| download: | SibinChat.exe |
| Full analysis: | https://app.any.run/tasks/ff77edd2-d350-40f0-831e-c31d3f40ce8b |
| Verdict: | Malicious activity |
| Analysis date: | March 21, 2019, 12:49:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 303DCCD080BA1D1CEF930129C71ADF9B |
| SHA1: | B7F1878B23F53521B0B7F69118F555FA14D7A01E |
| SHA256: | 3A32AF77061C984923CB887B2611DD7169C519C08A81D87E16E5644D747F7C51 |
| SSDEEP: | 393216:rD2GKnLPoqNDxU2OUbWxNmCvUbe0rBxZGEc8D1W+kvIH//ndeqpPt4J5nfLnytGR:ryBNtU2lbgNHQe0zcakvIH/FDPt4JdyY |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- SibinChat.exe (PID: 2700)
- SibinChat.tmp (PID: 1376)
Reads Windows owner or organization settings
- SibinChat.tmp (PID: 1376)
Creates files in the user directory
- SibinChat.tmp (PID: 1376)
- Telegram.exe (PID: 2864)
Reads the Windows organization settings
- SibinChat.tmp (PID: 1376)
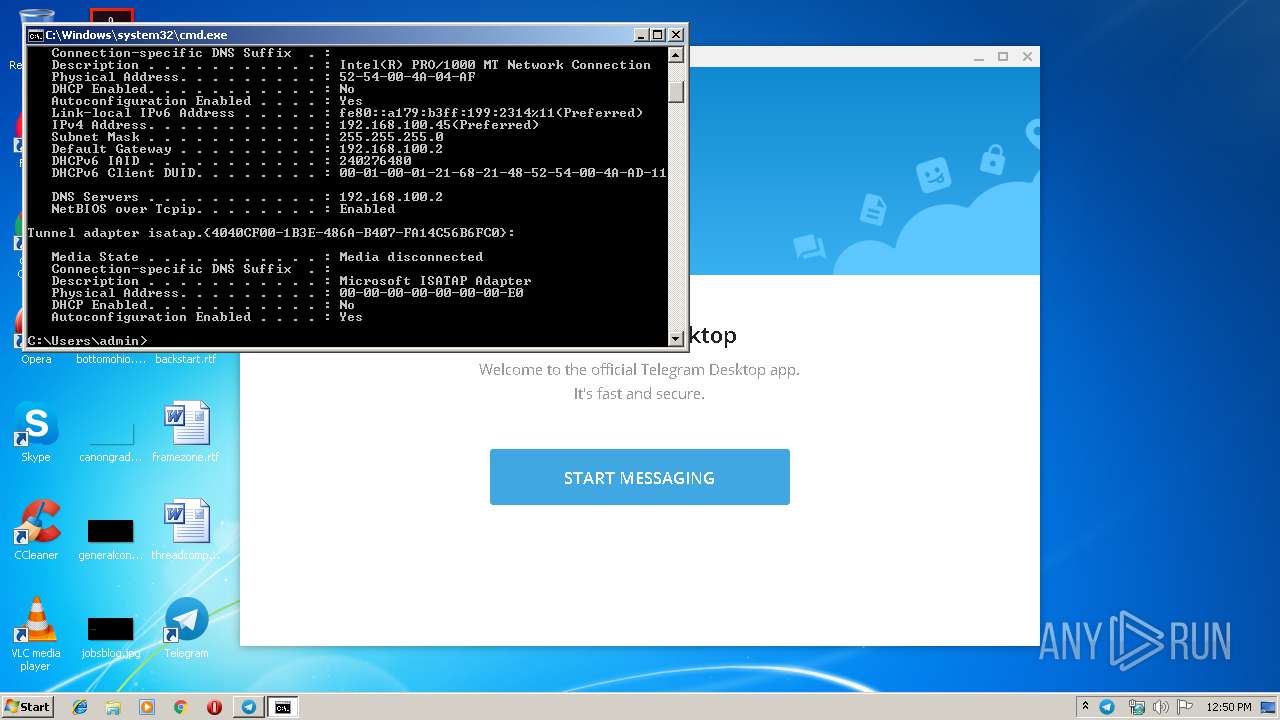
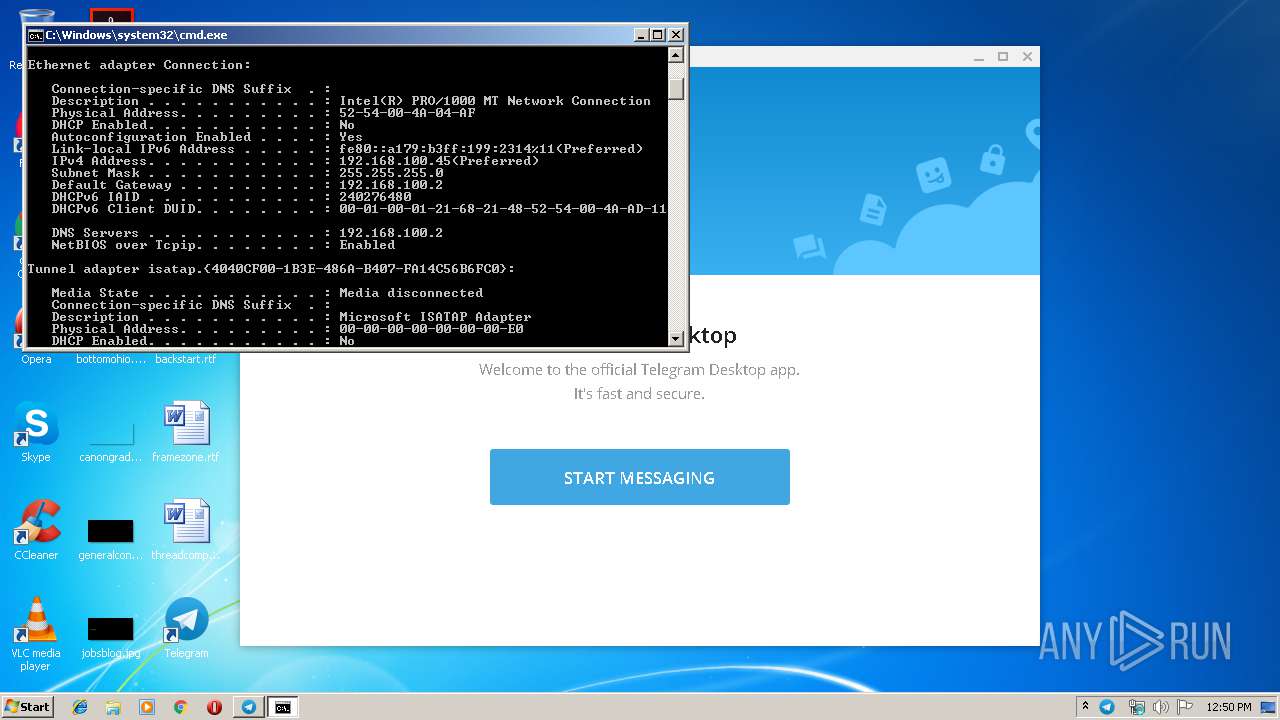
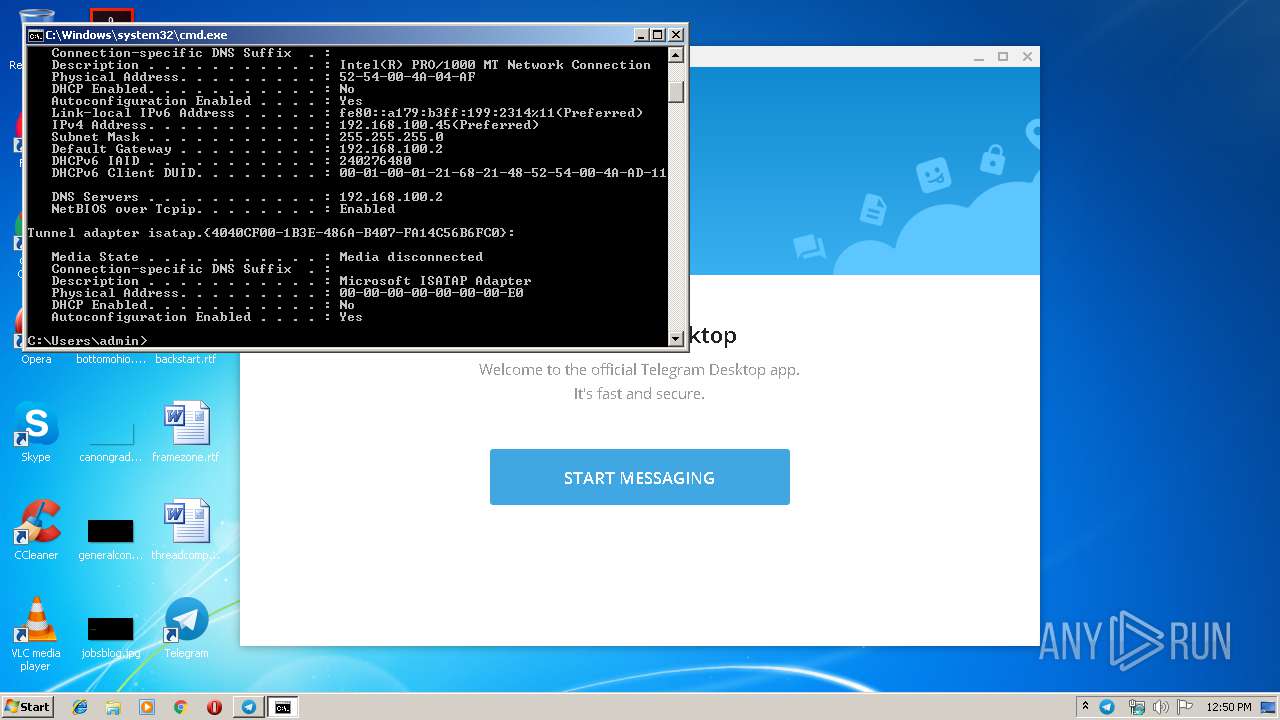
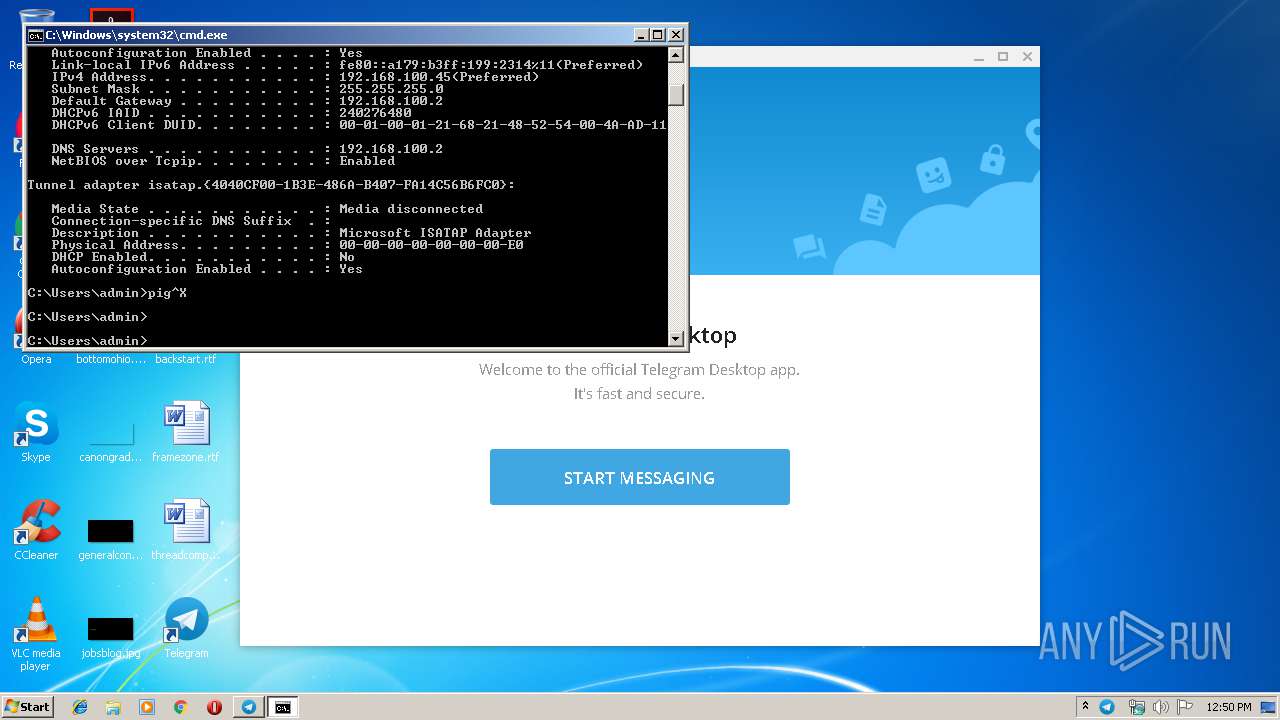
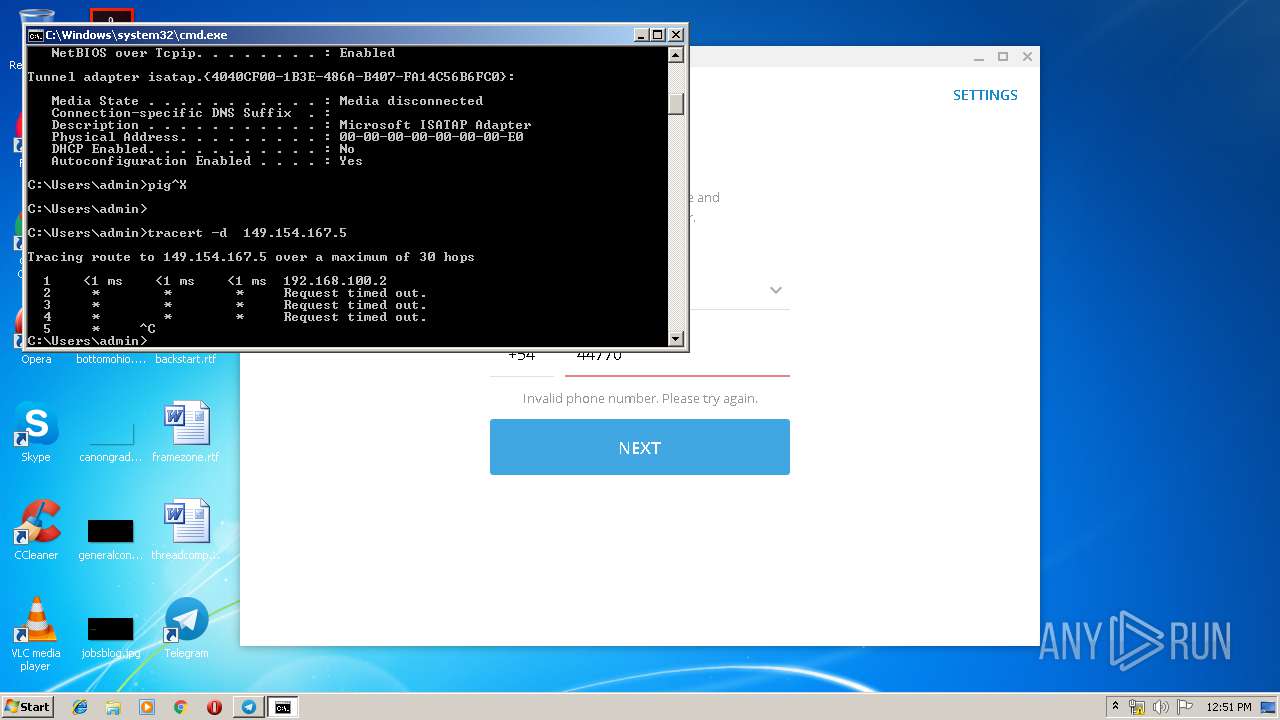
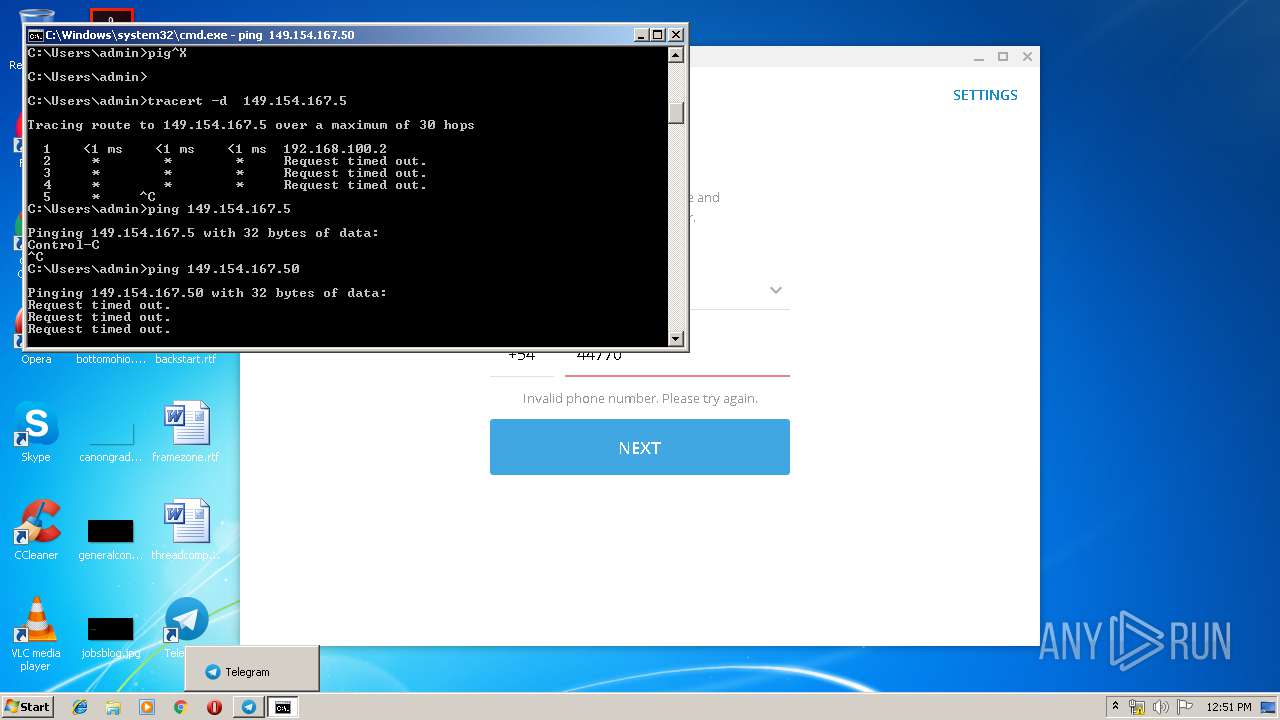
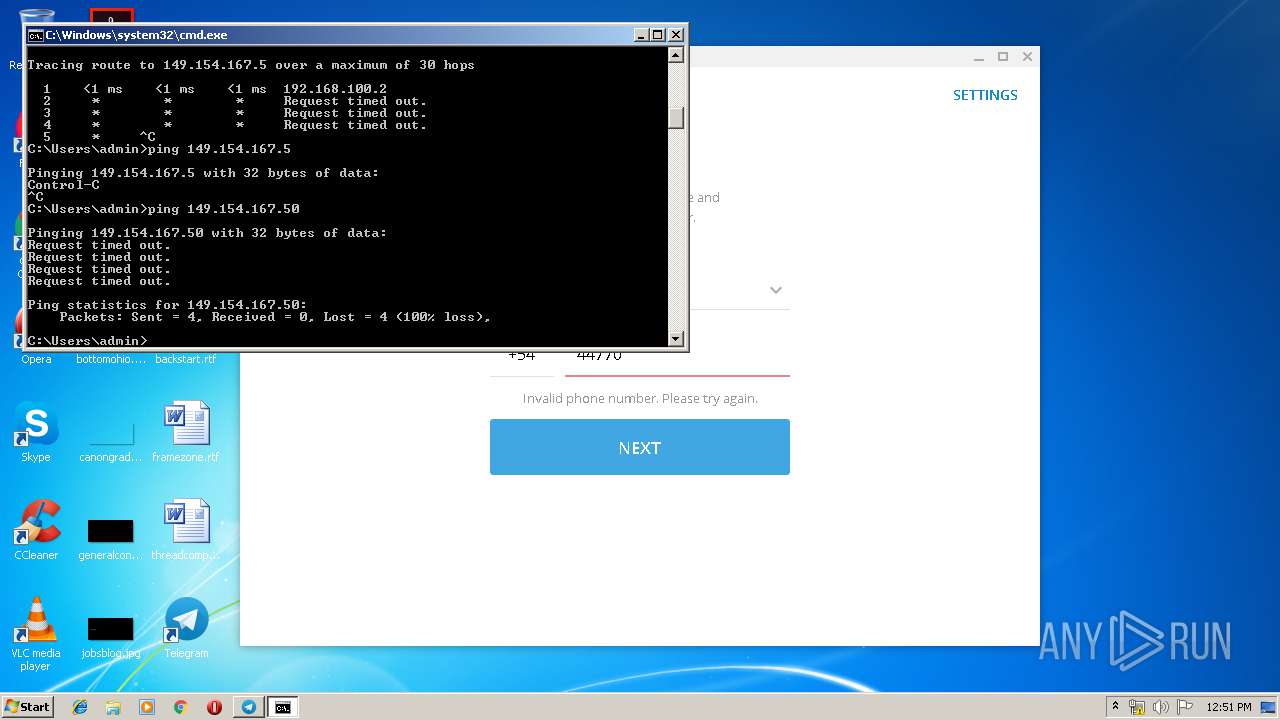
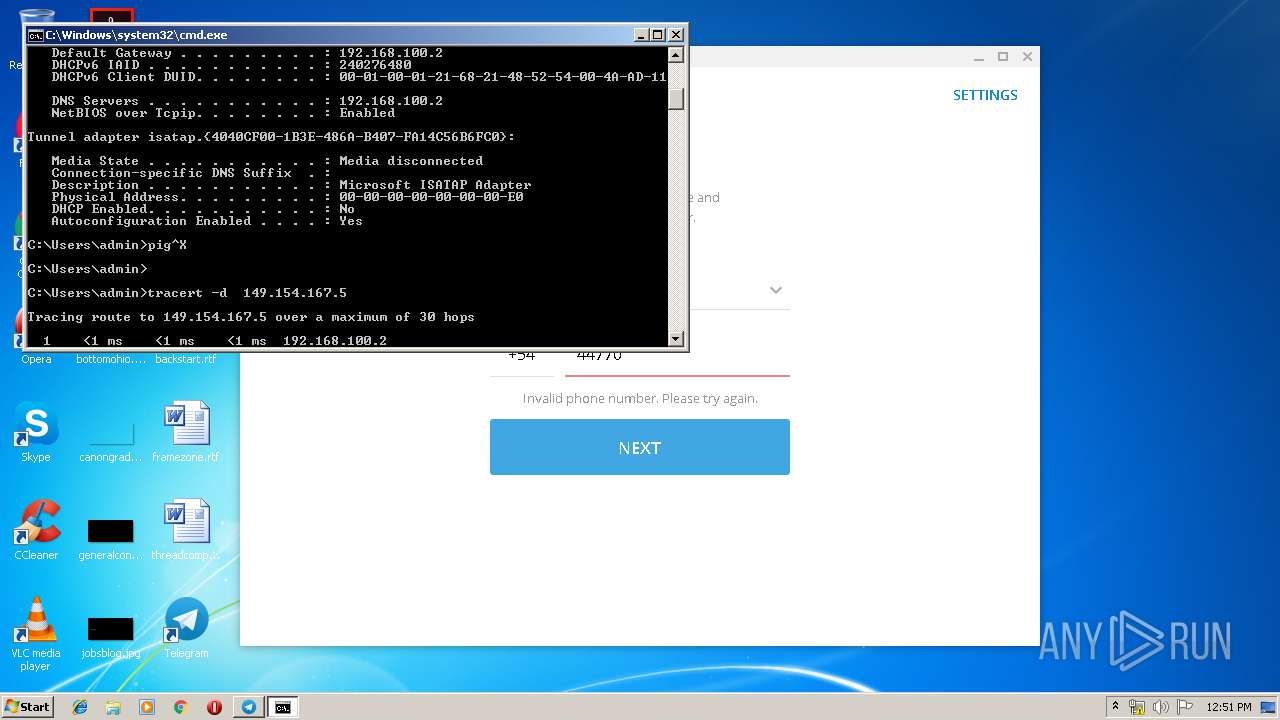
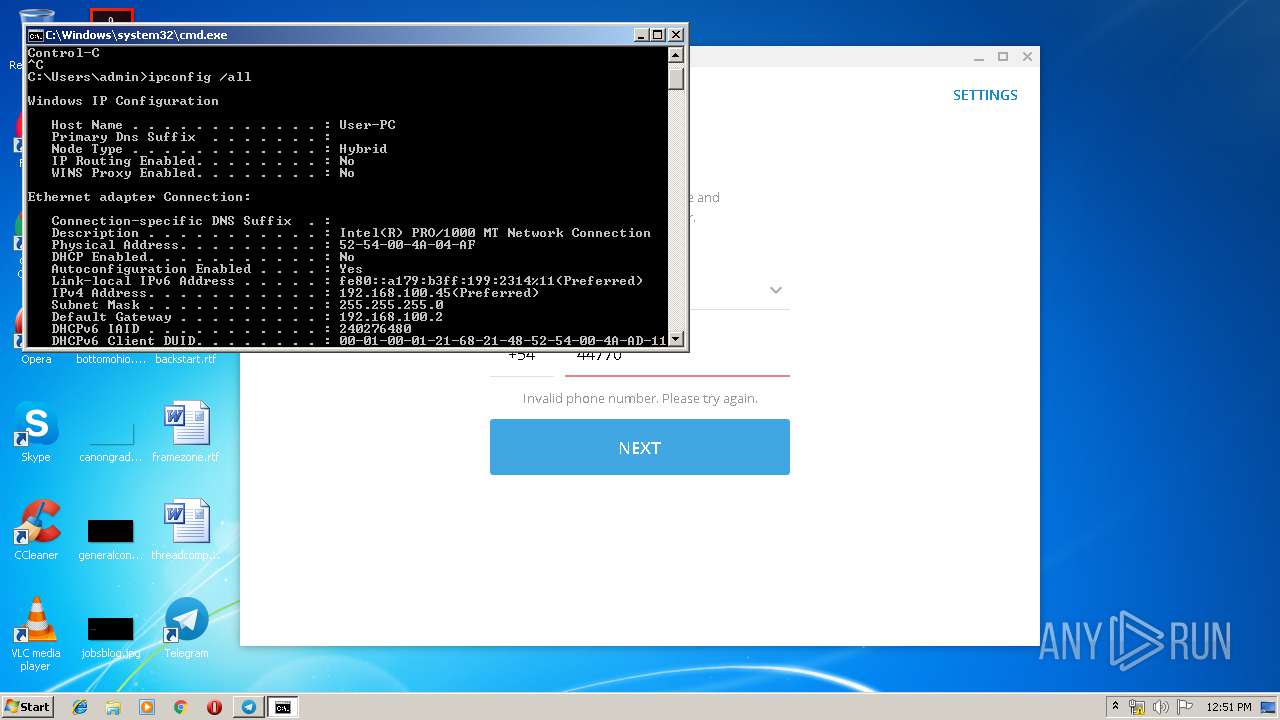
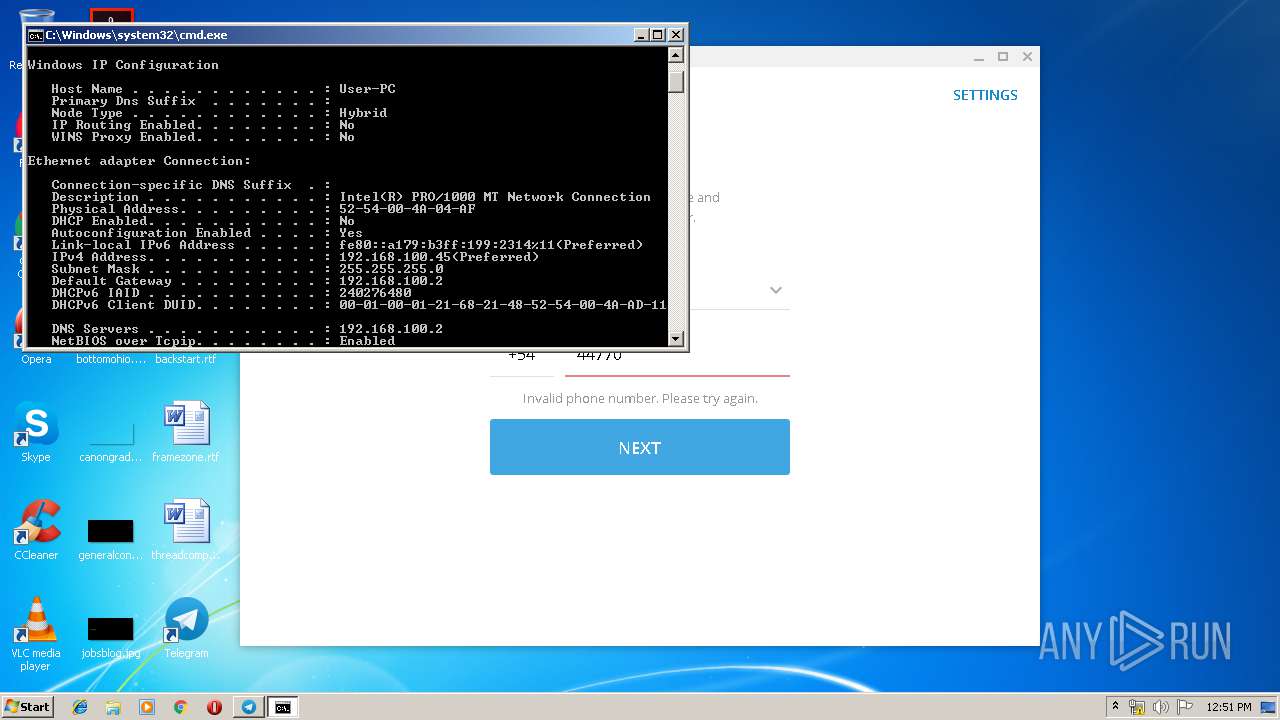
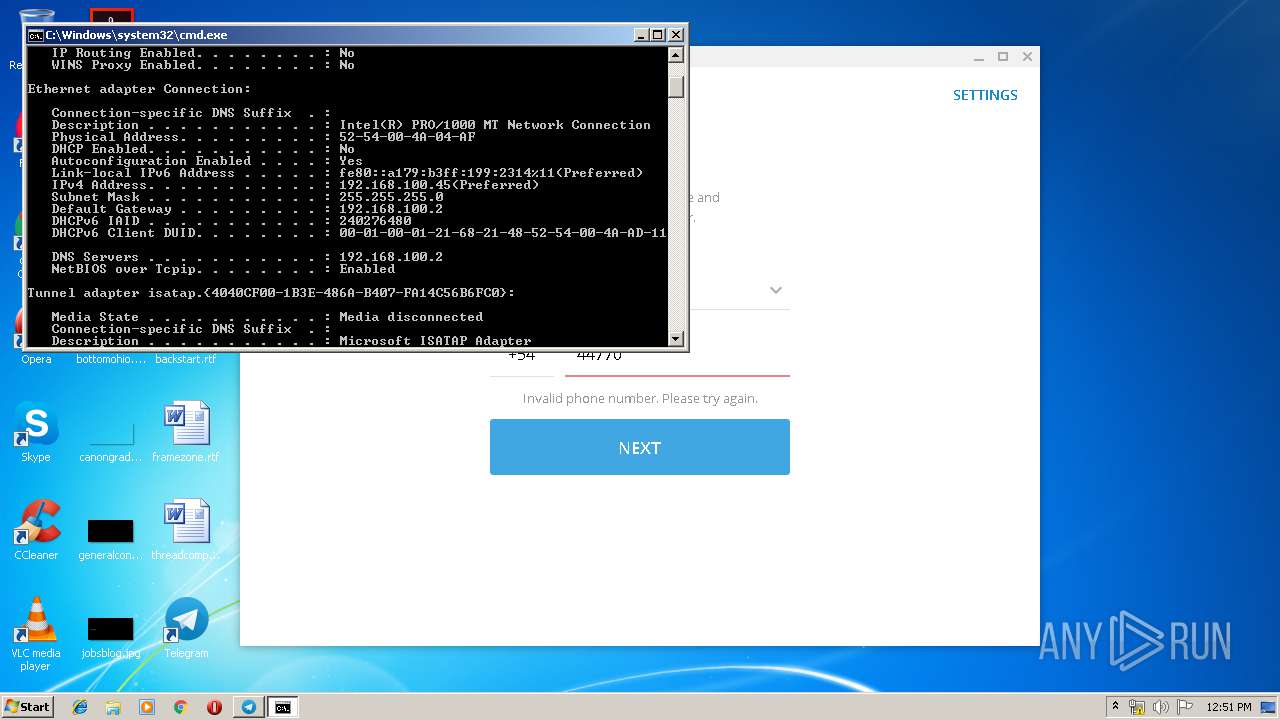
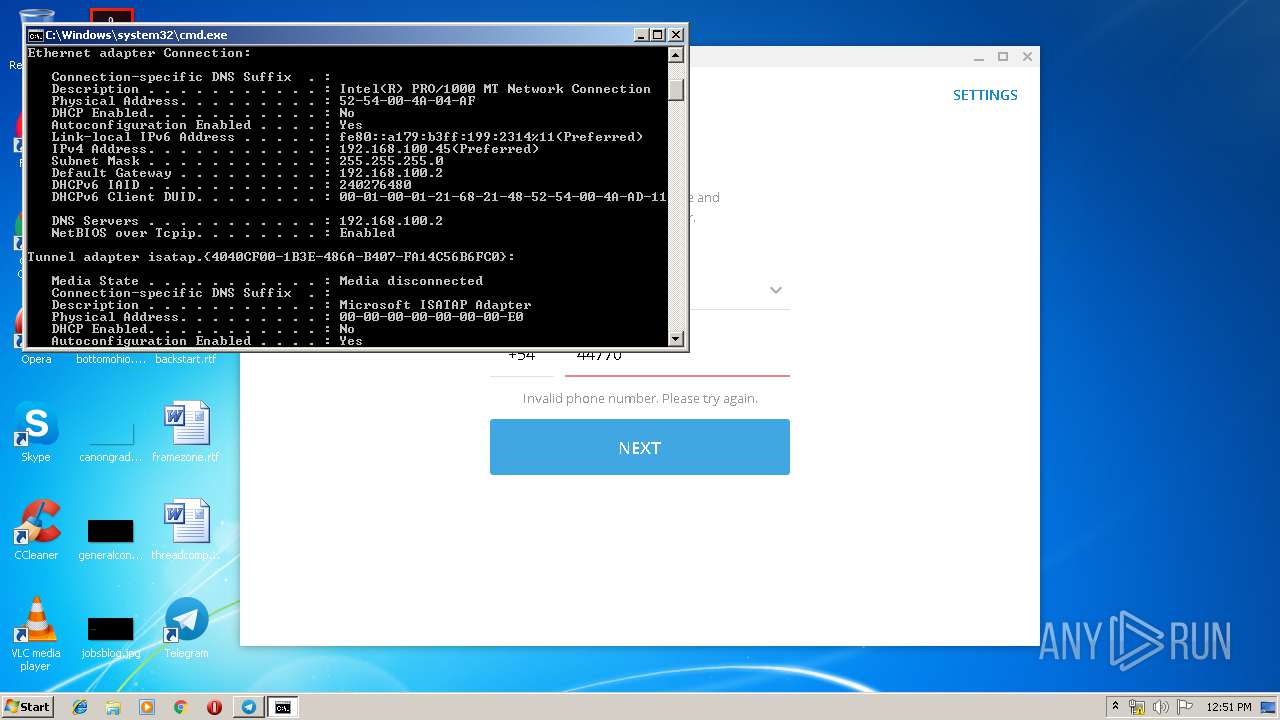
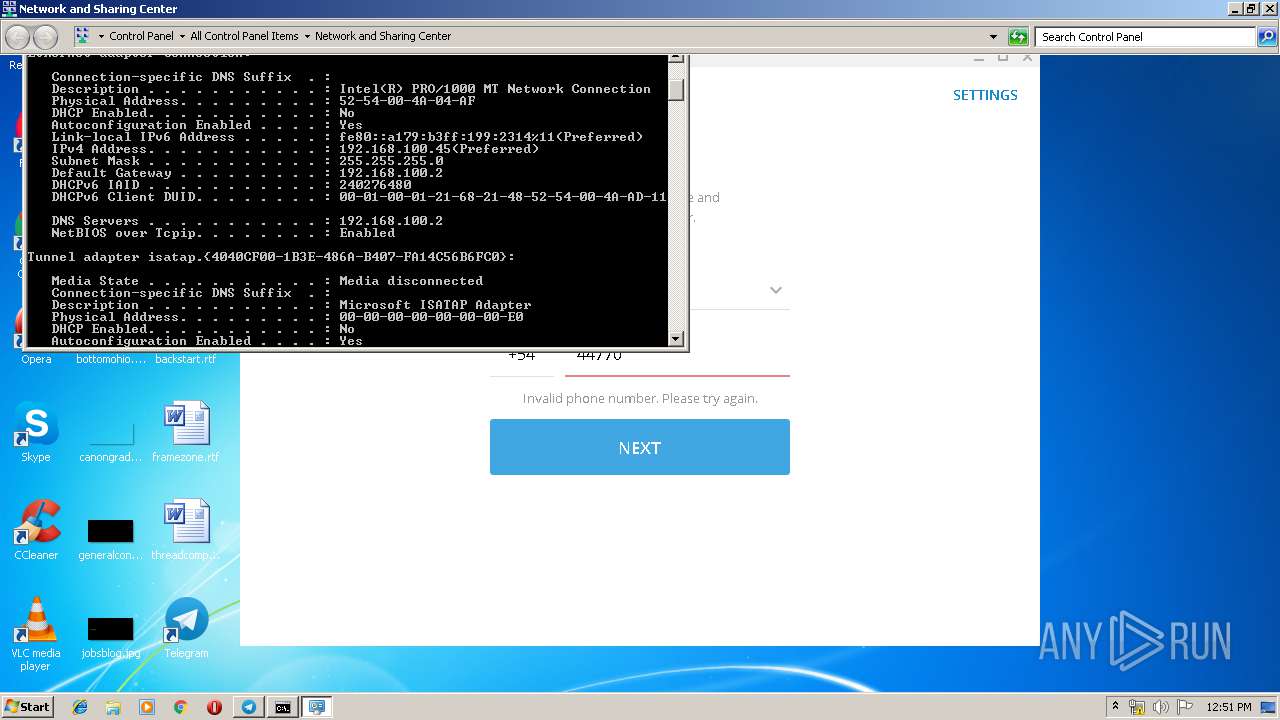
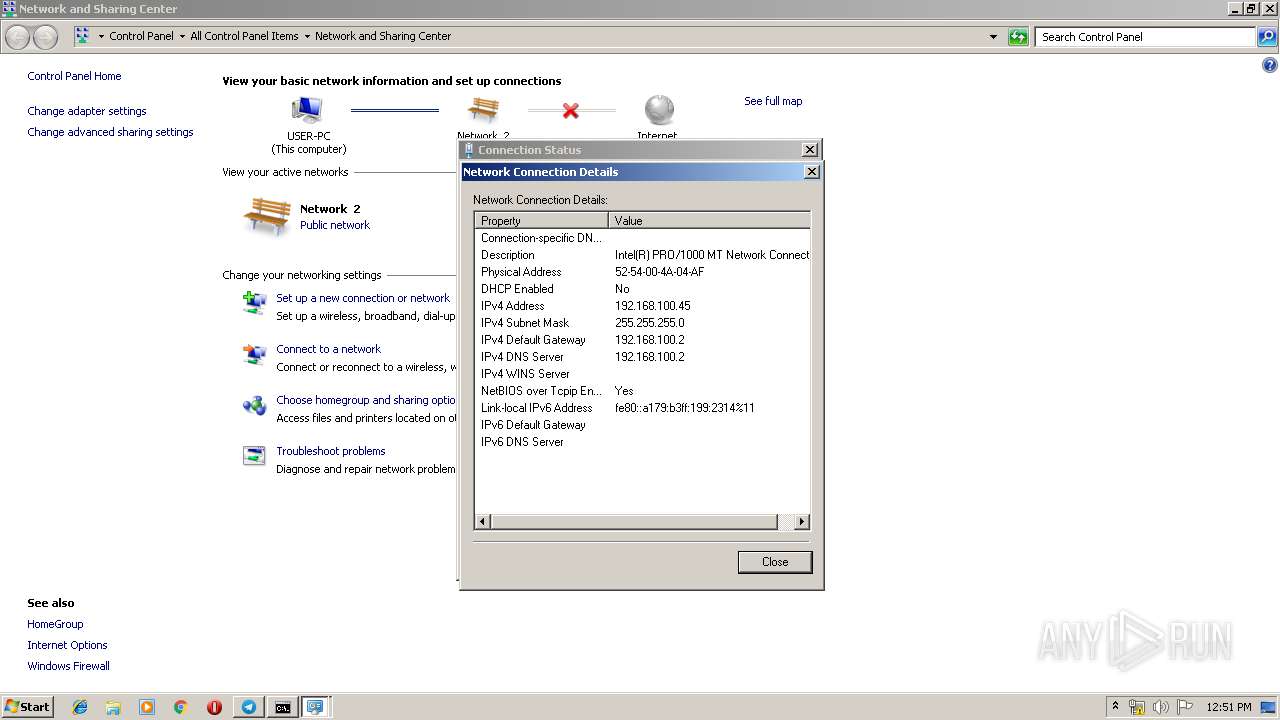
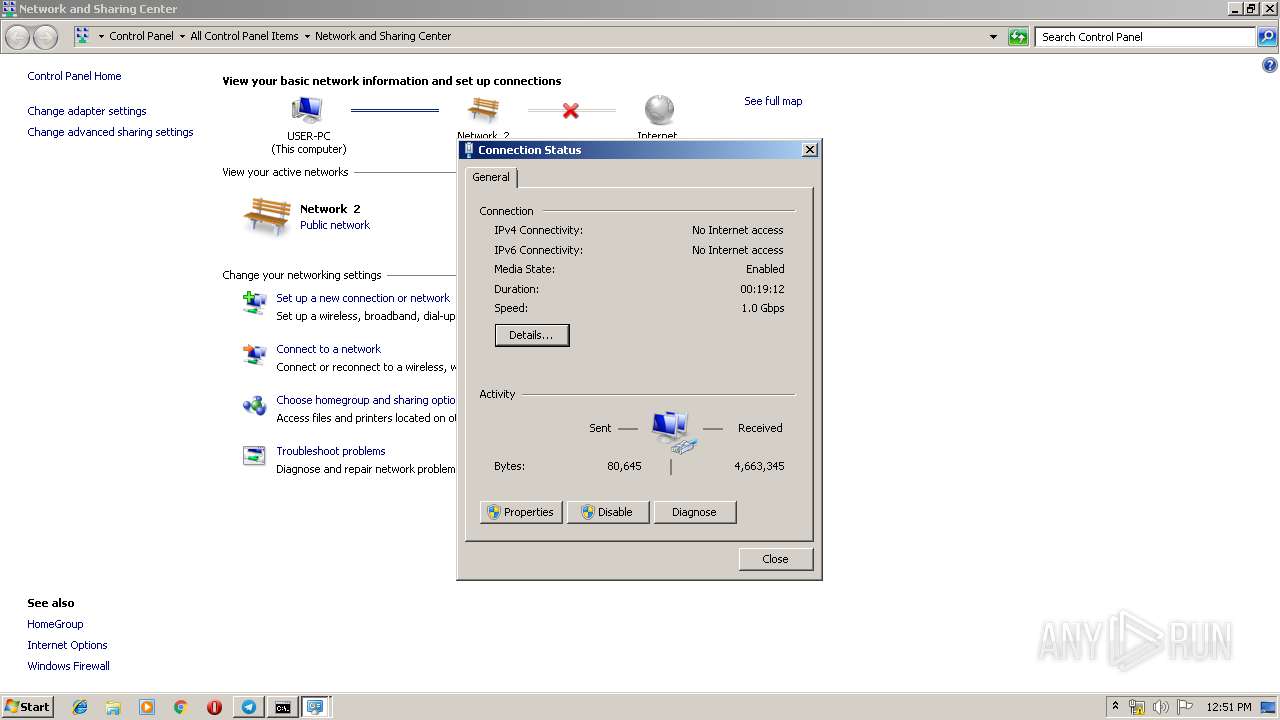
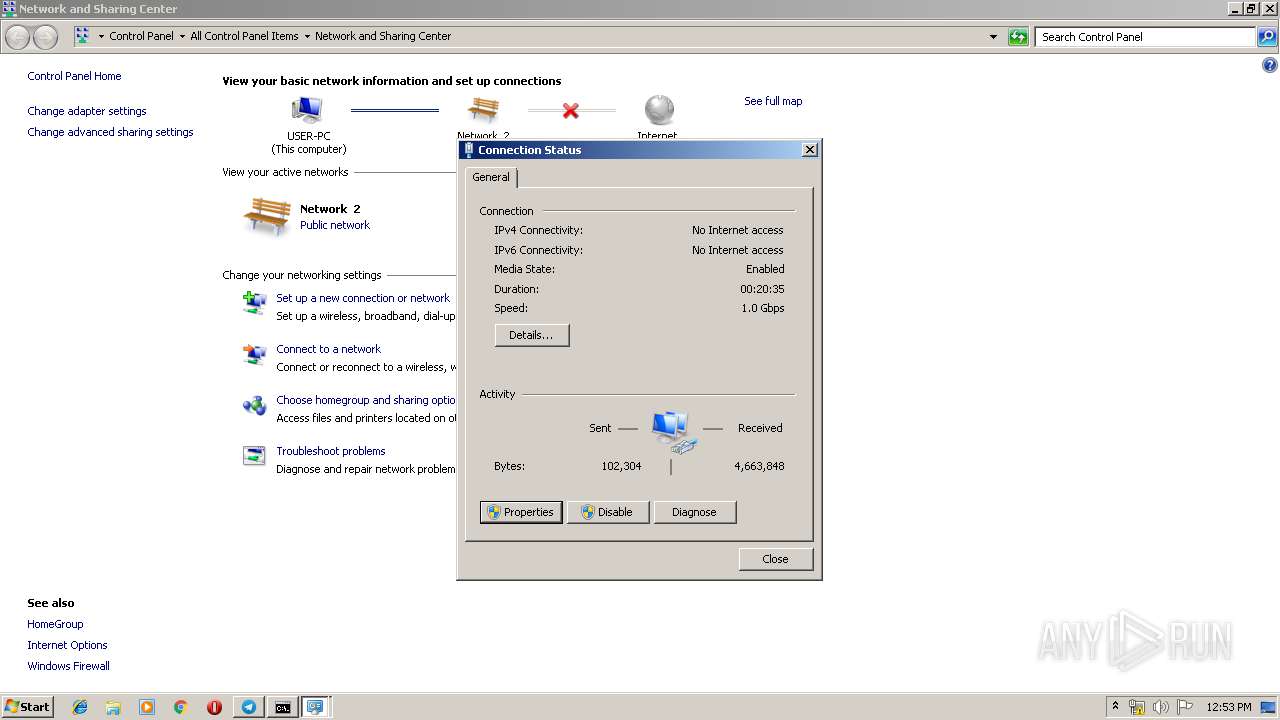
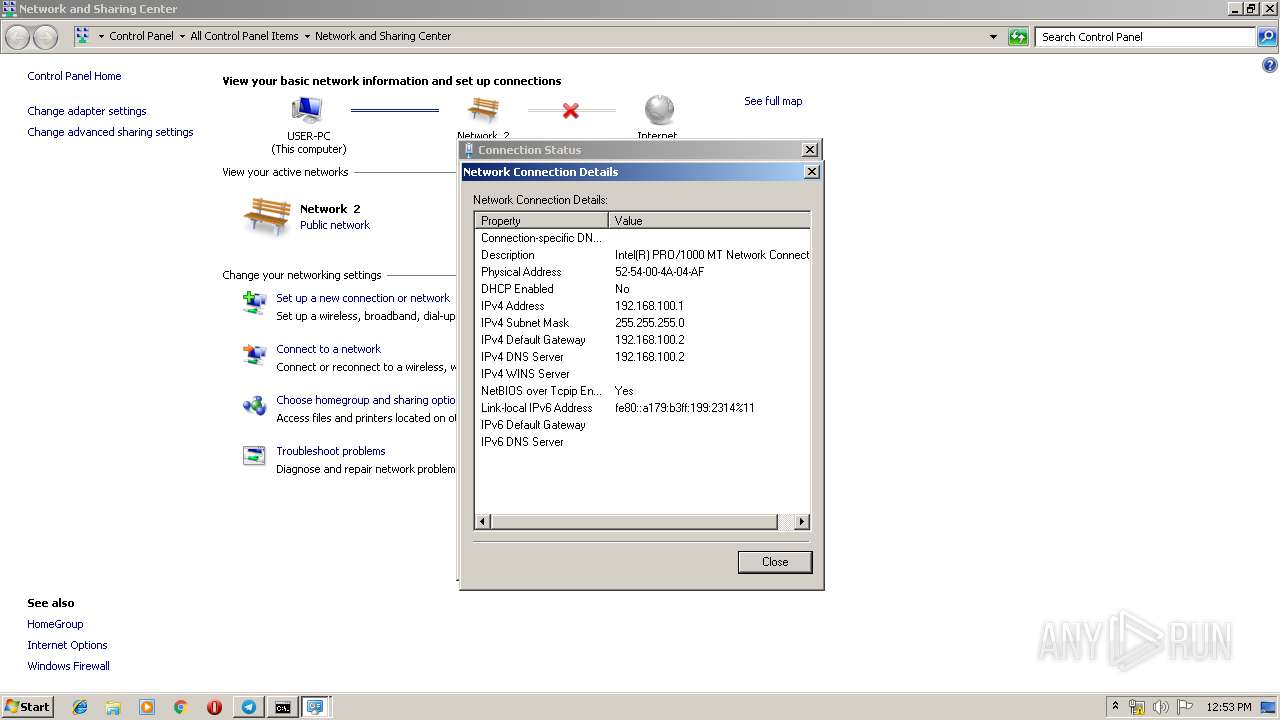
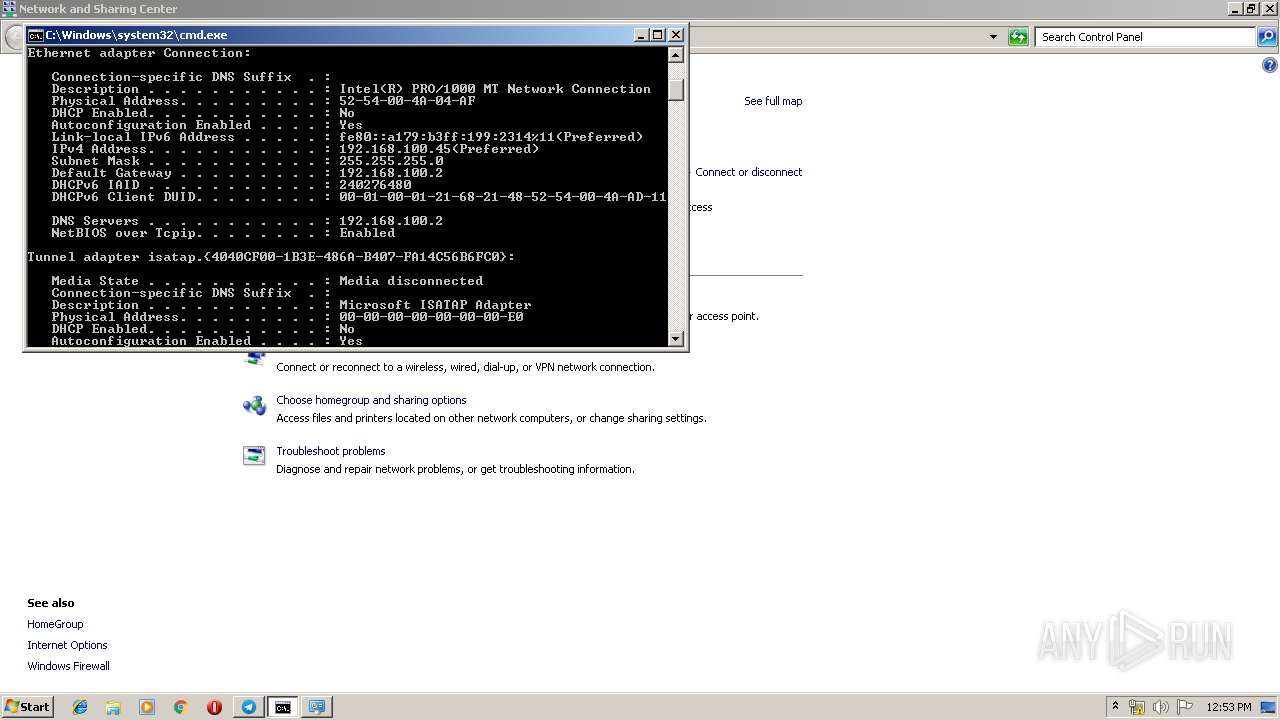
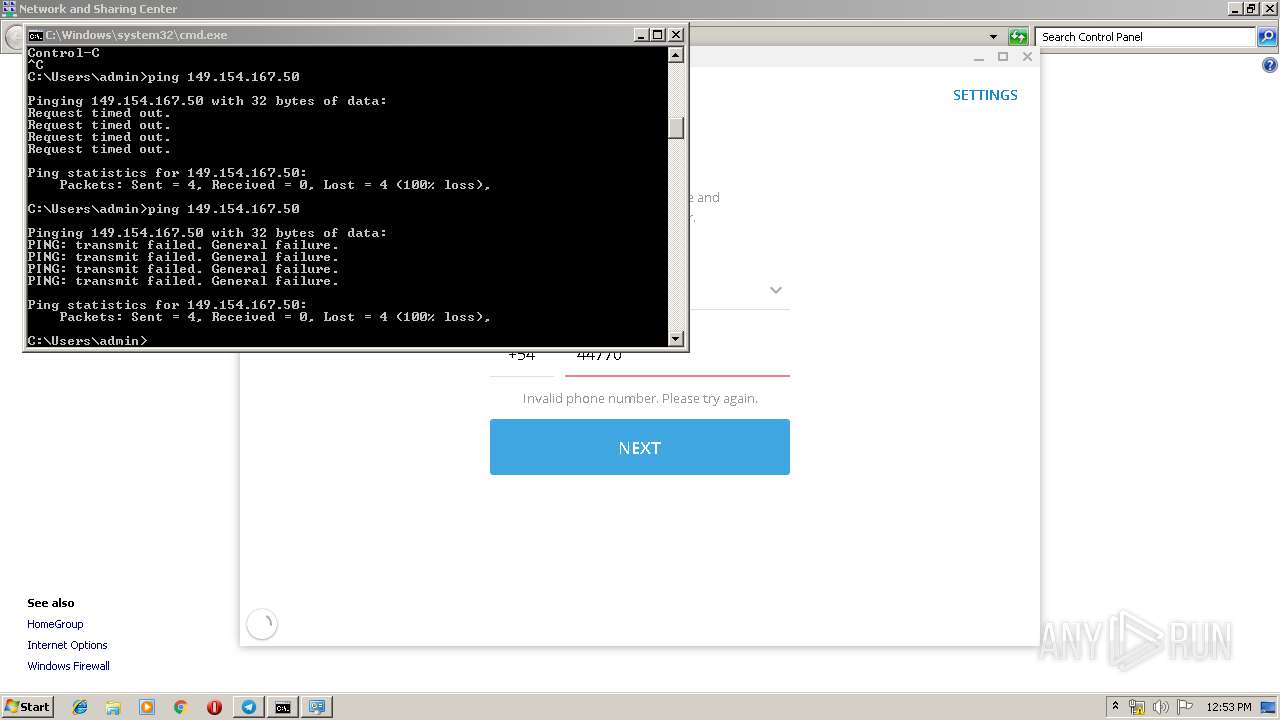
Uses IPCONFIG.EXE to discover IP address
- cmd.exe (PID: 2520)
Modifies the open verb of a shell class
- Telegram.exe (PID: 2864)
INFO
Application was dropped or rewritten from another process
- SibinChat.tmp (PID: 1376)
Creates a software uninstall entry
- SibinChat.tmp (PID: 1376)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (42.6) |
|---|---|---|
| .exe | | | Win16/32 Executable Delphi generic (19.5) |
| .exe | | | Generic Win/DOS Executable (18.9) |
| .exe | | | DOS Executable Generic (18.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:04:06 16:39:04+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 66560 |
| InitializedDataSize: | 419328 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x117dc |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.3.9.0 |
| ProductVersionNumber: | 1.3.9.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Telegram Messenger LLP |
| FileDescription: | Telegram Desktop Setup |
| FileVersion: | 1.3.9.0 |
| LegalCopyright: | |
| ProductName: | Telegram Desktop |
| ProductVersion: | 1.3.9 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 06-Apr-2016 14:39:04 |
| Detected languages: |
|
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Telegram Messenger LLP |
| FileDescription: | Telegram Desktop Setup |
| FileVersion: | 1.3.9.0 |
| LegalCopyright: | - |
| ProductName: | Telegram Desktop |
| ProductVersion: | 1.3.9 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 06-Apr-2016 14:39:04 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0000F244 | 0x0000F400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.37521 |
.itext | 0x00011000 | 0x00000F64 | 0x00001000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.7322 |
.data | 0x00012000 | 0x00000C88 | 0x00000E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.29672 |
.bss | 0x00013000 | 0x000056BC | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x00019000 | 0x00000E04 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.59781 |
.tls | 0x0001A000 | 0x00000008 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x0001B000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0.204488 |
.rsrc | 0x0001C000 | 0x00064408 | 0x00064600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.21032 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.13965 | 1580 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 5.36104 | 4264 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 5.21573 | 9640 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 5.17285 | 16936 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 5.0538 | 67624 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 4.99592 | 270376 | Latin 1 / Western European | English - United States | RT_ICON |
4091 | 2.56031 | 104 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4092 | 3.25287 | 212 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4093 | 3.26919 | 164 | Latin 1 / Western European | UNKNOWN | RT_STRING |
4094 | 3.33268 | 684 | Latin 1 / Western European | UNKNOWN | RT_STRING |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
oleaut32.dll |
user32.dll |
Total processes
61
Monitored processes
17
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
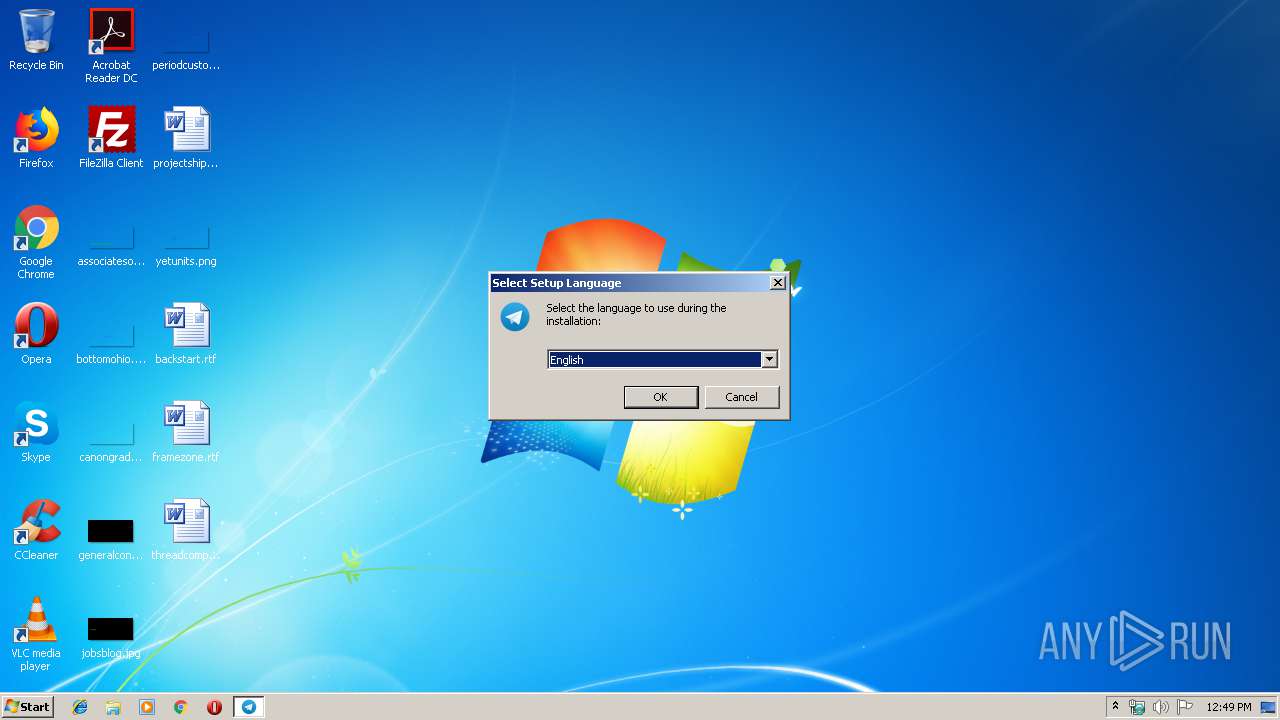
| 1376 | "C:\Users\admin\AppData\Local\Temp\is-1L7AE.tmp\SibinChat.tmp" /SL5="$3015E,22580887,486912,C:\Users\admin\AppData\Local\Temp\SibinChat.exe" | C:\Users\admin\AppData\Local\Temp\is-1L7AE.tmp\SibinChat.tmp | SibinChat.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
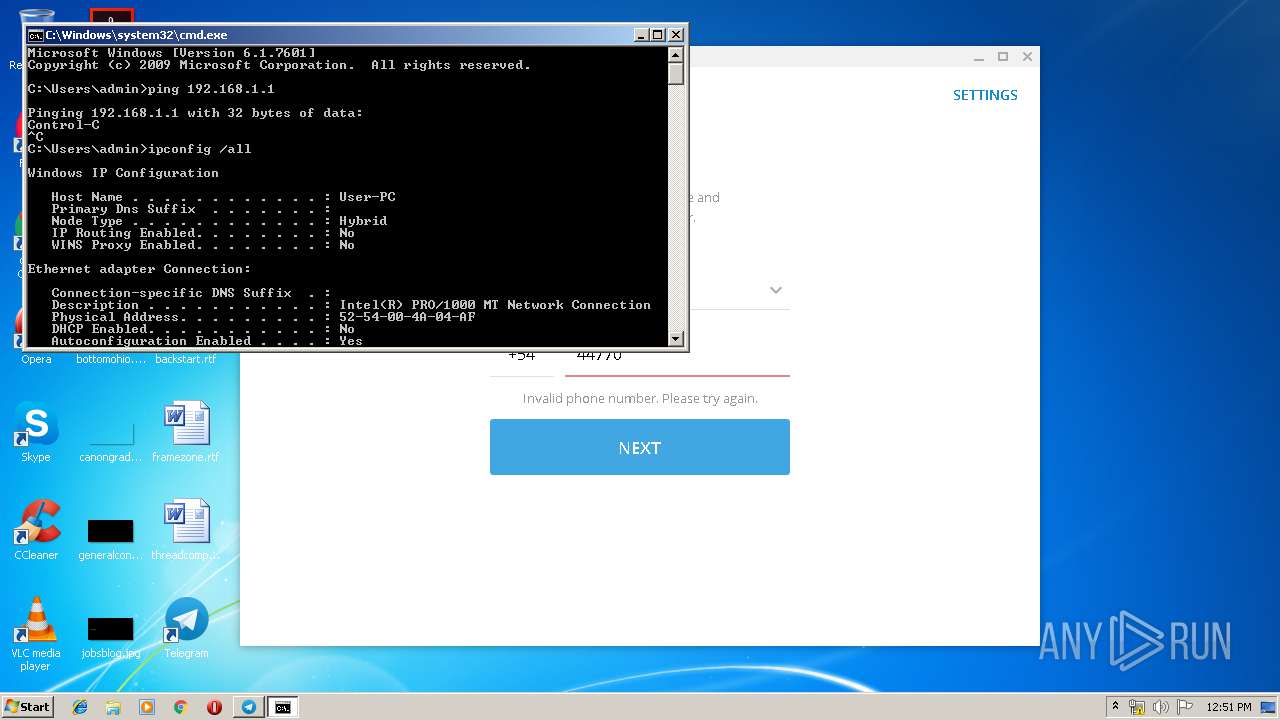
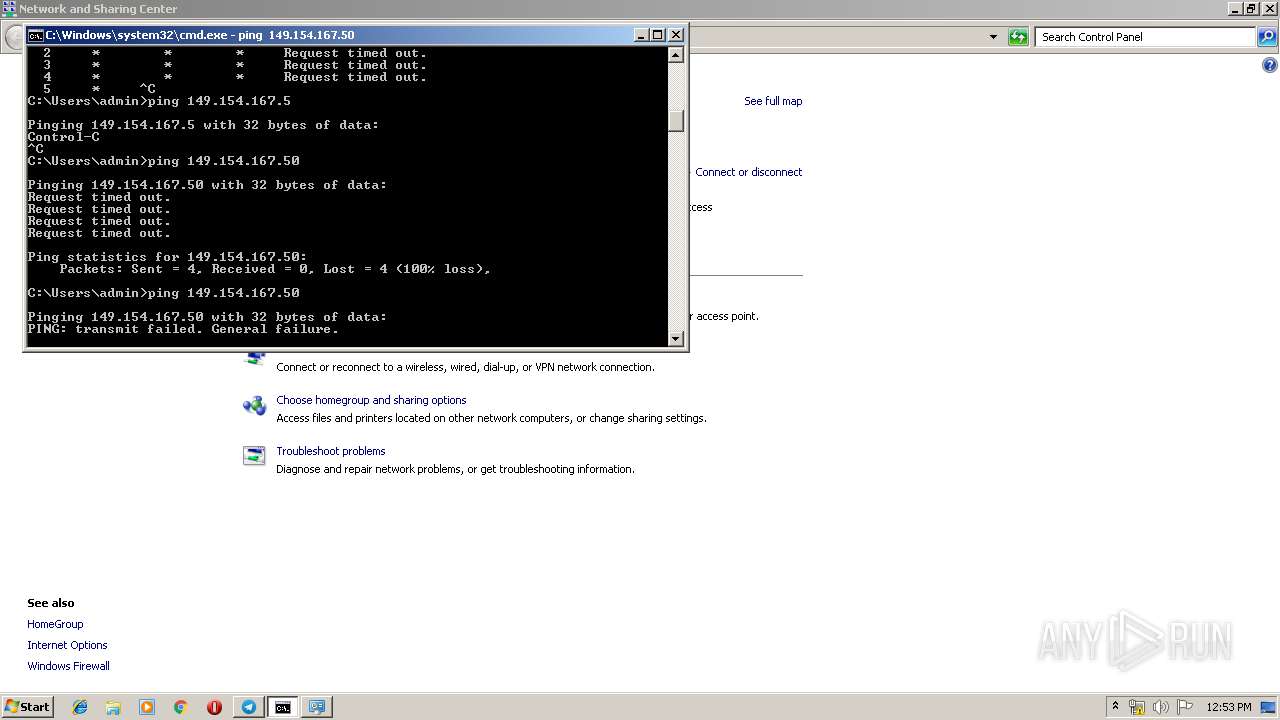
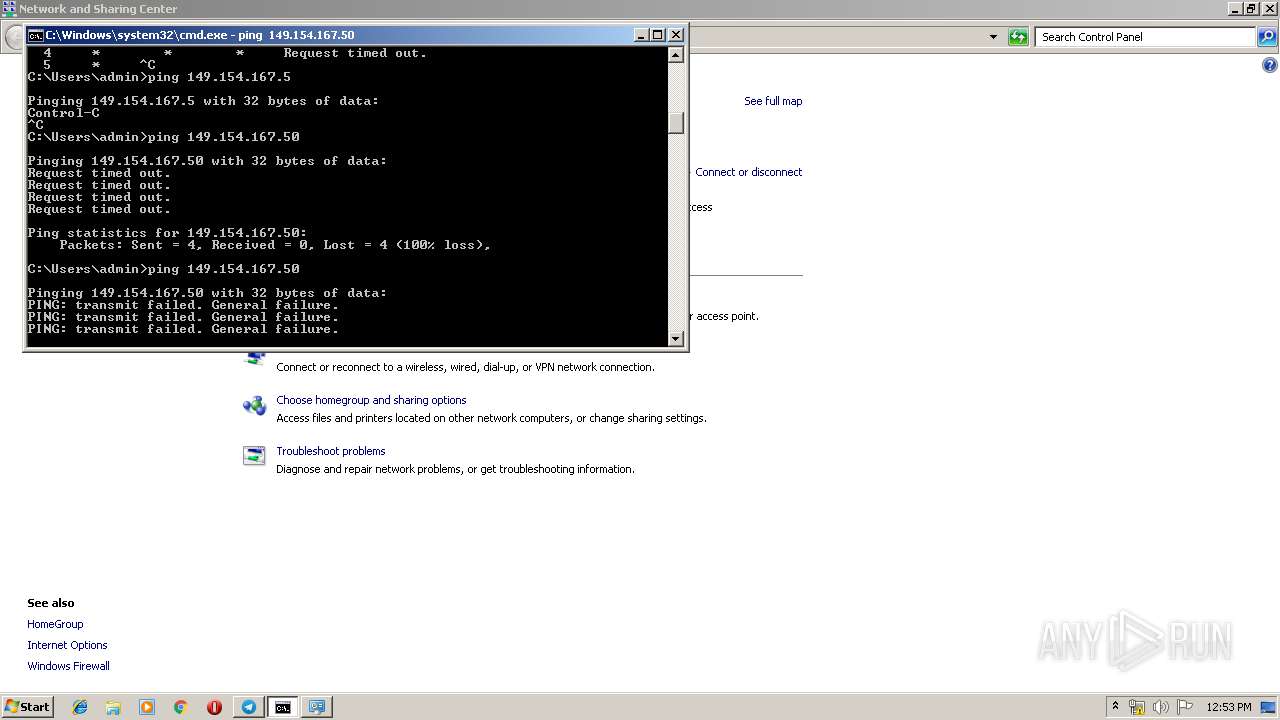
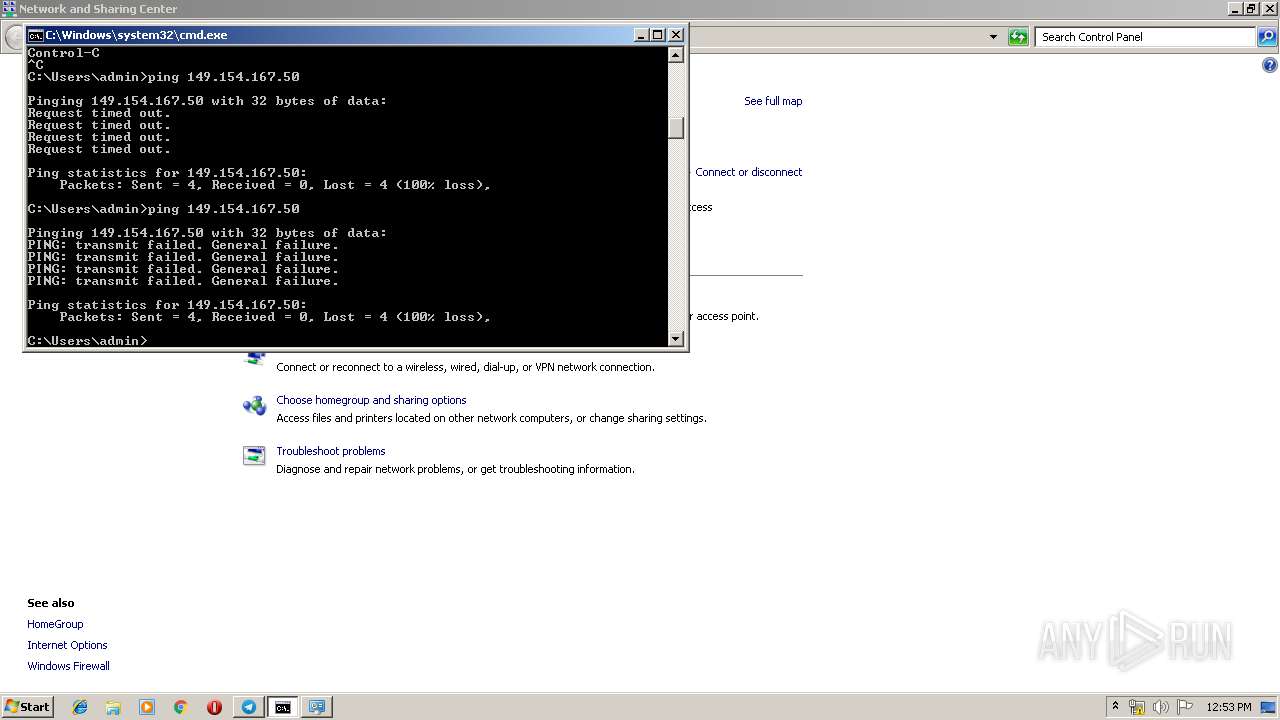
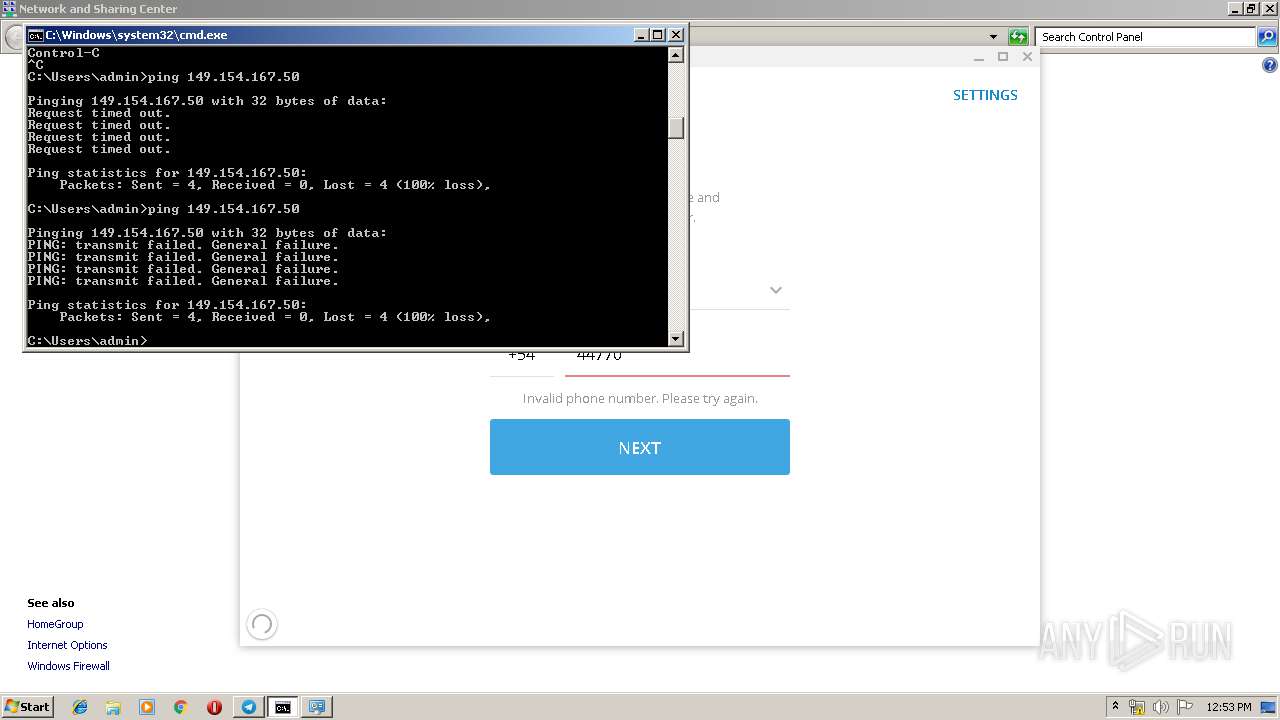
| 1472 | ping 192.168.1.1 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 3221225786 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1880 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\compmgmt.msc" /s | C:\Windows\system32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2228 | C:\Windows\system32\DllHost.exe /Processid:{7007ACD1-3202-11D1-AAD2-00805FC1270E} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2376 | C:\Windows\system32\DeviceDisplayObjectProvider.exe -Embedding | C:\Windows\system32\DeviceDisplayObjectProvider.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Device Display Object Function Discovery Provider Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2520 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2524 | C:\Windows\system32\DllHost.exe /Processid:{7007ACD1-3202-11D1-AAD2-00805FC1270E} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2592 | ipconfig /all | C:\Windows\system32\ipconfig.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
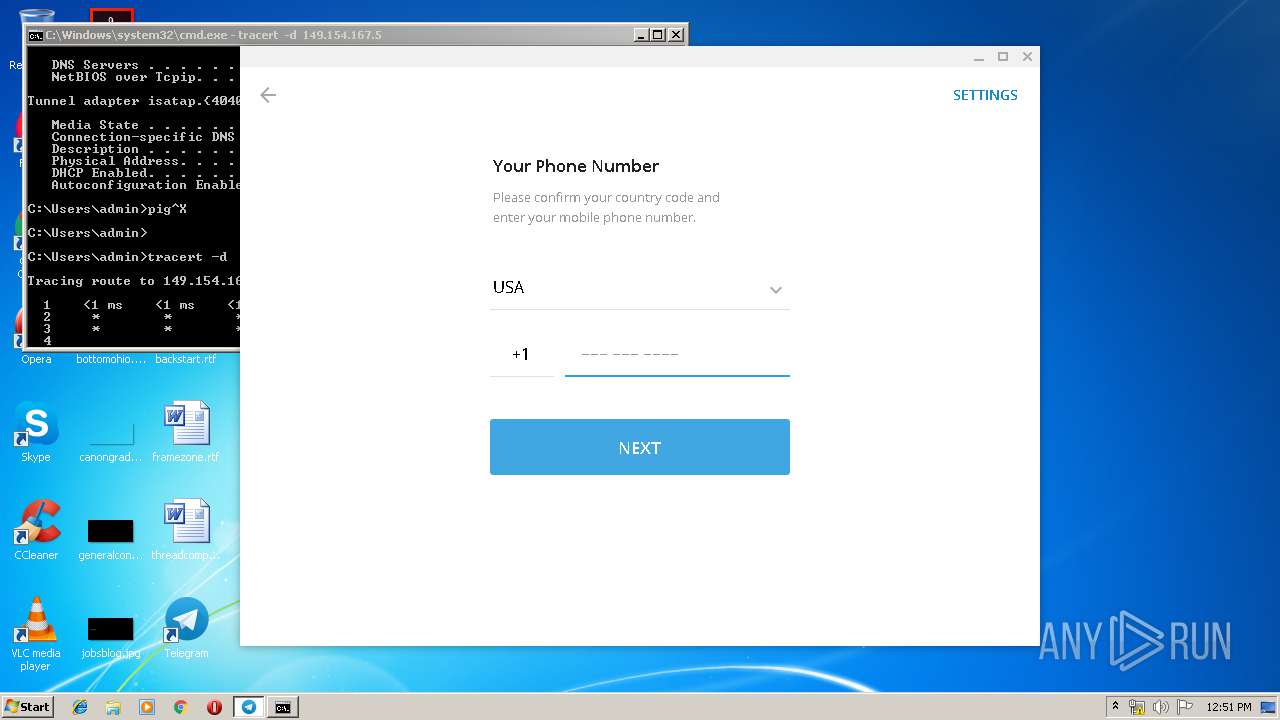
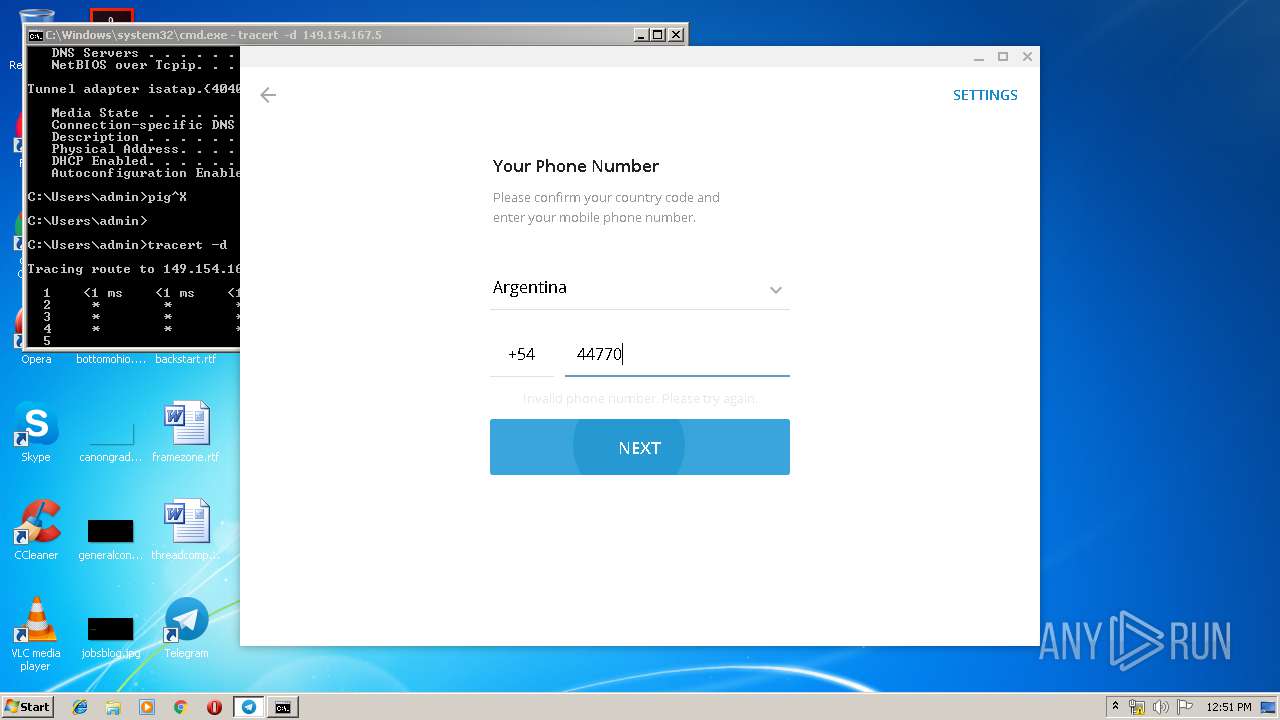
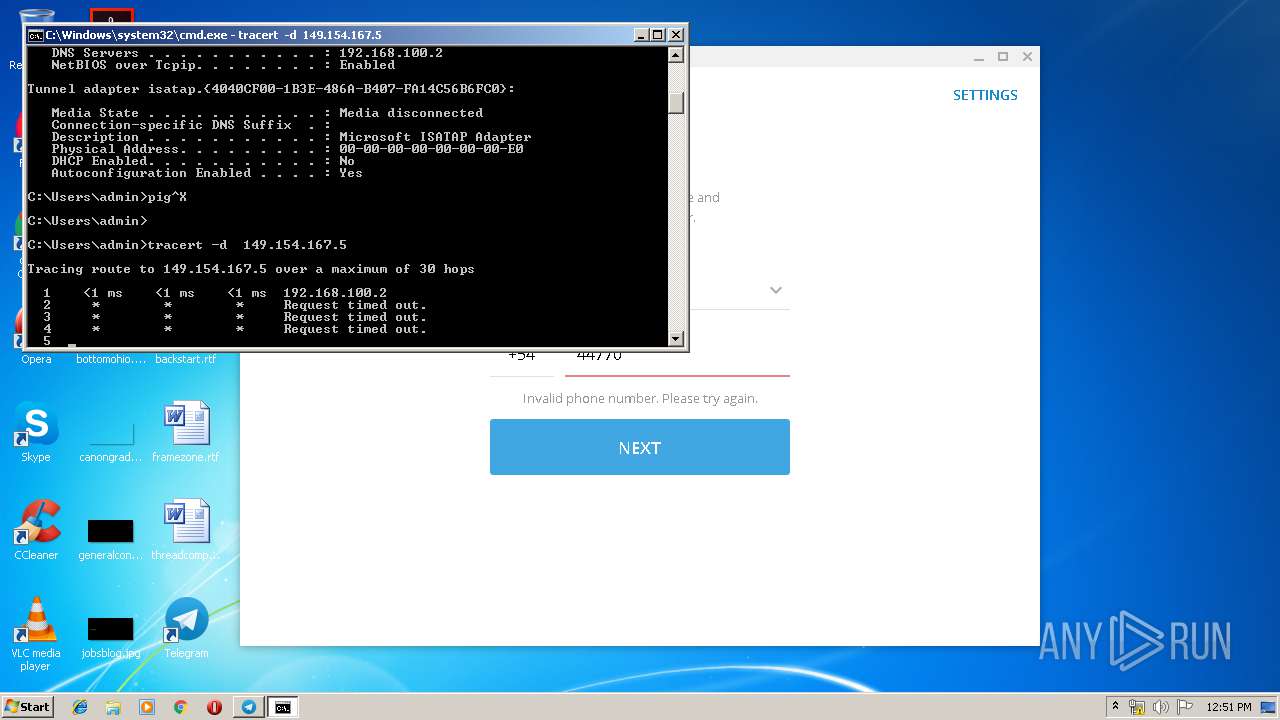
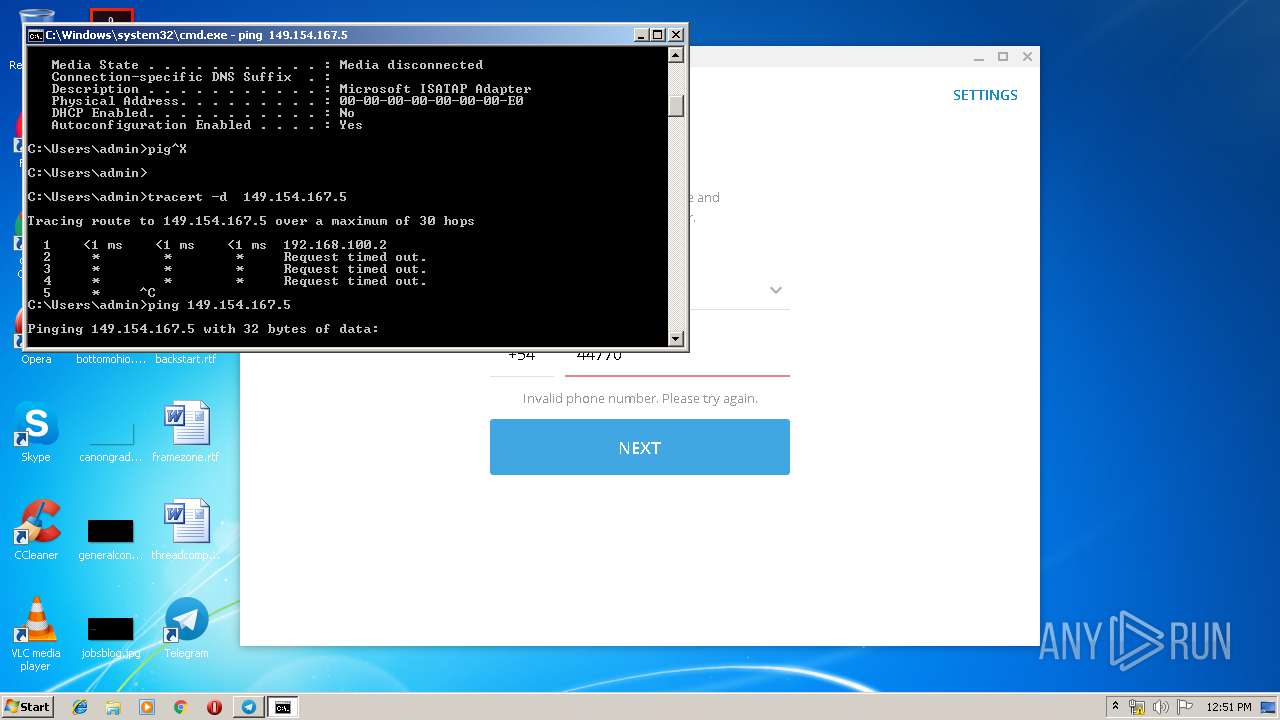
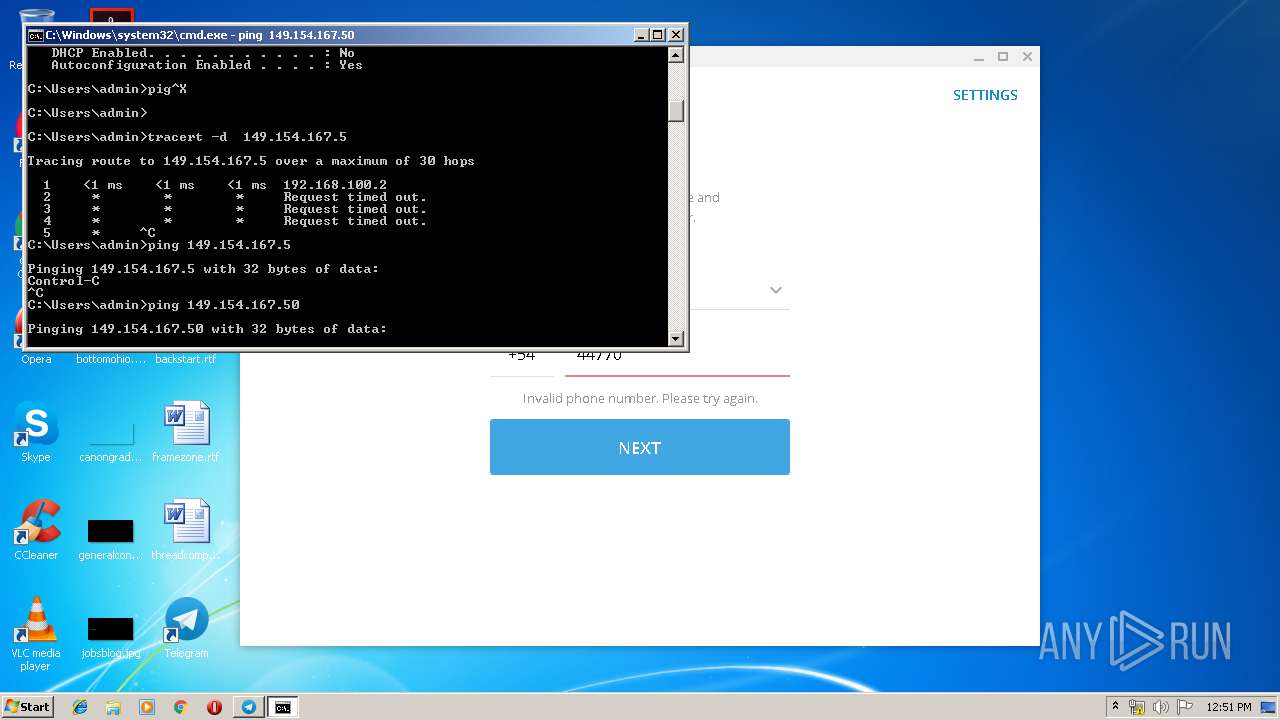
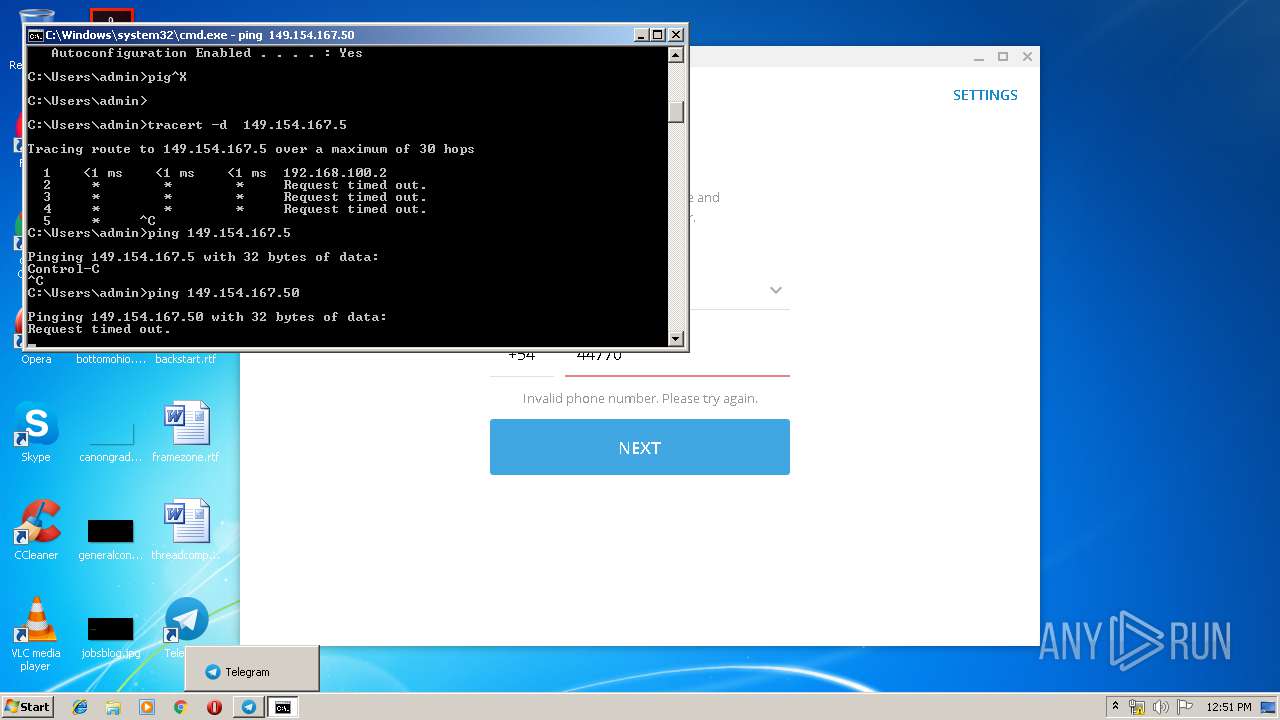
| 2684 | tracert -d 149.154.167.5 | C:\Windows\system32\TRACERT.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Traceroute Command Exit code: 3221225786 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
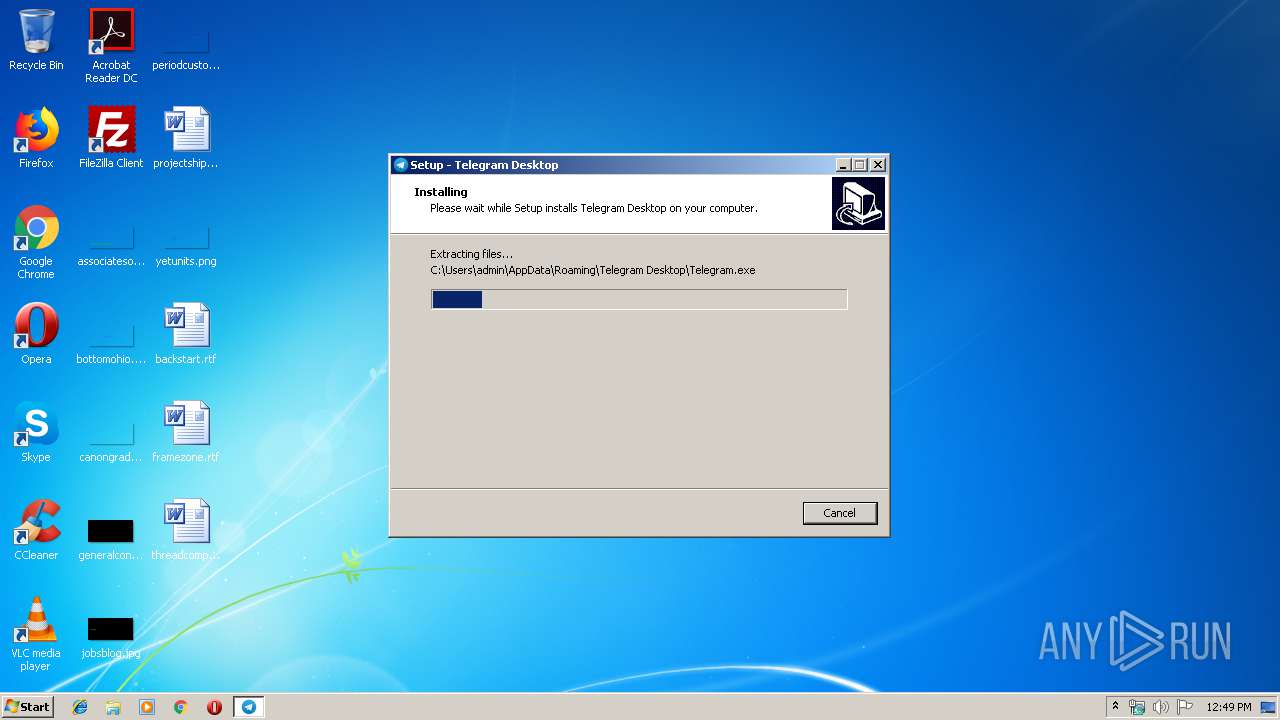
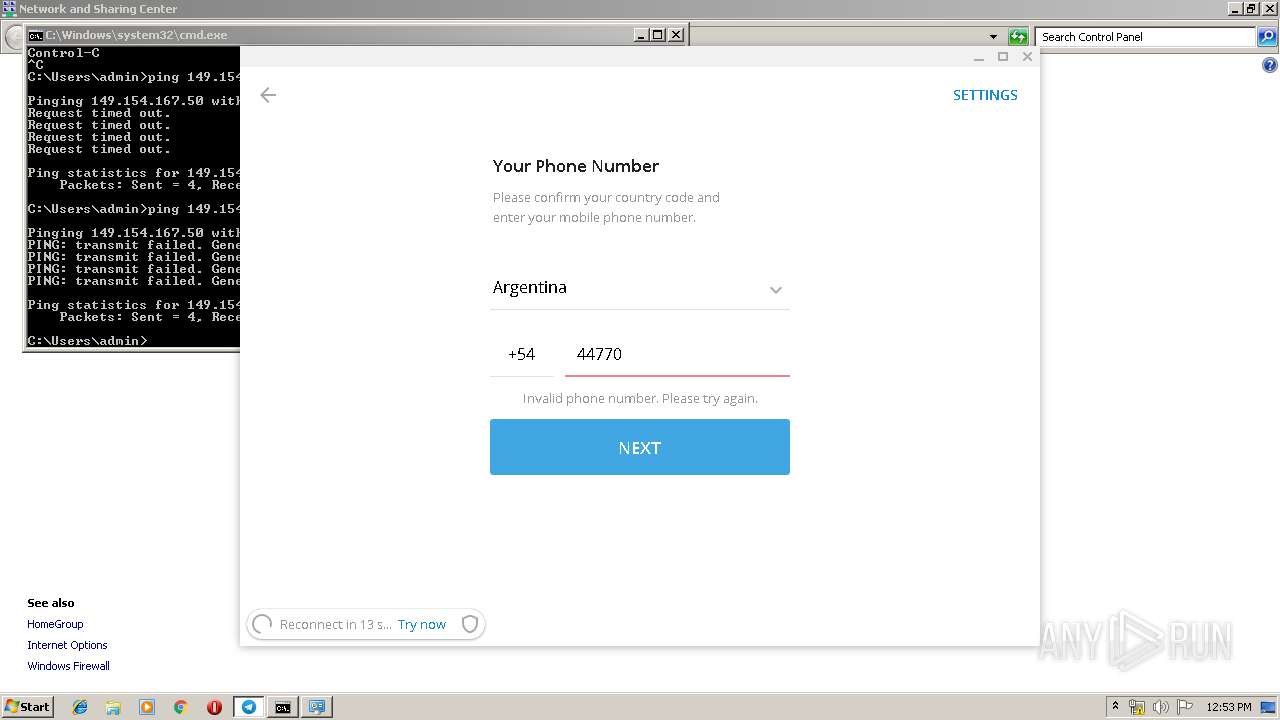
| 2700 | "C:\Users\admin\AppData\Local\Temp\SibinChat.exe" | C:\Users\admin\AppData\Local\Temp\SibinChat.exe | explorer.exe | ||||||||||||
User: admin Company: Telegram Messenger LLP Integrity Level: MEDIUM Description: Telegram Desktop Setup Exit code: 0 Version: 1.3.9.0 Modules
| |||||||||||||||
Total events
1 152
Read events
903
Write events
222
Delete events
27
Modification events
| (PID) Process: | (1376) SibinChat.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 600500004668A692E4DFD401 | |||
| (PID) Process: | (1376) SibinChat.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 7ADA1D5CD3FA6EF4015F332420C908A157C5B2D44193E25C5903246B7EB0FF92 | |||
| (PID) Process: | (1376) SibinChat.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (1376) SibinChat.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
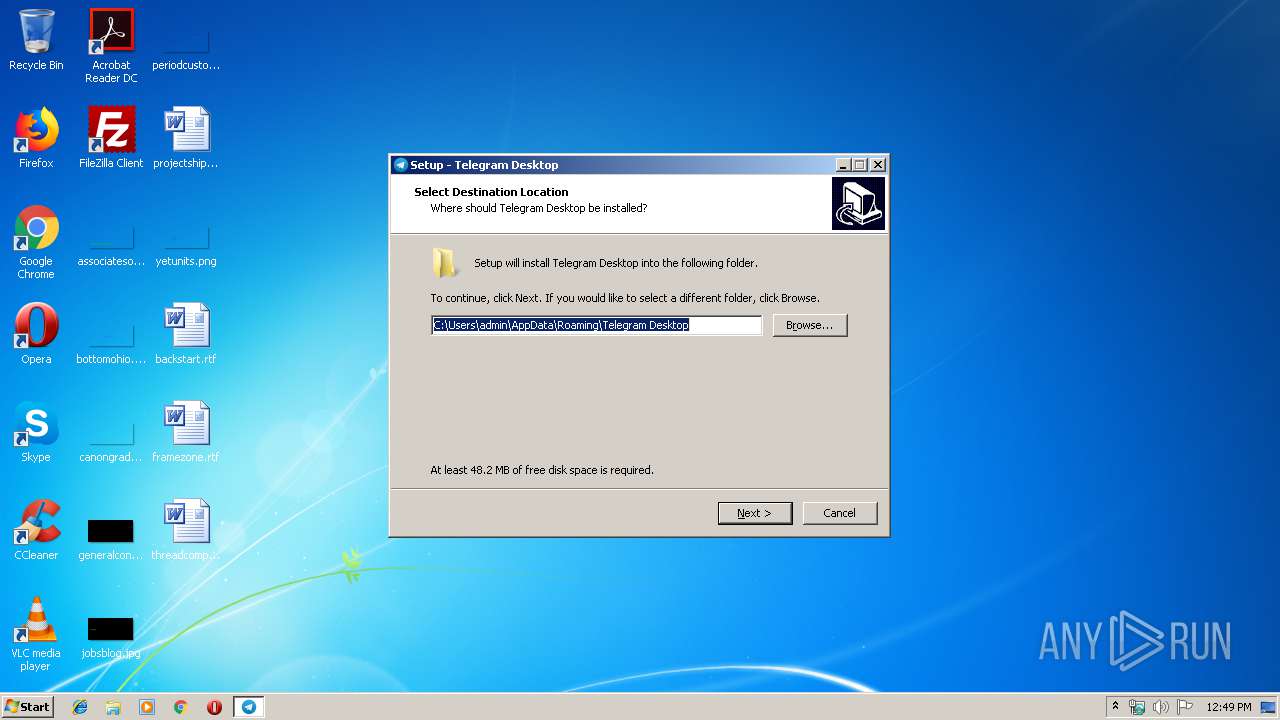
Value: C:\Users\admin\AppData\Roaming\Telegram Desktop\Telegram.exe | |||
| (PID) Process: | (1376) SibinChat.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: D6F3C00D4F0F4701441CD83C8D8183A89335B445E346AF194A0E59FCB64E042B | |||
| (PID) Process: | (1376) SibinChat.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\{53F49750-6209-4FBF-9CA8-7A333C87D1ED}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.5.9 (u) | |||
| (PID) Process: | (1376) SibinChat.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\{53F49750-6209-4FBF-9CA8-7A333C87D1ED}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Users\admin\AppData\Roaming\Telegram Desktop | |||
| (PID) Process: | (1376) SibinChat.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\{53F49750-6209-4FBF-9CA8-7A333C87D1ED}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Roaming\Telegram Desktop\ | |||
| (PID) Process: | (1376) SibinChat.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\{53F49750-6209-4FBF-9CA8-7A333C87D1ED}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: Telegram Desktop | |||
| (PID) Process: | (1376) SibinChat.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\{53F49750-6209-4FBF-9CA8-7A333C87D1ED}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
Executable files
3
Suspicious files
9
Text files
4
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1376 | SibinChat.tmp | C:\Users\admin\AppData\Roaming\Telegram Desktop\is-UPB09.tmp | — | |
MD5:— | SHA256:— | |||
| 1376 | SibinChat.tmp | C:\Users\admin\AppData\Roaming\Telegram Desktop\is-7NNGT.tmp | — | |
MD5:— | SHA256:— | |||
| 1376 | SibinChat.tmp | C:\Users\admin\AppData\Roaming\Telegram Desktop\Telegram.exe | — | |
MD5:— | SHA256:— | |||
| 1376 | SibinChat.tmp | C:\Users\admin\AppData\Roaming\Telegram Desktop\is-KJCA9.tmp | — | |
MD5:— | SHA256:— | |||
| 2864 | Telegram.exe | C:\Users\admin\AppData\Roaming\Telegram Desktop\log_start0.txt | — | |
MD5:— | SHA256:— | |||
| 2864 | Telegram.exe | C:\Users\admin\AppData\Roaming\Telegram Desktop\tdata\D877F783D5D3EF8C0 | — | |
MD5:— | SHA256:— | |||
| 2864 | Telegram.exe | C:\Users\admin\AppData\Roaming\Telegram Desktop\tupdates\tupdate1006001 | — | |
MD5:— | SHA256:— | |||
| 2376 | DeviceDisplayObjectProvider.exe | C:\Users\admin\AppData\Local\Temp\1553172824\PackageInfo.xml | — | |
MD5:— | SHA256:— | |||
| 2376 | DeviceDisplayObjectProvider.exe | C:\Users\admin\AppData\Local\Temp\DEL5C7B.tmp | — | |
MD5:— | SHA256:— | |||
| 2376 | DeviceDisplayObjectProvider.exe | C:\Users\admin\AppData\Local\Temp\DEL5CDA.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
208
DNS requests
103
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
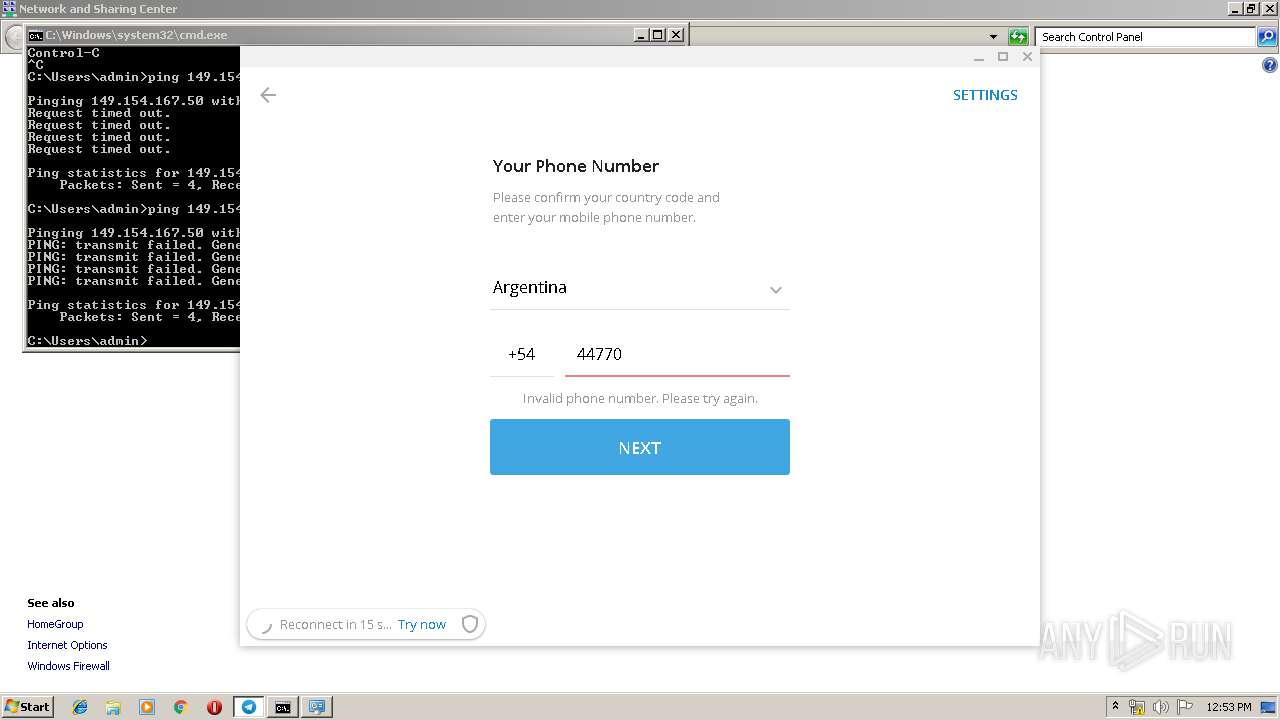
2864 | Telegram.exe | POST | — | 149.154.167.51:80 | http://149.154.167.51:80/api | GB | — | — | suspicious |
2864 | Telegram.exe | POST | — | 149.154.167.51:80 | http://149.154.167.51:80/api | GB | — | — | suspicious |
2864 | Telegram.exe | POST | 200 | 149.154.167.51:80 | http://149.154.167.51:80/api | GB | binary | 84 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2864 | Telegram.exe | 149.154.167.51:443 | — | Telegram Messenger LLP | GB | suspicious |
2864 | Telegram.exe | 149.154.167.51:80 | — | Telegram Messenger LLP | GB | suspicious |
2864 | Telegram.exe | 149.154.175.100:443 | — | Telegram Messenger LLP | GB | suspicious |
2864 | Telegram.exe | 149.154.167.92:443 | — | Telegram Messenger LLP | GB | suspicious |
2864 | Telegram.exe | 91.108.56.190:443 | — | Telegram Messenger LLP | NL | unknown |
2864 | Telegram.exe | 91.108.56.190:80 | — | Telegram Messenger LLP | NL | unknown |
2864 | Telegram.exe | 91.108.56.143:80 | — | Telegram Messenger LLP | NL | unknown |
2864 | Telegram.exe | 149.154.175.50:443 | — | Telegram Messenger LLP | GB | suspicious |
2864 | Telegram.exe | 149.154.175.50:80 | — | Telegram Messenger LLP | GB | suspicious |
— | — | 91.108.56.190:443 | — | Telegram Messenger LLP | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
updates.tdesktop.com |
| suspicious |
google.ru |
| whitelisted |
software-download.microsoft.com |
| whitelisted |
www.google.com |
| malicious |
google.com |
| malicious |
www.google.ru |
| whitelisted |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2864 | Telegram.exe | Misc activity | APP [PTsecurity] Telegram Messenger v3 HTTP |
2864 | Telegram.exe | Misc activity | APP [PTsecurity] Telegram Messenger v3 HTTP |
Process | Message |
|---|---|
mmc.exe | ViewerConfigPath = 'C:\ProgramData\Microsoft\Event Viewer': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerViewsFolderPath = 'C:\ProgramData\Microsoft\Event Viewer\Views': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerAdminViewsPath = 'C:\ProgramData\Microsoft\Event Viewer\Views\ApplicationViewsRootNode': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerExternalLogsPath = 'C:\ProgramData\Microsoft\Event Viewer\ExternalLogs': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerExtension
|