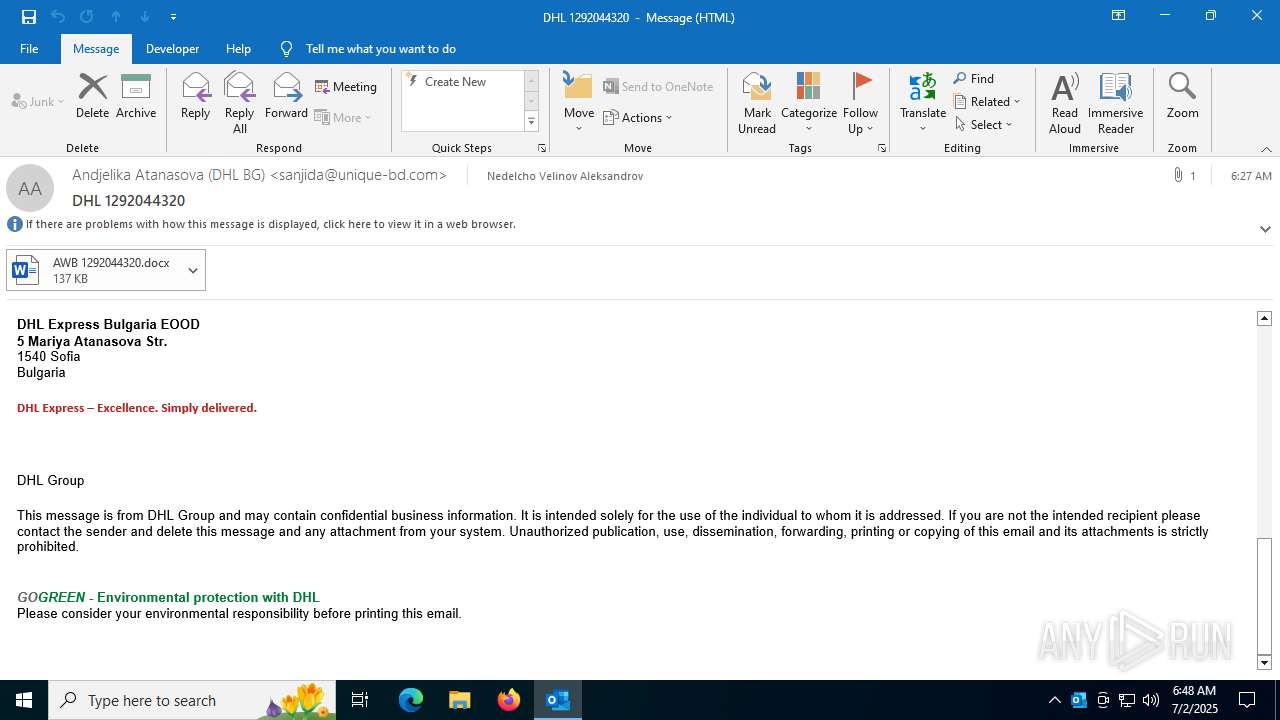
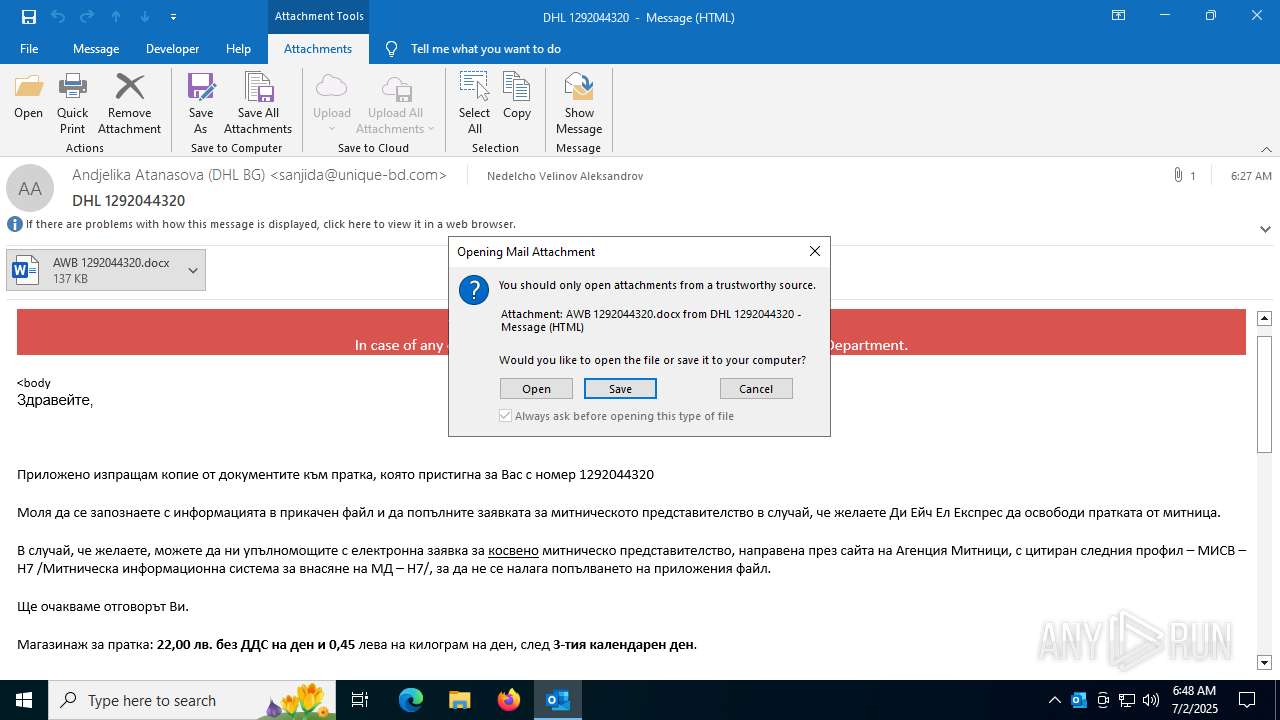
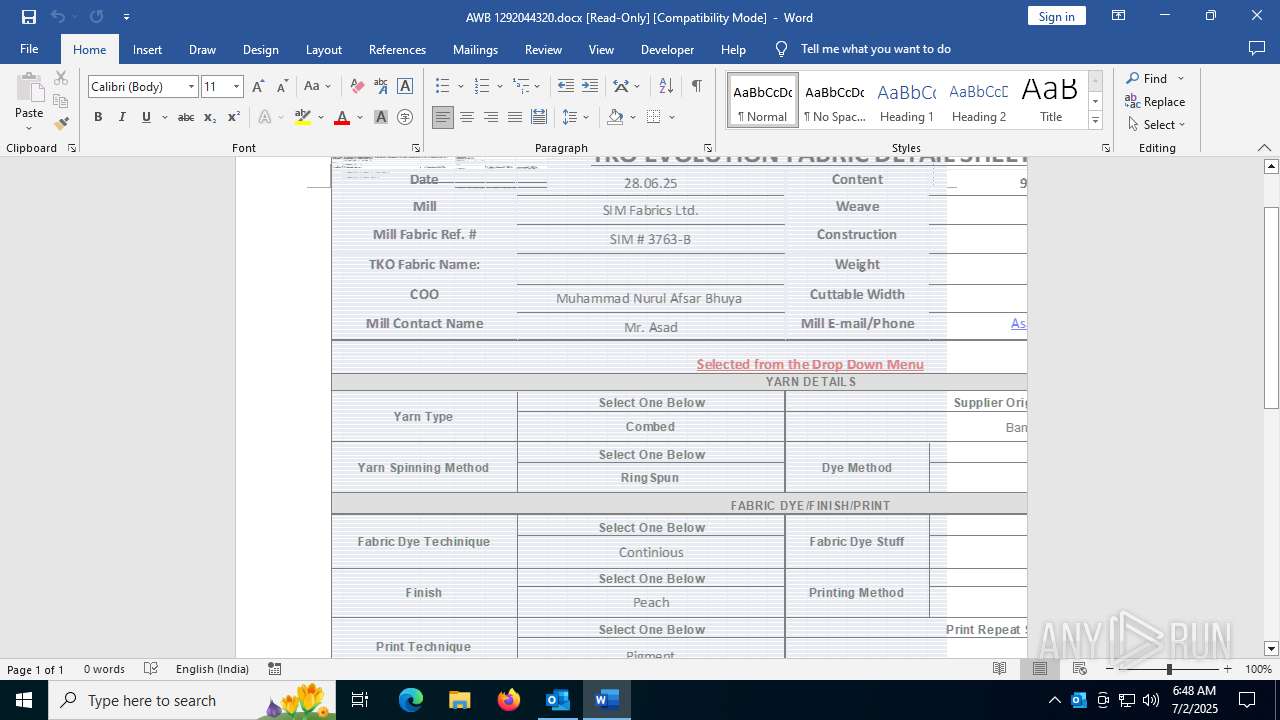
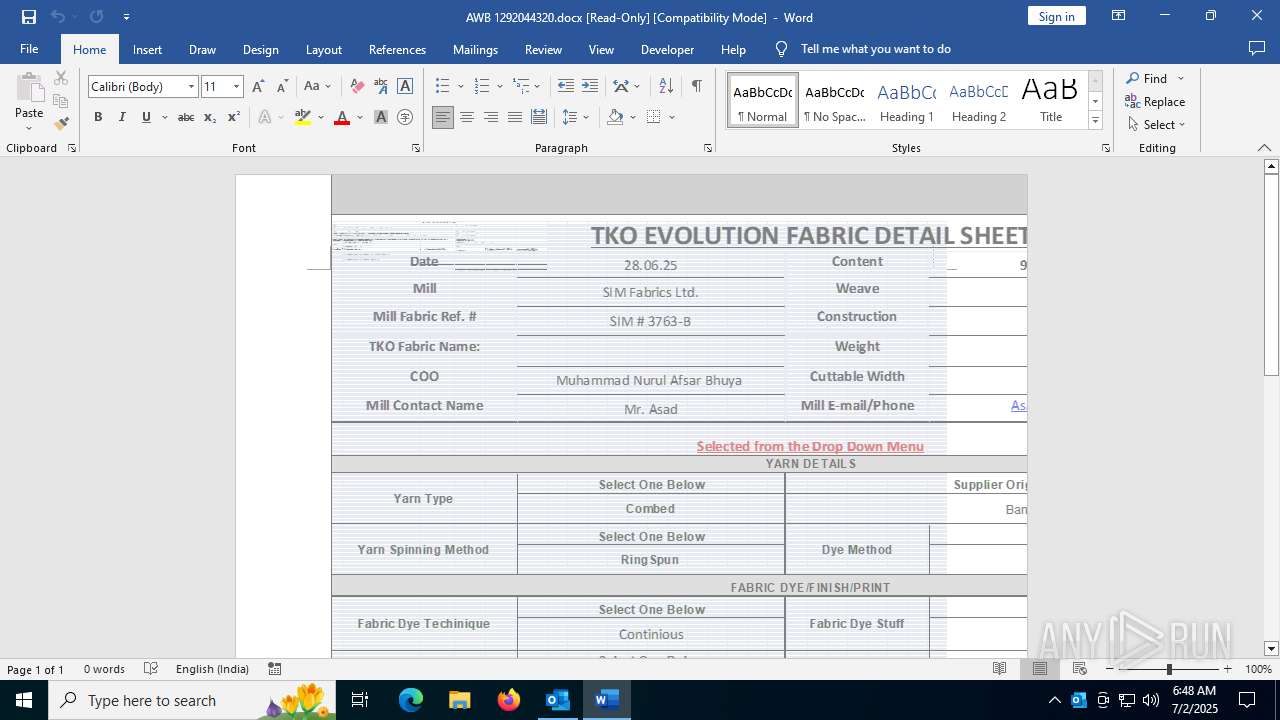
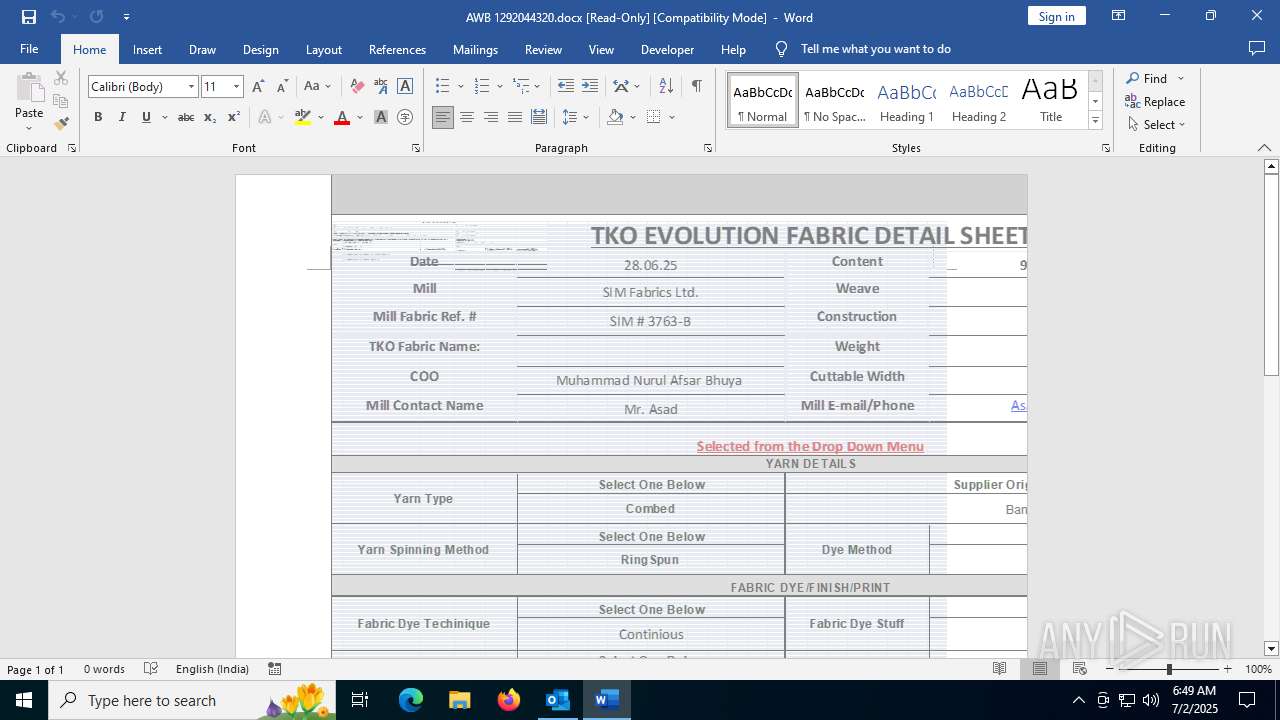
| File name: | phish_alert_iocp_v1.4.85.eml |
| Full analysis: | https://app.any.run/tasks/7ea98cb2-e229-42e4-96ac-8c6b8baee84a |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2025, 06:47:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF line terminators |
| MD5: | 3AEFBC5D9A579D8076DEF841623CF04A |
| SHA1: | 1CB1DA2AA6754B233F1E530A7D9C1A8E664D488F |
| SHA256: | 3AE3C37D612B2EABFA666BE2239AAC96FFFD49689F1C3A6B86E479CF3EC65193 |
| SSDEEP: | 3072:AW9+pLUjZLALbbv3yuMPxeSFnzzbcqKMq5tia5sEhdTk0RC/dNwfe1xKD:Wl+ZLALMcMTcv7N5jzTi/dtKD |
MALICIOUS
EXPLOIT has been detected (SURICATA)
- WINWORD.EXE (PID: 3460)
SUSPICIOUS
Connects to the server without a host name
- WINWORD.EXE (PID: 3460)
INFO
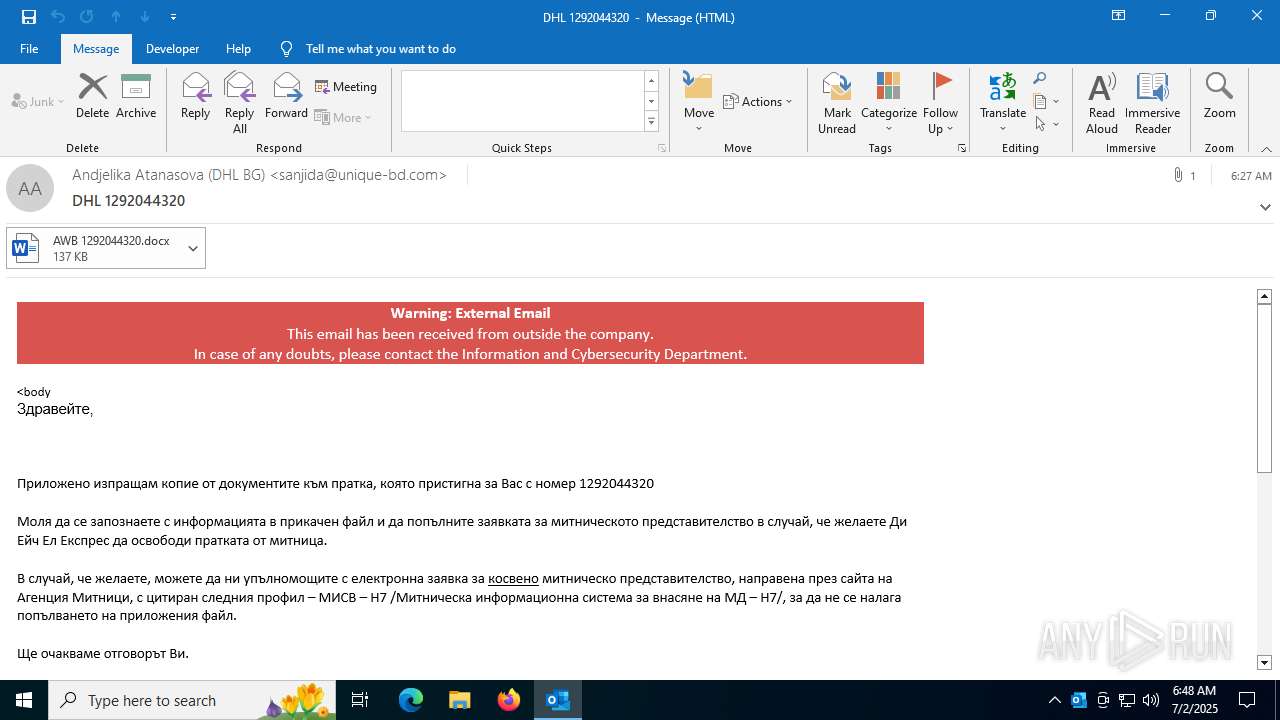
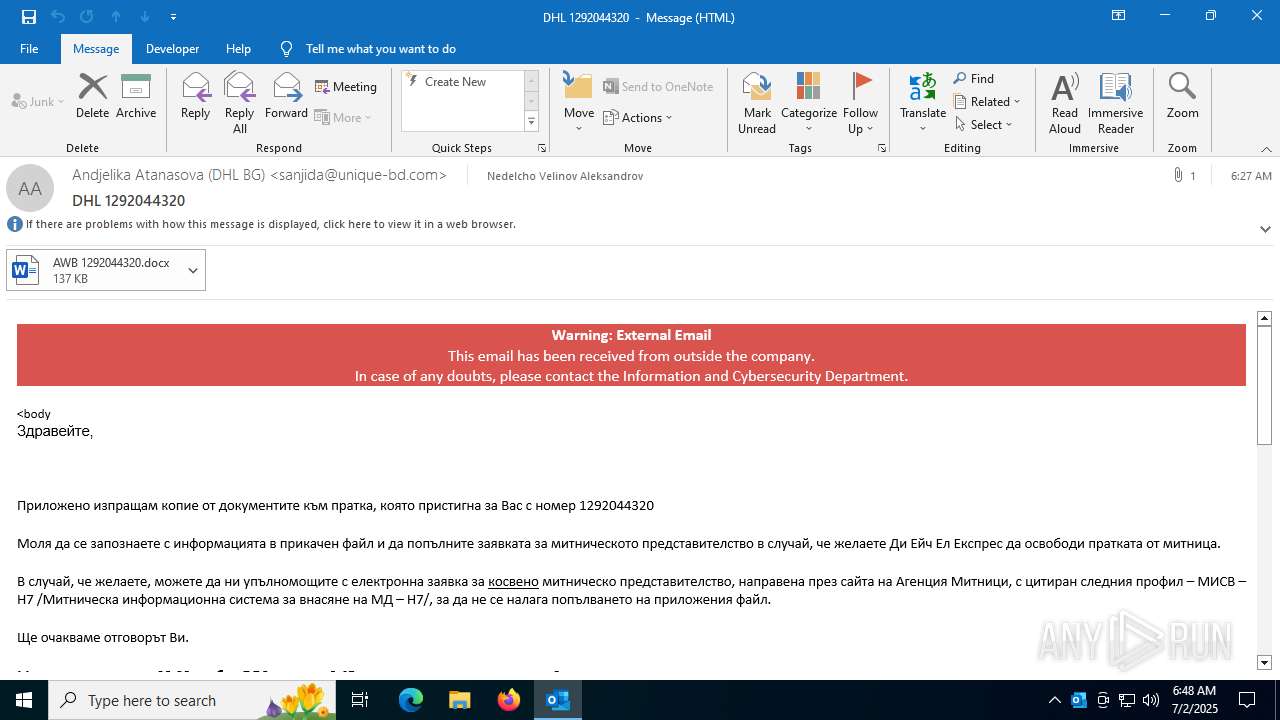
Email with attachments
- OUTLOOK.EXE (PID: 440)
Checks proxy server information
- slui.exe (PID: 4960)
Reads the software policy settings
- slui.exe (PID: 4960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
144
Monitored processes
5
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml C:\Users\admin\AppData\Local\Temp\phish_alert_iocp_v1.4.85.eml | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
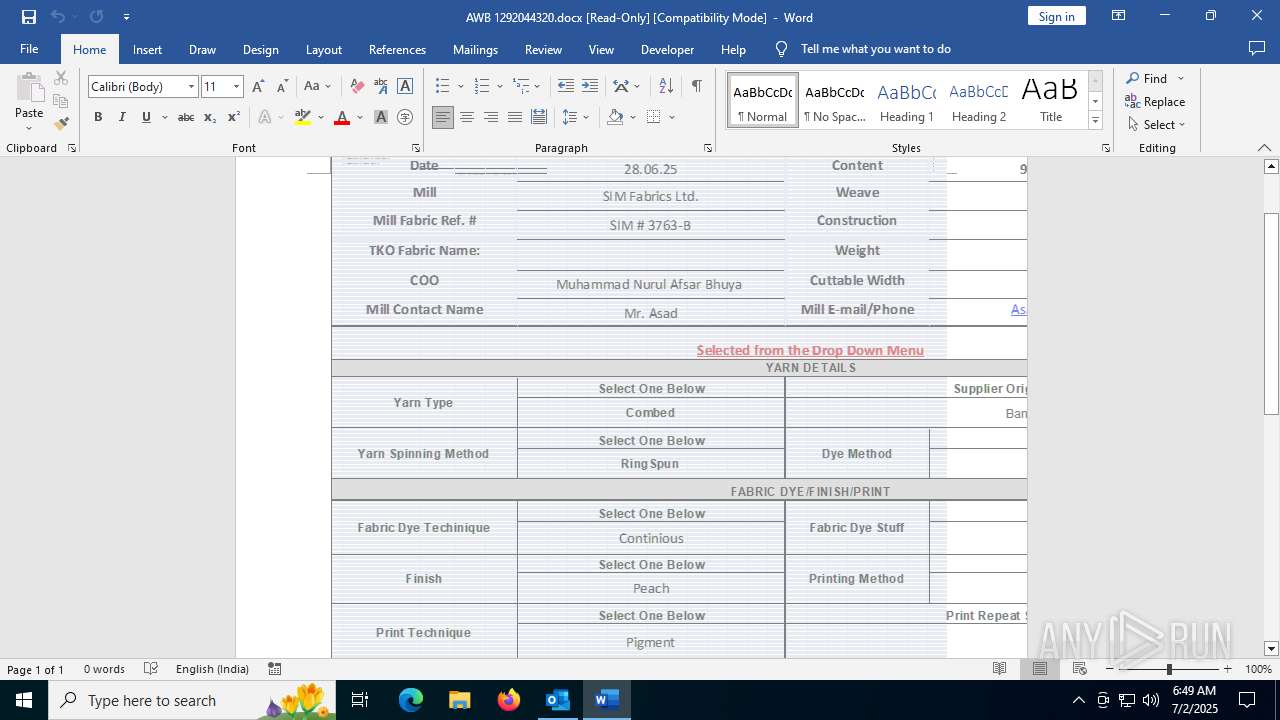
| 3460 | "C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\OAJT1433\AWB 1292044320.docx" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 3476 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "38C8FFB2-B9C4-4862-9F05-3BDD2F99B9FF" "22C865FA-F678-4149-9ECA-319C66D26A6E" "3460" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 3948 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "1E090A18-D2B5-485A-B075-D95B63598006" "6FD3124F-B9CD-4B87-9EAE-168B6581C1AE" "440" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 4960 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
25 856
Read events
24 257
Write events
1 423
Delete events
176
Modification events
| (PID) Process: | (440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\440 |
| Operation: | write | Name: | 0 |
Value: 0B0E102FDBA65EA8DB6E4B91CCC8C1A8CA1FF5230046CAB6D29AD4E3FAED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511B803D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
0
Suspicious files
122
Text files
55
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 440 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 440 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olk58DE.tmp | compressed | |
MD5:650E9C1B7E41810079247D700A2EC58C | SHA256:6BC17CF93AE195D2D5C7A71B8BC04EB5CBDBD7FD203C84CB6556E26E7C7F9607 | |||
| 3460 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:FBC7C057A101B5CB97B3878A8E44E318 | SHA256:0070EE62EE603C5777BCD0FBC18A8F942979BC04B979CDCC19EB60E788CC1AFA | |||
| 440 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | der | |
MD5:28EE921AA7FD32A77B23FC016B5C3651 | SHA256:20735237B3D4FCF7062127C28F0A2F93F1AD60FF041502A2A3DC1EBC068B1C06 | |||
| 440 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\OAJT1433\AWB 1292044320.docx:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 440 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\OAJT1433\AWB 1292044320 (002).docx:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 440 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\OAJT1433\AWB 1292044320 (002).docx | document | |
MD5:336BA033E87DE87638AFCCED163D3337 | SHA256:D17835FE82D637EDCC53DAE88C3C7BE2B2844584167DEA2D75E4BF35CE90B1FA | |||
| 440 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:C6BAC676C7C24EFEF923B4054D8D5E8F | SHA256:AF89501A1BBF7072A7E779FB2143FEDDA32497BFC05917F915A7B78A9275AD5B | |||
| 3460 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\ResourceInfoCache\07fc2a8c43a1d1f16572d21e959a4847e306edae.temp | binary | |
MD5:DDBE6A39C4C09F97CD651D09DEBBFD93 | SHA256:7CB5E62BEEF7864B8AB73C4652A5B6D1B1AB63EC0688360E6D1F8A2B6A6FA936 | |||
| 3460 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\wesdendayagivingbestthingswithgreatpersongoodfor_________wesdendayagivingbestthingswithgreatpersongoodfor________wesdendayagivingbestthingswithgreatpersongoodfor[1].doc | text | |
MD5:92C20CEA3FB3A901F6EE4751FC06AB8D | SHA256:30B01A68DABE5A588131FDBACFD91567BC7A300F17245227FA8F7DEE50E683F2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
90
DNS requests
41
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.18.121.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.20.154.94:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6320 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
440 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
3460 | WINWORD.EXE | HEAD | 200 | 216.9.224.32:80 | http://216.9.224.32/160/uhb/wesdendayagivingbestthingswithgreatpersongoodfor_________wesdendayagivingbestthingswithgreatpersongoodfor________wesdendayagivingbestthingswithgreatpersongoodfor.doc | unknown | — | — | unknown |
3460 | WINWORD.EXE | GET | 200 | 104.18.20.213:80 | http://r11.c.lencr.org/72.crl | unknown | — | — | whitelisted |
3588 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3460 | WINWORD.EXE | HEAD | 200 | 216.9.224.32:80 | http://216.9.224.32/160/uhb/wesdendayagivingbestthingswithgreatpersongoodfor_________wesdendayagivingbestthingswithgreatpersongoodfor________wesdendayagivingbestthingswithgreatpersongoodfor.doc | unknown | — | — | unknown |
3588 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3460 | WINWORD.EXE | GET | — | 2.16.241.14:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2664 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
440 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
440 | OUTLOOK.EXE | 2.16.168.101:443 | omex.cdn.office.net | Akamai International B.V. | RU | whitelisted |
440 | OUTLOOK.EXE | 52.109.16.3:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1268 | svchost.exe | 2.18.121.147:80 | crl.microsoft.com | AKAMAI-AS | FR | whitelisted |
1268 | svchost.exe | 2.20.154.94:80 | www.microsoft.com | Telkom-Internet | ZA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3460 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
3460 | WINWORD.EXE | Misc activity | ET INFO Observed UA-CPU Header |
3460 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
3460 | WINWORD.EXE | Potentially Bad Traffic | ET HUNTING Microsoft Office User-Agent Requesting A Doc File |
3460 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
3460 | WINWORD.EXE | Misc activity | ET USER_AGENTS Microsoft Office Existence Discovery User-Agent |
3460 | WINWORD.EXE | Misc Attack | EXPLOIT [ANY.RUN] Obfuscated RTF document including the CLSID of the Equation Editor (CVE-2017-11882) |
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|