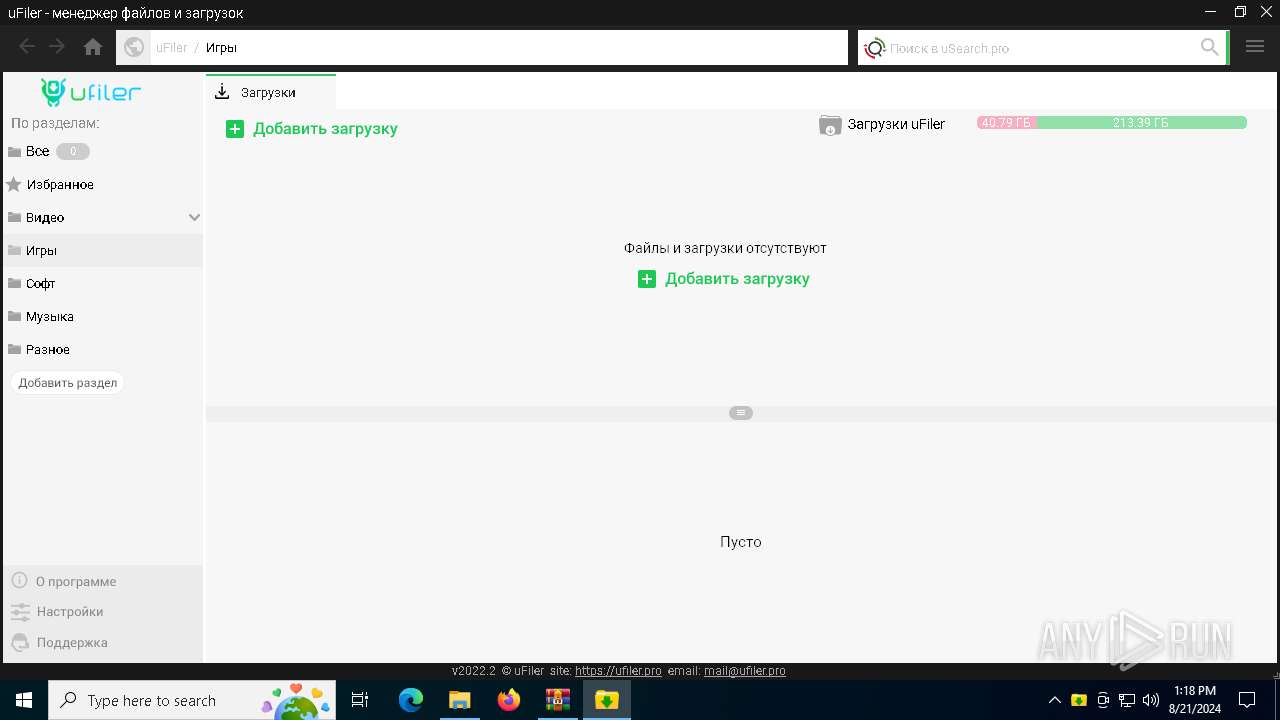
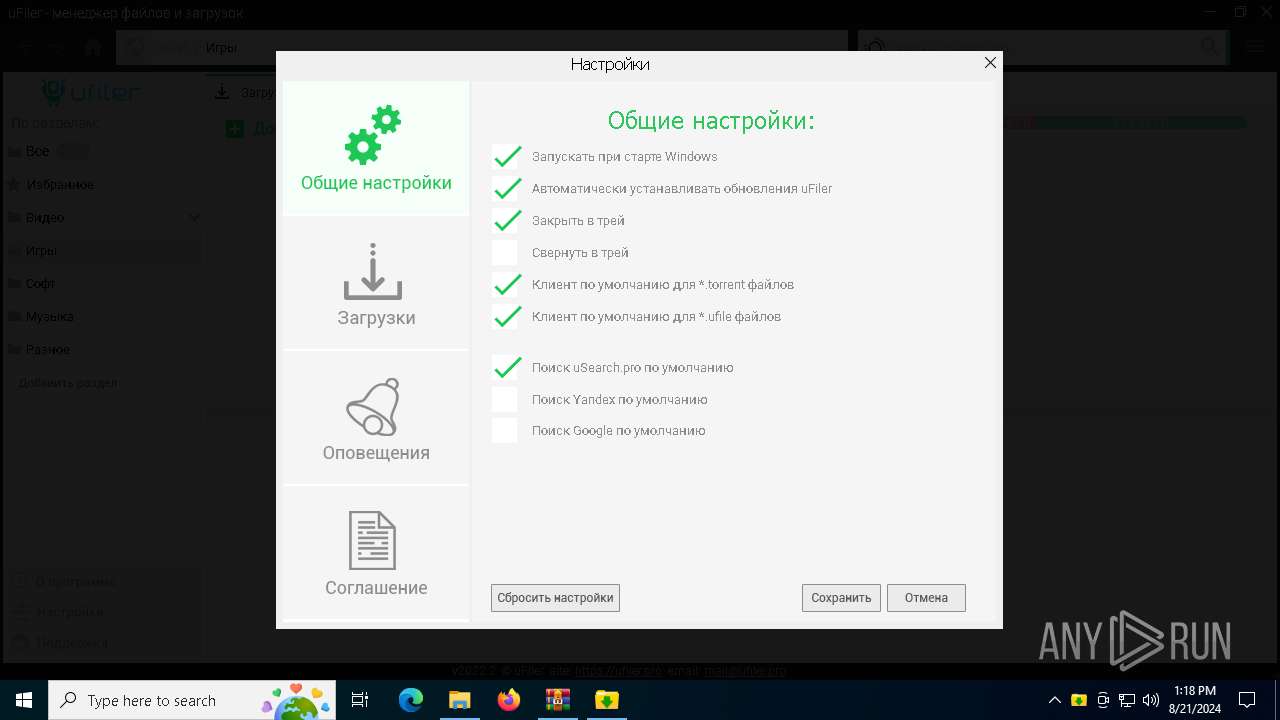
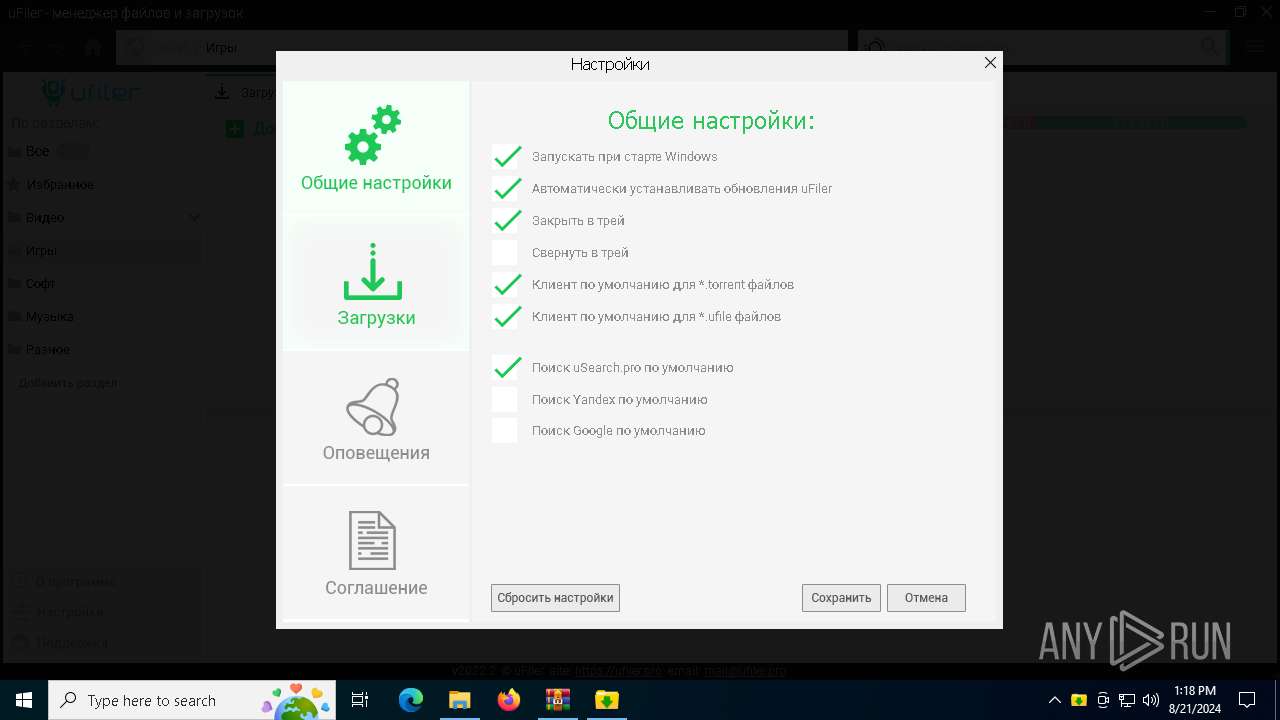
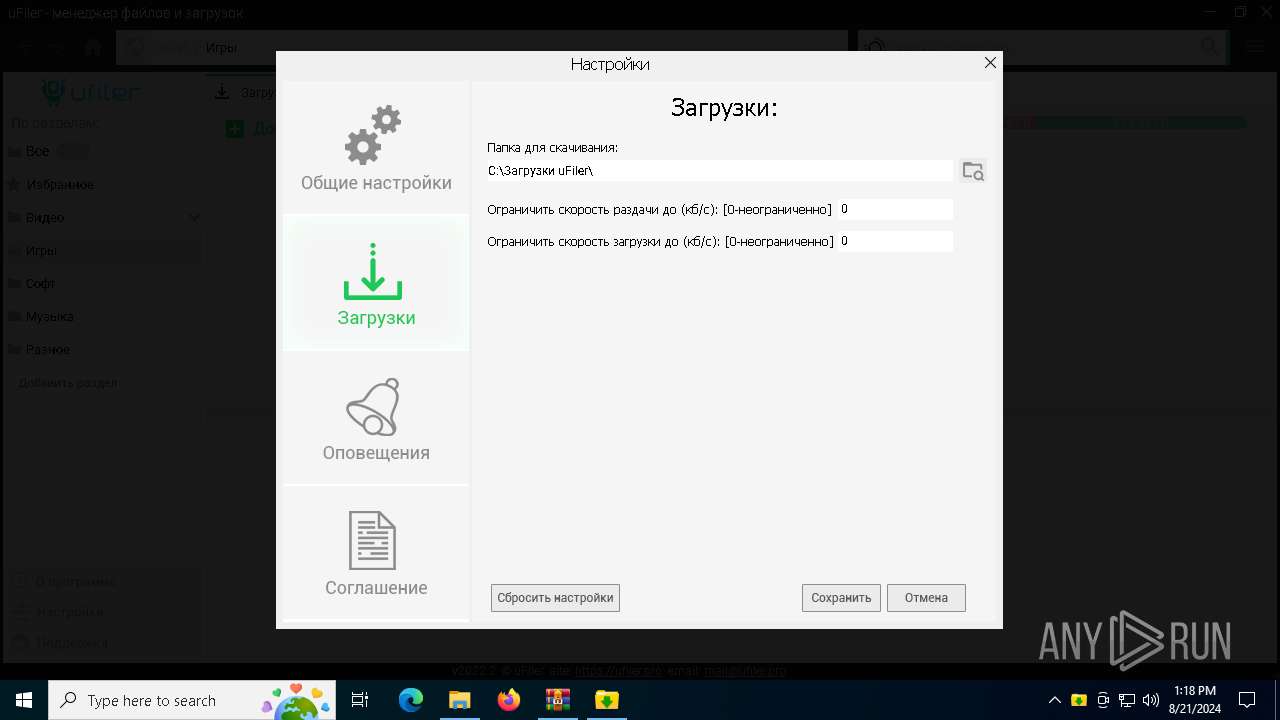
| File name: | a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.7z |
| Full analysis: | https://app.any.run/tasks/cd575afb-070c-4663-9b01-7ed4175c46bb |
| Verdict: | Malicious activity |
| Analysis date: | August 21, 2024, 13:16:56 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | A3957A44269CD7E1724EFA5DFD3DE0A6 |
| SHA1: | 59A6C0E2279A3A494DC7483E77EFECDFFFC5C139 |
| SHA256: | 39F108A275808876BEF11682DB654AE468B875466D74A21B025F75CFD0294E06 |
| SSDEEP: | 98304:4nl/RBDGp62oL2xIQ6+fFVteC7aiMcuEf9tUnXOqTWbTygKV7jM1FmxN/bk8Yatg:plS9WQBYzS1X7fAEq |
MALICIOUS
Changes the autorun value in the registry
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 6300)
SUSPICIOUS
Application launched itself
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 1608)
Creates a software uninstall entry
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 1608)
The process verifies whether the antivirus software is installed
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 6300)
Reads security settings of Internet Explorer
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 6552)
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 1608)
Reads the date of Windows installation
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 6552)
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 1608)
Potential Corporate Privacy Violation
- uFiler.exe (PID: 2032)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6752)
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 6300)
Executable content was dropped or overwritten
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 6300)
Starts itself from another location
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 6552)
INFO
Manual execution by a user
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 1608)
Creates files in the program directory
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 1608)
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 6300)
- uFiler.exe (PID: 2032)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6752)
Process checks computer location settings
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 6552)
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 1608)
Checks supported languages
- uFiler.exe (PID: 2032)
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 1608)
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 6552)
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 6300)
UPX packer has been detected
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 6300)
Reads the computer name
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 1608)
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 6300)
- a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe (PID: 6552)
- uFiler.exe (PID: 2032)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 5468)
Reads the machine GUID from the registry
- uFiler.exe (PID: 2032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
143
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1608 | "C:\Users\admin\Desktop\a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe" | C:\Users\admin\Desktop\a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe | — | explorer.exe | |||||||||||
User: admin Company: uFiler.pro Integrity Level: MEDIUM Description: uFiler Exit code: 0 Version: 2022.2.0.0 Modules
| |||||||||||||||
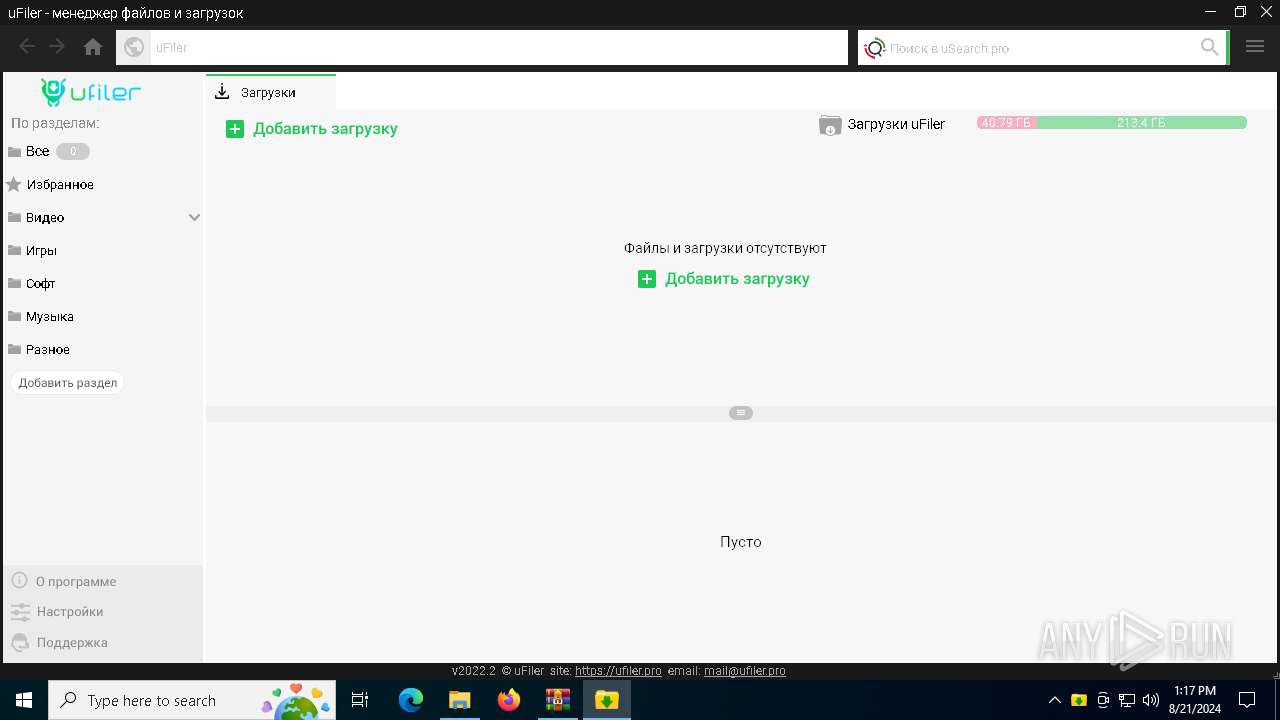
| 2032 | "C:\Program Files (x86)\uFiler\uFiler.exe" | C:\Program Files (x86)\uFiler\uFiler.exe | a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe | ||||||||||||
User: admin Company: uFiler.pro Integrity Level: MEDIUM Description: uFiler Version: 2022.2.0.0 Modules
| |||||||||||||||
| 2636 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5468 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6300 | "C:\Users\admin\Desktop\a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe" -a -pipe | C:\Users\admin\Desktop\a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe | a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe | ||||||||||||
User: admin Company: uFiler.pro Integrity Level: HIGH Description: uFiler Version: 2022.2.0.0 Modules
| |||||||||||||||
| 6552 | "C:\Users\admin\Desktop\a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe" | C:\Users\admin\Desktop\a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe | — | a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe | |||||||||||
User: admin Company: uFiler.pro Integrity Level: MEDIUM Description: uFiler Exit code: 0 Version: 2022.2.0.0 Modules
| |||||||||||||||
| 6752 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
10 082
Read events
10 033
Write events
48
Delete events
1
Modification events
| (PID) Process: | (6752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.7z | |||
| (PID) Process: | (6752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (6752) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
6
Suspicious files
2
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1608 | a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe | C:\Users\admin\Desktop\uFiler.lnk | lnk | |
MD5:8F035729225E0CFE9537071BB686B72F | SHA256:48D23BAFDEA06D0381F31EF0450CBCDAC1905BD94E8122A1DE74438C1A75D0C4 | |||
| 6300 | a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe | C:\Program Files (x86)\uFiler\uFiler.exe | executable | |
MD5:9595E49300C884EA972200F03D7551AA | SHA256:A4C8B95638E736BFD4CABDF43121EBB65229C3754A2BB35FFE9A81A8091C2D16 | |||
| 6300 | a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe | C:\Program Files (x86)\uFiler\modules\ubtorrent\ubtorrent.dll | executable | |
MD5:39FD9F3BA43E3E1896467C690053523A | SHA256:C7B7AF783ECD72104159CCA39FA347F1E110D512E8BD5863D130DA9DE8594D7C | |||
| 2032 | uFiler.exe | C:\ProgramData\uFiler\data\uFiler.db | binary | |
MD5:B4DC16C81C773E52271B8289C58BD63B | SHA256:392A0A67888A7E66DEF6AC168A0BB2E89E5F734BB92E51C67BB2640C8AA383B2 | |||
| 6752 | WinRAR.exe | C:\Users\admin\Desktop\a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16 | executable | |
MD5:9595E49300C884EA972200F03D7551AA | SHA256:A4C8B95638E736BFD4CABDF43121EBB65229C3754A2BB35FFE9A81A8091C2D16 | |||
| 2032 | uFiler.exe | C:\ProgramData\uFiler\data\uFiler.db-journal | gmc | |
MD5:E0D907CAAAC4CC9069BB4EA392553C8F | SHA256:E55AD5CAD255118DEC027DBB07FC88FFC2388E5951E1F695BC8DF378890AEB7E | |||
| 6300 | a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe | C:\ProgramData\uFiler\data\uFiler.exe | executable | |
MD5:9595E49300C884EA972200F03D7551AA | SHA256:A4C8B95638E736BFD4CABDF43121EBB65229C3754A2BB35FFE9A81A8091C2D16 | |||
| 6300 | a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe | C:\Program Files (x86)\uFiler\modules\ssleay32.dll | executable | |
MD5:5D7476F34764F278852406CDB3BEACB6 | SHA256:DF74479FC4CFF960FAAB94C481DB6B962844E1396716FF5E84FD97EB0FCFA661 | |||
| 6300 | a4c8b95638e736bfd4cabdf43121ebb65229c3754a2bb35ffe9a81a8091c2d16.exe | C:\Program Files (x86)\uFiler\modules\libeay32.dll | executable | |
MD5:900DAFE19A17F2E21729BA1AD2A7DDF2 | SHA256:E970087342A29079BFF6B8B37FE58EBF579FD9BF8B5C0815BDC4231B73F9529F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
127
DNS requests
18
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
236 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7152 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6544 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6716 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5116 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3236 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3236 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
236 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
236 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7152 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2032 | uFiler.exe | Potential Corporate Privacy Violation | ET P2P BitTorrent DHT ping request |