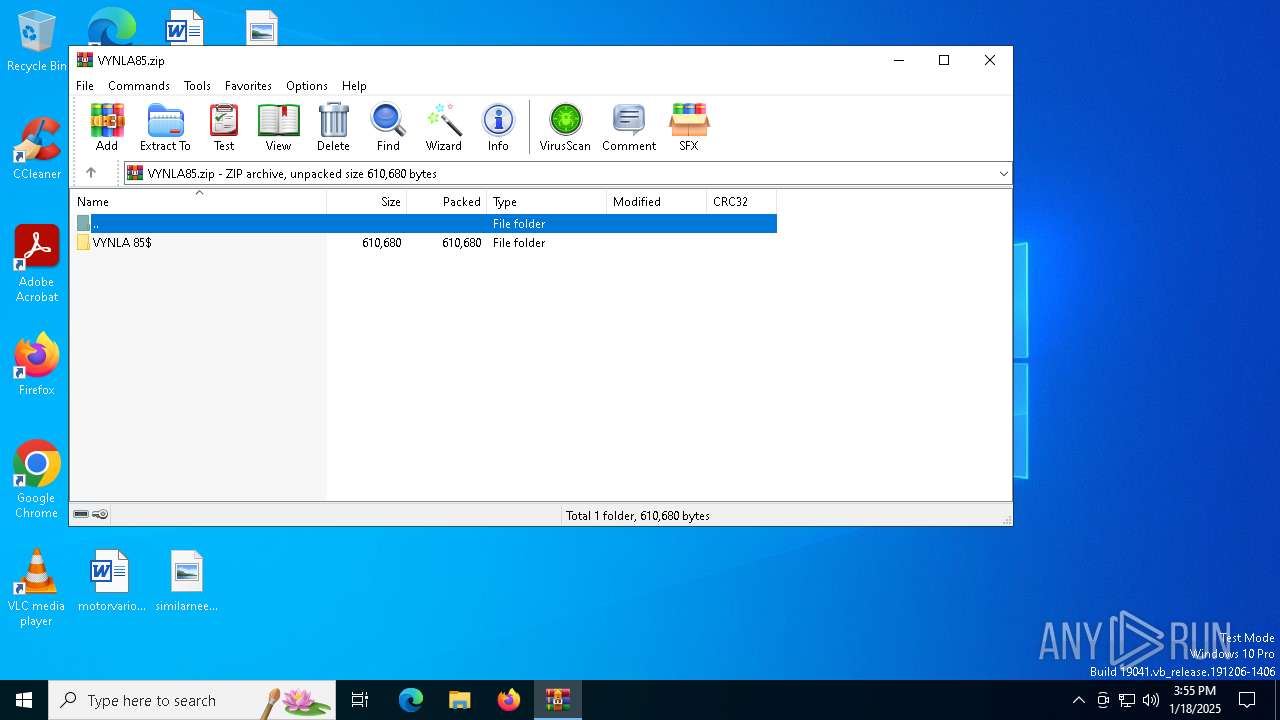
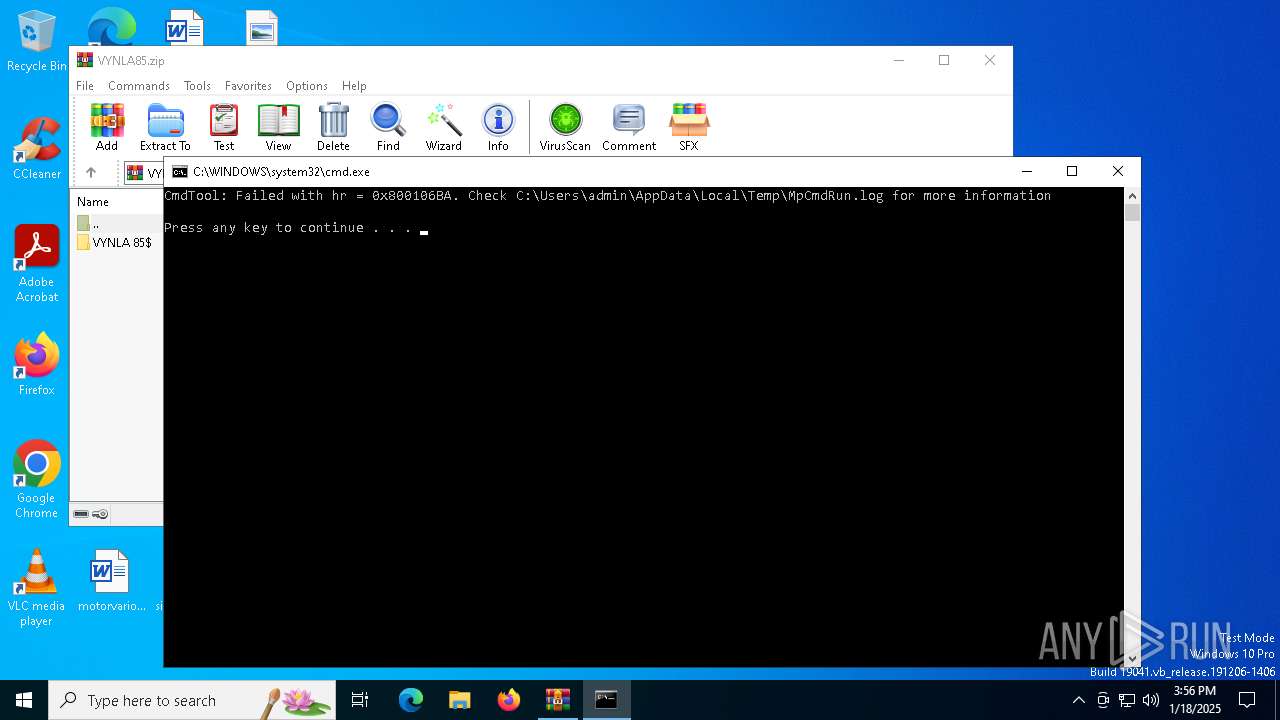
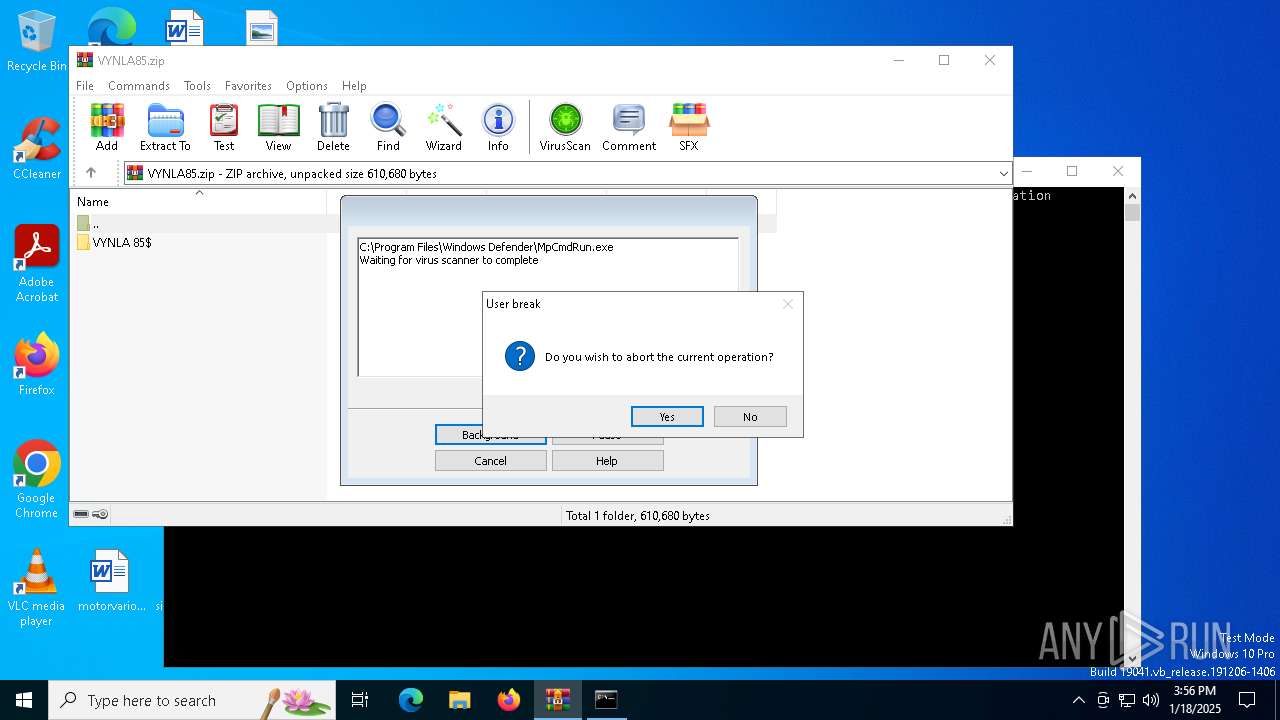
| File name: | VYNLA85.zip |
| Full analysis: | https://app.any.run/tasks/b15e3383-dad8-4155-8b63-5b614bc8ee97 |
| Verdict: | Malicious activity |
| Analysis date: | January 18, 2025, 15:55:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | BF5789285A91F5932B6AE4A90F8D9DDE |
| SHA1: | BFABAAFC617381CB2ABDE85C45F0275EDD47780C |
| SHA256: | 3AC5E00D4E1CE29D586D253985752560C2CFBC7E0CF18D12385DA97B74EF1CA1 |
| SSDEEP: | 24576:FObUHDV2+CA9gwYVo2cUBmUNdTqz/WHWN/GwJC:FObUHDV0A9gwYe2cUBmUNdTqz/WHWN/C |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1864)
- StartMenuExperienceHost.exe (PID: 848)
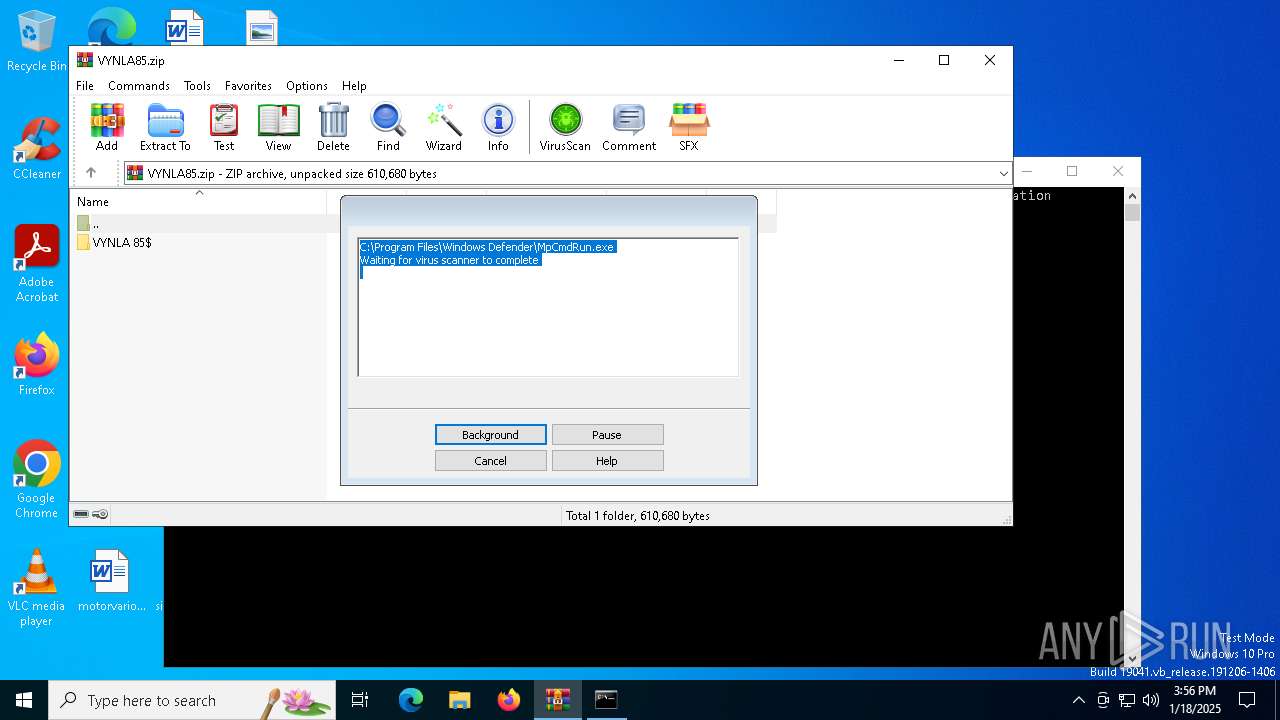
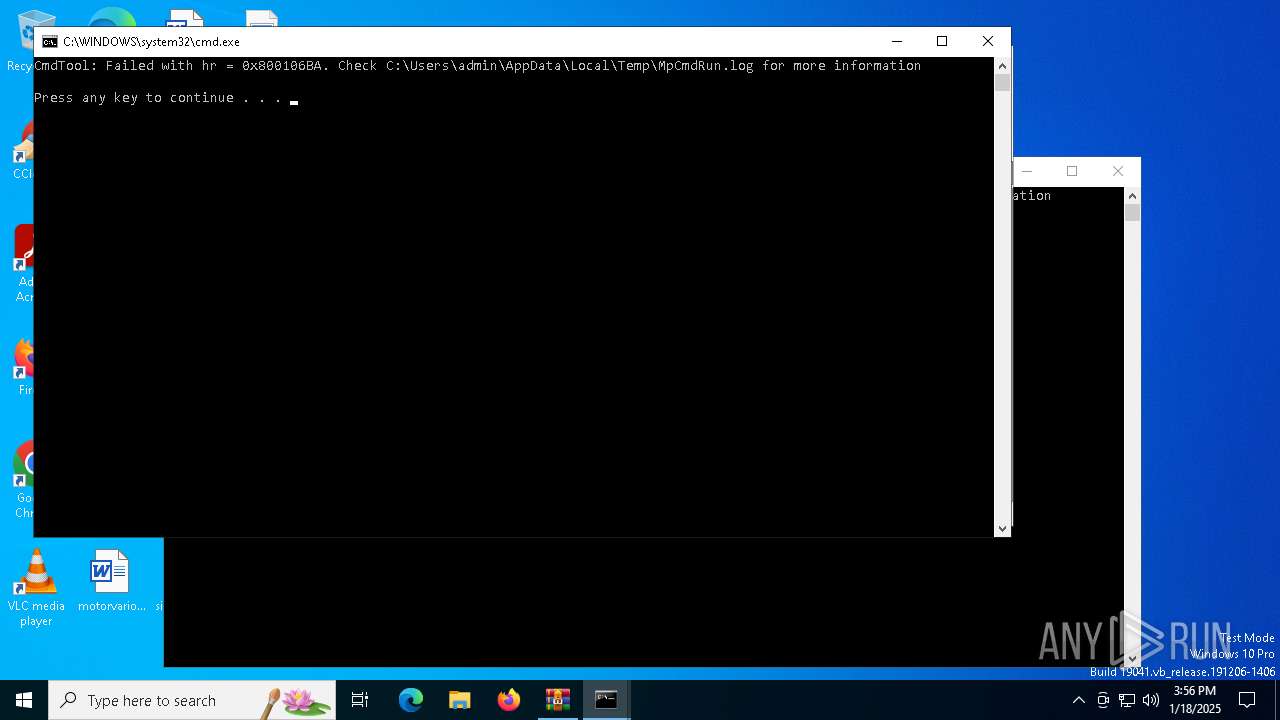
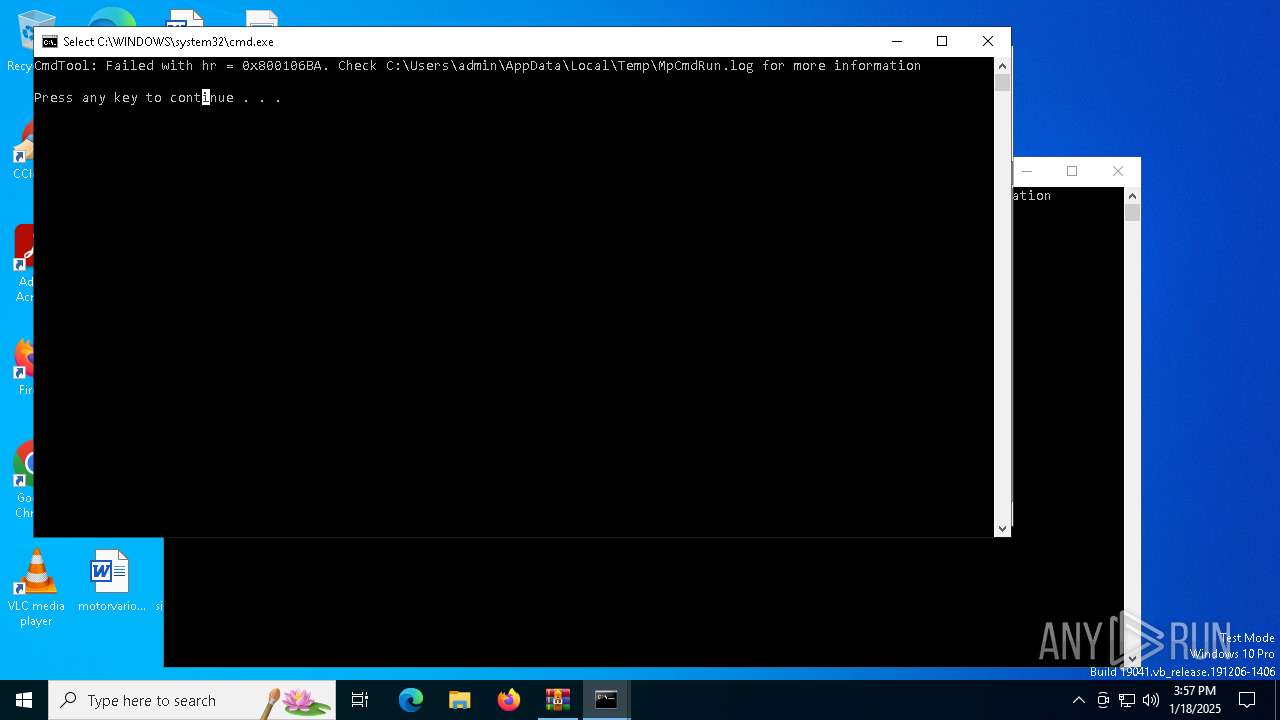
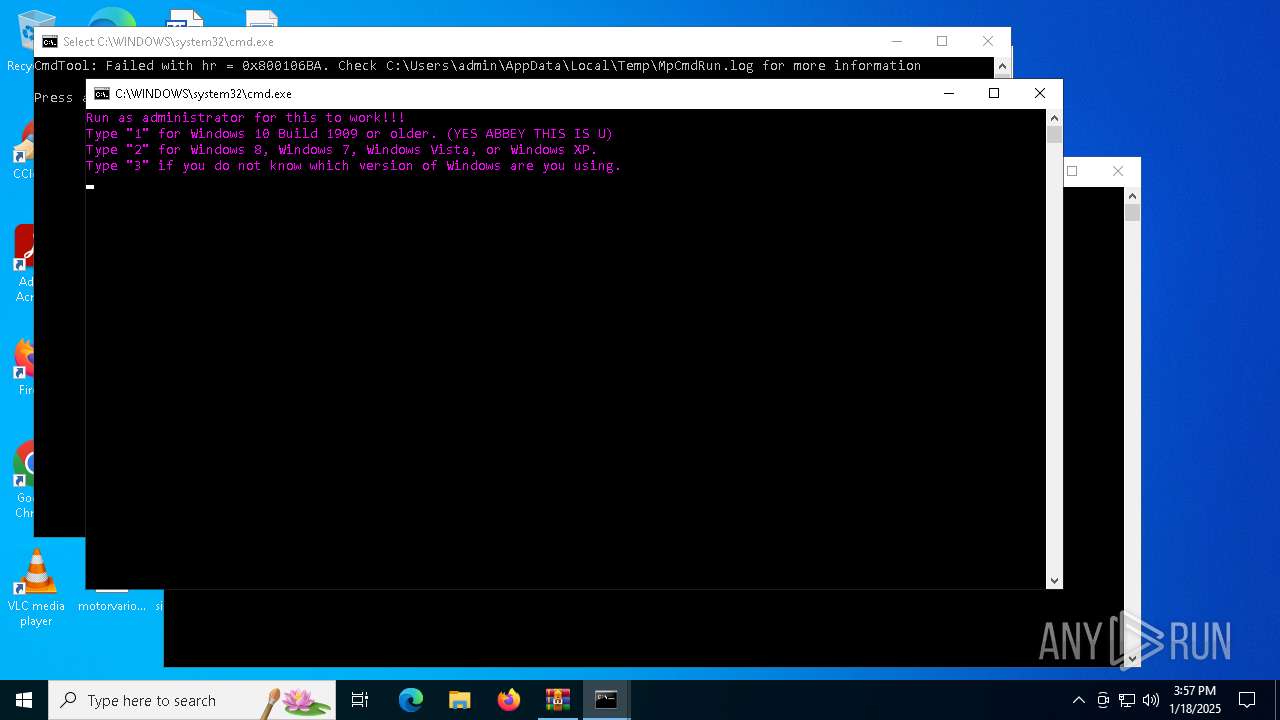
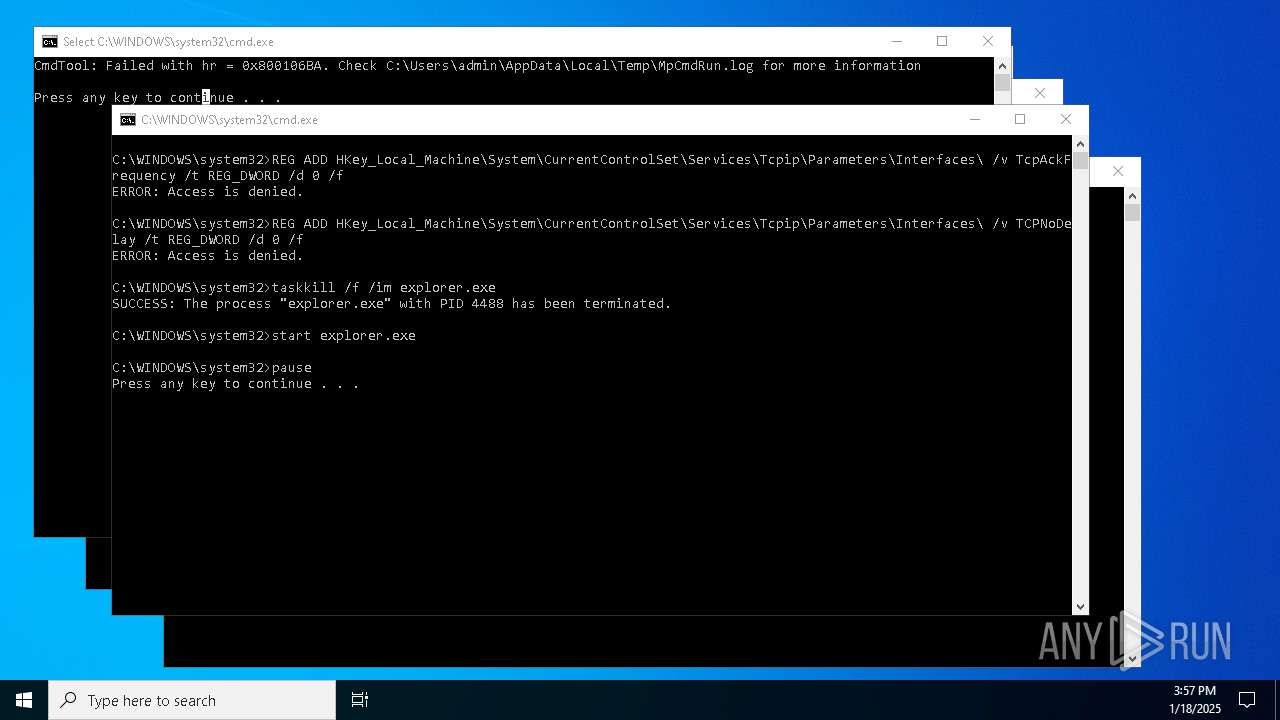
Executing commands from a ".bat" file
- WinRAR.exe (PID: 1864)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 1864)
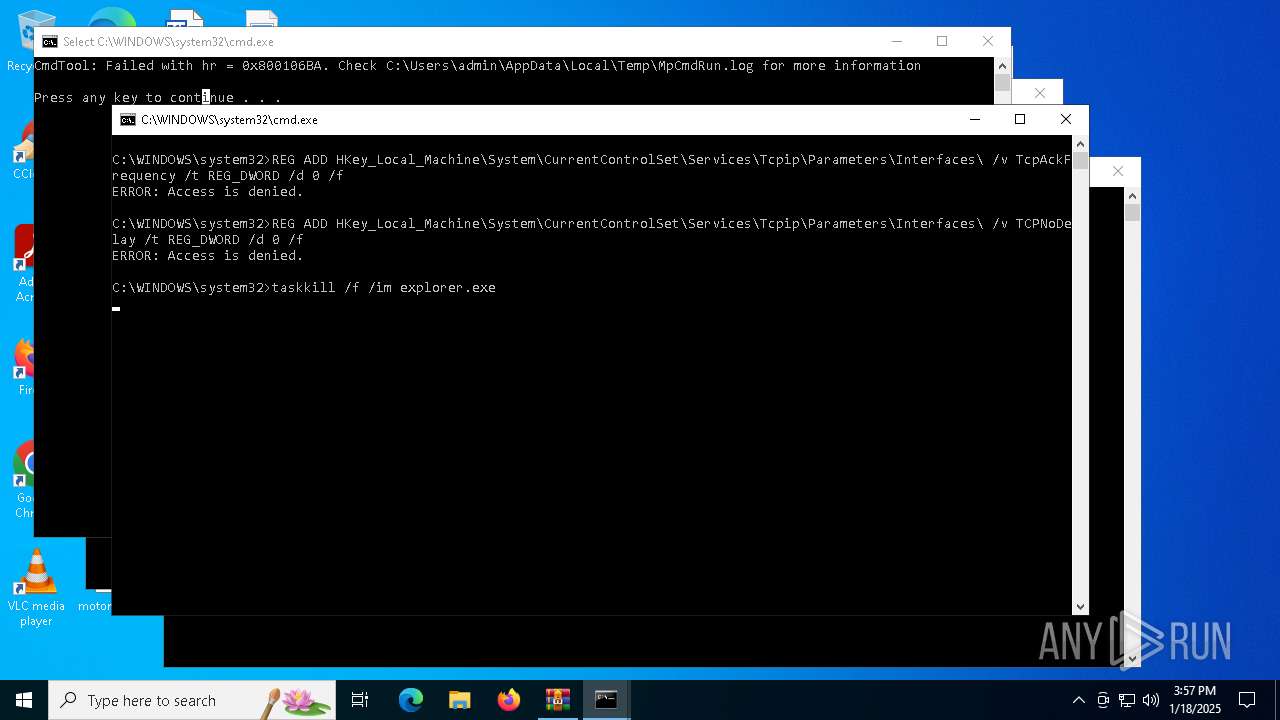
Suspicious use of NETSH.EXE
- cmd.exe (PID: 1688)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 848)
- SearchApp.exe (PID: 4992)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4596)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4596)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 1864)
Checks supported languages
- MpCmdRun.exe (PID: 5748)
- MpCmdRun.exe (PID: 2136)
- TextInputHost.exe (PID: 5720)
- StartMenuExperienceHost.exe (PID: 848)
- SearchApp.exe (PID: 4992)
Create files in a temporary directory
- MpCmdRun.exe (PID: 5748)
Disables trace logs
- netsh.exe (PID: 3364)
Reads the computer name
- MpCmdRun.exe (PID: 5748)
- MpCmdRun.exe (PID: 2136)
- StartMenuExperienceHost.exe (PID: 848)
- TextInputHost.exe (PID: 5720)
- SearchApp.exe (PID: 4992)
Manual execution by a user
- cmd.exe (PID: 4596)
- cmd.exe (PID: 5588)
- cmd.exe (PID: 1688)
Reads security settings of Internet Explorer
- explorer.exe (PID: 2280)
Reads the software policy settings
- SearchApp.exe (PID: 4992)
Sends debugging messages
- StartMenuExperienceHost.exe (PID: 848)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 848)
- SearchApp.exe (PID: 4992)
Checks proxy server information
- explorer.exe (PID: 2280)
- SearchApp.exe (PID: 4992)
Reads Environment values
- SearchApp.exe (PID: 4992)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 4992)
Creates files or folders in the user directory
- explorer.exe (PID: 2280)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | None |
| ZipModifyDate: | 2023:09:08 22:36:38 |
| ZipCRC: | 0xea69f247 |
| ZipCompressedSize: | 442 |
| ZipUncompressedSize: | 442 |
| ZipFileName: | VYNLA 85$/DELAY PRO NA PLAYERS/Attributes.reg |
Total processes
139
Monitored processes
22
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1572 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR1864.8839\Rar$Scan21959.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1688 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\9. TCP Tune.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1864 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\VYNLA85.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
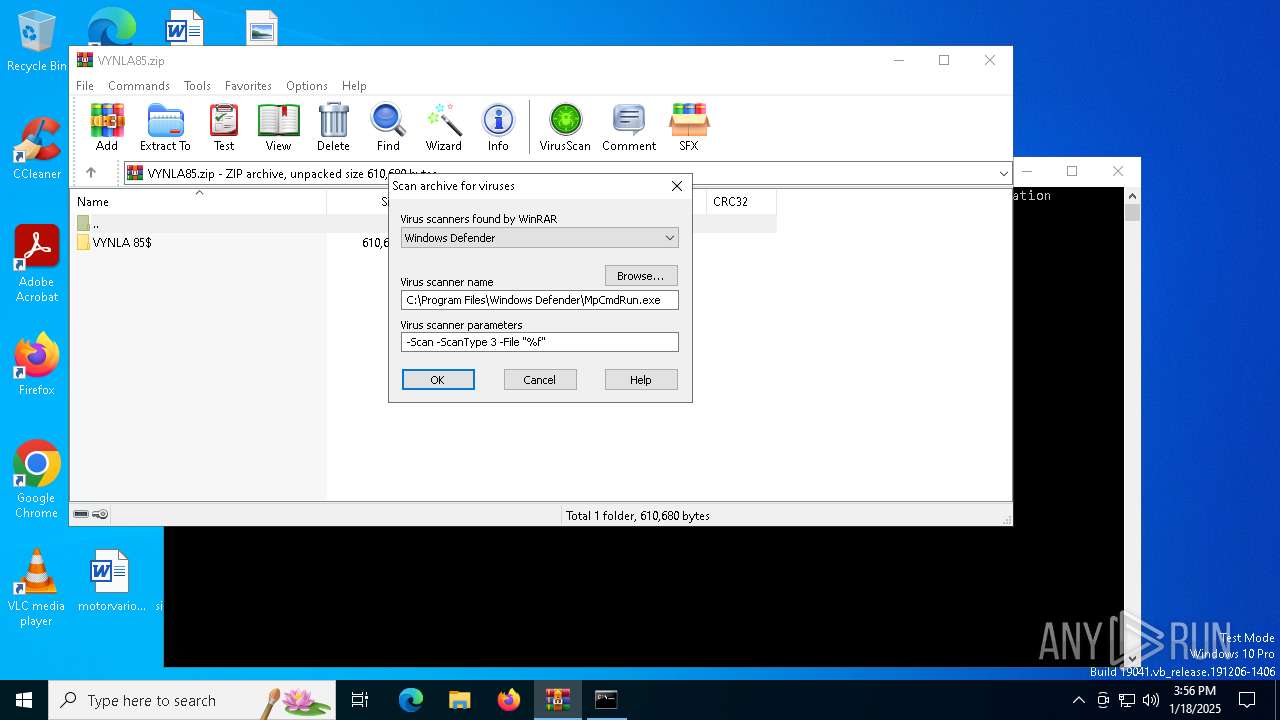
| 2136 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR1864.8839" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2280 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2324 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3140 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3364 | netsh int tcp set global autotuninglevel=disabled | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3420 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
23 593
Read events
23 371
Write events
209
Delete events
13
Modification events
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\VYNLA85.zip | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
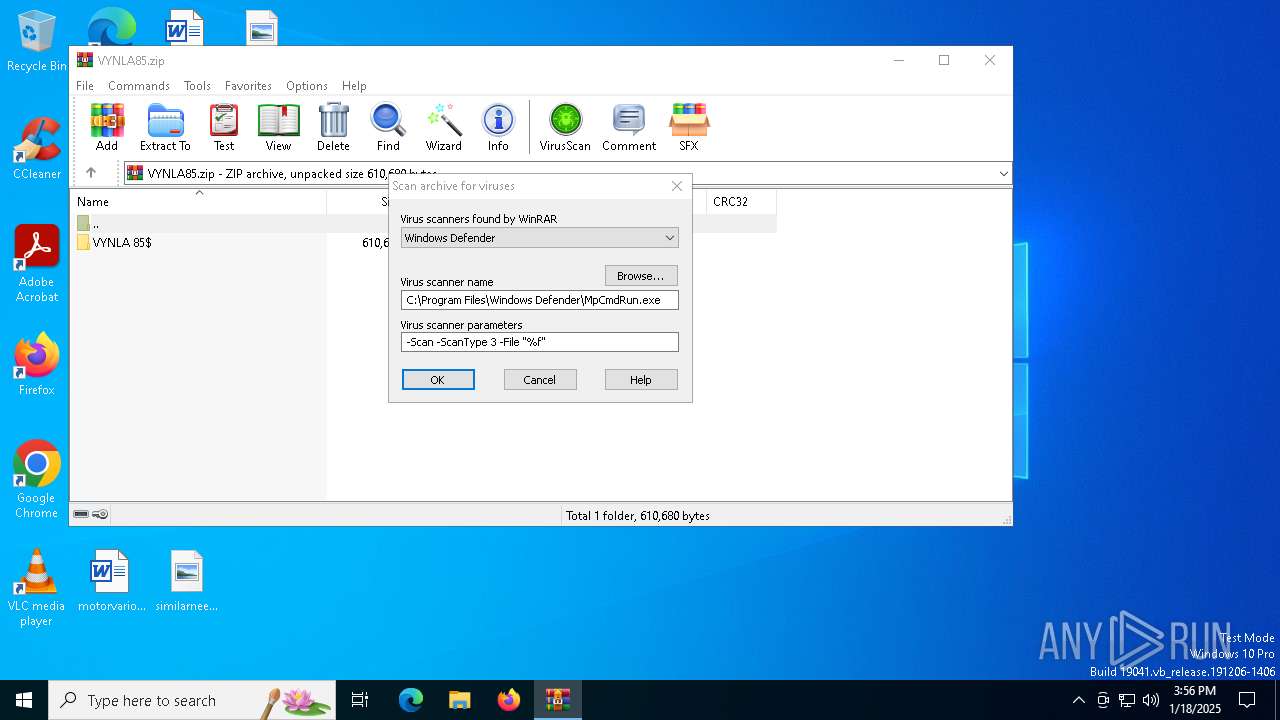
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
| (PID) Process: | (2280) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\CPC\Volume\{2f5c5e72-85a9-11eb-90a8-9a9b76358421} |
| Operation: | write | Name: | Data |
Value: D60D00000DF0ADBA41000000080000000000008000000000000000300000000000000000FF06E703FF00000016000000FA99B7261F00000004400000030000000000000000000000000000000000000000005C005C003F005C00530054004F005200410047004500230056006F006C0075006D00650023007B00390030006300660033006400640036002D0030006100660037002D0031003100650063002D0062003400380030002D003800300036006500360066003600650036003900360033007D002300300030003000300030003000300030003100460035003000300030003000300023007B00350033006600350036003300300064002D0062003600620066002D0031003100640030002D0039003400660032002D003000300061003000630039003100650066006200380062007D000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000005C005C003F005C0056006F006C0075006D0065007B00320066003500630035006500370032002D0038003500610039002D0031003100650062002D0039003000610038002D003900610039006200370036003300350038003400320031007D005C0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000004E005400460053000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0000 | |||
Executable files
2
Suspicious files
6
Text files
124
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1864.7255\VYNLA85.zip\VYNLA 85$\DELAY PRO NA PLAYERS\TOP regedits for delay\VYNLA (6).reg | text | |
MD5:330231968027A75C9527F25713FAA032 | SHA256:23FEDB99100307DD34278FDFBCCEE9CB0CF764087F444F3E492E8E3B096DFFBE | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1864.7255\VYNLA85.zip\VYNLA 85$\DELAY PRO NA PLAYERS\TCPNoDelay.reg | text | |
MD5:3827910CE1FD933092B3E34B035475ED | SHA256:6D46BE15D6C95576CB93327C70E0A54B7F0A5E385E18C19CAF373E4ED4796F5B | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1864.7255\VYNLA85.zip\VYNLA 85$\DELAY PRO NA PLAYERS\TcpAckFrequency.reg | text | |
MD5:B1E24290785C63AFD024A560ED354EEC | SHA256:E0C22912B2607A9E336AFA4272270354A27EF8E1CEB258496B4C869977146C2B | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1864.7255\VYNLA85.zip\VYNLA 85$\DELAY PRO NA PLAYERS\TOP regedits for delay\VYNLA (10).reg | text | |
MD5:FB08E25FA6E1F8BDBC6DF3FFCECEF384 | SHA256:DC9F24F65B8E740F7568629B1D0BD6E07A49D5F00296EFD6E231958C13DAD232 | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1864.7255\VYNLA85.zip\VYNLA 85$\DELAY PRO NA PLAYERS\TOP regedits for delay\VYNLA (14).reg | text | |
MD5:B97C454B92A2BFCD55DB6D4FF379A261 | SHA256:593E47184C9094052E2F2F15A56E864CBC8DAD8393B33713B3503D0F27894DB2 | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1864.7255\VYNLA85.zip\VYNLA 85$\DELAY PRO NA PLAYERS\READ BEFORE U RUN IT\VYNLA BEST TWEAK.bat | text | |
MD5:87F2B5F9A73DF862122F26318F6C256A | SHA256:E0E398A5DE9BD8337FD39DED1720B345EDAFA59EAB07E1C67BFBCAF380DADA0A | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1864.7255\VYNLA85.zip\VYNLA 85$\DELAY PRO NA PLAYERS\TOP regedits for delay\VYNLA (2).reg | text | |
MD5:A33A770344437B9A6E7032734F0A2D9D | SHA256:230888C9D1BDABBF898E44AEA761E5C747E472C12982B56D29EDF35FAB089A5E | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1864.7255\VYNLA85.zip\VYNLA 85$\DELAY PRO NA PLAYERS\TOP regedits for delay\VYNLA (15).reg | text | |
MD5:88BBE9129BA3A80EC0C5580273FA6019 | SHA256:05131027B26093A861A25D74C3420314EC1EDE1E002A242E30DA3249E111D5BA | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1864.7255\VYNLA85.zip\VYNLA 85$\DELAY PRO NA PLAYERS\TOP regedits for delay\VYNLA (9).reg | text | |
MD5:7E4BF6DD11A30883D006BDC481344BF1 | SHA256:D31CA5E85FDF4B947F62E3448338A93700CB61A678687C401CF3B98E17BE143C | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1864.7255\VYNLA85.zip\VYNLA 85$\DELAY PRO NA PLAYERS\TOP regedits for delay\VYNLA (1).reg | text | |
MD5:FB6C5FAC6A5866186C446A86C7B6E3F1 | SHA256:AC5B3C9B7B7D5F6CD2BB7700E57FF41A565E5B93DAFCB952A572C53BE12047FD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
21
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 204 | 104.126.37.170:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | unknown |
— | — | POST | 204 | 104.126.37.176:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | unknown |
— | — | GET | 200 | 104.126.37.176:443 | https://www.bing.com/manifest/threshold.appcache | unknown | text | 3.46 Kb | unknown |
— | — | GET | 200 | 104.126.37.171:443 | https://www.bing.com/rb/19/cir3,ortl,cc,nc/vOJNaIfAXvJzmnBm845ss-M9YR8.css?bu=B_kCWecCzwFtbYQD&or=w | unknown | text | 5.97 Kb | unknown |
— | — | GET | 200 | 104.126.37.123:443 | https://www.bing.com/rb/16/jnc,nj/Swi4yFavETfuSZ9mHxnUvb4UdTw.js?bu=Dis0fYwBkQGUAYkBggGGAcwBzwE0wAHSAQ&or=w | unknown | s | 21.4 Kb | unknown |
— | — | GET | 200 | 104.126.37.163:443 | https://www.bing.com/rb/18/jnc,nj/6hU_LneafI_NFLeDvM367ebFaKQ.js?bu=DyIrb3t-gQF4cnWyAbUBK6UBK7gB&or=w | unknown | s | 21.3 Kb | unknown |
— | — | GET | 200 | 104.126.37.179:443 | https://www.bing.com/rb/6i/cir3,ortl,cc,nc/wU-YmSK-j9YaNg2gj_x4wAl_UoI.css?bu=M8cKwQrNCsEKsQvBCrcLwQrBCsEKwgvBCskLwQrPC8EK1QvBCtsLwQrfCsEK5QrBCtkKwQrBCqgLwQr0CsEK-grBCu4KwQqAC4oLjQvBCsEKpQuTC8EKmQucC8EKhwzBCuELwQrADA&or=w | unknown | text | 444 Kb | unknown |
— | — | GET | 200 | 104.126.37.178:443 | https://www.bing.com/AS/API/WindowsCortanaPane/V2/Init | unknown | html | 125 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.155:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.164:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3976 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4992 | SearchApp.exe | 104.126.37.176:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |