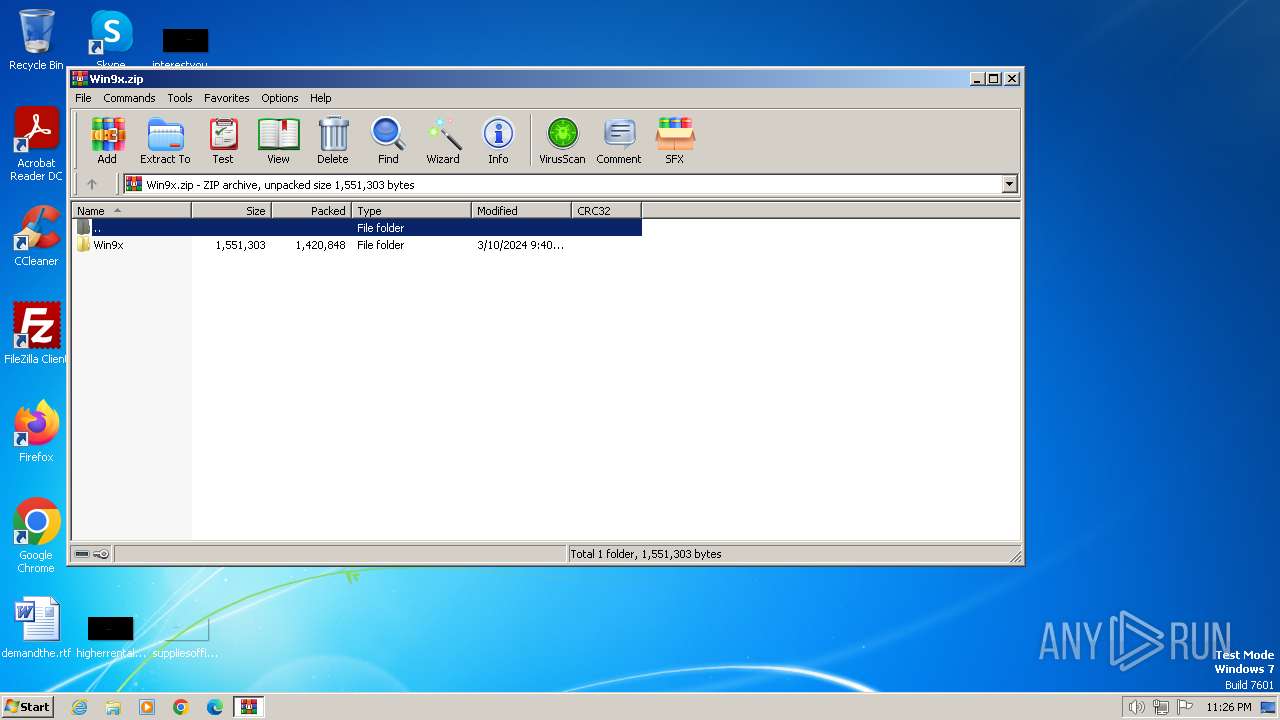
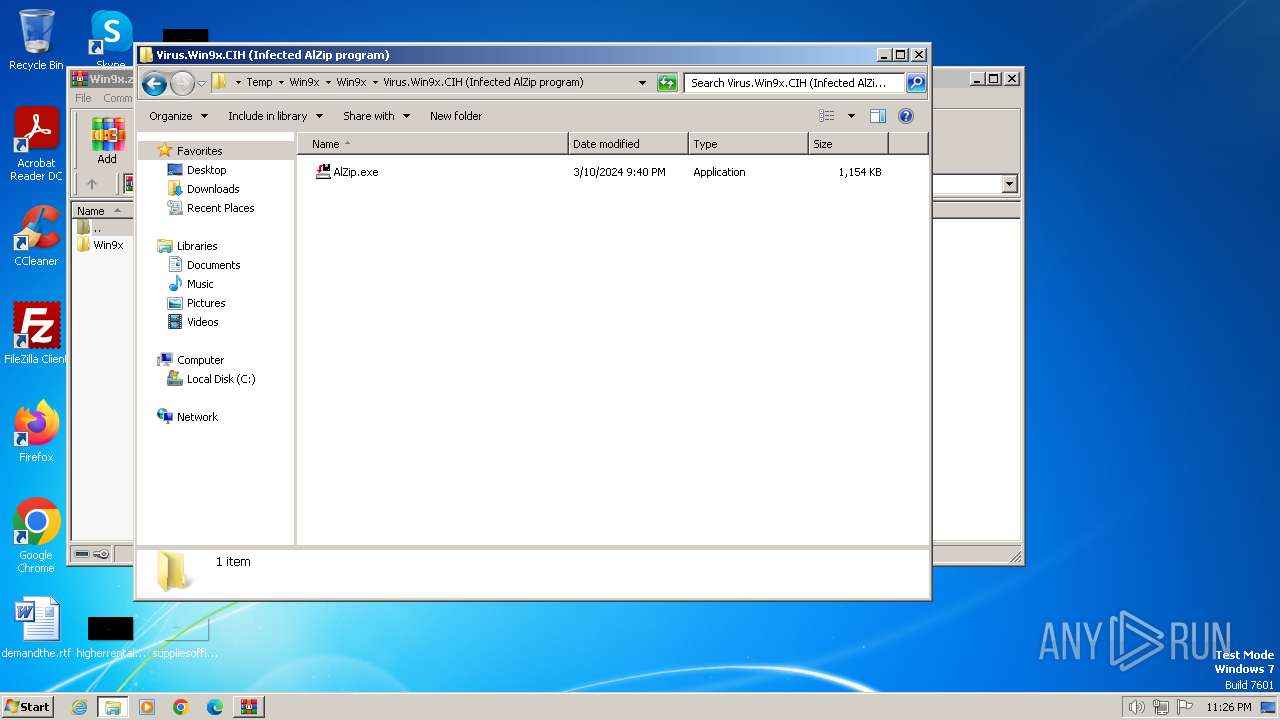
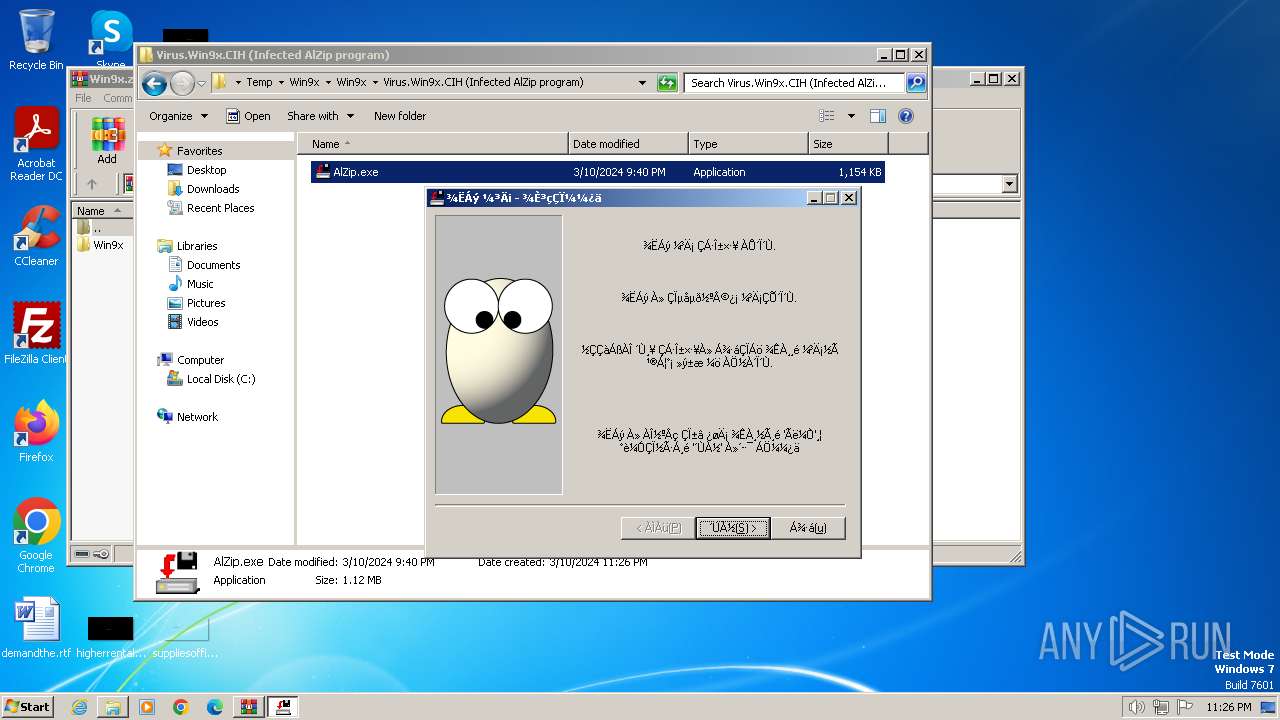
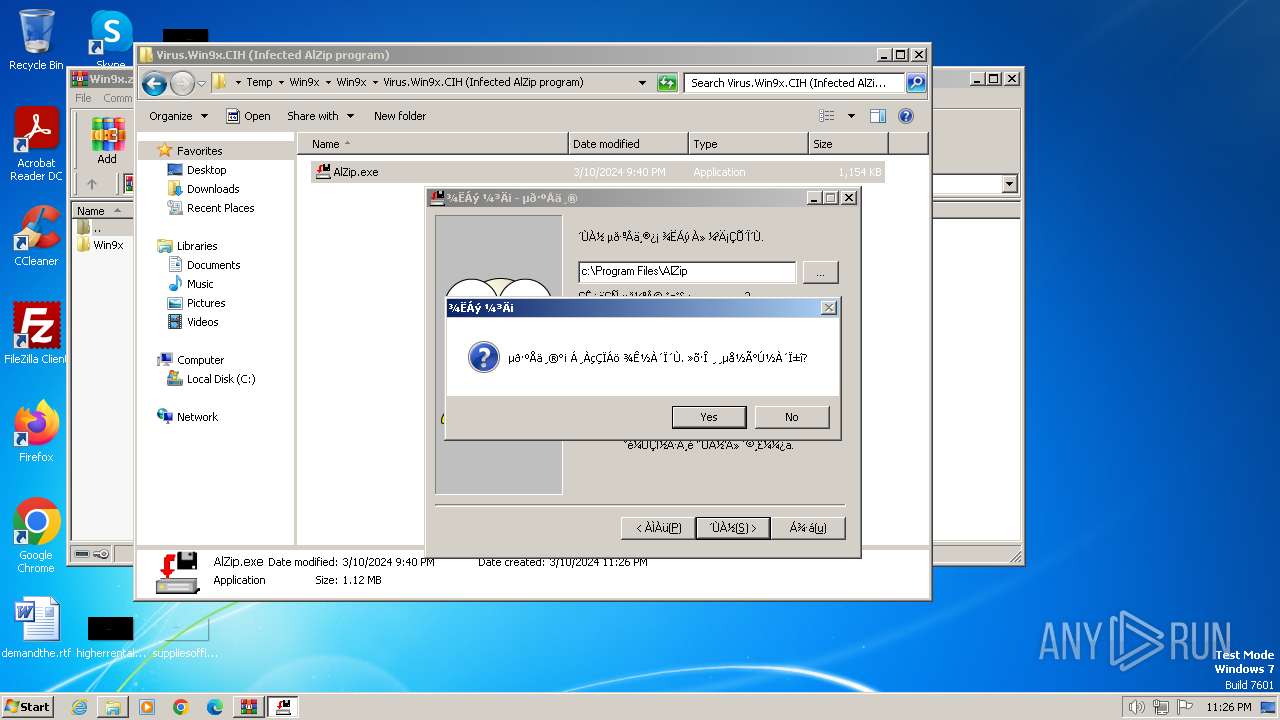
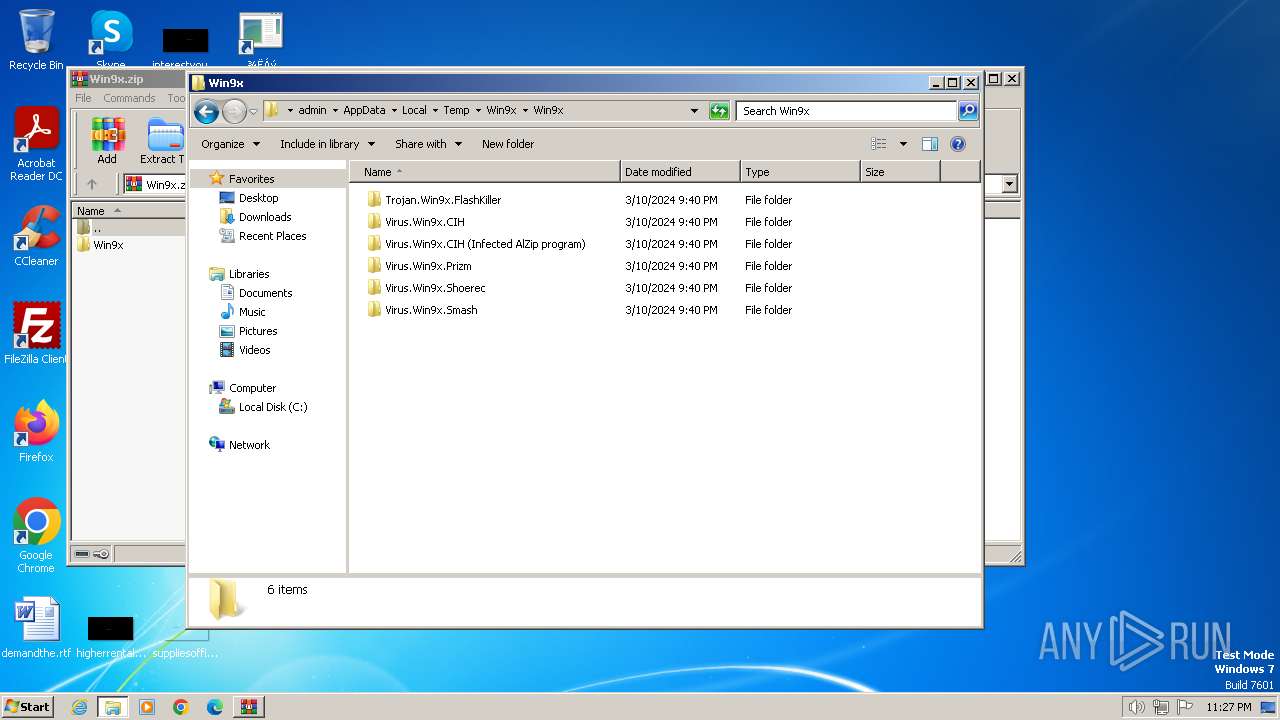
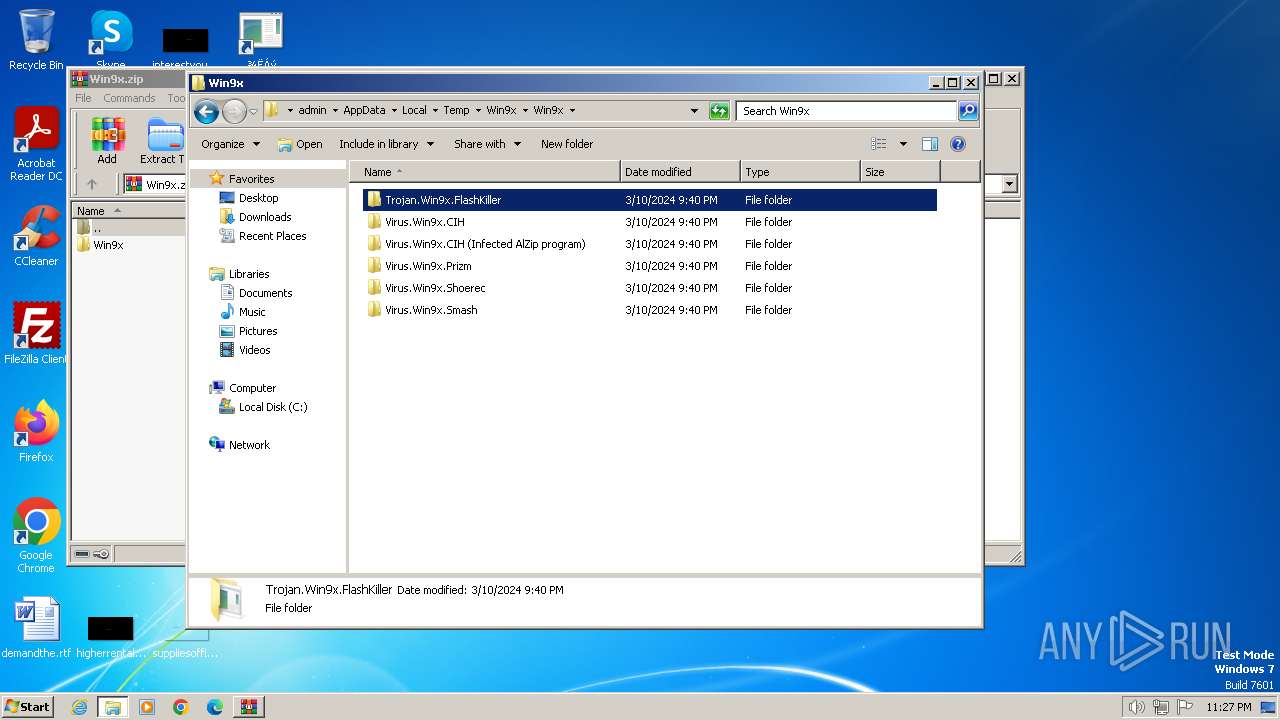
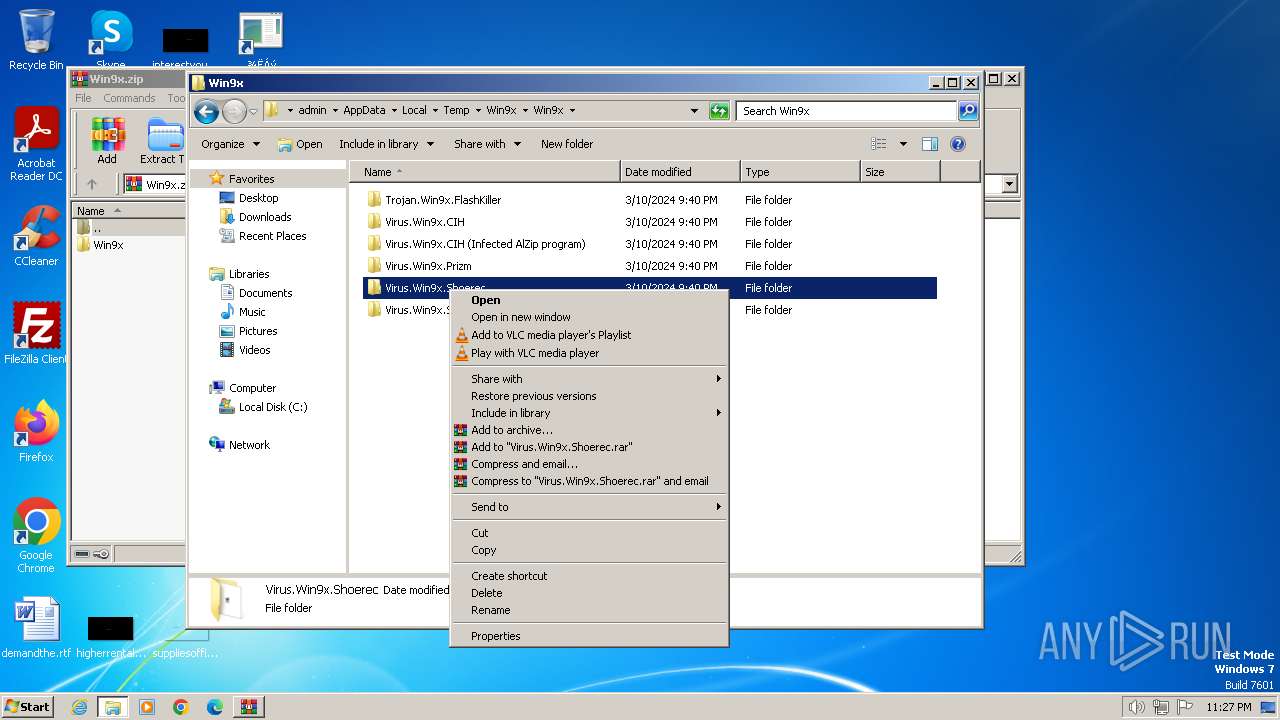
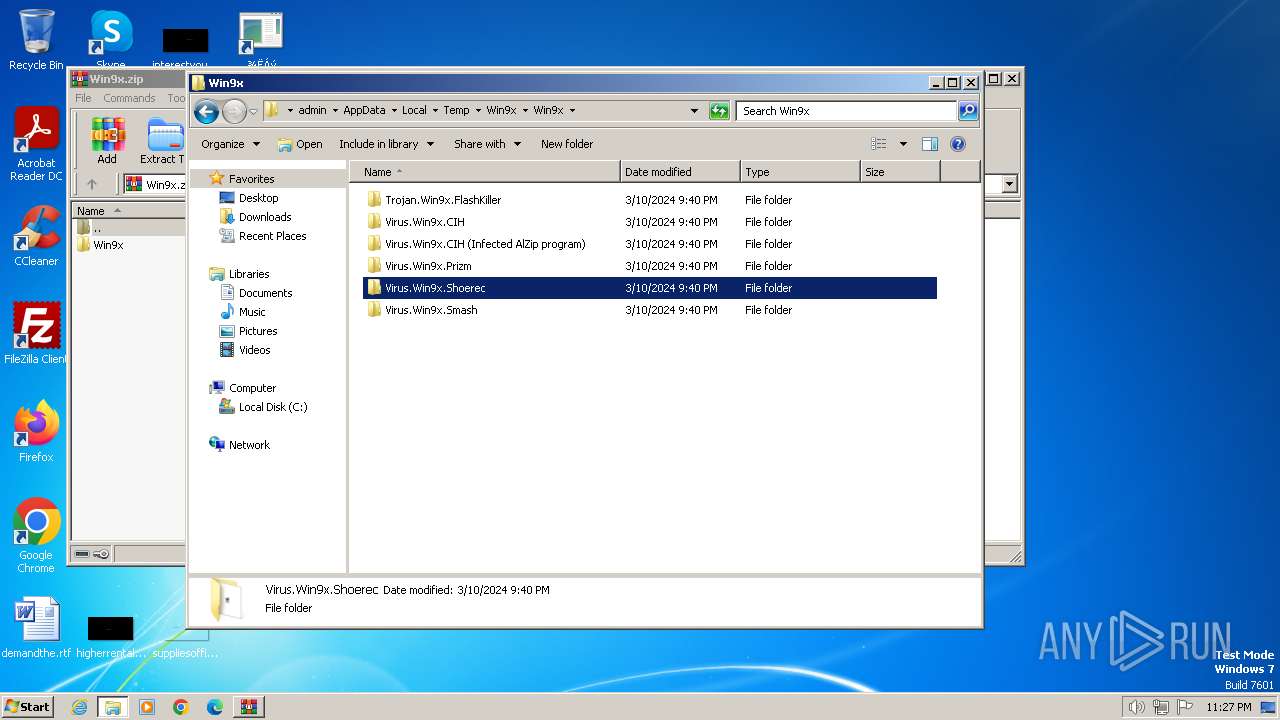
| File name: | Win9x.zip |
| Full analysis: | https://app.any.run/tasks/811b4d20-470e-411c-8cc1-8db77fe2c4b4 |
| Verdict: | Malicious activity |
| Analysis date: | March 10, 2024, 23:26:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | E5FCF4C5B90E585AC6084BBE1377D03D |
| SHA1: | 47355CC3AAF20F4951EDAE89E11E2D088EDC678E |
| SHA256: | 3B34AD22B264B89548E713B6737A35294F49920586DD66DE7585C86D288AF7C6 |
| SSDEEP: | 49152:7yn7wqjrbqPoZEZfZyAD6Ja1uNgjFt80zirh0udJKFOoxTqobr2oSzX2akMT6zP6:g7NruPoZEZfg6a66JdJK9vSb2abT6DU5 |
MALICIOUS
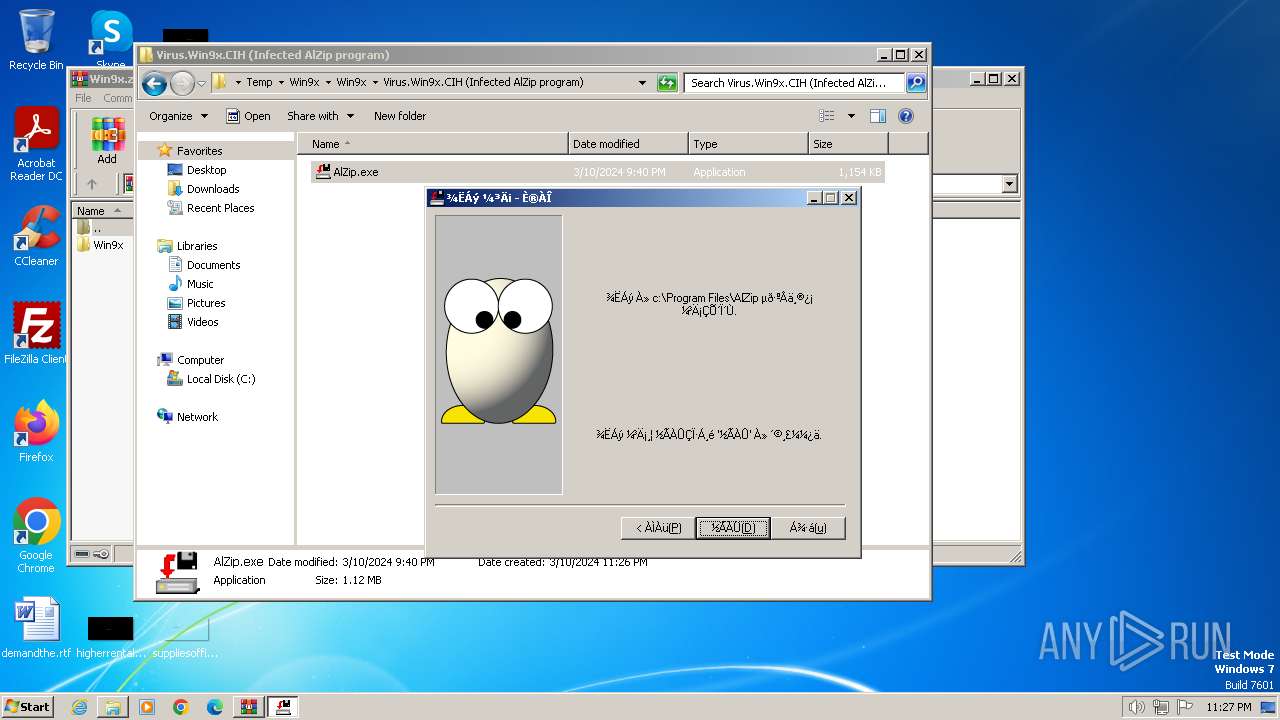
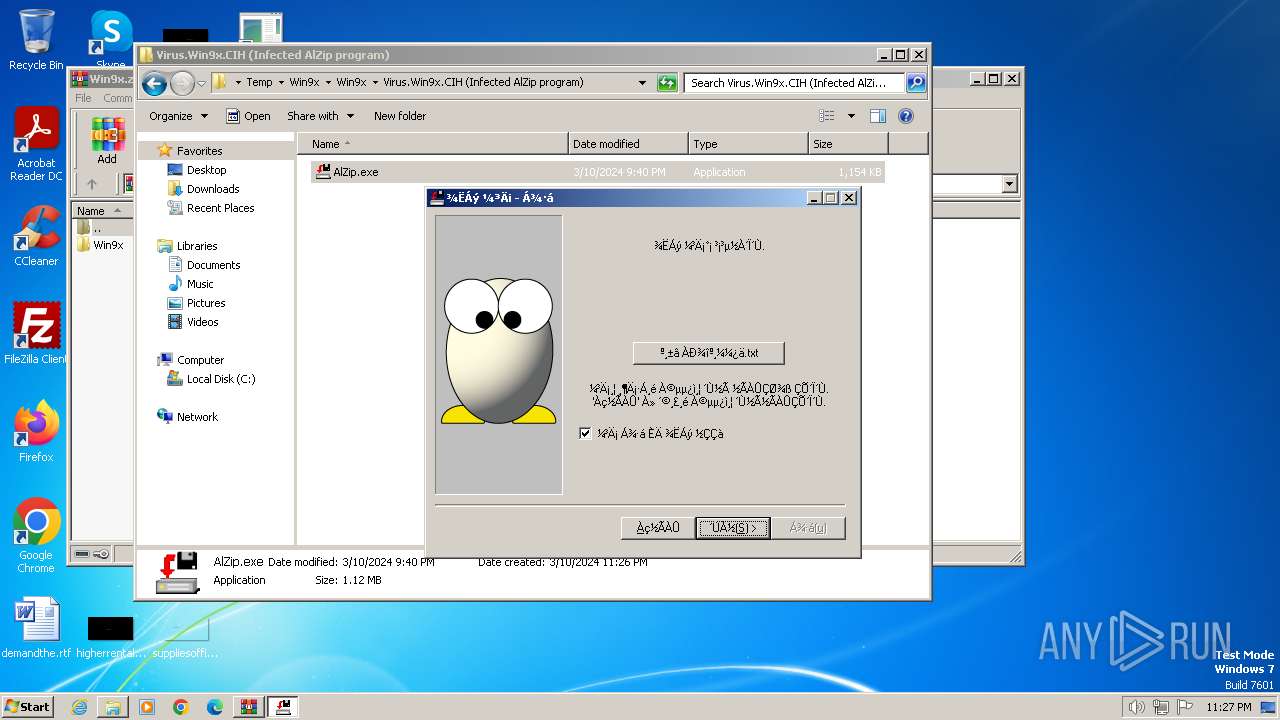
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3656)
- AlZip.exe (PID: 2504)
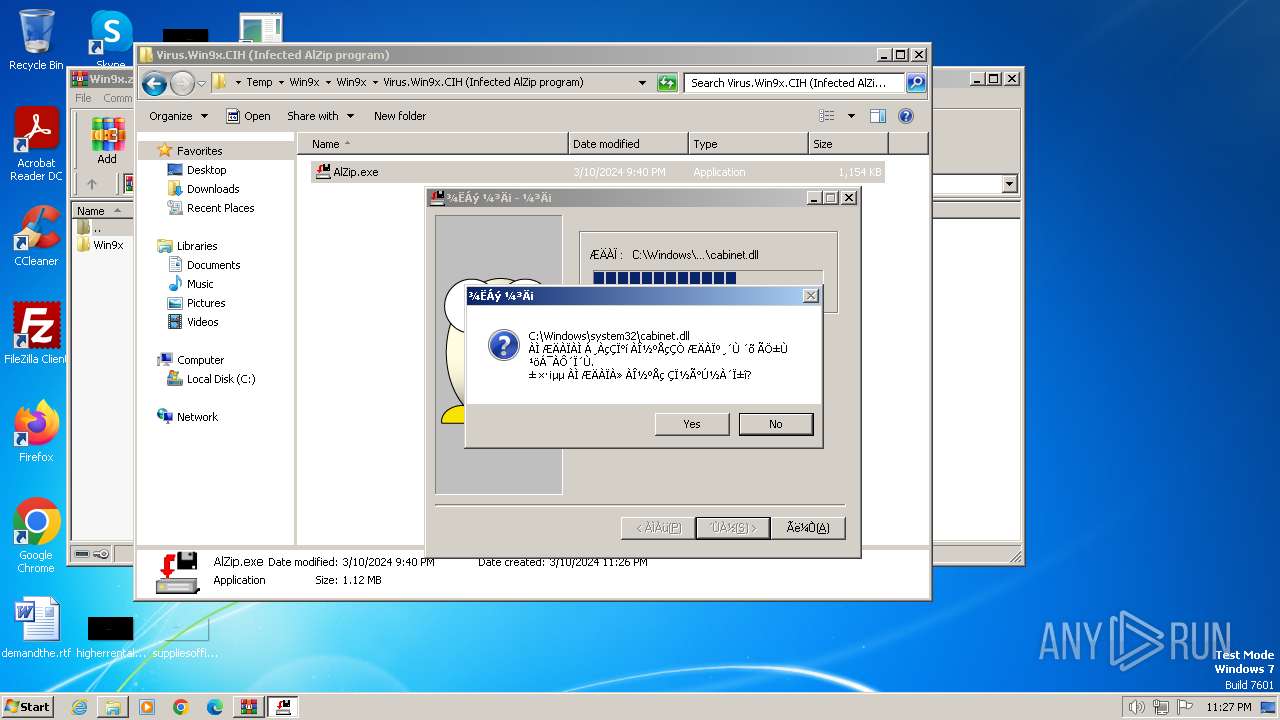
Creates a writable file in the system directory
- AlZip.exe (PID: 2504)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3656)
- AlZip.exe (PID: 2504)
Executable content was dropped or overwritten
- AlZip.exe (PID: 2504)
Starts a Microsoft application from unusual location
- CIH.exe (PID: 3036)
INFO
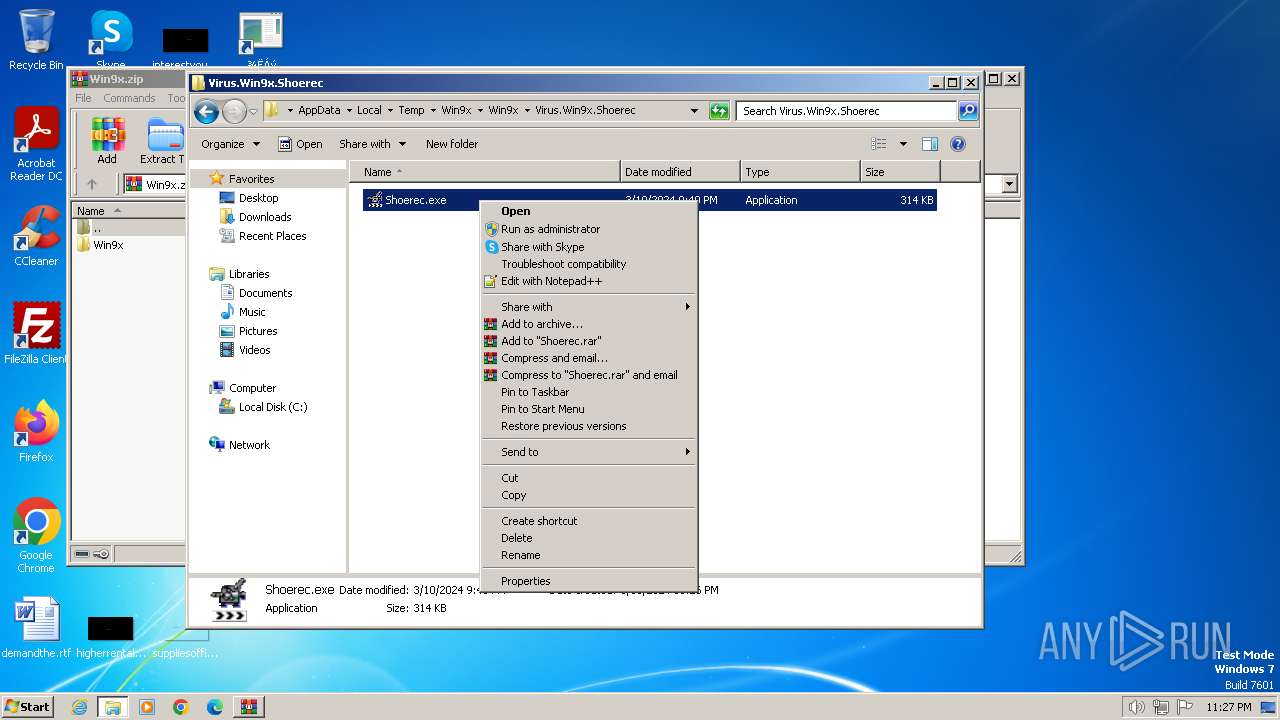
Manual execution by a user
- Prizm.exe (PID: 1644)
- AlZip.exe (PID: 2780)
- AlZip.exe (PID: 2504)
- Smash.exe (PID: 3500)
- CIH.exe (PID: 3036)
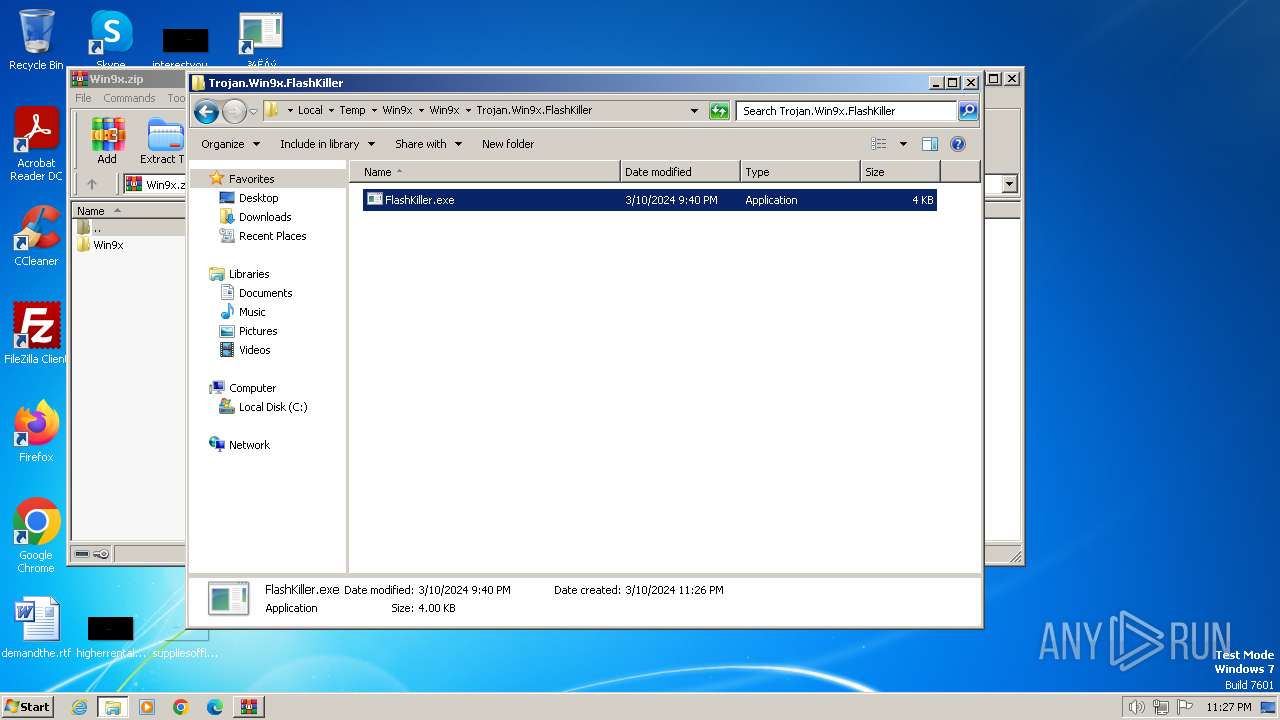
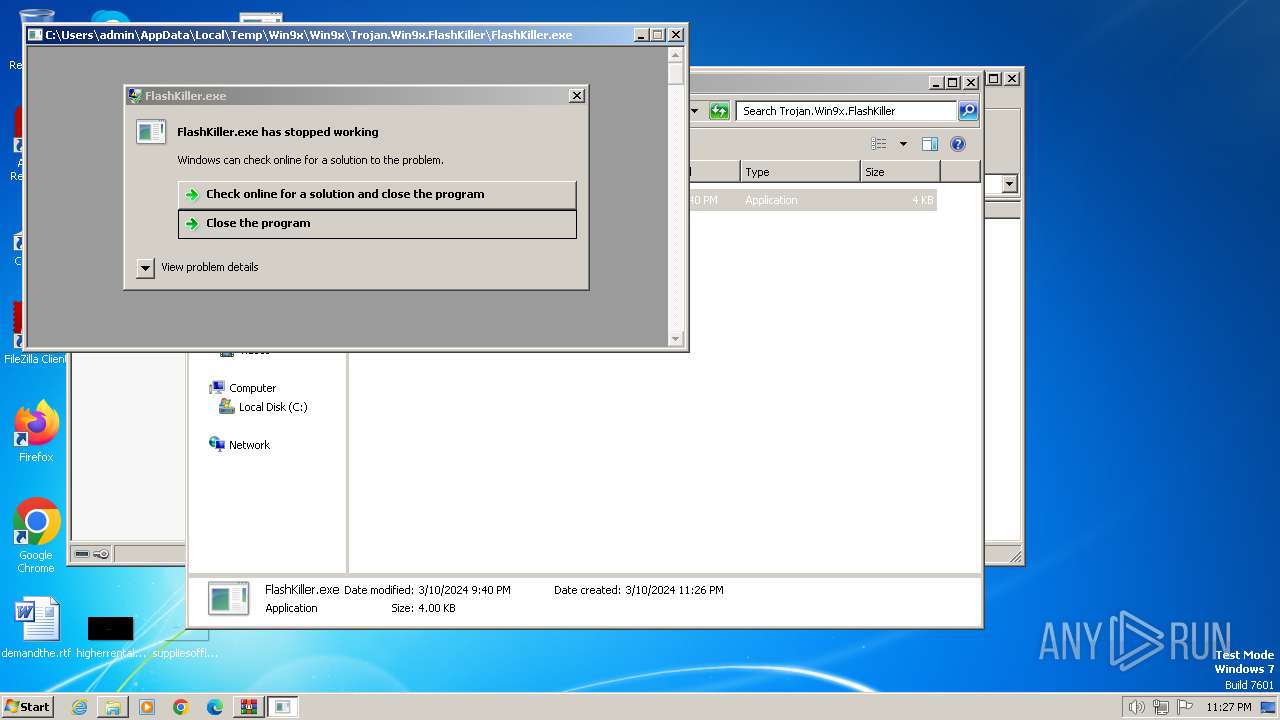
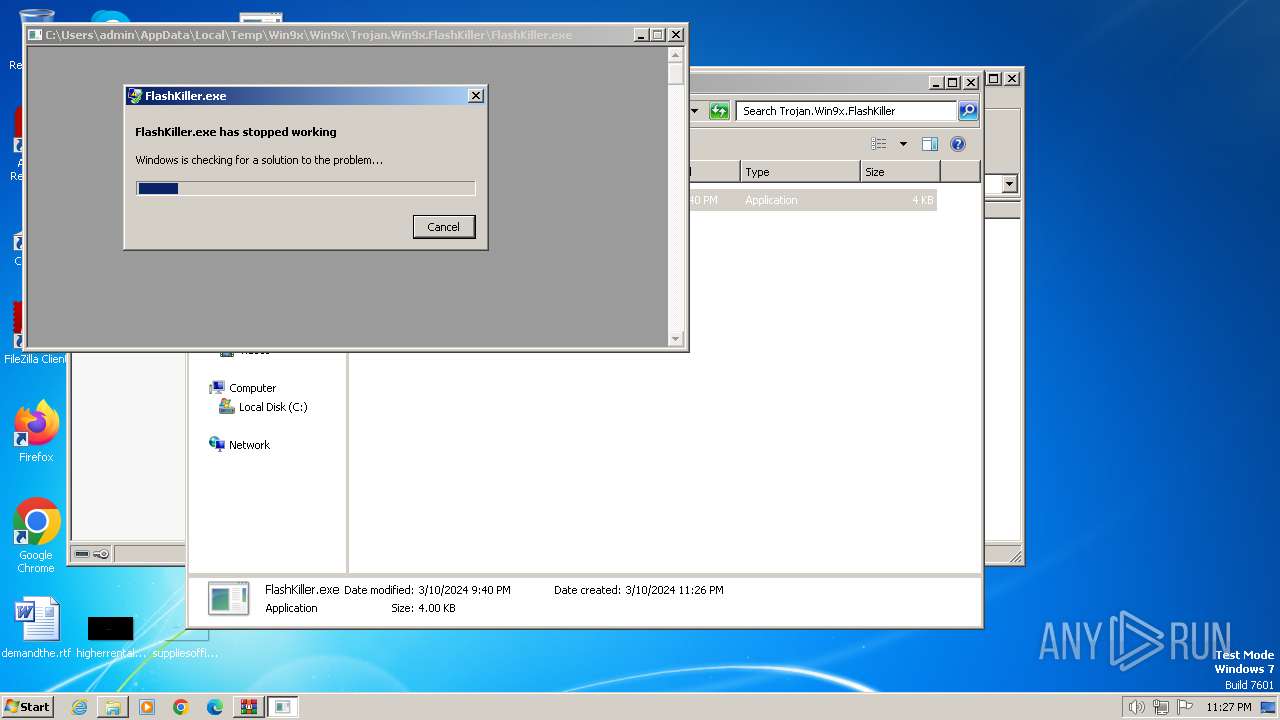
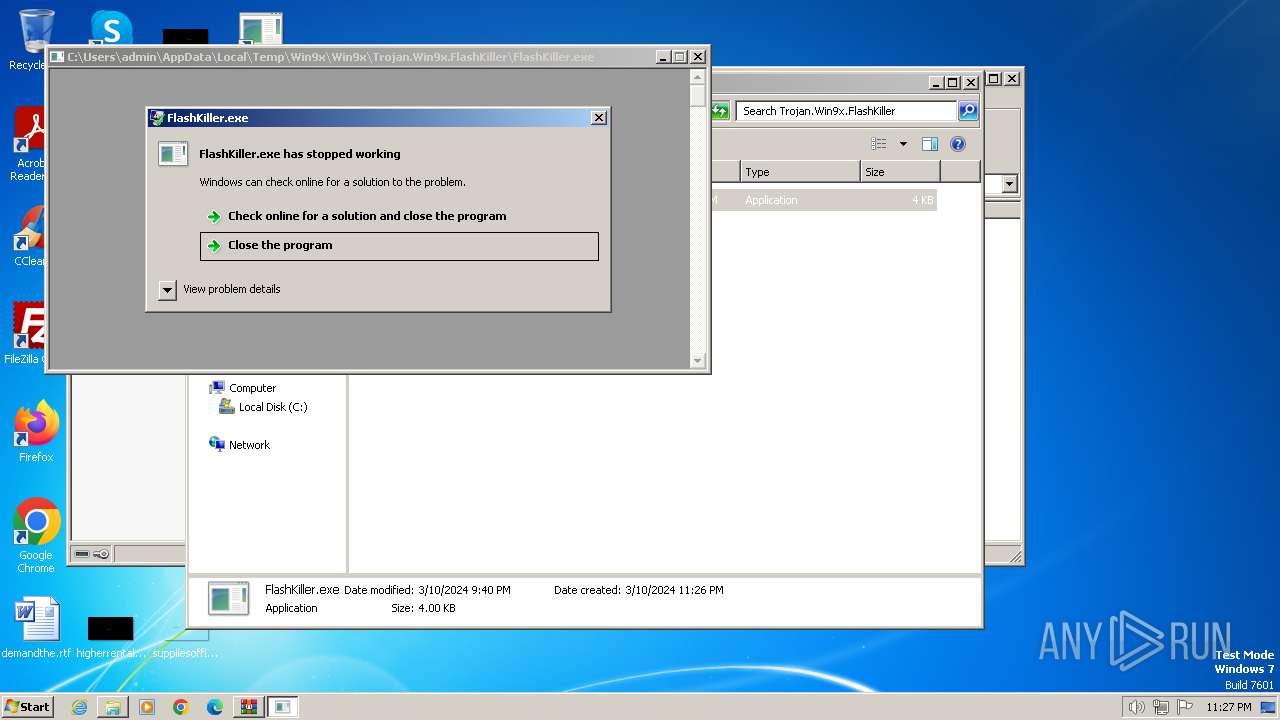
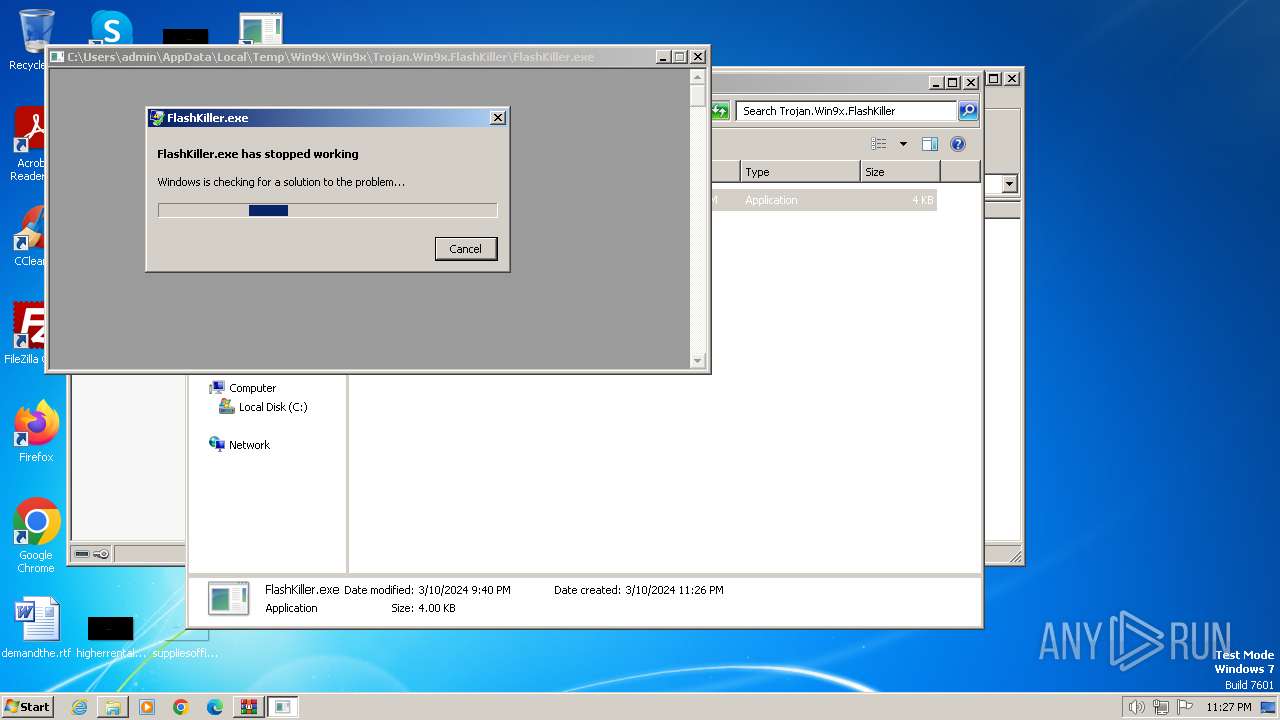
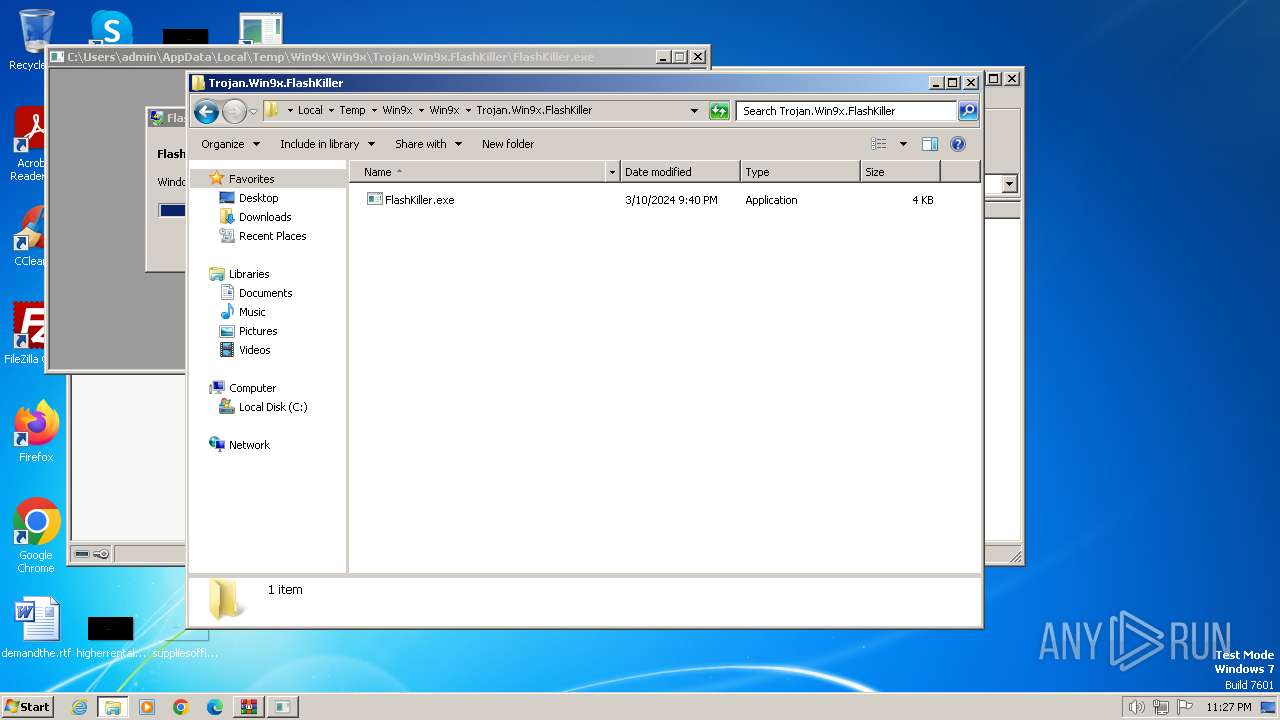
- FlashKiller.exe (PID: 3780)
- FlashKiller.exe (PID: 908)
- Smash.exe (PID: 3392)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3656)
Checks supported languages
- Prizm.exe (PID: 1644)
- AlZip.exe (PID: 2504)
- AlZip.exe (PID: 2780)
Creates files or folders in the user directory
- AlZip.exe (PID: 2504)
Reads the computer name
- AlZip.exe (PID: 2504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 45 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:03:10 21:40:24 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 2 |
| ZipUncompressedSize: | - |
| ZipFileName: | Win9x/ |
Total processes
64
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 908 | "C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Trojan.Win9x.FlashKiller\FlashKiller.exe" | C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Trojan.Win9x.FlashKiller\FlashKiller.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 1644 | "C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Virus.Win9x.Prizm\Prizm.exe" | C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Virus.Win9x.Prizm\Prizm.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1986719548 Modules
| |||||||||||||||
| 2504 | "C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Virus.Win9x.CIH (Infected AlZip program)\AlZip.exe" | C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Virus.Win9x.CIH (Infected AlZip program)\AlZip.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2780 | "C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Virus.Win9x.CIH (Infected AlZip program)\AlZip.exe" | C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Virus.Win9x.CIH (Infected AlZip program)\AlZip.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
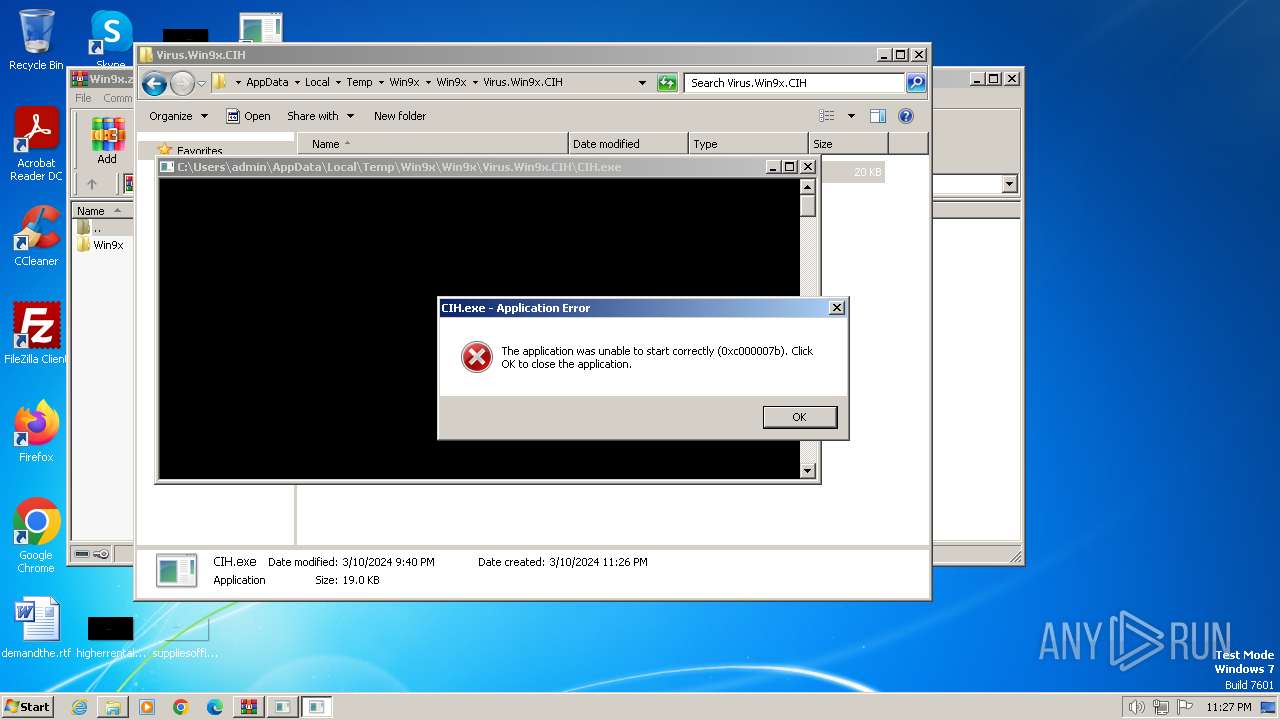
| 3036 | "C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Virus.Win9x.CIH\CIH.exe" | C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Virus.Win9x.CIH\CIH.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Arp Command Exit code: 3221225595 Version: 3.51 Modules
| |||||||||||||||
| 3392 | "C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Virus.Win9x.Smash\Smash.exe" | C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Virus.Win9x.Smash\Smash.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3500 | "C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Virus.Win9x.Smash\Smash.exe" | C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Virus.Win9x.Smash\Smash.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3656 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Win9x.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3780 | "C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Trojan.Win9x.FlashKiller\FlashKiller.exe" | C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Trojan.Win9x.FlashKiller\FlashKiller.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
Total events
4 457
Read events
4 440
Write events
17
Delete events
0
Modification events
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Win9x.zip | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
15
Suspicious files
2
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2504 | AlZip.exe | — | ||
MD5:— | SHA256:— | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Trojan.Win9x.FlashKiller\FlashKiller.exe | executable | |
MD5:331973644859575A72F7B08BA0447F2A | SHA256:353DF4F186C06A626373B0978D15EC6357510FD0D4AC54B63217B37142AB52D3 | |||
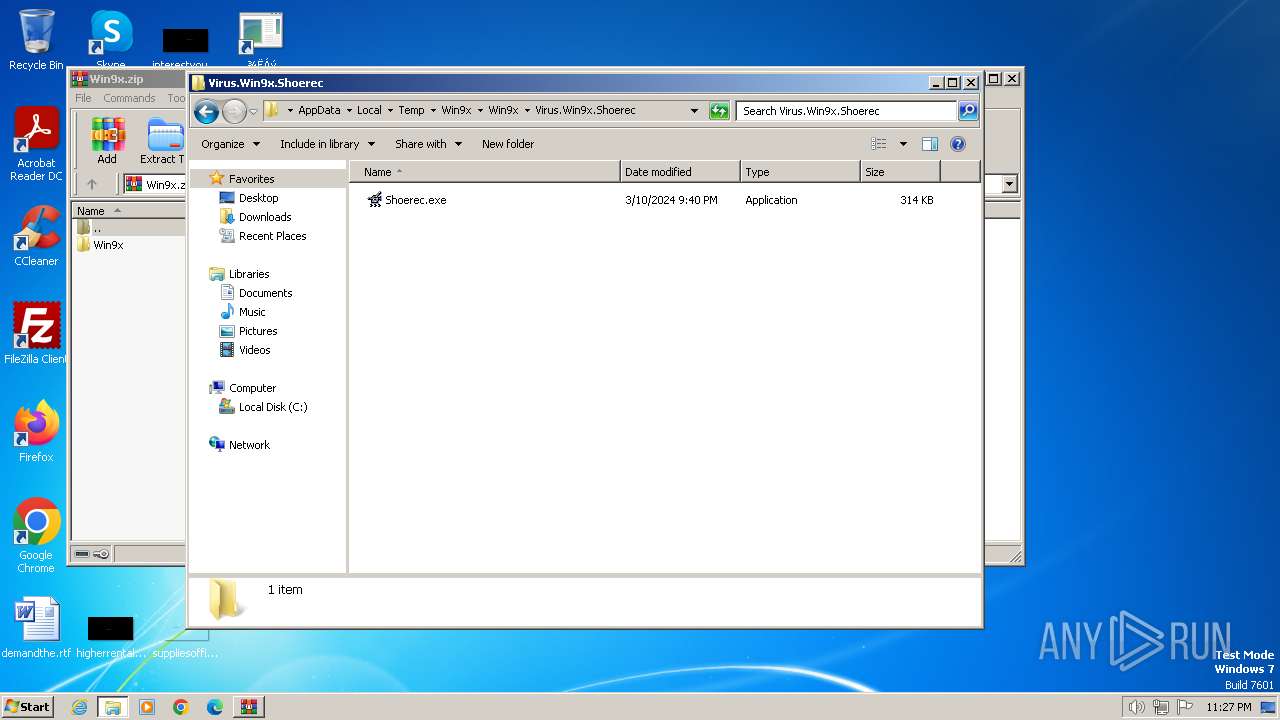
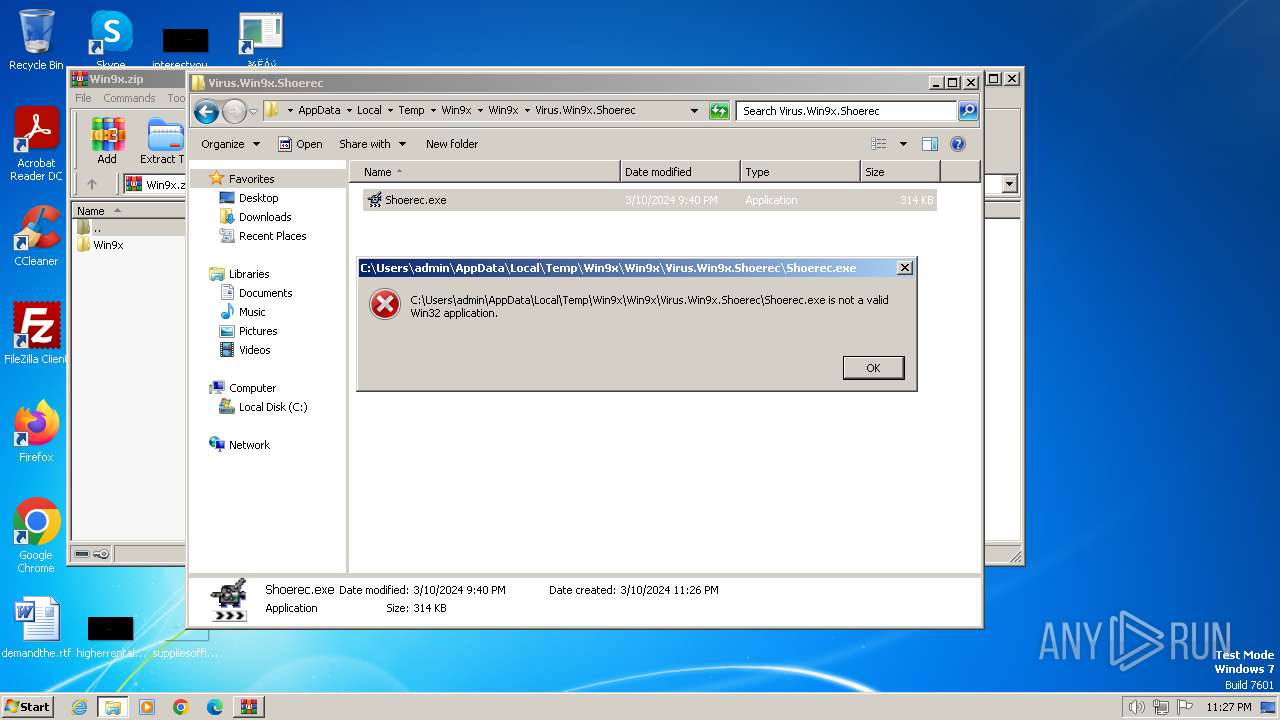
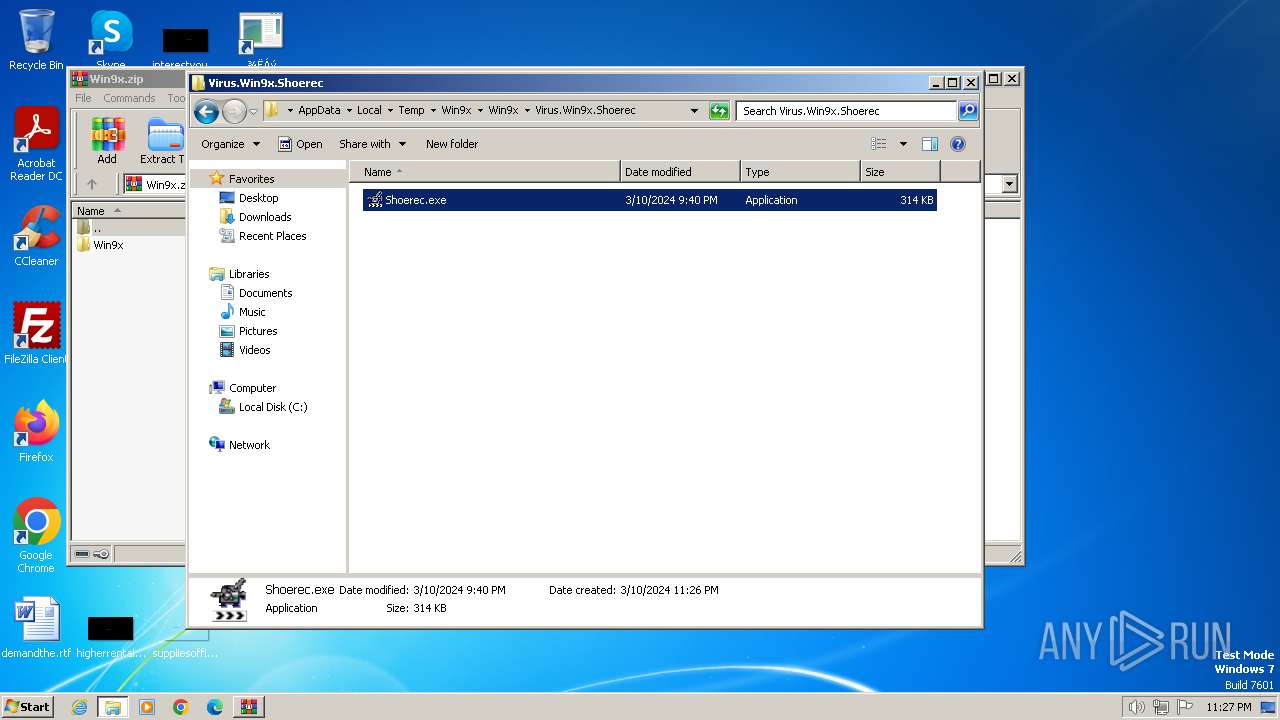
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Virus.Win9x.Shoerec\Shoerec.exe | executable | |
MD5:F257A5F19F616F63785052CB3B316927 | SHA256:A7FC7287EFA7BFC2362399975C785F9E60F028E48A0F5BDE316243DA4EB6C797 | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Virus.Win9x.CIH (Infected AlZip program)\AlZip.exe | executable | |
MD5:7BC322D95951DFE16E8CF47EE586E909 | SHA256:6BF4879E15B5E25B35144FE4E136705AFB501B21F78EB1CACF45618A1452D272 | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Virus.Win9x.Prizm\Prizm.exe | executable | |
MD5:FEEF71C9299C0B6F7313074260FAE590 | SHA256:96D2EAFF43D5807EE8C55E6AC9A8D32855198DC3BF83327766E53E4E7A88FF53 | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Virus.Win9x.CIH\CIH.exe | executable | |
MD5:0255AB089FC9394E2339CF87ACD073E6 | SHA256:65317A4BF674804D0D98DFC695B8423EA07A4F9B633511F5371D6F0A97A86E7C | |||
| 2504 | AlZip.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\AlZip\Alzip.$A | executable | |
MD5:DC9230367FD6678E9C06C99FBBD1B0E6 | SHA256:94ADFA6C8E091E3485F9C6C6704E4E950306DCCAEAAF1BDD4DE34A1C99BB4C9C | |||
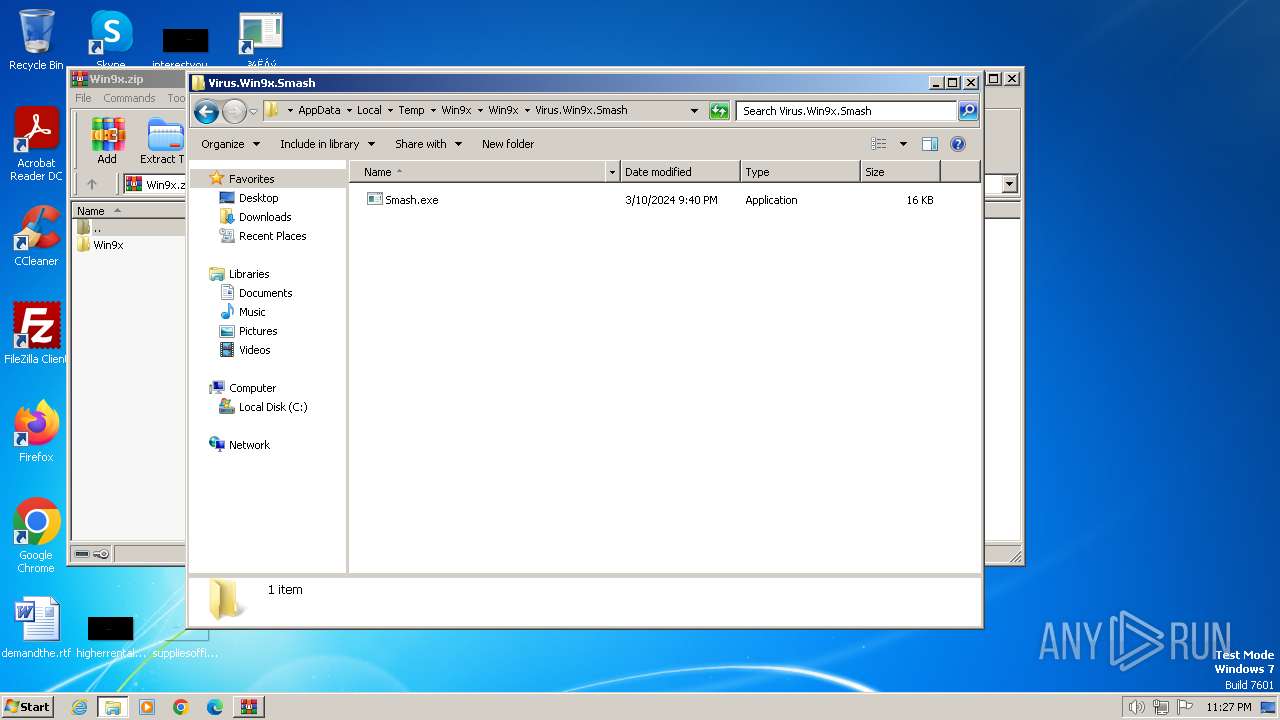
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Win9x\Win9x\Virus.Win9x.Smash\Smash.exe | executable | |
MD5:628CA226D18EA3DF1C4B02882329B044 | SHA256:5F7D233D25994AC890720A89DB315D2FE66C6F512A919BA74F27F28DB629A309 | |||
| 2504 | AlZip.exe | C:\Users\admin\AppData\Local\VirtualStore\Windows\System32\unrar.$A | executable | |
MD5:0D509B000ED82223628C303FD49C2022 | SHA256:FACB32D617482B60A27472570449A2DD8B0B77B88BA6EE2D4C7F2952CCB8F119 | |||
| 2504 | AlZip.exe | C:\Users\admin\AppData\Local\VirtualStore\Windows\System32\zipSFX.$A | executable | |
MD5:A532650392D3A85805276A8DA4AF31AE | SHA256:AB17AF60CAE6249B17B8D5B8B98D78C4C48E4086D16712744FB81918A223F1FA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3792 | WerFault.exe | 104.208.16.93:443 | watson.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3872 | WerFault.exe | 104.208.16.93:443 | watson.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
watson.microsoft.com |
| whitelisted |