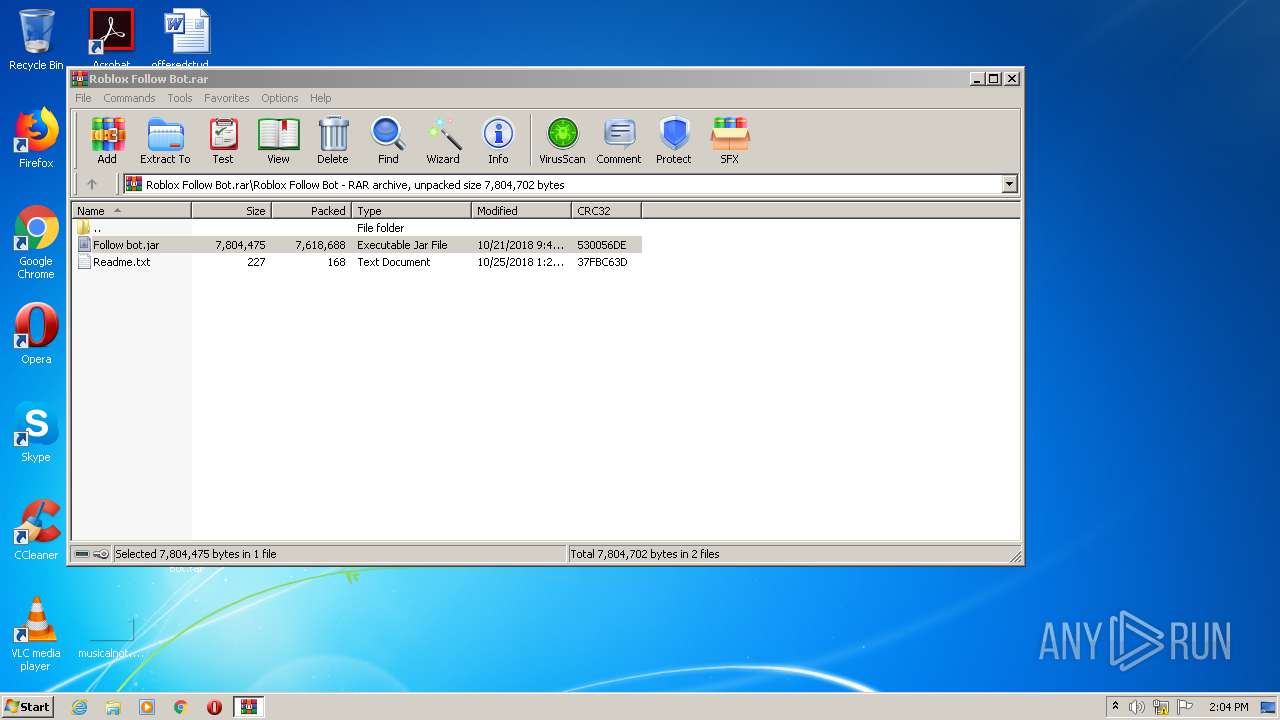
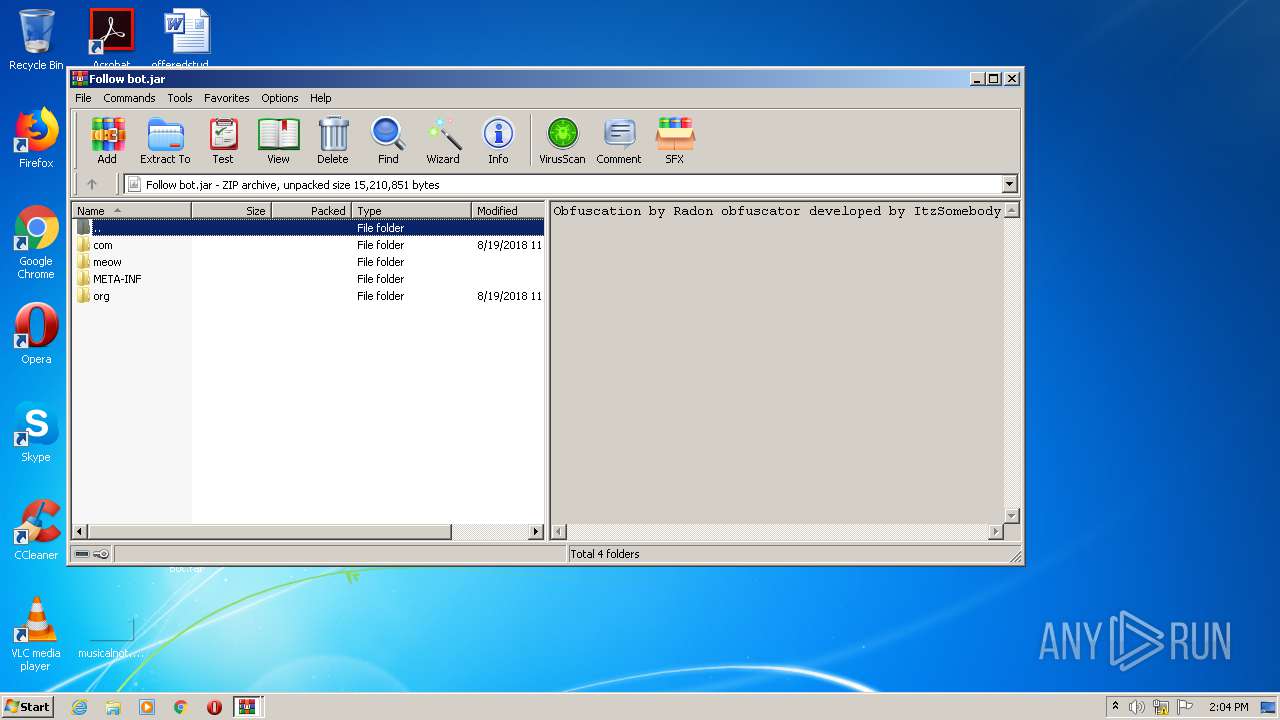
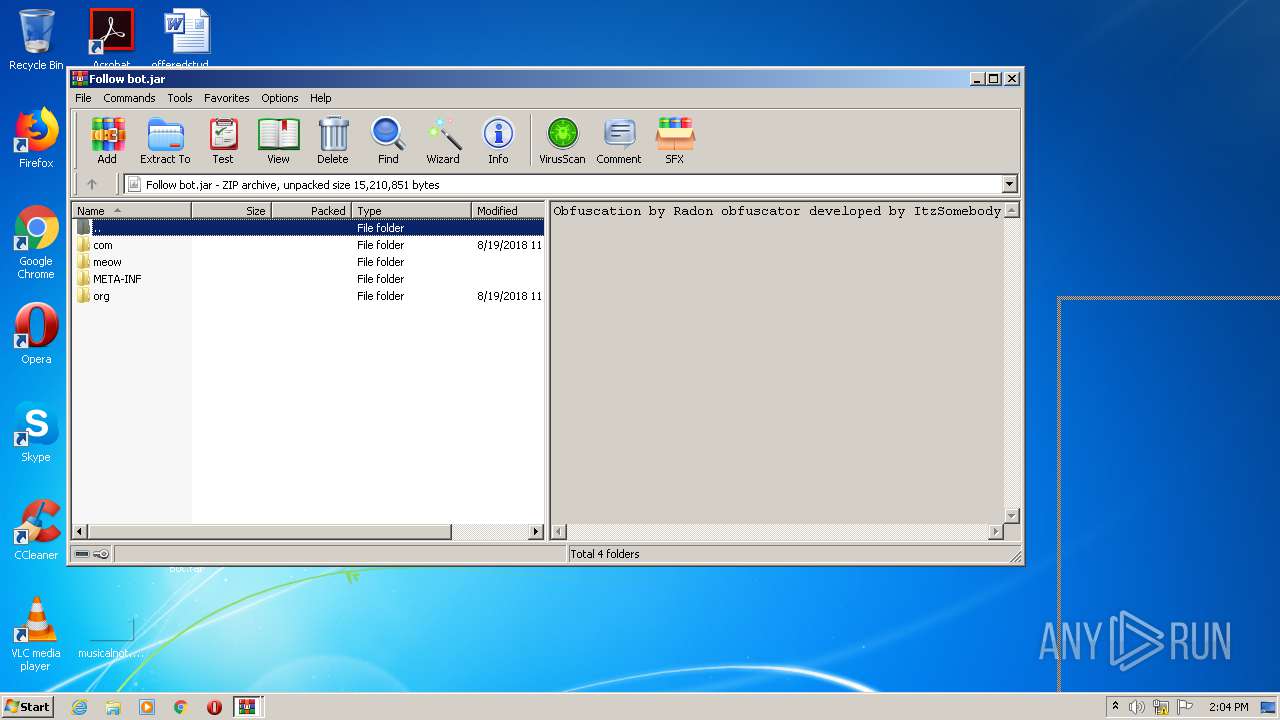
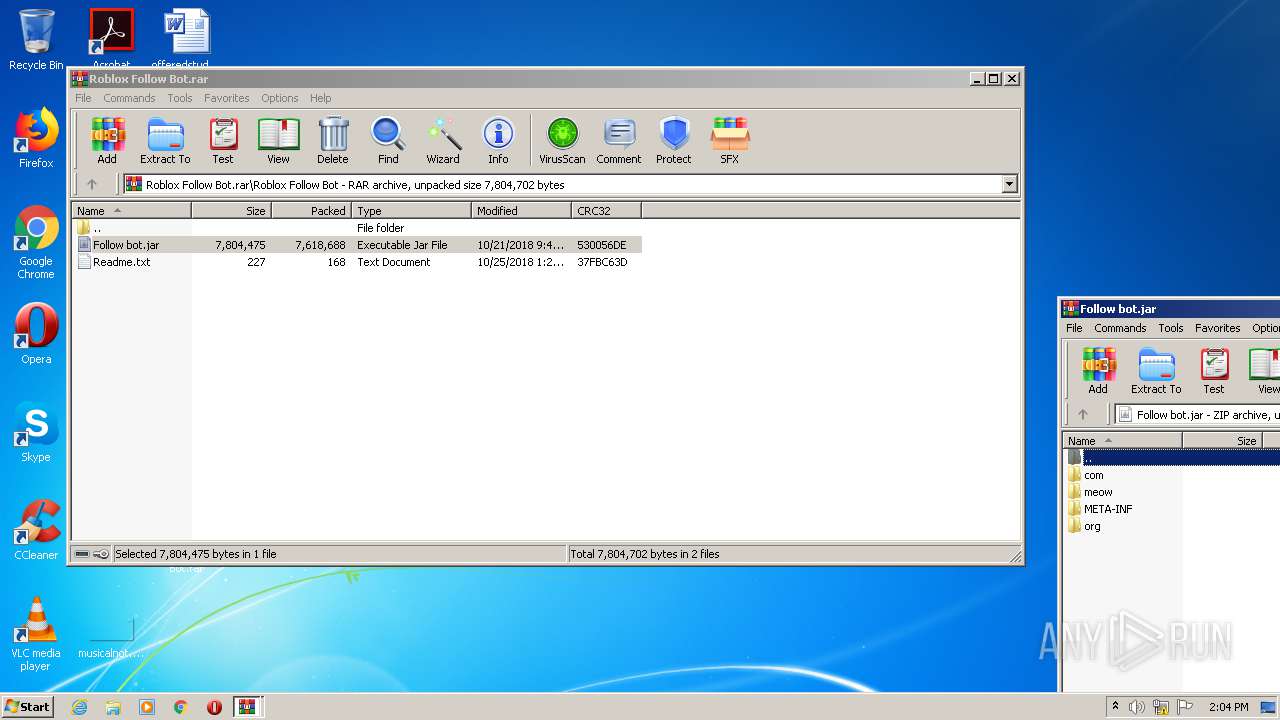
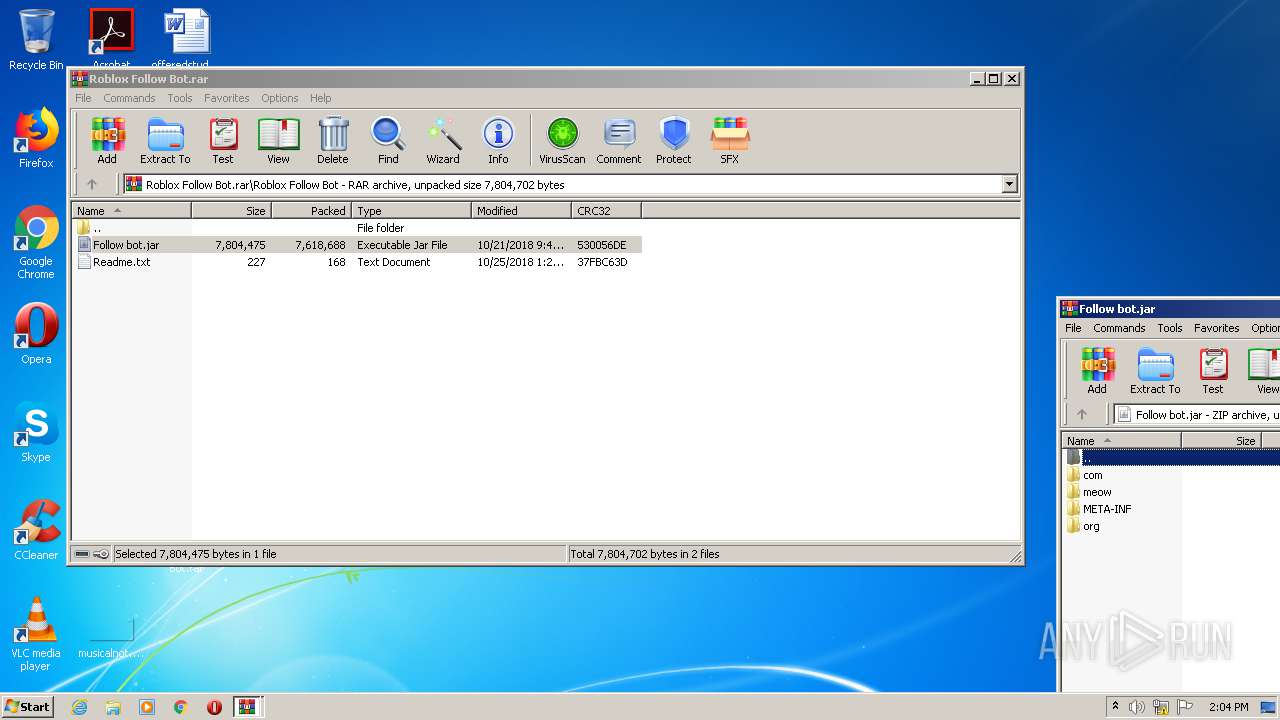
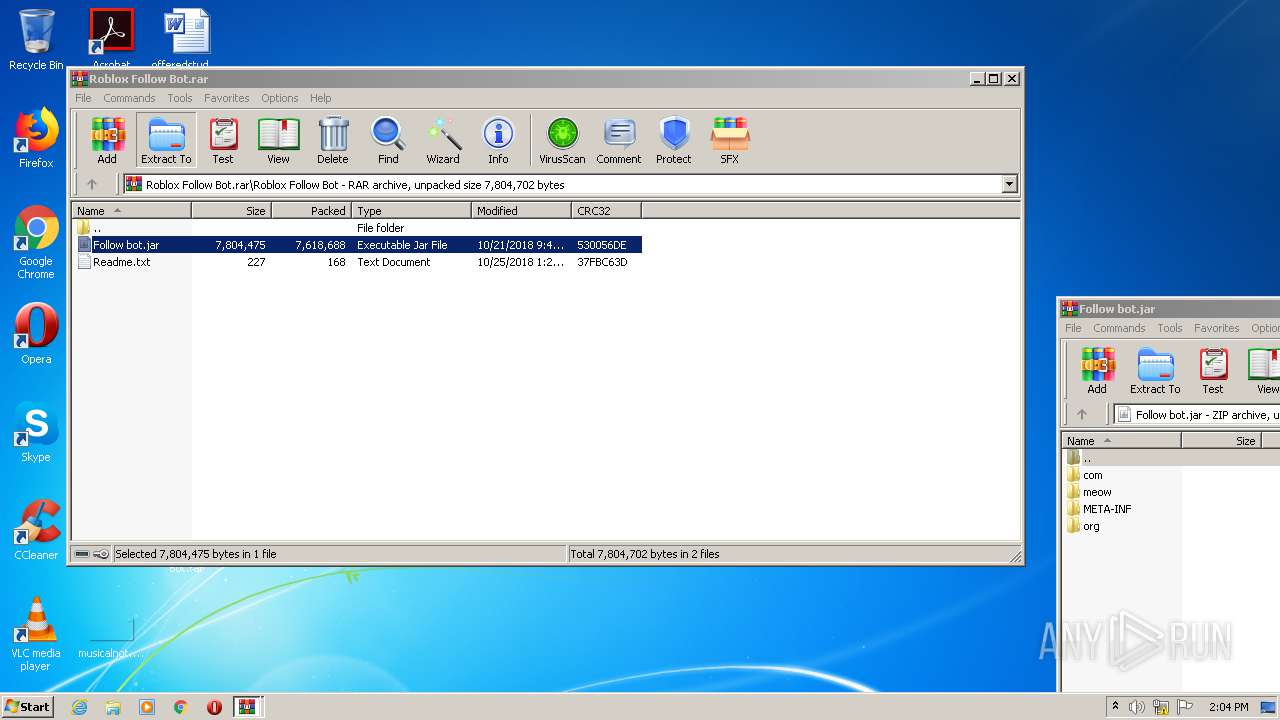
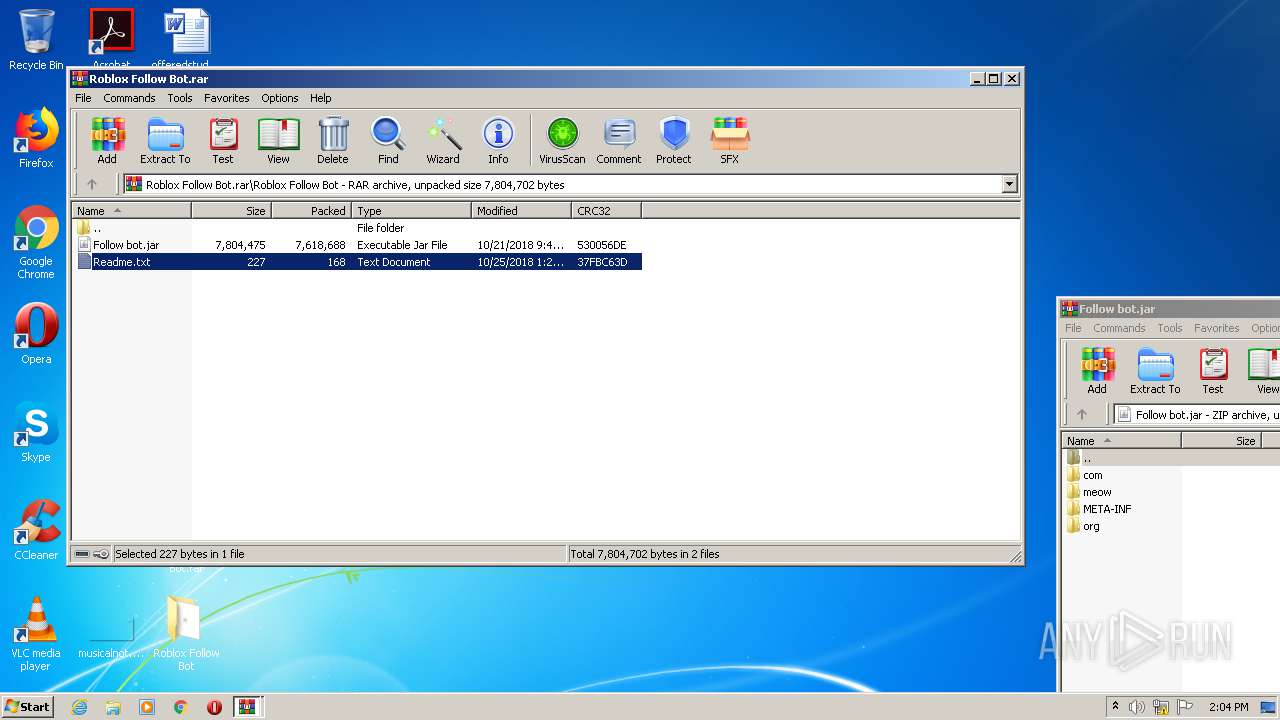
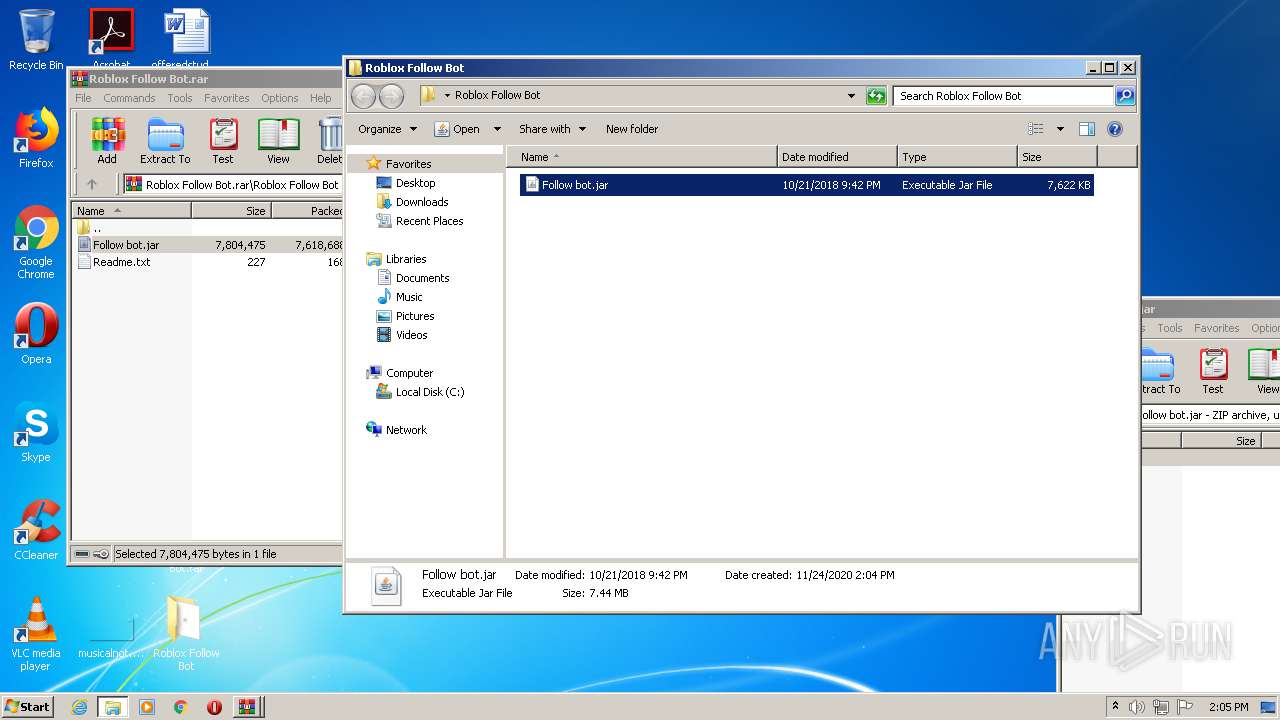
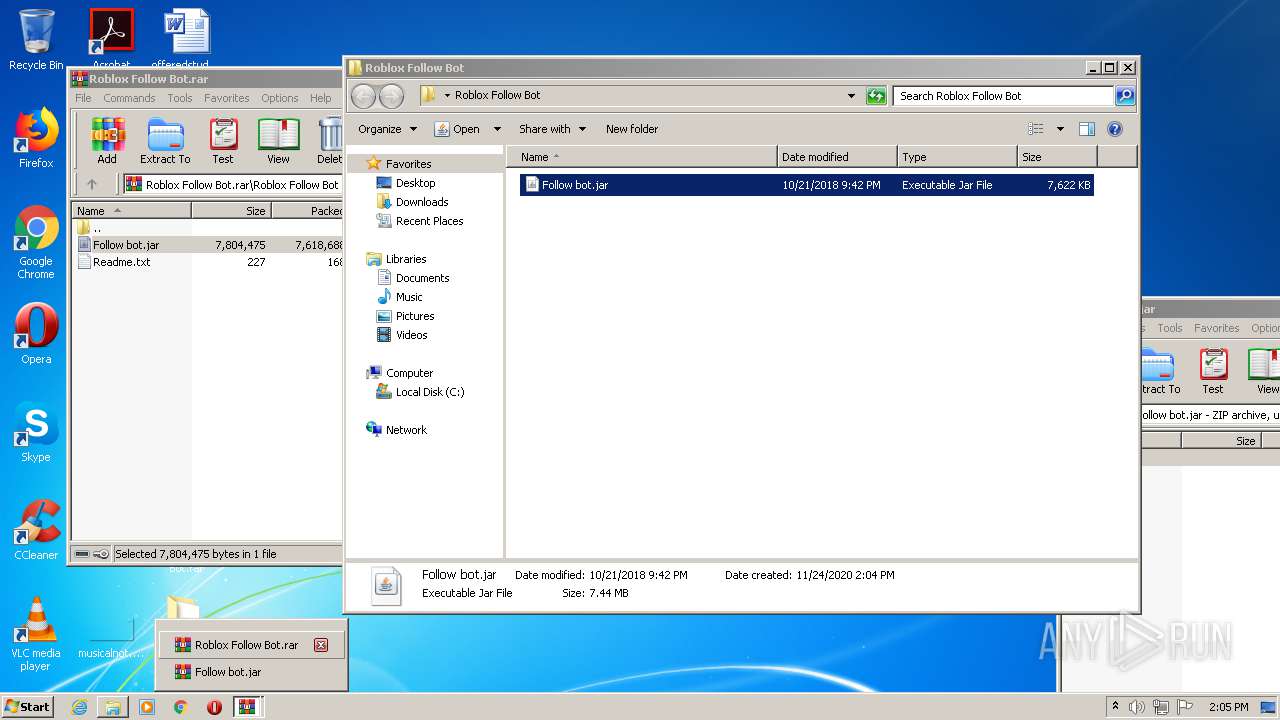
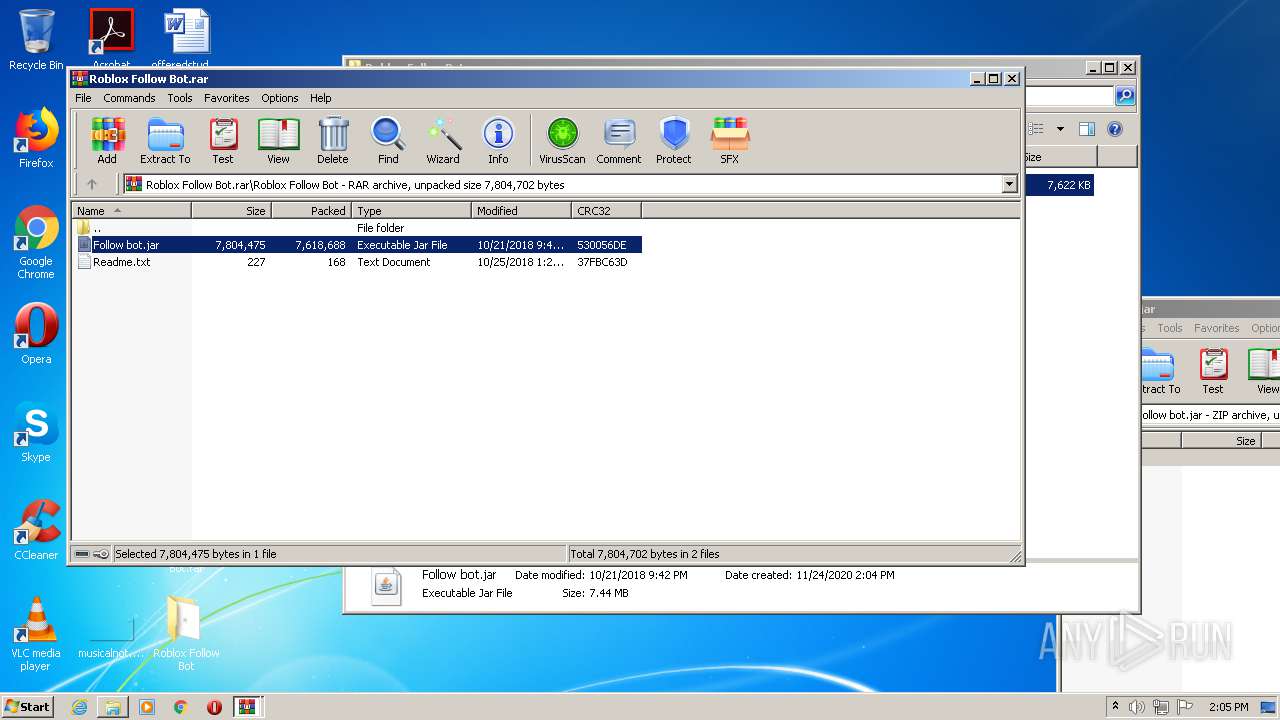
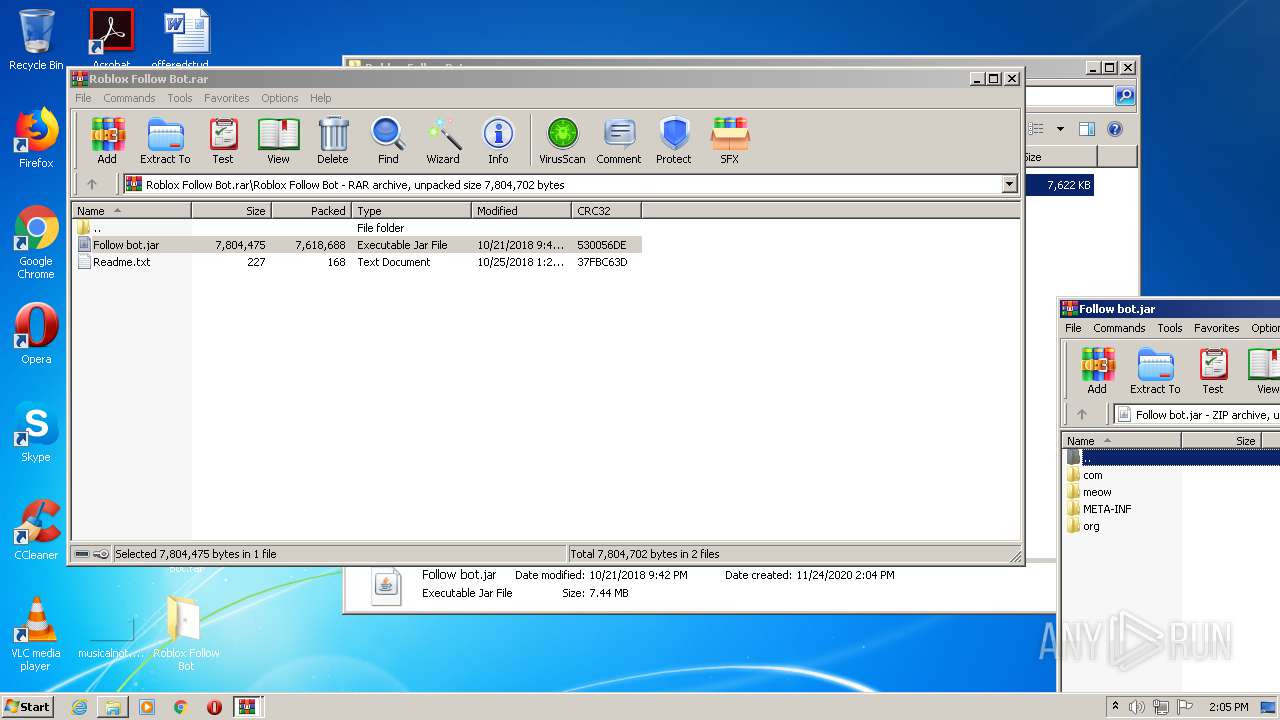
| File name: | Roblox Follow Bot.rar |
| Full analysis: | https://app.any.run/tasks/432e22ce-b75d-47a2-8665-8d187580abef |
| Verdict: | No threats detected |
| Analysis date: | November 24, 2020, 14:03:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | A5632E5C29EA3C50846CD1960BFFD660 |
| SHA1: | 76F515017BAAA95733E8871E1B9FD91769AC219C |
| SHA256: | 3B61F73019732B76E5FBFE0E71794966037122A6204C8D0D70BE6EEBA93EC216 |
| SSDEEP: | 196608:TDwac+jxcGFT5ZQluTnoJ2QLLwQs+kCdNgH:g+PfQUtCc |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 3428)
INFO
Manual execution by user
- javaw.exe (PID: 2976)
- javaw.exe (PID: 624)
- javaw.exe (PID: 3792)
- javaw.exe (PID: 2660)
- javaw.exe (PID: 3620)
- javaw.exe (PID: 4048)
- javaw.exe (PID: 2132)
- javaw.exe (PID: 572)
- javaw.exe (PID: 3664)
- javaw.exe (PID: 2904)
- javaw.exe (PID: 3592)
- javaw.exe (PID: 1392)
- javaw.exe (PID: 1944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
MPEG
| MPEGAudioVersion: | 2 |
|---|---|
| AudioLayer: | 3 |
| AudioBitrate: | 8 kbps |
| SampleRate: | 22050 |
| ChannelMode: | Stereo |
| MSStereo: | Off |
| IntensityStereo: | On |
| CopyrightFlag: | |
| OriginalMedia: | |
| Emphasis: | CCIT J.17 |
Composite
| Duration: | 2:06:59 (approx) |
|---|
Total processes
52
Monitored processes
16
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 572 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Desktop\Roblox Follow Bot\Follow bot.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 624 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Desktop\Roblox Follow Bot\Follow bot.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 1240 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa3428.47874\Follow bot.jar" | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1392 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Desktop\Roblox Follow Bot\Follow bot.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
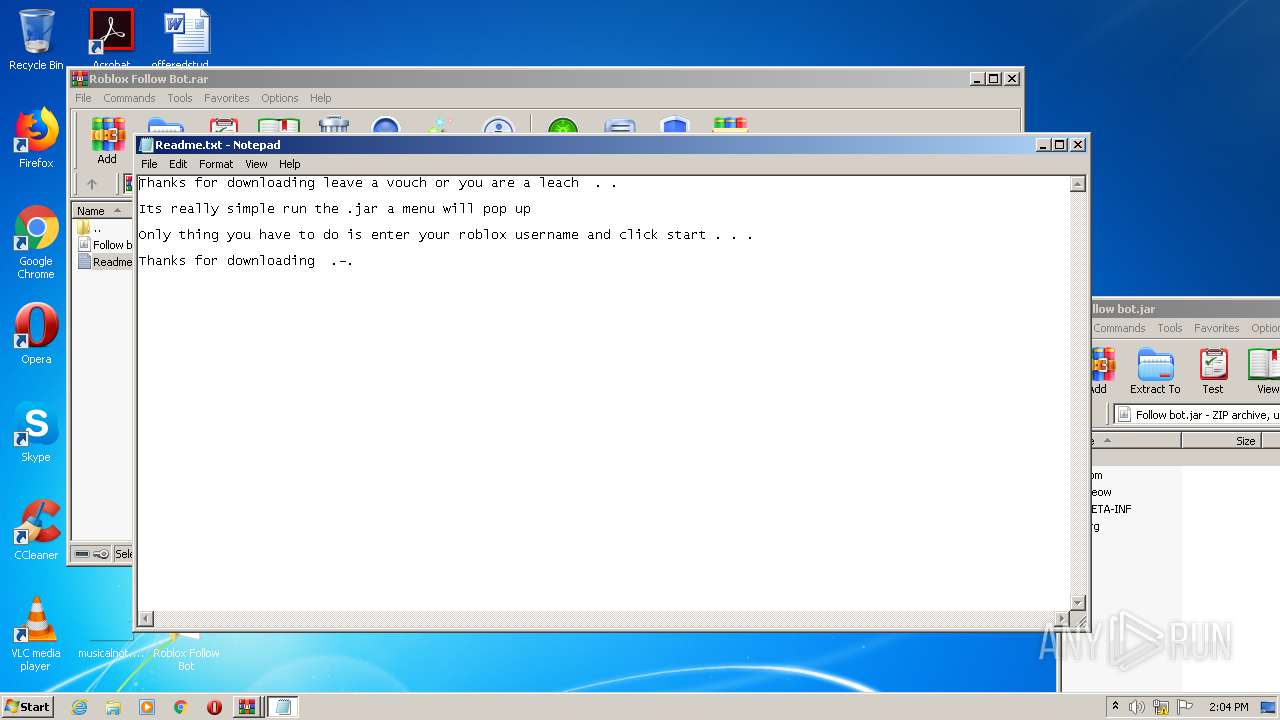
| 1560 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa3428.783\Readme.txt | C:\Windows\system32\NOTEPAD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1944 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Desktop\Roblox Follow Bot\Follow bot.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2132 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Desktop\Roblox Follow Bot\Follow bot.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2660 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Desktop\Roblox Follow Bot\Follow bot.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2904 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Desktop\Roblox Follow Bot\Follow bot.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2976 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Desktop\Roblox Follow Bot\Follow bot.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.920.14 Modules
| |||||||||||||||
Total events
1 033
Read events
998
Write events
35
Delete events
0
Modification events
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Roblox Follow Bot.rar | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
0
Suspicious files
2
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3792 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3428.783\Readme.txt | text | |
MD5:— | SHA256:— | |||
| 3428 | WinRAR.exe | C:\Users\admin\Desktop\Roblox Follow Bot\Follow bot.jar | compressed | |
MD5:— | SHA256:— | |||
| 624 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 3592 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2132 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2904 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2660 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 3664 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 1944 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
13
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3792 | javaw.exe | 51.255.4.237:1337 | — | OVH SAS | FR | unknown |
4048 | javaw.exe | 51.255.4.237:1337 | — | OVH SAS | FR | unknown |
2976 | javaw.exe | 51.255.4.237:1337 | — | OVH SAS | FR | unknown |
3620 | javaw.exe | 51.255.4.237:1337 | — | OVH SAS | FR | unknown |
624 | javaw.exe | 51.255.4.237:1337 | — | OVH SAS | FR | unknown |
2132 | javaw.exe | 51.255.4.237:1337 | — | OVH SAS | FR | unknown |
— | — | 51.255.4.237:1337 | — | OVH SAS | FR | unknown |