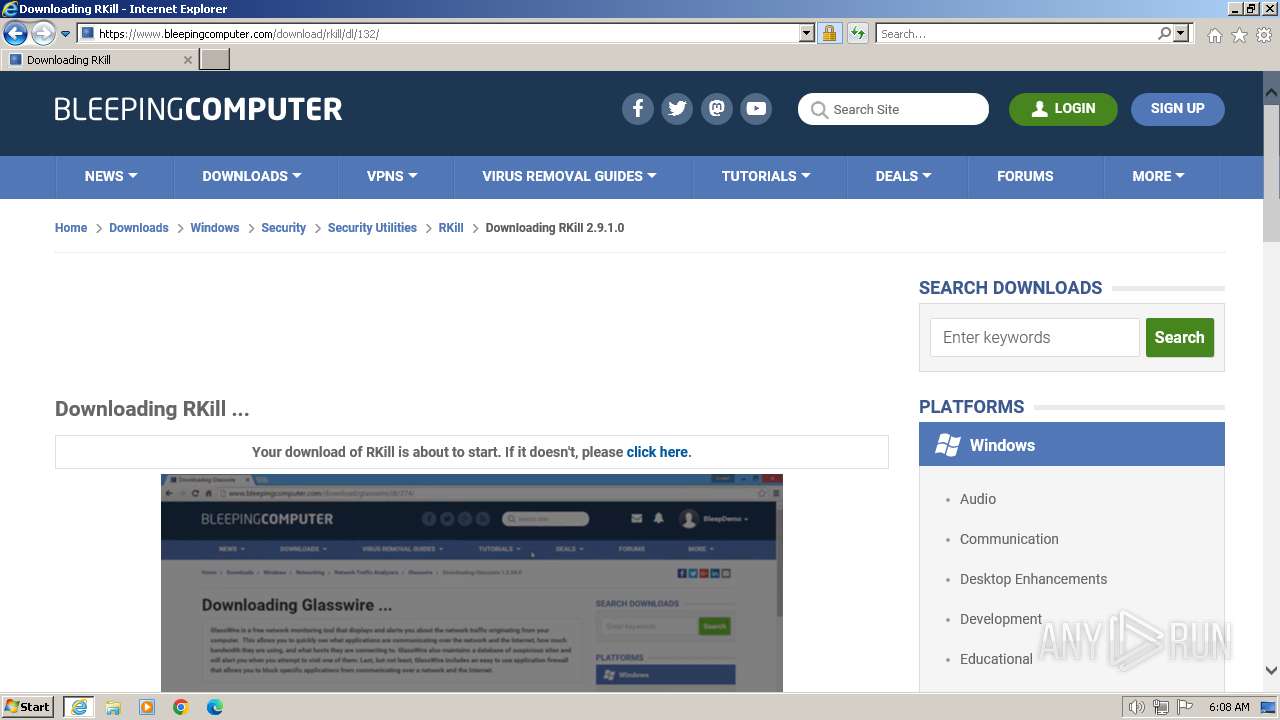
| URL: | https://www.bleepingcomputer.com/download/rkill/ |
| Full analysis: | https://app.any.run/tasks/019cfe06-30d5-4d11-9e4b-239ba369f0c9 |
| Verdict: | Malicious activity |
| Analysis date: | January 12, 2024, 06:08:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 269DD5737BA0615B5620DE1EF50C44DE |
| SHA1: | FCAF2BAE902345BBA5A2EF29D4F689E0B2BF2025 |
| SHA256: | 3B52D6886CAB1B7D00A89F4B2B292C34A205AE68D22E5A0236300F75F3A1751B |
| SSDEEP: | 3:N8DSLpyCGTVEApMLzKn:2OLdRi |
MALICIOUS
No malicious indicators.SUSPICIOUS
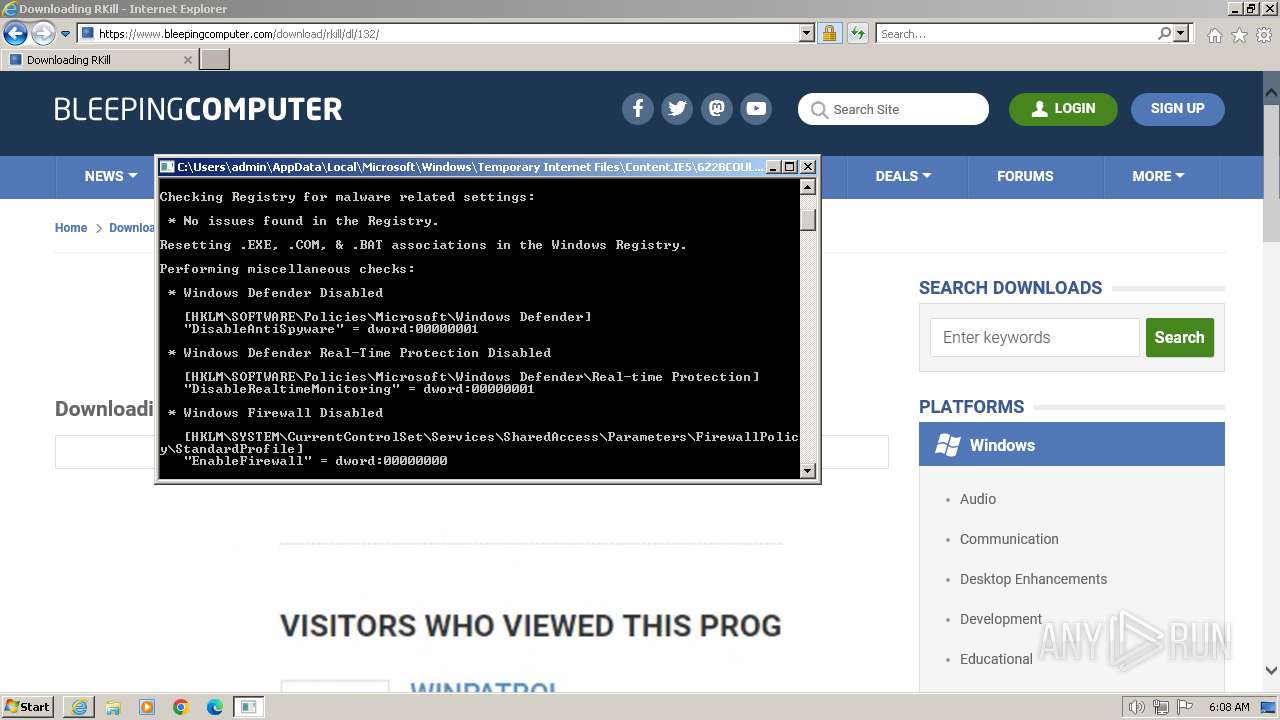
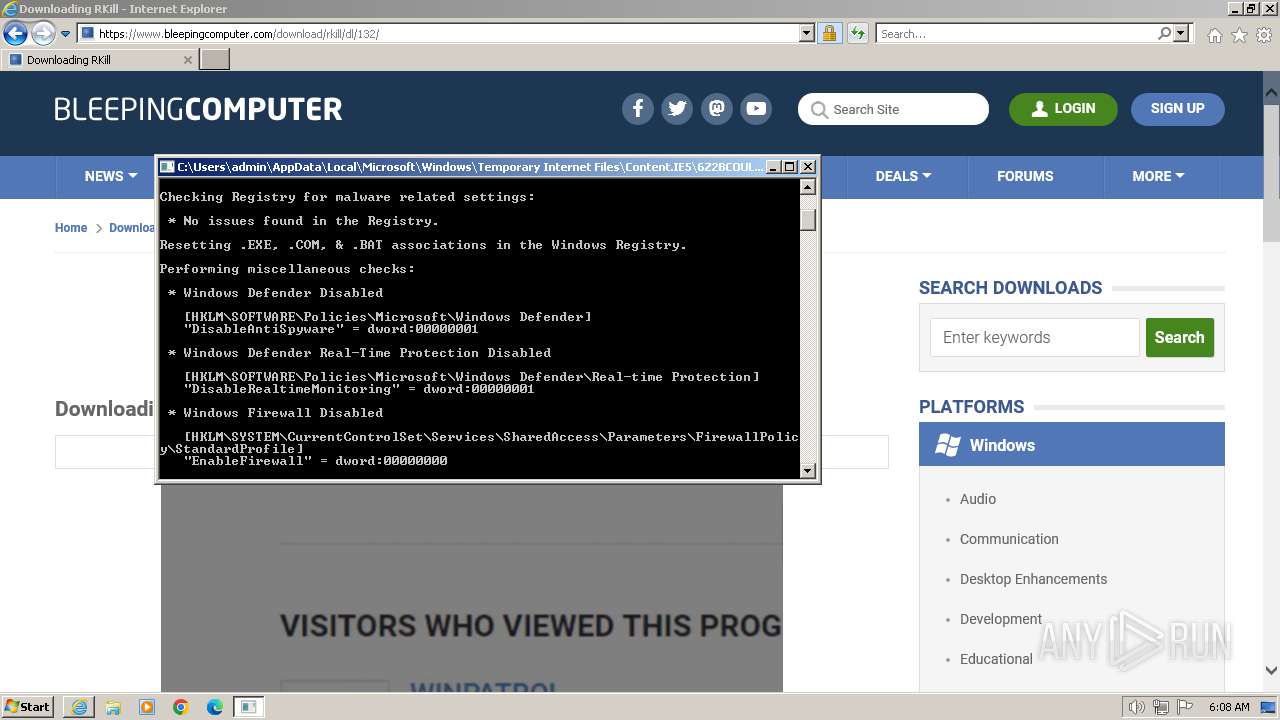
Reads security settings of Internet Explorer
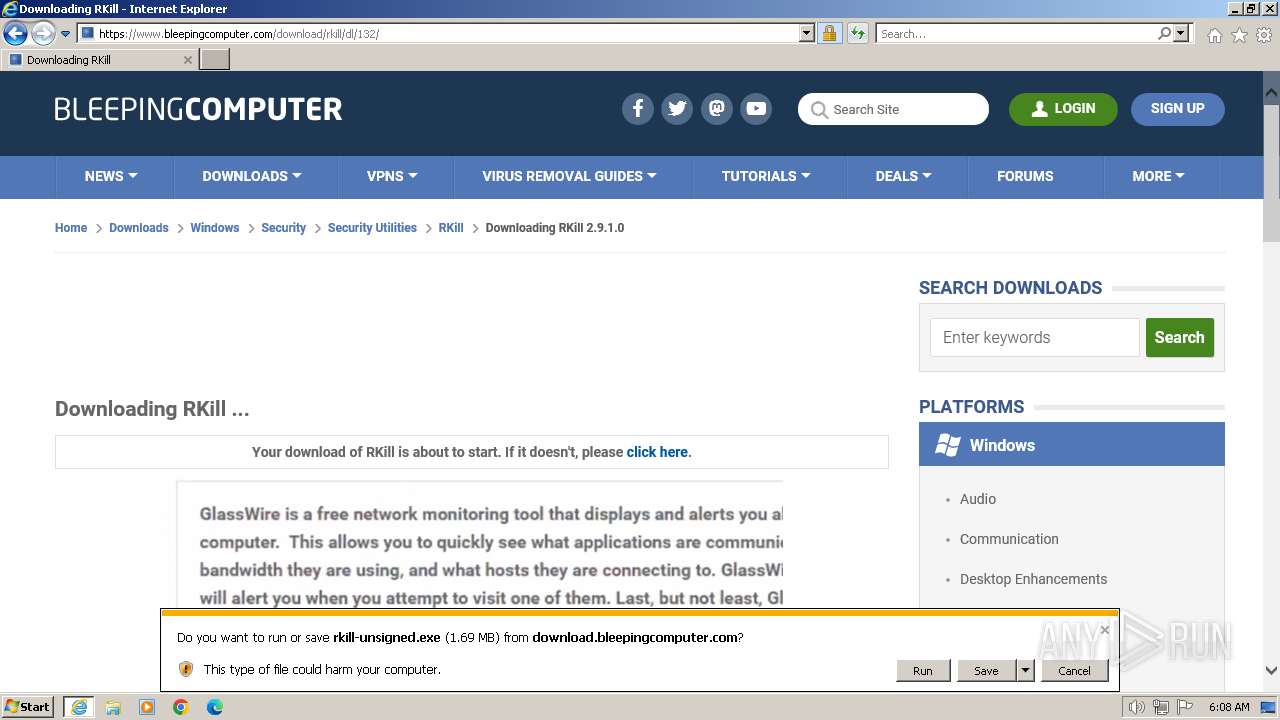
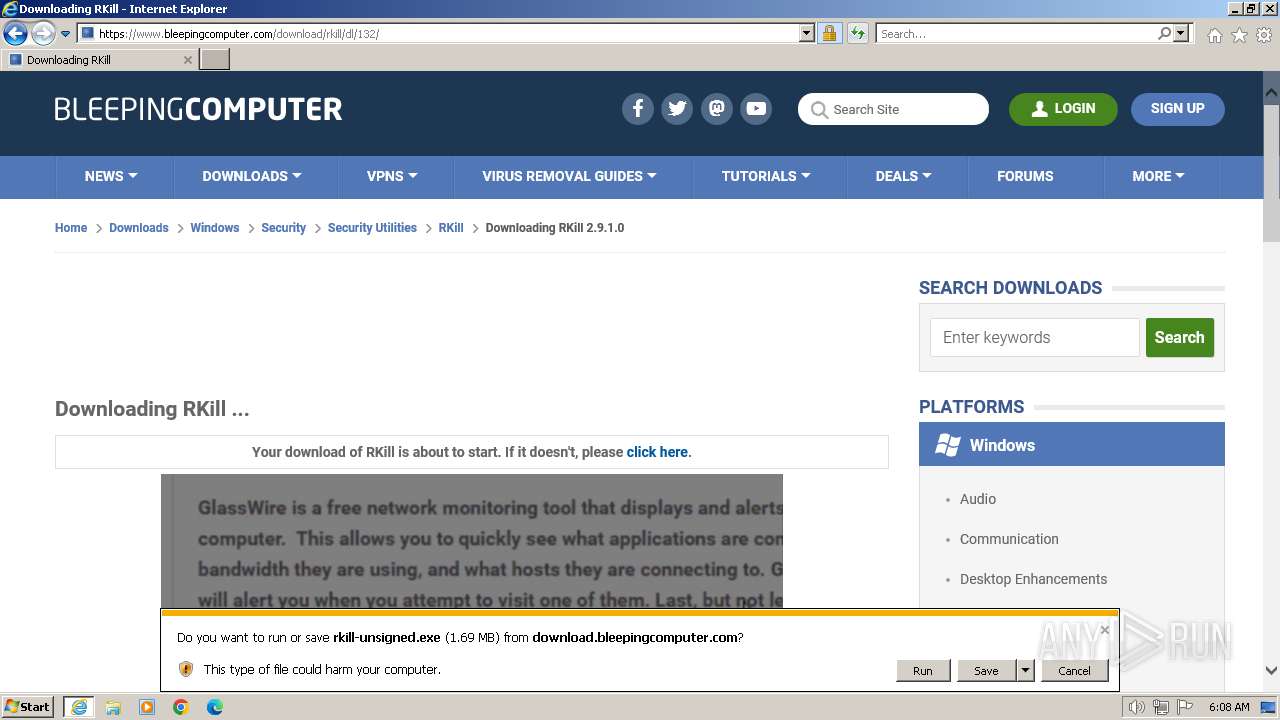
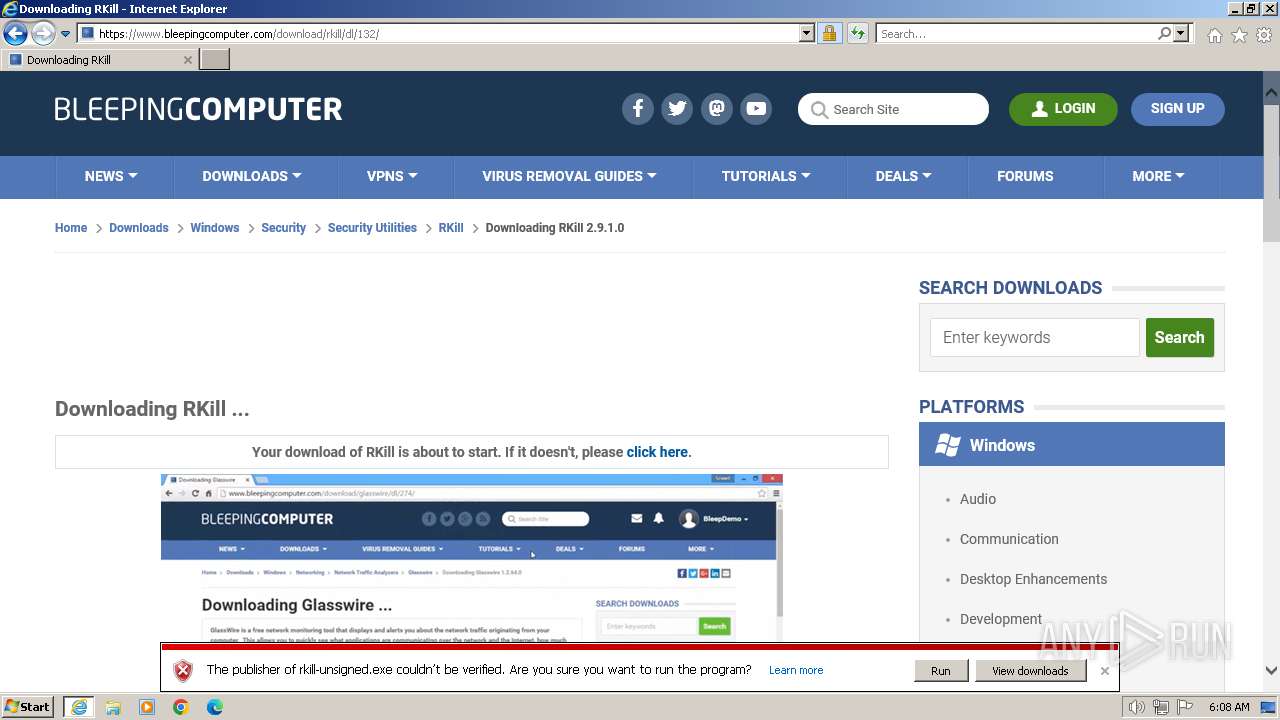
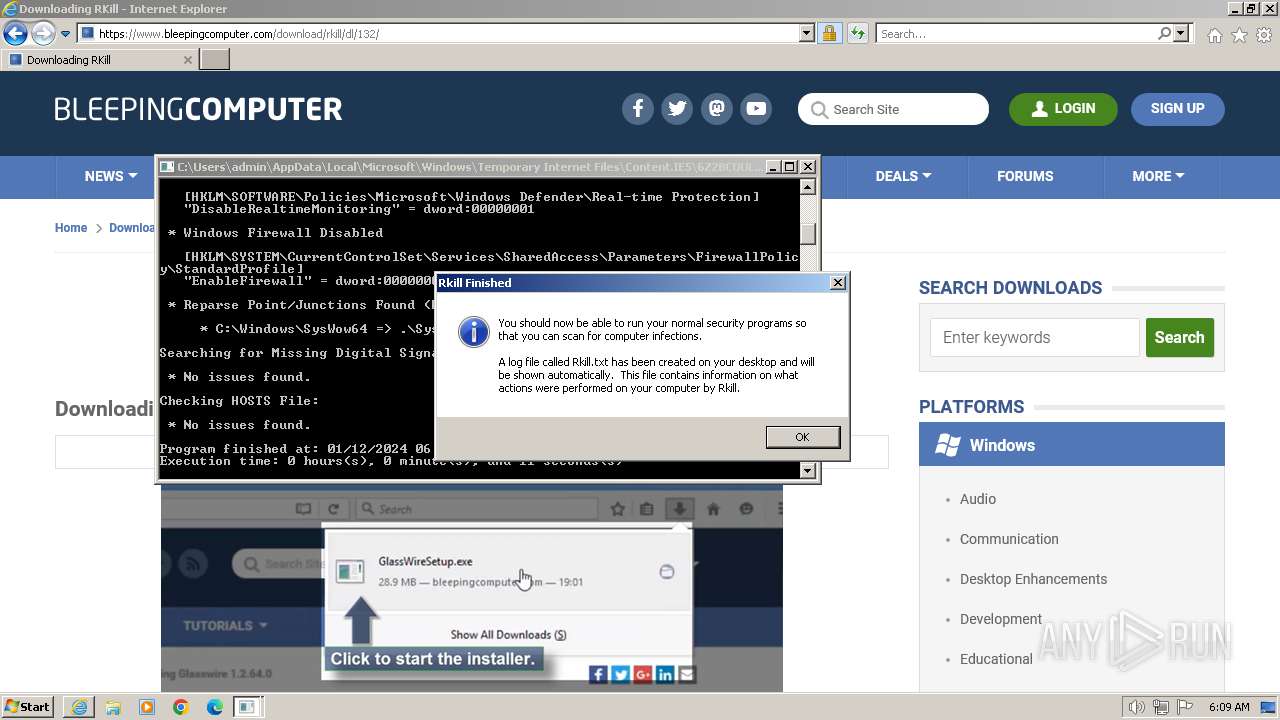
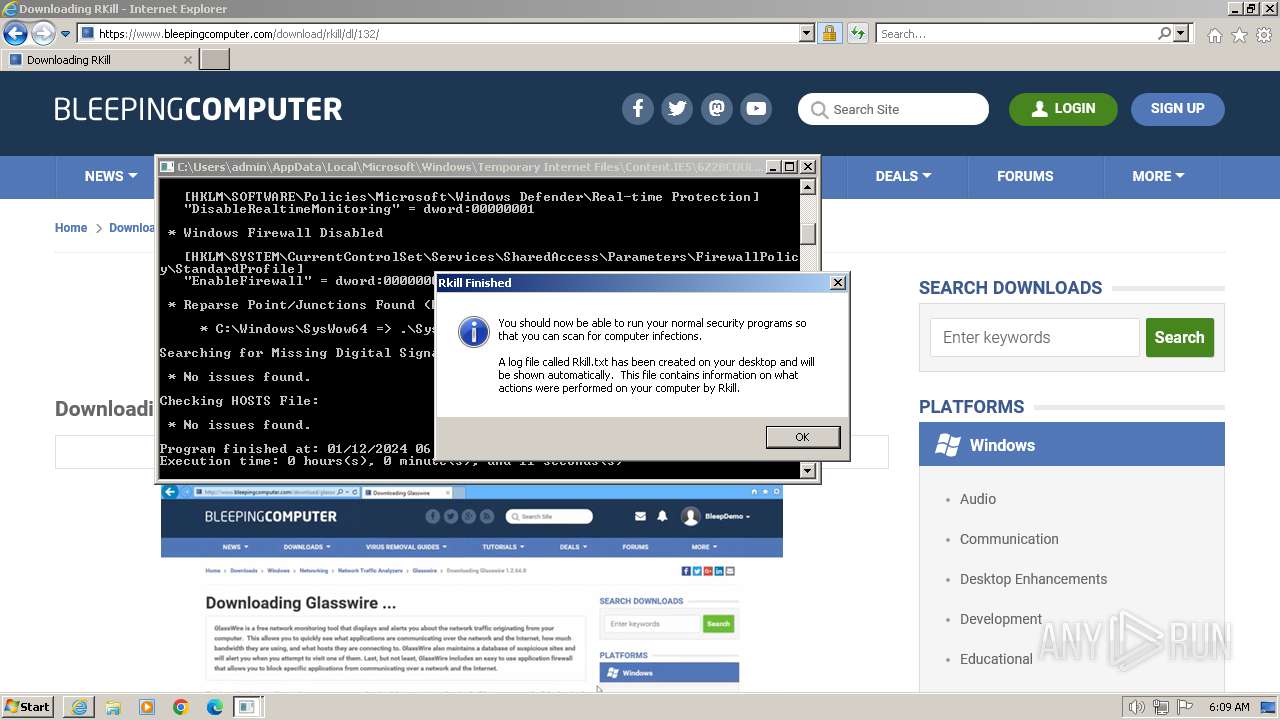
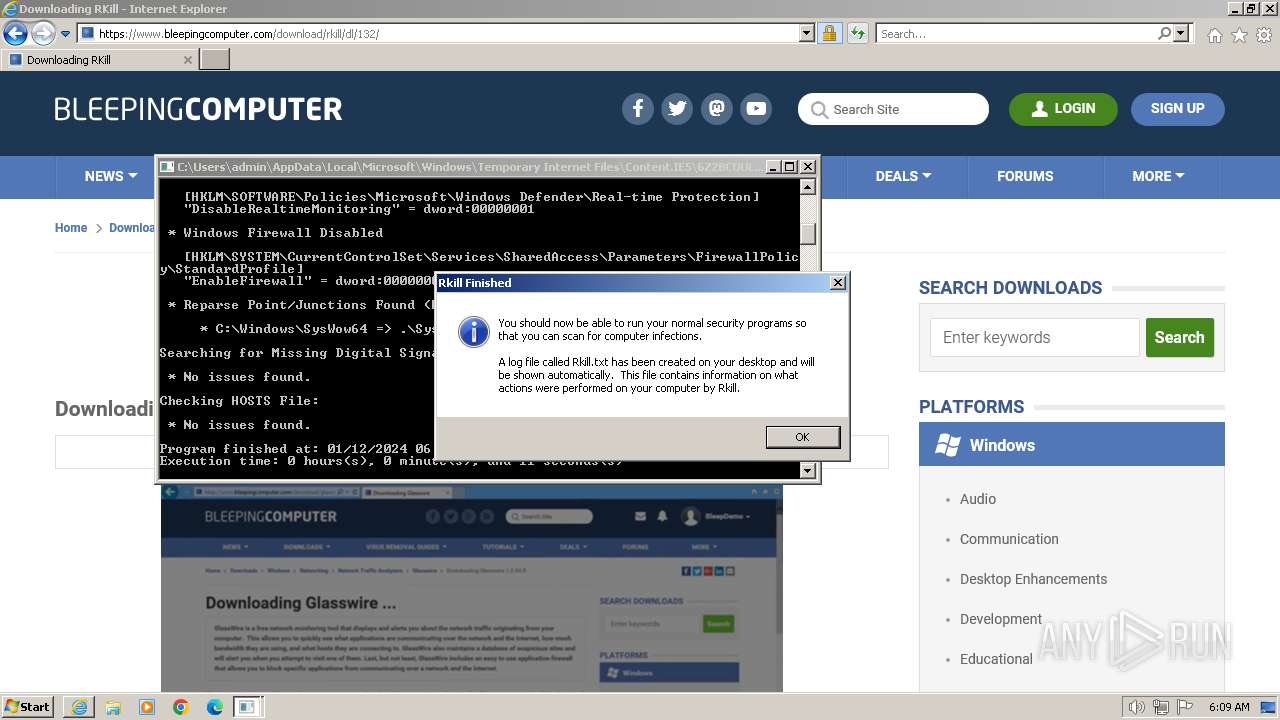
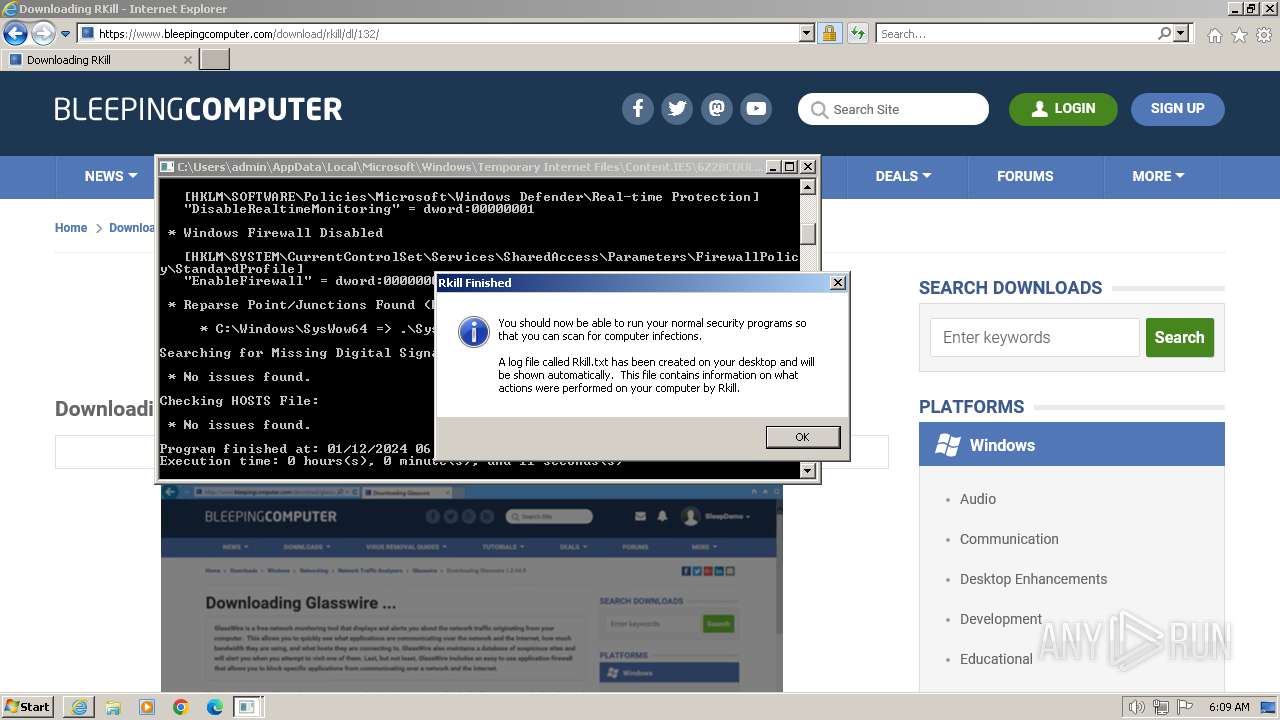
- rkill-unsigned.exe (PID: 2960)
Reads settings of System Certificates
- rkill-unsigned.exe (PID: 2960)
Reads the Internet Settings
- rkill-unsigned.exe (PID: 2960)
Changes default file association
- rkill-unsigned.exe (PID: 2960)
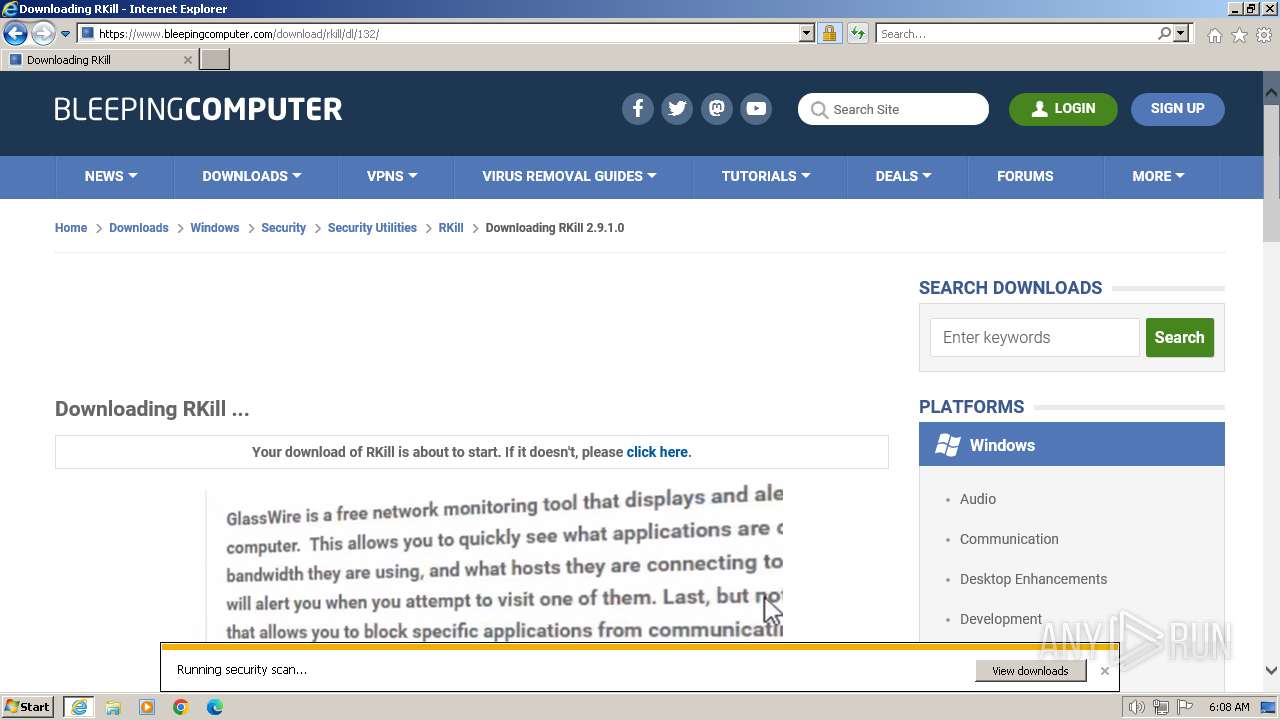
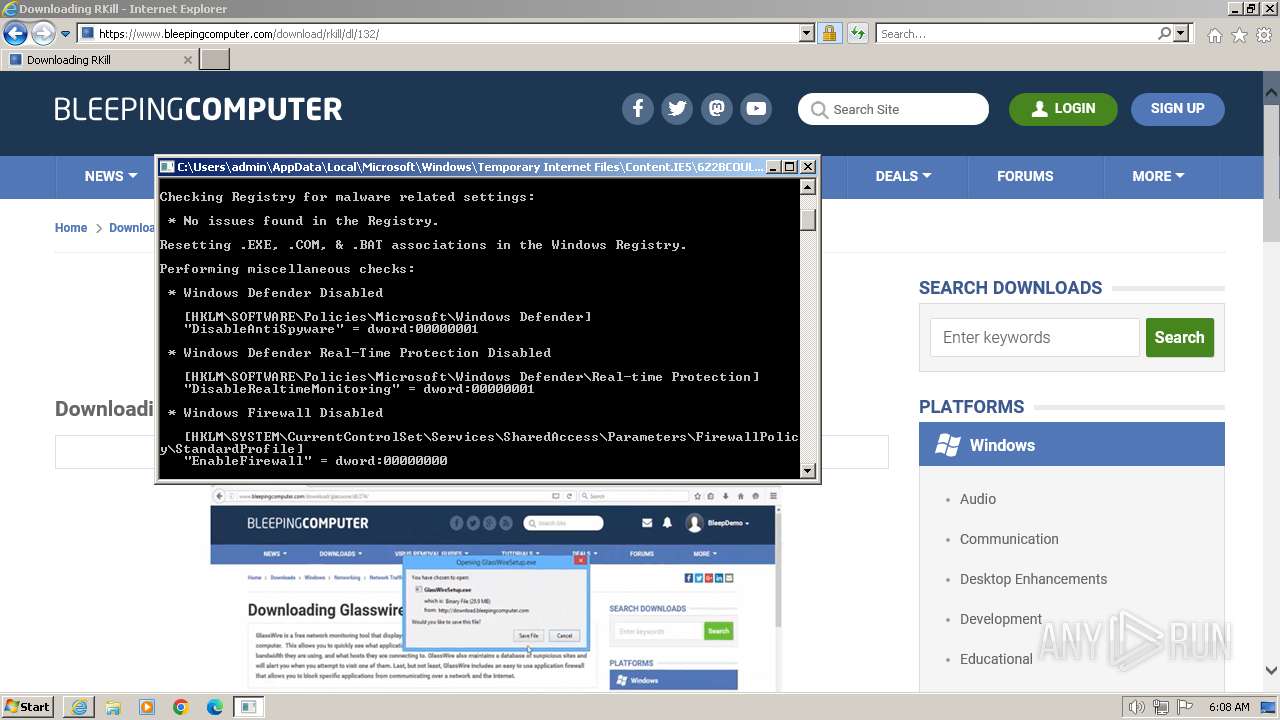
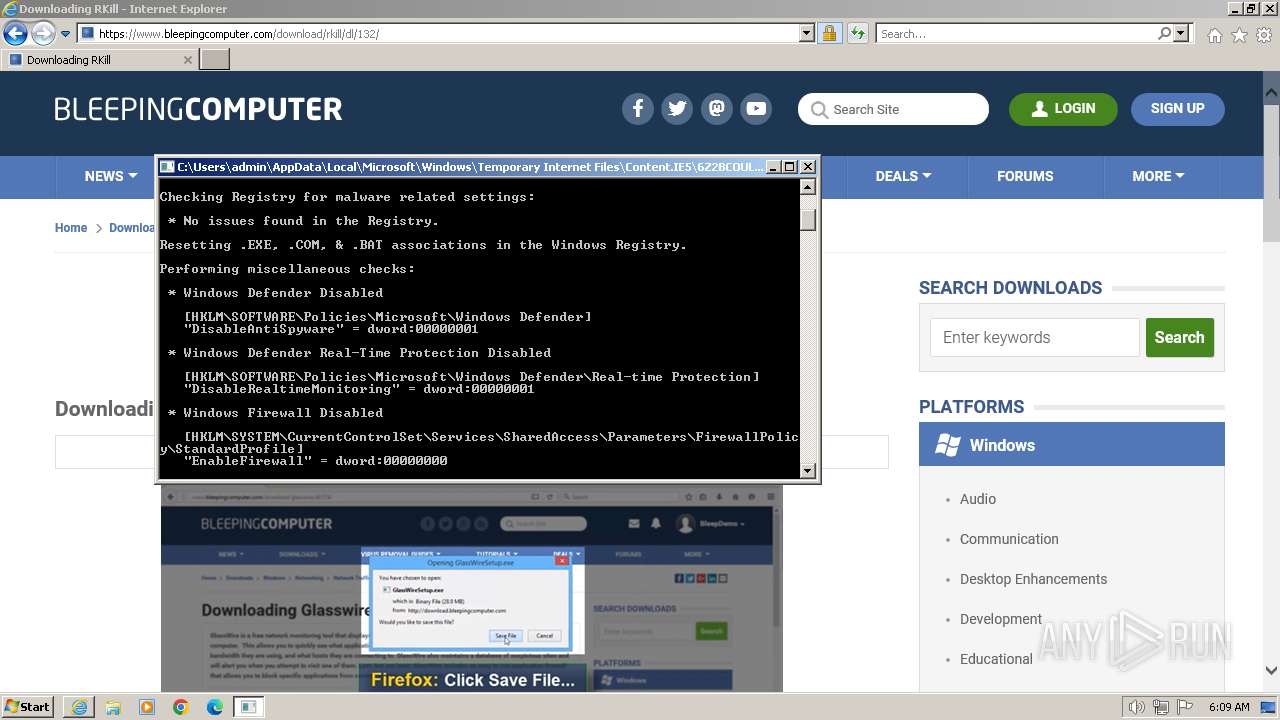
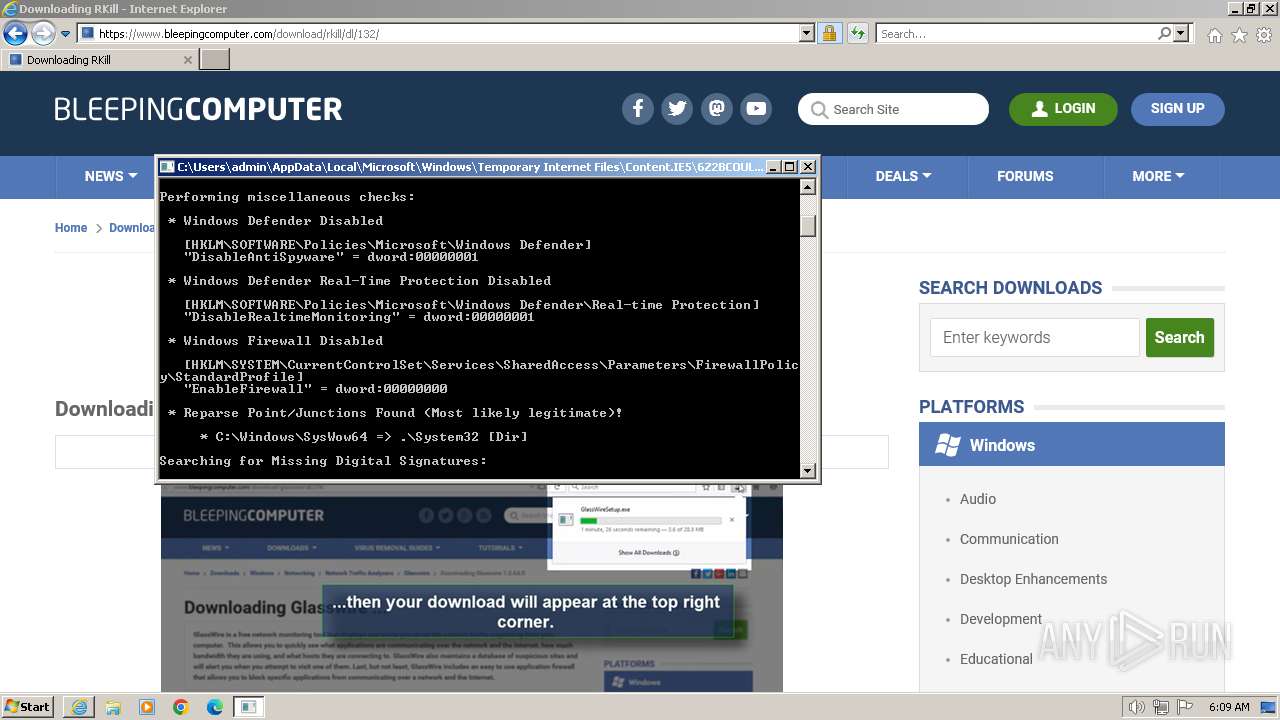
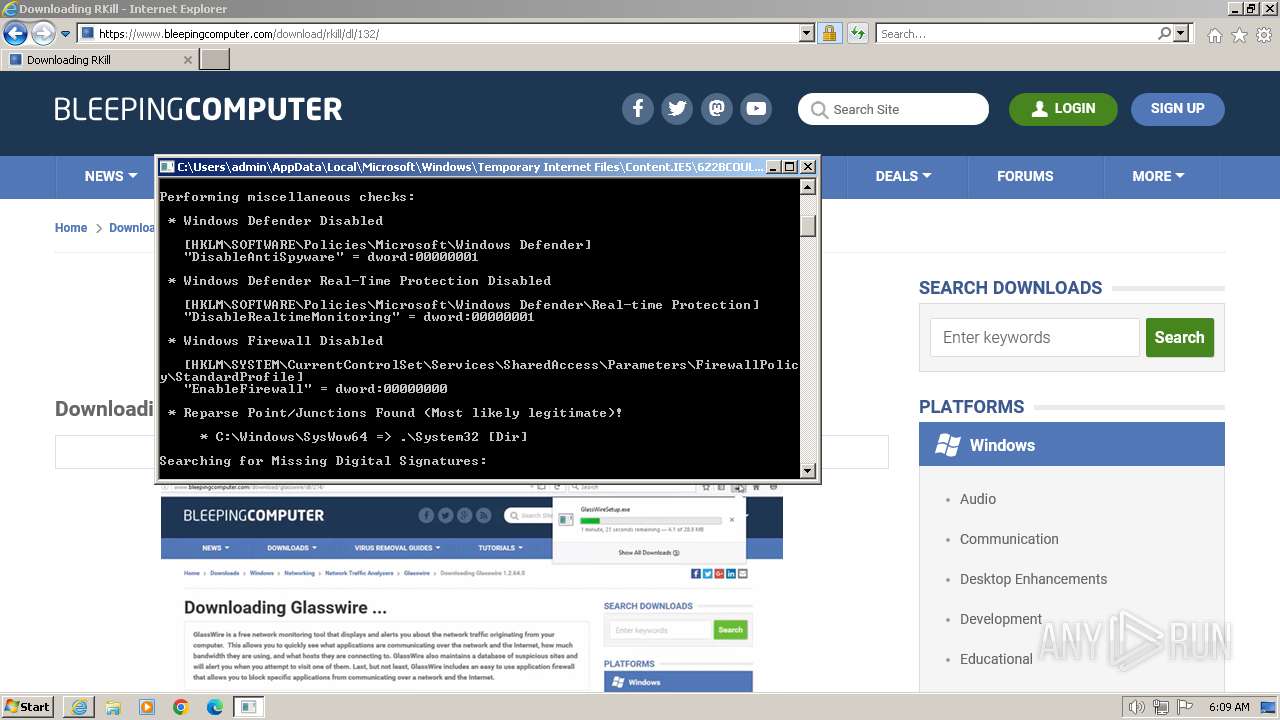
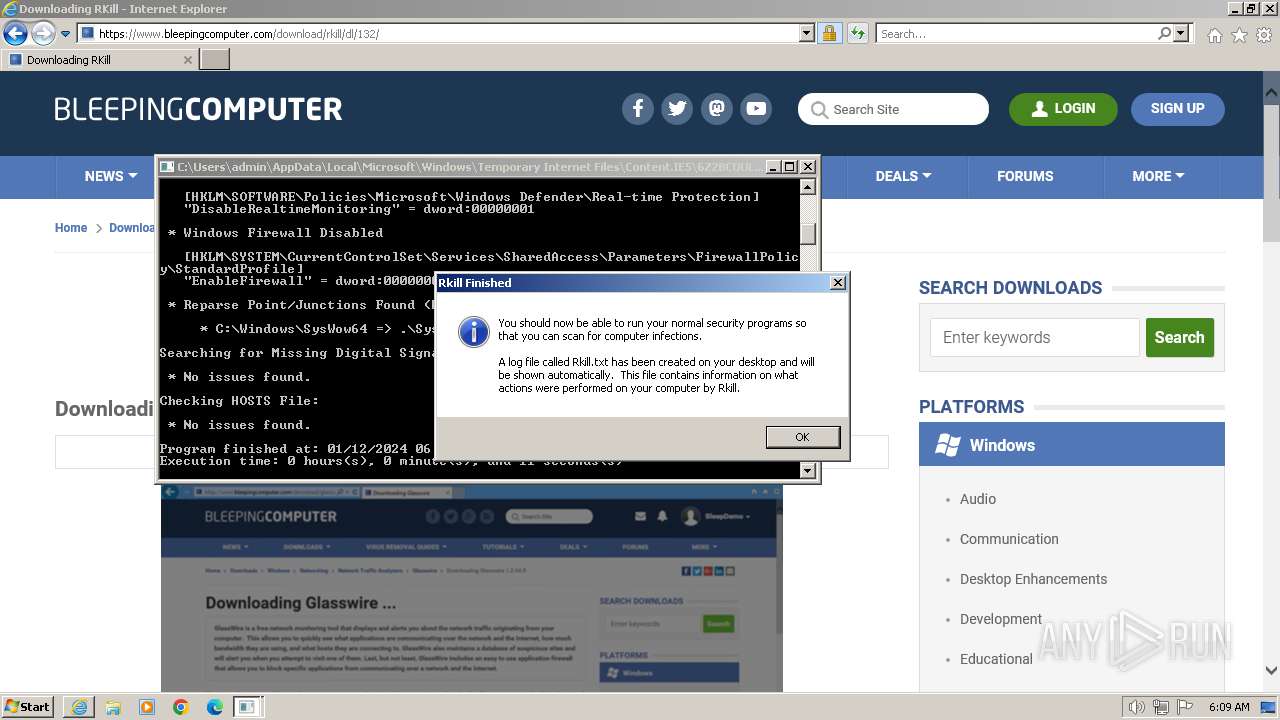
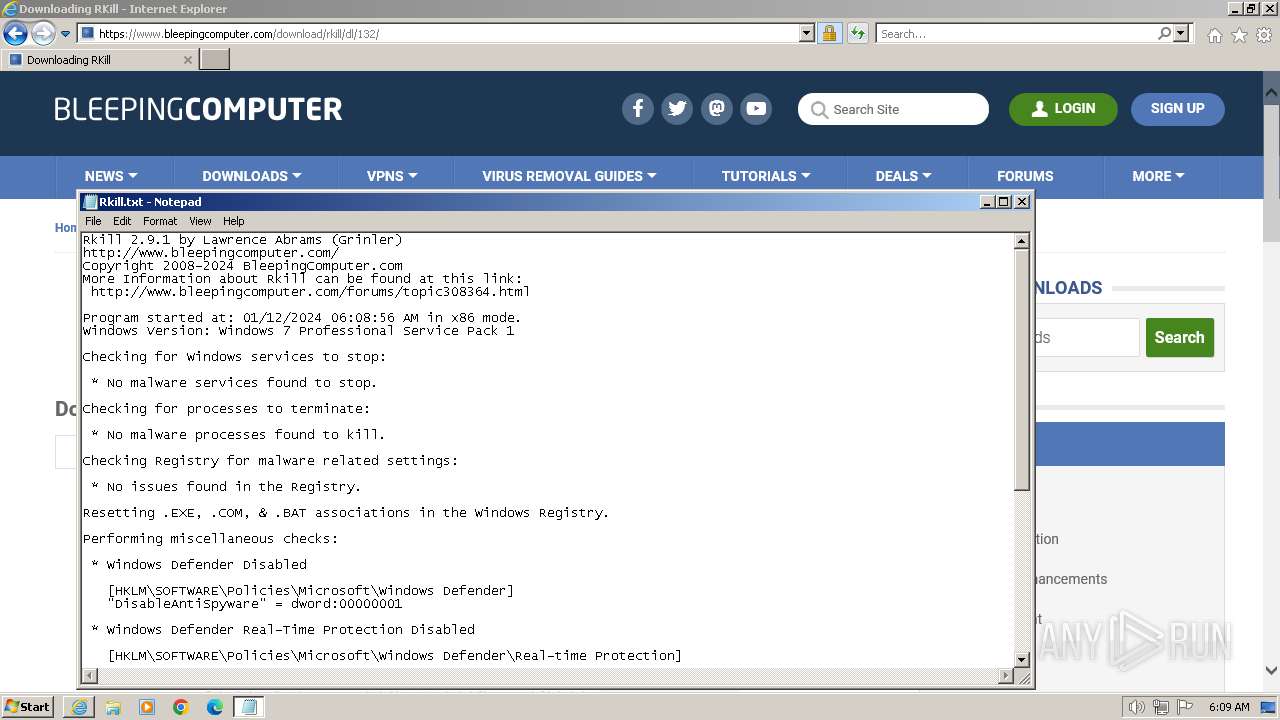
Start notepad (likely ransomware note)
- rkill-unsigned.exe (PID: 2960)
Checks Windows Trust Settings
- rkill-unsigned.exe (PID: 2960)
INFO
Application launched itself
- iexplore.exe (PID: 2124)
- msedge.exe (PID: 2372)
Drops the executable file immediately after the start
- iexplore.exe (PID: 1308)
- iexplore.exe (PID: 2124)
The process uses the downloaded file
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 188)
- iexplore.exe (PID: 2124)
Checks supported languages
- rkill-unsigned.exe (PID: 2960)
Reads product name
- rkill-unsigned.exe (PID: 2960)
Reads Environment values
- rkill-unsigned.exe (PID: 2960)
Reads the computer name
- rkill-unsigned.exe (PID: 2960)
Reads the machine GUID from the registry
- rkill-unsigned.exe (PID: 2960)
Checks proxy server information
- rkill-unsigned.exe (PID: 2960)
Manual execution by a user
- msedge.exe (PID: 2372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
54
Monitored processes
14
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | C:\Windows\system32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe -Embedding | C:\Windows\System32\Macromed\Flash\FlashUtil32_32_0_0_453_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 32.0 r0 Exit code: 0 Version: 32,0,0,453 Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1616 --field-trial-handle=1312,i,15353947571964735514,12191711016762354078,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1308 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2124 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2124 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.bleepingcomputer.com/download/rkill/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
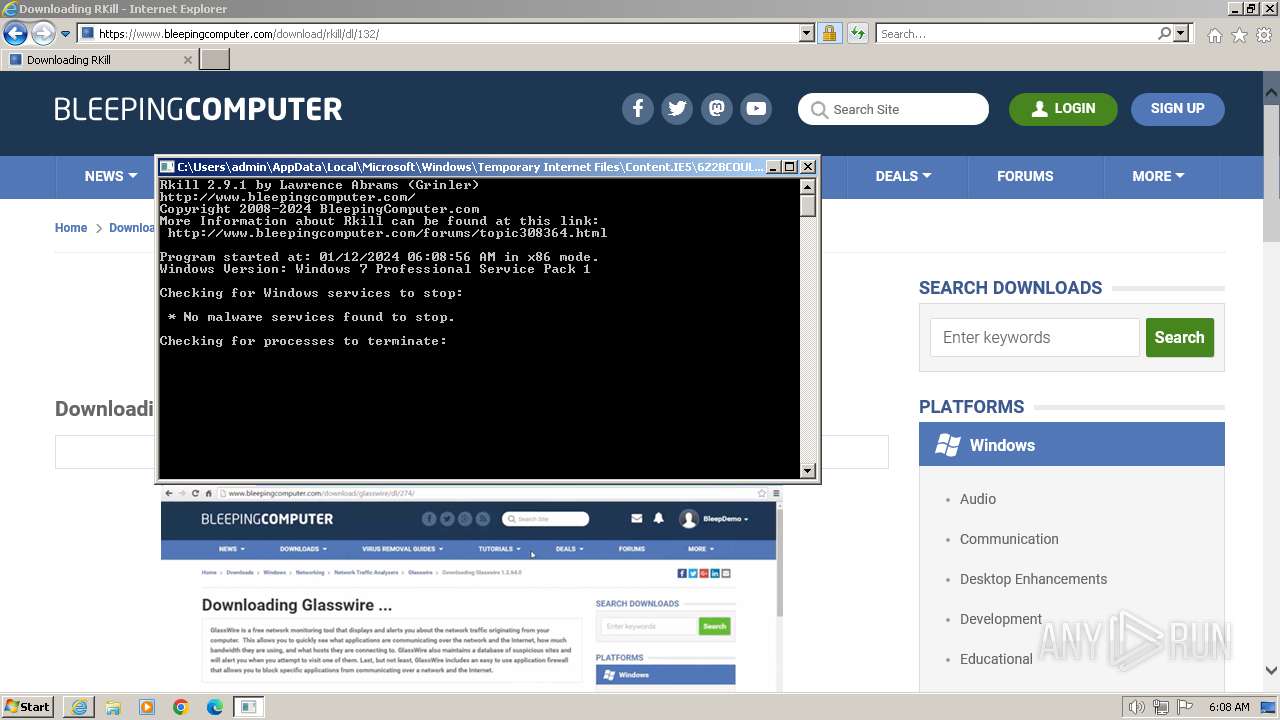
| 2324 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\rkill-unsigned.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\rkill-unsigned.exe | — | iexplore.exe | |||||||||||
User: admin Company: Bleeping Computer, LLC Integrity Level: MEDIUM Description: Terminates malware processes so that you can run your normal security programs. Exit code: 3221226540 Version: 2.9.1 Modules
| |||||||||||||||
| 2372 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" | C:\Program Files\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2460 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2312 --field-trial-handle=1312,i,15353947571964735514,12191711016762354078,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2524 | Notepad.exe C:\Users\admin\Desktop\Rkill.txt | C:\Windows\System32\notepad.exe | — | rkill-unsigned.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2860 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x686bf598,0x686bf5a8,0x686bf5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2944 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1424 --field-trial-handle=1312,i,15353947571964735514,12191711016762354078,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
67 954
Read events
67 831
Write events
121
Delete events
2
Modification events
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
15
Suspicious files
148
Text files
139
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1308 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\rkill[1].htm | html | |
MD5:6582AA452865725C1D94420869FC34BF | SHA256:96AC698EDF329F20D82AF856F7C286A2329BBA2C7EDD8F6B36653D8BE544D507 | |||
| 1308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | der | |
MD5:6DF4B06A2B6A15932B5C7868FEC2B4E3 | SHA256:1BC4686BEAA67FF6E2A285CA18BEC0E7DEE6E82D156E634C658A832FE8BDAD39 | |||
| 1308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:43A3D0EBCF73F7A52D5ED8A1E5579592 | SHA256:05F5D5EF17028B4F1DBEA4307D5BA8BC8231560A965B82E046A3D45B2DC5FB48 | |||
| 1308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | der | |
MD5:6CE814673E9AE499631E7DBEA248E0F1 | SHA256:A215ED43A730CA12B6C7926AFF876DB551B4B8B74E2B4C7FD8526CA1C591151E | |||
| 1308 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\C4XYTWOR.txt | text | |
MD5:1AC529707D161BB41BA7B17BFF52C641 | SHA256:CBB8994285DA81E05AE67A7C7F236884FDCAC48BE17BF0246EB3F748AF1083A6 | |||
| 1308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:7D263AB01F75F82474E9E546D3F5747B | SHA256:4DCDFBF686EBC1FF3A0BF6D8CFFBA73406830ED5B80561474929D3F0F349ADDD | |||
| 1308 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\jquery-3.5.1.min[1].js | text | |
MD5:DC5E7F18C8D36AC1D3D4753A87C98D0A | SHA256:F7F6A5894F1D19DDAD6FA392B2ECE2C5E578CBF7DA4EA805B6885EB6985B6E3D | |||
| 1308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:C834811DAFC6D0418E59682FE188313F | SHA256:24F0153499CD06692ACFFA2E0483AB7EE4086A3893A6557268E20A424F71D3C6 | |||
| 1308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:E700CFB01196F803AAEF294235D461A1 | SHA256:316D0D66FF065E2D39FAE5FADB15575A70E082C111F6D6C0A1A6261BF285B684 | |||
| 1308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:E4DB82AB77B9010DB8301893112D4C69 | SHA256:DFB156027F0239F9DF58D677E44368307F15635AC6FB20B10AD109A43D79D7A6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
121
DNS requests
92
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1308 | iexplore.exe | GET | 200 | 23.53.40.40:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6b21170b0e7a1648 | unknown | compressed | 4.66 Kb | unknown |
1308 | iexplore.exe | GET | 200 | 23.53.40.40:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?53bfb7cf8a6cf97e | unknown | compressed | 4.66 Kb | unknown |
1308 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | binary | 1.42 Kb | unknown |
1308 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | binary | 2.18 Kb | unknown |
1308 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
1308 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
1308 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
1308 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCECbzjAowsPTyEMLulIc7EGw%3D | unknown | binary | 471 b | unknown |
1308 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCECO0Y37WzHRLPzhV9vNju | unknown | binary | 472 b | unknown |
1308 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQD7vSzSbK8Z0QnHSrEZ7mPf | unknown | binary | 472 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1308 | iexplore.exe | 104.20.59.209:443 | www.bleepingcomputer.com | CLOUDFLARENET | — | shared |
1308 | iexplore.exe | 23.53.40.40:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1308 | iexplore.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
1308 | iexplore.exe | 142.250.186.170:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
1308 | iexplore.exe | 172.67.75.139:443 | www.bleepstatic.com | CLOUDFLARENET | US | unknown |
1308 | iexplore.exe | 104.18.20.206:443 | a.pub.network | CLOUDFLARENET | — | unknown |
1308 | iexplore.exe | 142.250.184.196:443 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bleepingcomputer.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.bleepstatic.com |
| whitelisted |
a.pub.network |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
www.google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |