| File name: | 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77 |
| Full analysis: | https://app.any.run/tasks/3319a290-cb30-421a-95b4-57d00d06be47 |
| Verdict: | Malicious activity |
| Analysis date: | March 26, 2025, 02:25:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | 5E2221D2C830ED4B3578CA262A8987D6 |
| SHA1: | FC2D4CCB2B88FD6A1521B5293D4CC7DDAF587BB1 |
| SHA256: | 3B34C6DE5409FDFE08B92F3A1B07A5BA57E52FCD0ADB6511B9466D131E780A77 |
| SSDEEP: | 98304:m5XiuFEA6+gHp3nmajYQfu0MhZ7TuELTo7Yjsbs6GzGA3Wk6dVcB36HpcOWWHl91:72E9 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe (PID: 7300)
Reads security settings of Internet Explorer
- 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe (PID: 7300)
- ShellExperienceHost.exe (PID: 1188)
Process drops legitimate windows executable
- 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe (PID: 7300)
Reads Internet Explorer settings
- 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe (PID: 7300)
There is functionality for taking screenshot (YARA)
- 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe (PID: 7300)
Starts application with an unusual extension
- 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe (PID: 7300)
Executable content was dropped or overwritten
- 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe (PID: 7300)
INFO
Checks supported languages
- 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe (PID: 7300)
- Bugreport-328464.dll (PID: 7656)
- ShellExperienceHost.exe (PID: 1188)
Reads the computer name
- 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe (PID: 7300)
- ShellExperienceHost.exe (PID: 1188)
The sample compiled with english language support
- 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe (PID: 7300)
UPX packer has been detected
- 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe (PID: 7300)
Creates files or folders in the user directory
- 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe (PID: 7300)
Checks proxy server information
- 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe (PID: 7300)
- slui.exe (PID: 5740)
Process checks computer location settings
- ShellExperienceHost.exe (PID: 1188)
Reads the machine GUID from the registry
- ShellExperienceHost.exe (PID: 1188)
Reads the software policy settings
- slui.exe (PID: 5740)
Create files in a temporary directory
- 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe (PID: 7300)
Compiled with Borland Delphi (YARA)
- 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe (PID: 7300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (28.6) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (28) |
| .exe | | | Win32 EXE Yoda's Crypter (27.5) |
| .dll | | | Win32 Dynamic Link Library (generic) (6.8) |
| .exe | | | Win32 Executable (generic) (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:03:20 02:18:06+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 1957888 |
| InitializedDataSize: | 24576 |
| UninitializedDataSize: | 2863104 |
| EntryPoint: | 0x499b90 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
133
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1188 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2104 | C:\WINDOWS\system32\svchost.exe -k wusvcs -p -s WaaSMedicSvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5740 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
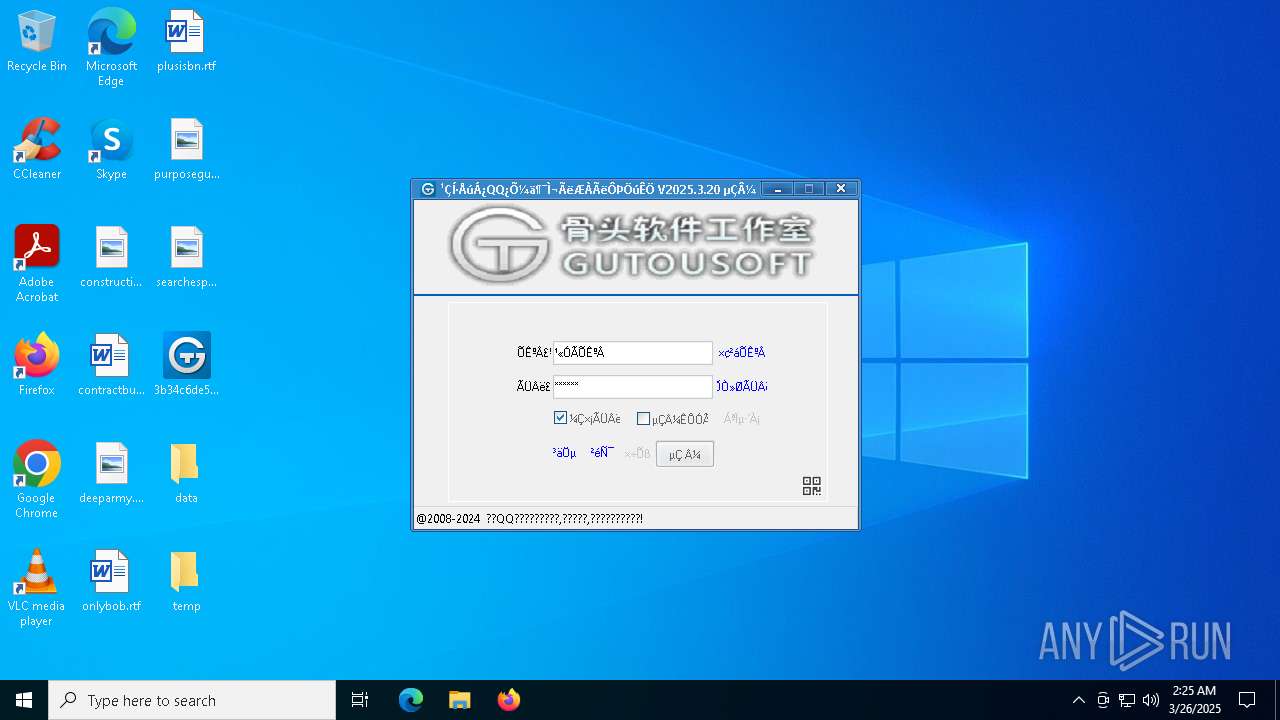
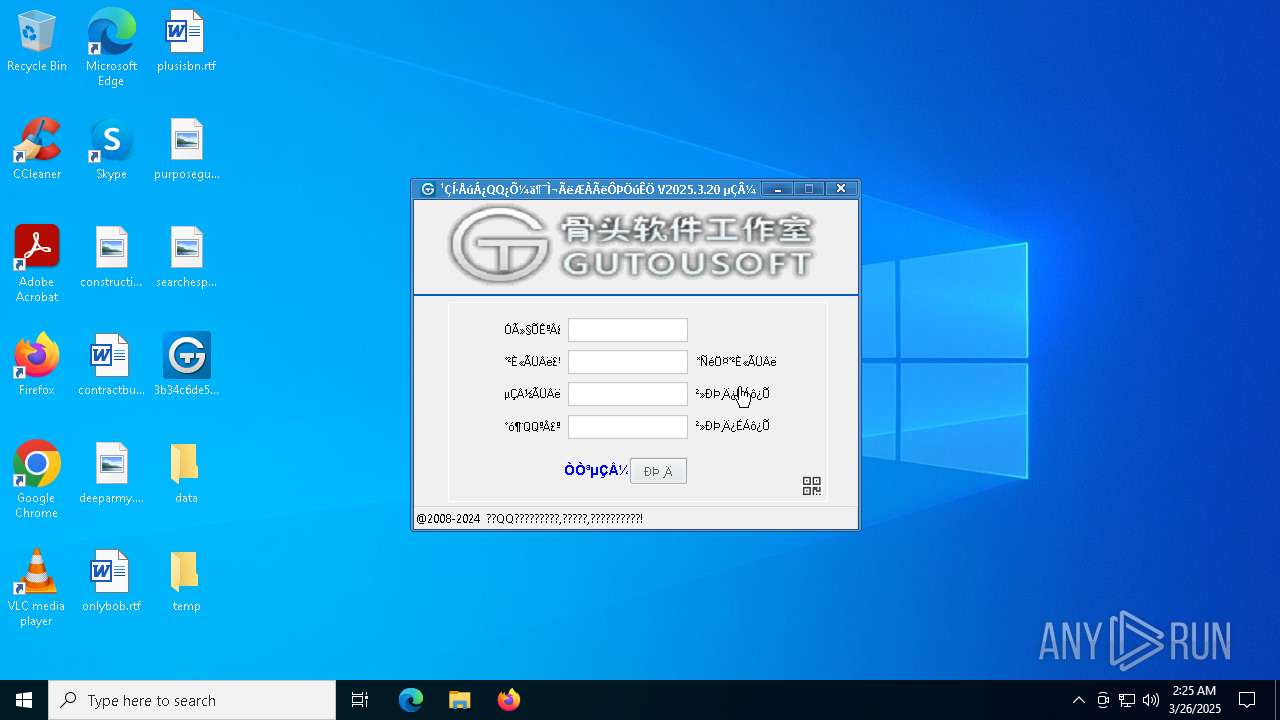
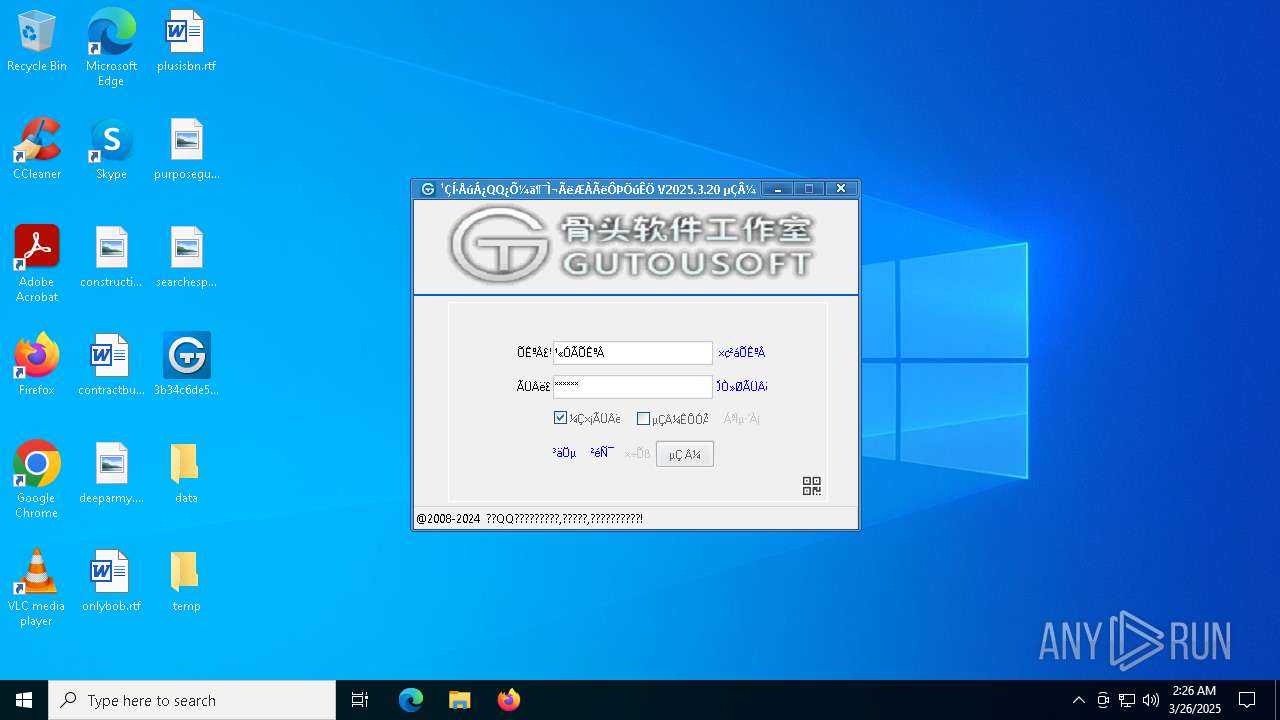
| 7300 | "C:\Users\admin\Desktop\3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe" | C:\Users\admin\Desktop\3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7656 | C:\Users\admin\Desktop\data\Bugreport-328464.dll Bugreport %E7%A7%92%E8%AF%84%E7%A7%92%20 | C:\Users\admin\Desktop\data\Bugreport-328464.dll | — | 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | |||||||||||
User: admin Company: Bugreport Integrity Level: MEDIUM Description: Bugreport Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
21 146
Read events
20 882
Write events
215
Delete events
49
Modification events
| (PID) Process: | (7300) 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Multimedia\DrawDib |
| Operation: | write | Name: | 1280x720x32(BGR 0) |
Value: 31,31,31,31 | |||
| (PID) Process: | (7300) 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7300) 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2104) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\WaaS\WaaSMedic\Configuration |
| Operation: | write | Name: | ETag |
Value: "66A2A386BBA04BD5A6331A0AD7AF8FD8389BA07DAF02CB8E5F846CAC" | |||
| (PID) Process: | (2104) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\WaaS\WaaSMedic\Configuration |
| Operation: | write | Name: | refreshInterval |
Value: 720 | |||
| (PID) Process: | (2104) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\WaaS\WaaSMedic\Configuration |
| Operation: | write | Name: | refreshAfter |
Value: 4EABC286BF9EDB01 | |||
| (PID) Process: | (2104) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\WaaS\WaaSMedic\Configuration\SERVICEHEALTHPLUGIN |
| Operation: | write | Name: | ORDER |
Value: 1 | |||
| (PID) Process: | (2104) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\WaaS\WaaSMedic\Configuration\SCHEDULEDTASKSPLUGIN |
| Operation: | write | Name: | MAXUPTIMETHRESHOLD |
Value: 20 | |||
| (PID) Process: | (2104) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\WaaS\WaaSMedic\Configuration\SERVICEHEALTHPLUGIN |
| Operation: | write | Name: | MINUPTIMETHRESHOLD |
Value: 0 | |||
| (PID) Process: | (2104) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\WaaS\WaaSMedic\Configuration\SERVICINGCLEANUPPLUGIN |
| Operation: | write | Name: | RUNONMANAGED |
Value: | |||
Executable files
3
Suspicious files
5
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7300 | 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | C:\Users\admin\Desktop\data\Gutou.ini | text | |
MD5:190923B1471016E8A760BD0BC88EB527 | SHA256:07C2277A9CDE3F71AFB5662CB84C7041F89F3FE37797036DE417698AE1B383D1 | |||
| 7300 | 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | C:\Users\admin\AppData\Local\Temp\iext1.fnr.bbs.125.la | executable | |
MD5:A96FBD5E66B31F3D816AD80F623E9BD9 | SHA256:2E67BA278646FDE95BB614DCBCC7DA1C6BF7976C918B2C6AD3D78640000326F3 | |||
| 2104 | svchost.exe | C:\Windows\Logs\waasmediccapsule\WaasRemediation.004.etl | binary | |
MD5:A83C439448C1E67E6FFC948FEF1FCE18 | SHA256:9FAA75F166CFDD869D3549B76139DDDDDB6A50790A5C6CC81B2084A432D7D60F | |||
| 2104 | svchost.exe | C:\Windows\System32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:3B5E0BD6640456A749D9155E6C135727 | SHA256:C362A3D2B661C6066A02FC169FAAA1976C2F6160DA5837C7E68B7E0F67B794ED | |||
| 7300 | 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | C:\Users\admin\Desktop\data\Bugreport-328464.dll | executable | |
MD5:89E441BB191BD836DF8D7F5B8204F922 | SHA256:162EA4DCD2A885FBE2F245A5A6202A2423B61F2CA0504361ABED639687280503 | |||
| 2104 | svchost.exe | C:\Windows\System32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:2729720330F9CD6B25D6EDD0BF4BCDD5 | SHA256:D1FC11130092712C7A3DD9B156F5BDB48BF91BF0854ED4D3FE319D0B1243611D | |||
| 7300 | 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | C:\Users\admin\AppData\Local\VirtualStore\.rand | text | |
MD5:3DFABC2DC272E6C57DBF5FE5F318D9C9 | SHA256:44622D268EDC5E82D9F297269E03D5957321F5478955DF59634D9B35CEB91D70 | |||
| 7656 | Bugreport-328464.dll | C:\Users\admin\Desktop\data\Bugreport_error.ini | text | |
MD5:40BF43E3AC2E80C5A5DDA44A1567D7F4 | SHA256:88F04ECB5C0F04AA82630B6D74001AAC05790EBFBB1E97E2D4C14A9D4D6DBEAA | |||
| 7300 | 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\VNP779MF.htm | text | |
MD5:ECAA88F7FA0BF610A5A26CF545DCD3AA | SHA256:F1945CD6C19E56B3C1C78943EF5EC18116907A4CA1EFC40A57D48AB1DB7ADFC5 | |||
| 7300 | 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | C:\Users\admin\Desktop\data\Bugreport.ini | text | |
MD5:B2FFA0CC5B2C73CAE26DB03F1EEC15D2 | SHA256:4D2C6706B68D5979DB87FBC4C01743F109AD22970A389DC6D203D2ECED6CDA83 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
63
DNS requests
23
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7300 | 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | GET | 200 | 120.24.75.226:80 | http://d.gutousoft.com/%E5%85%AC%E5%85%B1%E8%BD%AF%E4%BB%B6%E4%B8%8B%E8%BD%BD/%E7%A7%92%E8%AF%84%E7%A7%92%E8%B5%9E.txt?V=2025.3.20 | unknown | — | — | unknown |
2104 | svchost.exe | GET | 200 | 104.124.11.58:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7300 | 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | GET | 200 | 203.195.236.181:80 | http://vip.gutou.cc/ | unknown | — | — | malicious |
7300 | 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | GET | 403 | 120.24.75.226:80 | http://y.gutousoft.com/ | unknown | — | — | malicious |
7300 | 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | GET | — | 120.24.75.226:80 | http://www.gutou.cc/up/tongji.htm | unknown | — | — | malicious |
7300 | 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | GET | 404 | 120.24.75.226:80 | http://www.gutou.cc/up/tongji.htm | unknown | — | — | malicious |
7300 | 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | GET | 200 | 203.195.236.181:80 | http://vip.gutou.cc/kss_api/api.php?a=uplog&apiver=903&c=0&gdata=1&softcode=1000004&&x=1104640 | unknown | — | — | malicious |
— | — | GET | 304 | 4.245.163.56:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
8052 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
8052 | SIHClient.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7300 | 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | 120.24.75.226:80 | d.gutousoft.com | Hangzhou Alibaba Advertising Co.,Ltd. | CN | malicious |
2104 | svchost.exe | 104.124.11.58:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7300 | 3b34c6de5409fdfe08b92f3a1b07a5ba57e52fcd0adb6511b9466d131e780a77.exe | 203.195.236.181:80 | vip.gutou.cc | Shenzhen Tencent Computer Systems Company Limited | CN | malicious |
6544 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
d.gutousoft.com |
| unknown |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
vip.gutou.cc |
| malicious |
y.gutousoft.com |
| malicious |
login.live.com |
| whitelisted |
www.gutou.cc |
| malicious |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |