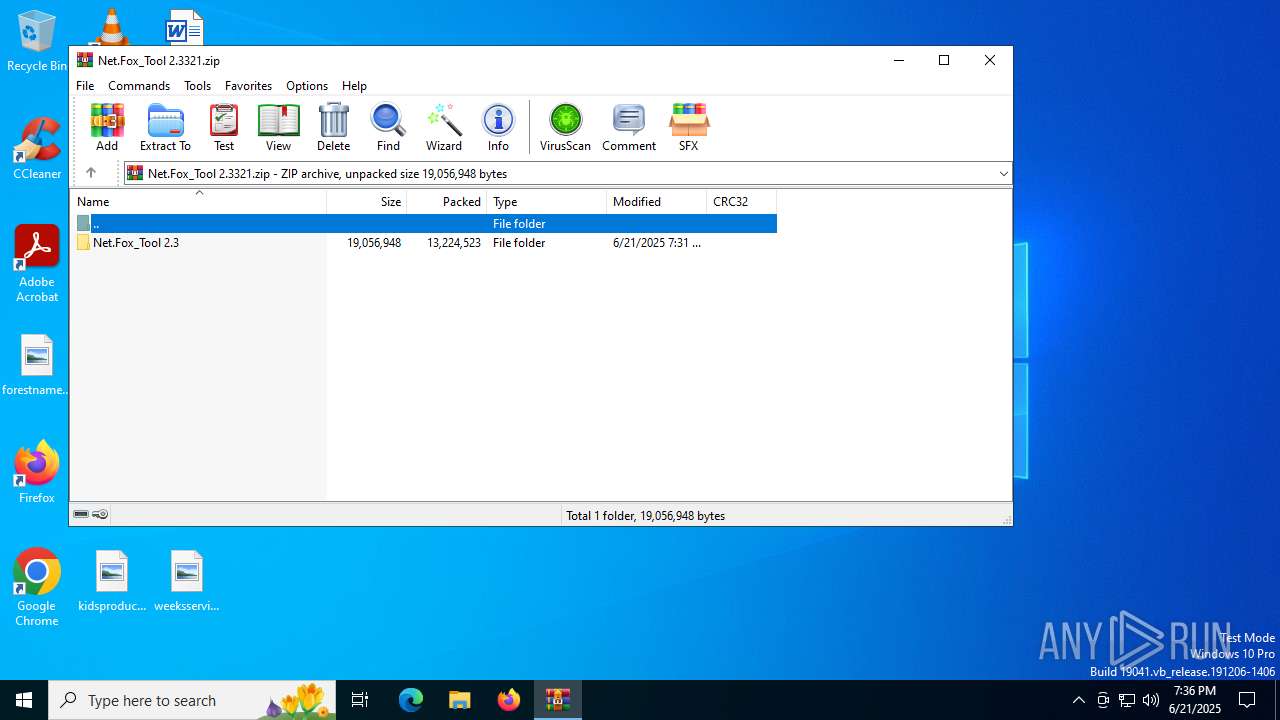
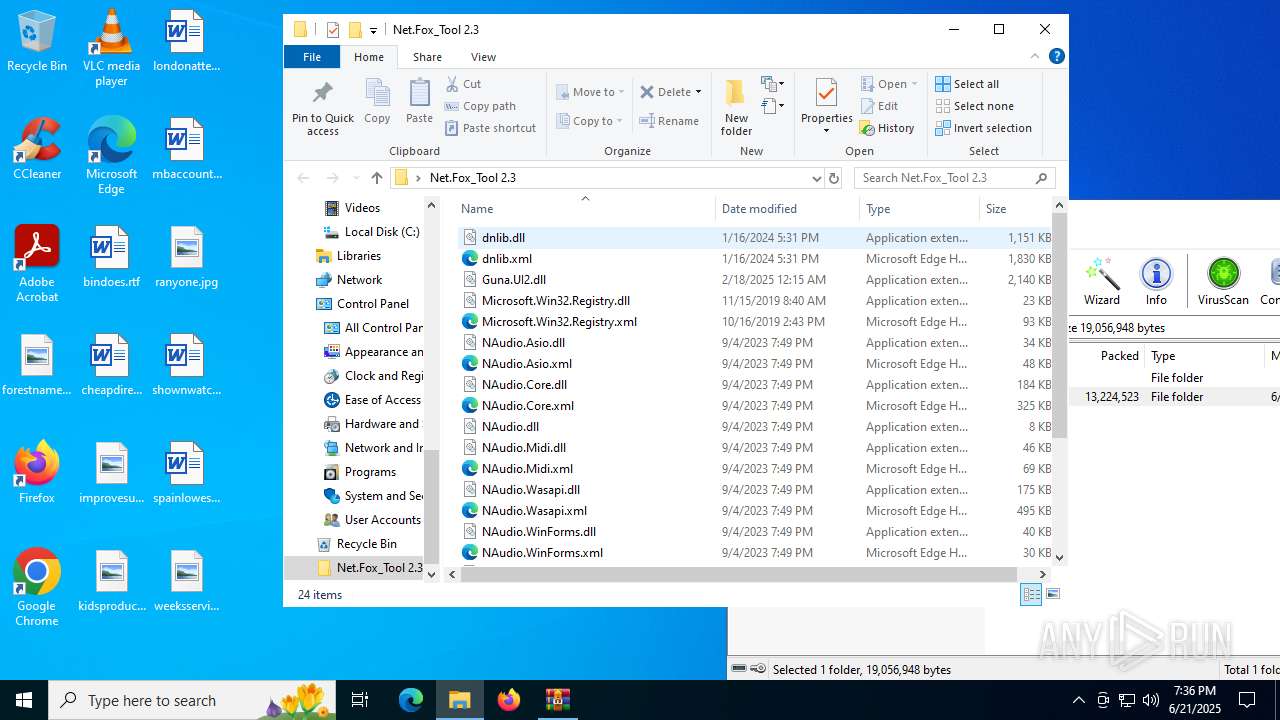
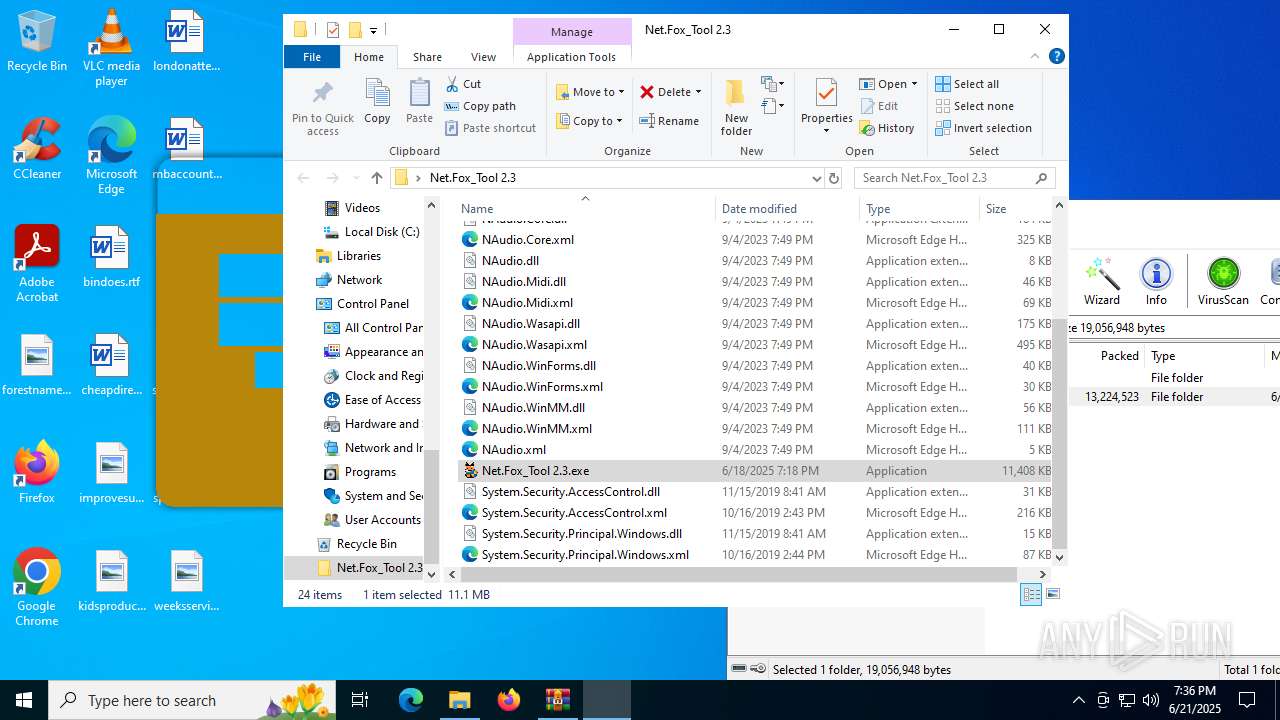
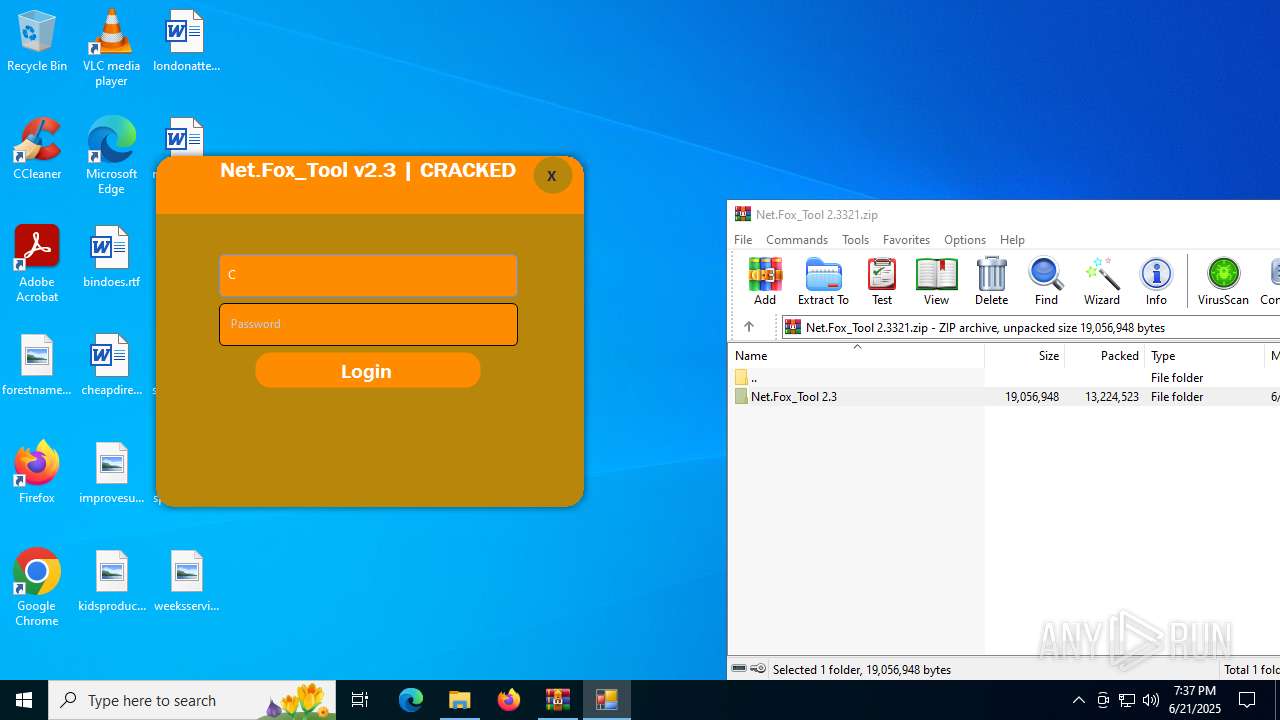
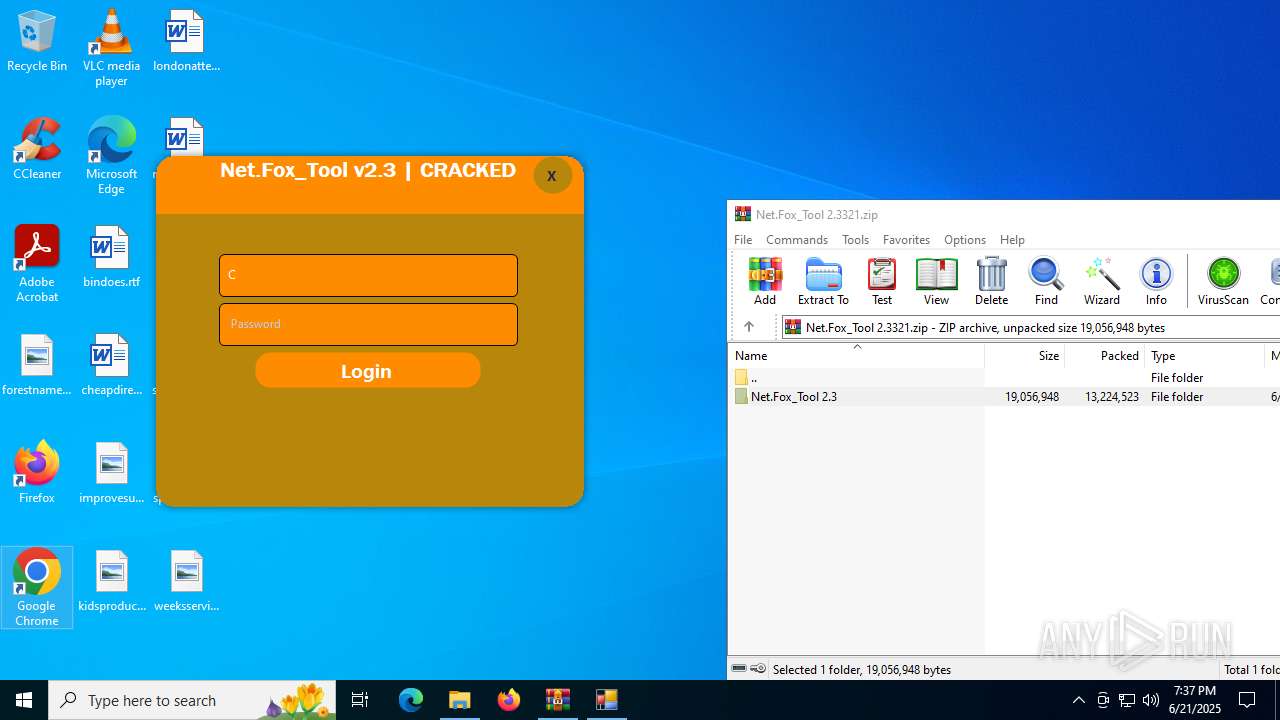
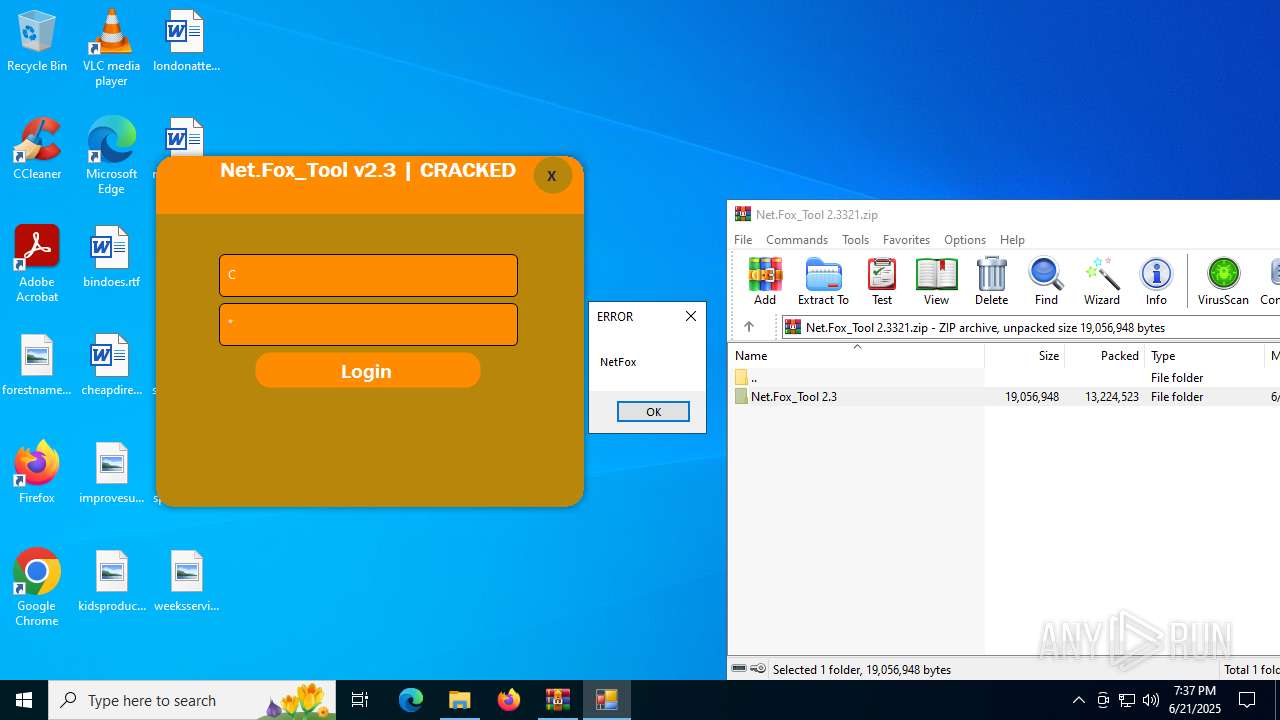
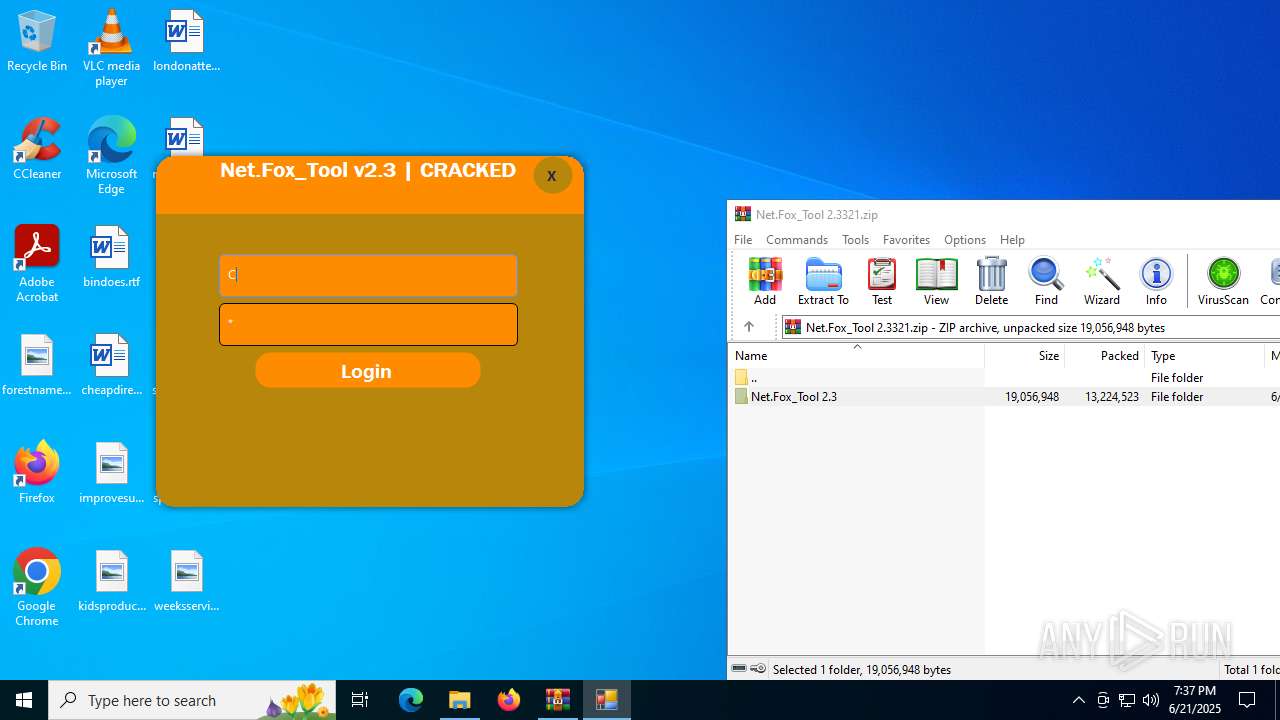
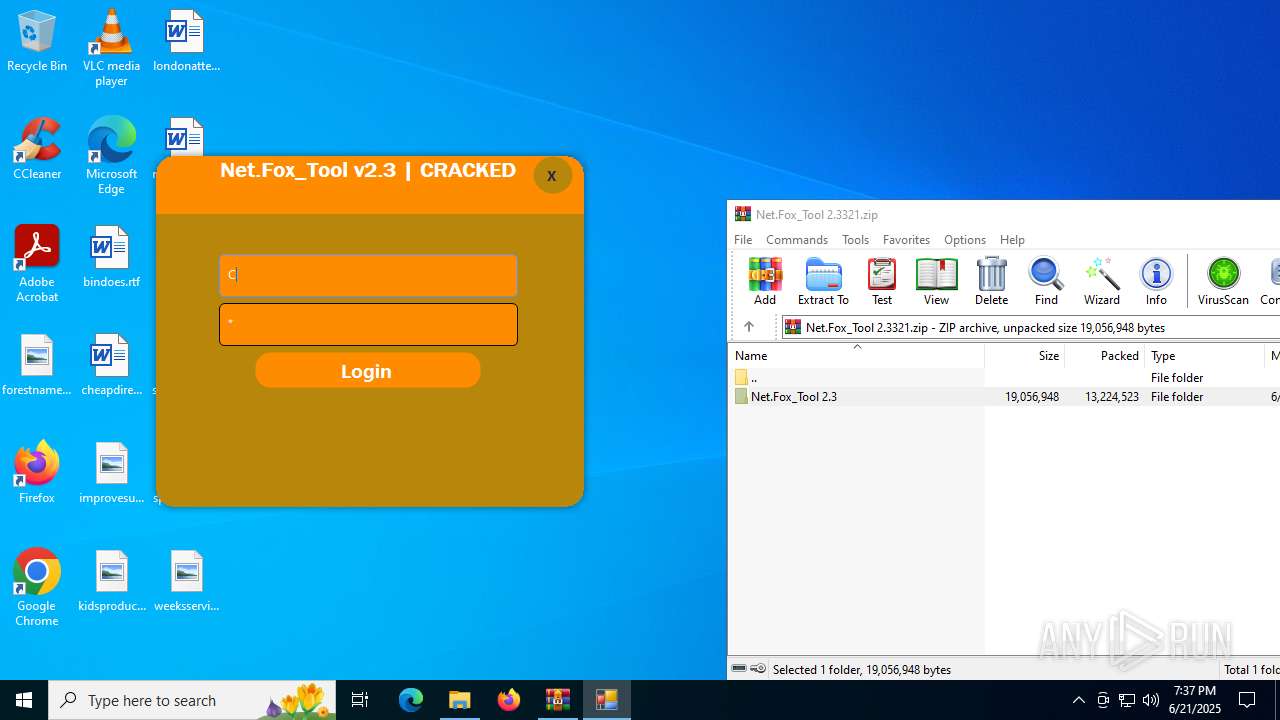
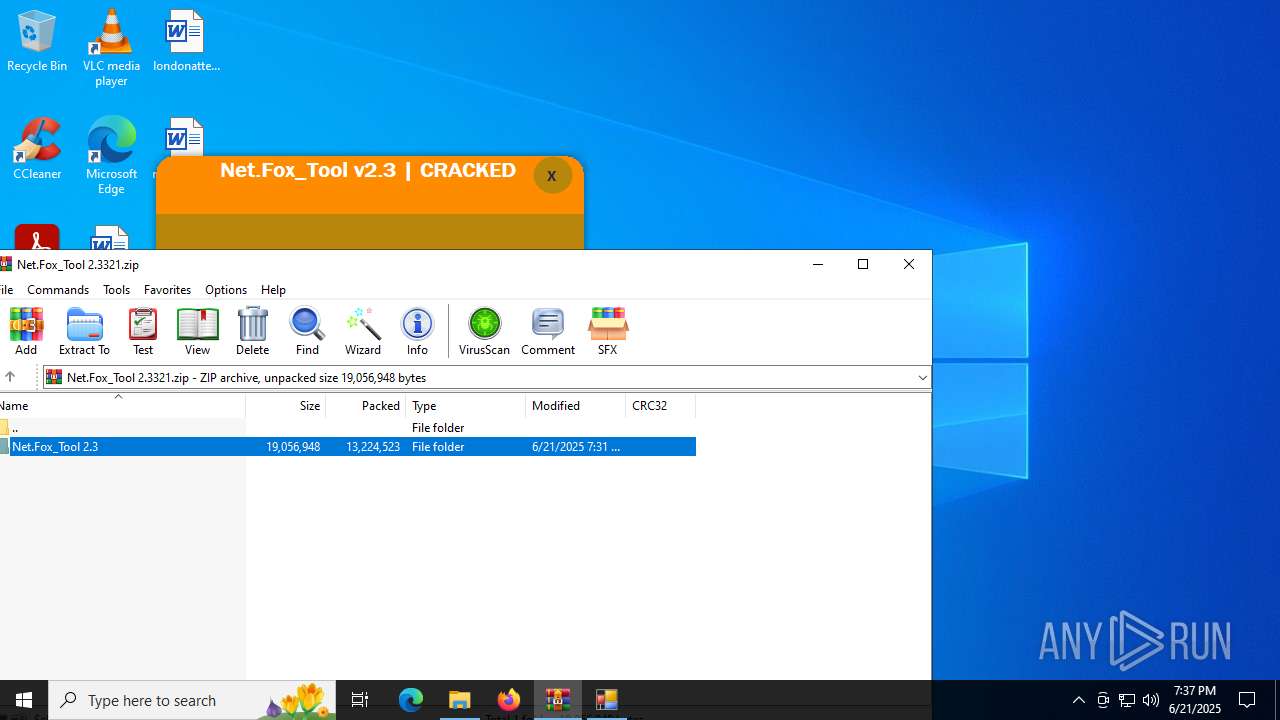
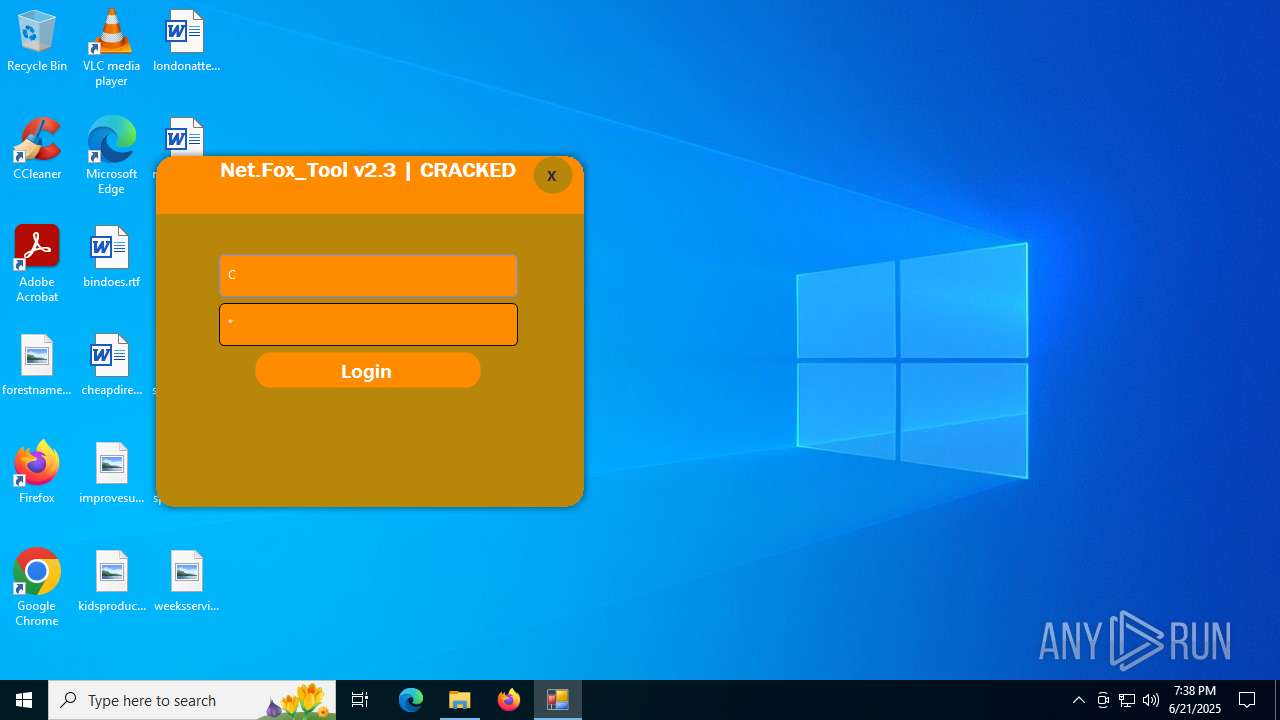
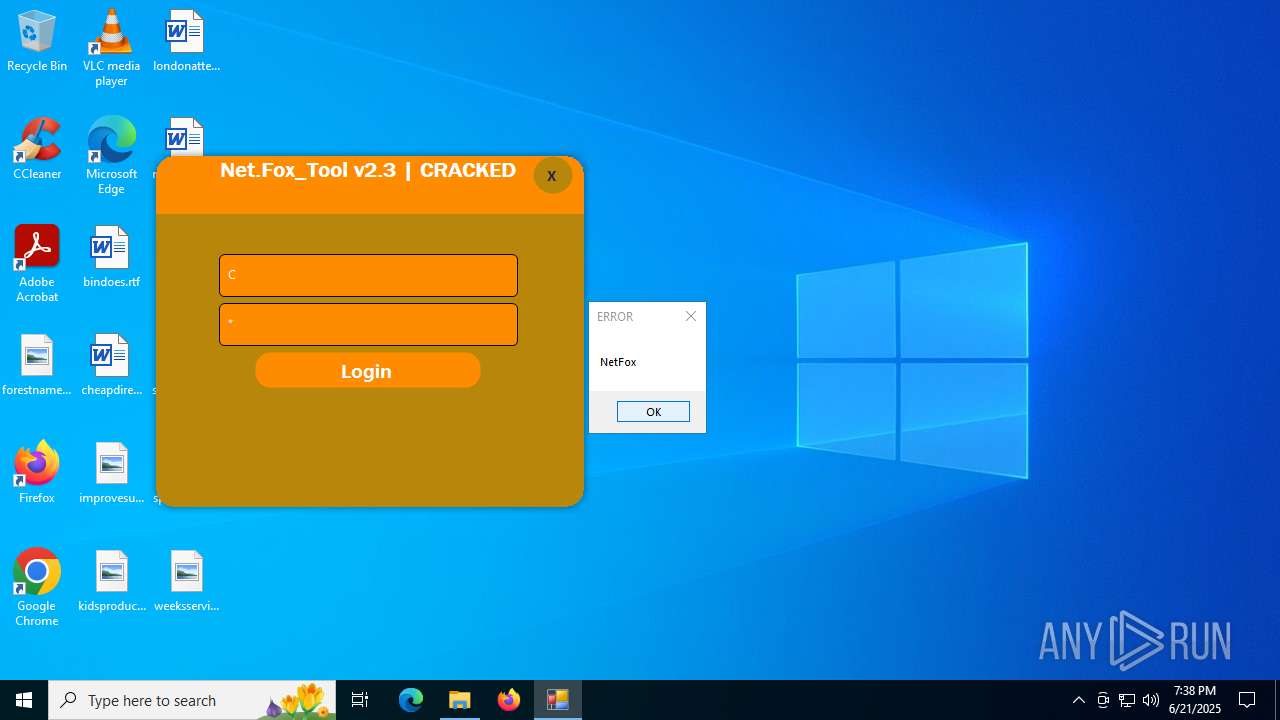
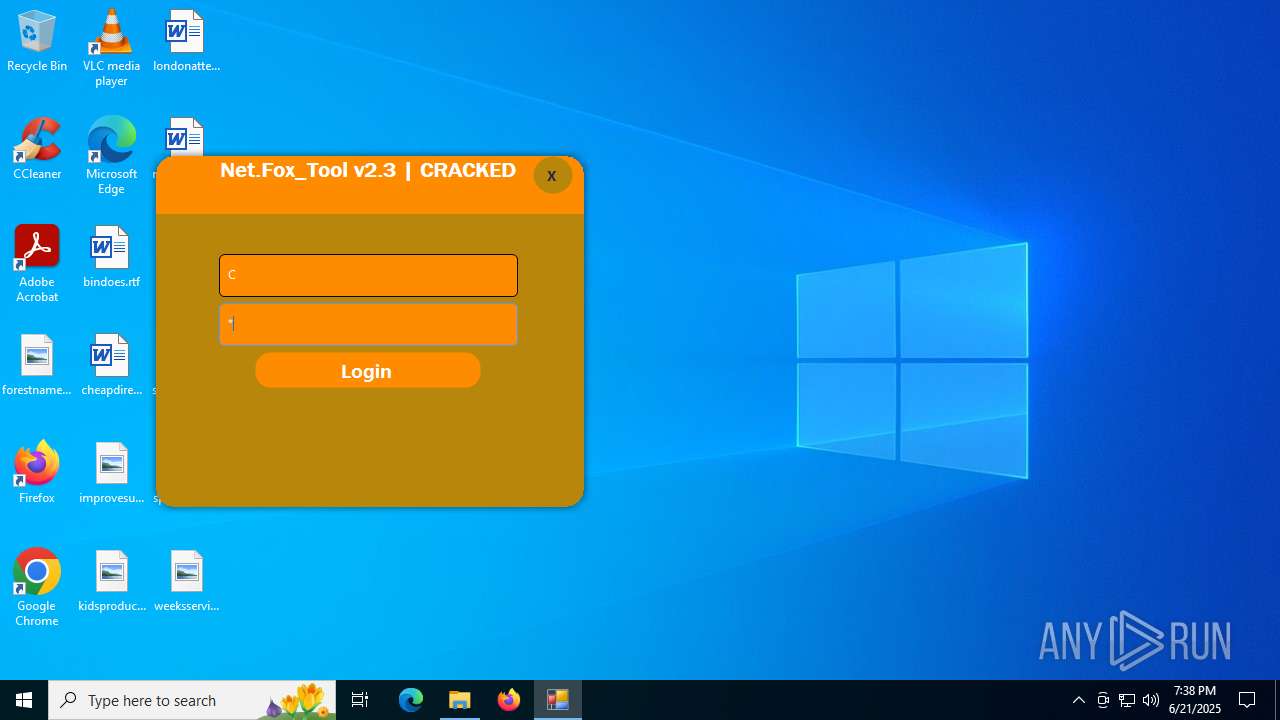
| File name: | Net.Fox_Tool 2.3321.zip |
| Full analysis: | https://app.any.run/tasks/02e397f7-8bef-4985-b2e2-e88889219e2e |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 19:36:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 82E5B7D48ACB952BB729BECD13A62622 |
| SHA1: | D188521755222540F13E3515A942FC81E4A218F9 |
| SHA256: | 3B3EC10756AFFE8813EEBF7C295C0DEDFCD2180ACA12198C8F3D1048D26AF999 |
| SSDEEP: | 98304:Y7pg9/wmMWlwGX5f0XD190qfF7EcHhTiYxtfaNgGSSqN3dV9bYa9Mdvs91Rp1CRv:yg+1yXu8ZLA0aKdpLHqGrzxWcAsURgxL |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3656)
Executable content was dropped or overwritten
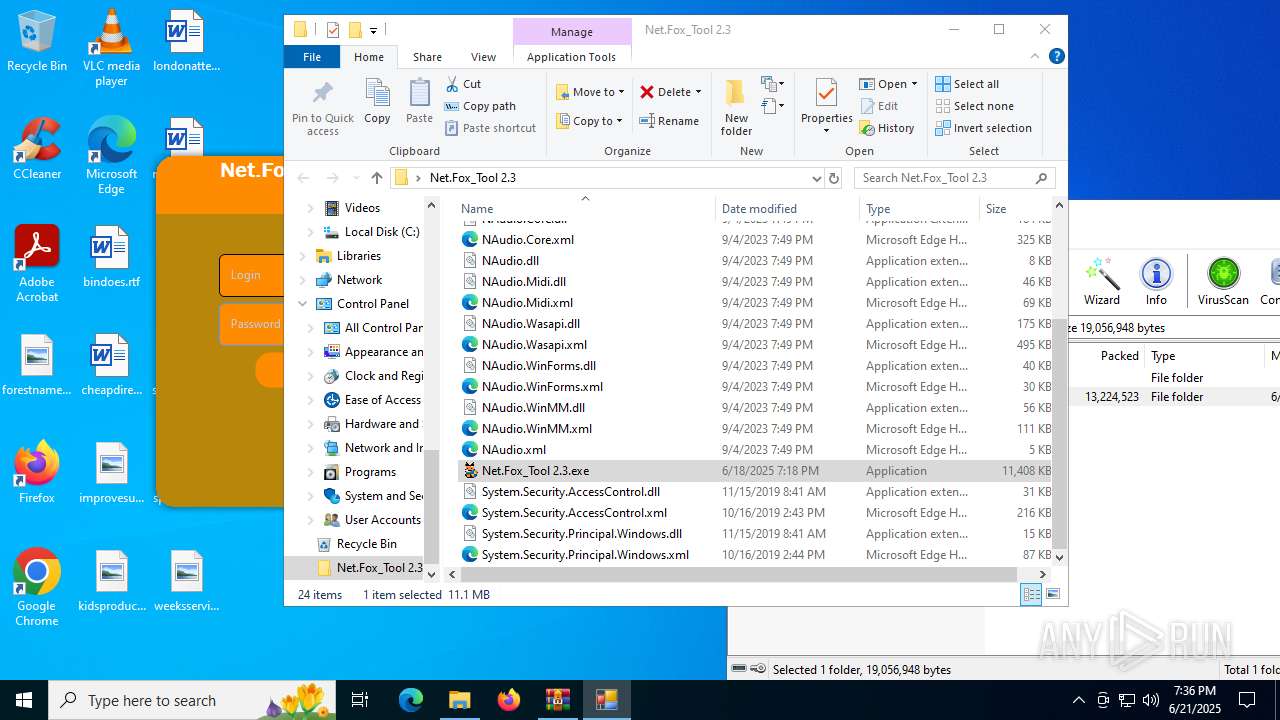
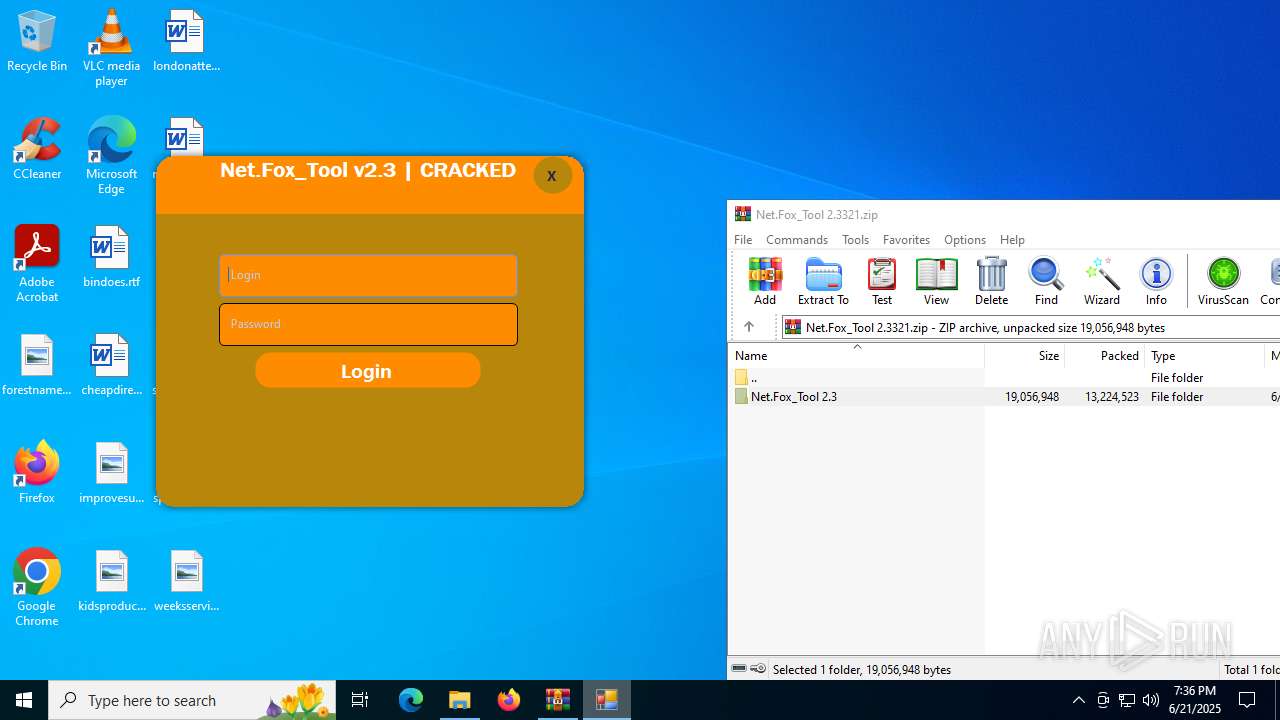
- Net.Fox_Tool 2.3.exe (PID: 984)
Reads the BIOS version
- Net.Fox_Tool 2.3.exe (PID: 984)
Reads security settings of Internet Explorer
- Net.Fox_Tool 2.3.exe (PID: 984)
There is functionality for taking screenshot (YARA)
- Net.Fox_Tool 2.3.exe (PID: 984)
INFO
Manual execution by a user
- Net.Fox_Tool 2.3.exe (PID: 5400)
- Net.Fox_Tool 2.3.exe (PID: 984)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3656)
Reads the computer name
- Net.Fox_Tool 2.3.exe (PID: 984)
Create files in a temporary directory
- Net.Fox_Tool 2.3.exe (PID: 984)
Process checks whether UAC notifications are on
- Net.Fox_Tool 2.3.exe (PID: 984)
Reads the software policy settings
- Net.Fox_Tool 2.3.exe (PID: 984)
- slui.exe (PID: 2716)
Checks proxy server information
- Net.Fox_Tool 2.3.exe (PID: 984)
- slui.exe (PID: 2716)
Reads the machine GUID from the registry
- Net.Fox_Tool 2.3.exe (PID: 984)
Checks supported languages
- Net.Fox_Tool 2.3.exe (PID: 984)
Themida protector has been detected
- Net.Fox_Tool 2.3.exe (PID: 984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:06:22 04:31:12 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Net.Fox_Tool 2.3/ |
Total processes
139
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 984 | "C:\Users\admin\Desktop\Net.Fox_Tool 2.3\Net.Fox_Tool 2.3.exe" | C:\Users\admin\Desktop\Net.Fox_Tool 2.3\Net.Fox_Tool 2.3.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: NETFOXEXPLOIT2.3 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2716 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3100 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3656 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Net.Fox_Tool 2.3321.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5400 | "C:\Users\admin\Desktop\Net.Fox_Tool 2.3\Net.Fox_Tool 2.3.exe" | C:\Users\admin\Desktop\Net.Fox_Tool 2.3\Net.Fox_Tool 2.3.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: NETFOXEXPLOIT2.3 Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
8 844
Read events
8 824
Write events
20
Delete events
0
Modification events
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Net.Fox_Tool 2.3321.zip | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
14
Suspicious files
4
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3656.40847\Net.Fox_Tool 2.3\NAudio.Asio.xml | xml | |
MD5:C416A46EE20410C9989A5145F33BFD0E | SHA256:79C97FFAFC1860285CD19CAFE104C9AD4739D8CA5958575DE4C6995A5A531B3D | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3656.40847\Net.Fox_Tool 2.3\NAudio.WinMM.dll | executable | |
MD5:FAF1BA532964984A34D60674FBC7A5A7 | SHA256:749A01EBBB5EDD8B1A03C5263B04DE6ACADECF52E4CC84D7412BC6E93F180958 | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3656.40847\Net.Fox_Tool 2.3\dnlib.xml | xml | |
MD5:4F66F6D14A67BBD0F70012557D88D17B | SHA256:F453807C0866BDB424541C9297A4C55107143C0103CB84F23D070044F62B7273 | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3656.40847\Net.Fox_Tool 2.3\Microsoft.Win32.Registry.dll | executable | |
MD5:DA40F3DB8B34571684C0CB5BCECD2A79 | SHA256:619737E2AF8FB713085726631DD2E522FE130CAC1D388A59C38907A47D7AADEA | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3656.40847\Net.Fox_Tool 2.3\NAudio.Core.xml | xml | |
MD5:3EC48FA66AB5CF0A3EC350D550957C0C | SHA256:EF3C495408488D648888C1A571B83E858F7CDCB65B7A9B71EE1808B50CC07C4C | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3656.40847\Net.Fox_Tool 2.3\NAudio.Asio.dll | executable | |
MD5:EB254B04D63A9F03B77563243805F68F | SHA256:CA03780217139B37F7F5B6921D59DEFB8D24988315B16B167A77FA88CAA7D00F | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3656.40847\Net.Fox_Tool 2.3\NAudio.Core.dll | executable | |
MD5:48867F392B8E77DC06C062638C6FBD36 | SHA256:FCF493FC47A2F478A65303886B975FBDBF714CBB1F2D79F7FCE97E4BB16B01A8 | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3656.40847\Net.Fox_Tool 2.3\NAudio.Midi.xml | xml | |
MD5:0C57AAD70E5F035FA40B1FE21D755B4D | SHA256:B890AB3831E49FE591F9524FD1EC681CFF0715ABF439312E93ECCBD31DC9FFF4 | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3656.40847\Net.Fox_Tool 2.3\NAudio.Midi.dll | executable | |
MD5:3F5C79100F4F7902114C3FCBA275C606 | SHA256:F246E29921797B173B54229685E997A11F9CC388FA1E589C212328ABD7A94EBE | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3656.40847\Net.Fox_Tool 2.3\NAudio.Wasapi.dll | executable | |
MD5:278EBB79DA14ECF8E0559530C2FDA076 | SHA256:618EF0E49D64E7A66DFE64BBF6AE81705B9D9683D8A9F321E5C3024D666BDF82 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
26
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
984 | Net.Fox_Tool 2.3.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
984 | Net.Fox_Tool 2.3.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3480 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3480 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
4168 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3956 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.55.104.172:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
984 | Net.Fox_Tool 2.3.exe | 23.55.104.172:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
984 | Net.Fox_Tool 2.3.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |