| download: | /a/7z2500.exe |
| Full analysis: | https://app.any.run/tasks/eec845d1-a18e-443a-af50-5a9dcb259ef6 |
| Verdict: | Malicious activity |
| Analysis date: | July 05, 2025, 22:21:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 33140969AE4757AC2A23815581FD3696 |
| SHA1: | BE42A1295F5BE0EF7CCE0C8A9ED74338925679EC |
| SHA256: | 3B7DCD86A17A2C4DEBAE0417DD98BB7467A69184357A23F6A3EE052356219720 |
| SSDEEP: | 49152:WPHtcOHyP4Rdkd2XMixIU8P8K1lGEfmvzxEq4SMHwzTVGHQB5JMczCJLdJeozEzI:WftcdWK2XMgqkKbt4aSMQzTc45JiL1Q8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
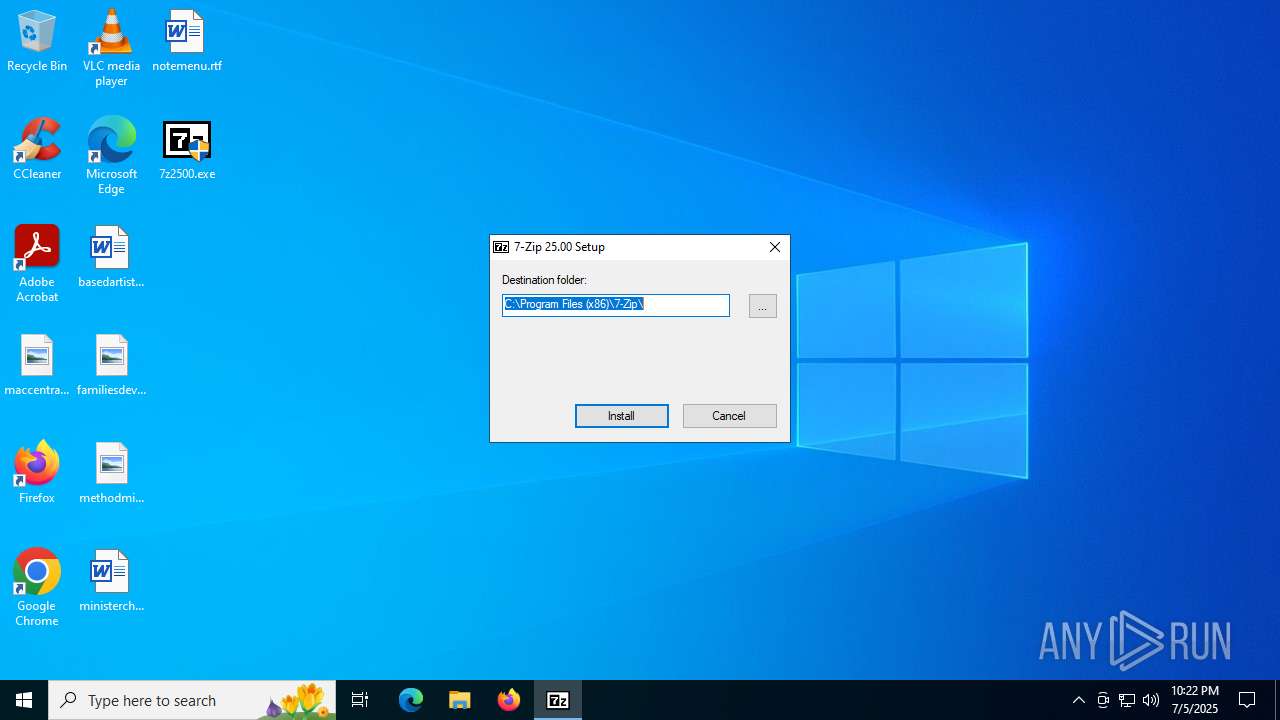
Drops 7-zip archiver for unpacking
- 7z2500.exe (PID: 2136)
Executable content was dropped or overwritten
- 7z2500.exe (PID: 2136)
Creates/Modifies COM task schedule object
- 7z2500.exe (PID: 2136)
Creates a software uninstall entry
- 7z2500.exe (PID: 2136)
INFO
Checks supported languages
- 7z2500.exe (PID: 2136)
- SearchApp.exe (PID: 5328)
- 7zFM.exe (PID: 4760)
The sample compiled with english language support
- 7z2500.exe (PID: 2136)
Creates files in the program directory
- 7z2500.exe (PID: 2136)
The sample compiled with russian language support
- 7z2500.exe (PID: 2136)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5328)
Reads the computer name
- 7zFM.exe (PID: 4760)
- 7z2500.exe (PID: 2136)
Process checks computer location settings
- SearchApp.exe (PID: 5328)
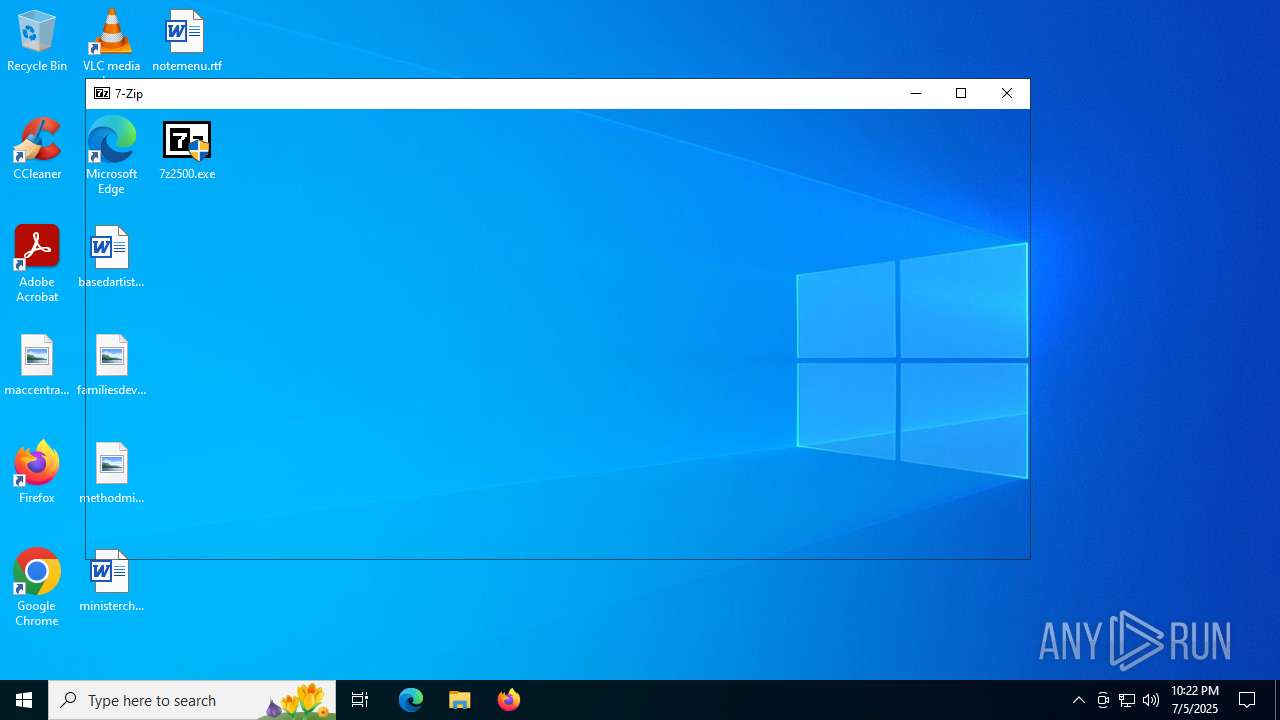
Manual execution by a user
- 7zFM.exe (PID: 4760)
Reads the software policy settings
- SearchApp.exe (PID: 5328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:07:05 12:00:00+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 24064 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x7144 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 25.0.0.0 |
| ProductVersionNumber: | 25.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Igor Pavlov |
| FileDescription: | 7-Zip Installer |
| FileVersion: | 25 |
| InternalName: | 7zipInstall |
| LegalCopyright: | Copyright (c) 1999-2025 Igor Pavlov |
| OriginalFileName: | 7zipInstall.exe |
| ProductName: | 7-Zip |
| ProductVersion: | 25 |
Total processes
142
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2136 | "C:\Users\admin\Desktop\7z2500.exe" | C:\Users\admin\Desktop\7z2500.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Installer Exit code: 0 Version: 25.00 Modules
| |||||||||||||||
| 3832 | "C:\Users\admin\Desktop\7z2500.exe" | C:\Users\admin\Desktop\7z2500.exe | — | explorer.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Installer Exit code: 3221226540 Version: 25.00 Modules
| |||||||||||||||
| 4760 | "C:\Program Files (x86)\7-Zip\7zFM.exe" | C:\Program Files (x86)\7-Zip\7zFM.exe | — | explorer.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip File Manager Version: 25.00 Modules
| |||||||||||||||
| 5328 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 005
Read events
3 938
Write events
63
Delete events
4
Modification events
| (PID) Process: | (2136) 7z2500.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path32 |
Value: C:\Program Files (x86)\7-Zip\ | |||
| (PID) Process: | (2136) 7z2500.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path |
Value: C:\Program Files (x86)\7-Zip\ | |||
| (PID) Process: | (2136) 7z2500.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\7-Zip |
| Operation: | write | Name: | Path32 |
Value: C:\Program Files (x86)\7-Zip\ | |||
| (PID) Process: | (2136) 7z2500.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\7-Zip |
| Operation: | write | Name: | Path |
Value: C:\Program Files (x86)\7-Zip\ | |||
| (PID) Process: | (2136) 7z2500.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (2136) 7z2500.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved |
| Operation: | write | Name: | {23170F69-40C1-278A-1000-000100020000} |
Value: 7-Zip Shell Extension | |||
| (PID) Process: | (2136) 7z2500.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\7zFM.exe |
| Operation: | write | Name: | Path |
Value: C:\Program Files (x86)\7-Zip\ | |||
| (PID) Process: | (2136) 7z2500.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\7-Zip |
| Operation: | write | Name: | DisplayName |
Value: 7-Zip 25.00 | |||
| (PID) Process: | (2136) 7z2500.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\7-Zip |
| Operation: | write | Name: | DisplayVersion |
Value: 25.00 | |||
| (PID) Process: | (2136) 7z2500.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\7-Zip |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\7-Zip\7zFM.exe | |||
Executable files
12
Suspicious files
13
Text files
106
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2136 | 7z2500.exe | C:\Program Files (x86)\7-Zip\descript.ion | text | |
MD5:EB7E322BDC62614E49DED60E0FB23845 | SHA256:1DA513F5A4E8018B9AE143884EB3EAF72454B606FD51F2401B7CFD9BE4DBBF4F | |||
| 2136 | 7z2500.exe | C:\Program Files (x86)\7-Zip\Lang\br.txt | text | |
MD5:07504A4EDAB058C2F67C8BCB95C605DD | SHA256:432BDB3EAA9953B084EE14EEE8FE0ABBC1B384CBDD984CCF35F0415D45AABBA8 | |||
| 2136 | 7z2500.exe | C:\Program Files (x86)\7-Zip\Lang\da.txt | text | |
MD5:C397E8AC4B966E1476ADBCE006BB49E4 | SHA256:5CCD481367F7D8C544DE6177187AFF53F1143AE451AE755CE9ED9B52C5F5D478 | |||
| 2136 | 7z2500.exe | C:\Program Files (x86)\7-Zip\Lang\ba.txt | text | |
MD5:387FF78CF5F524FC44640F3025746145 | SHA256:8A85C3FCB5F81157490971EE4F5E6B9E4F80BE69A802EBED04E6724CE859713F | |||
| 2136 | 7z2500.exe | C:\Program Files (x86)\7-Zip\Lang\bn.txt | text | |
MD5:771C8B73A374CB30DF4DF682D9C40EDF | SHA256:3F55B2EC5033C39C159593C6F5ECE667B92F32938B38FCAF58B4B2A98176C1FC | |||
| 2136 | 7z2500.exe | C:\Program Files (x86)\7-Zip\Lang\ca.txt | text | |
MD5:A77210BE2527533D1ECEB8F0EA49607A | SHA256:DA4DF6490C7BC8AFD804509F696F9AFA6F709B7A327044E2781FA6C95770B239 | |||
| 2136 | 7z2500.exe | C:\Program Files (x86)\7-Zip\Lang\az.txt | text | |
MD5:9CD3A23CA6F66F570607F63BE6AA0001 | SHA256:1DA941116E20E69F61A4A68481797E302C11FCF462CA7203A565588B26011615 | |||
| 2136 | 7z2500.exe | C:\Program Files (x86)\7-Zip\Lang\bg.txt | text | |
MD5:2D0C8197D84A083EF904F8F5608AFE46 | SHA256:62C6F410D011A109ABECB79CAA24D8AEB98B0046D329D611A4D07E66460EEF3F | |||
| 2136 | 7z2500.exe | C:\Program Files (x86)\7-Zip\Lang\cs.txt | text | |
MD5:1130ABF0E51093DC7EDD2C0C334BE5D8 | SHA256:DA788D30AA74B3F8B3D920E98C535E4544756E9E4E235ED0221654F3177D3D2A | |||
| 2136 | 7z2500.exe | C:\Program Files (x86)\7-Zip\Lang\cy.txt | text | |
MD5:6BDF25354B531370754506223B146600 | SHA256:470EAF5E67F5EAD5B8C3ECC1B5B21B29D16C73591EB0047B681660346E25B3FB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
26
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2612 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2220 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2220 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2664 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2612 | svchost.exe | 40.126.31.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2612 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |