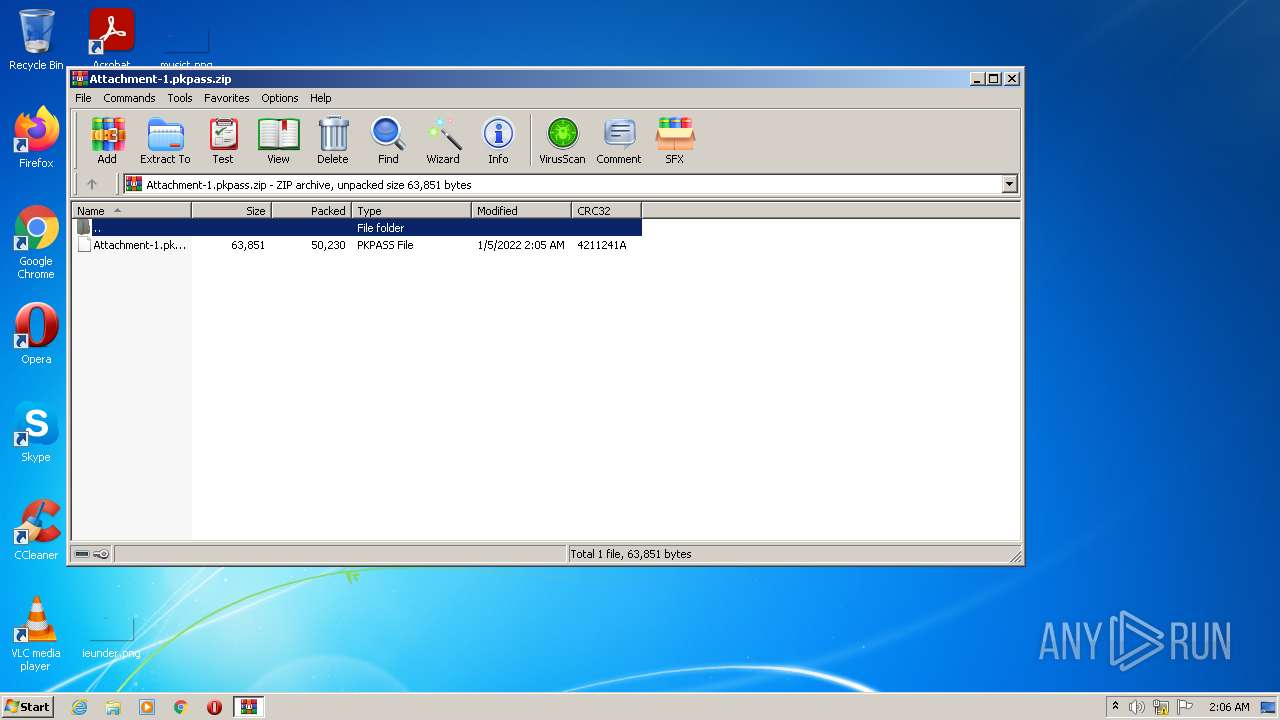
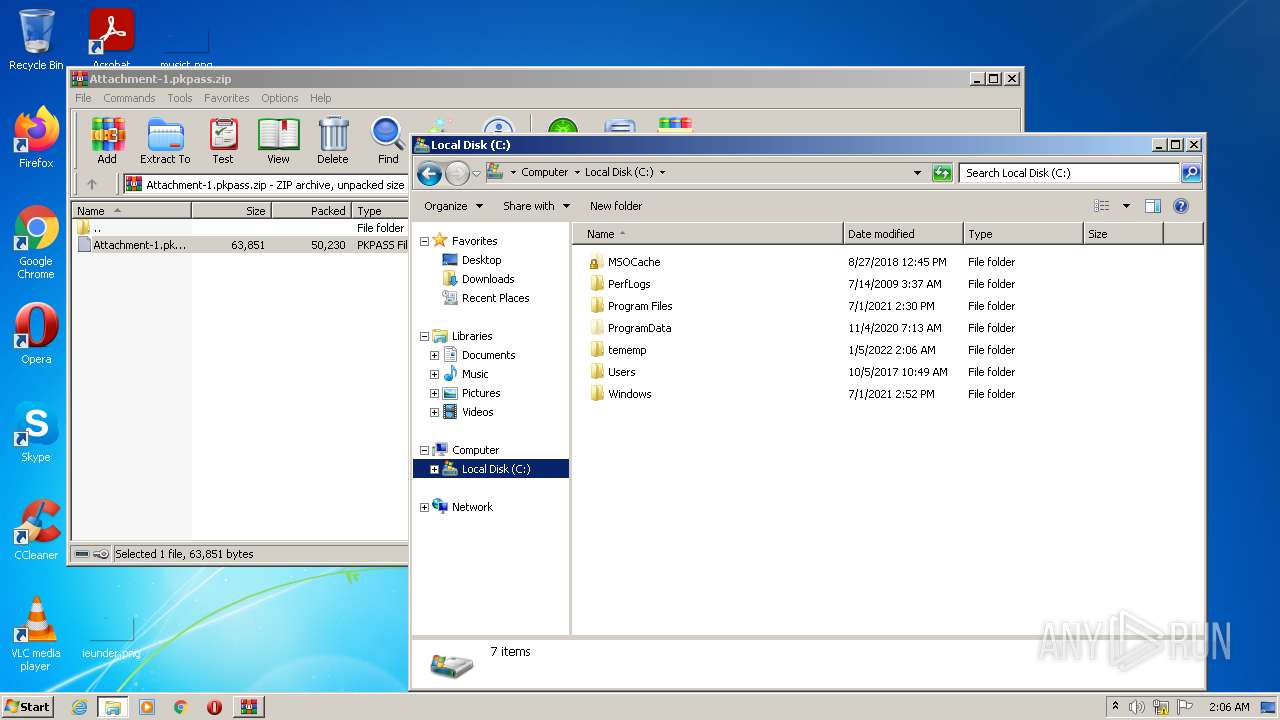
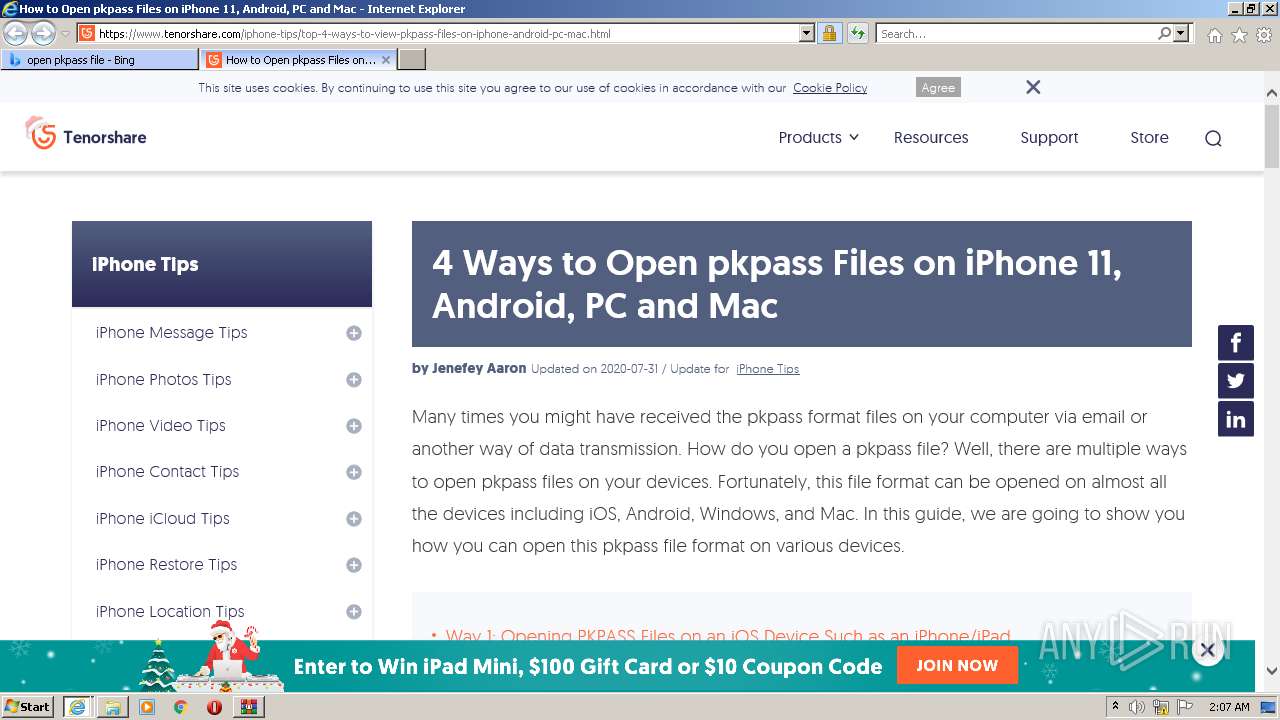
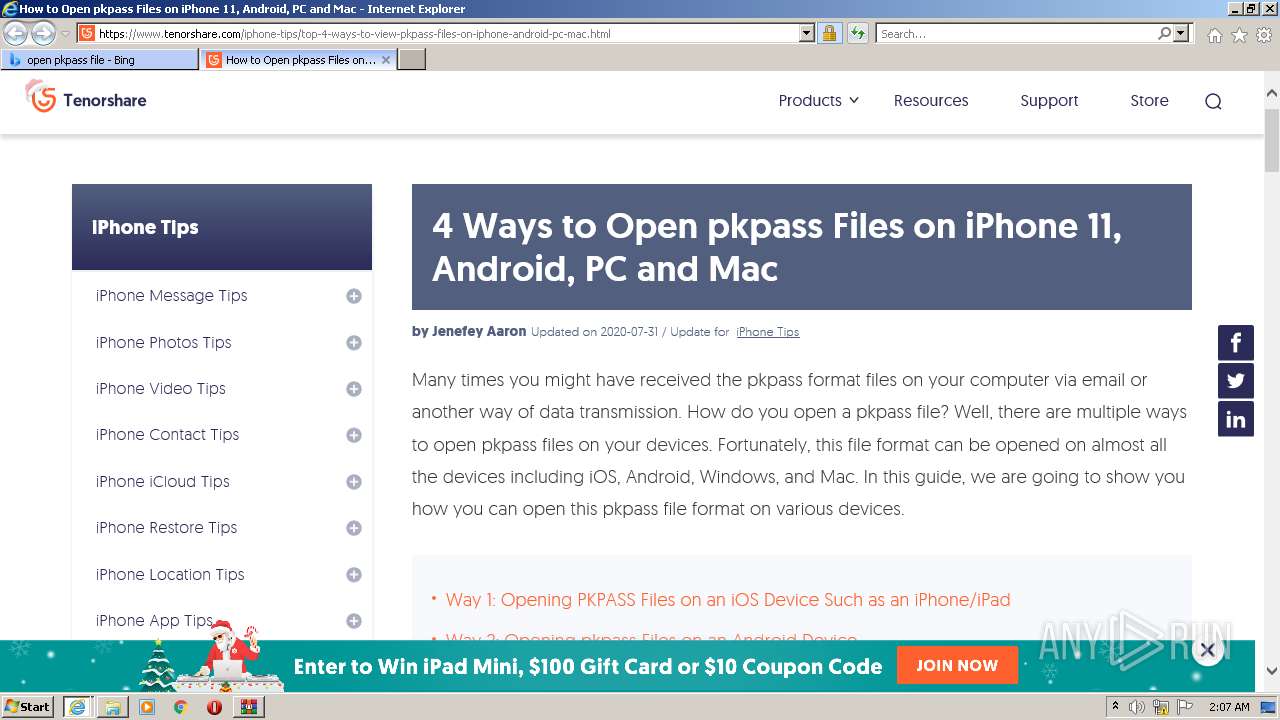
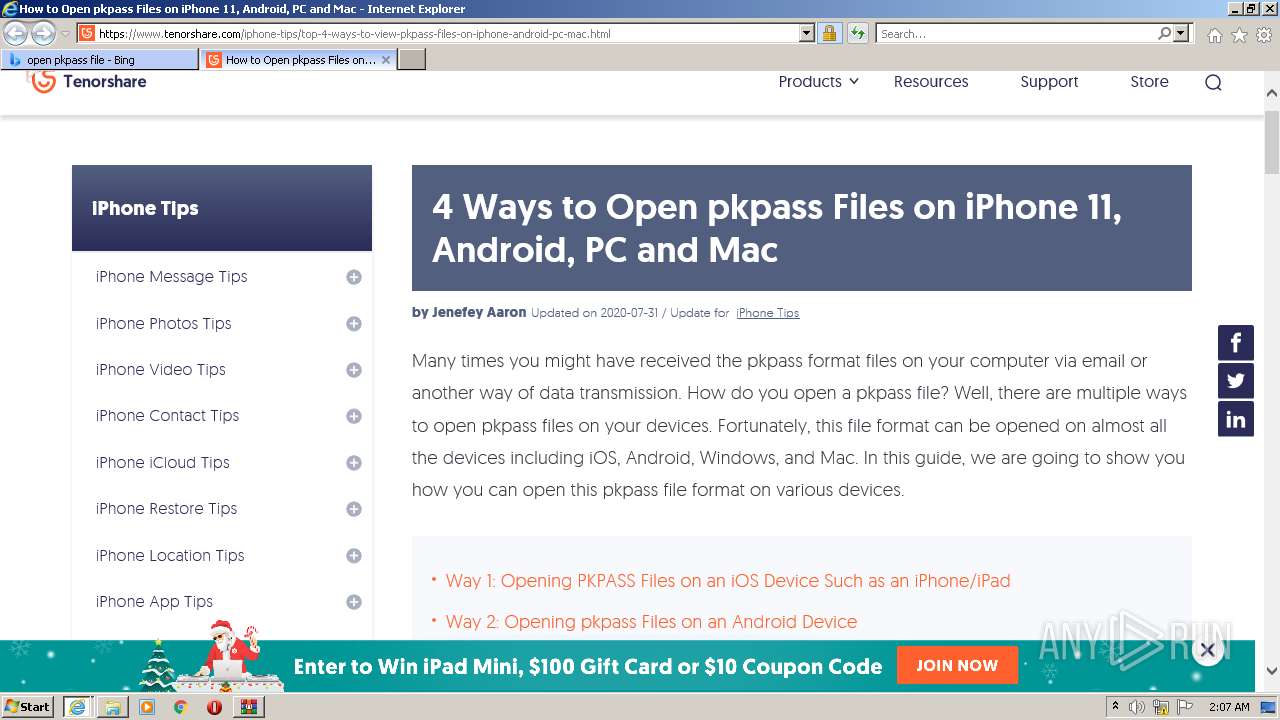
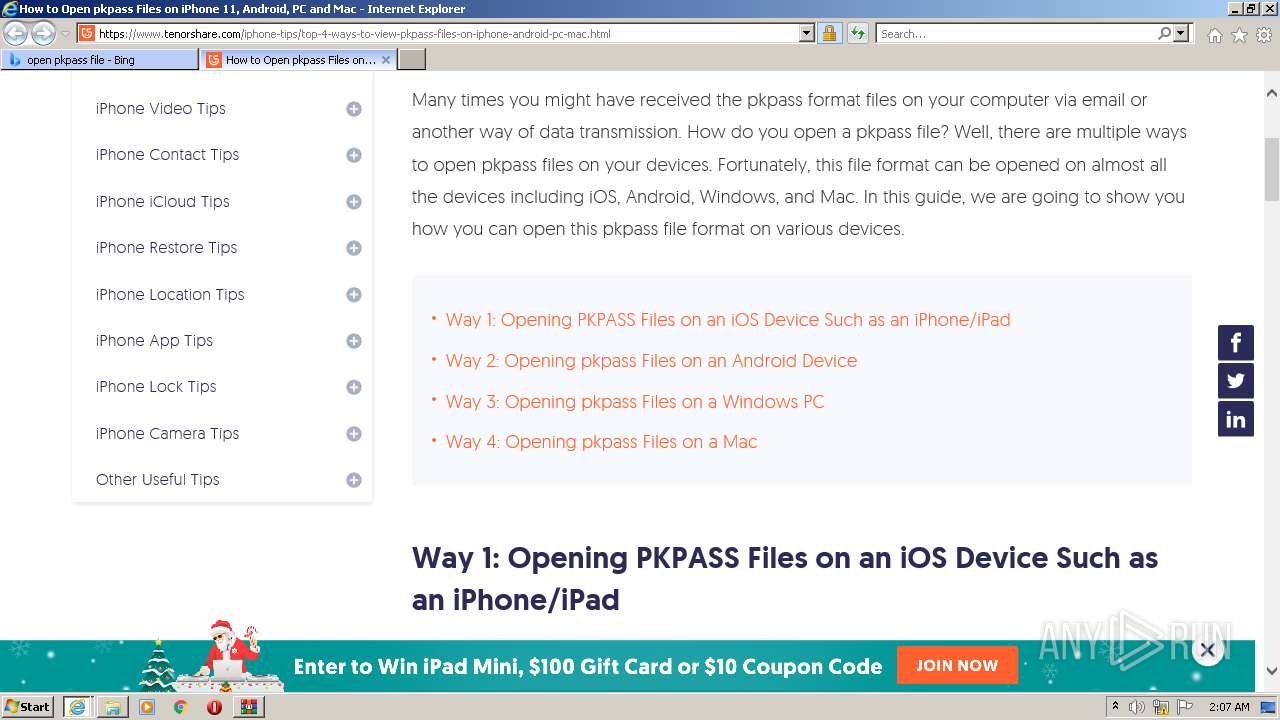
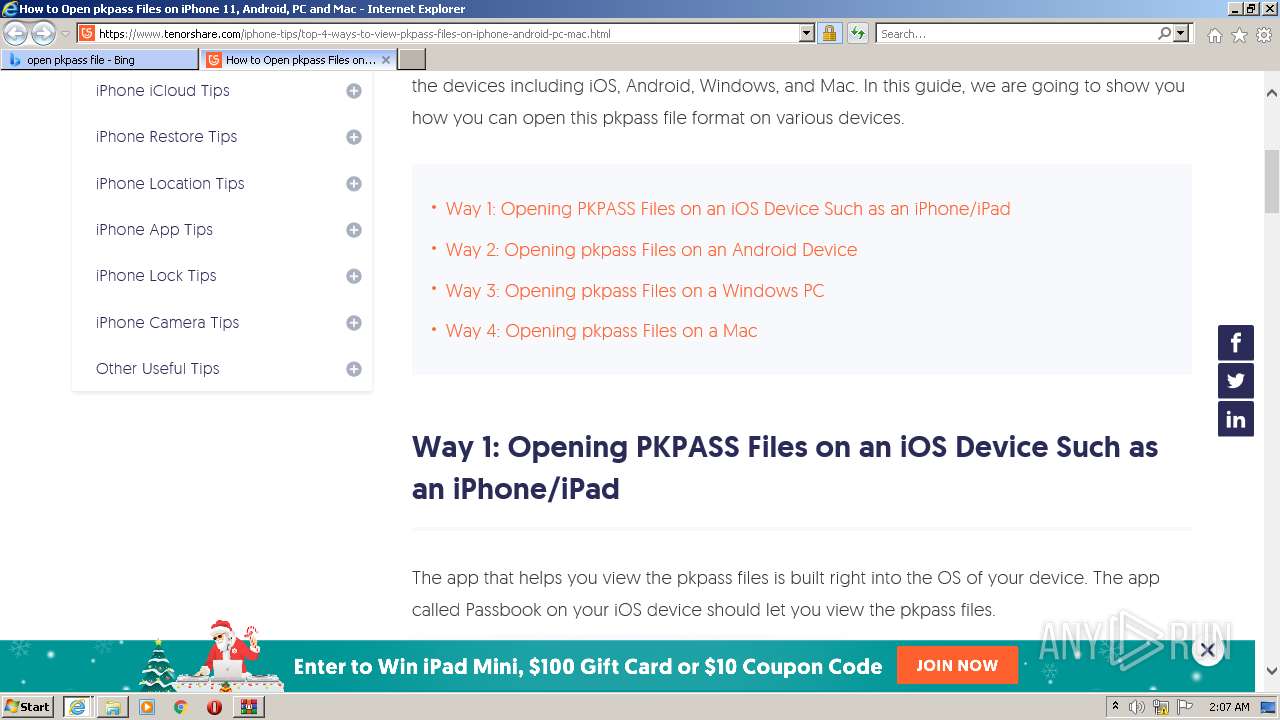
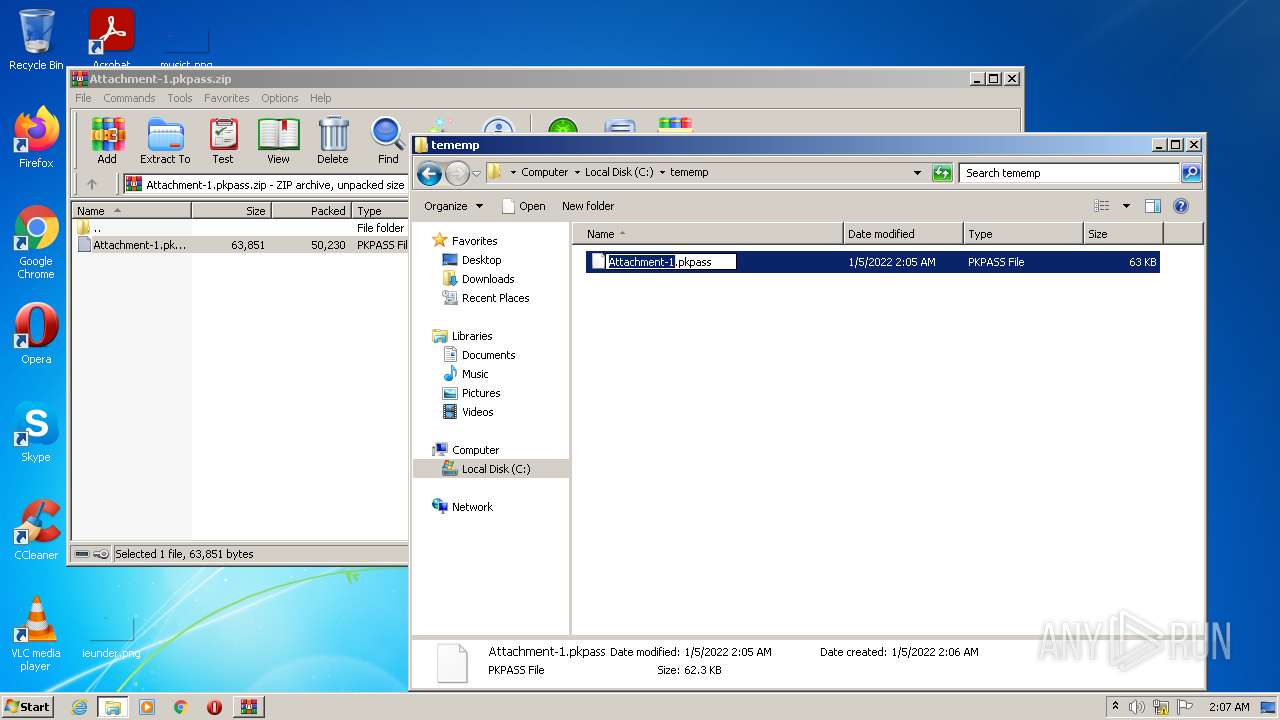
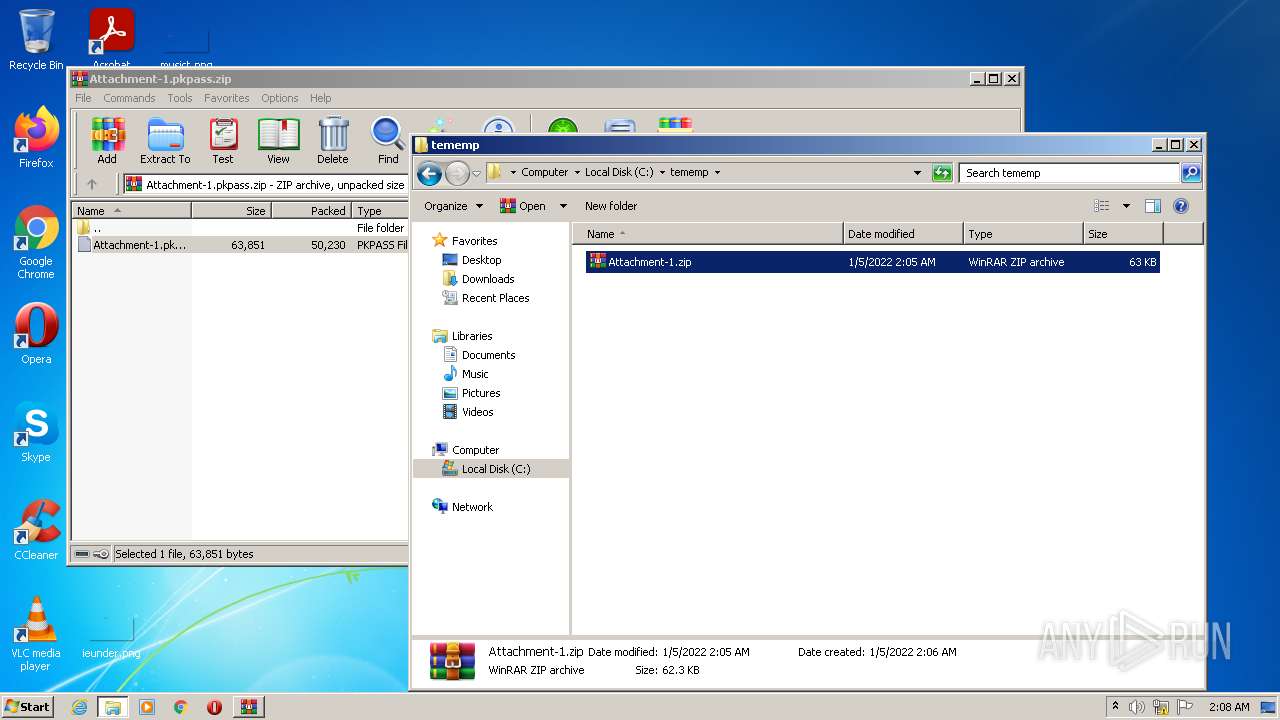
| File name: | Attachment-1.pkpass.zip |
| Full analysis: | https://app.any.run/tasks/7c397901-09e5-411f-b40a-790d90c218a6 |
| Verdict: | Malicious activity |
| Analysis date: | January 05, 2022, 02:06:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | C29DBF33232C633DD804D81BE3EA9EF1 |
| SHA1: | 1E88F3B48251E93A60FFACD7D46B405C061C9709 |
| SHA256: | 3B7208D8730B86FDA45C0428FA16124F57AD8EFB89F43563A15918FD7A5F5119 |
| SSDEEP: | 768:Mqhy2DNNhGYTEVb9DiCngtF2UBIjAor7xqopkMs1vCKdx62clt2yKg6FLk3gQaKu:6yERV5D3nkFQNwi+1v3W2cX2yumCjb |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 1396)
- WinRAR.exe (PID: 624)
Reads the computer name
- WinRAR.exe (PID: 1396)
- WinRAR.exe (PID: 624)
Starts Internet Explorer
- rundll32.exe (PID: 3320)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 928)
- iexplore.exe (PID: 3160)
INFO
Checks supported languages
- explorer.exe (PID: 1344)
- rundll32.exe (PID: 3320)
- iexplore.exe (PID: 3352)
- iexplore.exe (PID: 928)
- iexplore.exe (PID: 3160)
Reads the computer name
- explorer.exe (PID: 1344)
- rundll32.exe (PID: 3320)
- iexplore.exe (PID: 3352)
- iexplore.exe (PID: 928)
- iexplore.exe (PID: 3160)
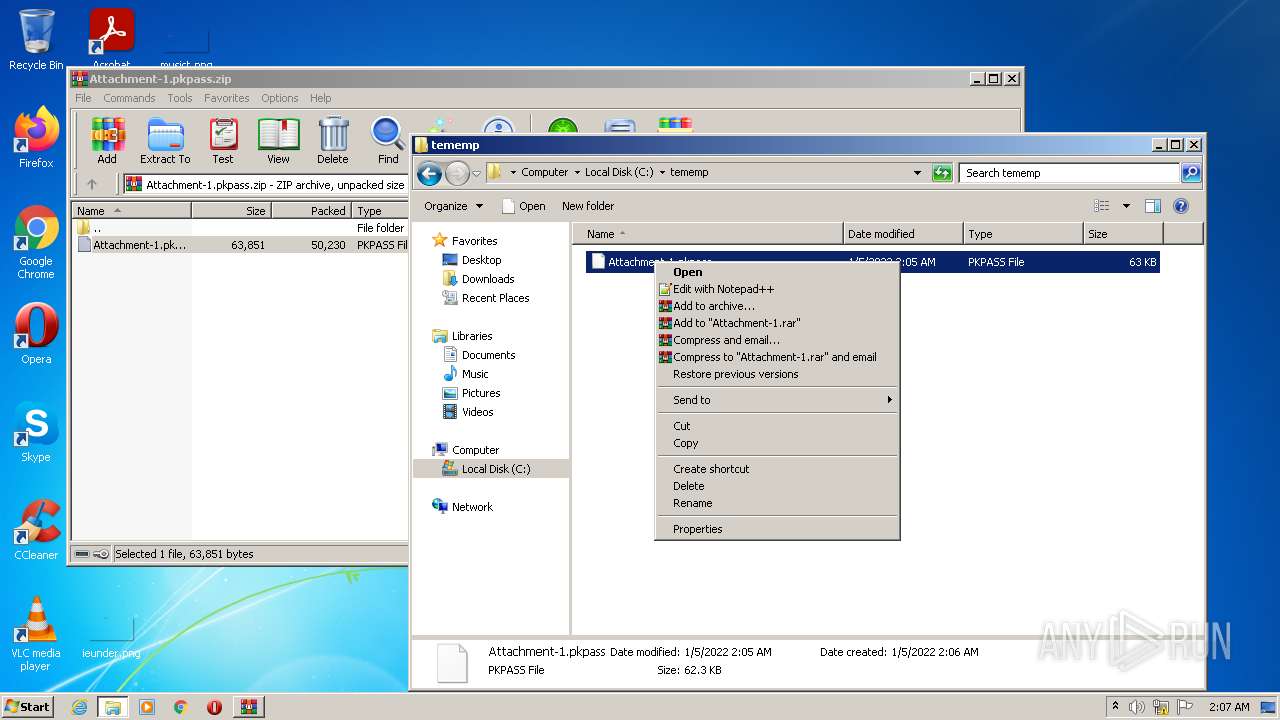
Manual execution by user
- rundll32.exe (PID: 3320)
- explorer.exe (PID: 1344)
- WinRAR.exe (PID: 624)
Changes internet zones settings
- iexplore.exe (PID: 3352)
Application launched itself
- iexplore.exe (PID: 3352)
Checks Windows Trust Settings
- iexplore.exe (PID: 928)
- iexplore.exe (PID: 3352)
- iexplore.exe (PID: 3160)
Reads settings of System Certificates
- iexplore.exe (PID: 928)
- iexplore.exe (PID: 3352)
- iexplore.exe (PID: 3160)
Creates files in the user directory
- iexplore.exe (PID: 928)
- iexplore.exe (PID: 3352)
- iexplore.exe (PID: 3160)
Reads internet explorer settings
- iexplore.exe (PID: 928)
- iexplore.exe (PID: 3160)
Reads the date of Windows installation
- iexplore.exe (PID: 3352)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
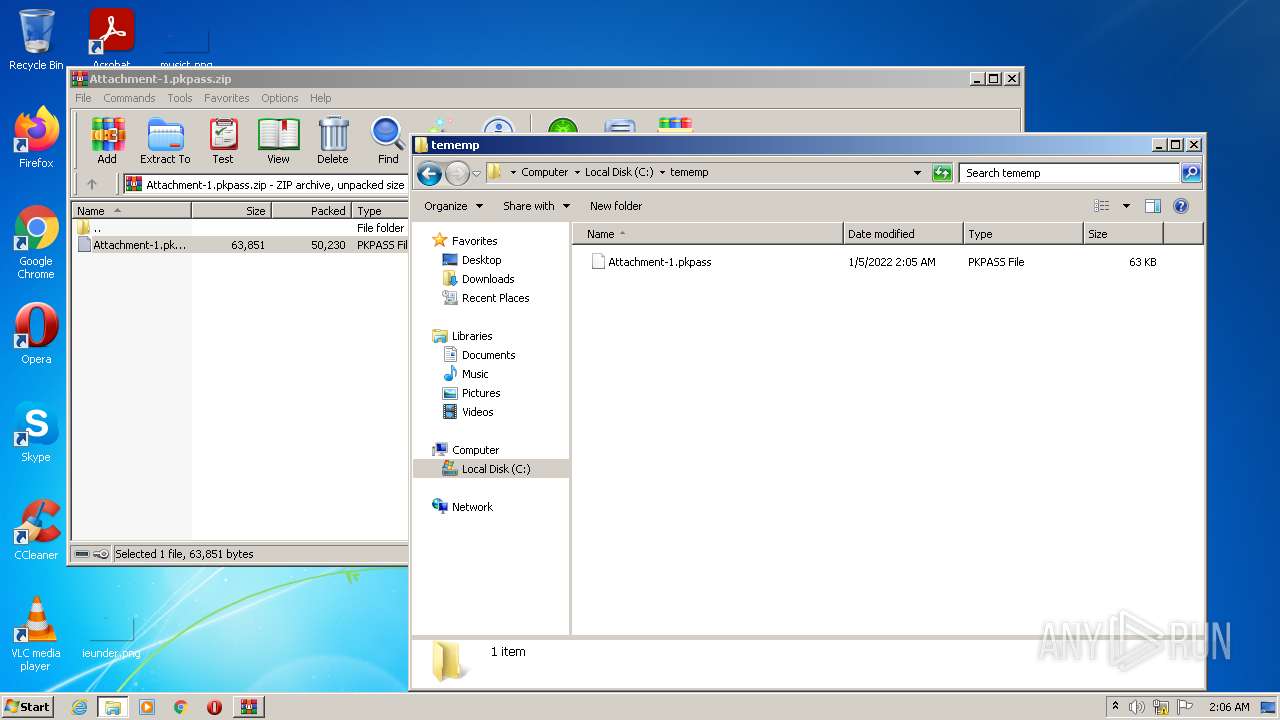
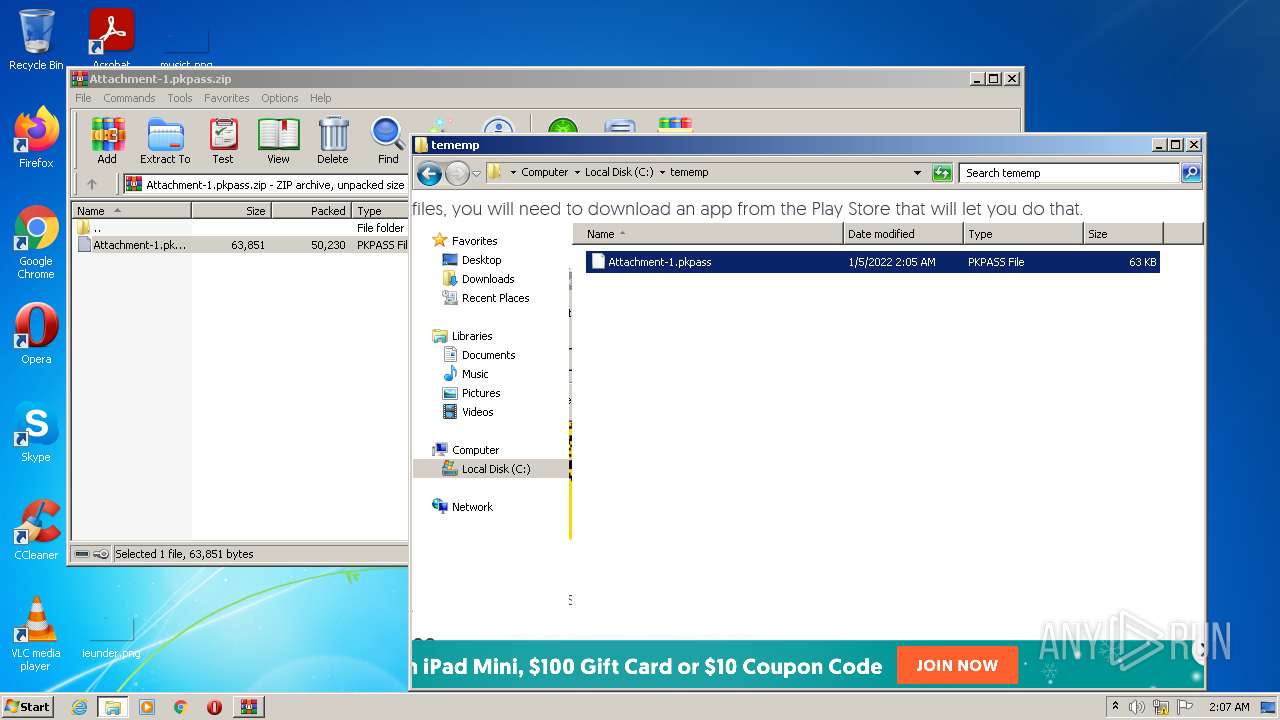
| ZipFileName: | Attachment-1.pkpass |
|---|---|
| ZipUncompressedSize: | 63851 |
| ZipCompressedSize: | 50230 |
| ZipCRC: | 0x4211241a |
| ZipModifyDate: | 2022:01:05 02:05:12 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
44
Monitored processes
7
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
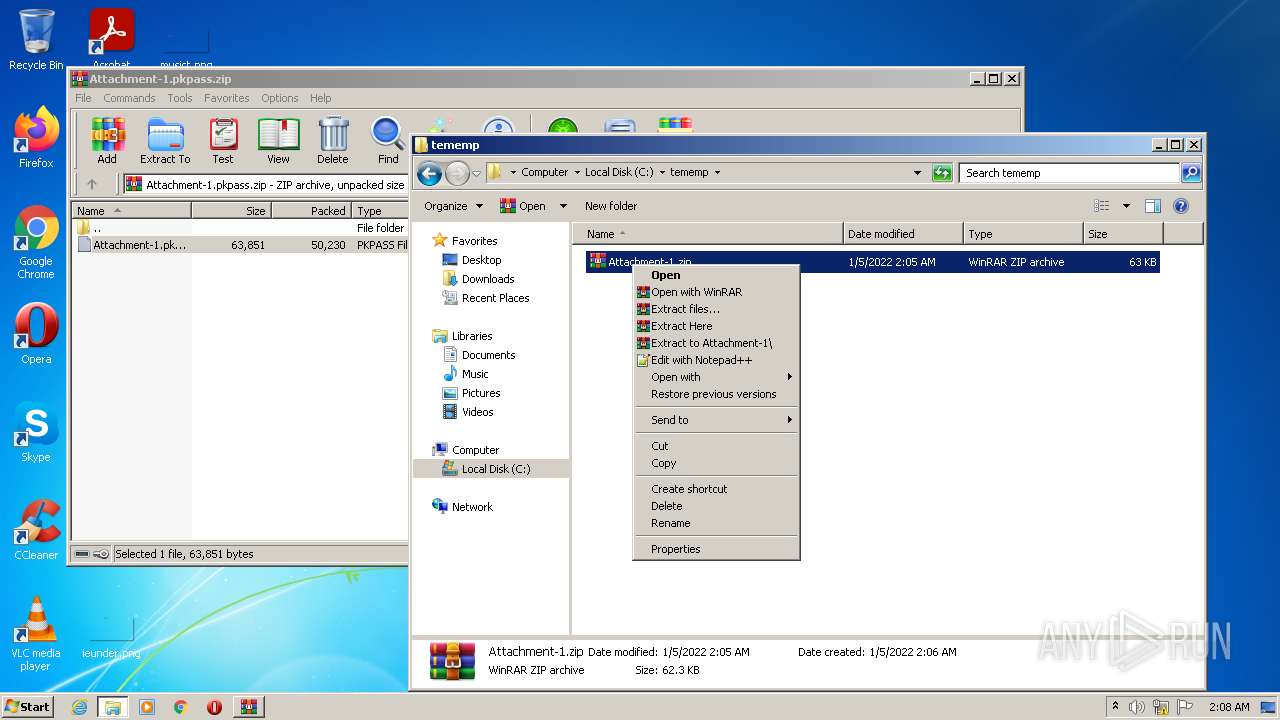
| 624 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\tememp\Attachment-1.zip" C:\tememp\ | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 928 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3352 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1344 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1396 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Attachment-1.pkpass.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3160 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3352 CREDAT:1185034 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
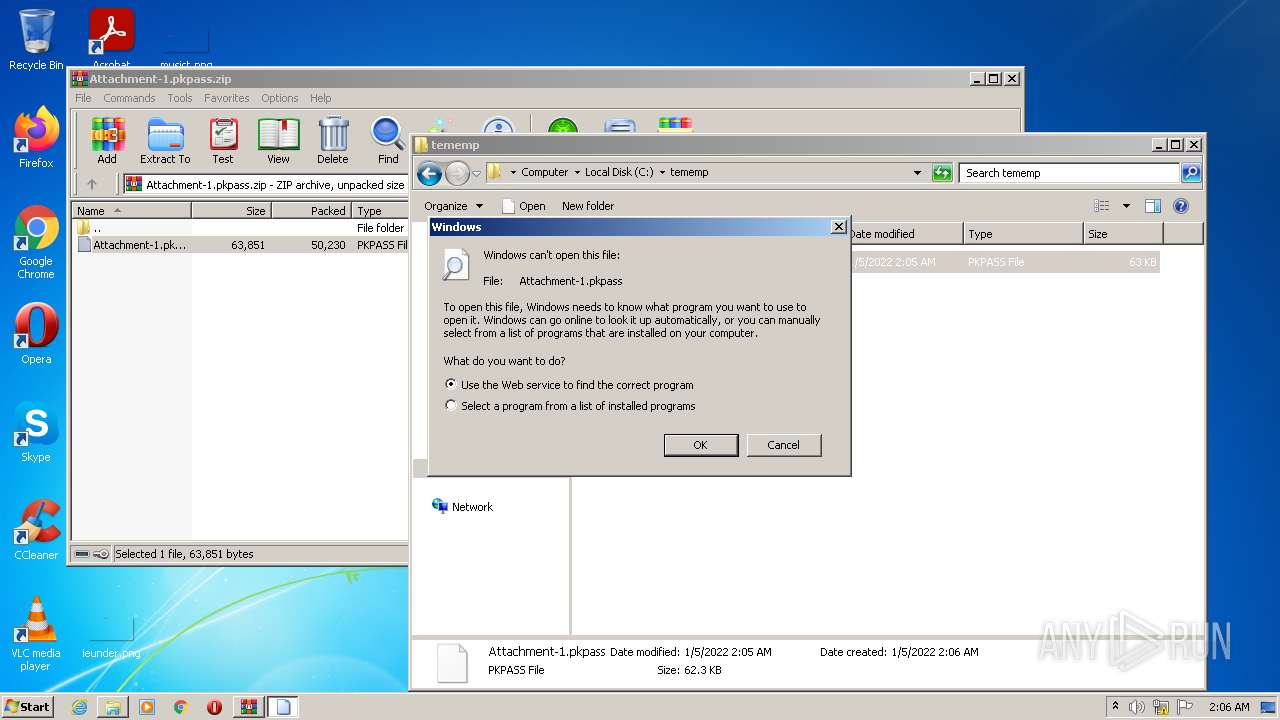
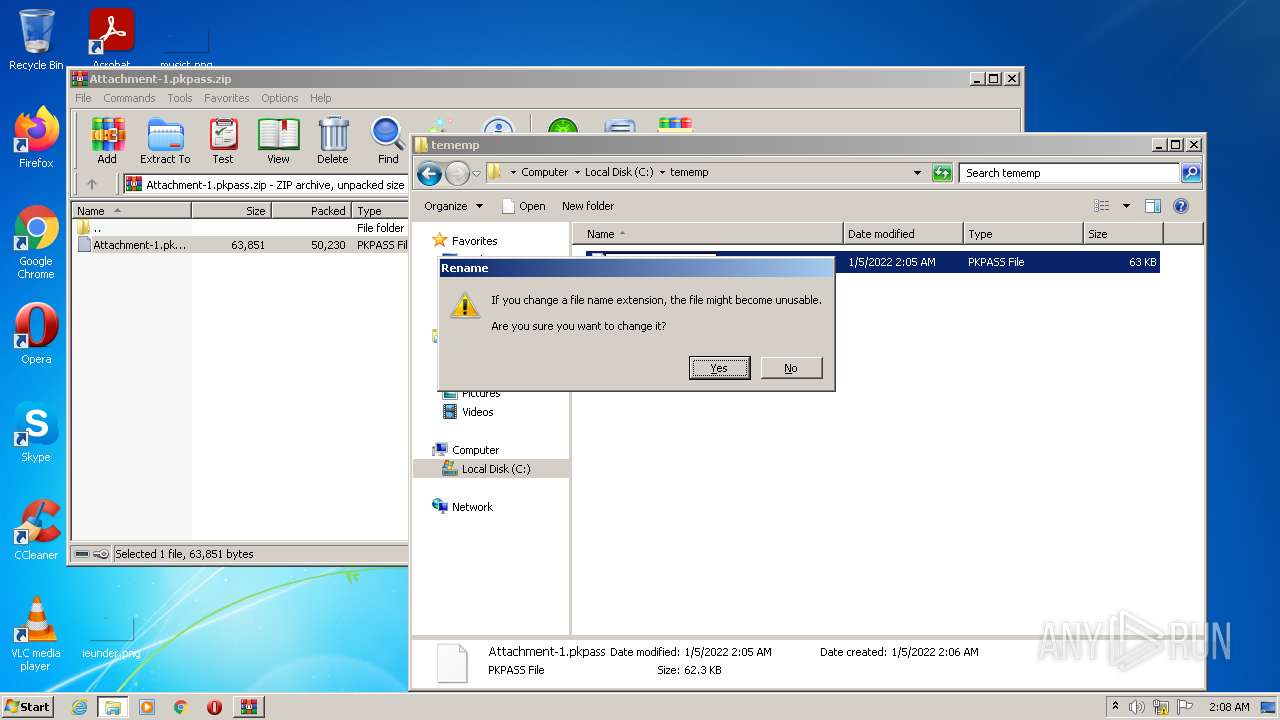
| 3320 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\tememp\Attachment-1.pkpass | C:\Windows\system32\rundll32.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
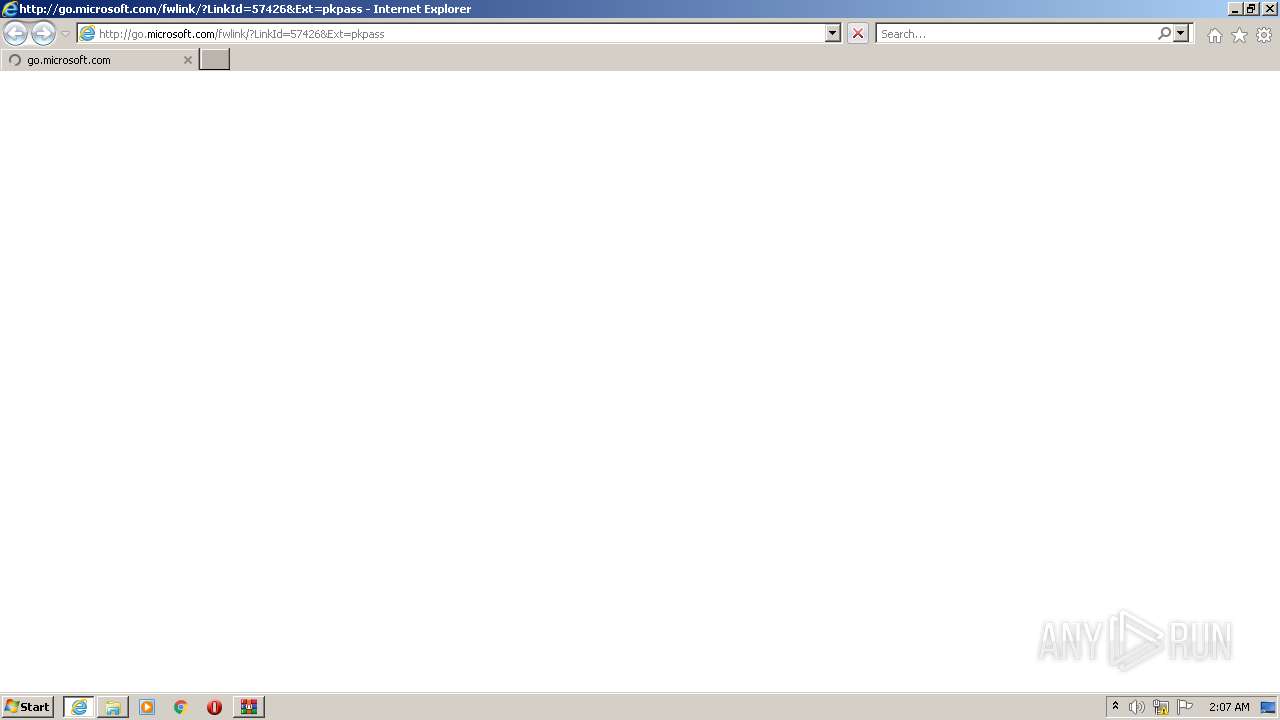
| 3352 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?LinkId=57426&Ext=pkpass | C:\Program Files\Internet Explorer\iexplore.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
26 054
Read events
25 876
Write events
177
Delete events
1
Modification events
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Attachment-1.pkpass.zip | |||
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1396) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
35
Text files
154
Unknown types
34
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 928 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\LZFRIBPH.txt | text | |
MD5:— | SHA256:— | |||
| 928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 928 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\0JO7T01U.txt | text | |
MD5:— | SHA256:— | |||
| 928 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\MX5BUGLF.txt | text | |
MD5:— | SHA256:— | |||
| 928 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\SRSKN0OD.txt | text | |
MD5:— | SHA256:— | |||
| 1396 | WinRAR.exe | C:\tememp\Attachment-1.pkpass | compressed | |
MD5:— | SHA256:— | |||
| 928 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\T1Q08T7U.txt | text | |
MD5:— | SHA256:— | |||
| 928 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\Q35CYKZX.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
77
DNS requests
35
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
928 | iexplore.exe | GET | 301 | 2.16.186.27:80 | http://shell.windows.com/fileassoc/fileassoc.asp?Ext=pkpass | unknown | — | — | whitelisted |
3160 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA9bw6F2y3ieICDHiTyBZ7Q%3D | US | der | 1.47 Kb | whitelisted |
3160 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEAPb0zJbprzPUZGUCIYHrnk%3D | US | der | 280 b | whitelisted |
3160 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDqD%2FXHbAMzNwoAAAABJgAZ | US | der | 472 b | whitelisted |
3160 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCZ2fjZwSXF%2BwoAAAABJfz9 | US | der | 472 b | whitelisted |
928 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3160 | iexplore.exe | GET | 200 | 143.204.101.74:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
3160 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | US | der | 471 b | whitelisted |
3160 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDDxQmkH%2FlDagoAAAABJgJE | US | der | 472 b | whitelisted |
3160 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
928 | iexplore.exe | 104.111.242.51:443 | go.microsoft.com | Akamai International B.V. | NL | unknown |
928 | iexplore.exe | 8.248.115.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
928 | iexplore.exe | 13.107.4.50:80 | ctldl.windowsupdate.com | Microsoft Corporation | US | whitelisted |
928 | iexplore.exe | 2.16.186.27:80 | shell.windows.com | Akamai International B.V. | — | whitelisted |
928 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3352 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3160 | iexplore.exe | 104.18.25.249:443 | www.tenorshare.com | Cloudflare Inc | US | suspicious |
928 | iexplore.exe | 20.190.151.6:443 | login.live.com | Microsoft Corporation | US | suspicious |
3160 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3160 | iexplore.exe | 104.18.24.249:443 | www.tenorshare.com | Cloudflare Inc | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
shell.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.microsoftonline.com |
| whitelisted |
login.live.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.tenorshare.com |
| whitelisted |
images.tenorshare.com |
| whitelisted |