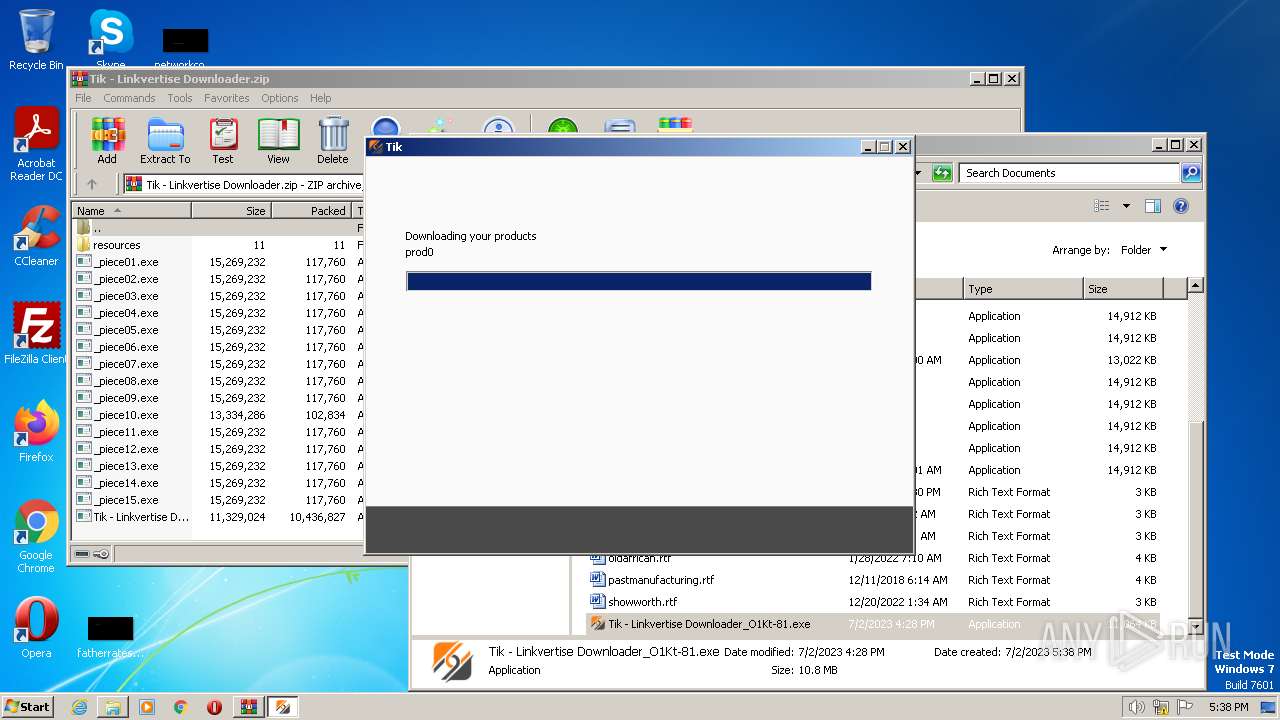
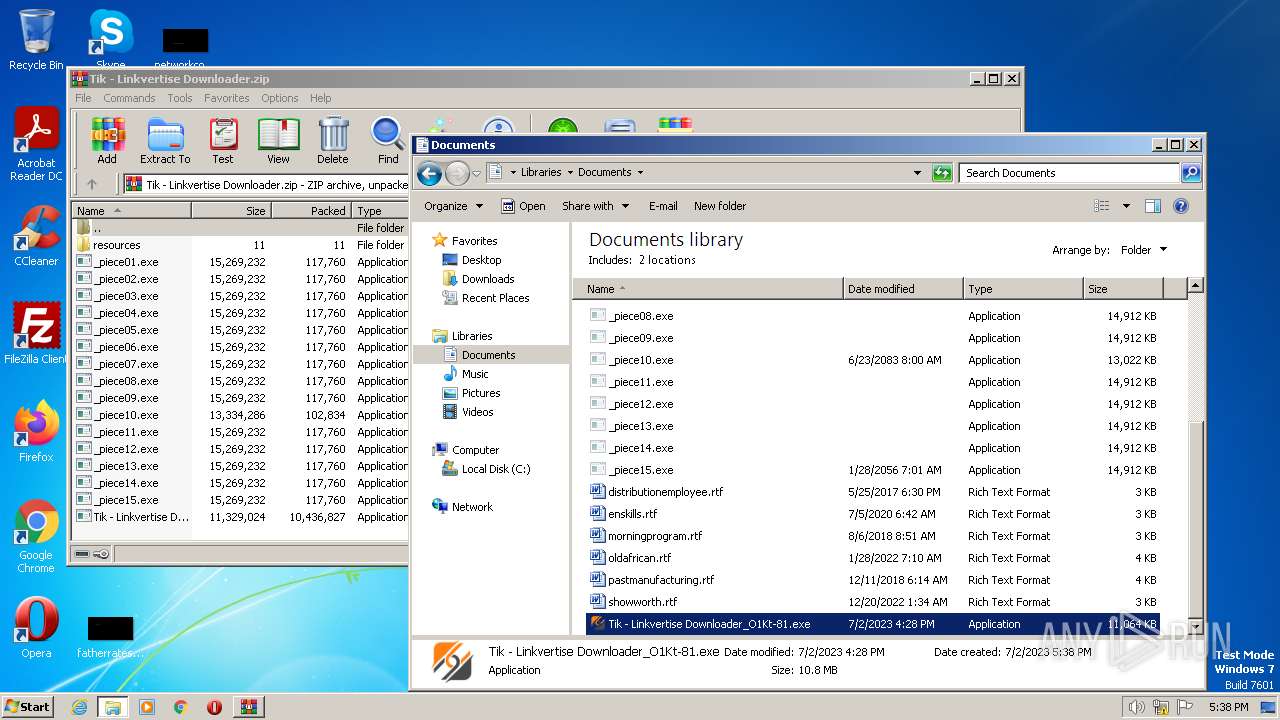
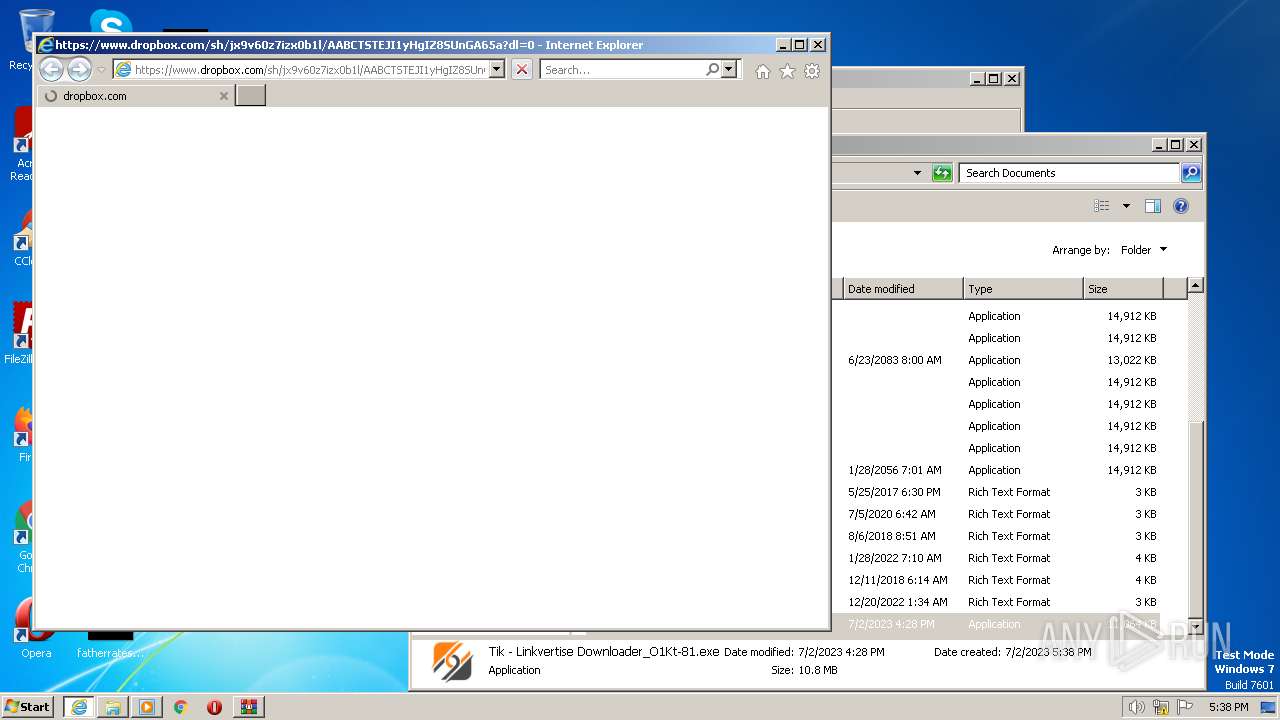
| File name: | Tik - Linkvertise Downloader.zip |
| Full analysis: | https://app.any.run/tasks/2dc5644d-f72a-41b7-bb84-7ecfbb428a31 |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2023, 16:37:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | CCBBF0DFF2E7E4330D70CD1016815444 |
| SHA1: | 7B119F65918FF29988B07D4216E2DFEC02B2B079 |
| SHA256: | 3B77EBCB8C8C21850E96002CC7E89DFB8E0B42BB3183224D3685AD05AB729CF4 |
| SSDEEP: | 196608:2iRu3GRp0YvcFLVBHs7wklhuSKpbpiTwmCAj2qJNWUySvgMbkWR3:lvvEBMMkaNpbUT7CAaQmSvPI+ |
MALICIOUS
Application was dropped or rewritten from another process
- Tik - Linkvertise Downloader_O1Kt-81.exe (PID: 2240)
- Tik - Linkvertise Downloader_O1Kt-81.exe (PID: 2892)
- saBSI.exe (PID: 676)
Loads dropped or rewritten executable
- Tik - Linkvertise Downloader_O1Kt-81.tmp (PID: 3796)
SUSPICIOUS
Executable content was dropped or overwritten
- Tik - Linkvertise Downloader_O1Kt-81.exe (PID: 2240)
- Tik - Linkvertise Downloader_O1Kt-81.exe (PID: 2892)
- Tik - Linkvertise Downloader_O1Kt-81.tmp (PID: 3796)
Reads the Windows owner or organization settings
- Tik - Linkvertise Downloader_O1Kt-81.tmp (PID: 3796)
Reads settings of System Certificates
- Tik - Linkvertise Downloader_O1Kt-81.tmp (PID: 3796)
- saBSI.exe (PID: 676)
Reads the Internet Settings
- Tik - Linkvertise Downloader_O1Kt-81.tmp (PID: 3796)
- saBSI.exe (PID: 676)
Adds/modifies Windows certificates
- Tik - Linkvertise Downloader_O1Kt-81.tmp (PID: 3796)
Checks Windows Trust Settings
- saBSI.exe (PID: 676)
Reads security settings of Internet Explorer
- saBSI.exe (PID: 676)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3416)
The process checks LSA protection
- explorer.exe (PID: 4040)
- Tik - Linkvertise Downloader_O1Kt-81.tmp (PID: 2500)
- Tik - Linkvertise Downloader_O1Kt-81.tmp (PID: 3796)
- saBSI.exe (PID: 676)
- wmpnscfg.exe (PID: 3236)
Manual execution by a user
- Tik - Linkvertise Downloader_O1Kt-81.exe (PID: 2240)
- explorer.exe (PID: 4040)
- WINWORD.EXE (PID: 2584)
- chrome.exe (PID: 1280)
- chrome.exe (PID: 3212)
- wmpnscfg.exe (PID: 3236)
Checks supported languages
- Tik - Linkvertise Downloader_O1Kt-81.exe (PID: 2240)
- Tik - Linkvertise Downloader_O1Kt-81.tmp (PID: 2500)
- Tik - Linkvertise Downloader_O1Kt-81.exe (PID: 2892)
- Tik - Linkvertise Downloader_O1Kt-81.tmp (PID: 3796)
- saBSI.exe (PID: 676)
- wmpnscfg.exe (PID: 3236)
Create files in a temporary directory
- Tik - Linkvertise Downloader_O1Kt-81.exe (PID: 2240)
- Tik - Linkvertise Downloader_O1Kt-81.exe (PID: 2892)
- Tik - Linkvertise Downloader_O1Kt-81.tmp (PID: 3796)
Reads the computer name
- Tik - Linkvertise Downloader_O1Kt-81.tmp (PID: 2500)
- Tik - Linkvertise Downloader_O1Kt-81.tmp (PID: 3796)
- saBSI.exe (PID: 676)
- wmpnscfg.exe (PID: 3236)
Application was dropped or rewritten from another process
- Tik - Linkvertise Downloader_O1Kt-81.tmp (PID: 2500)
- Tik - Linkvertise Downloader_O1Kt-81.tmp (PID: 3796)
Reads the machine GUID from the registry
- Tik - Linkvertise Downloader_O1Kt-81.tmp (PID: 3796)
- saBSI.exe (PID: 676)
- wmpnscfg.exe (PID: 3236)
Creates files in the program directory
- saBSI.exe (PID: 676)
Application launched itself
- iexplore.exe (PID: 2880)
- chrome.exe (PID: 1280)
- chrome.exe (PID: 3212)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | _piece01.exe |
|---|---|
| ZipUncompressedSize: | 15269232 |
| ZipCompressedSize: | 117760 |
| ZipCRC: | 0x1574d1fb |
| ZipModifyDate: | 2023:06:01 12:28:32 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
94
Monitored processes
52
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 548 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1124,14020415513119246817,3030494163327590621,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2276 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 656 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1028,12853057911912968401,13103877010976181382,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1568 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 676 | "C:\Users\admin\AppData\Local\Temp\is-8UV93.tmp\prod0_extract\saBSI.exe" /affid 91082 PaidDistribution=true | C:\Users\admin\AppData\Local\Temp\is-8UV93.tmp\prod0_extract\saBSI.exe | Tik - Linkvertise Downloader_O1Kt-81.tmp | ||||||||||||
User: admin Company: McAfee, LLC Integrity Level: HIGH Description: McAfee WebAdvisor(bootstrap installer) Exit code: 4294967295 Version: 4,1,1,663 Modules
| |||||||||||||||
| 676 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --field-trial-handle=1028,12853057911912968401,13103877010976181382,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1668 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 768 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1124,14020415513119246817,3030494163327590621,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3152 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1004 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1028,12853057911912968401,13103877010976181382,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1292 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1024 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1124,14020415513119246817,3030494163327590621,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3200 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1048 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1124,14020415513119246817,3030494163327590621,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2968 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1160 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,12853057911912968401,13103877010976181382,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2012 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1028,12853057911912968401,13103877010976181382,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1580 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
39 845
Read events
39 009
Write events
648
Delete events
188
Modification events
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3796) Tik - Linkvertise Downloader_O1Kt-81.tmp | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3796) Tik - Linkvertise Downloader_O1Kt-81.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
13
Suspicious files
335
Text files
248
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3416 | WinRAR.exe | C:\Users\admin\Documents\_piece01.exe | — | |
MD5:— | SHA256:— | |||
| 3416 | WinRAR.exe | C:\Users\admin\Documents\_piece02.exe | — | |
MD5:— | SHA256:— | |||
| 3416 | WinRAR.exe | C:\Users\admin\Documents\_piece03.exe | — | |
MD5:— | SHA256:— | |||
| 3416 | WinRAR.exe | C:\Users\admin\Documents\_piece04.exe | — | |
MD5:— | SHA256:— | |||
| 3416 | WinRAR.exe | C:\Users\admin\Documents\_piece05.exe | — | |
MD5:— | SHA256:— | |||
| 3416 | WinRAR.exe | C:\Users\admin\Documents\_piece06.exe | — | |
MD5:— | SHA256:— | |||
| 3416 | WinRAR.exe | C:\Users\admin\Documents\_piece07.exe | — | |
MD5:— | SHA256:— | |||
| 3416 | WinRAR.exe | C:\Users\admin\Documents\_piece08.exe | — | |
MD5:— | SHA256:— | |||
| 3416 | WinRAR.exe | C:\Users\admin\Documents\_piece09.exe | — | |
MD5:— | SHA256:— | |||
| 3416 | WinRAR.exe | C:\Users\admin\Documents\_piece10.exe | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
104
DNS requests
50
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
852 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/n3xmszuzmcp4pxq3qhmant63nm_9.45.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.45.0_all_ecp3yewcq3fuvht5wyi7t7s37y.crx3 | US | — | — | whitelisted |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/n3xmszuzmcp4pxq3qhmant63nm_9.45.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.45.0_all_ecp3yewcq3fuvht5wyi7t7s37y.crx3 | US | binary | 10.0 Kb | whitelisted |
2880 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/n3xmszuzmcp4pxq3qhmant63nm_9.45.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.45.0_all_ecp3yewcq3fuvht5wyi7t7s37y.crx3 | US | binary | 373 b | whitelisted |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac6cjvoq6bgr22ybbtz3ko5axura_20230624.543158698.14/obedbbhbpmojnkanicioggnmelmoomoc_20230624.543158698.14_all_ENUS_hfpw7vhyzu7pcmieo6c5fn22ke.crx3 | US | binary | 44.6 Kb | whitelisted |
852 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac6cjvoq6bgr22ybbtz3ko5axura_20230624.543158698.14/obedbbhbpmojnkanicioggnmelmoomoc_20230624.543158698.14_all_ENUS_hfpw7vhyzu7pcmieo6c5fn22ke.crx3 | US | binary | 373 b | whitelisted |
2880 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/n3xmszuzmcp4pxq3qhmant63nm_9.45.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.45.0_all_ecp3yewcq3fuvht5wyi7t7s37y.crx3 | US | binary | 10.0 Kb | whitelisted |
852 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac6cjvoq6bgr22ybbtz3ko5axura_20230624.543158698.14/obedbbhbpmojnkanicioggnmelmoomoc_20230624.543158698.14_all_ENUS_hfpw7vhyzu7pcmieo6c5fn22ke.crx3 | US | binary | 63.3 Kb | whitelisted |
3336 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEAJd%2FV9ZAIQwR79yTjL2qBc%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1852 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3796 | Tik - Linkvertise Downloader_O1Kt-81.tmp | 13.225.84.184:443 | d2vlpggfgyaxd1.cloudfront.net | AMAZON-02 | US | unknown |
676 | saBSI.exe | 104.208.16.0:443 | cu1pehnswad01.servicebus.windows.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
676 | saBSI.exe | 34.210.30.129:443 | apis.mosaic.analytics.awscommon.mcafee.com | AMAZON-02 | US | unknown |
3336 | iexplore.exe | 162.125.66.18:443 | www.dropbox.com | DROPBOX | DE | suspicious |
2880 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
2880 | iexplore.exe | 104.126.37.139:443 | www.bing.com | Akamai International B.V. | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
d2vlpggfgyaxd1.cloudfront.net |
| unknown |
cu1pehnswad01.servicebus.windows.net |
| whitelisted |
apis.mosaic.analytics.awscommon.mcafee.com |
| unknown |
www.dropbox.com |
| shared |
sadownload.mcafee.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
cfl.dropboxstatic.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3336 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY Dropbox.com Offsite File Backup in Use |
1076 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
2076 | chrome.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
1004 | chrome.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request On Non-Standard High Port) |
1004 | chrome.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request On Non-Standard High Port) |
1004 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY Dropbox.com Offsite File Backup in Use |
Process | Message |
|---|---|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-8UV93.tmp\prod0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-8UV93.tmp\prod0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-8UV93.tmp\prod0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-8UV93.tmp\prod0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\is-8UV93.tmp\prod0_extract\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\is-8UV93.tmp\prod0_extract\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|