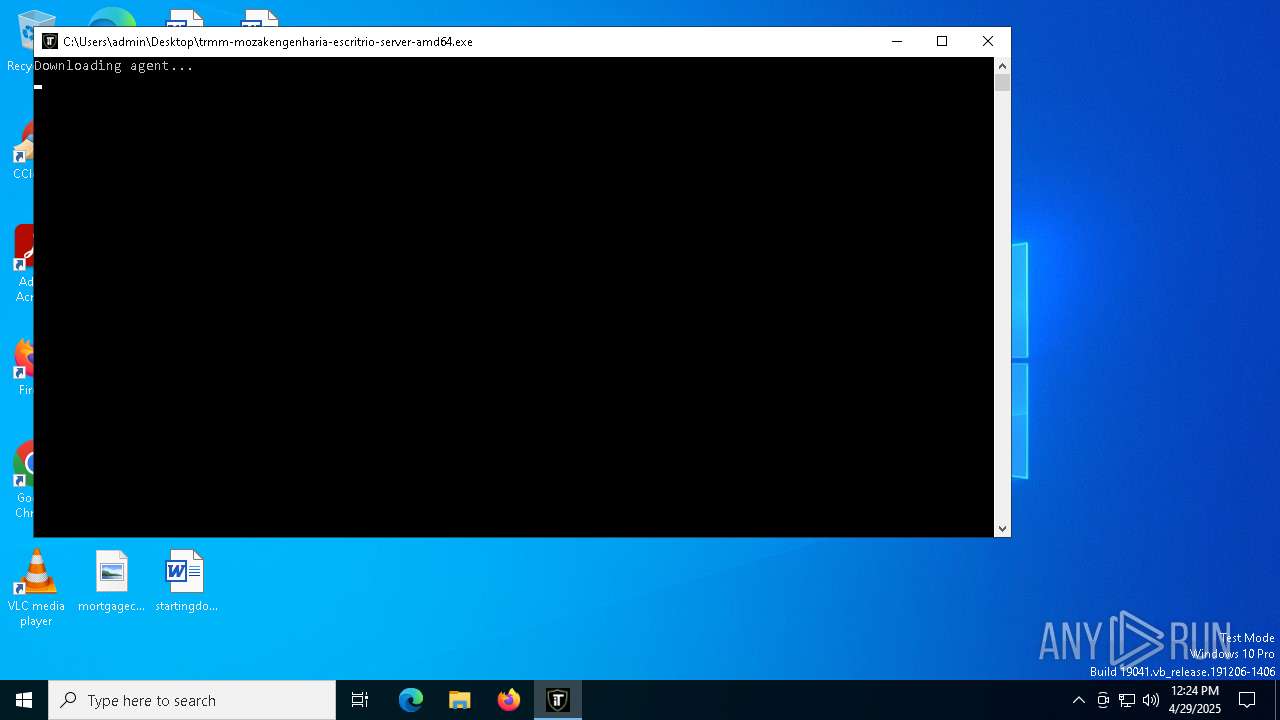
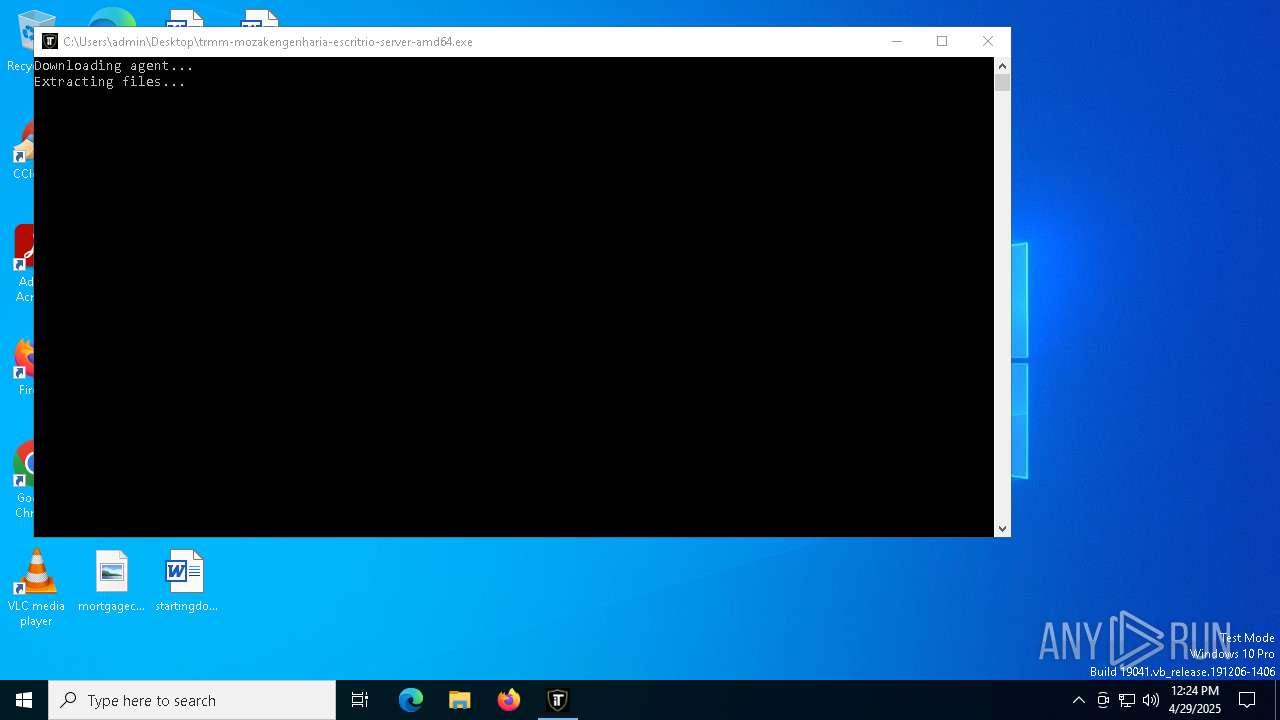
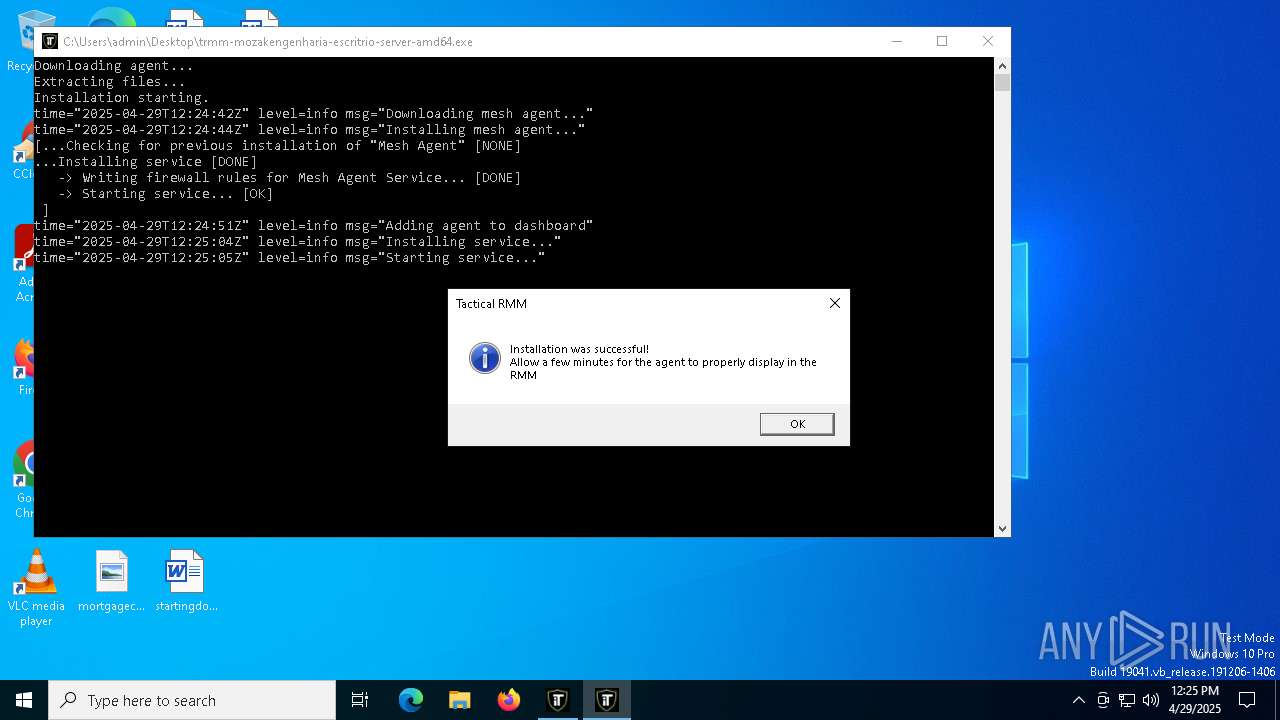
| File name: | trmm-mozakengenharia-escritrio-server-amd64.exe |
| Full analysis: | https://app.any.run/tasks/108a91c5-2b81-4077-a744-622305969033 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 12:24:16 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64 (stripped to external PDB), for MS Windows, 7 sections |
| MD5: | 89F2A0C991F8AC7DC814EAC3F6B1B01F |
| SHA1: | 7BDD8CE20A08FBE6FBEFB5C9A0B6FA0E139D0659 |
| SHA256: | 3B64B8C0D56202045B74C22C8BA22AE2DA6286CAFCA2A56B07D0D35C3E779FB3 |
| SSDEEP: | 98304:3DOaPjDwAxfaOhcU3s9e4ZSCDk1YYQau6qH:x6 |
MALICIOUS
Starts NET.EXE for service management
- cmd.exe (PID: 1180)
- net.exe (PID: 1324)
- net.exe (PID: 1244)
- net.exe (PID: 2236)
- cmd.exe (PID: 1452)
- cmd.exe (PID: 7148)
- net.exe (PID: 7852)
- cmd.exe (PID: 7796)
Executing a file with an untrusted certificate
- meshagent.exe (PID: 8024)
- MeshAgent.exe (PID: 8080)
- MeshAgent.exe (PID: 7480)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 5640)
SUSPICIOUS
Executable content was dropped or overwritten
- trmm-mozakengenharia-escritrio-server-amd64.exe (PID: 5200)
- tacticalagent-v2.9.0-windows-amd64.exe (PID: 2852)
- tacticalagent-v2.9.0-windows-amd64.tmp (PID: 5772)
- meshagent.exe (PID: 8024)
- tacticalrmm.exe (PID: 7948)
- tacticalrmm.exe (PID: 4164)
Reads the Windows owner or organization settings
- tacticalagent-v2.9.0-windows-amd64.tmp (PID: 5772)
Starts CMD.EXE for commands execution
- tacticalagent-v2.9.0-windows-amd64.tmp (PID: 5772)
- MeshAgent.exe (PID: 8080)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1180)
- cmd.exe (PID: 1452)
Windows service management via SC.EXE
- sc.exe (PID: 7480)
- sc.exe (PID: 7564)
Creates or modifies Windows services
- tacticalrmm.exe (PID: 7732)
- tacticalrmm.exe (PID: 7948)
- meshagent.exe (PID: 8024)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7204)
Creates a software uninstall entry
- meshagent.exe (PID: 8024)
- MeshAgent.exe (PID: 8080)
Executes as Windows Service
- MeshAgent.exe (PID: 8080)
- tacticalrmm.exe (PID: 4164)
Uses WMIC.EXE to obtain operating system information
- MeshAgent.exe (PID: 8080)
Uses WMIC.EXE to obtain computer system information
- MeshAgent.exe (PID: 8080)
Uses WMIC.EXE to obtain system information
- MeshAgent.exe (PID: 8080)
The process bypasses the loading of PowerShell profile settings
- MeshAgent.exe (PID: 8080)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 5640)
Starts POWERSHELL.EXE for commands execution
- MeshAgent.exe (PID: 8080)
The process hides Powershell's copyright startup banner
- MeshAgent.exe (PID: 8080)
Searches for installed software
- tacticalrmm.exe (PID: 7948)
Reads security settings of Internet Explorer
- MeshAgent.exe (PID: 8080)
Process drops python dynamic module
- tacticalrmm.exe (PID: 4164)
Application launched itself
- tacticalrmm.exe (PID: 4164)
Process drops legitimate windows executable
- tacticalrmm.exe (PID: 4164)
INFO
Reads the software policy settings
- trmm-mozakengenharia-escritrio-server-amd64.exe (PID: 5200)
- tacticalrmm.exe (PID: 7948)
- tacticalrmm.exe (PID: 4164)
The sample compiled with english language support
- trmm-mozakengenharia-escritrio-server-amd64.exe (PID: 5200)
- tacticalrmm.exe (PID: 7948)
- meshagent.exe (PID: 8024)
- tacticalrmm.exe (PID: 4164)
Creates files in the program directory
- trmm-mozakengenharia-escritrio-server-amd64.exe (PID: 5200)
- tacticalagent-v2.9.0-windows-amd64.tmp (PID: 5772)
- tacticalrmm.exe (PID: 7732)
- meshagent.exe (PID: 8024)
- tacticalrmm.exe (PID: 7948)
- MeshAgent.exe (PID: 8080)
Checks supported languages
- trmm-mozakengenharia-escritrio-server-amd64.exe (PID: 5200)
- tacticalagent-v2.9.0-windows-amd64.exe (PID: 2852)
- tacticalagent-v2.9.0-windows-amd64.tmp (PID: 5772)
- tacticalrmm.exe (PID: 7948)
- tacticalrmm.exe (PID: 7732)
- meshagent.exe (PID: 8024)
- MeshAgent.exe (PID: 7480)
- MeshAgent.exe (PID: 8080)
- tacticalrmm.exe (PID: 4164)
Reads the computer name
- trmm-mozakengenharia-escritrio-server-amd64.exe (PID: 5200)
- tacticalagent-v2.9.0-windows-amd64.tmp (PID: 5772)
- tacticalrmm.exe (PID: 7732)
- tacticalrmm.exe (PID: 7948)
- meshagent.exe (PID: 8024)
- MeshAgent.exe (PID: 8080)
Reads the machine GUID from the registry
- trmm-mozakengenharia-escritrio-server-amd64.exe (PID: 5200)
- tacticalrmm.exe (PID: 7948)
- tacticalrmm.exe (PID: 7732)
- MeshAgent.exe (PID: 8080)
- tacticalrmm.exe (PID: 4164)
Create files in a temporary directory
- tacticalagent-v2.9.0-windows-amd64.exe (PID: 2852)
- tacticalagent-v2.9.0-windows-amd64.tmp (PID: 5772)
TACTICALRMM has been detected
- tacticalrmm.exe (PID: 7732)
- tacticalagent-v2.9.0-windows-amd64.tmp (PID: 5772)
- conhost.exe (PID: 7676)
- cmd.exe (PID: 7664)
- trmm-mozakengenharia-escritrio-server-amd64.exe (PID: 5200)
- tacticalrmm.exe (PID: 7948)
- meshagent.exe (PID: 8024)
- tacticalrmm.exe (PID: 4164)
Creates a software uninstall entry
- tacticalagent-v2.9.0-windows-amd64.tmp (PID: 5772)
Detects GO elliptic curve encryption (YARA)
- trmm-mozakengenharia-escritrio-server-amd64.exe (PID: 5200)
Application based on Golang
- trmm-mozakengenharia-escritrio-server-amd64.exe (PID: 5200)
Reads product name
- tacticalrmm.exe (PID: 7948)
- tacticalrmm.exe (PID: 7732)
- tacticalrmm.exe (PID: 4164)
Reads Environment values
- tacticalrmm.exe (PID: 7948)
- tacticalrmm.exe (PID: 7732)
- tacticalrmm.exe (PID: 4164)
MESHAGENT has been detected
- meshagent.exe (PID: 8024)
- WMIC.exe (PID: 4000)
- WMIC.exe (PID: 2108)
- WMIC.exe (PID: 7412)
- MeshAgent.exe (PID: 7480)
- MeshAgent.exe (PID: 8080)
- MeshAgent.exe (PID: 8080)
- WMIC.exe (PID: 7516)
- WMIC.exe (PID: 7588)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 4000)
- WMIC.exe (PID: 2108)
- WMIC.exe (PID: 7412)
- WMIC.exe (PID: 7456)
- WMIC.exe (PID: 7588)
- WMIC.exe (PID: 7516)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1040)
- powershell.exe (PID: 7872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 3 |
| CodeSize: | 2520576 |
| InitializedDataSize: | 246784 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x66fe0 |
| OSVersion: | 6.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 2.0.4.0 |
| ProductVersionNumber: | 2.0.4.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | AmidaWare LLC |
| FileDescription: | Tactical RMM Installer |
| FileVersion: | v2.0.4.0 |
| InternalName: | rmm.exe |
| LegalCopyright: | Copyright (c) 2022 AmidaWare LLC |
| OriginalFileName: | installer.go |
| ProductName: | Tactical RMM Installer |
| ProductVersion: | v2.0.4.0 |
Total processes
200
Monitored processes
67
Malicious processes
7
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1020 | ping 127.0.0.1 -n 2 | C:\Windows\SysWOW64\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | powershell -noprofile -nologo -command - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | MeshAgent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tacticalrmm.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | "cmd.exe" /c ping 127.0.0.1 -n 2 && net stop tacticalrpc | C:\Windows\SysWOW64\cmd.exe | — | tacticalagent-v2.9.0-windows-amd64.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | C:\WINDOWS\system32\net1 stop tacticalagent | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1244 | net stop tacticalagent | C:\Windows\SysWOW64\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | net stop tacticalrpc | C:\Windows\SysWOW64\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | "cmd.exe" /c ping 127.0.0.1 -n 2 && net stop tacticalrmm | C:\Windows\SysWOW64\cmd.exe | — | tacticalagent-v2.9.0-windows-amd64.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
43 271
Read events
43 199
Write events
64
Delete events
8
Modification events
| (PID) Process: | (5200) trmm-mozakengenharia-escritrio-server-amd64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | 2A1D6027D94AB10A1C4D915CCD33A0CB3E2D54CB |
Value: | |||
| (PID) Process: | (5200) trmm-mozakengenharia-escritrio-server-amd64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\2A1D6027D94AB10A1C4D915CCD33A0CB3E2D54CB |
| Operation: | write | Name: | Blob |
Value: 0400000001000000100000005DB66AC46017246A1A99A84BEE5EB426140000000100000014000000804CD6EB74FF4936A3D5D8FCB53EC56AF0941D8C62000000010000002000000071CCA5391F9E794B04802530B363E121DA8A3043BB26662FEA4DCA7FC951A4BD19000000010000001000000086665B2DECDDA69376F98E02CD5FA29A0300000001000000140000002A1D6027D94AB10A1C4D915CCD33A0CB3E2D54CB0F0000000100000030000000DF03EE17776FAE07203AE956F6094206455C833A06297419E38793A34C4E010E8E0DD06107E0CD574F970FB35FB7C04E09000000010000002A000000302806082B0601050507030206082B0601050507030406082B0601050507030106082B060105050703080B0000000100000018000000470054005300200052006F006F00740020005200340000001D00000001000000100000006D81CF5A57E7A81939F2FA048E7CB95020000000010000000E0200003082020A30820191A00302010202106E47A9C88B94B6E8BB3B2AD8A2B2C199300A06082A8648CE3D0403033047310B300906035504061302555331223020060355040A1319476F6F676C65205472757374205365727669636573204C4C43311430120603550403130B47545320526F6F74205234301E170D3136303632323030303030305A170D3336303632323030303030305A3047310B300906035504061302555331223020060355040A1319476F6F676C65205472757374205365727669636573204C4C43311430120603550403130B47545320526F6F742052343076301006072A8648CE3D020106052B8104002203620004F37473A7688B60AE43B835C581307B4B499DFBC161CEE6DE46BD6BD5611835AE40DD73F78991305AEB3CEE857CA240763BA9C6B847D82AE792916A73E9B172399F299FA298D35F5E5886650FA1846506D1DC8BC9C773C88C6A2FE5C4ABD11D8AA3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E04160414804CD6EB74FF4936A3D5D8FCB53EC56AF0941D8C300A06082A8648CE3D040303036700306402306A50527408C470DC9E507421E88D7A21C34F966E15D12235612DFA0837EE196DADDBB2CC7D0734F560192CB534D96F2002300371B1BAA3600B86ED9A086A95689FE2B3E193647C5E93A6DF792D8D85E394CF235D71CCF2B04DD6FE99C894A975A2E3 | |||
| (PID) Process: | (5200) trmm-mozakengenharia-escritrio-server-amd64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\2A1D6027D94AB10A1C4D915CCD33A0CB3E2D54CB |
| Operation: | write | Name: | Blob |
Value: 5C0000000100000004000000800100001D00000001000000100000006D81CF5A57E7A81939F2FA048E7CB9500B0000000100000018000000470054005300200052006F006F007400200052003400000009000000010000002A000000302806082B0601050507030206082B0601050507030406082B0601050507030106082B060105050703080F0000000100000030000000DF03EE17776FAE07203AE956F6094206455C833A06297419E38793A34C4E010E8E0DD06107E0CD574F970FB35FB7C04E0300000001000000140000002A1D6027D94AB10A1C4D915CCD33A0CB3E2D54CB19000000010000001000000086665B2DECDDA69376F98E02CD5FA29A62000000010000002000000071CCA5391F9E794B04802530B363E121DA8A3043BB26662FEA4DCA7FC951A4BD140000000100000014000000804CD6EB74FF4936A3D5D8FCB53EC56AF0941D8C0400000001000000100000005DB66AC46017246A1A99A84BEE5EB42620000000010000000E0200003082020A30820191A00302010202106E47A9C88B94B6E8BB3B2AD8A2B2C199300A06082A8648CE3D0403033047310B300906035504061302555331223020060355040A1319476F6F676C65205472757374205365727669636573204C4C43311430120603550403130B47545320526F6F74205234301E170D3136303632323030303030305A170D3336303632323030303030305A3047310B300906035504061302555331223020060355040A1319476F6F676C65205472757374205365727669636573204C4C43311430120603550403130B47545320526F6F742052343076301006072A8648CE3D020106052B8104002203620004F37473A7688B60AE43B835C581307B4B499DFBC161CEE6DE46BD6BD5611835AE40DD73F78991305AEB3CEE857CA240763BA9C6B847D82AE792916A73E9B172399F299FA298D35F5E5886650FA1846506D1DC8BC9C773C88C6A2FE5C4ABD11D8AA3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E04160414804CD6EB74FF4936A3D5D8FCB53EC56AF0941D8C300A06082A8648CE3D040303036700306402306A50527408C470DC9E507421E88D7A21C34F966E15D12235612DFA0837EE196DADDBB2CC7D0734F560192CB534D96F2002300371B1BAA3600B86ED9A086A95689FE2B3E193647C5E93A6DF792D8D85E394CF235D71CCF2B04DD6FE99C894A975A2E3 | |||
| (PID) Process: | (5772) tacticalagent-v2.9.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.2.2 | |||
| (PID) Process: | (5772) tacticalagent-v2.9.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\TacticalAgent | |||
| (PID) Process: | (5772) tacticalagent-v2.9.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\TacticalAgent\ | |||
| (PID) Process: | (5772) tacticalagent-v2.9.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: (Default) | |||
| (PID) Process: | (5772) tacticalagent-v2.9.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (5772) tacticalagent-v2.9.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: english | |||
| (PID) Process: | (5772) tacticalagent-v2.9.0-windows-amd64.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0D34D278-5FAF-4159-A4A0-4E2D2C08139D}_is1 |
| Operation: | write | Name: | DisplayName |
Value: Tactical RMM Agent | |||
Executable files
110
Suspicious files
10
Text files
442
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2852 | tacticalagent-v2.9.0-windows-amd64.exe | C:\Users\admin\AppData\Local\Temp\is-UK0HQ.tmp\tacticalagent-v2.9.0-windows-amd64.tmp | executable | |
MD5:F7B0A85F1A18F9689015113AA1FA44EE | SHA256:CDF9A208A33E94C5BEC44A613A444AD9D7EDEA4735C0F42E894356EE5C079134 | |||
| 5772 | tacticalagent-v2.9.0-windows-amd64.tmp | C:\Users\admin\AppData\Local\Temp\is-11N2P.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 7948 | tacticalrmm.exe | C:\Program Files\TacticalAgent\meshagent.exe | executable | |
MD5:343CD5E3E7115A8BBCE0DC03D1A383F9 | SHA256:CBA2D560DDAEEC63EFB53514E62A3E6F6D71957EBA120C52B2DAB254F40A1BD8 | |||
| 5772 | tacticalagent-v2.9.0-windows-amd64.tmp | C:\Program Files\TacticalAgent\unins000.exe | executable | |
MD5:231C790F354DE2EDAA9EE0A38CA3B9B1 | SHA256:156765088D513FE8FC37F2865A25178FB8B79C0C868415E3C2354F96C0B66235 | |||
| 5772 | tacticalagent-v2.9.0-windows-amd64.tmp | C:\Program Files\TacticalAgent\is-DGCMC.tmp | executable | |
MD5:231C790F354DE2EDAA9EE0A38CA3B9B1 | SHA256:156765088D513FE8FC37F2865A25178FB8B79C0C868415E3C2354F96C0B66235 | |||
| 5772 | tacticalagent-v2.9.0-windows-amd64.tmp | C:\Program Files\TacticalAgent\tacticalrmm.exe | executable | |
MD5:9CE7D5FDA18D04AA74F5C43160E27653 | SHA256:169E5A4139CF51351E1CF23B04D5A319990AA73F2B4FAC99392E09CDB74AAB2C | |||
| 5772 | tacticalagent-v2.9.0-windows-amd64.tmp | C:\Users\admin\AppData\Local\Temp\Setup Log 2025-04-29 #001.txt | text | |
MD5:ED98610BF7A756DE330FADEDFC47E1CC | SHA256:9766031E6184950AA30FC80DAE489FB4AC862946D321CE80D3FA3520BCBFBB16 | |||
| 8080 | MeshAgent.exe | C:\Program Files\Mesh Agent\MeshAgent.msh | text | |
MD5:EFA45C50F4539EF52D45765C56CE56FF | SHA256:48DD530B66C14C8F5E8CAA6DB608FD91CAC8EB13C485E69B8A438723ED7EBC91 | |||
| 8024 | meshagent.exe | C:\Program Files\Mesh Agent\MeshAgent.exe | executable | |
MD5:343CD5E3E7115A8BBCE0DC03D1A383F9 | SHA256:CBA2D560DDAEEC63EFB53514E62A3E6F6D71957EBA120C52B2DAB254F40A1BD8 | |||
| 5772 | tacticalagent-v2.9.0-windows-amd64.tmp | C:\Program Files\TacticalAgent\unins000.dat | binary | |
MD5:4EFBDD819A51213B7BD156735C5091CF | SHA256:45D10B5527E323F7C5B3A34CB3285E0CB93AA15E616176B6F970E348484C23DC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
30
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.169:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5416 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5416 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.169:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5200 | trmm-mozakengenharia-escritrio-server-amd64.exe | 172.67.151.233:443 | agents.tacticalrmm.com | CLOUDFLARENET | US | unknown |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
agents.tacticalrmm.com |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.multipla-ti.com.br |
| unknown |
mesh.multipla-ti.com.br |
| unknown |