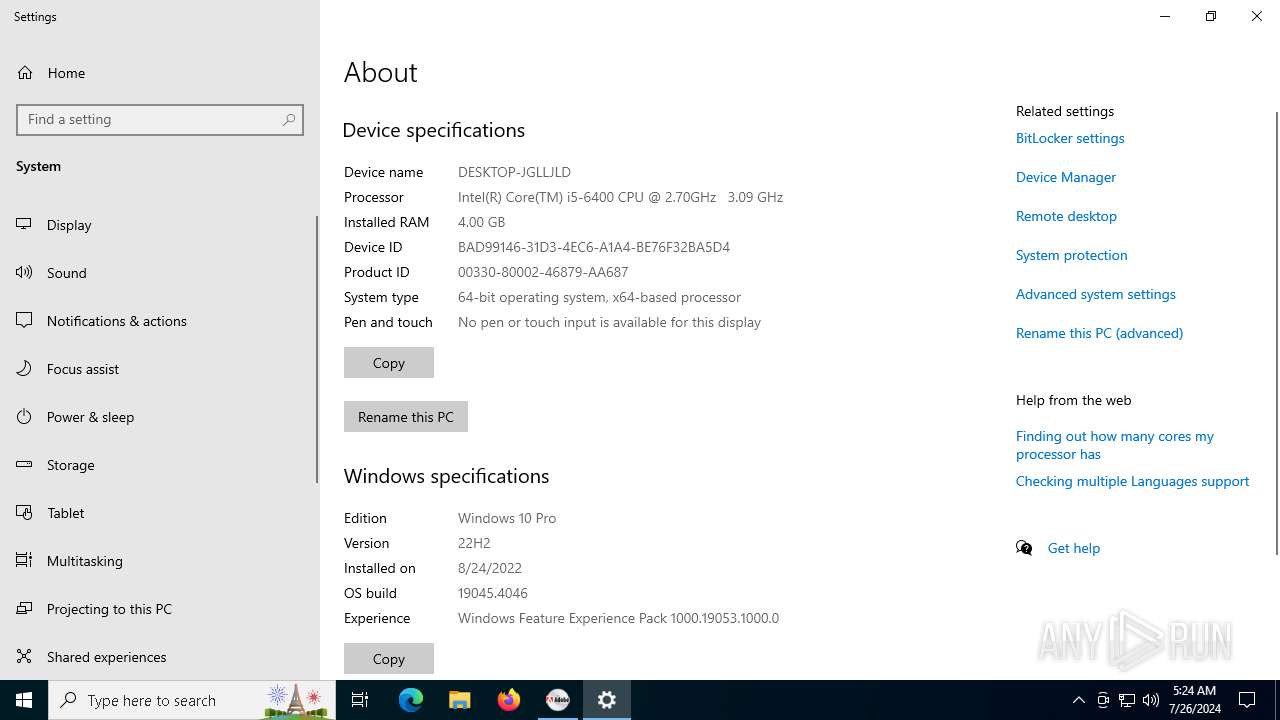
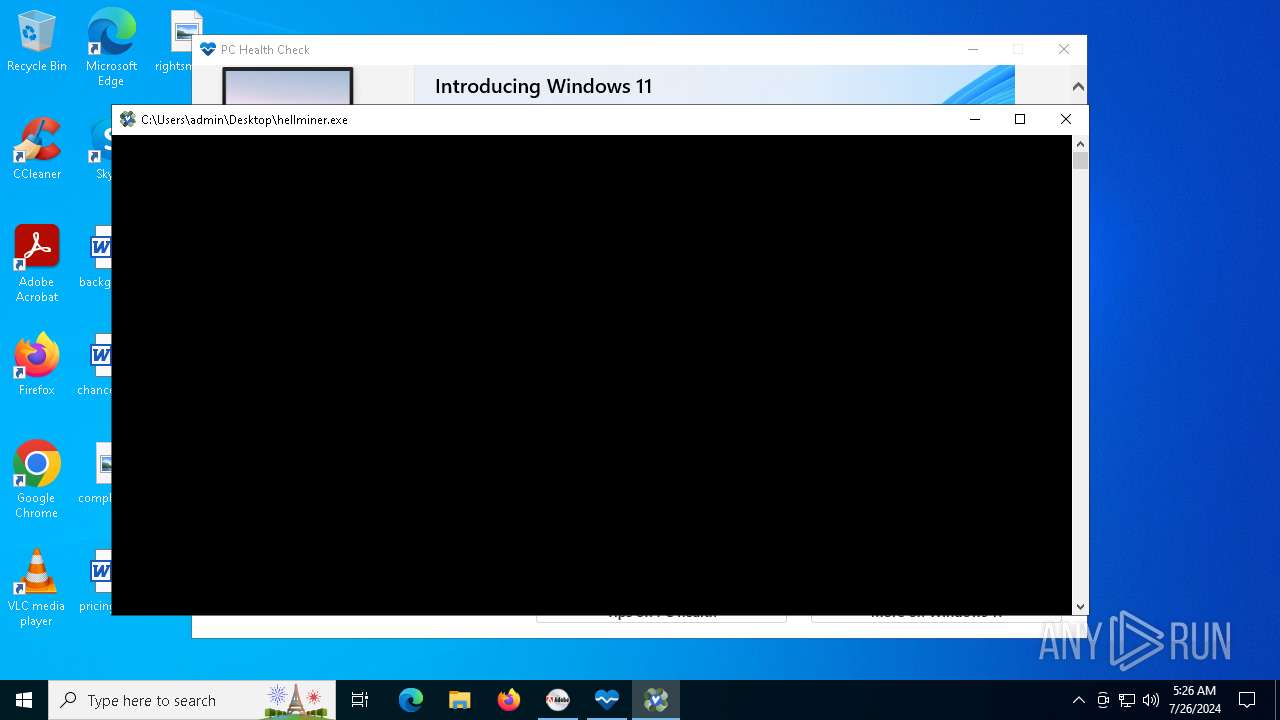
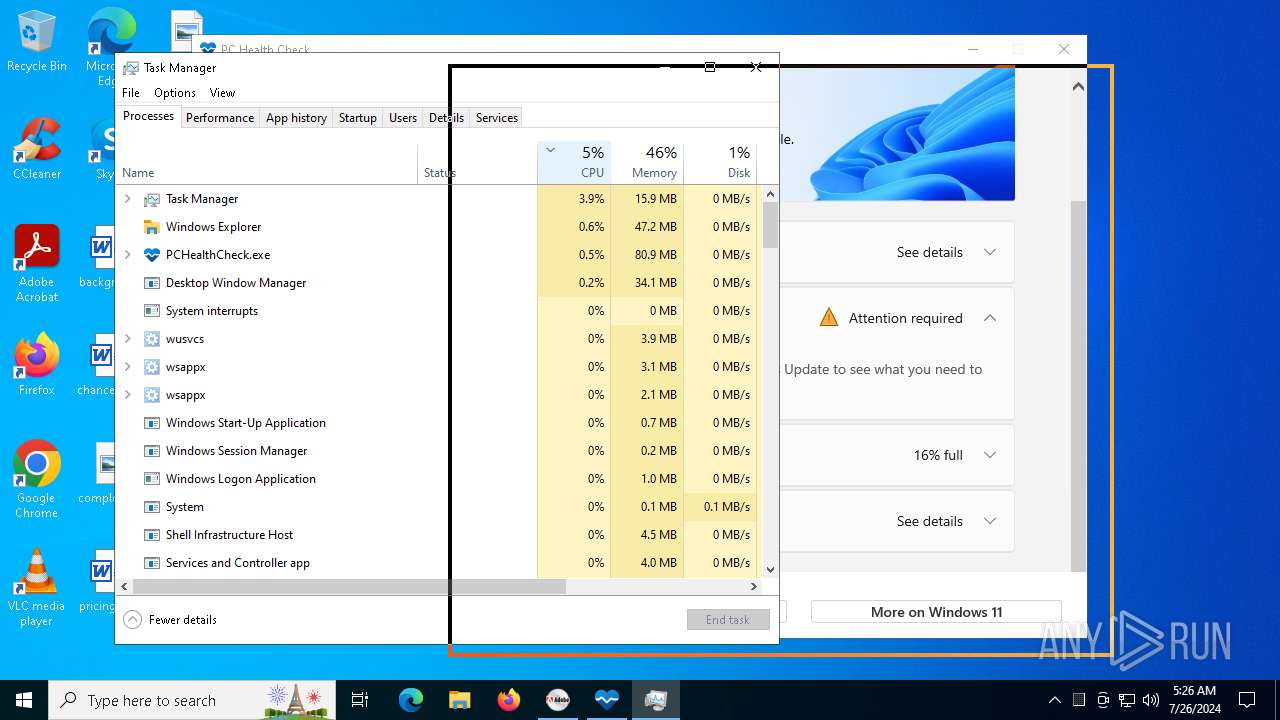
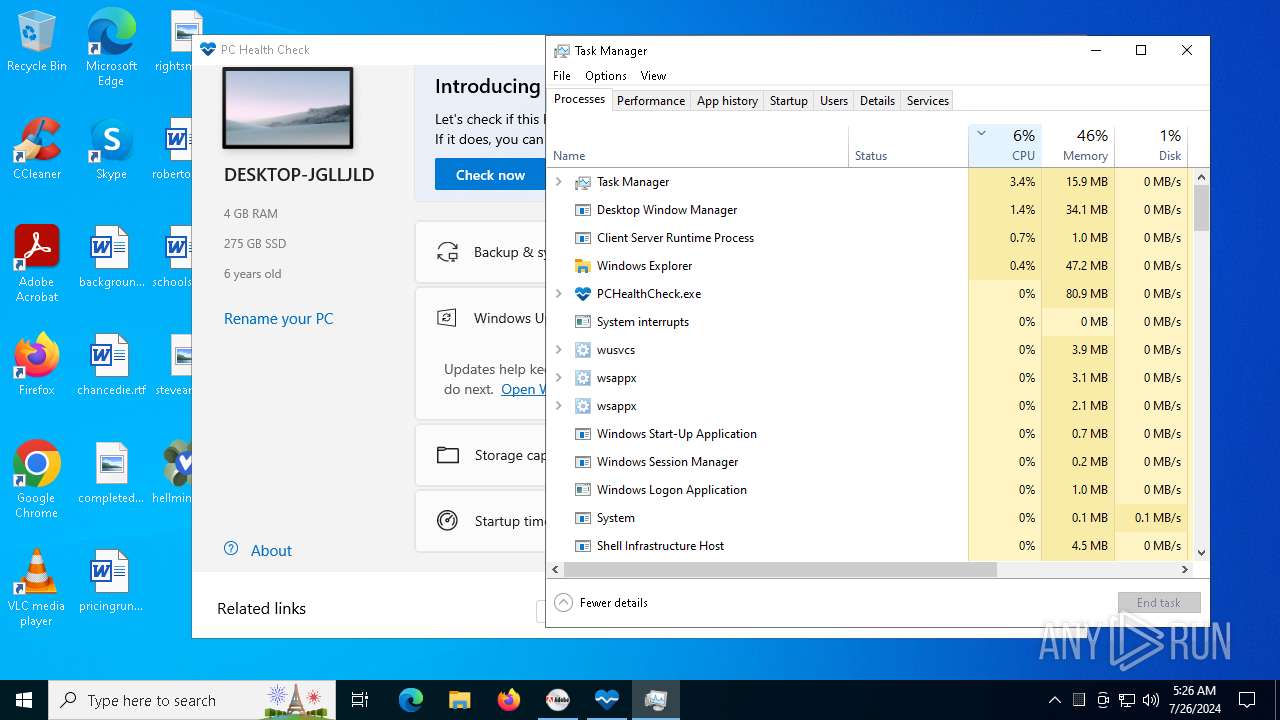
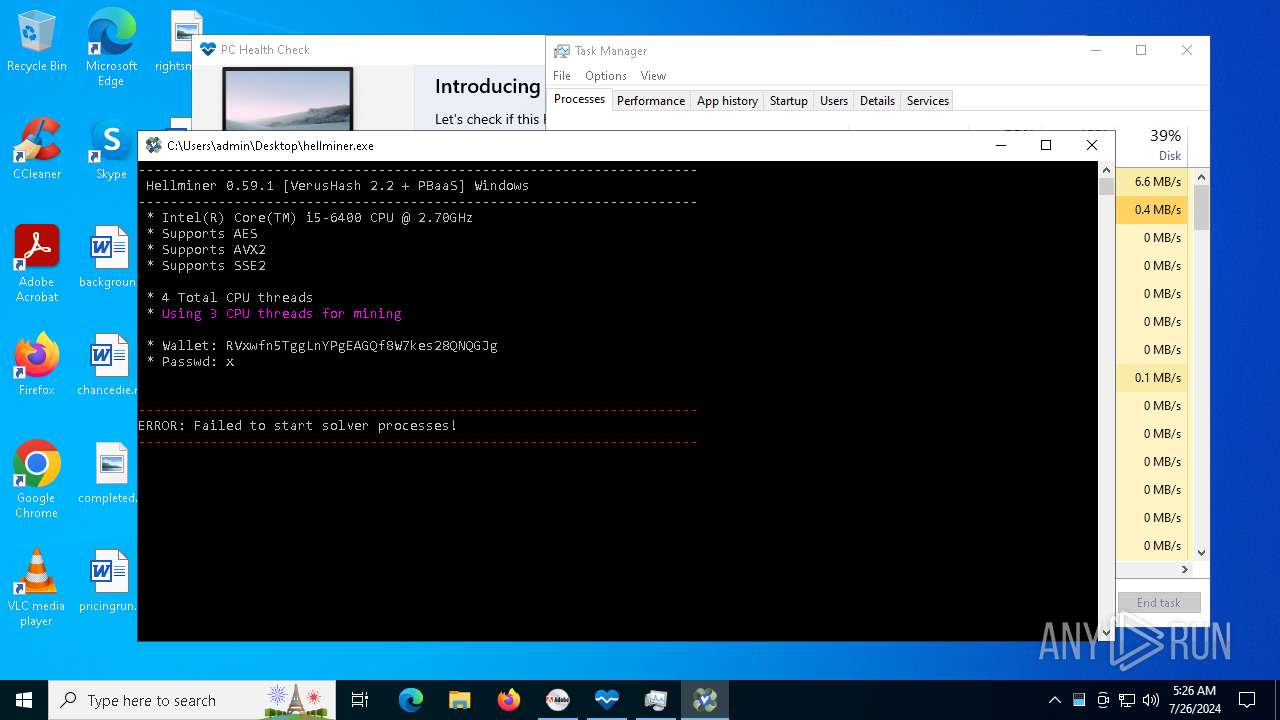
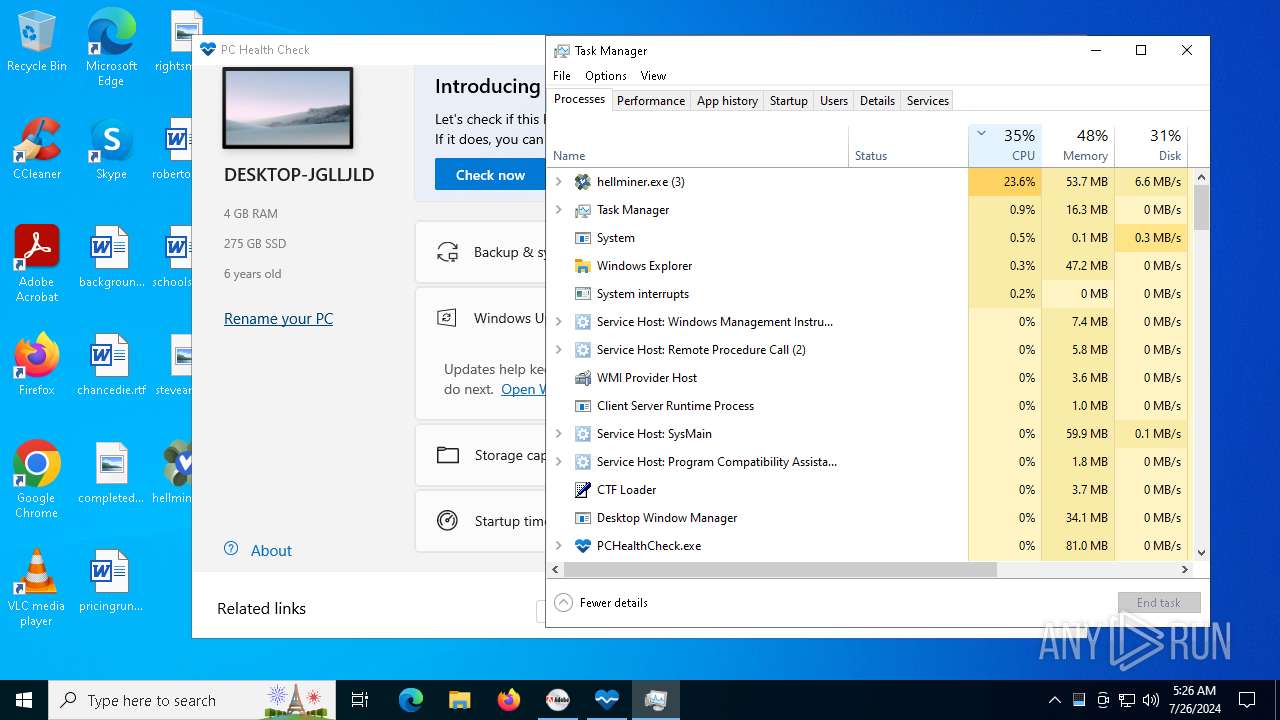
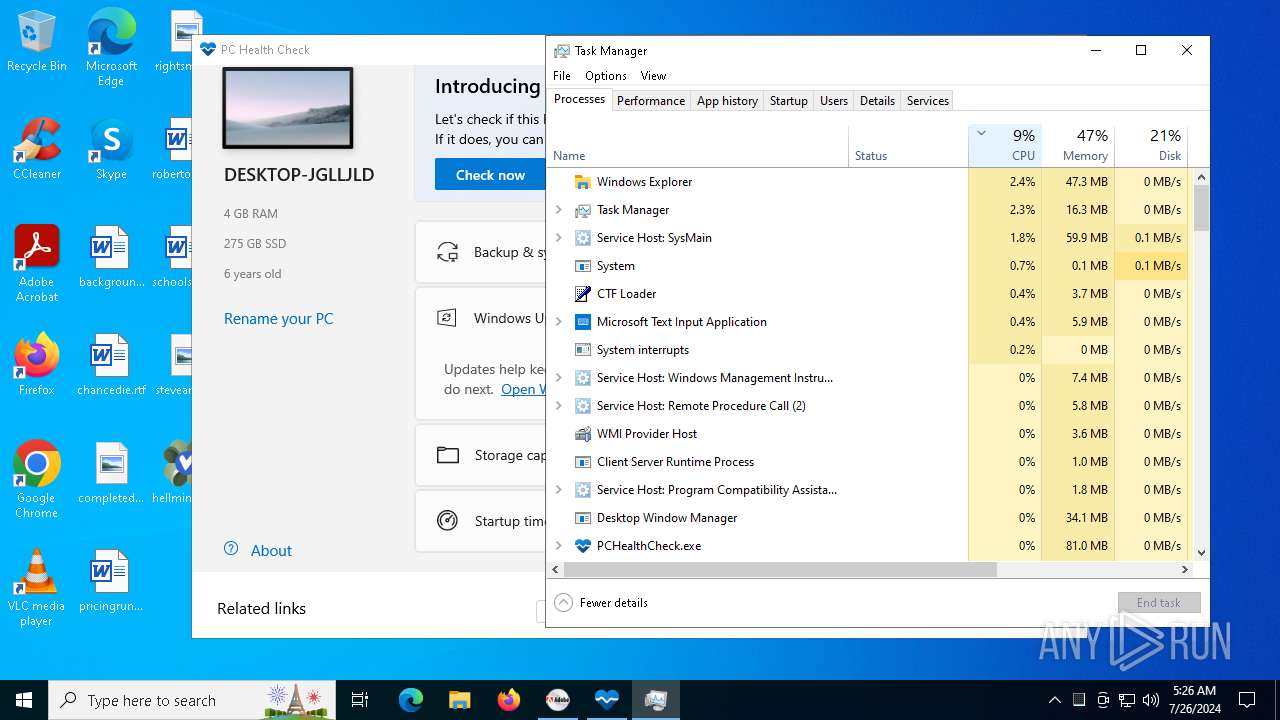
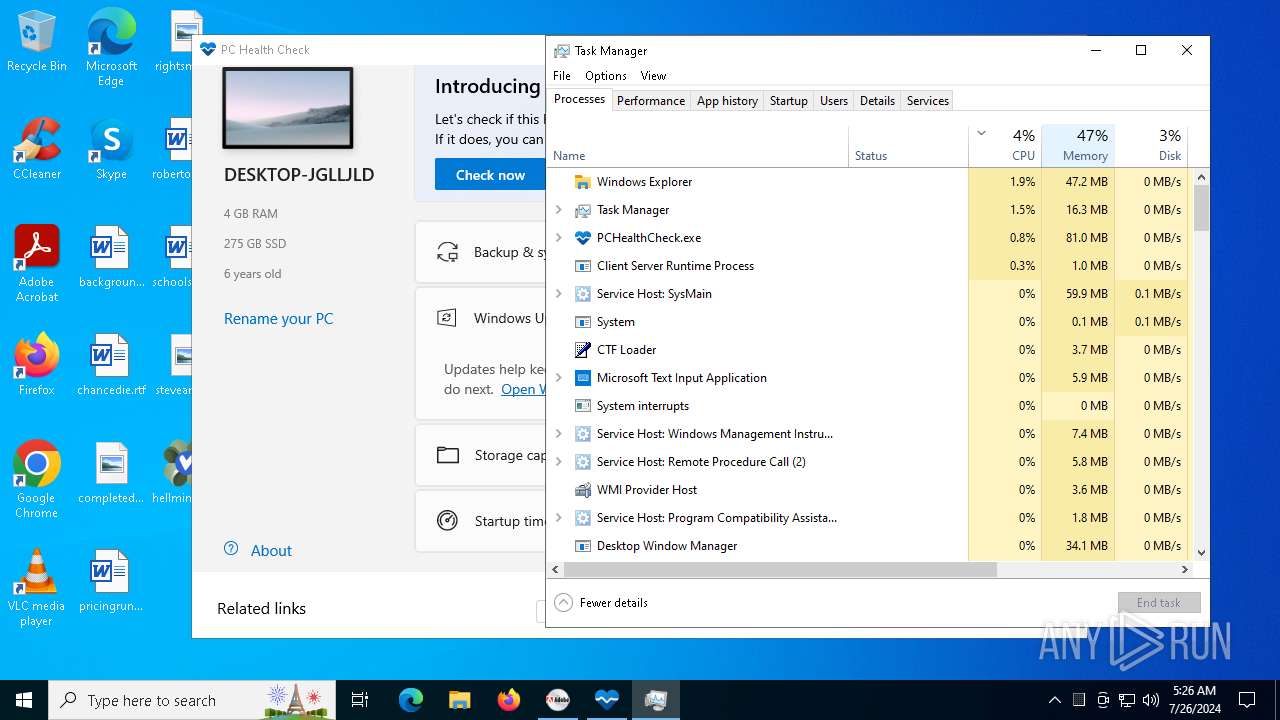
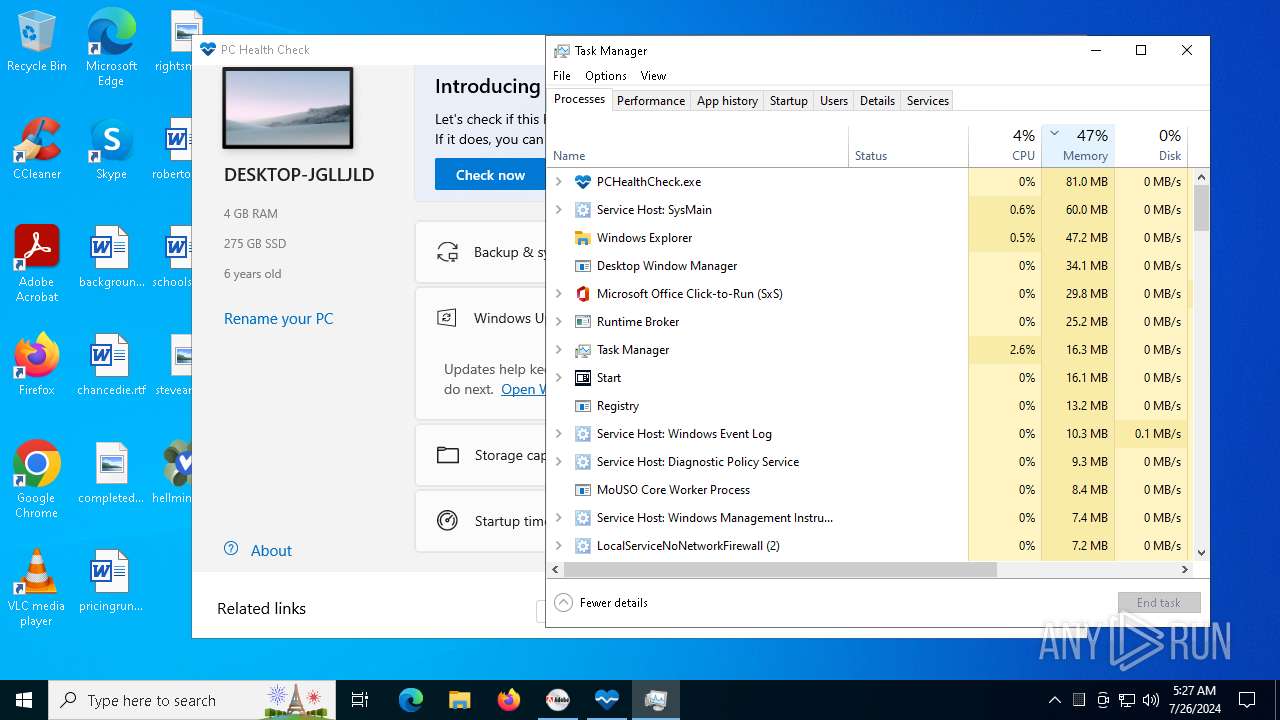
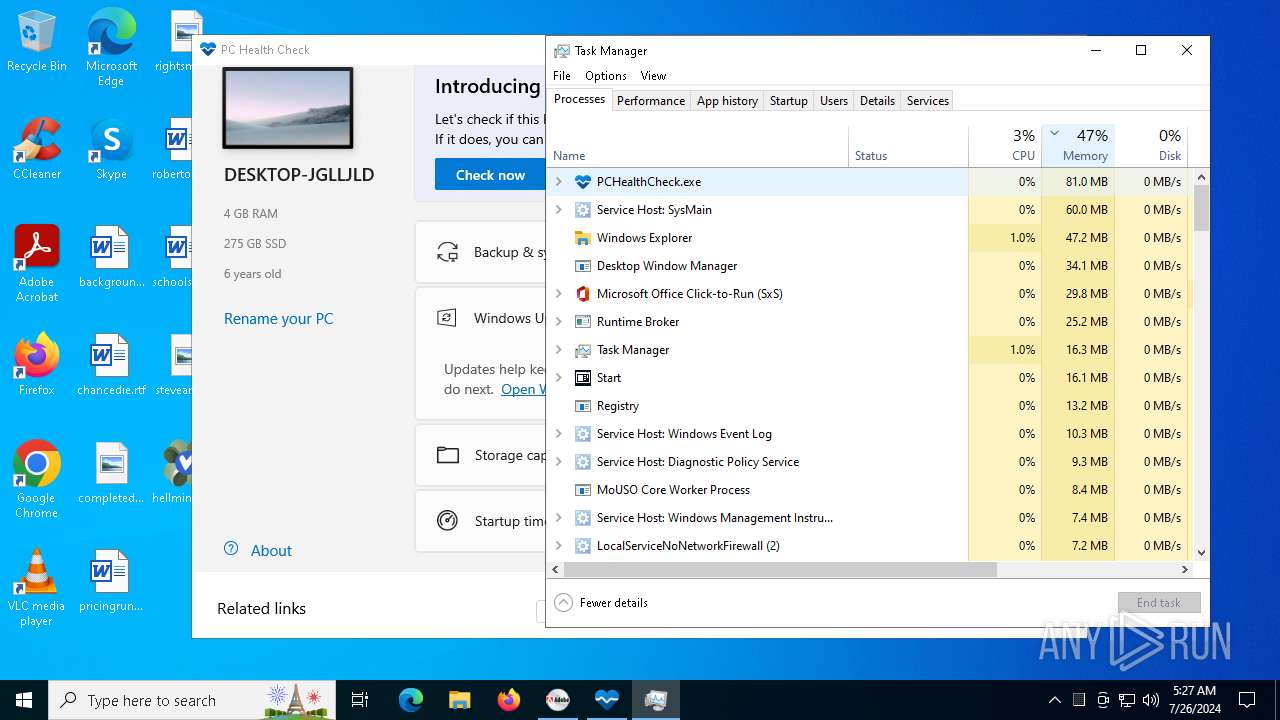
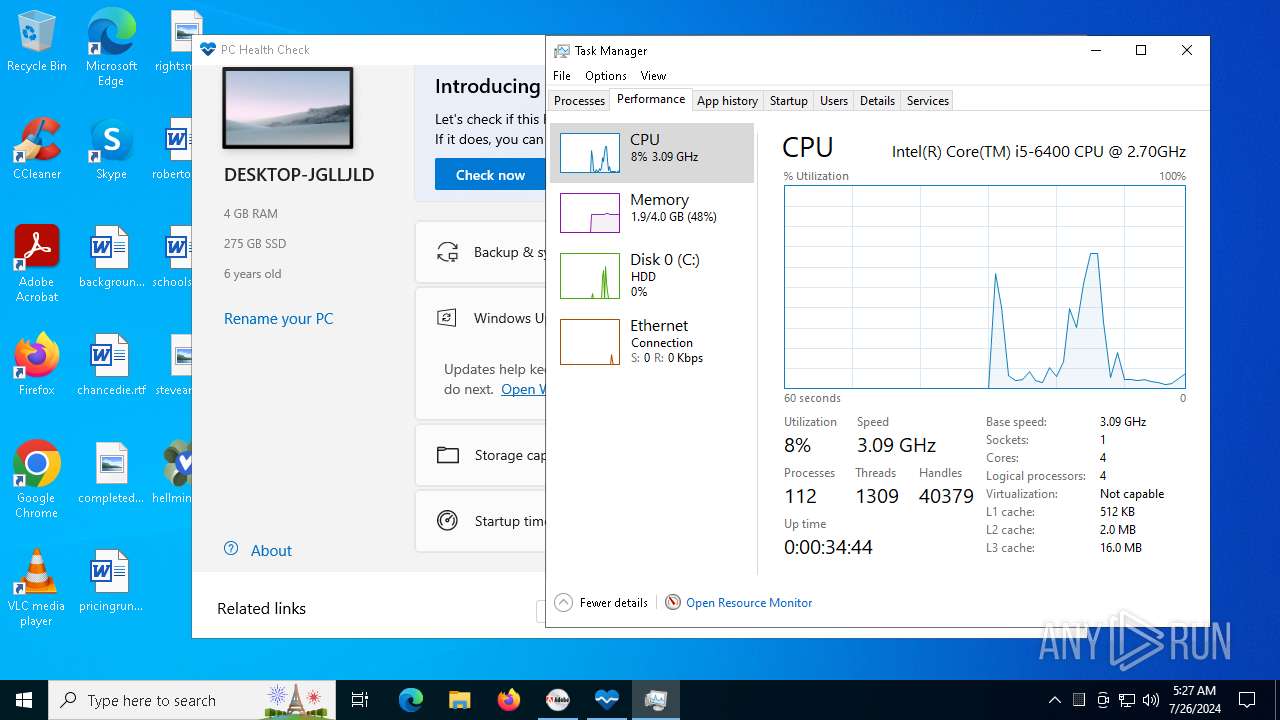
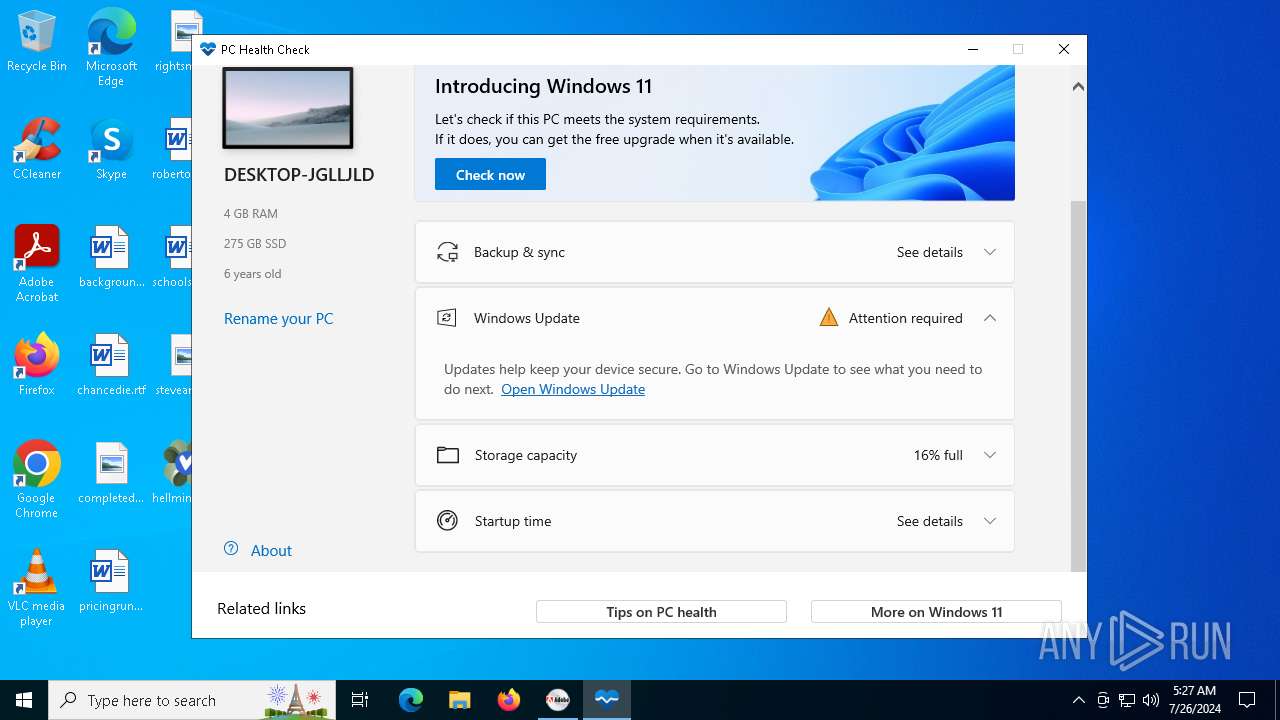
| File name: | autoplay.exe |
| Full analysis: | https://app.any.run/tasks/8248ea71-ee0a-40c8-bc88-e713904208b6 |
| Verdict: | Malicious activity |
| Analysis date: | July 26, 2024, 05:22:53 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 76EF16E94F77454AAFFDFA4C700BE85F |
| SHA1: | 9B45B3826706337A11E43248095FB2C62E42D14D |
| SHA256: | 3B9DABD99DC58A5242616CB6D1D876BCA3046119A9B150C7D7868BF02202EA82 |
| SSDEEP: | 3072:fNCpBPbYsMn1mx6nWGdN6YROBxQo6PfSPgHvUJjX1qINSxT3OIpkApPxn:fNiGC6nWGdN6YO6Pf9vAjX1qINGLdRz |
MALICIOUS
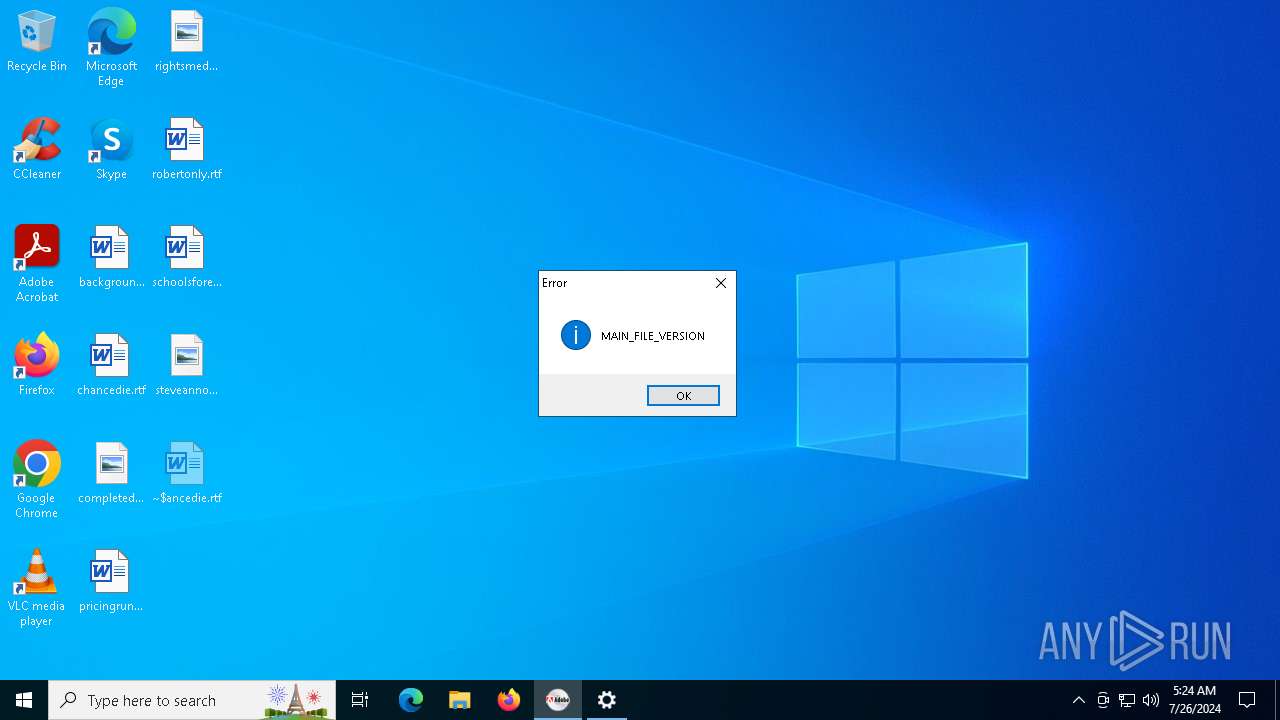
Drops the executable file immediately after the start
- autoplay.exe (PID: 3556)
- hellminer.exe (PID: 3680)
- hellminer.exe (PID: 8156)
SUSPICIOUS
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- wscript.exe (PID: 7996)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 7996)
Reads data from a binary Stream object (SCRIPT)
- wscript.exe (PID: 7996)
Reads Microsoft Outlook installation path
- PCHealthCheck.exe (PID: 2884)
Reads security settings of Internet Explorer
- PCHealthCheck.exe (PID: 2884)
Reads Internet Explorer settings
- PCHealthCheck.exe (PID: 2884)
Process drops legitimate windows executable
- hellminer.exe (PID: 3680)
- hellminer.exe (PID: 8156)
Reads the date of Windows installation
- PCHealthCheck.exe (PID: 2884)
Process drops python dynamic module
- hellminer.exe (PID: 3680)
- hellminer.exe (PID: 8156)
Executable content was dropped or overwritten
- hellminer.exe (PID: 3680)
- hellminer.exe (PID: 8156)
The process drops C-runtime libraries
- hellminer.exe (PID: 3680)
- hellminer.exe (PID: 8156)
Application launched itself
- hellminer.exe (PID: 3680)
- hellminer.exe (PID: 5836)
- hellminer.exe (PID: 8156)
- hellminer.exe (PID: 3336)
Uses WMIC.EXE to obtain CPU information
- hellminer.exe (PID: 5836)
- hellminer.exe (PID: 3336)
Loads Python modules
- hellminer.exe (PID: 6076)
- hellminer.exe (PID: 5836)
- hellminer.exe (PID: 3336)
- hellminer.exe (PID: 2936)
Starts CMD.EXE for commands execution
- hellminer.exe (PID: 6076)
- hellminer.exe (PID: 5836)
- hellminer.exe (PID: 3336)
- hellminer.exe (PID: 2936)
Uses WMIC.EXE to obtain operating system information
- hellminer.exe (PID: 5836)
- hellminer.exe (PID: 3336)
INFO
Checks supported languages
- autoplay.exe (PID: 3556)
- PCHealthCheck.exe (PID: 2884)
- hellminer.exe (PID: 3680)
- hellminer.exe (PID: 6076)
- hellminer.exe (PID: 5836)
- hellminer.exe (PID: 8156)
- hellminer.exe (PID: 3336)
- hellminer.exe (PID: 2936)
Manual execution by a user
- EXCEL.EXE (PID: 6036)
- WINWORD.EXE (PID: 7384)
- wscript.exe (PID: 7996)
- PCHealthCheck.exe (PID: 2884)
- hellminer.exe (PID: 3680)
- Taskmgr.exe (PID: 5220)
- Taskmgr.exe (PID: 8068)
- hellminer.exe (PID: 8156)
- mspaint.exe (PID: 2828)
Reads the computer name
- autoplay.exe (PID: 3556)
- PCHealthCheck.exe (PID: 2884)
- hellminer.exe (PID: 3680)
- hellminer.exe (PID: 8156)
Reads the software policy settings
- slui.exe (PID: 1432)
- PCHealthCheck.exe (PID: 2884)
Checks proxy server information
- slui.exe (PID: 1432)
- PCHealthCheck.exe (PID: 2884)
Process checks Internet Explorer phishing filters
- PCHealthCheck.exe (PID: 2884)
Reads Environment values
- PCHealthCheck.exe (PID: 2884)
Reads CPU info
- PCHealthCheck.exe (PID: 2884)
- hellminer.exe (PID: 5836)
- hellminer.exe (PID: 3336)
Create files in a temporary directory
- hellminer.exe (PID: 3680)
- hellminer.exe (PID: 6076)
- hellminer.exe (PID: 5836)
- hellminer.exe (PID: 8156)
- hellminer.exe (PID: 3336)
- hellminer.exe (PID: 2936)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6636)
- Taskmgr.exe (PID: 8068)
- WMIC.exe (PID: 2124)
- WMIC.exe (PID: 704)
- WMIC.exe (PID: 7360)
Checks operating system version
- hellminer.exe (PID: 6076)
- hellminer.exe (PID: 5836)
- hellminer.exe (PID: 3336)
- hellminer.exe (PID: 2936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2008:08:05 15:01:45+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 7.1 |
| CodeSize: | 118784 |
| InitializedDataSize: | 602112 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1257a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.0.0.0 |
| ProductVersionNumber: | 6.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Adobe Systems Incorporated |
| FileDescription: | AutoPlay |
| FileVersion: | 6 |
| InternalName: | AutoPlay |
| LegalCopyright: | © 1990-2008 Adobe Systems Incorporated |
| OriginalFileName: | AutoPlay.exe |
| ProductName: | Autoplay |
| ProductVersion: | 6 |
Total processes
190
Monitored processes
29
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 704 | wmic os get Version | C:\Windows\System32\wbem\WMIC.exe | — | hellminer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1432 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2124 | wmic os get Version | C:\Windows\System32\wbem\WMIC.exe | — | hellminer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2828 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\completedcareers.jpg" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2884 | "C:\Program Files\PCHealthCheck\PCHealthCheck.exe" | C:\Program Files\PCHealthCheck\PCHealthCheck.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2936 | "C:\Users\admin\Desktop\hellminer.exe" "--multiprocessing-fork" "parent_pid=3336" "pipe_handle=876" | C:\Users\admin\Desktop\hellminer.exe | — | hellminer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2976 | C:\WINDOWS\system32\cmd.exe /c "ver" | C:\Windows\System32\cmd.exe | — | hellminer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3336 | "C:\Users\admin\Desktop\hellminer.exe" | C:\Users\admin\Desktop\hellminer.exe | — | hellminer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3556 | "C:\Users\admin\AppData\Local\Temp\autoplay.exe" | C:\Users\admin\AppData\Local\Temp\autoplay.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: HIGH Description: AutoPlay Version: 6.0 Modules
| |||||||||||||||
| 3680 | "C:\Users\admin\Desktop\hellminer.exe" | C:\Users\admin\Desktop\hellminer.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
36 720
Read events
34 957
Write events
1 632
Delete events
131
Modification events
| (PID) Process: | (6036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (6036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\EXCEL\6036 |
| Operation: | write | Name: | 0 |
Value: 0B0E10D2FD6D5903358B46821E1A65BA3B4A49230046B9D4CCEDBEE3B7ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511942FD2120965007800630065006C002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (6036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (6036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (6036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (6036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (6036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (6036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (6036) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
181
Suspicious files
129
Text files
150
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6036 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\DTS\en-US{64146E5C-0C25-4BCA-80DF-21942DD6B965}\{BEF93B73-9FCF-4292-809B-C5677C985F8D}mt10000137.png | image | |
MD5:DE55D11D4C4071BB9F1B2A91487F41BE | SHA256:57733C40F13A9C7F44584AA52F0C1D1DB26C41C0AF73FD3EDD47C3288B85E892 | |||
| 6036 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:FAE54CE1C9C27A507D1BC31AB392C277 | SHA256:A8B8E071B1E3AB33760FC3F2C14A8584811BA1C0957D6CEABDD859E8F4174C87 | |||
| 6036 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\DTS\en-US{64146E5C-0C25-4BCA-80DF-21942DD6B965}\{AC34E556-9F63-4864-8835-58480FA35BF1}mt66963475.png | image | |
MD5:565A50517A947BCB35AA059AE76DC136 | SHA256:3DE17AA75ACA81445352705476C412168CC30993426E94D06265CCAE143CD5C8 | |||
| 6036 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\DTS\en-US{64146E5C-0C25-4BCA-80DF-21942DD6B965}\{387D716A-83CD-4D27-9C5C-1587D507CDBD}mt11414620.png | image | |
MD5:E37661AB4A1AEB408D06DDA183117349 | SHA256:0AF5FC368F802B927A820673ACFDE18B22B15DA0CE865203C065604939875A3F | |||
| 6036 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\DTS\en-US{64146E5C-0C25-4BCA-80DF-21942DD6B965}\{6870D108-418E-4CDE-A68C-B589A2AF0836}mt45299826.png | image | |
MD5:1A06FCC9279FE0FA76E1E74E2A26A747 | SHA256:55704B4D08BC44CB39D7BE93D9C595ECA75D2F6EAA4ADE529754360427F2396E | |||
| 6036 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:F0EE35F17F579389CDBF4B2007EB27EA | SHA256:3BDB219DAB26224B56BC4133FFEE6A16822BEBD9AAFA2DBCBE4BF4952F871134 | |||
| 6036 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\DTS\en-US{64146E5C-0C25-4BCA-80DF-21942DD6B965}\{86DA58C5-9DC3-407E-875D-C6D7A2321B39}mt67739505.png | image | |
MD5:FE238D4D994149381553BA0A5CD17B17 | SHA256:F25507CB3FAE7439117F05285EC6DE20A5A7356FAE74F5F935D31A63430598DA | |||
| 6036 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\DTS\en-US{64146E5C-0C25-4BCA-80DF-21942DD6B965}\{1F1D020B-6C8D-4BB1-88D5-D99C70E52F3A}mt16400647.png | image | |
MD5:D3590428E83DC27B626978EC0867477A | SHA256:6B7382E1BF3F58C62F21300DA74F13C649C46BC0FC244188371BA55C56B6117D | |||
| 6036 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\DTS\en-US{64146E5C-0C25-4BCA-80DF-21942DD6B965}\{4FCAE75E-AED0-465A-8048-89B9DD390451}mt11829122.png | image | |
MD5:3EE6FB71B09A2ECADEEAC7C3B55E1382 | SHA256:3A982A3B7E10EC50D2AF3A126277D48F41AE65756C7A5FDD5802049B5350704A | |||
| 6036 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\DTS\en-US{64146E5C-0C25-4BCA-80DF-21942DD6B965}\{16AFE128-D8F7-4739-890E-94E63648F782}mt16400656.png | image | |
MD5:0B4B576B60F444C6502461711E7432DB | SHA256:07F2B6E764FFBDD8D0FF28642B47417F27072E52BB581280D8C50261E01D4C96 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
192
DNS requests
60
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1328 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6036 | EXCEL.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4172 | SystemSettings.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4172 | SystemSettings.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7384 | WINWORD.EXE | GET | 200 | 23.32.238.34:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
7384 | WINWORD.EXE | GET | 200 | 23.32.238.34:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5368 | SearchApp.exe | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5368 | SearchApp.exe | 104.126.37.162:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4548 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6012 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5284 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6716 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1320 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
t-ring-fdv2.msedge.net |
| unknown |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
s-ring.msedge.net |
| unknown |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|