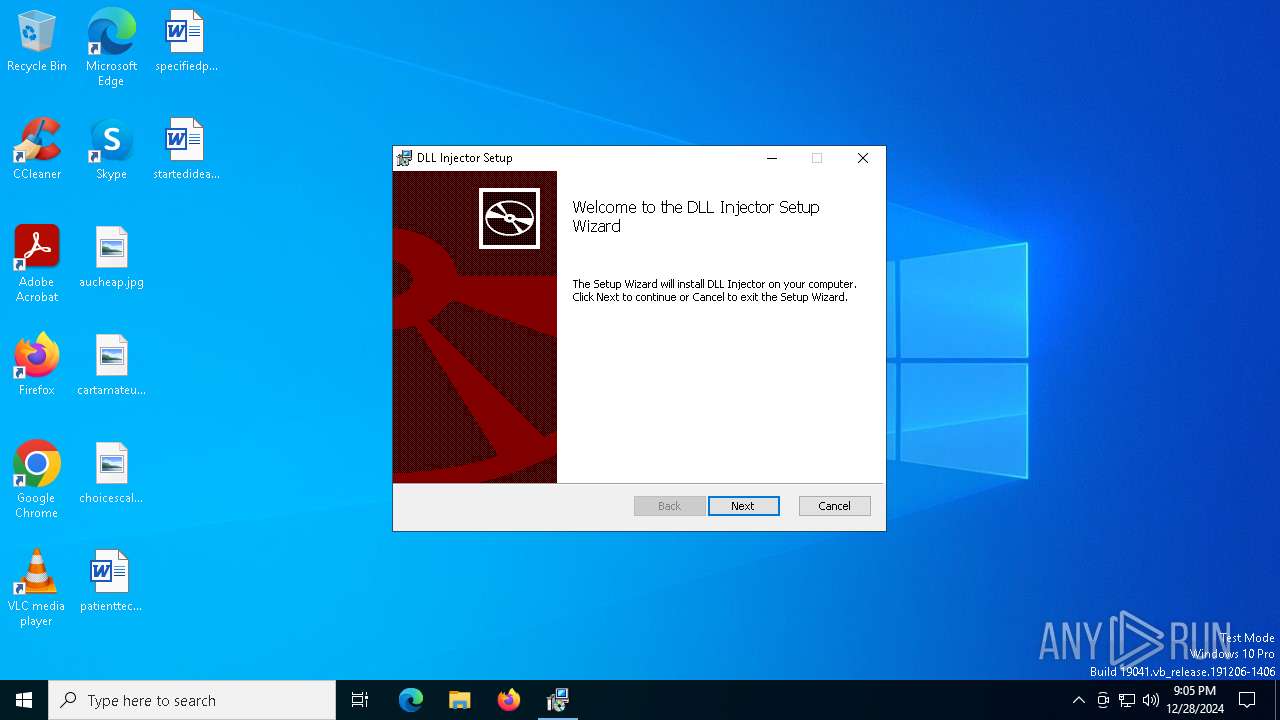
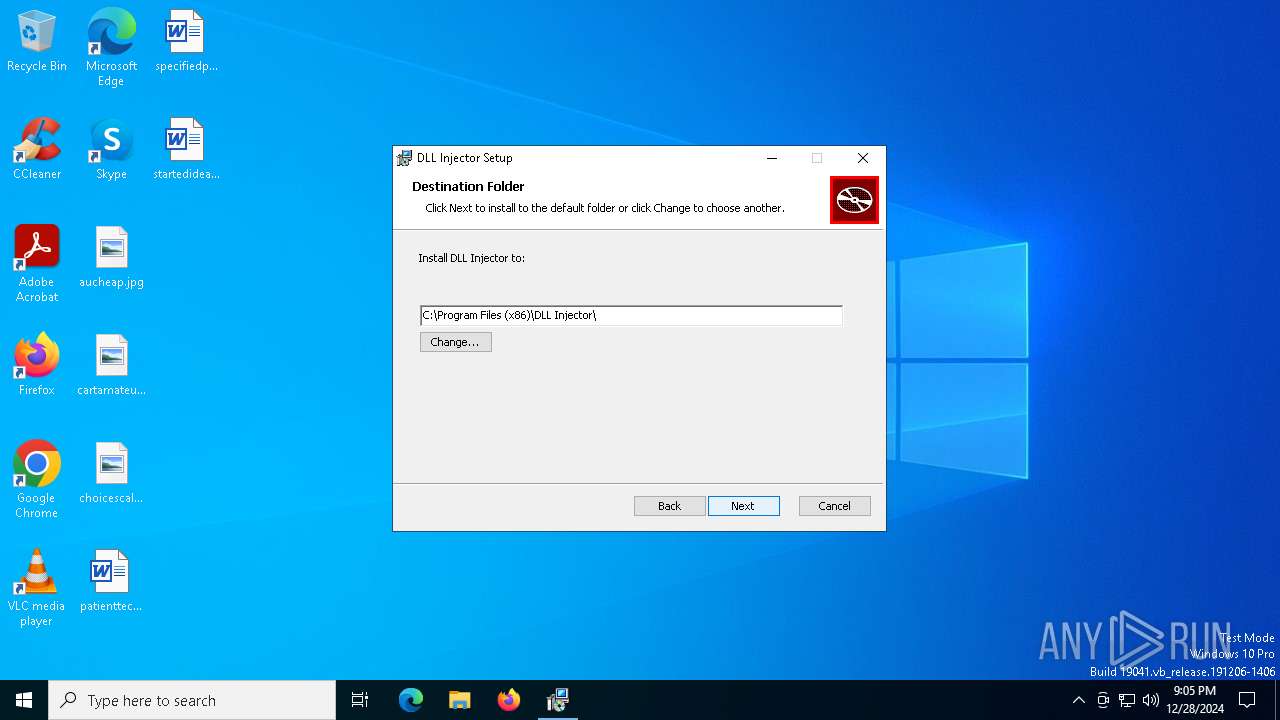
| File name: | DLL Injector_2.1.0_x86_en-US.msi |
| Full analysis: | https://app.any.run/tasks/4f82c7cc-163a-4bbc-af07-d785c86bc827 |
| Verdict: | Malicious activity |
| Analysis date: | December 28, 2024, 21:05:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: DLL Injector, Author: dllinjector, Keywords: Installer, Comments: This installer database contains the logic and data required to install DLL Injector., Template: Intel;0, Revision Number: {E548A4FB-865F-44C0-B2B9-28DA9B180D1F}, Create Time/Date: Tue Mar 14 20:31:28 2023, Last Saved Time/Date: Tue Mar 14 20:31:28 2023, Number of Pages: 450, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | 0592CA25CF22E8D5DAABACD1130D38F6 |
| SHA1: | 0A59FD8723DE4CB9BF6C3272A5DB7771E575EFF9 |
| SHA256: | 3B8991F1EEBFC46988DB25FE0DED11C3C08DF81AE2CA1BAF9103BA8259CAFC99 |
| SSDEEP: | 49152:TXt8FXtmZR9m+/YXz573yI2FvlfC+fM//uuEUNLTVx+pv/Z1BWCMnT5ldQqnUIwJ:T98FXinYXz5ryI2FvvM/mu/NLT41BWdG |
MALICIOUS
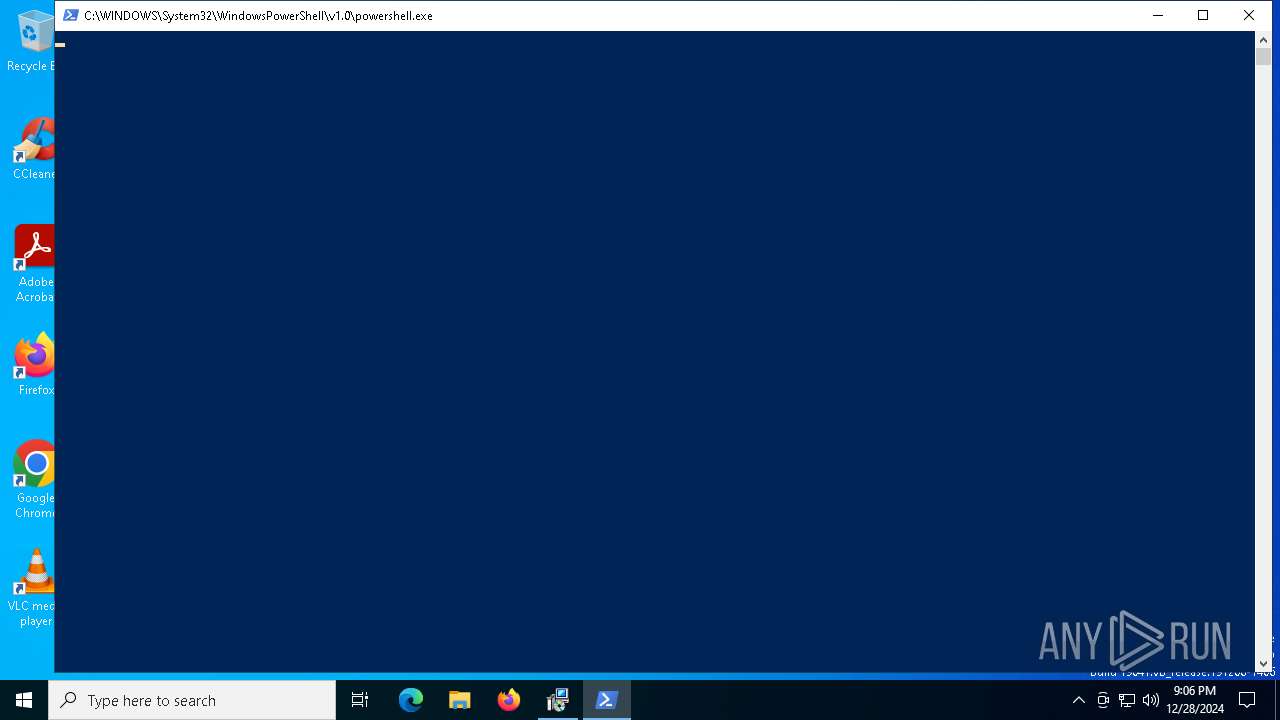
Run PowerShell with an invisible window
- powershell.exe (PID: 4528)
Changes the autorun value in the registry
- MicrosoftEdgeUpdate.exe (PID: 7016)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 7096)
Starts process via Powershell
- powershell.exe (PID: 4528)
Downloads file from URI via Powershell
- powershell.exe (PID: 4528)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 6424)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 6424)
Manipulates environment variables
- powershell.exe (PID: 4528)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 4528)
Executable content was dropped or overwritten
- powershell.exe (PID: 4528)
- MicrosoftEdgeWebview2Setup.exe (PID: 6876)
- MicrosoftEdgeUpdate.exe (PID: 7016)
Process drops legitimate windows executable
- powershell.exe (PID: 4528)
- MicrosoftEdgeUpdate.exe (PID: 7016)
- MicrosoftEdgeWebview2Setup.exe (PID: 6876)
Starts a Microsoft application from unusual location
- MicrosoftEdgeWebview2Setup.exe (PID: 6876)
- MicrosoftEdgeUpdate.exe (PID: 7016)
Creates/Modifies COM task schedule object
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2076)
- MicrosoftEdgeUpdate.exe (PID: 5732)
Reads security settings of Internet Explorer
- MicrosoftEdgeUpdate.exe (PID: 7016)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 7016)
Potential Corporate Privacy Violation
- svchost.exe (PID: 6232)
INFO
An automatically generated document
- msiexec.exe (PID: 6308)
Reads the computer name
- msiexec.exe (PID: 7044)
- msiexec.exe (PID: 6424)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2076)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 5972)
- MicrosoftEdgeUpdate.exe (PID: 2396)
- MicrosoftEdgeUpdate.exe (PID: 7016)
- MicrosoftEdgeUpdate.exe (PID: 5732)
- MicrosoftEdgeUpdate.exe (PID: 5780)
- MicrosoftEdgeUpdate.exe (PID: 736)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6308)
- msiexec.exe (PID: 6424)
Checks supported languages
- msiexec.exe (PID: 6424)
- msiexec.exe (PID: 7044)
- MicrosoftEdgeWebview2Setup.exe (PID: 6876)
- MicrosoftEdgeUpdate.exe (PID: 7016)
- MicrosoftEdgeUpdate.exe (PID: 5732)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2076)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 5972)
- MicrosoftEdgeUpdate.exe (PID: 2396)
- MicrosoftEdgeUpdate.exe (PID: 5780)
- MicrosoftEdgeUpdate.exe (PID: 736)
Manages system restore points
- SrTasks.exe (PID: 3364)
Creates a software uninstall entry
- msiexec.exe (PID: 6424)
Disables trace logs
- powershell.exe (PID: 4528)
Checks proxy server information
- powershell.exe (PID: 4528)
- MicrosoftEdgeUpdate.exe (PID: 2396)
- MicrosoftEdgeUpdate.exe (PID: 736)
The executable file from the user directory is run by the Powershell process
- MicrosoftEdgeWebview2Setup.exe (PID: 6876)
The sample compiled with english language support
- powershell.exe (PID: 4528)
- MicrosoftEdgeUpdate.exe (PID: 7016)
- MicrosoftEdgeWebview2Setup.exe (PID: 6876)
Create files in a temporary directory
- MicrosoftEdgeWebview2Setup.exe (PID: 6876)
- svchost.exe (PID: 6232)
Creates files or folders in the user directory
- MicrosoftEdgeUpdate.exe (PID: 7016)
Reads Environment values
- MicrosoftEdgeUpdate.exe (PID: 2396)
Reads the software policy settings
- MicrosoftEdgeUpdate.exe (PID: 2396)
- MicrosoftEdgeUpdate.exe (PID: 736)
Process checks computer location settings
- MicrosoftEdgeUpdate.exe (PID: 7016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | DLL Injector |
| Author: | dllinjector |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install DLL Injector. |
| Template: | Intel;0 |
| RevisionNumber: | {E548A4FB-865F-44C0-B2B9-28DA9B180D1F} |
| CreateDate: | 2023:03:14 20:31:28 |
| ModifyDate: | 2023:03:14 20:31:28 |
| Pages: | 450 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
149
Monitored processes
18
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 736 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" -Embedding | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Version: 1.3.195.43 Modules
| |||||||||||||||
| 2076 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.43\MicrosoftEdgeUpdateComRegisterShell64.exe" /user | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.43\MicrosoftEdgeUpdateComRegisterShell64.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update COM Registration Helper Exit code: 0 Version: 1.3.195.43 Modules
| |||||||||||||||
| 2396 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /ping PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiPz48cmVxdWVzdCBwcm90b2NvbD0iMy4wIiB1cGRhdGVyPSJPbWFoYSIgdXBkYXRlcnZlcnNpb249IjEuMy4xOTUuNDMiIHNoZWxsX3ZlcnNpb249IjEuMy4xOTUuNDMiIGlzbWFjaGluZT0iMCIgc2Vzc2lvbmlkPSJ7RTQ5NzVCRTktMTRGQy00NUVGLUJDMjctRUU5QUZCNzY0QTdFfSIgdXNlcmlkPSJ7OTE0Mzg2NDgtNUYyMy00NUYxLUJFNzAtMjIwQjk5NjdDODYwfSIgaW5zdGFsbHNvdXJjZT0ib3RoZXJpbnN0YWxsY21kIiByZXF1ZXN0aWQ9IntBQTg0NUEyMi1FQkNELTQ0MjAtOUYxMC0wNkI5MDNDNDU5NkR9IiBkZWR1cD0iY3IiIGRvbWFpbmpvaW5lZD0iMCI-PGh3IGxvZ2ljYWxfY3B1cz0iNCIgcGh5c21lbW9yeT0iNCIgZGlza190eXBlPSIyIiBzc2U9IjEiIHNzZTI9IjEiIHNzZTM9IjEiIHNzc2UzPSIxIiBzc2U0MT0iMSIgc3NlNDI9IjEiIGF2eD0iMSIvPjxvcyBwbGF0Zm9ybT0id2luIiB2ZXJzaW9uPSIxMC4wLjE5MDQ1LjQwNDYiIHNwPSIiIGFyY2g9Ing2NCIgcHJvZHVjdF90eXBlPSI0OCIgaXNfd2lwPSIwIiBpc19pbl9sb2NrZG93bl9tb2RlPSIwIi8-PG9lbSBwcm9kdWN0X21hbnVmYWN0dXJlcj0iREVMTCIgcHJvZHVjdF9uYW1lPSJERUxMIi8-PGV4cCBldGFnPSIiLz48YXBwIGFwcGlkPSJ7RjNDNEZFMDAtRUZENS00MDNCLTk1NjktMzk4QTIwRjFCQTRBfSIgdmVyc2lvbj0iIiBuZXh0dmVyc2lvbj0iMS4zLjE5NS40MyIgbGFuZz0iIiBicmFuZD0iIiBjbGllbnQ9IiI-PGV2ZW50IGV2ZW50dHlwZT0iMiIgZXZlbnRyZXN1bHQ9IjEiIGVycm9yY29kZT0iMCIgZXh0cmFjb2RlMT0iMCIgc3lzdGVtX3VwdGltZV90aWNrcz0iMTI5NjY1NDcyMDkiIGluc3RhbGxfdGltZV9tcz0iNTYzIi8-PC9hcHA-PC9yZXF1ZXN0Pg | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | MicrosoftEdgeUpdate.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.195.43 Modules
| |||||||||||||||
| 3224 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3364 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4528 | powershell.exe -NoProfile -windowstyle hidden try { [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12 } catch {}; Invoke-WebRequest -Uri "https://go.microsoft.com/fwlink/p/?LinkId=2124703" -OutFile "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" ; Start-Process -FilePath "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" -ArgumentList ('/silent', '/install') -Wait | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5732 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /regserver | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.195.43 Modules
| |||||||||||||||
| 5780 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /handoff "appguid={F3017226-FE2A-4295-8BDF-00C3A9A7E4C5}&appname=Microsoft%20Edge%20Webview2%20Runtime&needsadmin=false" /installsource otherinstallcmd /sessionid "{E4975BE9-14FC-45EF-BC27-EE9AFB764A7E}" /silent | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Version: 1.3.195.43 Modules
| |||||||||||||||
| 5972 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.43\MicrosoftEdgeUpdateComRegisterShell64.exe" /user | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.43\MicrosoftEdgeUpdateComRegisterShell64.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update COM Registration Helper Exit code: 0 Version: 1.3.195.43 Modules
| |||||||||||||||
Total events
12 648
Read events
11 446
Write events
1 159
Delete events
43
Modification events
| (PID) Process: | (6424) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000002719BD456C59DB0118190000A81B0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6424) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000002719BD456C59DB0118190000A81B0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6424) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000AC81FD456C59DB0118190000A81B0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6424) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000001E3602466C59DB0118190000A81B0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6424) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000A11CFB456C59DB0118190000A81B0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6424) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000A11CFB456C59DB0118190000A81B0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6424) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000918E6D466C59DB011819000028060000E80300000100000000000000000000002B2728EBAF6AA5488796F86ECDFB395700000000000000000000000000000000 | |||
| (PID) Process: | (7096) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4800000000000000909680466C59DB01B81B000038180000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7096) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7096) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
Executable files
207
Suspicious files
15
Text files
6
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6424 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6424 | msiexec.exe | C:\Windows\Installer\MSIAAAB.tmp | binary | |
MD5:2434F0C3E3B664BA599ADE3E1F7C8BB9 | SHA256:CE256FE56D7033985614F084C3AD193AB0C0B15971F9B409C788D15394DE0D71 | |||
| 6308 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI6862.tmp | executable | |
MD5:4FDD16752561CF585FED1506914D73E0 | SHA256:AECD2D2FE766F6D439ACC2BBF1346930ECC535012CF5AD7B3273D2875237B7E7 | |||
| 6424 | msiexec.exe | C:\Windows\Installer\13a79d.msi | executable | |
MD5:0592CA25CF22E8D5DAABACD1130D38F6 | SHA256:3B8991F1EEBFC46988DB25FE0DED11C3C08DF81AE2CA1BAF9103BA8259CAFC99 | |||
| 6424 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:903725DF5185BB3241D5CFA96535E553 | SHA256:9F40A4ADE19593DCC13B0809FE6281AB94D6608E015CB89A11846A14E39BDFBD | |||
| 6424 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{eb28272b-6aaf-48a5-8796-f86ecdfb3957}_OnDiskSnapshotProp | binary | |
MD5:BFE6504CC3EED32A237F96925BE2A6B1 | SHA256:5FA7BDD0A5D28BF954E8BEDF4665C4BB9AC3D688B22782CE545C0E68FB7962A1 | |||
| 6424 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:BFE6504CC3EED32A237F96925BE2A6B1 | SHA256:5FA7BDD0A5D28BF954E8BEDF4665C4BB9AC3D688B22782CE545C0E68FB7962A1 | |||
| 6424 | msiexec.exe | C:\Windows\Temp\~DF6652FA2ADD01C5B6.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 6424 | msiexec.exe | C:\Users\Public\Desktop\DLL Injector.lnk | binary | |
MD5:34877D28926581566B65B60191963D2B | SHA256:BF6E8375509FFCA6C3B6499DE6DA778E67F3B03547C4DA9912F34A5EE3993330 | |||
| 6424 | msiexec.exe | C:\Program Files (x86)\DLL Injector\Uninstall DLL Injector.lnk | binary | |
MD5:EB4094FB5E6F6963DF08C6FF5BACFA66 | SHA256:9C90996604D08BE934B8EBB4DF6BE4DAC234324FC219A2552AE81E4E6881D327 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
38
DNS requests
23
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4136 | SIHClient.exe | GET | 200 | 2.23.9.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6232 | svchost.exe | GET | — | 84.201.210.39:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7d9cd93c-1d5e-449b-9ad7-f1e8d6b90509?P1=1736024775&P2=404&P3=2&P4=AZ3LKc6tc0XzBkTWjcimB1L9cq%2fKY%2bT7kN1Zhqcqj4n1zFkDP1qJeT5NfbVppBNsKtRVAo0yEaOFa3lLmfCURg%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6552 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6232 | svchost.exe | HEAD | 200 | 84.201.210.39:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7d9cd93c-1d5e-449b-9ad7-f1e8d6b90509?P1=1736024775&P2=404&P3=2&P4=AZ3LKc6tc0XzBkTWjcimB1L9cq%2fKY%2bT7kN1Zhqcqj4n1zFkDP1qJeT5NfbVppBNsKtRVAo0yEaOFa3lLmfCURg%3d%3d | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4136 | SIHClient.exe | GET | 200 | 2.23.9.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.209.130:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
1176 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6232 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |