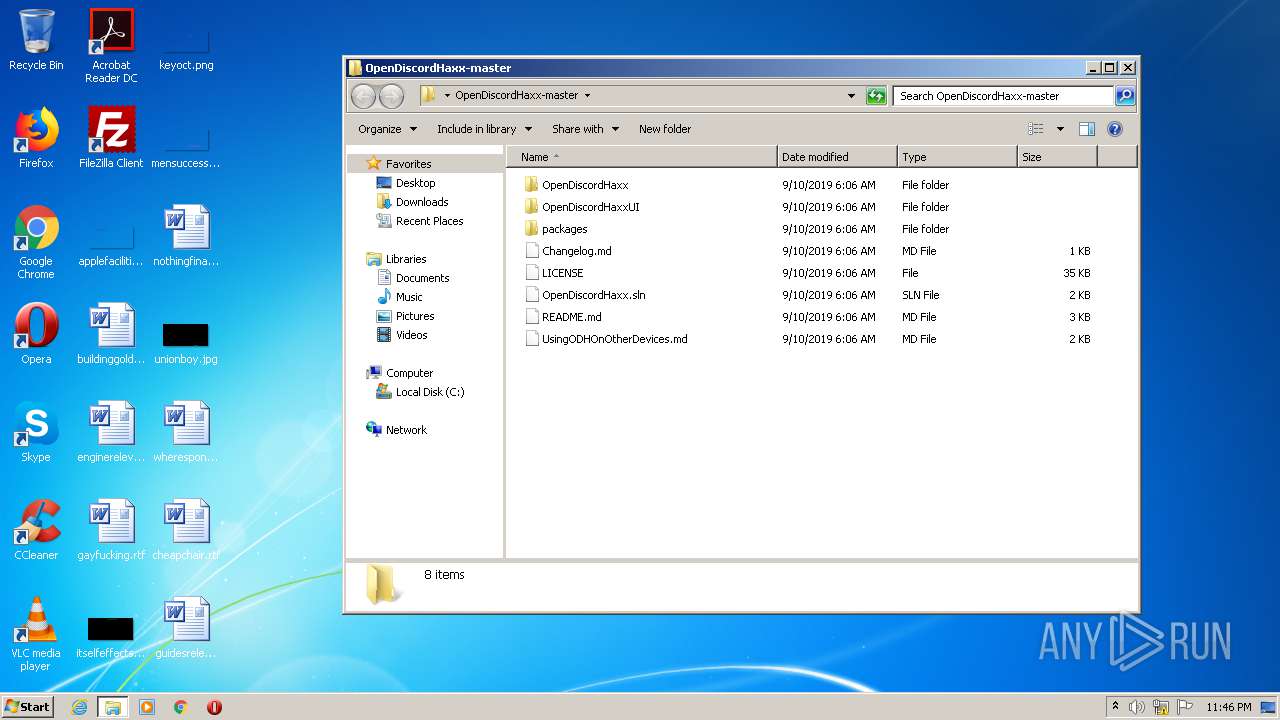
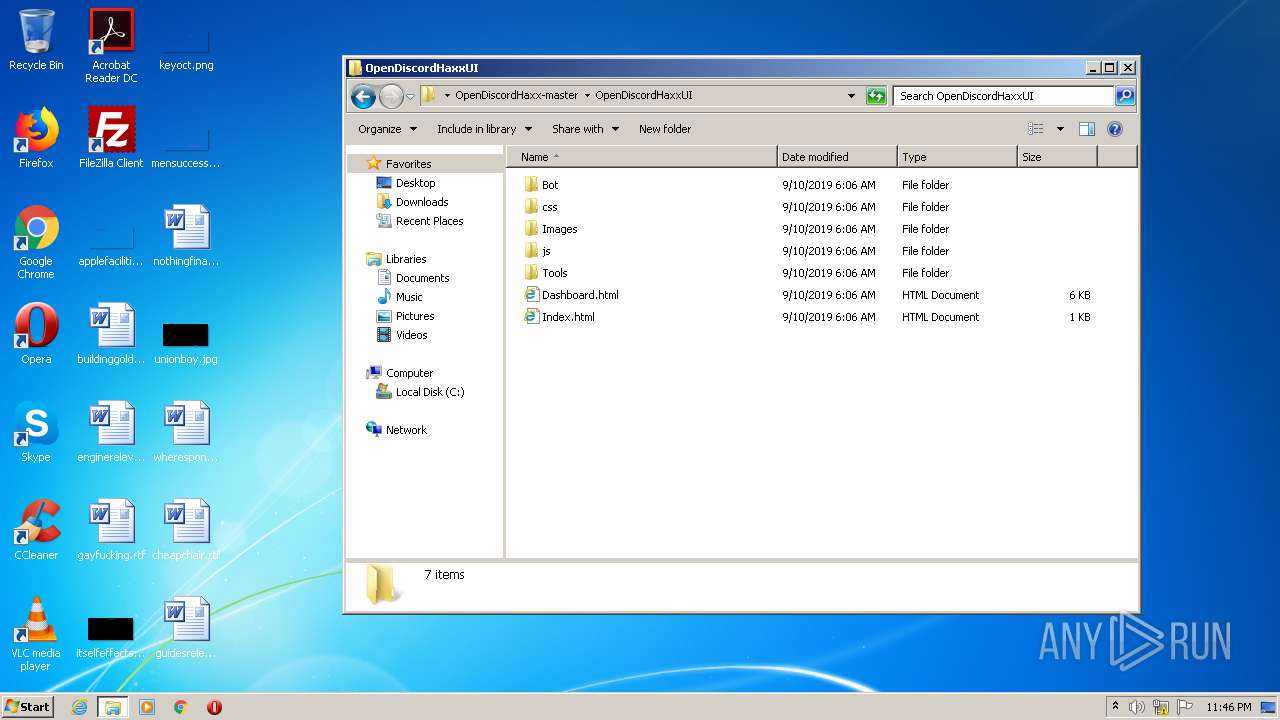
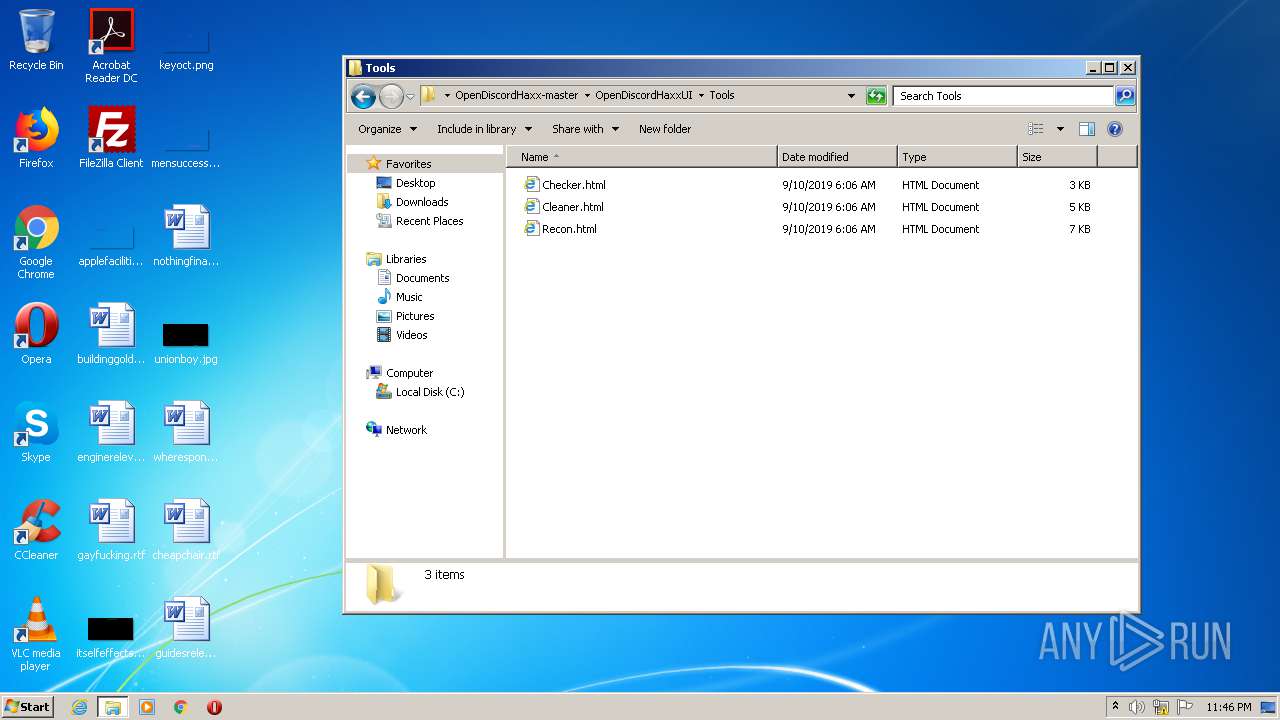
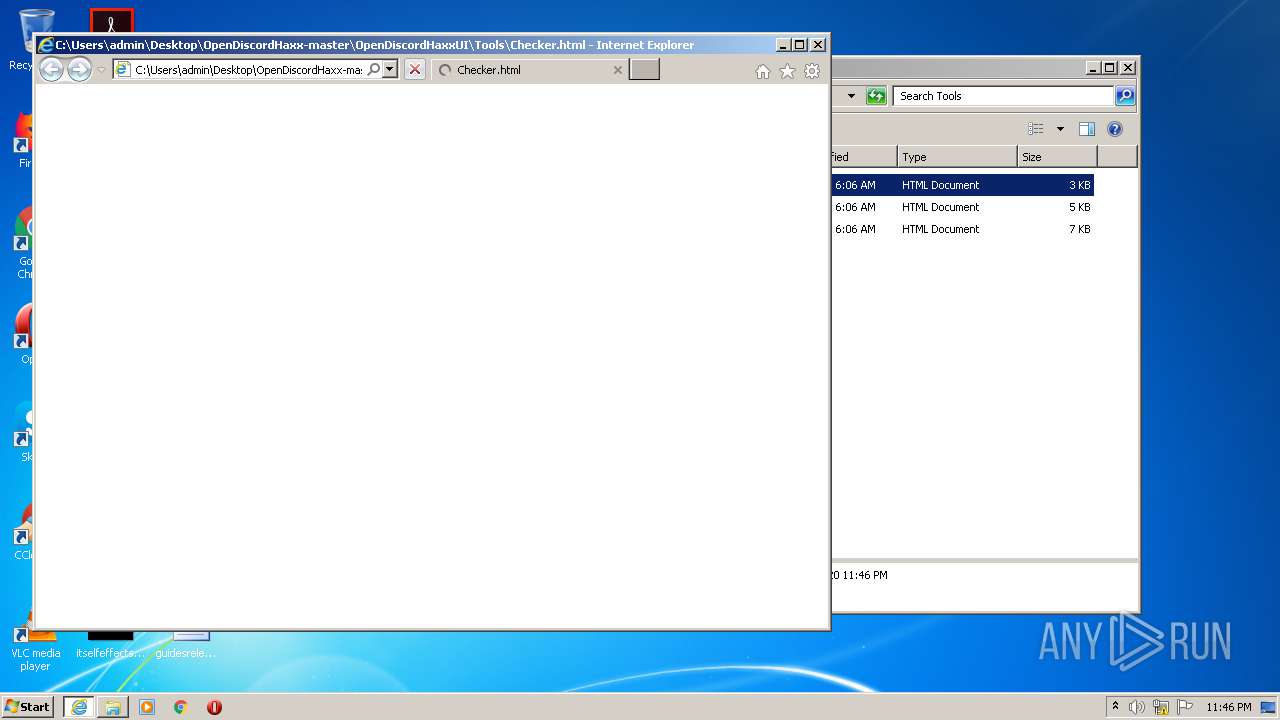
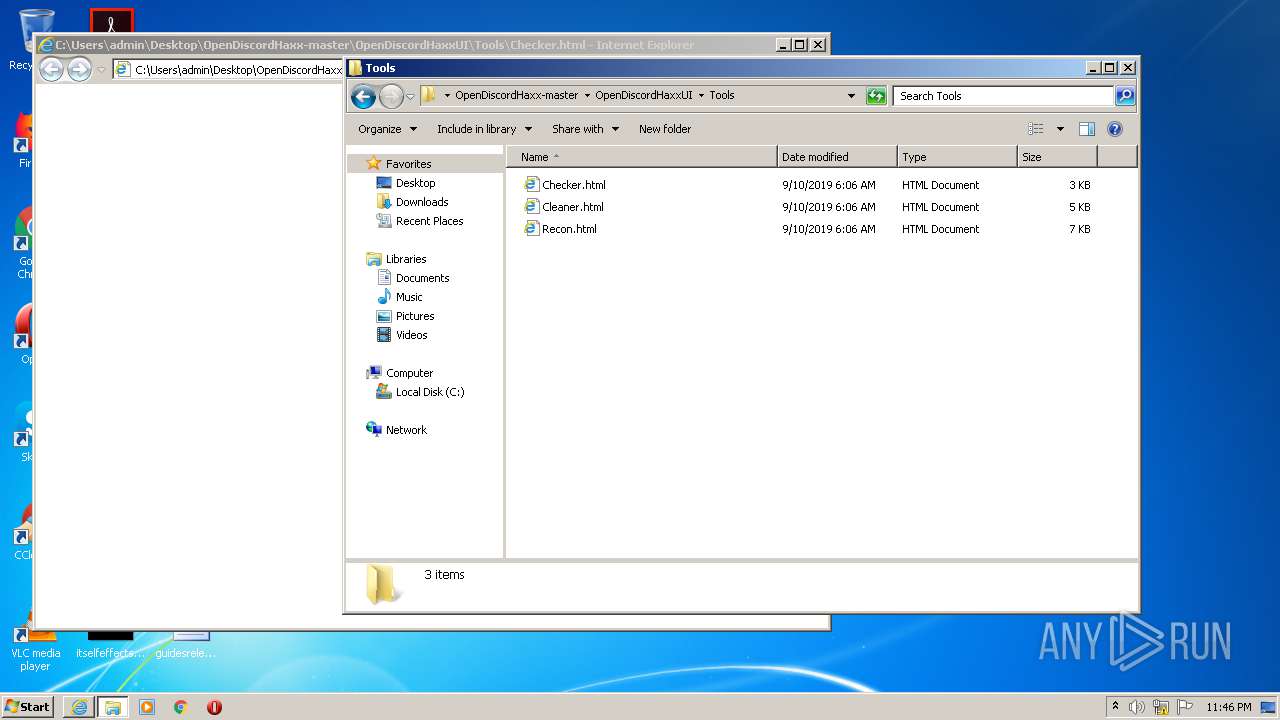
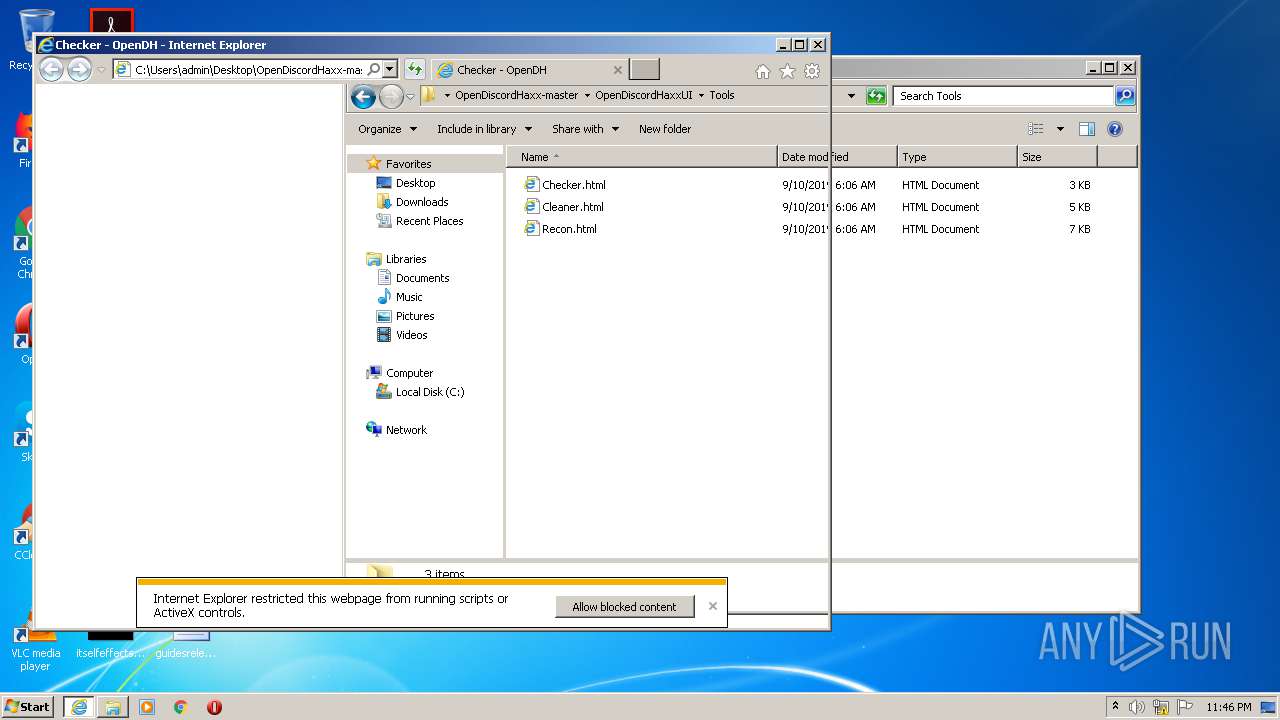
| File name: | OpenDiscordHaxx-master.zip |
| Full analysis: | https://app.any.run/tasks/ba3aa8f0-52bf-44f7-ad80-6139d78a318d |
| Verdict: | Malicious activity |
| Analysis date: | October 19, 2020, 22:46:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 793E61BCCD714F11D74F663A1BB5A518 |
| SHA1: | A50F08D451EA31301CC5D25DEE27EA8D9B009097 |
| SHA256: | 3A1CD8CFE27099E144C0A63E24649E1377E7F7A747D2DEA25F3B43C8772C61DB |
| SSDEEP: | 196608:x292JFP5D52JFuP7RAiU7tOSs8+A+2JFH+uHCmMmw669vkniNDq:xA2vL2OP9DlA+2Ximy1/Dq |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 996)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3288)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 1924)
Manual execution by user
- iexplore.exe (PID: 1924)
Reads internet explorer settings
- iexplore.exe (PID: 1752)
Changes internet zones settings
- iexplore.exe (PID: 1924)
Reads settings of System Certificates
- iexplore.exe (PID: 1752)
- iexplore.exe (PID: 1924)
Changes settings of System certificates
- iexplore.exe (PID: 1752)
- iexplore.exe (PID: 1924)
Application launched itself
- iexplore.exe (PID: 1924)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1752)
- iexplore.exe (PID: 1924)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:09:09 22:06:16 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | OpenDiscordHaxx-master/ |
Total processes
39
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 996 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1752 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1924 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1924 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\Desktop\OpenDiscordHaxx-master\OpenDiscordHaxxUI\Tools\Checker.html | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3288 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\OpenDiscordHaxx-master.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
2 207
Read events
2 065
Write events
136
Delete events
6
Modification events
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\OpenDiscordHaxx-master.zip | |||
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
24
Suspicious files
24
Text files
143
Unknown types
24
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3288 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3288.42566\OpenDiscordHaxx-master\Changelog.md | text | |
MD5:FB3D23D507B110219ADF3F626C1A7272 | SHA256:9B6470958BDC90CBA389B6B0ABB9050B895F221B1BCBB608180F3CB76328397F | |||
| 3288 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3288.42566\OpenDiscordHaxx-master\OpenDiscordHaxx\App.config | xml | |
MD5:335975BEBFD5E539FE2025FEAFF497E3 | SHA256:B0D8835D6D7686426FE217A3407B3CAC3AFFA286CA9F59763C5594DB76264F72 | |||
| 3288 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3288.42566\OpenDiscordHaxx-master\OpenDiscordHaxx\BotList\Requests\BotRequest.cs | text | |
MD5:562EA8FBAB57D7C97A11D45C30557A49 | SHA256:2565F3BB91AAEE238B5AB75F5BCAE9E843AF796A21FECAF7A8CBEB4A3DFC6B3D | |||
| 3288 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3288.42566\OpenDiscordHaxx-master\OpenDiscordHaxx\BotList\Endpoint.cs | text | |
MD5:14F88671E1085DB1D7BA27AC09600416 | SHA256:A83DD4BFB9B83A8B43EAF5F2A14DAC4344DF2BF13F91DED0292FC0B2B2421BB0 | |||
| 3288 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3288.42566\OpenDiscordHaxx-master\OpenDiscordHaxx\BotList\Requests\List\ListAction.cs | text | |
MD5:764CF6ECC3EDAAB2F0861B088310FB24 | SHA256:4A6B2C99885A7BA23DC936140E4DF74CFF9A5CF53AC048B26E3A5FC1210829F4 | |||
| 3288 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3288.42566\OpenDiscordHaxx-master\OpenDiscordHaxx\BotList\Requests\DiscordImage.cs | text | |
MD5:81C6074B7F485E2252C99C5FDB6E16A5 | SHA256:F0F5CEC77AA7E37A7A274B058FCA4F1F3ADEEB02E57F1A6A504BA1BC20EEDF28 | |||
| 3288 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3288.42566\OpenDiscordHaxx-master\OpenDiscordHaxx.sln | text | |
MD5:2B39EE3EE7D31BBDCDEC7013974963C1 | SHA256:4935092A8C0267CF8305B593FC7B5E638ECB7C93FE02CD06D3E5E7BA1107CB79 | |||
| 3288 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3288.42566\OpenDiscordHaxx-master\OpenDiscordHaxx\BotList\Requests\List\BasicBotInfo.cs | text | |
MD5:4EDDD64857A221149254BC357E178568 | SHA256:91292C858D4CDBAAC38416B98EA291B83E7B34585C013DCE36F667763334106C | |||
| 3288 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3288.42566\OpenDiscordHaxx-master\OpenDiscordHaxx\BotList\Requests\Token.cs | text | |
MD5:B76AA81C2816976548500D31EA63D65B | SHA256:2EC93A55F932D21E54A01D45BEF01897104C5075CA31BC532DC5B97B190129BD | |||
| 3288 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3288.42566\OpenDiscordHaxx-master\OpenDiscordHaxx\BotList\Requests\List\List.cs | text | |
MD5:AF6FDA63B07F5A476ADC6B96E93274C4 | SHA256:4F7F451CD4F4141B08D604DC04A03D012F4EEB8A5970D8230E8203BACE06C6BA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
20
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1752 | iexplore.exe | GET | 200 | 172.217.22.67:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEFdRKRguoh2MCAAAAABdwf0%3D | US | der | 471 b | whitelisted |
1752 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
1752 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
1752 | iexplore.exe | GET | 200 | 172.217.22.67:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQD6dnW313dJuggAAAAAXcH8 | US | der | 472 b | whitelisted |
1752 | iexplore.exe | GET | 200 | 172.217.22.67:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQD6dnW313dJuggAAAAAXcH8 | US | der | 472 b | whitelisted |
1752 | iexplore.exe | GET | 200 | 172.217.22.67:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCOUTy4wn8XWggAAAAAWy8I | US | der | 472 b | whitelisted |
1752 | iexplore.exe | GET | 200 | 172.217.22.67:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
1752 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
1752 | iexplore.exe | GET | 200 | 172.217.22.67:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
1924 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1752 | iexplore.exe | 209.197.3.15:443 | maxcdn.bootstrapcdn.com | Highwinds Network Group, Inc. | US | whitelisted |
1752 | iexplore.exe | 216.58.210.10:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
1752 | iexplore.exe | 216.58.205.234:443 | ajax.googleapis.com | Google Inc. | US | whitelisted |
— | — | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
1752 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1924 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1752 | iexplore.exe | 172.217.22.67:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
1752 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
1752 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1924 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fonts.googleapis.com |
| whitelisted |
maxcdn.bootstrapcdn.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |