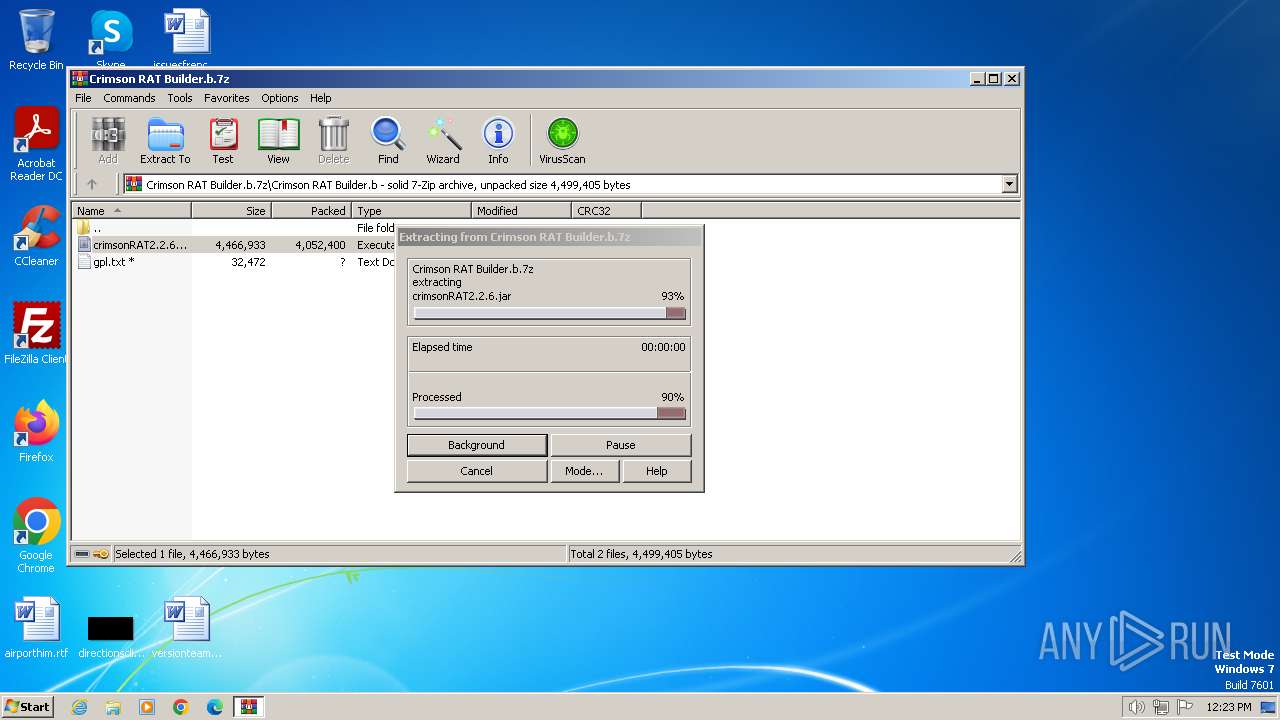
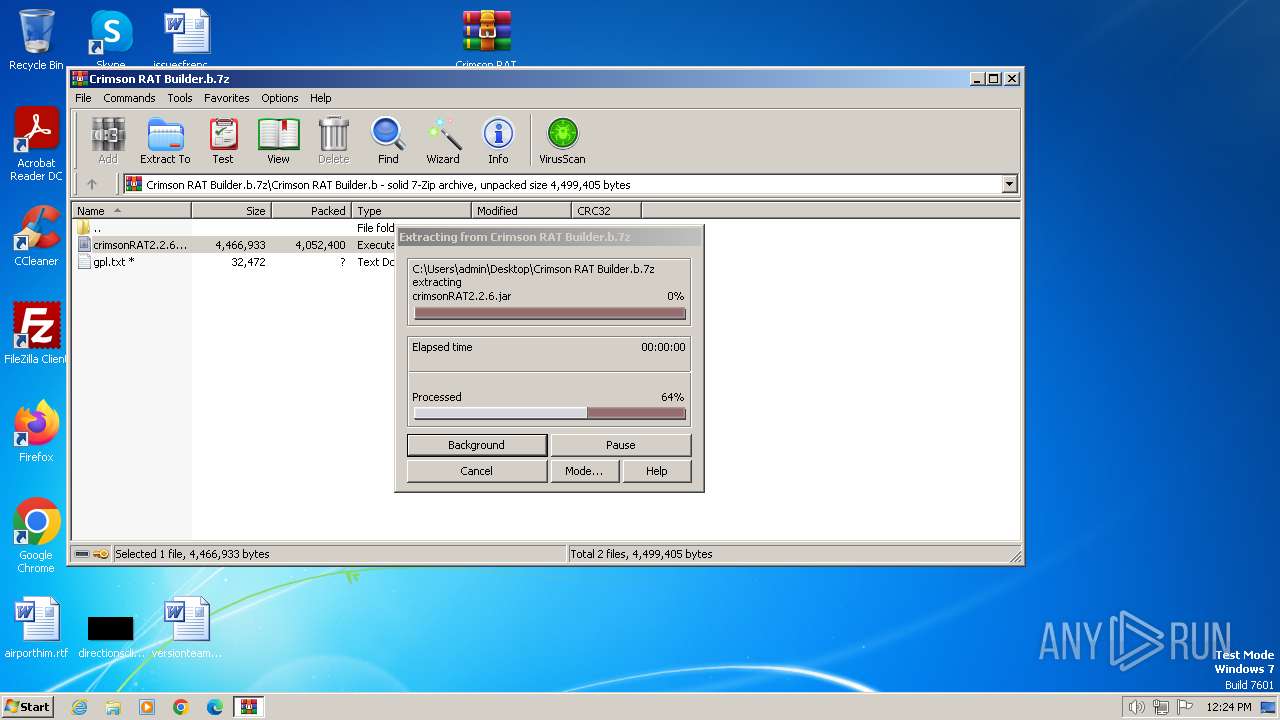
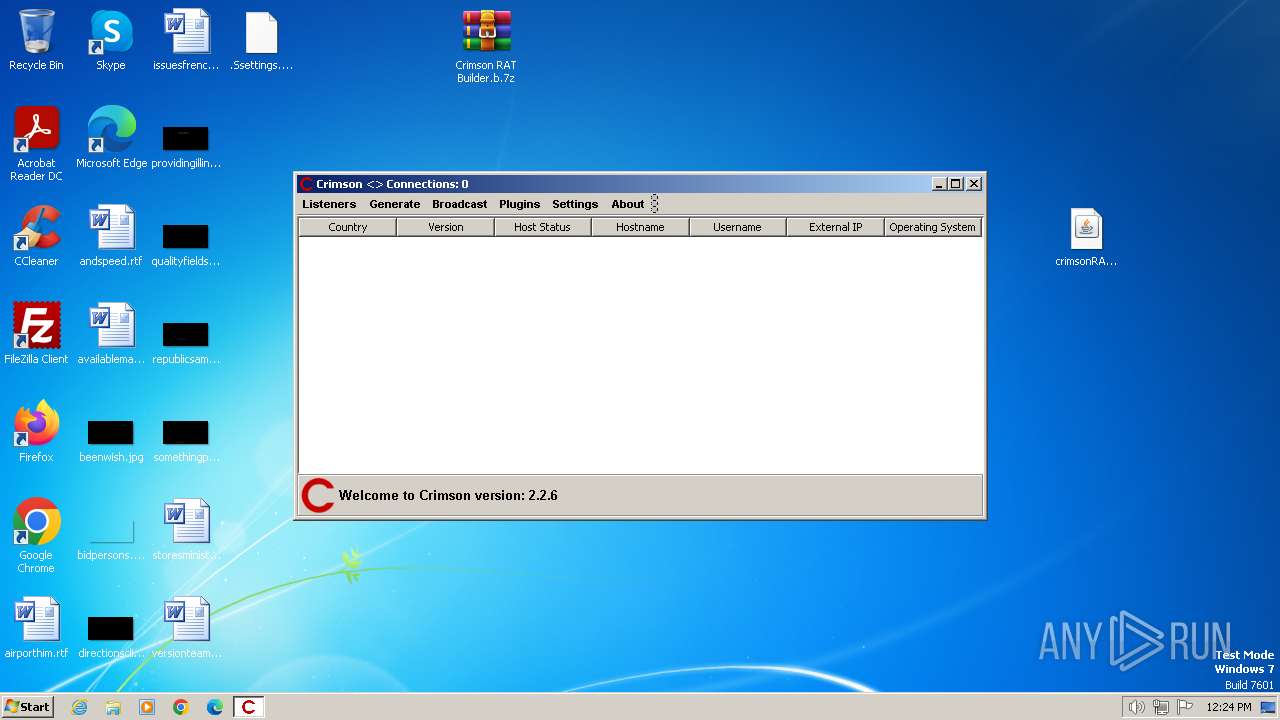
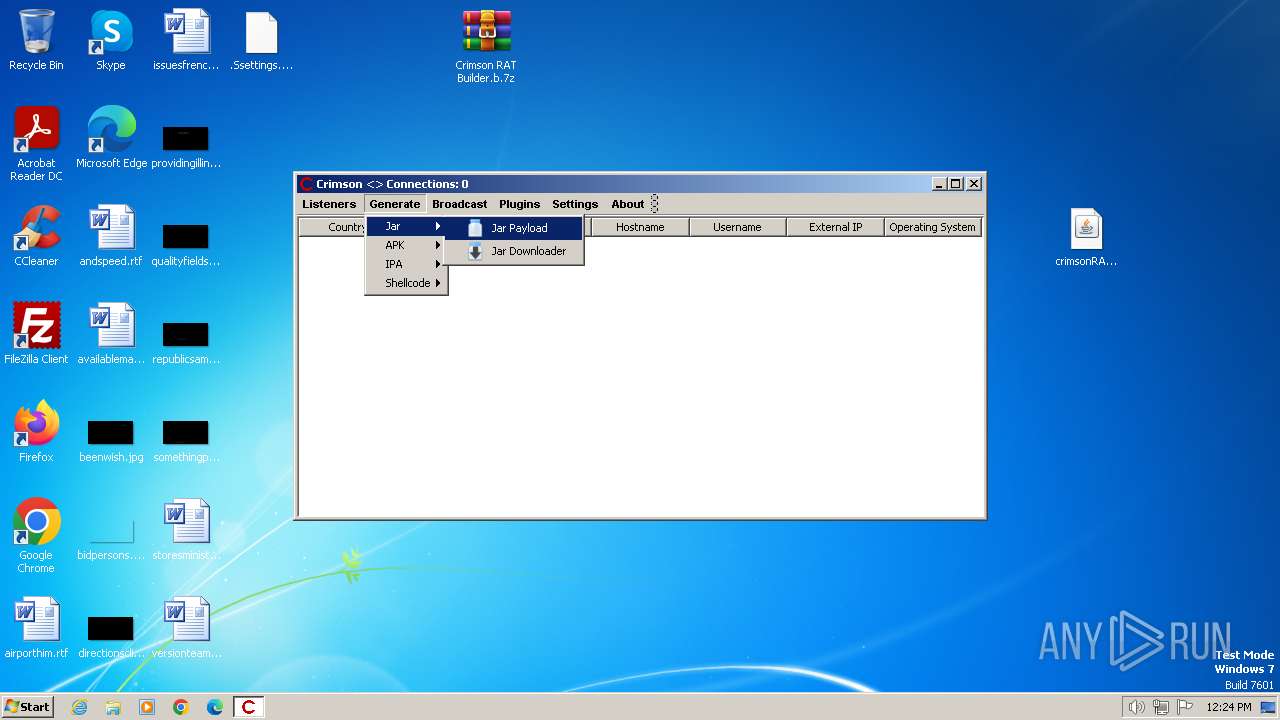
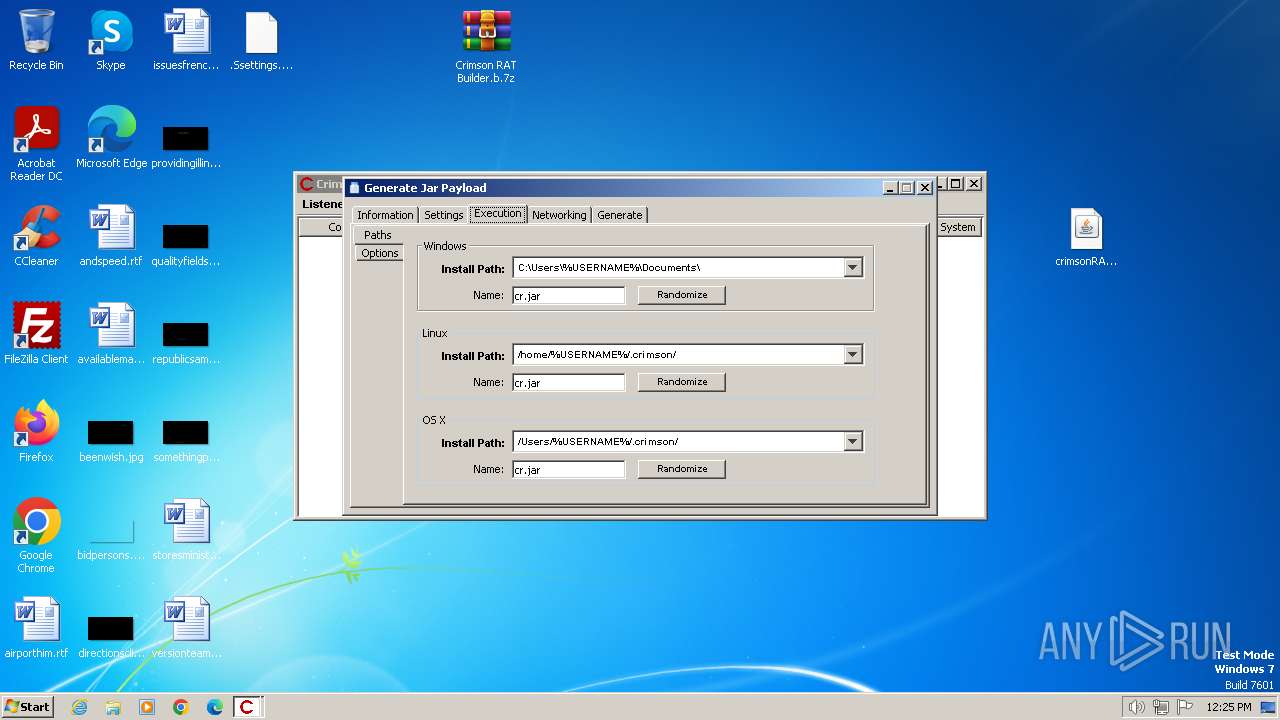
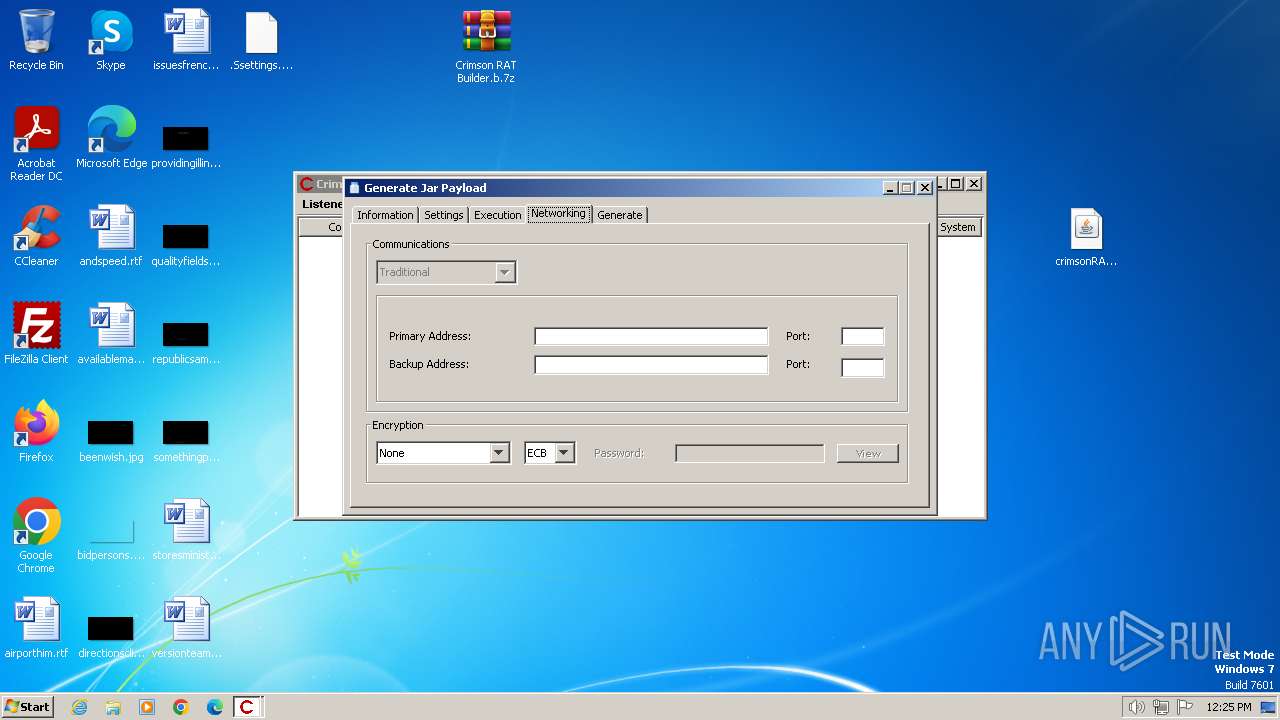
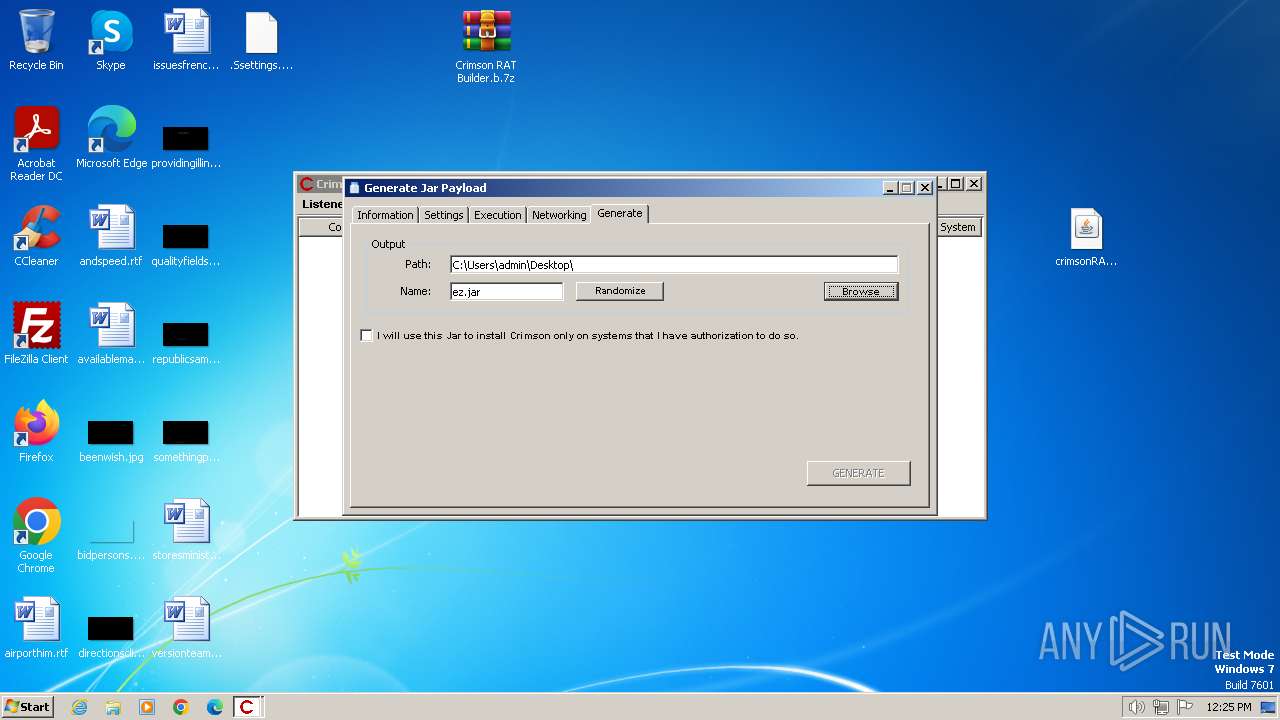
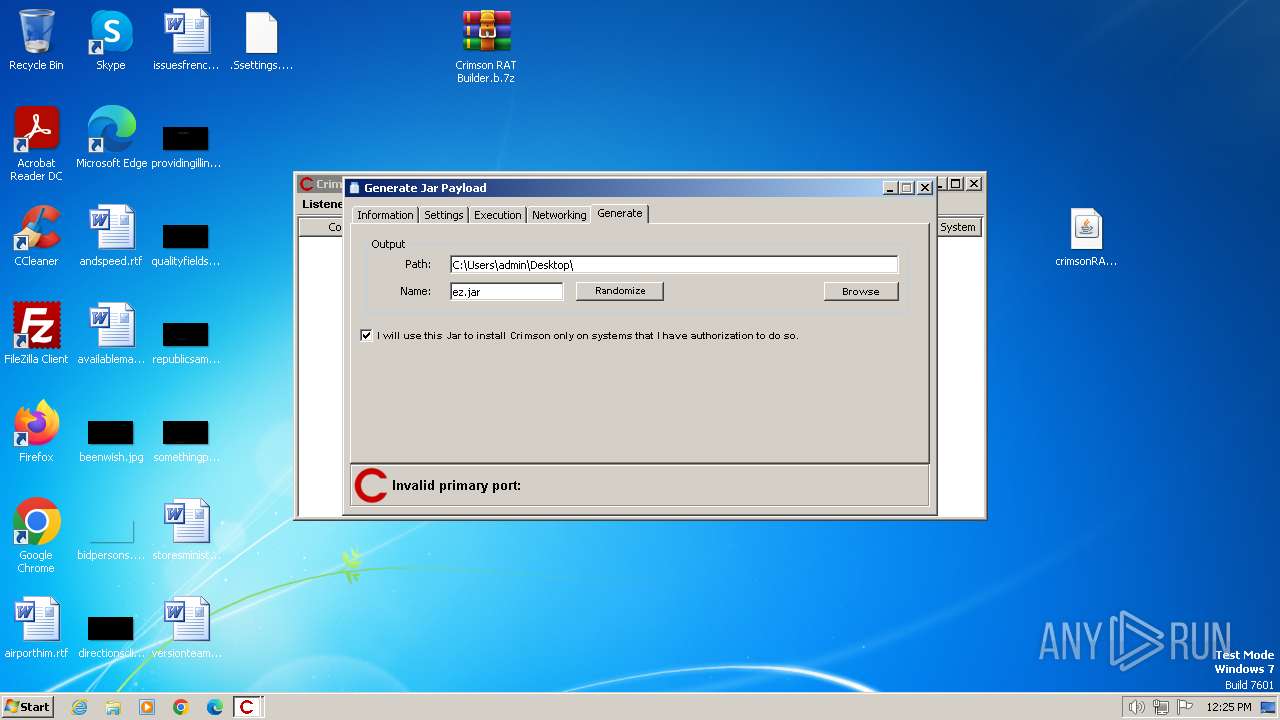
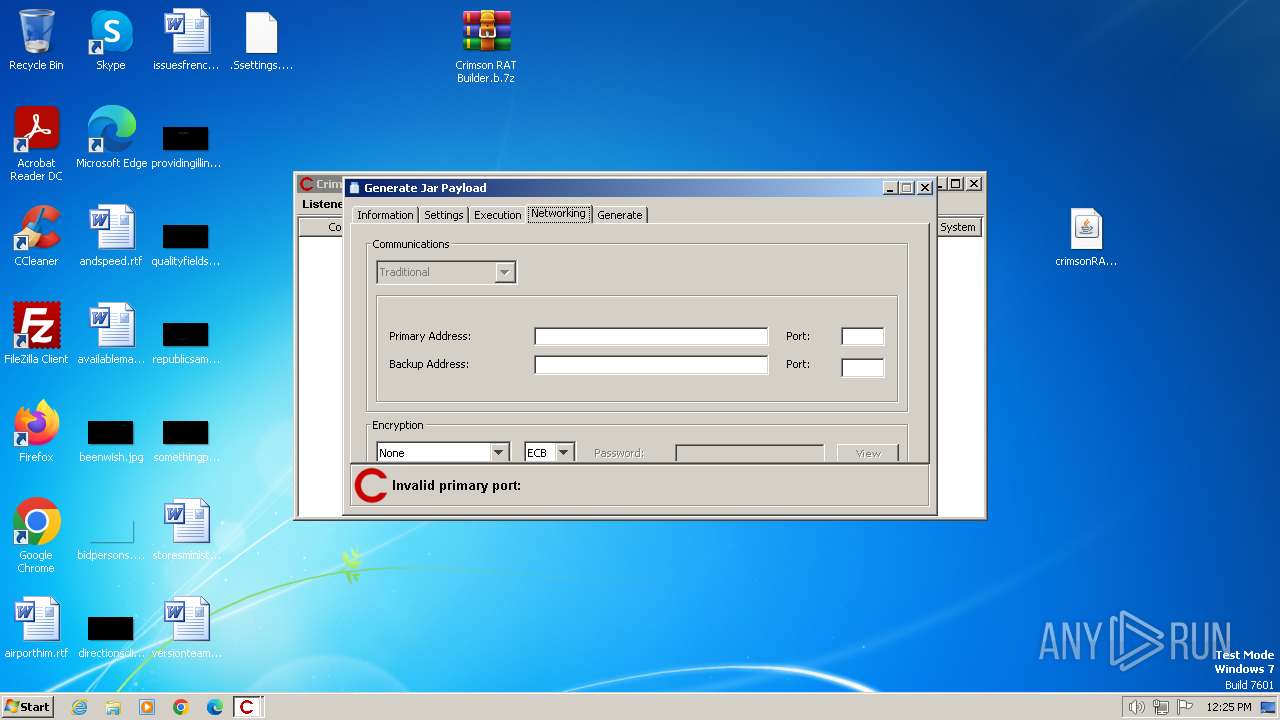
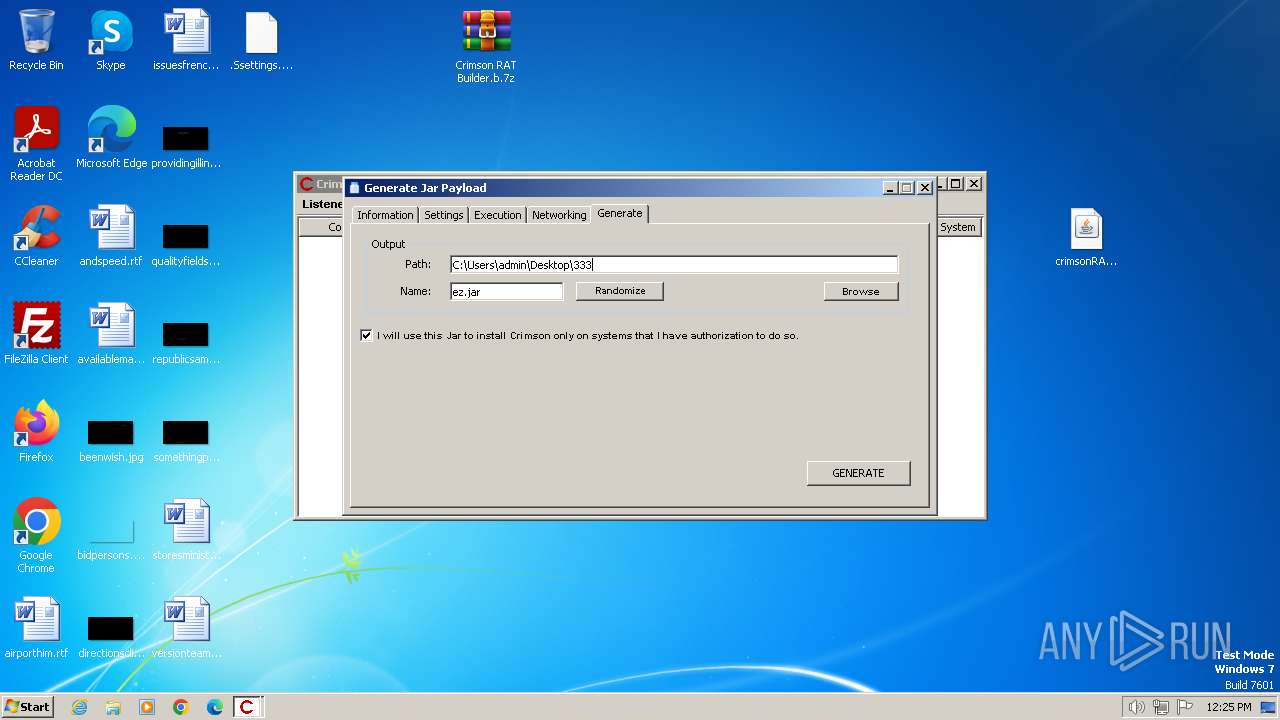
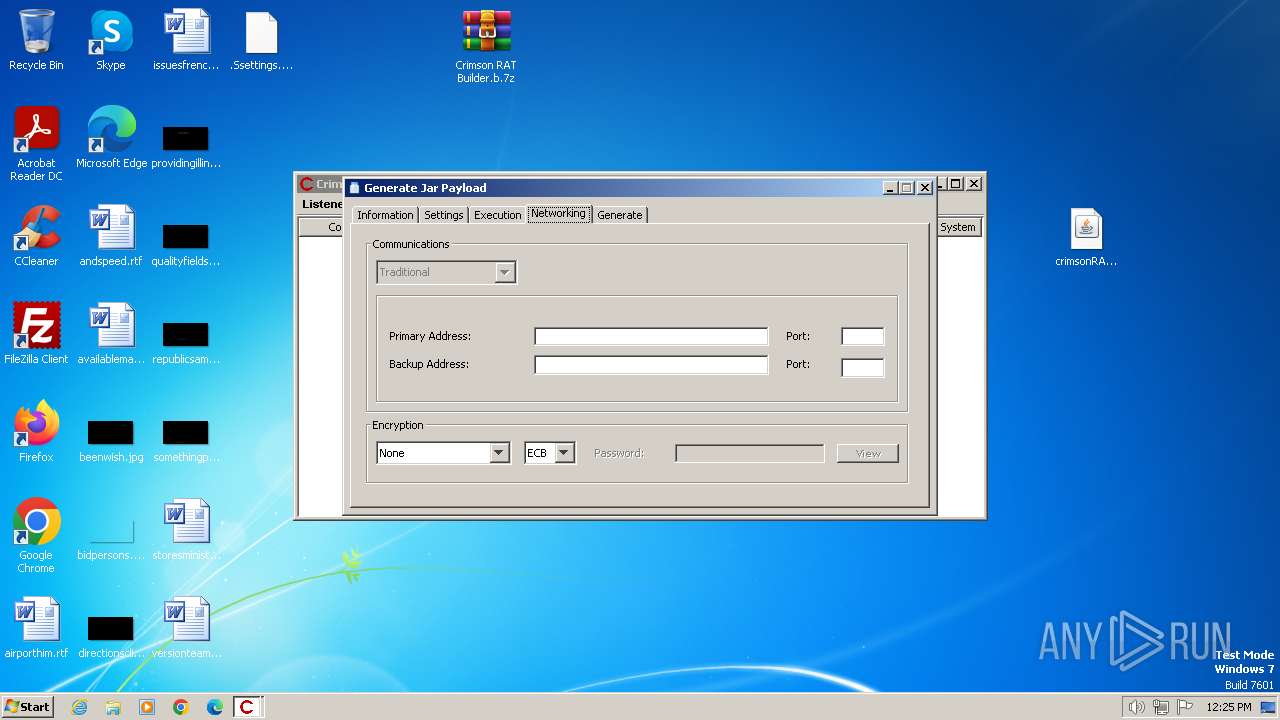
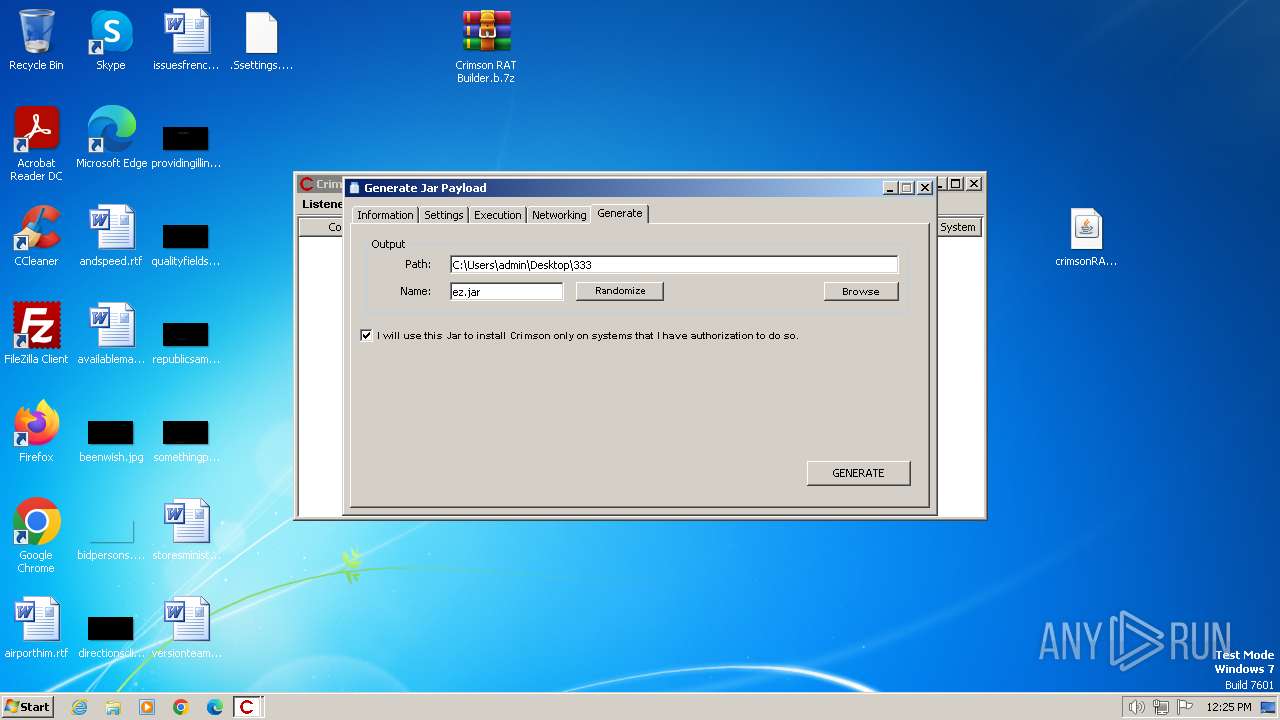
| File name: | Crimson RAT Builder.b.7z |
| Full analysis: | https://app.any.run/tasks/d62dc077-767c-45bc-9b27-fb0f00c7730d |
| Verdict: | Malicious activity |
| Analysis date: | December 29, 2023, 12:22:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 12882048688FCCC08FF7727A69BBF310 |
| SHA1: | 2A9DFDC220E7B90217D37B097577FEBE453B35D8 |
| SHA256: | 3A45283512A5A2A78FB0CC008A216CCDB3F6313B08E85851F380422BD3C65A62 |
| SSDEEP: | 98304:49I7vaB6AUybVprr/2DFWuj3HRBKfuFs9PBSC4lM33RMG+jpqJlpskmUwl/p97E+:4VK/1z4nezYH8V |
MALICIOUS
Actions looks like stealing of personal data
- javaw.exe (PID: 2844)
SUSPICIOUS
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 2596)
Uses ATTRIB.EXE to modify file attributes
- javaw.exe (PID: 2844)
INFO
Application launched itself
- WinRAR.exe (PID: 2184)
- iexplore.exe (PID: 1928)
- iexplore.exe (PID: 532)
- iexplore.exe (PID: 2084)
- WinRAR.exe (PID: 2596)
Checks supported languages
- javaw.exe (PID: 2844)
- wmpnscfg.exe (PID: 3740)
Manual execution by a user
- WinRAR.exe (PID: 2596)
- javaw.exe (PID: 2844)
- wmpnscfg.exe (PID: 3740)
- explorer.exe (PID: 604)
Creates files in the program directory
- javaw.exe (PID: 2844)
Reads the computer name
- wmpnscfg.exe (PID: 3740)
- javaw.exe (PID: 2844)
Checks for external IP
- javaw.exe (PID: 2844)
Create files in a temporary directory
- javaw.exe (PID: 2844)
Drops the executable file immediately after the start
- javaw.exe (PID: 2844)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
58
Monitored processes
15
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 532 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2084 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 604 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 968 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1112 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2084 CREDAT:333057 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1288 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIb2184.6817\crimsonRAT2.2.6.jar | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1928 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa1288.8643\Time.gif | C:\Program Files\Internet Explorer\iexplore.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1992 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIb2596.13940\crimsonRAT2.2.6.jar | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2084 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa1288.7865\Calendar.gif | C:\Program Files\Internet Explorer\iexplore.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2184 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Crimson RAT Builder.b.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2344 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1928 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
22 465
Read events
22 188
Write events
275
Delete events
2
Modification events
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2184) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
4
Suspicious files
769
Text files
135
Unknown types
37
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1928 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF9B9ADF895A3D7781.TMP | binary | |
MD5:F4B89A2831780B0513D4FB75BFF1E230 | SHA256:A455EFCB54200C67EDD78F34C9EA46C5001023AA4092BF5D7CF7C8C3F39916A0 | |||
| 1288 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa1288.7865\Calendar.gif | image | |
MD5:32BFDD4AB4E822A93135983D14F5F582 | SHA256:05A04271026E72DFDE99369B578AC3C03C8A9DA60F07DA765ED9C04CB7EB9827 | |||
| 2184 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2184.6817\crimsonRAT2.2.6.jar | compressed | |
MD5:A6324CDB52C0182CCB6E991E53B8B024 | SHA256:86592DA5B0F1FB41F2F12DA15EA754BAFA0011FDDBA02065984B164CF4623D4B | |||
| 2084 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{0A70B2BE-A645-11EE-AE0A-12A9866C77DE}.dat | binary | |
MD5:FCB5CCBB7C42AE94950D4F17B68328A5 | SHA256:128971EE95474C864AD7D4327922A29C66832661270D7ADE7874312F32875934 | |||
| 2084 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\RecoveryStore.{42C873D0-1D90-11EB-BA2C-12A9866C77DE}.dat | binary | |
MD5:7095FA7E93C1486A45445B95F181BFE1 | SHA256:BA5BA53E971D4E80F204226902BFBC11E417F156C4149908A9BA73AF6AB7F0BE | |||
| 2084 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF0F937A08742BF86A.TMP | binary | |
MD5:C5577F1BBE26313CB172084A3ED1A85E | SHA256:7A7F4E0F8ADF51144CB0243F6BAED931A32E18B1C97BF4F649DBE3E726A76C84 | |||
| 2084 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{0A70B2BD-A645-11EE-AE0A-12A9866C77DE}.dat | binary | |
MD5:C97EDA029491FD8C4E2067128371B77A | SHA256:AB54C03F593F986AC61B569B0E0DAFF02A60B978545160BFCFC98160BA84E173 | |||
| 2084 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF0EC6E7C31E0E1523.TMP | binary | |
MD5:A75B71A4871FCE448C6B73ADB6101199 | SHA256:9AAF6C596B84B9F04FF72E5CB7075E530E3734872CED7AE084D42FA4E0034E69 | |||
| 1928 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{0F11A378-A645-11EE-AE0A-12A9866C77DE}.dat | binary | |
MD5:168E56E781A5E3E2D7AAA554F4431A07 | SHA256:6A1038C63C0A37B6D4182231301324B2D095D0D486F6D9D516CB43604AF72CD6 | |||
| 2084 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF71B4B2BEA8B253AD.TMP | binary | |
MD5:7D2E840EB14C36D3103AFDBDAE9AD5C6 | SHA256:0F161A03E928E8B725F5D06A18A72ECC00A2BC510241AEB4594D9F7BBDA535FF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
18
DNS requests
8
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1080 | svchost.exe | GET | 304 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a414549a770d7263 | unknown | — | — | unknown |
2084 | iexplore.exe | GET | 200 | 184.25.51.113:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fd70820256555726 | unknown | compressed | 4.66 Kb | unknown |
2084 | iexplore.exe | GET | 200 | 184.25.51.113:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5ab10afc70c283f8 | unknown | compressed | 4.66 Kb | unknown |
2084 | iexplore.exe | GET | 200 | 184.25.51.113:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?2059bfb2f4ebfaa2 | unknown | compressed | 4.66 Kb | unknown |
2844 | javaw.exe | GET | 301 | 172.67.75.176:80 | http://freegeoip.net/xml/216.24.216.192 | unknown | — | — | unknown |
2084 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
2844 | javaw.exe | GET | 200 | 46.137.128.27:80 | http://checkip.amazonaws.com/ | unknown | text | 15 b | unknown |
2844 | javaw.exe | GET | 200 | 172.67.75.176:80 | http://freegeoip.net/shutdown | unknown | html | 1.00 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2084 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
2084 | iexplore.exe | 184.25.51.113:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2084 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1928 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 184.24.77.202:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2844 | javaw.exe | 46.137.128.27:80 | checkip.amazonaws.com | AMAZON-02 | IE | unknown |
2844 | javaw.exe | 172.67.75.176:80 | freegeoip.net | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
checkip.amazonaws.com |
| shared |
freegeoip.net |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain (freegeiop .net in DNS lookup) |
2844 | javaw.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
2844 | javaw.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
2844 | javaw.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] Received IP address from server as result of HTTP request |
4 ETPRO signatures available at the full report