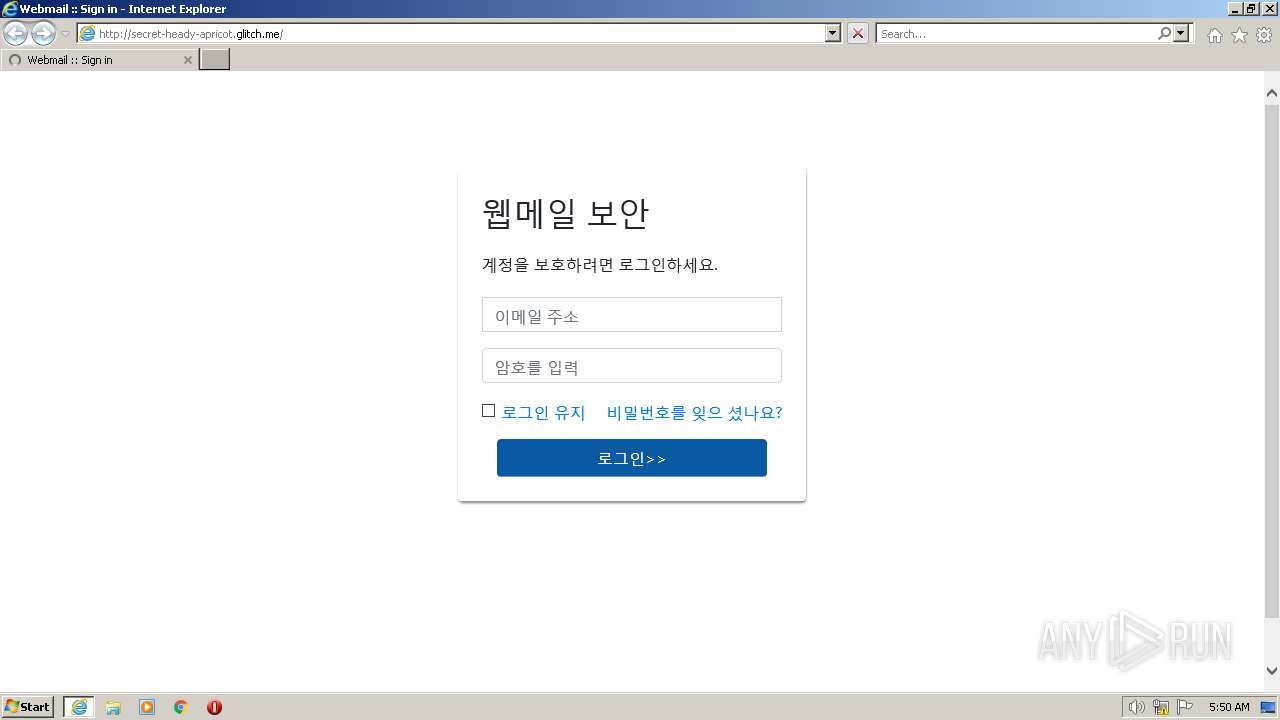
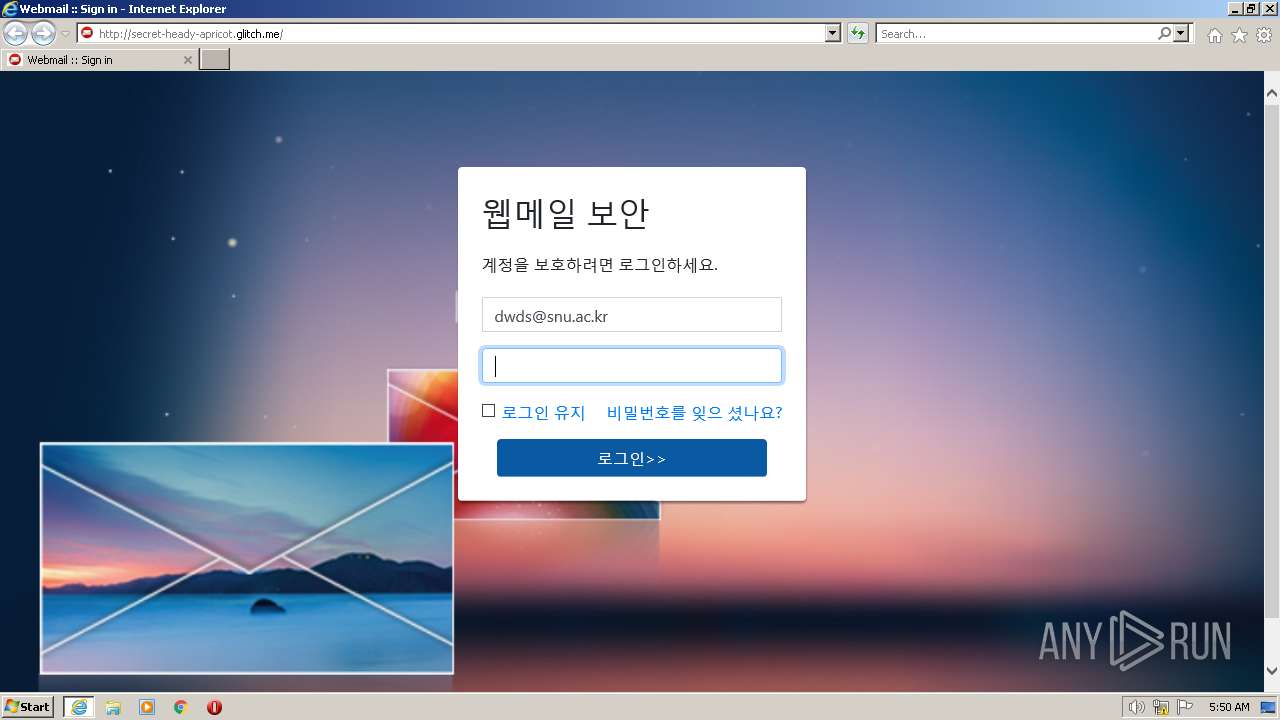
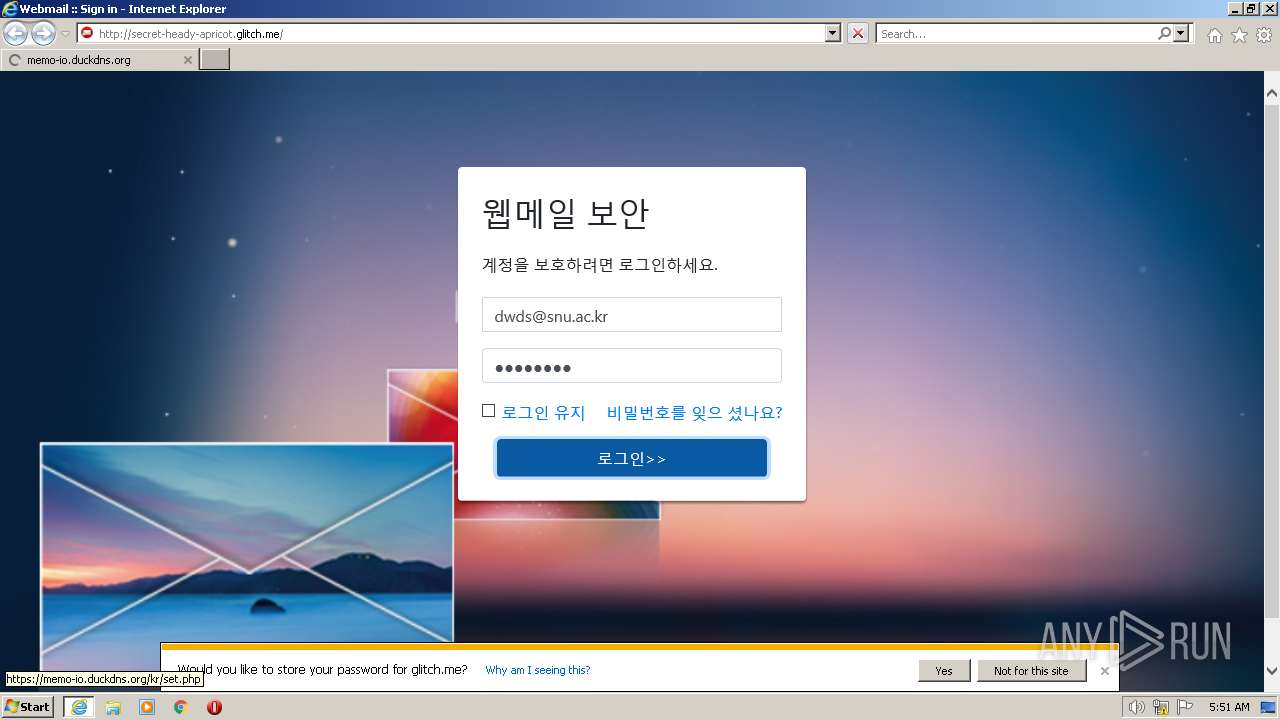
3768 | iexplore.exe | GET | 200 | 54.83.6.143:80 | http://secret-heady-apricot.glitch.me/ | US | html | 2.99 Kb | suspicious |
3768 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://status.geotrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR3enuod9bxDxzpICGW%2B2sabjf17QQUkFj%2FsJx1qFFUd7Ht8qNDFjiebMUCEA8q%2FLT2FaM7iCc5X8zga6c%3D | US | binary | 471 b | whitelisted |
3316 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3768 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?9d241eab883d24bf | US | compressed | 62.3 Kb | whitelisted |
3768 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAVG%2Fhgj9%2BGUHaOfzhTEYXM%3D | US | der | 471 b | whitelisted |
3768 | iexplore.exe | GET | 200 | 23.56.202.135:80 | http://x1.c.lencr.org/ | GB | der | 717 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3768 | iexplore.exe | 104.18.10.207:443 | maxcdn.bootstrapcdn.com | CLOUDFLARENET | — | suspicious |
3316 | iexplore.exe | 2.16.187.67:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
3768 | iexplore.exe | 104.18.8.178:443 | i.gyazo.com | CLOUDFLARENET | — | whitelisted |
3316 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3316 | iexplore.exe | 104.18.8.178:443 | i.gyazo.com | CLOUDFLARENET | — | whitelisted |
3768 | iexplore.exe | 84.38.134.199:443 | memo-io.duckdns.org | DataClub S.A. | LV | unknown |
3768 | iexplore.exe | 54.156.248.73:80 | secret-heady-apricot.glitch.me | AMAZON-AES | US | suspicious |
3768 | iexplore.exe | 2.16.186.35:80 | r3.o.lencr.org | Akamai International B.V. | DE | whitelisted |
3768 | iexplore.exe | 23.56.202.135:80 | x1.c.lencr.org | AKAMAI-AS | GB | suspicious |
3768 | iexplore.exe | 104.18.9.178:443 | i.gyazo.com | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
secret-heady-apricot.glitch.me |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
maxcdn.bootstrapcdn.com |
| whitelisted |
i.gyazo.com |
| whitelisted |
memo-io.duckdns.org |
| unknown |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Possible Social Engineering Attempted | ET HUNTING Suspicious Glitch Hosted DNS Request - Possible Phishing Landing |
3768 | iexplore.exe | Possible Social Engineering Attempted | ET HUNTING Suspicious Glitch Hosted GET Request - Possible Phishing Landing |
— | — | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
— | — | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |