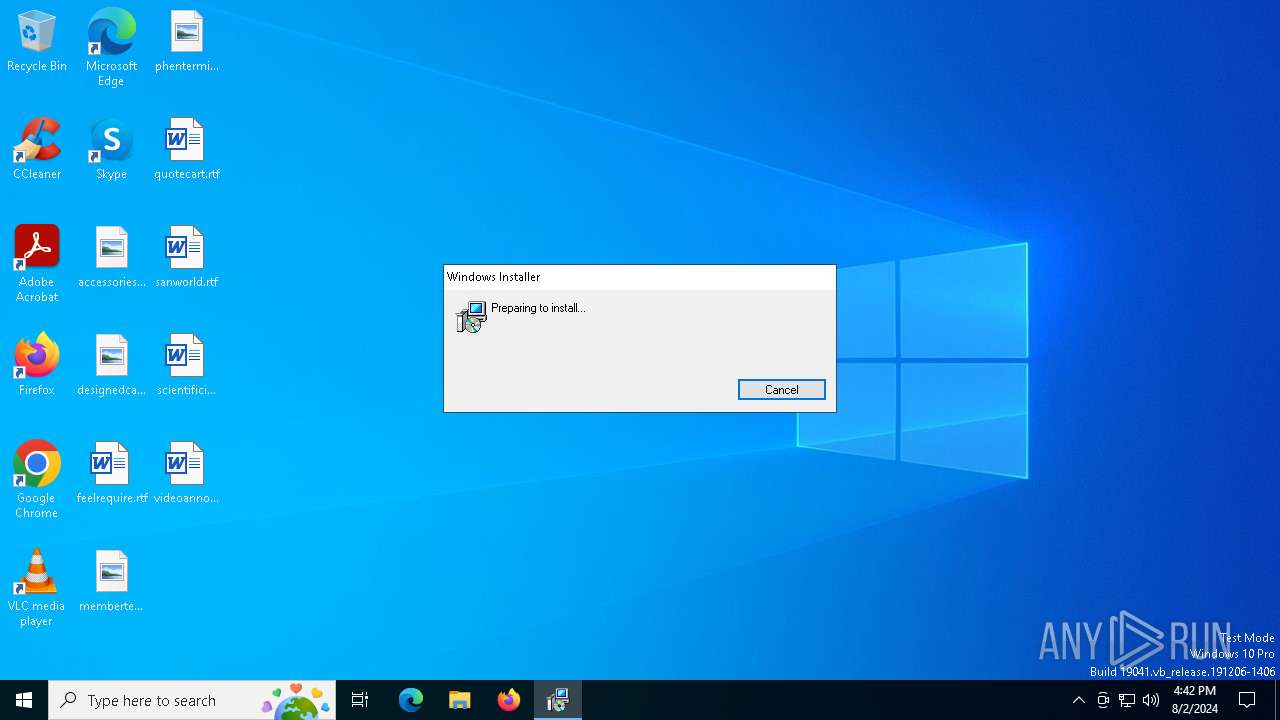
| File name: | Registration.msi |
| Full analysis: | https://app.any.run/tasks/6512ab62-f52d-456b-adbc-ab06768ede7b |
| Verdict: | Malicious activity |
| Analysis date: | August 02, 2024, 16:42:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Code page: 1252, Title: Installation Database, Subject: AteraAgent, Author: Atera networks, Keywords: Installer, Comments: This installer database contains the logic and data required to install AteraAgent., Template: Intel;1033, Revision Number: {721AD955-79FD-4019-BBF5-9DCC4C1175BB}, Create Time/Date: Wed Feb 28 10:52:02 2024, Last Saved Time/Date: Wed Feb 28 10:52:02 2024, Number of Pages: 200, Number of Words: 6, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | 4BE545C295F8D133189A35EACBAACEE0 |
| SHA1: | C269F7A962799F9A7D97A7AFF039CDD0A9643BD6 |
| SHA256: | 3A215A179B2F6F257BAEAAA49A5E765D58C705816E8268BA54BE2B06F594E2CE |
| SSDEEP: | 98304:4IZTffzvns6eLKLdpRwznfsJb+7J7ERXndiWaKzPtSjXmbABY/lT8vjkZBvrePVv:93XP9No |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 6260)
- msiexec.exe (PID: 6448)
- AteraAgent.exe (PID: 1564)
ATERAAGENT has been detected (YARA)
- msiexec.exe (PID: 6448)
Starts NET.EXE for service management
- msiexec.exe (PID: 6960)
- net.exe (PID: 3376)
Bypass execution policy to execute commands
- powershell.exe (PID: 7404)
- powershell.exe (PID: 4760)
Changes powershell execution policy (Bypass)
- AgentPackageAgentInformation.exe (PID: 6928)
- AgentPackageAgentInformation.exe (PID: 2680)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 6496)
- AteraAgent.exe (PID: 1564)
- AteraAgent.exe (PID: 7156)
Process drops legitimate windows executable
- msiexec.exe (PID: 6448)
- rundll32.exe (PID: 6492)
- rundll32.exe (PID: 2720)
- rundll32.exe (PID: 2360)
- rundll32.exe (PID: 6932)
- AteraAgent.exe (PID: 1564)
Checks Windows Trust Settings
- msiexec.exe (PID: 6448)
- AteraAgent.exe (PID: 6560)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6448)
Executable content was dropped or overwritten
- rundll32.exe (PID: 2360)
- rundll32.exe (PID: 6492)
- rundll32.exe (PID: 2720)
- AteraAgent.exe (PID: 1564)
- rundll32.exe (PID: 6932)
Reads security settings of Internet Explorer
- AteraAgent.exe (PID: 6560)
- AteraAgent.exe (PID: 1564)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 6960)
Starts SC.EXE for service management
- AteraAgent.exe (PID: 1564)
- AteraAgent.exe (PID: 7156)
Starts CMD.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 6928)
- AgentPackageAgentInformation.exe (PID: 2680)
Reads the date of Windows installation
- AteraAgent.exe (PID: 1564)
Executes application which crashes
- cscript.exe (PID: 7572)
- cscript.exe (PID: 7560)
Starts POWERSHELL.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 6928)
- AgentPackageAgentInformation.exe (PID: 2680)
- cmd.exe (PID: 7852)
- cmd.exe (PID: 7816)
Potential Corporate Privacy Violation
- AteraAgent.exe (PID: 1564)
- rundll32.exe (PID: 6492)
- rundll32.exe (PID: 6932)
The process executes Powershell scripts
- cmd.exe (PID: 7852)
- cmd.exe (PID: 7816)
The process executes VB scripts
- cmd.exe (PID: 7424)
- cmd.exe (PID: 7416)
INFO
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6260)
Creates files or folders in the user directory
- msiexec.exe (PID: 6260)
Checks proxy server information
- msiexec.exe (PID: 6260)
- rundll32.exe (PID: 6492)
- rundll32.exe (PID: 6932)
Reads the computer name
- msiexec.exe (PID: 6448)
- msiexec.exe (PID: 3812)
- msiexec.exe (PID: 6960)
- AteraAgent.exe (PID: 6560)
- AteraAgent.exe (PID: 1564)
Checks supported languages
- msiexec.exe (PID: 6448)
- msiexec.exe (PID: 3812)
- msiexec.exe (PID: 6960)
- AteraAgent.exe (PID: 1564)
- AteraAgent.exe (PID: 6560)
Reads the software policy settings
- msiexec.exe (PID: 6260)
- msiexec.exe (PID: 6448)
- rundll32.exe (PID: 6492)
- AteraAgent.exe (PID: 6560)
- AteraAgent.exe (PID: 1564)
- rundll32.exe (PID: 6932)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6448)
- AteraAgent.exe (PID: 6560)
- AteraAgent.exe (PID: 1564)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6448)
Create files in a temporary directory
- rundll32.exe (PID: 2360)
- rundll32.exe (PID: 6492)
- rundll32.exe (PID: 2720)
- rundll32.exe (PID: 6932)
Drops the executable file immediately after the start
- rundll32.exe (PID: 6492)
- rundll32.exe (PID: 2720)
- rundll32.exe (PID: 2360)
- rundll32.exe (PID: 6932)
Disables trace logs
- rundll32.exe (PID: 6492)
- AteraAgent.exe (PID: 1564)
- rundll32.exe (PID: 6932)
Creates files in the program directory
- AteraAgent.exe (PID: 6560)
Reads Environment values
- AteraAgent.exe (PID: 6560)
- AteraAgent.exe (PID: 1564)
Creates a software uninstall entry
- msiexec.exe (PID: 6448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | AteraAgent |
| Author: | Atera networks |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install AteraAgent. |
| Template: | Intel;1033 |
| RevisionNumber: | {721AD955-79FD-4019-BBF5-9DCC4C1175BB} |
| CreateDate: | 2024:02:28 10:52:02 |
| ModifyDate: | 2024:02:28 10:52:02 |
| Pages: | 200 |
| Words: | 6 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
193
Monitored processes
55
Malicious processes
2
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AgentPackageAgentInformation.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1248 | powershell.exe -File "C:\Program Files\Microsoft Office\Office16\vNextDiag.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1564 | "C:\Program Files (x86)\ATERA Networks\AteraAgent\AteraAgent.exe" | C:\Program Files (x86)\ATERA Networks\AteraAgent\AteraAgent.exe | services.exe | ||||||||||||
User: SYSTEM Company: ATERA Networks Ltd. Integrity Level: SYSTEM Description: AteraAgent Version: 1.8.7.2 Modules
| |||||||||||||||
| 2360 | rundll32.exe "C:\WINDOWS\Installer\MSID8F6.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_973218 2 AlphaControlAgentInstallation!AlphaControlAgentInstallation.CustomActions.GenerateAgentId | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2680 | "C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageAgentInformation\AgentPackageAgentInformation.exe" 475ae441-14ae-46be-8939-e894c554db04 "8b32f2c0-2da6-4fce-8b97-2c8758b7730c" agent-api.atera.com/Production 443 or8ixLi90Mf "generalinfo fromGui" 001Q300000Kgx52IAB | C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageAgentInformation\AgentPackageAgentInformation.exe | — | AteraAgent.exe | |||||||||||
User: SYSTEM Company: Atera Networks Integrity Level: SYSTEM Description: AgentPackageAgentInformation Version: 37.2.0.0 | |||||||||||||||
| 2720 | rundll32.exe "C:\WINDOWS\Installer\MSIE03C.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_974937 10 AlphaControlAgentInstallation!AlphaControlAgentInstallation.CustomActions.ShouldContinueInstallation | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3032 | "TaskKill.exe" /f /im AteraAgent.exe | C:\Windows\SysWOW64\taskkill.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3376 | "NET" STOP AteraAgent | C:\Windows\SysWOW64\net.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3812 | C:\Windows\syswow64\MsiExec.exe -Embedding 8ACDADACC74DA0E6B5305295EBC23865 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4364 | "C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageAgentInformation\AgentPackageAgentInformation.exe" 475ae441-14ae-46be-8939-e894c554db04 "48f63a96-c382-4e69-b746-74b74cb41014" agent-api.atera.com/Production 443 or8ixLi90Mf "identified" 001Q300000Kgx52IAB | C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageAgentInformation\AgentPackageAgentInformation.exe | — | AteraAgent.exe | |||||||||||
User: SYSTEM Company: Atera Networks Integrity Level: SYSTEM Description: AgentPackageAgentInformation Exit code: 0 Version: 37.2.0.0 | |||||||||||||||
Total events
21 084
Read events
20 760
Write events
305
Delete events
19
Modification events
| (PID) Process: | (6448) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000516A3F09FBE4DA013019000050190000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6448) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000079CE4109FBE4DA013019000050190000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6448) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000002812E30AFBE4DA013019000050190000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6448) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000002812E30AFBE4DA013019000050190000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6448) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000A4CD060BFBE4DA013019000050190000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6448) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000BC31090BFBE4DA013019000050190000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6448) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (6448) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 48000000000000005FEBBF0CFBE4DA013019000050190000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6448) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000AC9EC40CFBE4DA0130190000D4190000E8030000010000000000000000000000E119709437627C4E9EF96938E8AFC25900000000000000000000000000000000 | |||
| (PID) Process: | (6496) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000005ACACB0CFBE4DA016019000088190000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
56
Suspicious files
48
Text files
30
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6448 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6260 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:51D3B597FCEAC45F40BBC79BCDAF498D | SHA256:116CB73594E1828868F903970E67463688101E2627D50B122BD762FA95464328 | |||
| 6260 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | der | |
MD5:2FE44C94E0E9C088AE4E21BCB0856A1C | SHA256:5884545BE81CD89EC21374E05E8387DFC9E66CEEE63874C592C3038326D07F08 | |||
| 2360 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSID8F6.tmp-\System.Management.dll | executable | |
MD5:878E361C41C05C0519BFC72C7D6E141C | SHA256:24DE61B5CAB2E3495FE8D817FB6E80094662846F976CF38997987270F8BBAE40 | |||
| 2360 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSID8F6.tmp-\CustomAction.config | xml | |
MD5:BC17E956CDE8DD5425F2B2A68ED919F8 | SHA256:E4FF538599C2D8E898D7F90CCF74081192D5AFA8040E6B6C180F3AA0F46AD2C5 | |||
| 6492 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSIDC82.tmp-\Newtonsoft.Json.dll | executable | |
MD5:715A1FBEE4665E99E859EDA667FE8034 | SHA256:C5C83BBC1741BE6FF4C490C0AEE34C162945423EC577C646538B2D21CE13199E | |||
| 6492 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSIDC82.tmp-\Microsoft.Deployment.WindowsInstaller.dll | executable | |
MD5:1A5CAEA6734FDD07CAA514C3F3FB75DA | SHA256:CF06D4ED4A8BAF88C82D6C9AE0EFC81C469DE6DA8788AB35F373B350A4B4CDCA | |||
| 6448 | msiexec.exe | C:\Windows\Installer\MSIDC82.tmp | executable | |
MD5:88D29734F37BDCFFD202EAFCDD082F9D | SHA256:87C97269E2B68898BE87B884CD6A21880E6F15336B1194713E12A2DB45F1DCCF | |||
| 6260 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8EC9B1D0ABBD7F98B401D425828828CE_DEB07B5578A606ED6489DDA2E357A944 | der | |
MD5:4C3749BC4A3450321B4D541BF16DCA43 | SHA256:023FDA5307F4712B7C1B749A42CB6CA3FDF9A2AF5EB3332E3D88502247E304AE | |||
| 6492 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSIDC82.tmp-\AlphaControlAgentInstallation.dll | executable | |
MD5:AA1B9C5C685173FAD2DABEBEB3171F01 | SHA256:E44A6582CD3F84F4255D3C230E0A2C284E0CFFA0CA5E62E4D749E089555494C7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
53
DNS requests
21
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6260 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
6260 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
6260 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAooSZl45YmN9AojjrilUug%3D | unknown | — | — | whitelisted |
1536 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1536 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6208 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4540 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6560 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
6560 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAooSZl45YmN9AojjrilUug%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6260 | msiexec.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
568 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 104.126.37.161:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1536 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
19 ETPRO signatures available at the full report