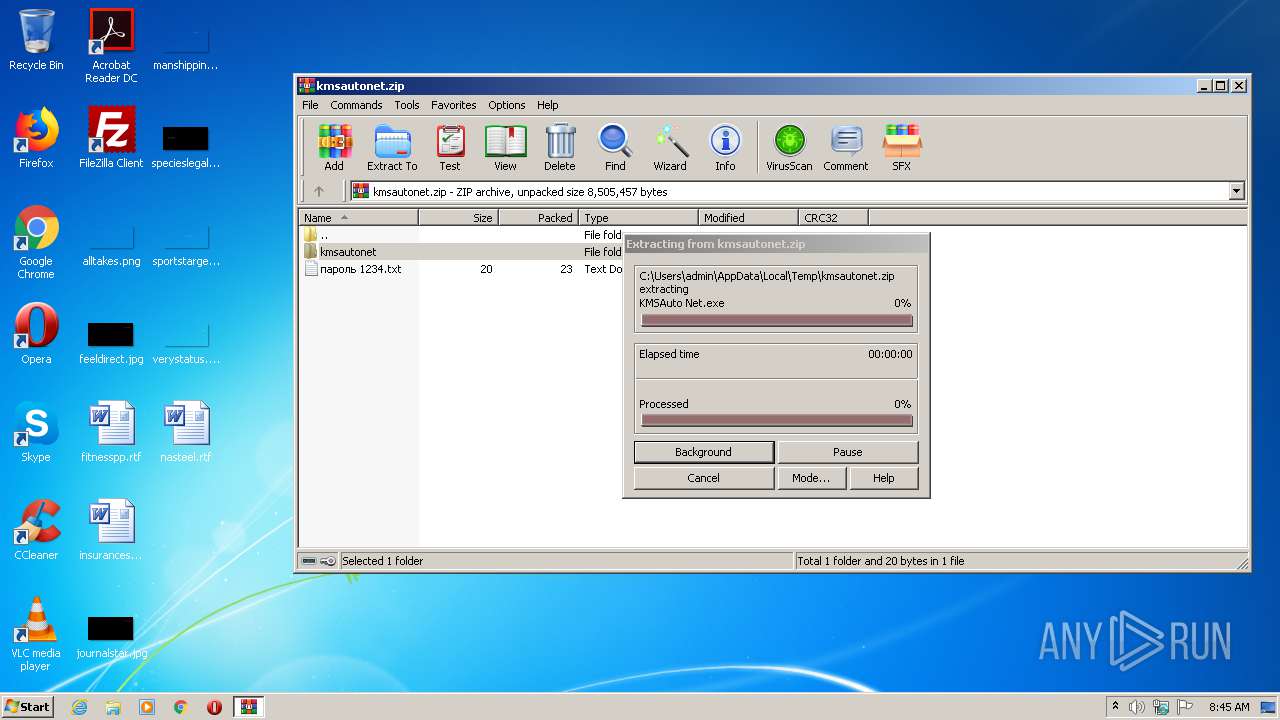
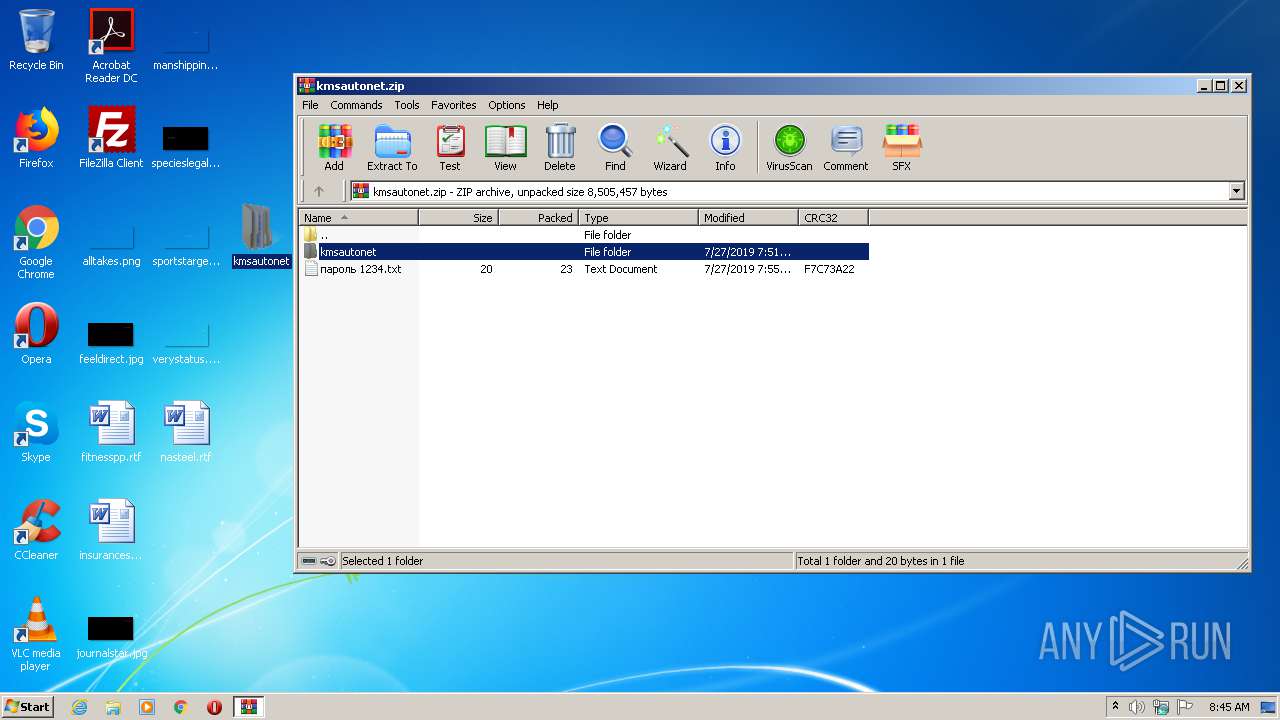
| File name: | kmsautonet.zip |
| Full analysis: | https://app.any.run/tasks/42bb72ed-ef4b-4372-9b33-cbb4ba66fe65 |
| Verdict: | Malicious activity |
| Analysis date: | July 28, 2020, 07:45:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 7ACBE962D3FABE645251EA8563D65BB4 |
| SHA1: | F032DCF8FD16E3A9757CB19C1E0FEBB9729C84B5 |
| SHA256: | 3B645D5AA6A32F0BCFE9AC0C04DEBEBF41740E14E8364D8962A5589792359094 |
| SSDEEP: | 98304:iGPoQJYWYOmnxhc597jSbByUQ9f/730/DJcBVBGlsW0VuhIBLE4Zo1RohX3uSJ3+:Ci6O8xhcn7mN85iCglXyqQLEiGRohuW+ |
MALICIOUS
Changes settings of System certificates
- certmgr.exe (PID: 2336)
- certmgr.exe (PID: 3784)
Application was dropped or rewritten from another process
- certmgr.exe (PID: 2336)
- certmgr.exe (PID: 3784)
- AESDecoder.exe (PID: 556)
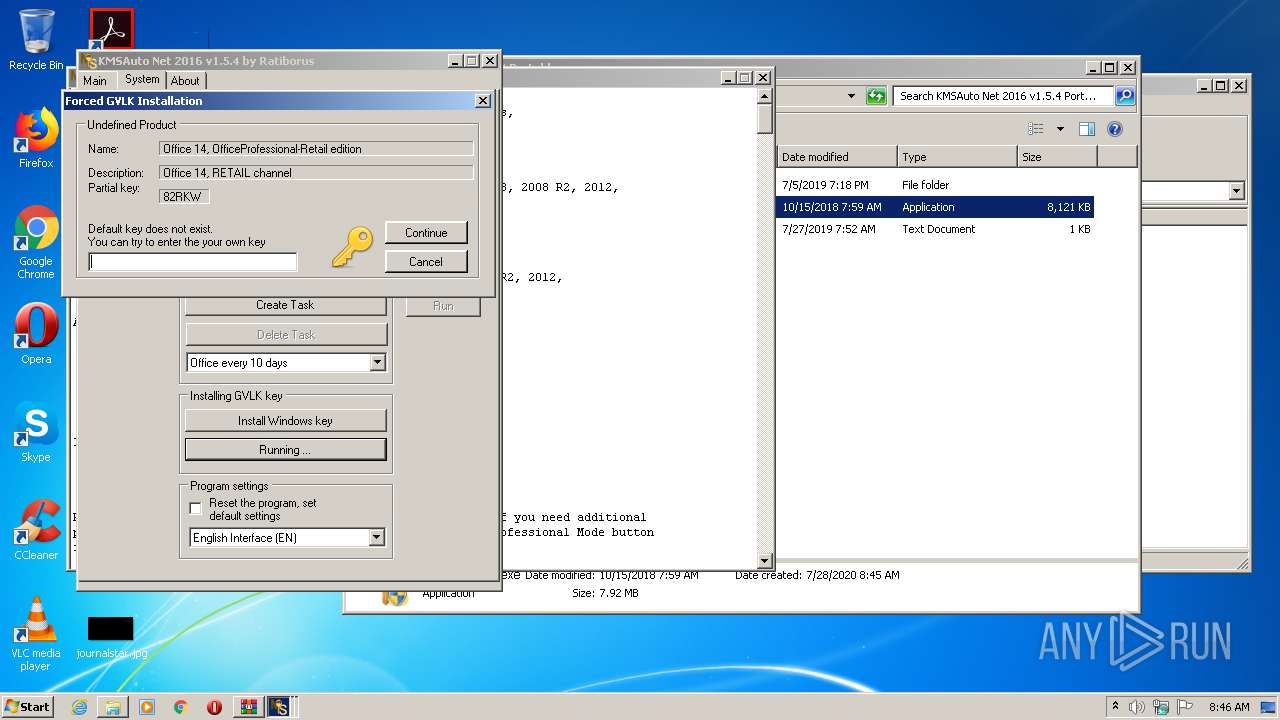
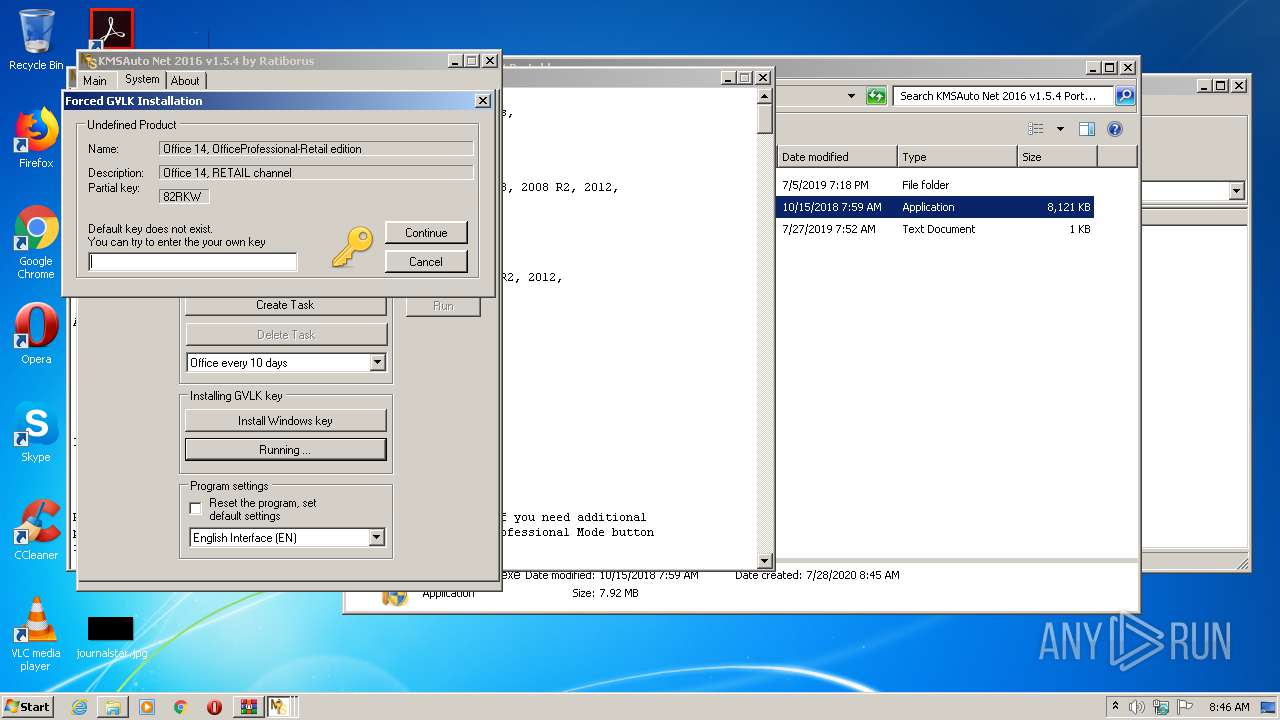
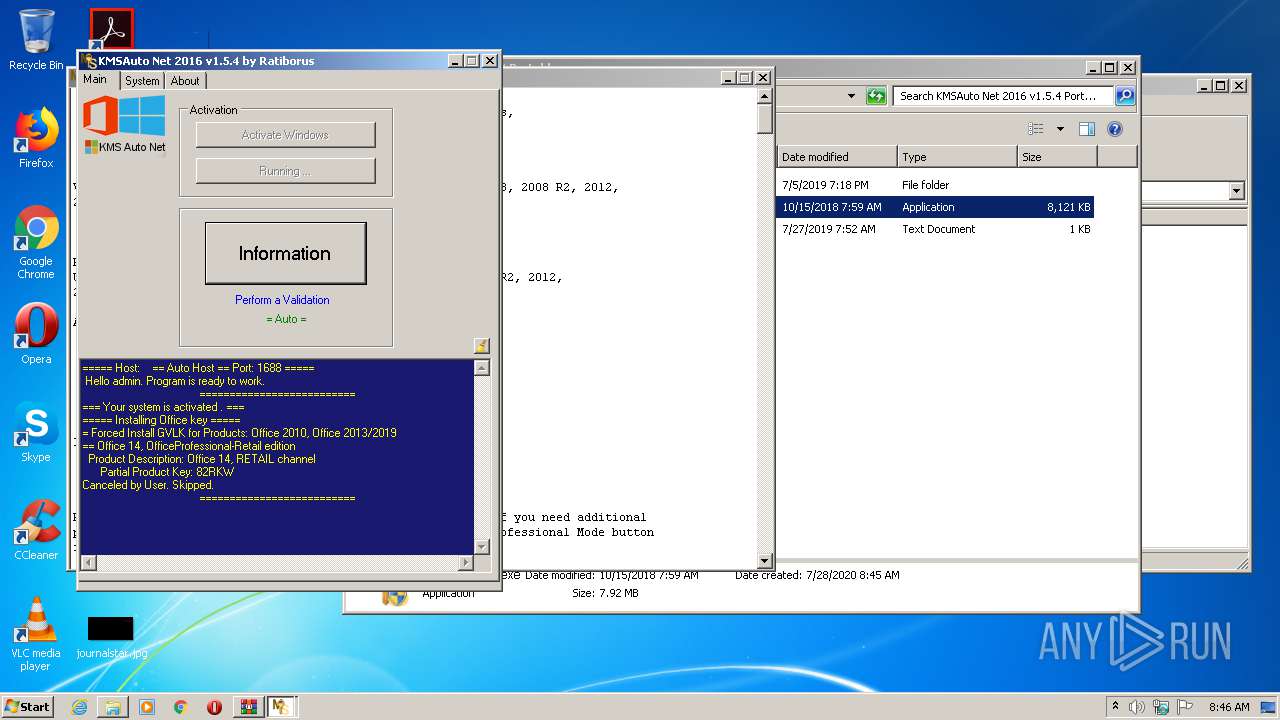
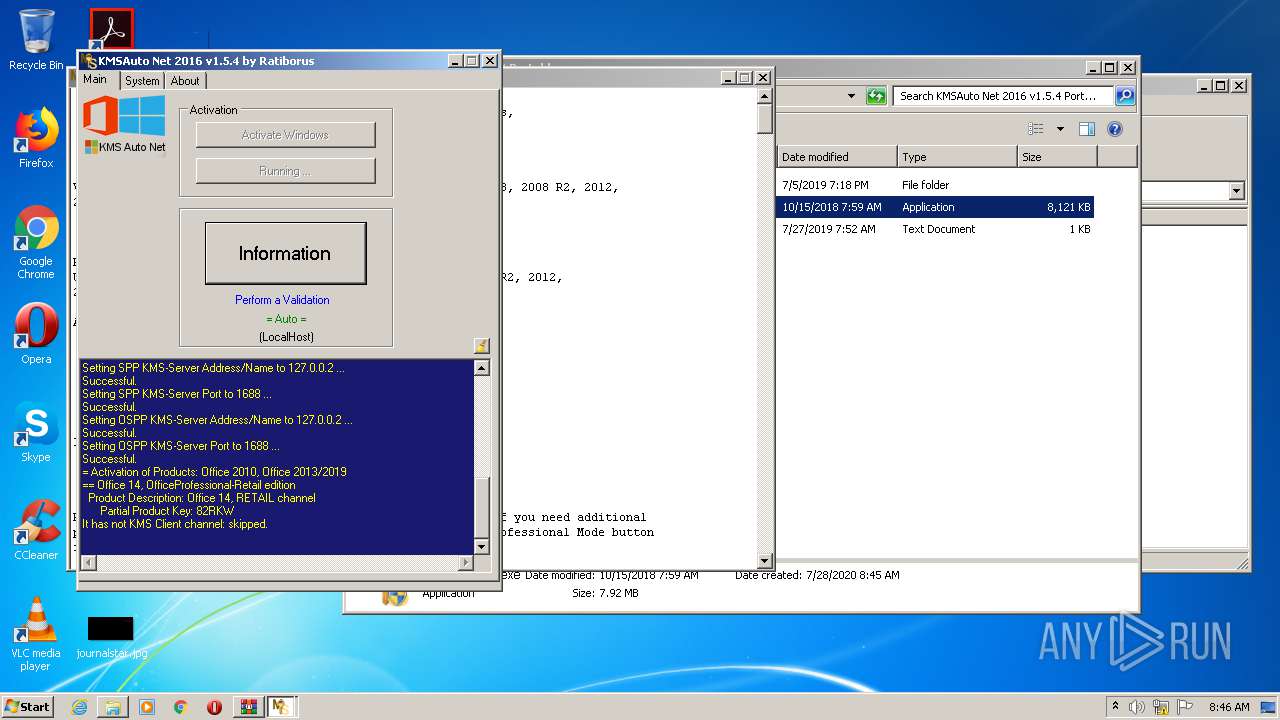
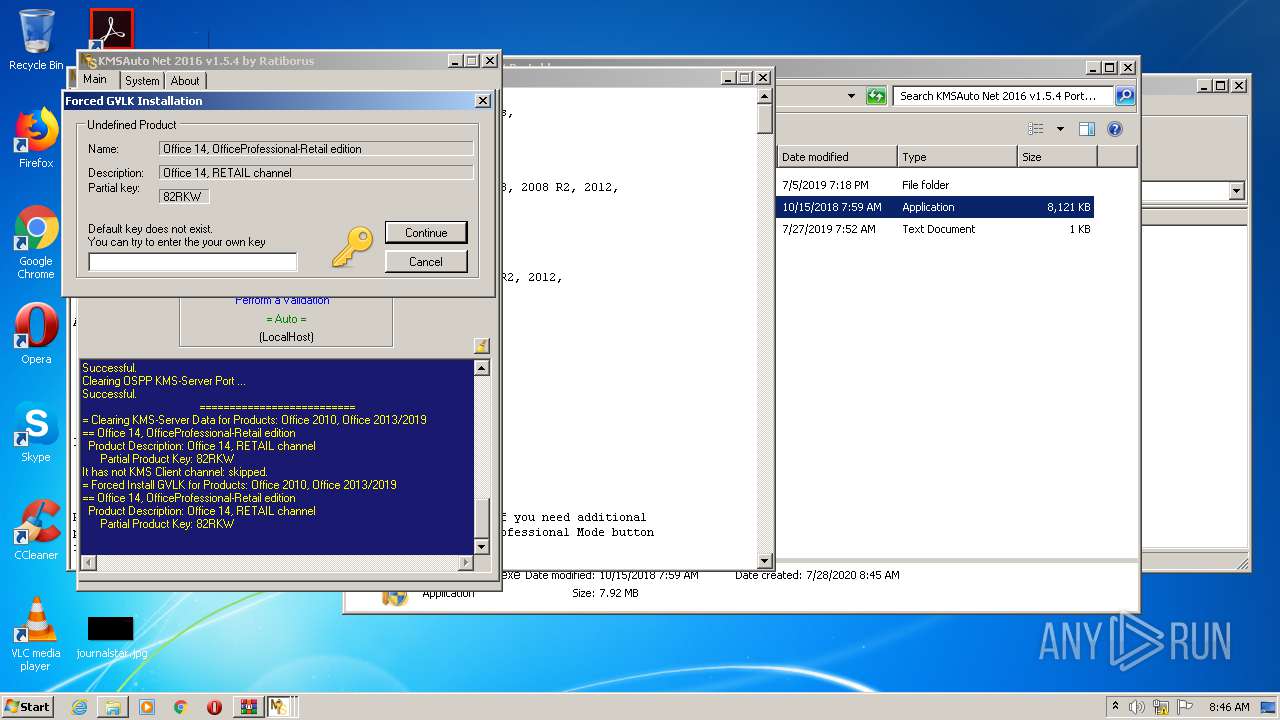
- KMSSS.exe (PID: 1684)
- KMSAuto Net.exe (PID: 1824)
- KMSAuto Net.exe (PID: 3392)
SUSPICIOUS
Creates files in the program directory
- KMSAuto Net.exe (PID: 3392)
- wzt.dat (PID: 252)
- bin.dat (PID: 3988)
- AESDecoder.exe (PID: 556)
- KMSSS.exe (PID: 1684)
- bin_x86.dat (PID: 340)
Starts CMD.EXE for self-deleting
- KMSAuto Net.exe (PID: 3392)
Starts CMD.EXE for commands execution
- KMSAuto Net.exe (PID: 3392)
- cmd.exe (PID: 3420)
Starts application with an unusual extension
- cmd.exe (PID: 1496)
- cmd.exe (PID: 2072)
- cmd.exe (PID: 3728)
Reads internet explorer settings
- KMSAuto Net.exe (PID: 3392)
Reads Environment values
- KMSAuto Net.exe (PID: 3392)
Executable content was dropped or overwritten
- wzt.dat (PID: 252)
- bin.dat (PID: 3988)
- bin_x86.dat (PID: 340)
- KMSAuto Net.exe (PID: 3392)
- AESDecoder.exe (PID: 556)
Uses NETSTAT.EXE to discover network connections
- cmd.exe (PID: 3848)
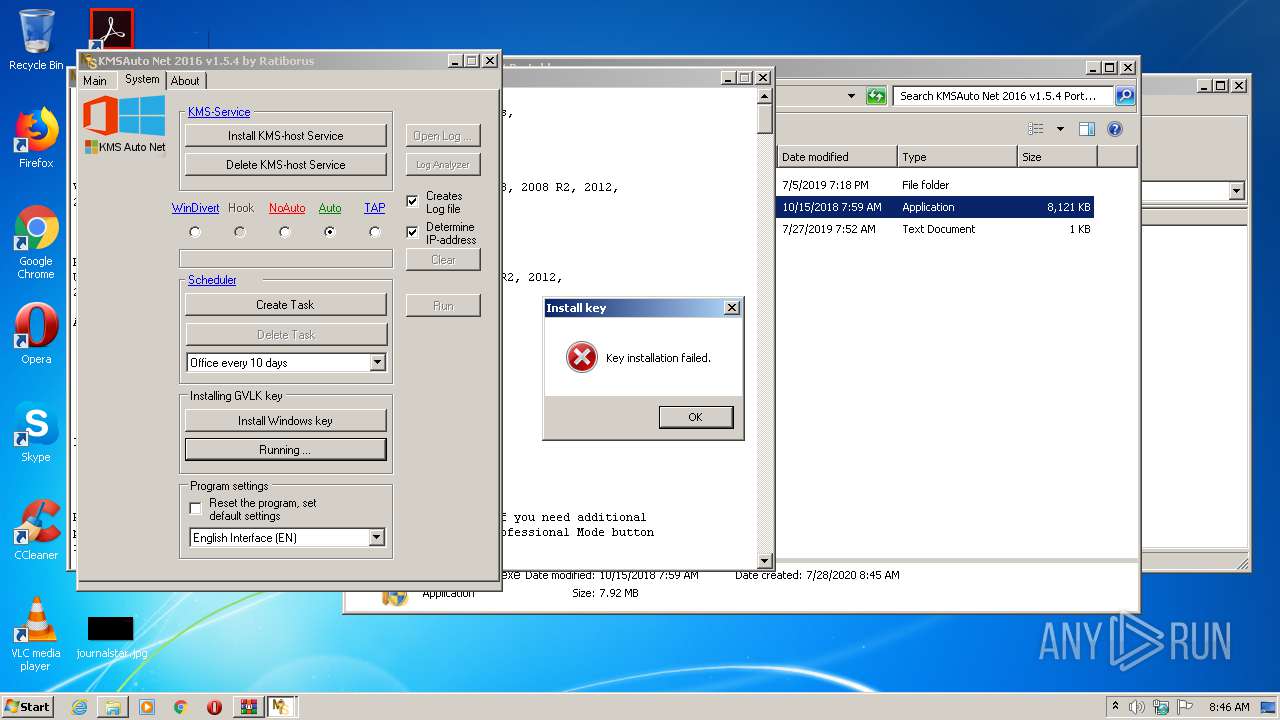
Starts SC.EXE for service management
- KMSAuto Net.exe (PID: 3392)
Uses NETSH.EXE for network configuration
- KMSAuto Net.exe (PID: 3392)
Creates or modifies windows services
- KMSAuto Net.exe (PID: 3392)
Executed as Windows Service
- KMSSS.exe (PID: 1684)
Uses REG.EXE to modify Windows registry
- KMSAuto Net.exe (PID: 3392)
INFO
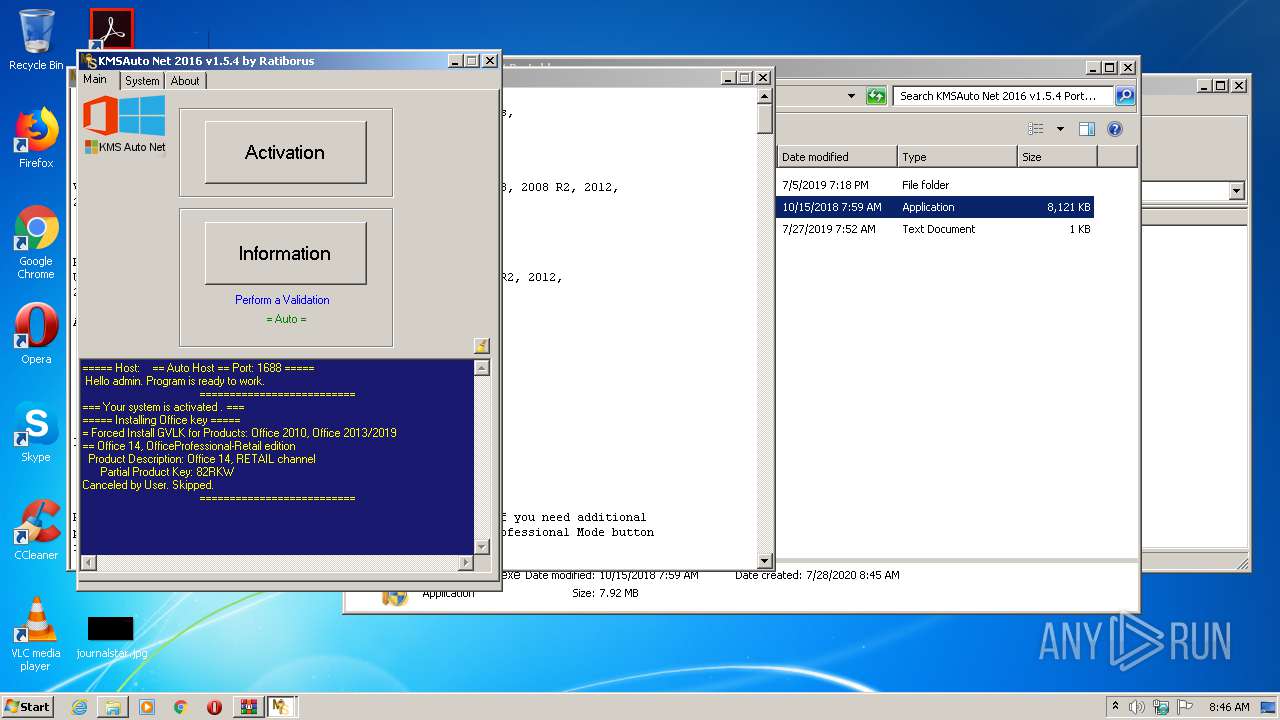
Manual execution by user
- KMSAuto Net.exe (PID: 3392)
- KMSAuto Net.exe (PID: 1824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:07:27 11:51:18 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | kmsautonet/ |
Total processes
108
Monitored processes
39
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | wzt.dat -y -pkmsauto | C:\ProgramData\KMSAuto\wzt.dat | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 296 | C:\Windows\System32\Netsh Advfirewall Firewall delete rule name="0pen Port KMS" protocol=TCP | C:\Windows\System32\Netsh.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 340 | bin_x86.dat -y -pkmsauto | C:\ProgramData\KMSAuto\bin_x86.dat | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 556 | AESDecoder.exe | C:\ProgramData\KMSAuto\bin\AESDecoder.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 564 | C:\Windows\System32\cmd.exe /c echo test>>"C:\Users\admin\Desktop\kmsautonet\KMSAuto Net 2016 v1.5.4 Portable\test.test" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1020 | "C:\Windows\System32\cmd.exe" /c rd "C:\ProgramData\KMSAuto\wzt" /S /Q | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1336 | C:\Windows\System32\cmd.exe /D /c certmgr.exe -add wzteam.cer -n wzteam -s -r localMachine TRUSTEDPUBLISHER | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1372 | C:\Windows\System32\Netsh Advfirewall Firewall add rule name="0pen Port KMS" dir=in action=allow protocol=TCP localport=1688 | C:\Windows\System32\Netsh.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1400 | C:\Windows\System32\cmd.exe /D /c del /F /Q "AESDecoder.exe" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1496 | C:\Windows\System32\cmd.exe /D /c wzt.dat -y -pkmsauto | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
695
Read events
570
Write events
121
Delete events
4
Modification events
| (PID) Process: | (1900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1900) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\132\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\kmsautonet.zip | |||
| (PID) Process: | (1900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1900) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\132\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
| (PID) Process: | (1900) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
14
Suspicious files
4
Text files
21
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1900.16812\kmsautonet\KMSAuto Net 2016 v1.5.4 Portable\KMSAuto Net.exe | — | |
MD5:— | SHA256:— | |||
| 1900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1900.16812\kmsautonet\KMSAuto Net 2016 v1.5.4 Portable\readme\readme_bg.txt | — | |
MD5:— | SHA256:— | |||
| 1900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1900.16812\kmsautonet\KMSAuto Net 2016 v1.5.4 Portable\readme\readme_cn.txt | — | |
MD5:— | SHA256:— | |||
| 1900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1900.16812\kmsautonet\KMSAuto Net 2016 v1.5.4 Portable\readme\readme_en.txt | — | |
MD5:— | SHA256:— | |||
| 1900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1900.16812\kmsautonet\KMSAuto Net 2016 v1.5.4 Portable\readme\readme_es.txt | — | |
MD5:— | SHA256:— | |||
| 1900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1900.16812\kmsautonet\KMSAuto Net 2016 v1.5.4 Portable\readme\readme_fr.txt | — | |
MD5:— | SHA256:— | |||
| 1900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1900.16812\kmsautonet\KMSAuto Net 2016 v1.5.4 Portable\readme\readme_kms.txt | — | |
MD5:— | SHA256:— | |||
| 1900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1900.16812\kmsautonet\KMSAuto Net 2016 v1.5.4 Portable\readme\readme_ru.txt | — | |
MD5:— | SHA256:— | |||
| 1900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1900.16812\kmsautonet\KMSAuto Net 2016 v1.5.4 Portable\readme\readme_ua.txt | — | |
MD5:— | SHA256:— | |||
| 1900 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1900.16812\kmsautonet\KMSAuto Net 2016 v1.5.4 Portable\readme\readme_vi.txt | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report