| File name: | OpenDiscordHaxx-master.zip |
| Full analysis: | https://app.any.run/tasks/7e82c220-49a2-462c-bd9e-75db5b5e01a9 |
| Verdict: | Malicious activity |
| Analysis date: | October 19, 2020, 22:55:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 793E61BCCD714F11D74F663A1BB5A518 |
| SHA1: | A50F08D451EA31301CC5D25DEE27EA8D9B009097 |
| SHA256: | 3A1CD8CFE27099E144C0A63E24649E1377E7F7A747D2DEA25F3B43C8772C61DB |
| SSDEEP: | 196608:x292JFP5D52JFuP7RAiU7tOSs8+A+2JFH+uHCmMmw669vkniNDq:xA2vL2OP9DlA+2Ximy1/Dq |
MALICIOUS
No malicious indicators.SUSPICIOUS
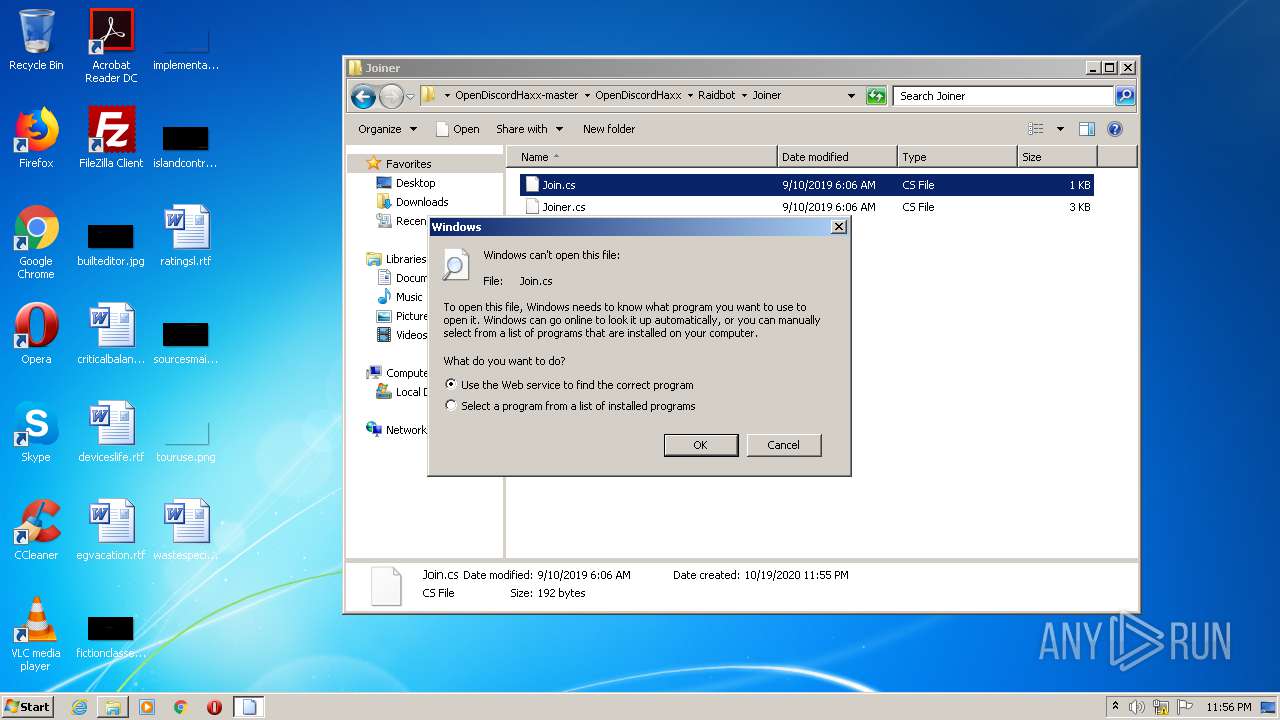
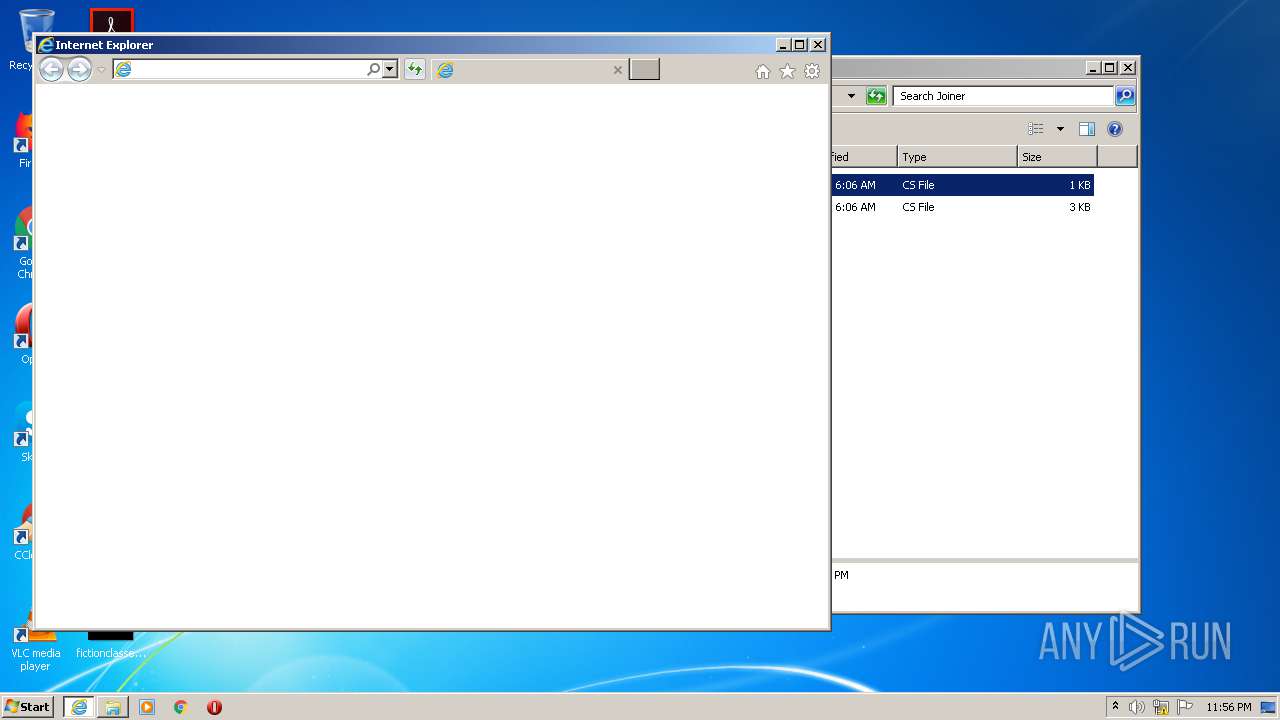
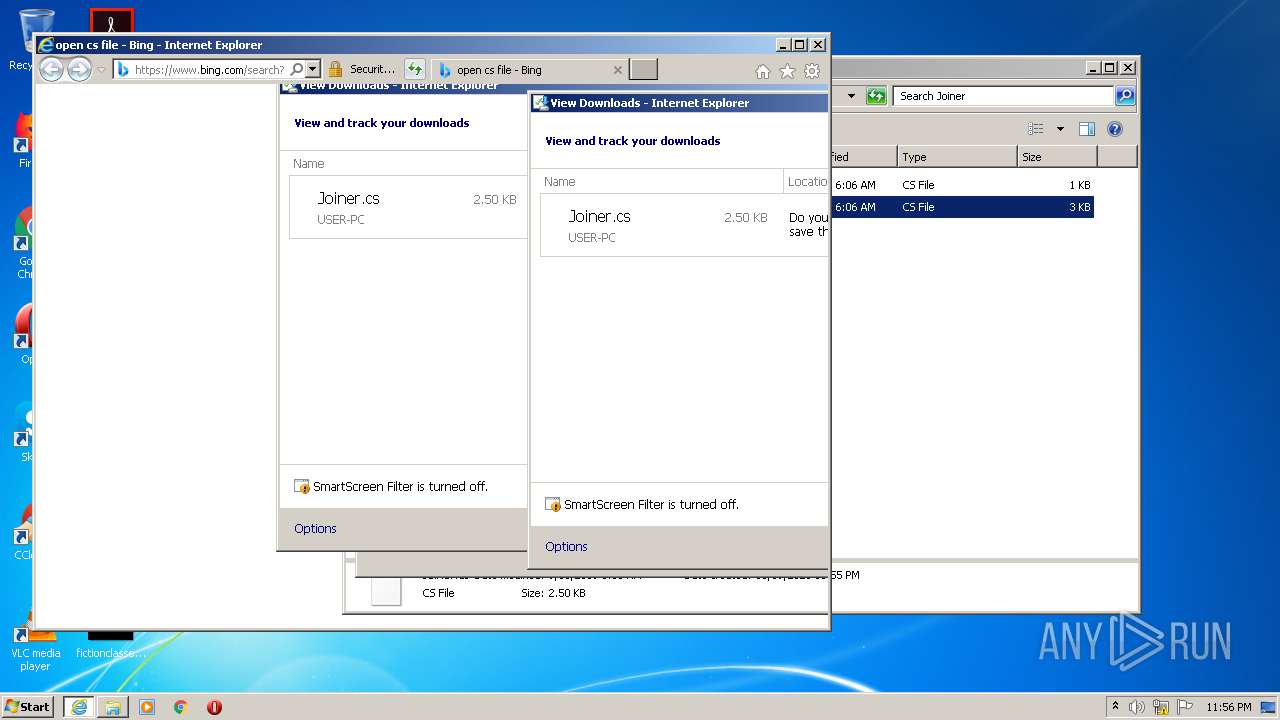
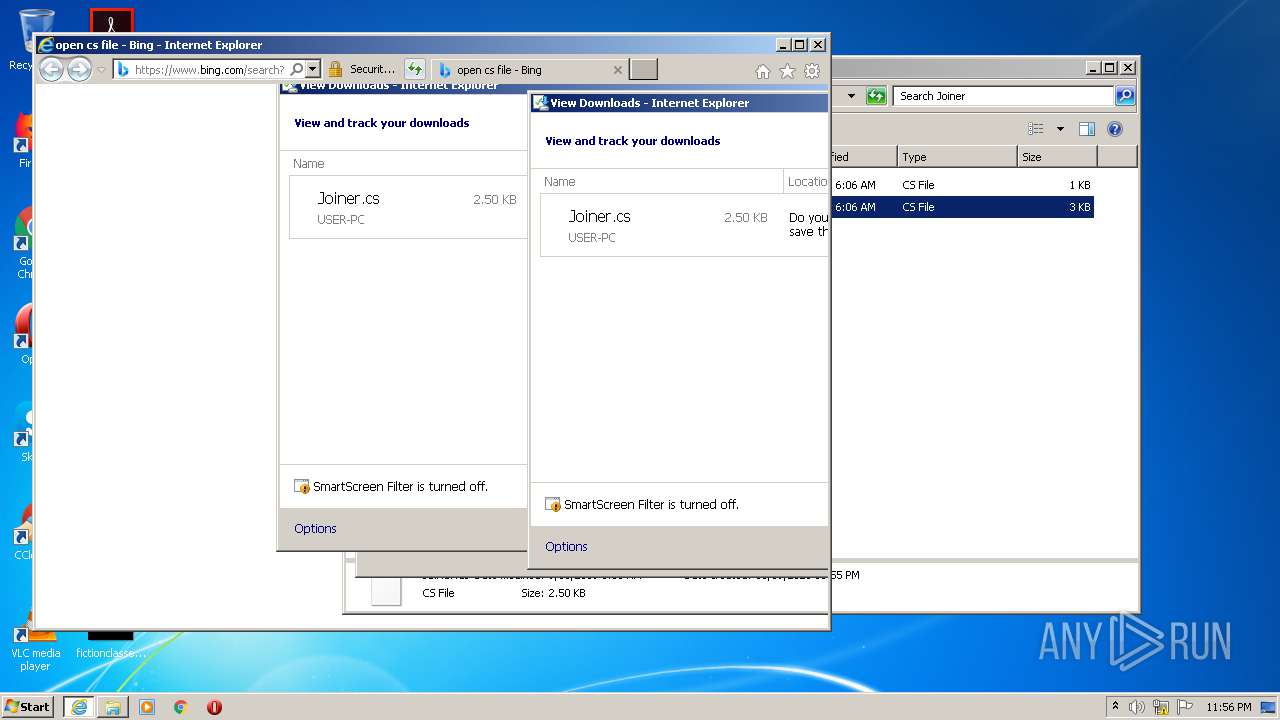
Starts Internet Explorer
- rundll32.exe (PID: 1136)
INFO
Application launched itself
- iexplore.exe (PID: 2492)
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 3568)
Reads settings of System Certificates
- iexplore.exe (PID: 2528)
- iexplore.exe (PID: 2492)
Manual execution by user
- rundll32.exe (PID: 1136)
- rundll32.exe (PID: 4004)
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 3568)
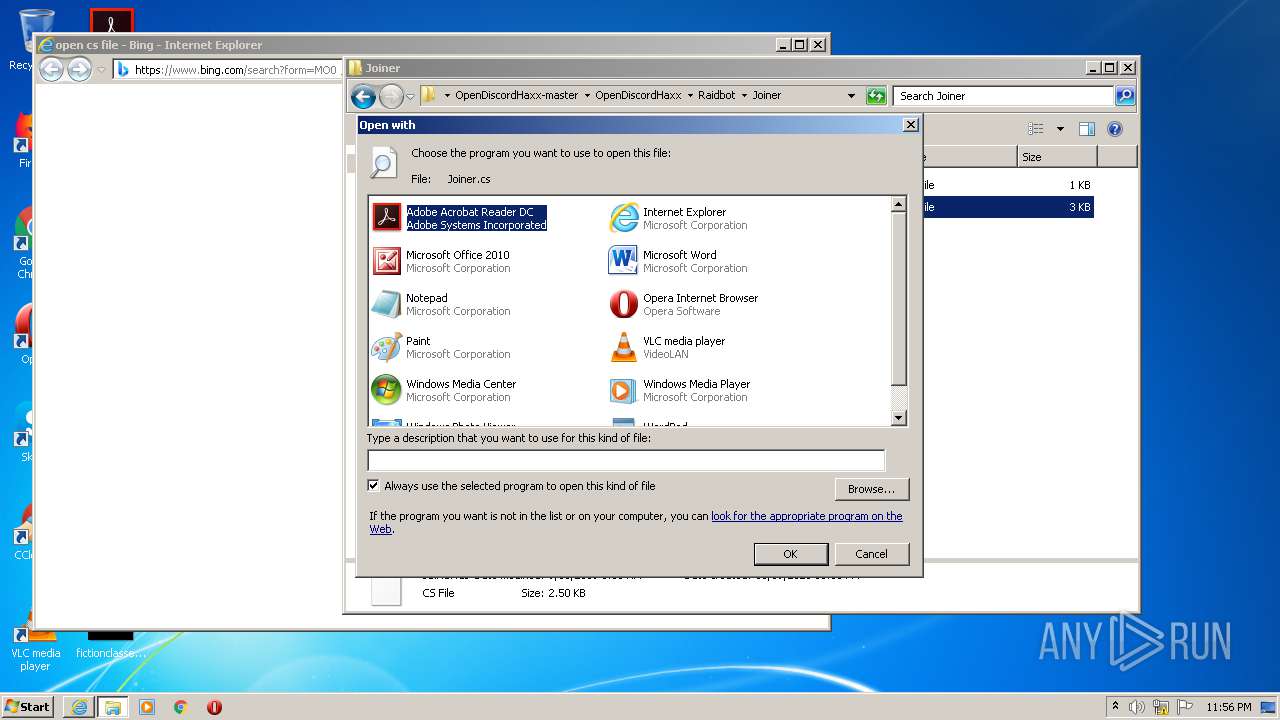
Modifies the open verb of a shell class
- rundll32.exe (PID: 4004)
Reads Internet Cache Settings
- iexplore.exe (PID: 2492)
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 2528)
- iexplore.exe (PID: 3568)
Changes internet zones settings
- iexplore.exe (PID: 2492)
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 3568)
Creates files in the user directory
- iexplore.exe (PID: 2492)
- iexplore.exe (PID: 2528)
Reads internet explorer settings
- iexplore.exe (PID: 2528)
Changes settings of System certificates
- iexplore.exe (PID: 2492)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2492)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:09:09 22:06:16 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | OpenDiscordHaxx-master/ |
Total processes
52
Monitored processes
12
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\OpenDiscordHaxx-master.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
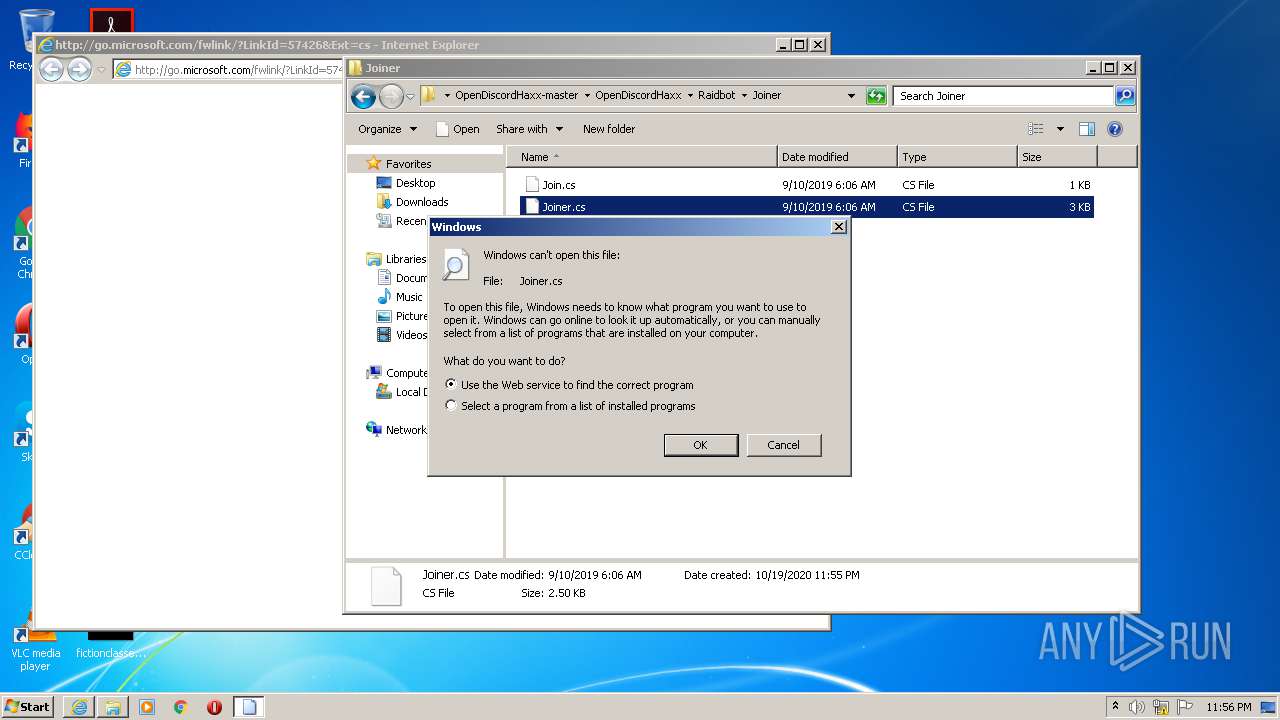
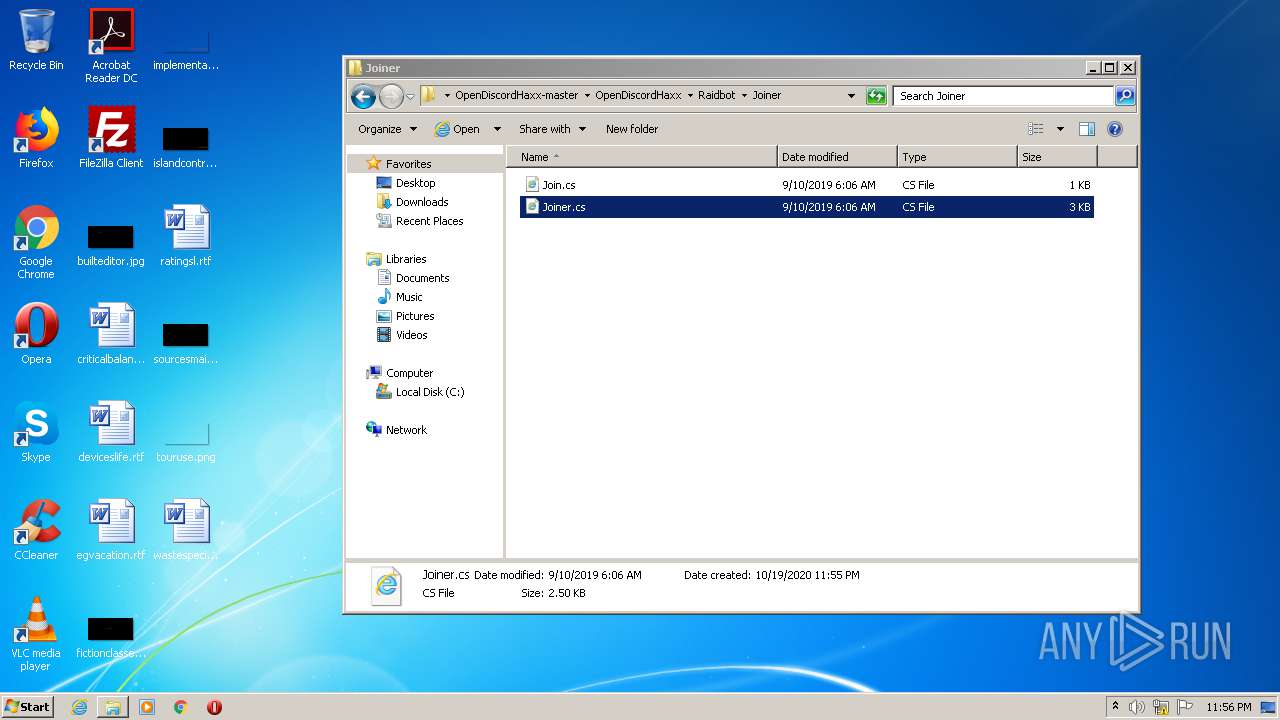
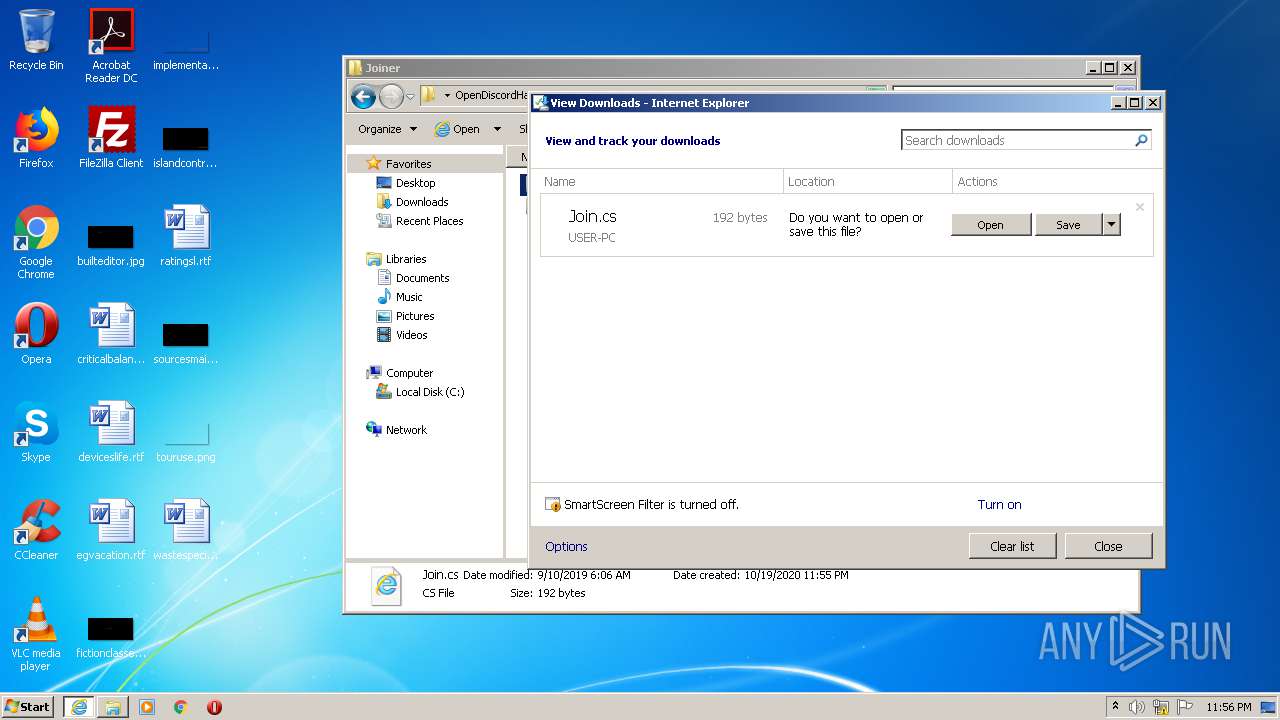
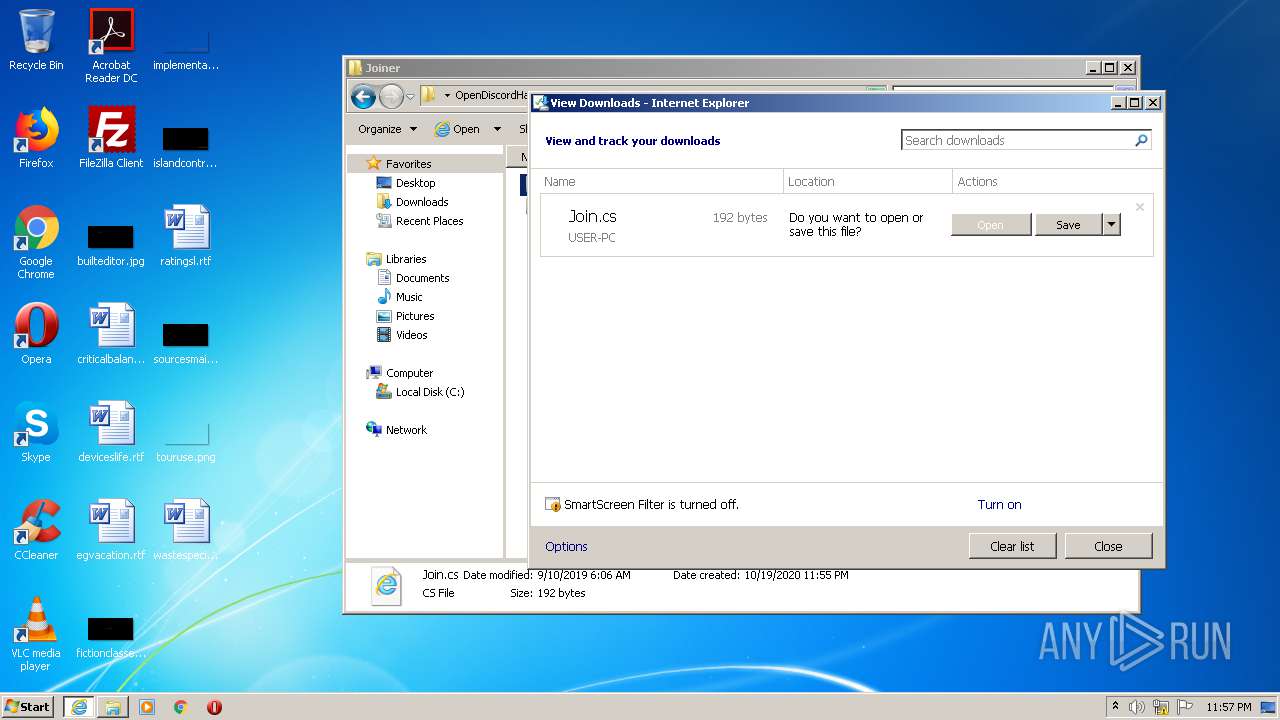
| 1136 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\OpenDiscordHaxx-master\OpenDiscordHaxx\Raidbot\Joiner\Join.cs | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1340 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\Desktop\OpenDiscordHaxx-master\OpenDiscordHaxx\Tools\Cleaner\Cleaner.cs | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1724 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2952 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2244 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2492 CREDAT:78849 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2492 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?LinkId=57426&Ext=cs | C:\Program Files\Internet Explorer\iexplore.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2528 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2492 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2552 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\Desktop\OpenDiscordHaxx-master\OpenDiscordHaxx\Raidbot\Joiner\Join.cs | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2724 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3568 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2952 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\Desktop\OpenDiscordHaxx-master\OpenDiscordHaxx\Raidbot\Joiner\Join.cs | C:\Program Files\Internet Explorer\iexplore.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
2 551
Read events
2 170
Write events
376
Delete events
5
Modification events
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\OpenDiscordHaxx-master.zip | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
0
Suspicious files
20
Text files
35
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.47677\OpenDiscordHaxx-master\OpenDiscordHaxx\BotList\Requests\BotRequest.cs | text | |
MD5:562EA8FBAB57D7C97A11D45C30557A49 | SHA256:2565F3BB91AAEE238B5AB75F5BCAE9E843AF796A21FECAF7A8CBEB4A3DFC6B3D | |||
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.47677\OpenDiscordHaxx-master\OpenDiscordHaxx\BotList\Requests\ModResp.cs | text | |
MD5:009C05797D8D66FB913CA5C60FB3D2B4 | SHA256:E3DCE319D5D9499EC1792098589BA179FDD3B99A4B18575479B5173108D1816D | |||
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.47677\OpenDiscordHaxx-master\OpenDiscordHaxx\BotList\Requests\List\BasicBotInfo.cs | text | |
MD5:4EDDD64857A221149254BC357E178568 | SHA256:91292C858D4CDBAAC38416B98EA291B83E7B34585C013DCE36F667763334106C | |||
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.47677\OpenDiscordHaxx-master\OpenDiscordHaxx\App.config | xml | |
MD5:335975BEBFD5E539FE2025FEAFF497E3 | SHA256:B0D8835D6D7686426FE217A3407B3CAC3AFFA286CA9F59763C5594DB76264F72 | |||
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.47677\OpenDiscordHaxx-master\OpenDiscordHaxx\BotList\Requests\List\List.cs | text | |
MD5:AF6FDA63B07F5A476ADC6B96E93274C4 | SHA256:4F7F451CD4F4141B08D604DC04A03D012F4EEB8A5970D8230E8203BACE06C6BA | |||
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.47677\OpenDiscordHaxx-master\OpenDiscordHaxx\BotList\Requests\Opcode.cs | text | |
MD5:71000A38F4CE8D2DF8F231C124FEC466 | SHA256:082848BE7E97B47DD396A63EE9ECC73D94C6D94E685D188DFBAE8DE2ECFFEF9B | |||
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.47677\OpenDiscordHaxx-master\OpenDiscordHaxx\BotList\Requests\Profile\BotInfo.cs | text | |
MD5:058039A8435BB87F17CA13D7F2713CC4 | SHA256:817F9744F0473532164417D437728422ACDB5D470DCA49C34B113C19D50B2B89 | |||
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.47677\OpenDiscordHaxx-master\OpenDiscordHaxx\Dashboard\Requests\Opcode.cs | — | |
MD5:— | SHA256:— | |||
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.47677\OpenDiscordHaxx-master\OpenDiscordHaxx\Dashboard\Requests\OverlookUpdate.cs | — | |
MD5:— | SHA256:— | |||
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa116.47677\OpenDiscordHaxx-master\OpenDiscordHaxx\Dashboard\Requests\Request.cs | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
17
DNS requests
7
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2528 | iexplore.exe | GET | 301 | 2.16.186.24:80 | http://shell.windows.com/fileassoc/fileassoc.asp?Ext=cs | unknown | — | — | whitelisted |
2528 | iexplore.exe | GET | 302 | 104.109.95.91:80 | http://go.microsoft.com/fwlink/?LinkId=57426&Ext=cs | NL | — | — | whitelisted |
2528 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2492 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
2528 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2528 | iexplore.exe | 104.109.95.91:80 | go.microsoft.com | Akamai International B.V. | NL | unknown |
2528 | iexplore.exe | 2.16.186.24:80 | shell.windows.com | Akamai International B.V. | — | whitelisted |
2492 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2528 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2492 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2528 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2492 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
shell.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2528 | iexplore.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
2528 | iexplore.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |