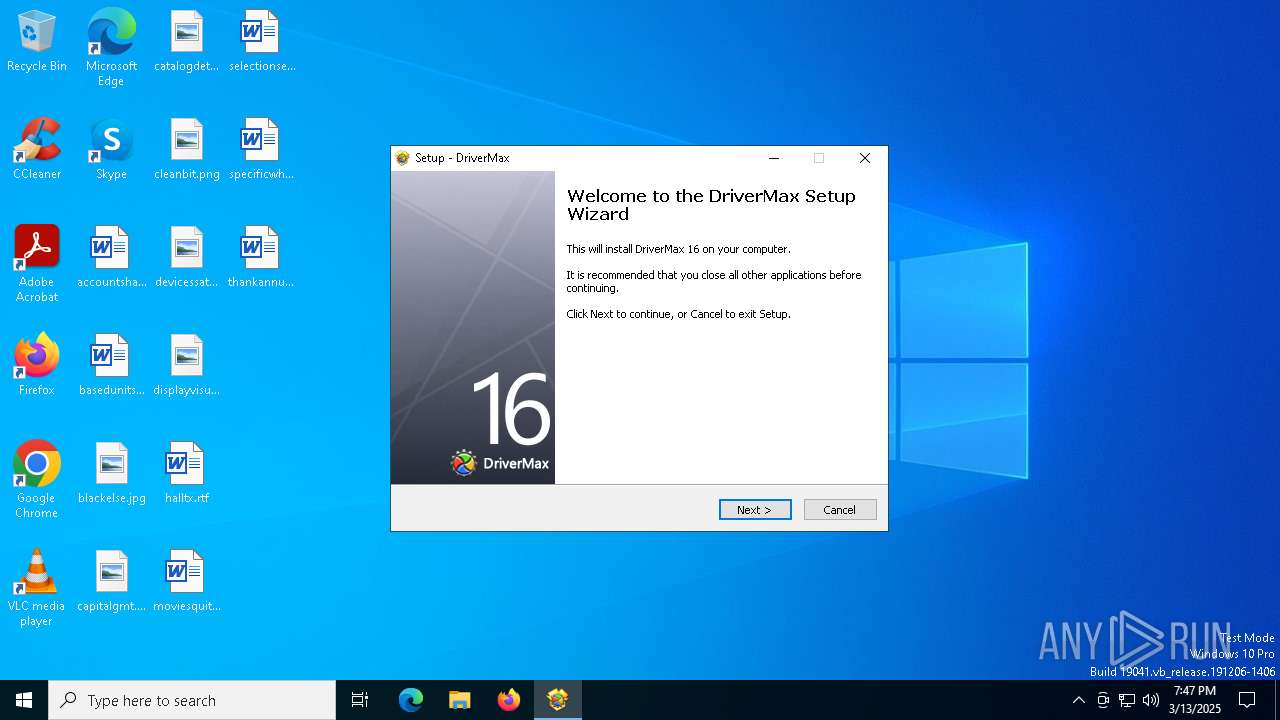
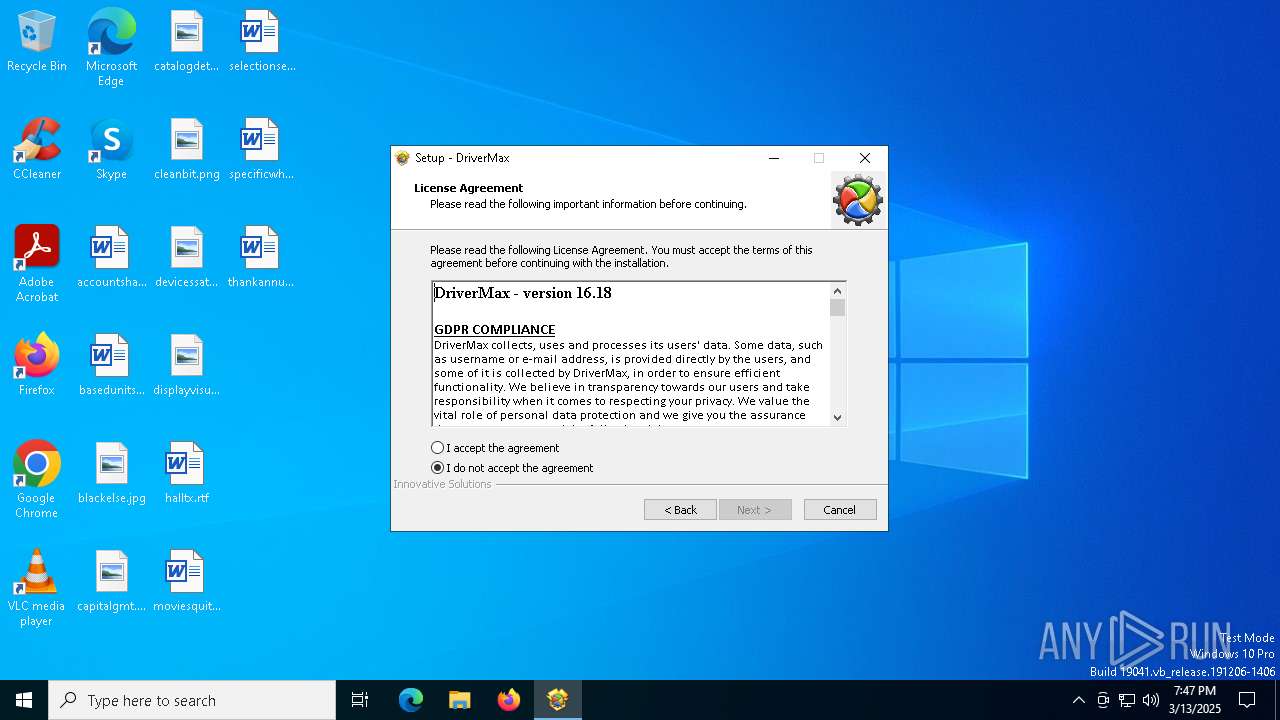
| File name: | drivermax.exe |
| Full analysis: | https://app.any.run/tasks/35326cd5-63b1-4be4-b6f1-58d3d294b9e3 |
| Verdict: | Malicious activity |
| Analysis date: | March 13, 2025, 19:47:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 803C342B5785667D72C5B4F2FB96EDC0 |
| SHA1: | 1AB8C786DE7682EBC6C977433CD884768AFDDB06 |
| SHA256: | 3A8C85A782E347A3497883923AD31B388A8BFBEF9051EB85B4CCAB257051E8F8 |
| SSDEEP: | 98304:0bavbi44C8QhHGK3YztSLfJ7SZfuC4OEUb4DoJ2V7/V60pv8T9rrcI/XkLn+zCeX:kvLMD/GWzR1g |
MALICIOUS
Connects to the CnC server
- drivermax.tmp (PID: 7276)
SUSPICIOUS
Executable content was dropped or overwritten
- drivermax.exe (PID: 4652)
- drivermax.exe (PID: 7256)
- drivermax.tmp (PID: 7276)
- drivermax.exe (PID: 6424)
- drivermax.exe (PID: 920)
Reads security settings of Internet Explorer
- drivermax.tmp (PID: 5720)
- drivermax.tmp (PID: 7276)
Reads the Windows owner or organization settings
- drivermax.tmp (PID: 7276)
Process drops legitimate windows executable
- drivermax.tmp (PID: 7276)
- drivermax.exe (PID: 920)
Checks for external IP
- drivermax.exe (PID: 2392)
- svchost.exe (PID: 2196)
- drivermax.tmp (PID: 7276)
- drivermax.exe (PID: 6424)
- drivermax.exe (PID: 920)
Uses TASKKILL.EXE to kill process
- drivermax.tmp (PID: 7276)
Potential Corporate Privacy Violation
- drivermax.exe (PID: 920)
Drops a system driver (possible attempt to evade defenses)
- drivermax.exe (PID: 6424)
- drivermax.exe (PID: 920)
Starts CMD.EXE for commands execution
- drivermax.exe (PID: 6424)
- drivermax.exe (PID: 920)
INFO
Create files in a temporary directory
- drivermax.exe (PID: 4652)
- drivermax.exe (PID: 7256)
- drivermax.tmp (PID: 7276)
Checks supported languages
- drivermax.exe (PID: 4652)
- drivermax.tmp (PID: 5720)
- drivermax.exe (PID: 7256)
- drivermax.tmp (PID: 7276)
Process checks computer location settings
- drivermax.tmp (PID: 5720)
Reads the computer name
- drivermax.tmp (PID: 5720)
- drivermax.tmp (PID: 7276)
The sample compiled with english language support
- drivermax.tmp (PID: 7276)
- drivermax.exe (PID: 6424)
- drivermax.exe (PID: 920)
Checks proxy server information
- drivermax.tmp (PID: 7276)
Creates files or folders in the user directory
- drivermax.tmp (PID: 7276)
- BackgroundTransferHost.exe (PID: 5956)
Reads the software policy settings
- drivermax.tmp (PID: 7276)
Creates files in the program directory
- drivermax.tmp (PID: 7276)
Reads the machine GUID from the registry
- drivermax.tmp (PID: 7276)
The sample compiled with arabic language support
- drivermax.tmp (PID: 7276)
Application launched itself
- msedge.exe (PID: 5056)
- msedge.exe (PID: 6712)
- msedge.exe (PID: 2772)
Manual execution by a user
- msedge.exe (PID: 2772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (74.3) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (9.6) |
| .scr | | | Windows screen saver (8.8) |
| .exe | | | Win32 Executable (generic) (3) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 40448 |
| InitializedDataSize: | 382976 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa5f8 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
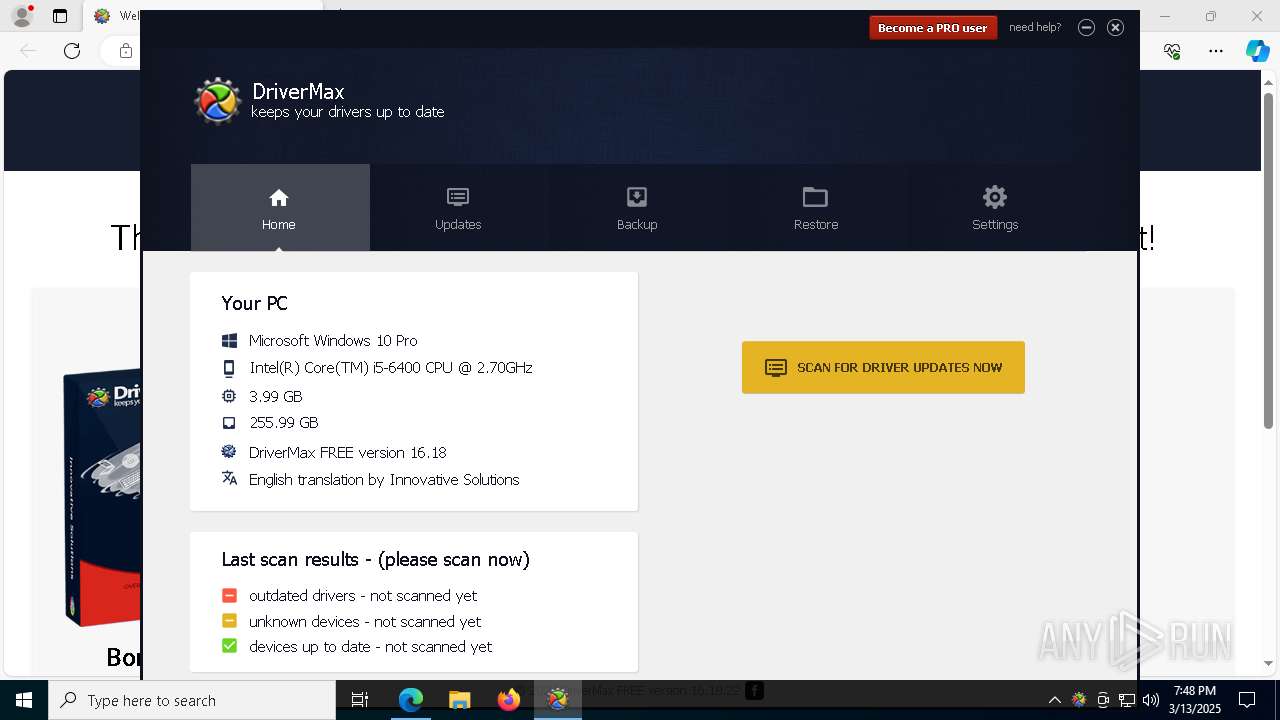
| CompanyName: | Innovative Solutions |
| FileDescription: | DriverMax Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | DriverMax |
| ProductVersion: | 16.18.0.22 |
Total processes
249
Monitored processes
116
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4036 --field-trial-handle=2496,i,9177898251473955988,5791548223932826697,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 856 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | "C:\Program Files (x86)\Innovative Solutions\DriverMax\drivermax.exe" | C:\Program Files (x86)\Innovative Solutions\DriverMax\drivermax.exe | drivermax.tmp | ||||||||||||
User: admin Company: Innovative Solutions Integrity Level: HIGH Description: DriverMax Version: 16.18.0.22 Modules
| |||||||||||||||
| 924 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=5948 --field-trial-handle=2496,i,9177898251473955988,5791548223932826697,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 960 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=4280 --field-trial-handle=2496,i,9177898251473955988,5791548223932826697,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1040 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2232 --field-trial-handle=2364,i,4931757483710068037,614258807683749555,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1180 | "Taskkill.exe" /IM innostp.exe /F | C:\Windows\SysWOW64\taskkill.exe | — | drivermax.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2272 --field-trial-handle=2276,i,6477106376672721591,13319837781136865721,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1532 | "Taskkill.exe" /IM stop_dmx.exe /F | C:\Windows\SysWOW64\taskkill.exe | — | drivermax.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
82 788
Read events
82 257
Write events
462
Delete events
69
Modification events
| (PID) Process: | (7276) drivermax.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | 2A1D6027D94AB10A1C4D915CCD33A0CB3E2D54CB |
Value: | |||
| (PID) Process: | (7276) drivermax.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\2A1D6027D94AB10A1C4D915CCD33A0CB3E2D54CB |
| Operation: | write | Name: | Blob |
Value: 0400000001000000100000005DB66AC46017246A1A99A84BEE5EB426140000000100000014000000804CD6EB74FF4936A3D5D8FCB53EC56AF0941D8C62000000010000002000000071CCA5391F9E794B04802530B363E121DA8A3043BB26662FEA4DCA7FC951A4BD19000000010000001000000086665B2DECDDA69376F98E02CD5FA29A0300000001000000140000002A1D6027D94AB10A1C4D915CCD33A0CB3E2D54CB0F0000000100000030000000DF03EE17776FAE07203AE956F6094206455C833A06297419E38793A34C4E010E8E0DD06107E0CD574F970FB35FB7C04E09000000010000002A000000302806082B0601050507030206082B0601050507030406082B0601050507030106082B060105050703080B0000000100000018000000470054005300200052006F006F00740020005200340000001D00000001000000100000006D81CF5A57E7A81939F2FA048E7CB95020000000010000000E0200003082020A30820191A00302010202106E47A9C88B94B6E8BB3B2AD8A2B2C199300A06082A8648CE3D0403033047310B300906035504061302555331223020060355040A1319476F6F676C65205472757374205365727669636573204C4C43311430120603550403130B47545320526F6F74205234301E170D3136303632323030303030305A170D3336303632323030303030305A3047310B300906035504061302555331223020060355040A1319476F6F676C65205472757374205365727669636573204C4C43311430120603550403130B47545320526F6F742052343076301006072A8648CE3D020106052B8104002203620004F37473A7688B60AE43B835C581307B4B499DFBC161CEE6DE46BD6BD5611835AE40DD73F78991305AEB3CEE857CA240763BA9C6B847D82AE792916A73E9B172399F299FA298D35F5E5886650FA1846506D1DC8BC9C773C88C6A2FE5C4ABD11D8AA3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E04160414804CD6EB74FF4936A3D5D8FCB53EC56AF0941D8C300A06082A8648CE3D040303036700306402306A50527408C470DC9E507421E88D7A21C34F966E15D12235612DFA0837EE196DADDBB2CC7D0734F560192CB534D96F2002300371B1BAA3600B86ED9A086A95689FE2B3E193647C5E93A6DF792D8D85E394CF235D71CCF2B04DD6FE99C894A975A2E3 | |||
| (PID) Process: | (7276) drivermax.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\2A1D6027D94AB10A1C4D915CCD33A0CB3E2D54CB |
| Operation: | write | Name: | Blob |
Value: 5C0000000100000004000000800100001D00000001000000100000006D81CF5A57E7A81939F2FA048E7CB9500B0000000100000018000000470054005300200052006F006F007400200052003400000009000000010000002A000000302806082B0601050507030206082B0601050507030406082B0601050507030106082B060105050703080F0000000100000030000000DF03EE17776FAE07203AE956F6094206455C833A06297419E38793A34C4E010E8E0DD06107E0CD574F970FB35FB7C04E0300000001000000140000002A1D6027D94AB10A1C4D915CCD33A0CB3E2D54CB19000000010000001000000086665B2DECDDA69376F98E02CD5FA29A62000000010000002000000071CCA5391F9E794B04802530B363E121DA8A3043BB26662FEA4DCA7FC951A4BD140000000100000014000000804CD6EB74FF4936A3D5D8FCB53EC56AF0941D8C0400000001000000100000005DB66AC46017246A1A99A84BEE5EB42620000000010000000E0200003082020A30820191A00302010202106E47A9C88B94B6E8BB3B2AD8A2B2C199300A06082A8648CE3D0403033047310B300906035504061302555331223020060355040A1319476F6F676C65205472757374205365727669636573204C4C43311430120603550403130B47545320526F6F74205234301E170D3136303632323030303030305A170D3336303632323030303030305A3047310B300906035504061302555331223020060355040A1319476F6F676C65205472757374205365727669636573204C4C43311430120603550403130B47545320526F6F742052343076301006072A8648CE3D020106052B8104002203620004F37473A7688B60AE43B835C581307B4B499DFBC161CEE6DE46BD6BD5611835AE40DD73F78991305AEB3CEE857CA240763BA9C6B847D82AE792916A73E9B172399F299FA298D35F5E5886650FA1846506D1DC8BC9C773C88C6A2FE5C4ABD11D8AA3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E04160414804CD6EB74FF4936A3D5D8FCB53EC56AF0941D8C300A06082A8648CE3D040303036700306402306A50527408C470DC9E507421E88D7A21C34F966E15D12235612DFA0837EE196DADDBB2CC7D0734F560192CB534D96F2002300371B1BAA3600B86ED9A086A95689FE2B3E193647C5E93A6DF792D8D85E394CF235D71CCF2B04DD6FE99C894A975A2E3 | |||
| (PID) Process: | (7276) drivermax.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Innovative Solutions\DriverMax |
| Operation: | write | Name: | Affiliate |
Value: Inno | |||
| (PID) Process: | (7276) drivermax.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7276) drivermax.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7276) drivermax.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7276) drivermax.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Innovative Solutions\DriverMax |
| Operation: | write | Name: | fc |
Value: DE | |||
| (PID) Process: | (7276) drivermax.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Innovative Solutions\DriverMax |
| Operation: | write | Name: | lc |
Value: DE | |||
| (PID) Process: | (7276) drivermax.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Innovative Solutions\Analytics |
| Operation: | write | Name: | cid |
Value: 92377058-E3FD-4E47-97F5-E38C5B2C8093 | |||
Executable files
73
Suspicious files
444
Text files
110
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4652 | drivermax.exe | C:\Users\admin\AppData\Local\Temp\is-T76LD.tmp\drivermax.tmp | executable | |
MD5:AB126F7F9FF2E7902FF2BBDC1A6D3158 | SHA256:89D0CFA56BACC7981227BF45E2983DD6BFF5BAA359EBF756EF2B171B5668E515 | |||
| 7276 | drivermax.tmp | C:\Program Files (x86)\Innovative Solutions\DriverMax\is-J8MCP.tmp | executable | |
MD5:DDA56268C2B003EA0ECF68982E950F9E | SHA256:61E4D3ED79FD304D8D8E9588A4E4ACDD9193FE44955A3E1CF3BF60A2B8351138 | |||
| 7276 | drivermax.tmp | C:\Users\admin\AppData\Local\Temp\is-L78RK.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 7276 | drivermax.tmp | C:\Users\admin\AppData\Local\Temp\is-L78RK.tmp\folder-images-icon.bmp | image | |
MD5:D393253B0477CCE0D1E2F6E96E1339E9 | SHA256:171092952FE01BACAFEEA6B4C7CF90AF0CA98EB251834F9B9E3E702DC878FA61 | |||
| 7276 | drivermax.tmp | C:\Program Files (x86)\Innovative Solutions\DriverMax\is-UDK97.tmp | executable | |
MD5:7064F23AA18D9DA00FD7502388AE5332 | SHA256:AF29EB812EECD677C4ADDA44C48A8FD146695472B38944583A1736947989B663 | |||
| 7256 | drivermax.exe | C:\Users\admin\AppData\Local\Temp\is-9C8GK.tmp\drivermax.tmp | executable | |
MD5:AB126F7F9FF2E7902FF2BBDC1A6D3158 | SHA256:89D0CFA56BACC7981227BF45E2983DD6BFF5BAA359EBF756EF2B171B5668E515 | |||
| 7276 | drivermax.tmp | C:\Program Files (x86)\Innovative Solutions\DriverMax\Readme\is-7RULS.tmp | text | |
MD5:9F32A7200E53AE9AE7D61D1B2F672165 | SHA256:0369014DDABCC82AFC72E7399C80D8F6C47A4DD2B8C339C52FAF9A480B5DBDB6 | |||
| 7276 | drivermax.tmp | C:\Program Files (x86)\Innovative Solutions\DriverMax\drivermax_launcher.exe | executable | |
MD5:FBBFC34F6425B4139B5794C70CB413F3 | SHA256:4631C6C1BA6DA4FE8AD8CB3BEA1AC6E562FECFE0043EBEC2D6BED39326586191 | |||
| 7276 | drivermax.tmp | C:\Program Files (x86)\Innovative Solutions\DriverMax\drivermax.exe | executable | |
MD5:AACCC6CF17D86CB416C406FCD11A7E2E | SHA256:93D5527E4154ECD9FD8C1AEC31A499858F5BAC44B1FE2576B0A4972549B7DFCE | |||
| 7276 | drivermax.tmp | C:\Program Files (x86)\Innovative Solutions\DriverMax\is-VMDBN.tmp | executable | |
MD5:AACCC6CF17D86CB416C406FCD11A7E2E | SHA256:93D5527E4154ECD9FD8C1AEC31A499858F5BAC44B1FE2576B0A4972549B7DFCE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
103
DNS requests
103
Threats
27
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7276 | drivermax.tmp | GET | 200 | 34.117.59.81:80 | http://ipinfo.io/json | unknown | — | — | whitelisted |
7836 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7836 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3176 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2392 | drivermax.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io/json | unknown | — | — | whitelisted |
5956 | BackgroundTransferHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2392 | drivermax.exe | GET | 200 | 151.101.194.133:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDCCtkc7alS0T%2BWxUPg%3D%3D | unknown | — | — | whitelisted |
6424 | drivermax.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io/json | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.65:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7276 | drivermax.tmp | 34.117.59.81:80 | ipinfo.io | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
7276 | drivermax.tmp | 34.117.59.81:443 | ipinfo.io | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
7276 | drivermax.tmp | 142.250.181.238:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
3176 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ipinfo.io |
| whitelisted |
www.google-analytics.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7276 | drivermax.tmp | Misc activity | ET ADWARE_PUP Drivermax Utility Checkin Activity |
7276 | drivermax.tmp | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ipinfo.io |
7276 | drivermax.tmp | Device Retrieving External IP Address Detected | ET INFO Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
2392 | drivermax.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ipinfo.io |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
6424 | drivermax.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ipinfo.io |
920 | drivermax.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ipinfo.io |
5544 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |