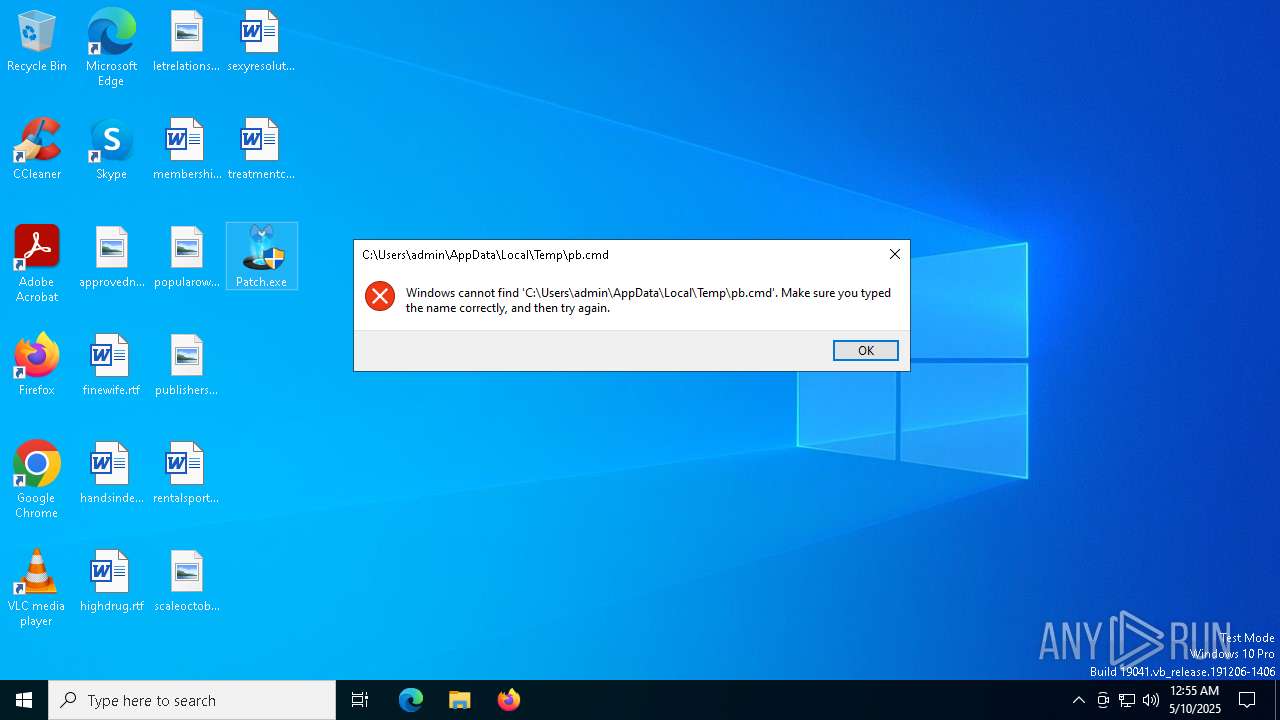
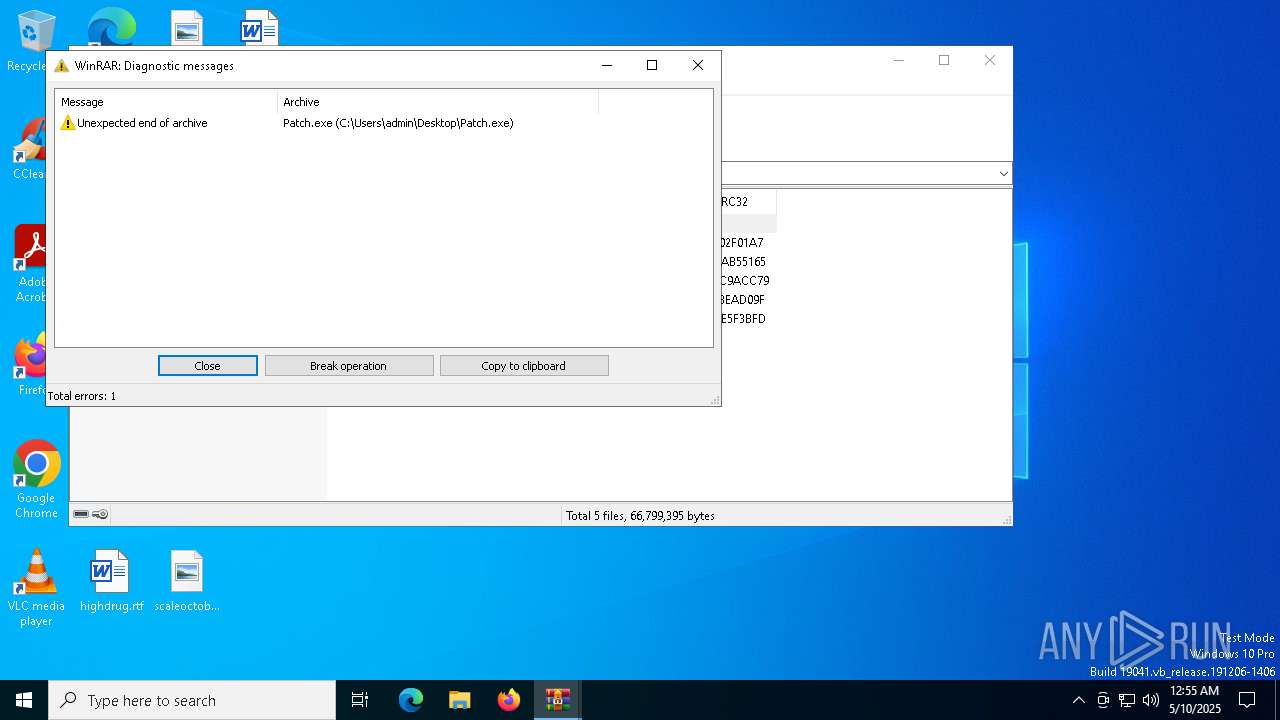
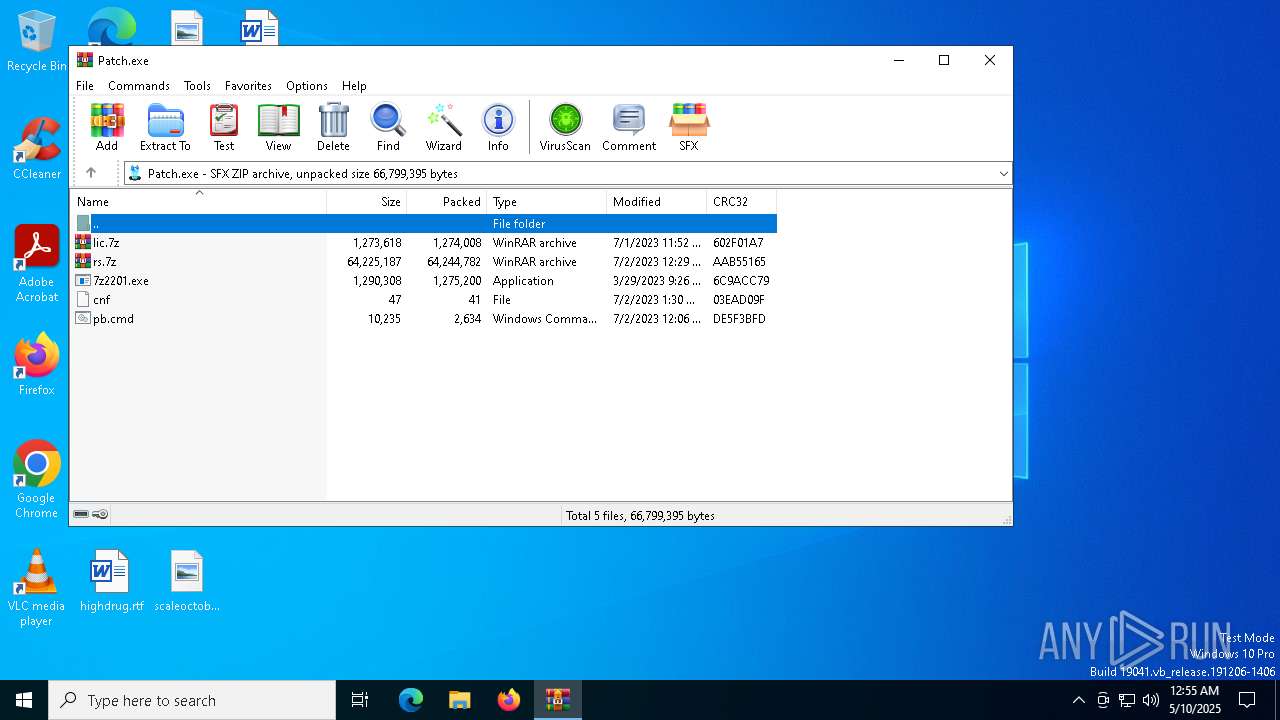
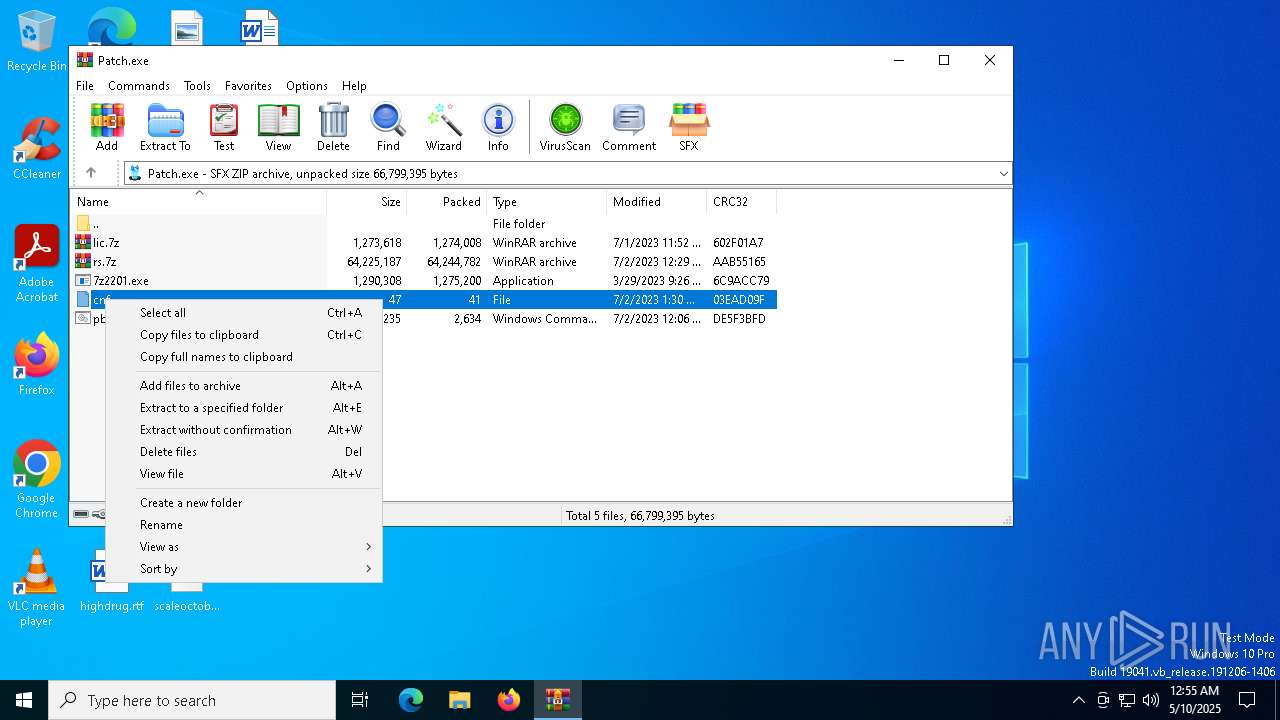
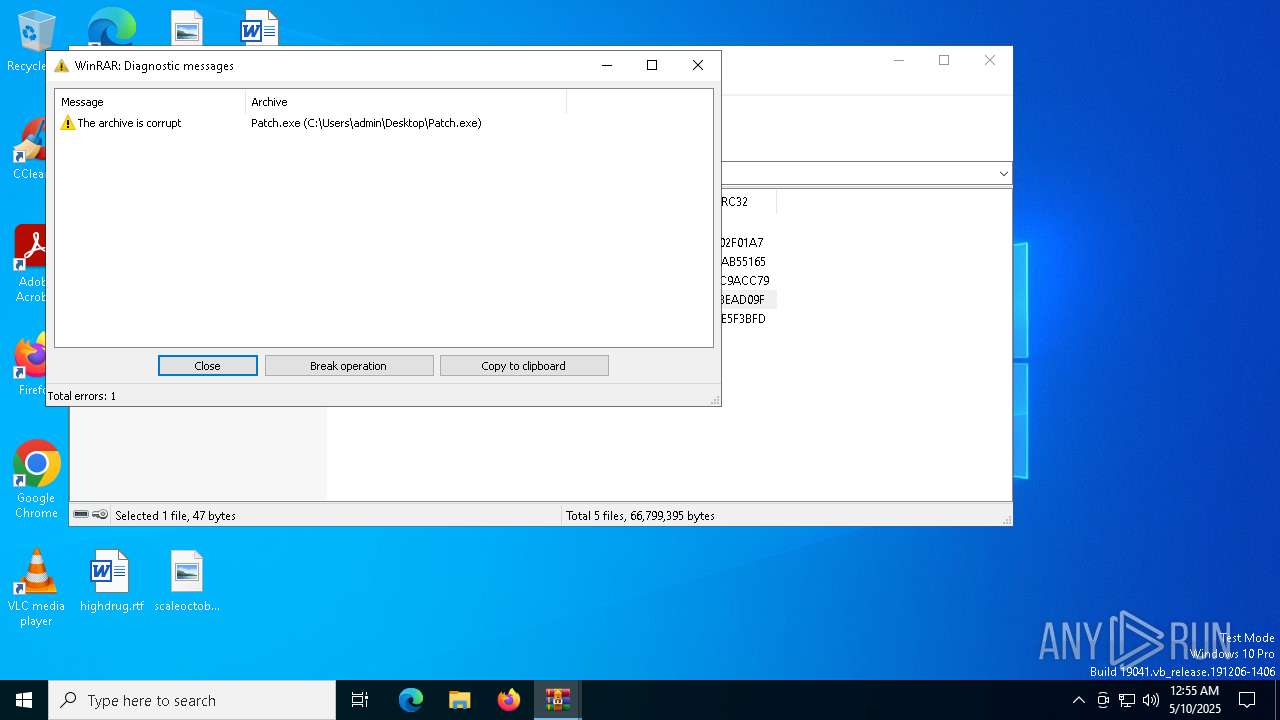
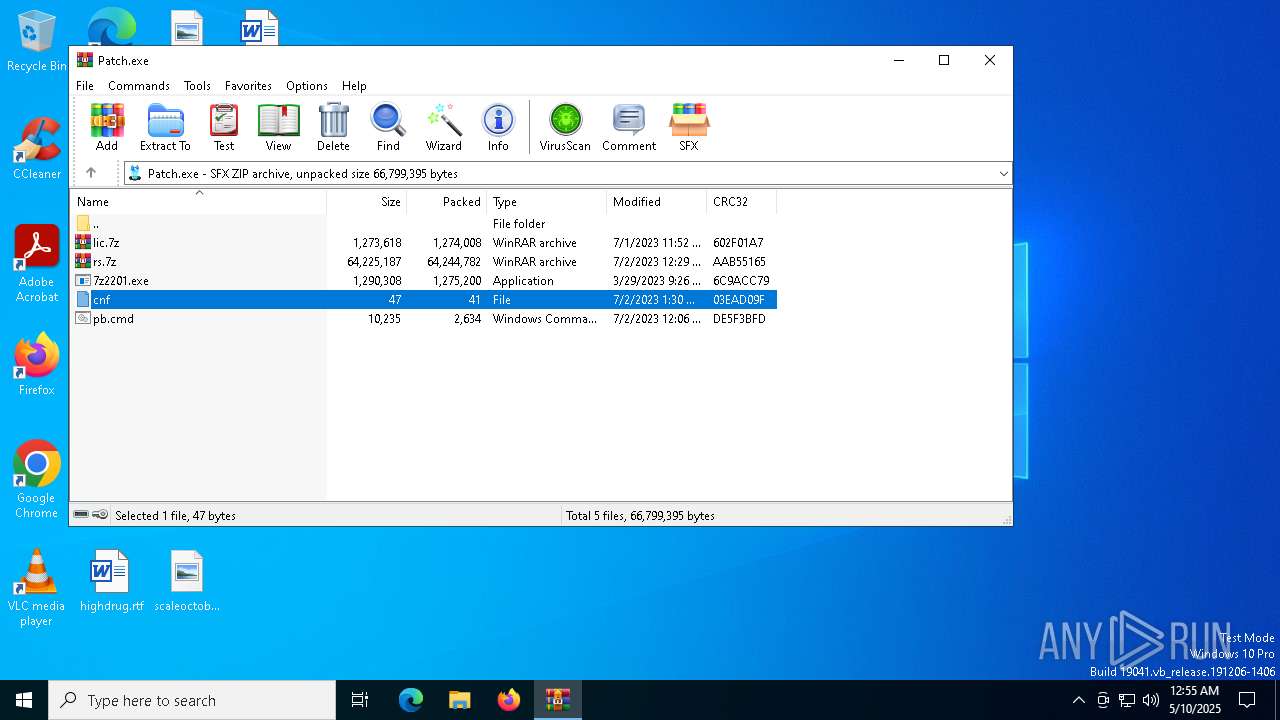
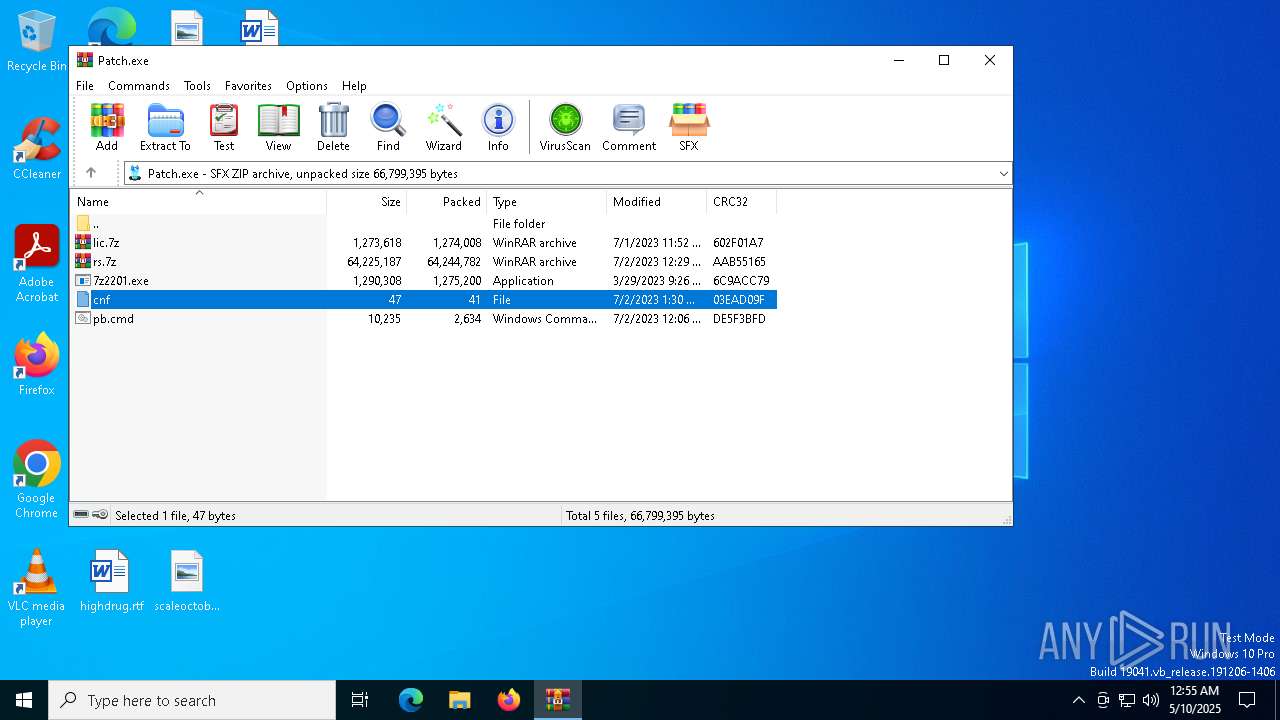
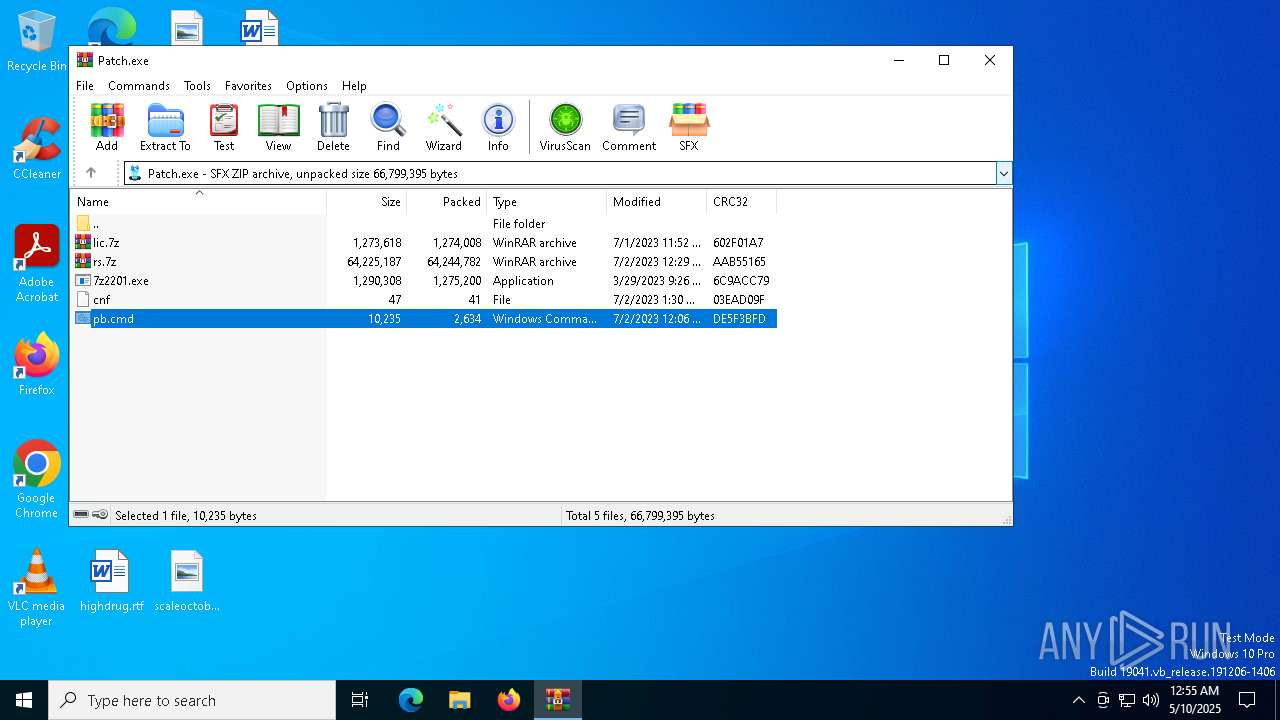
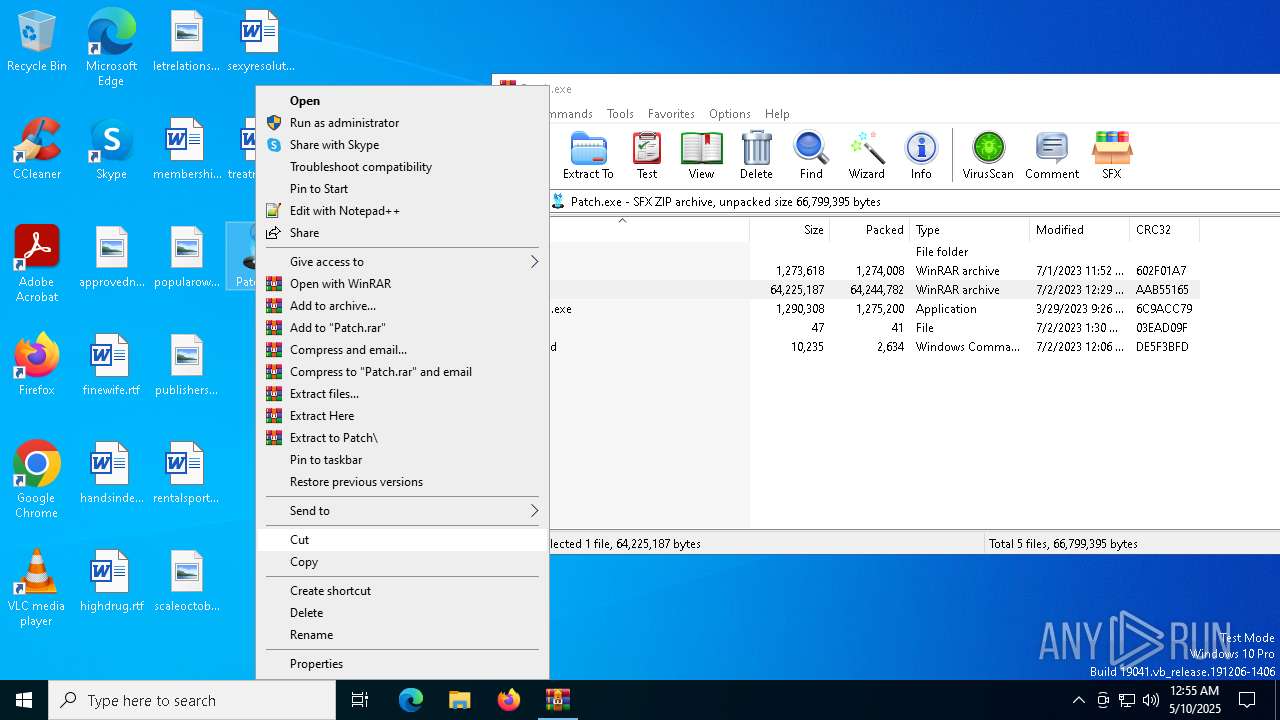
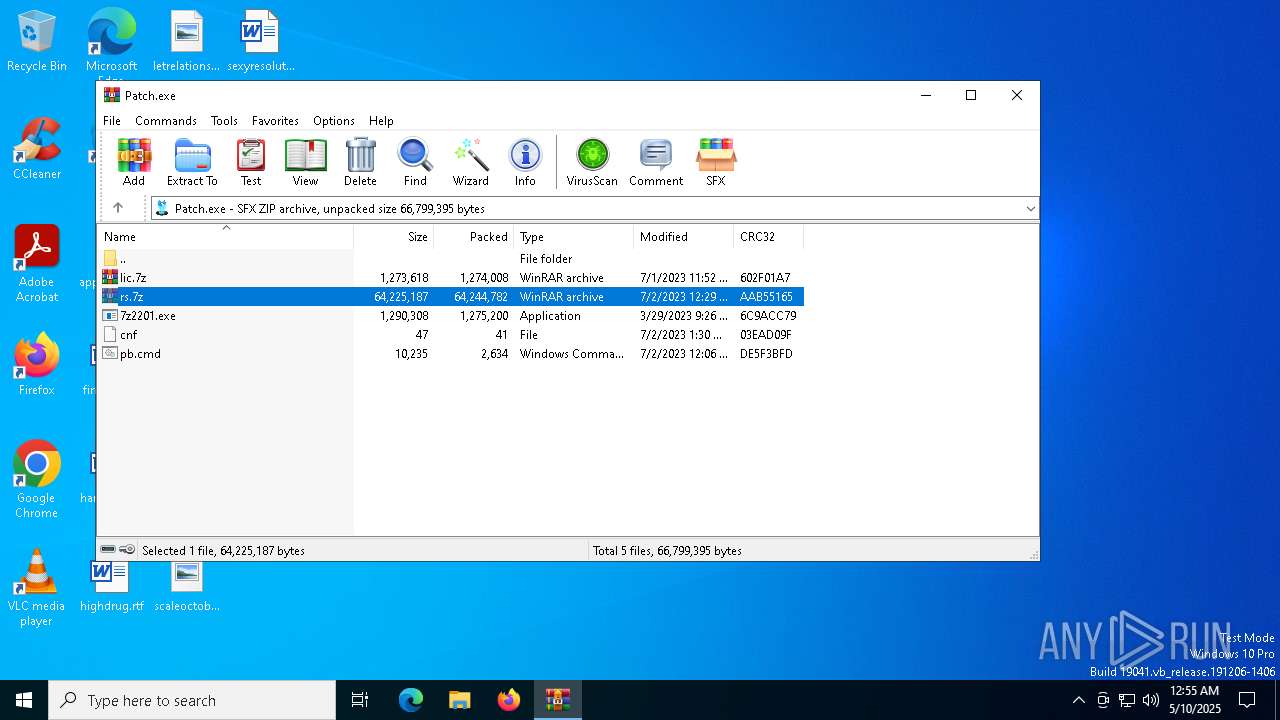
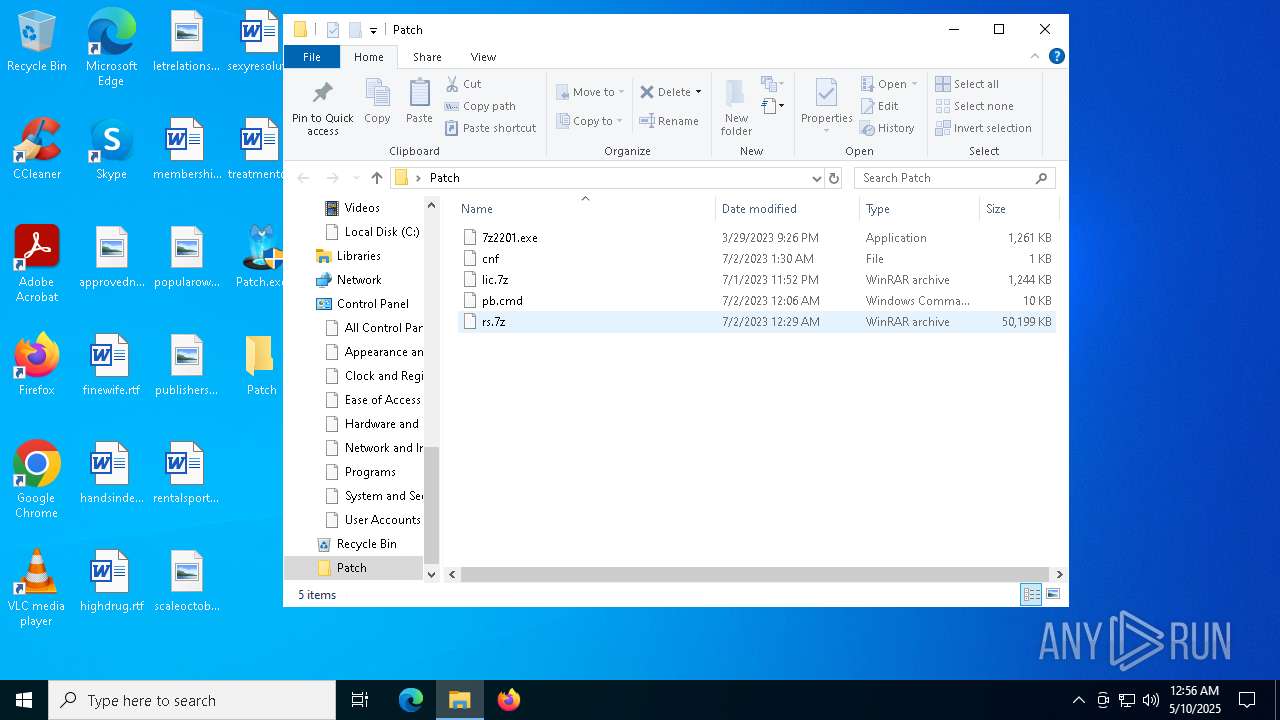
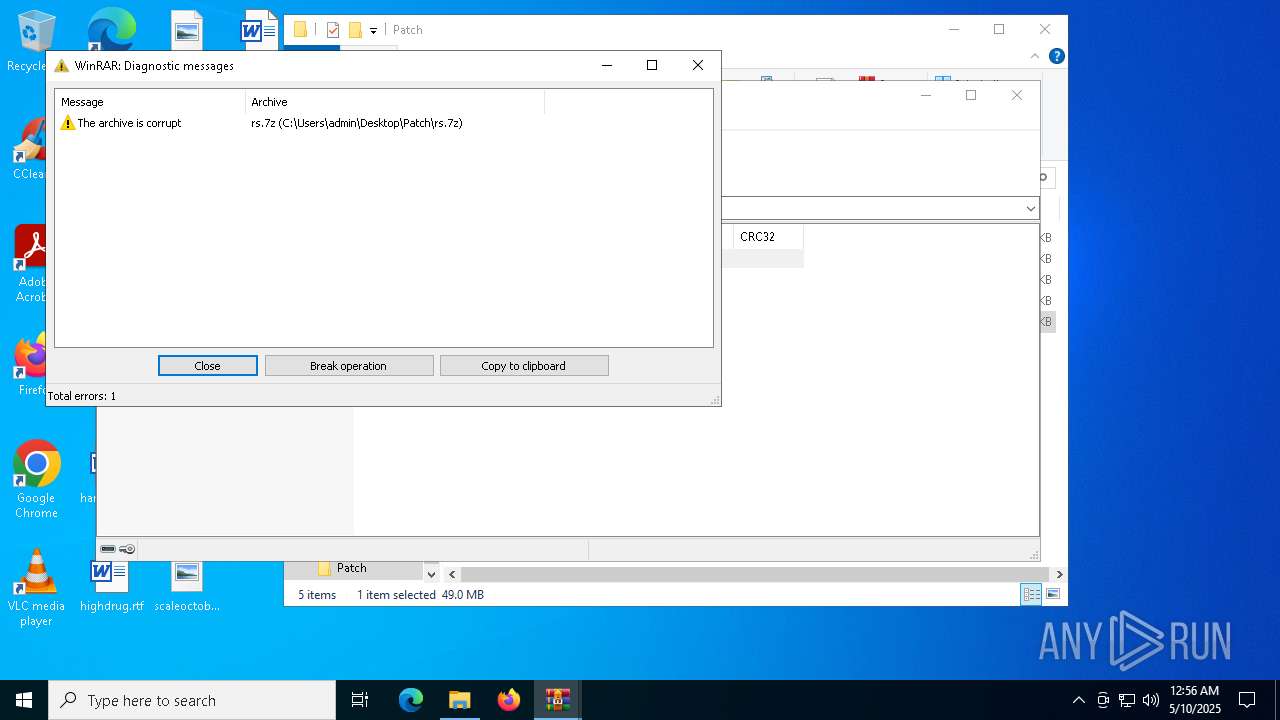
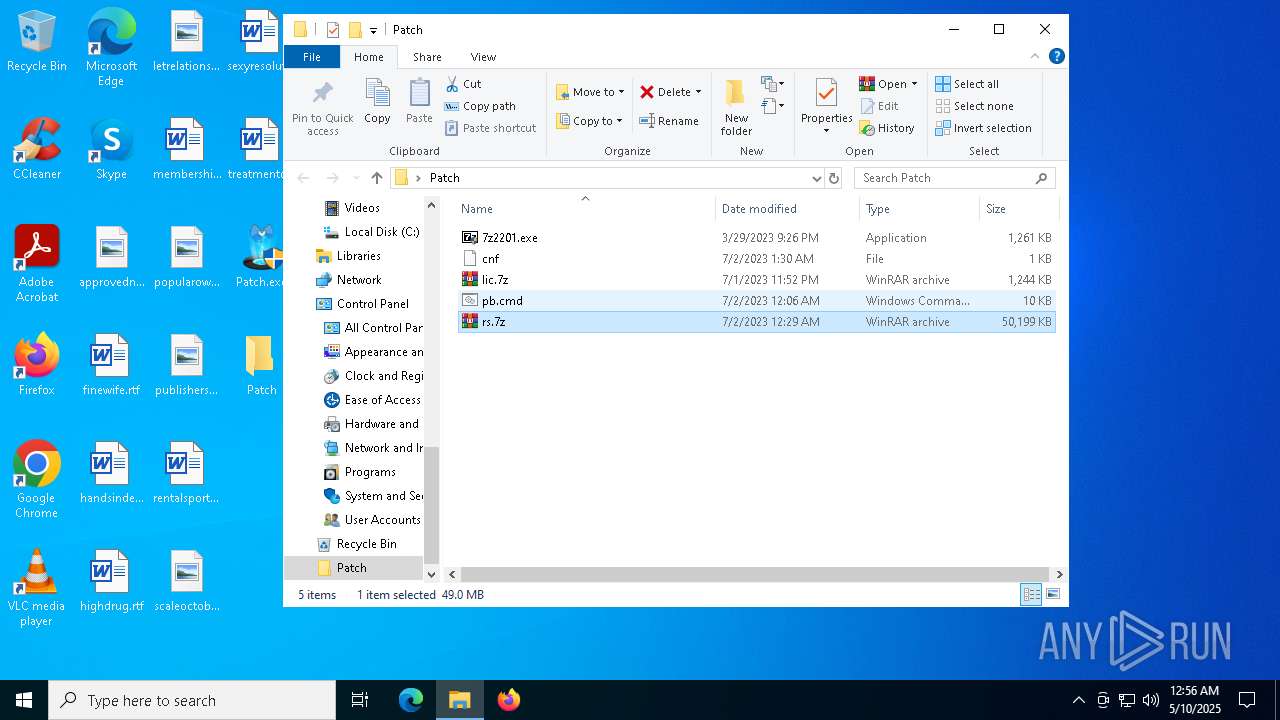
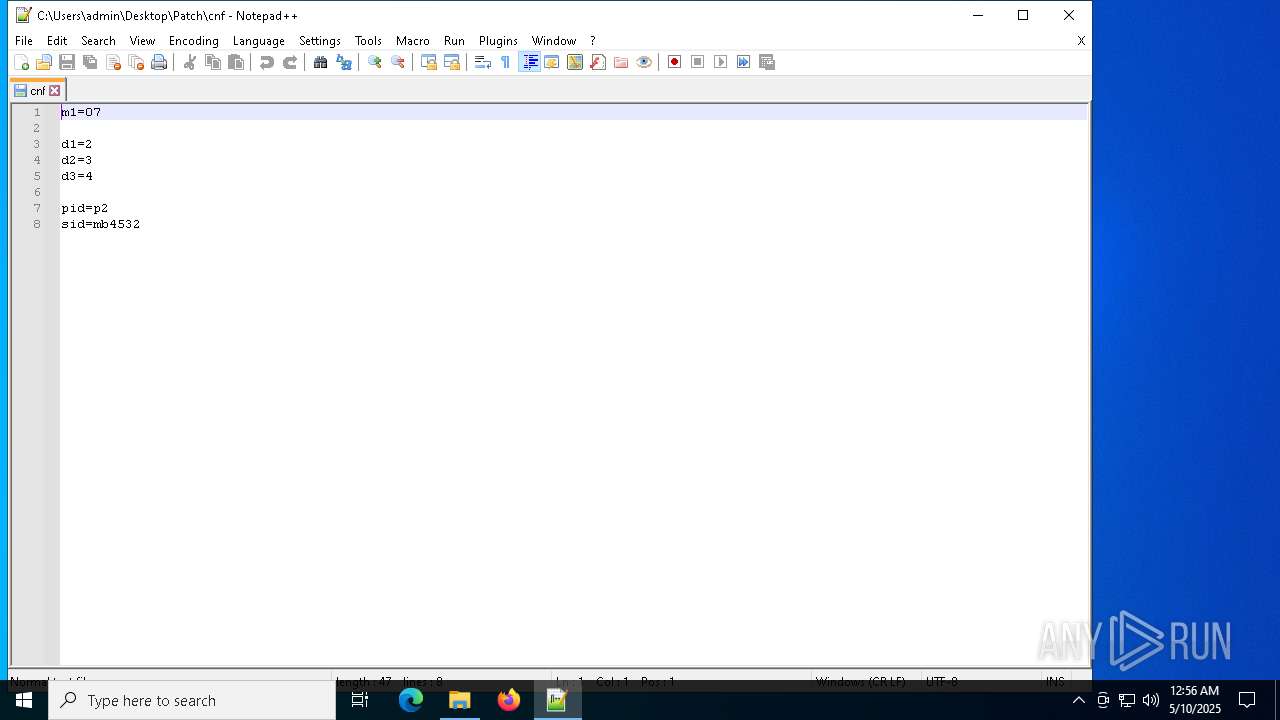
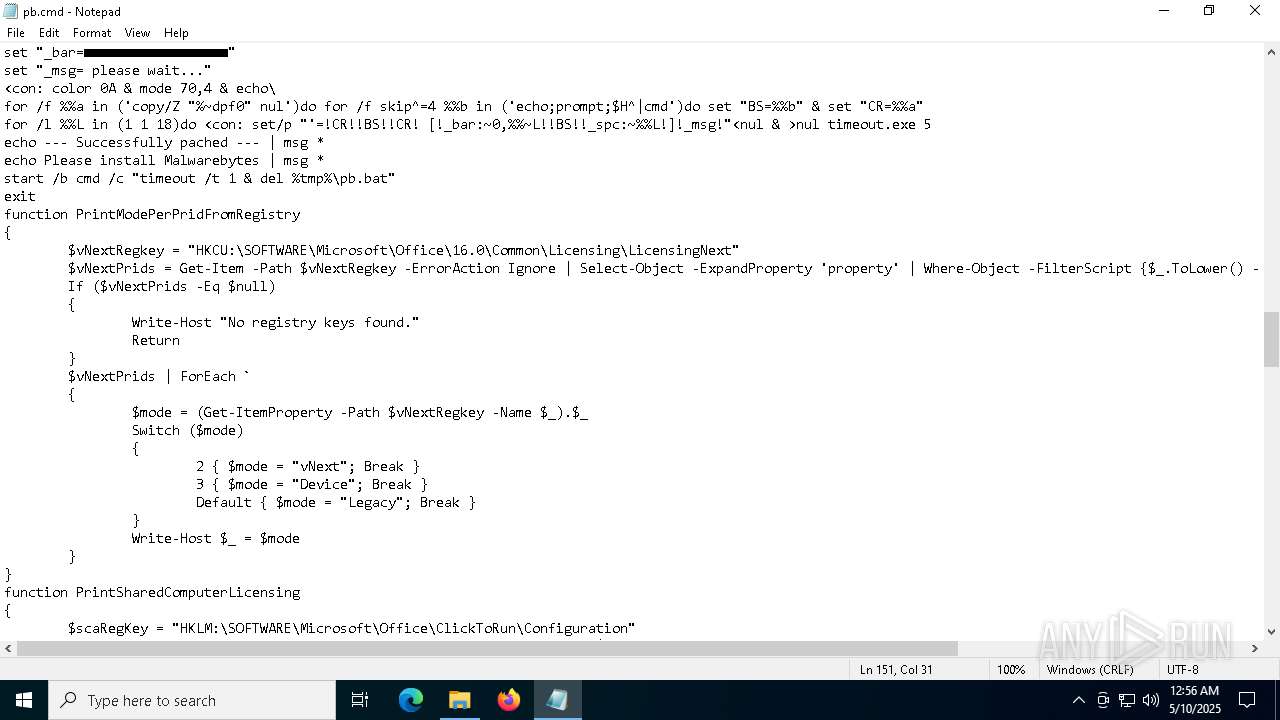
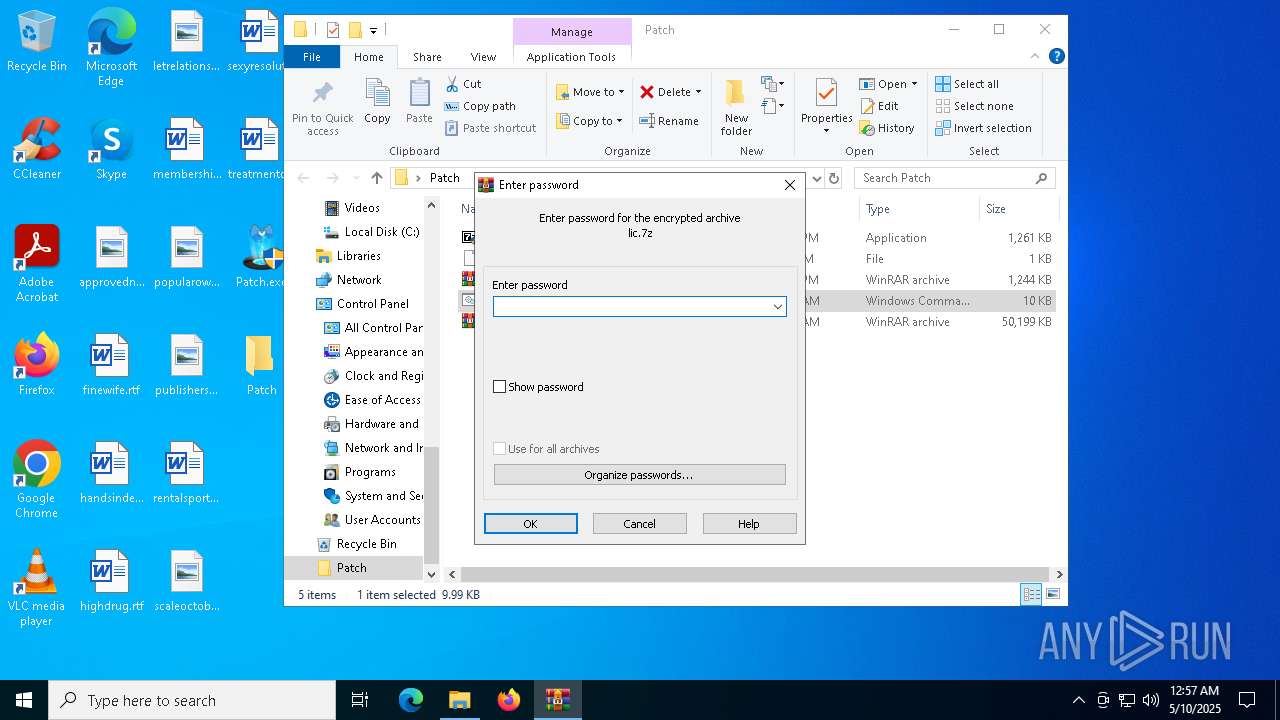
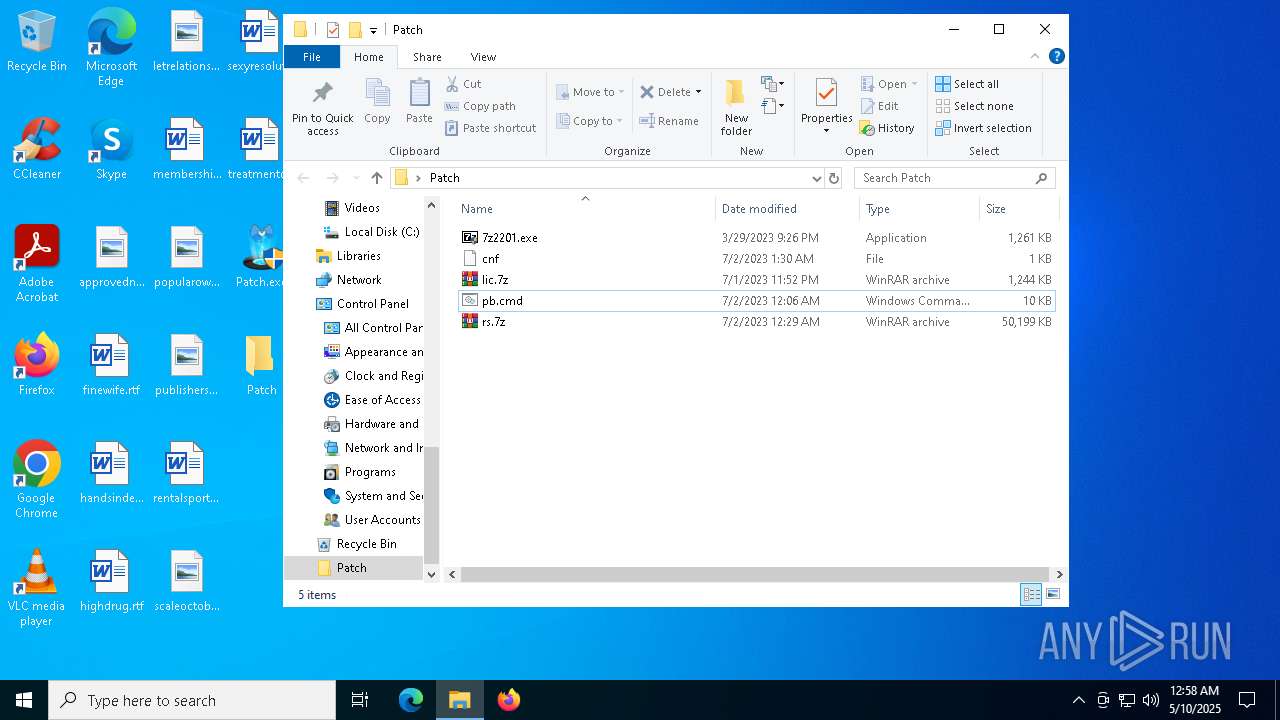
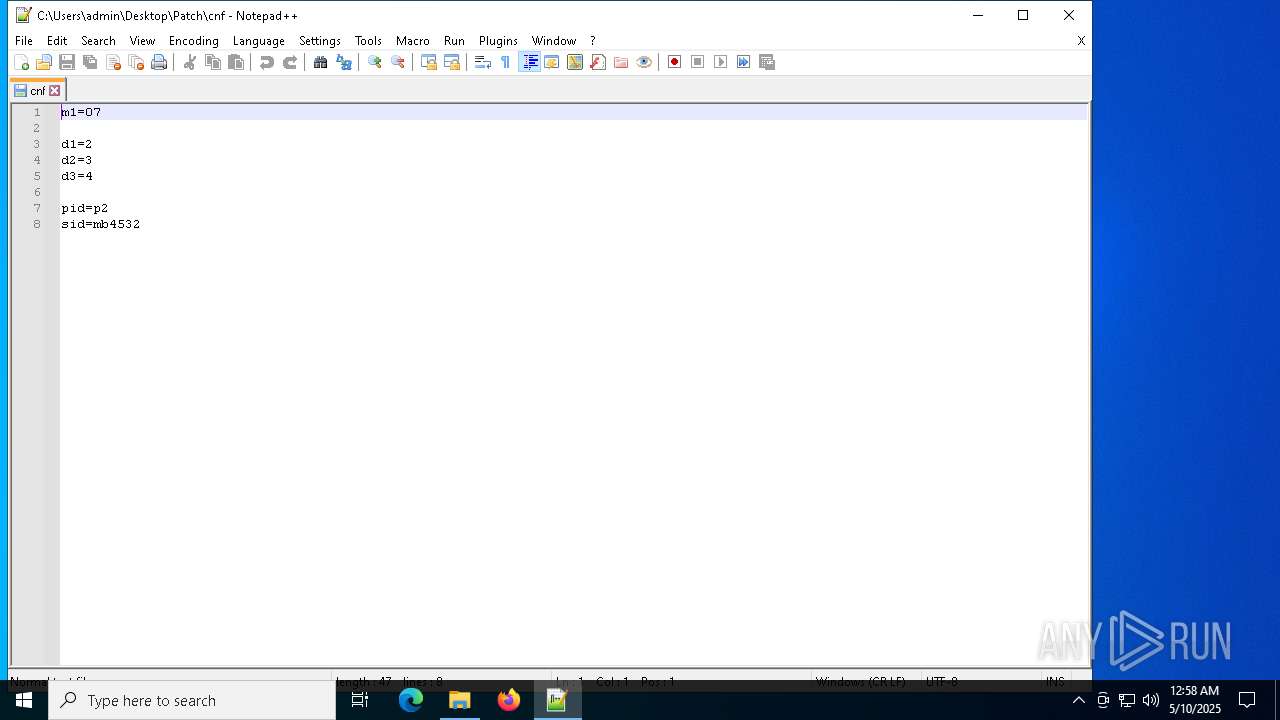
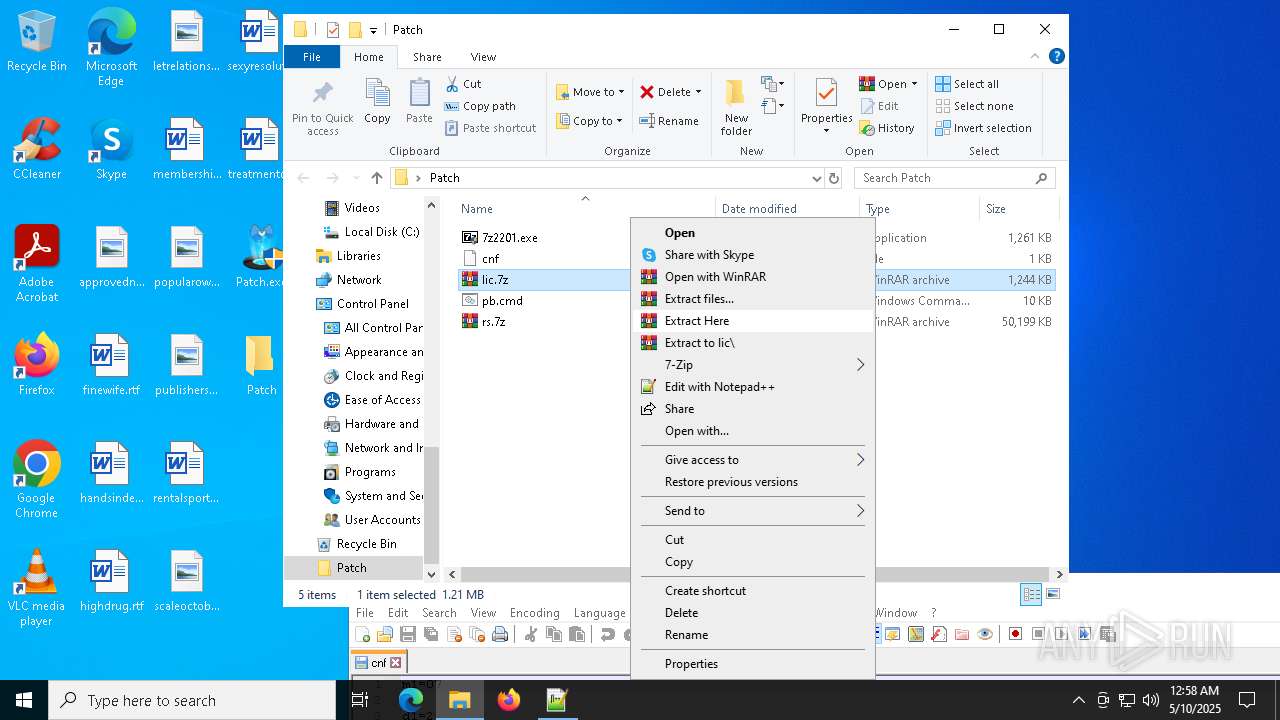
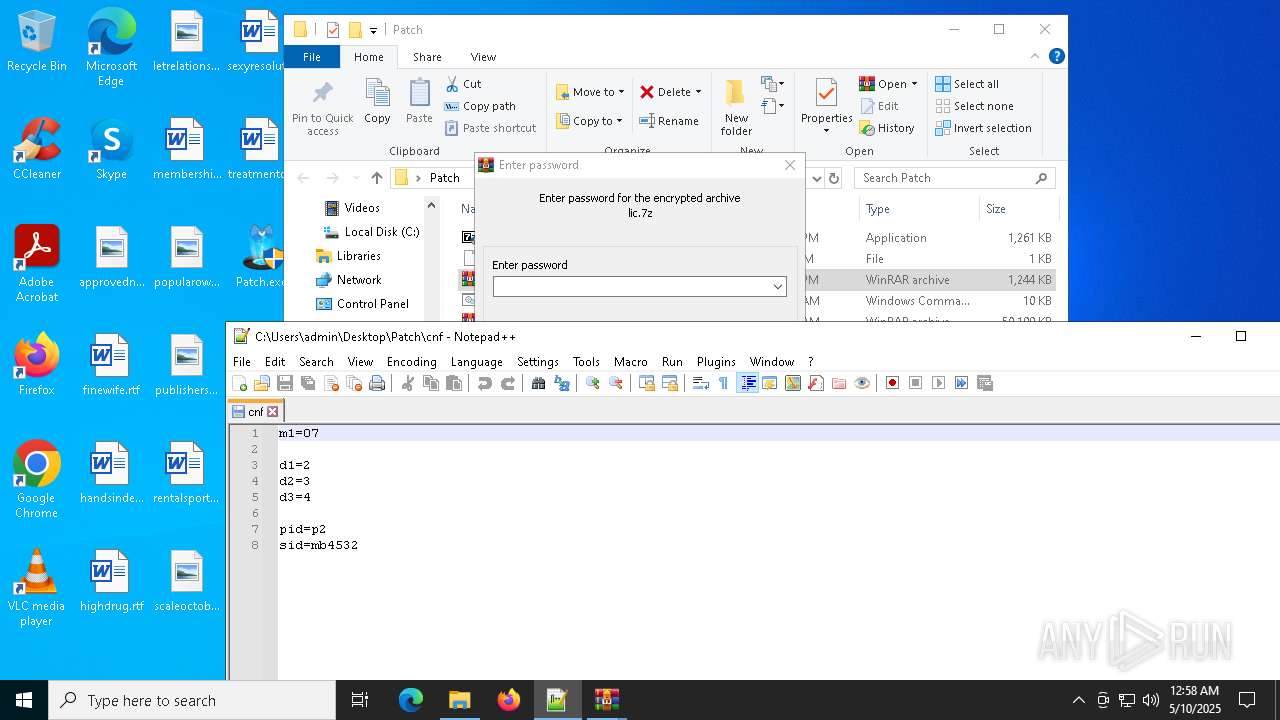
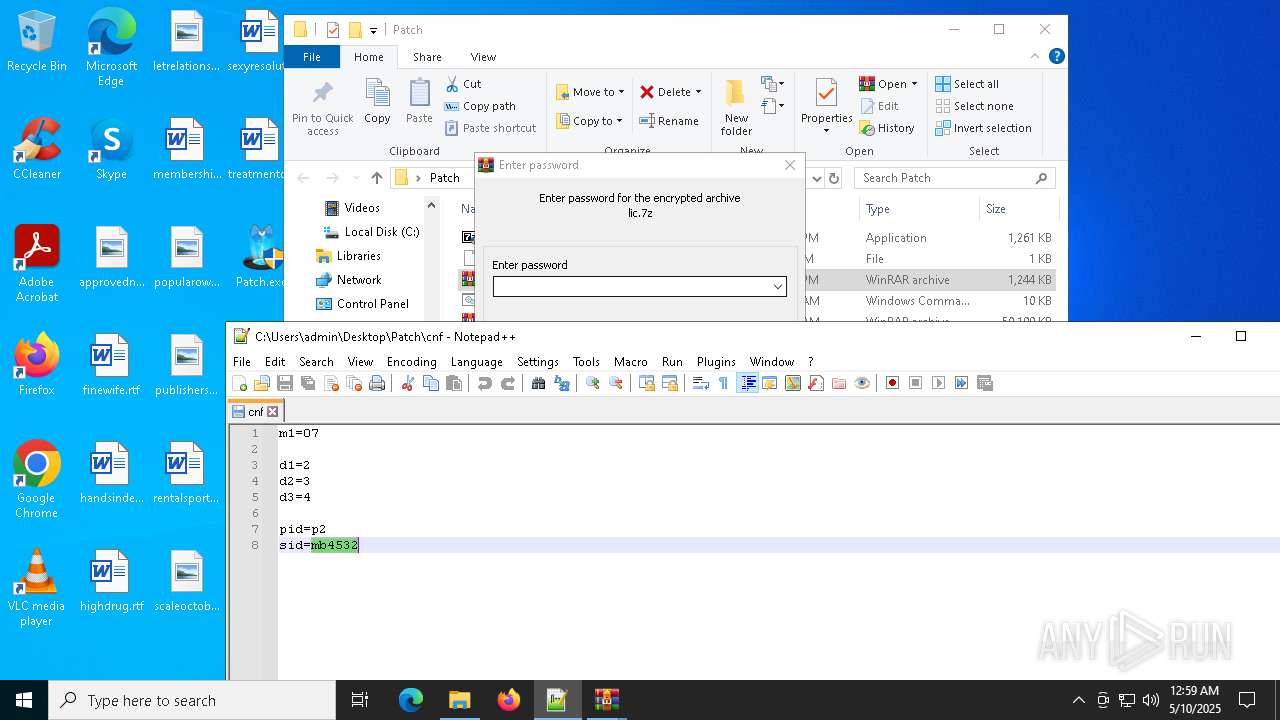
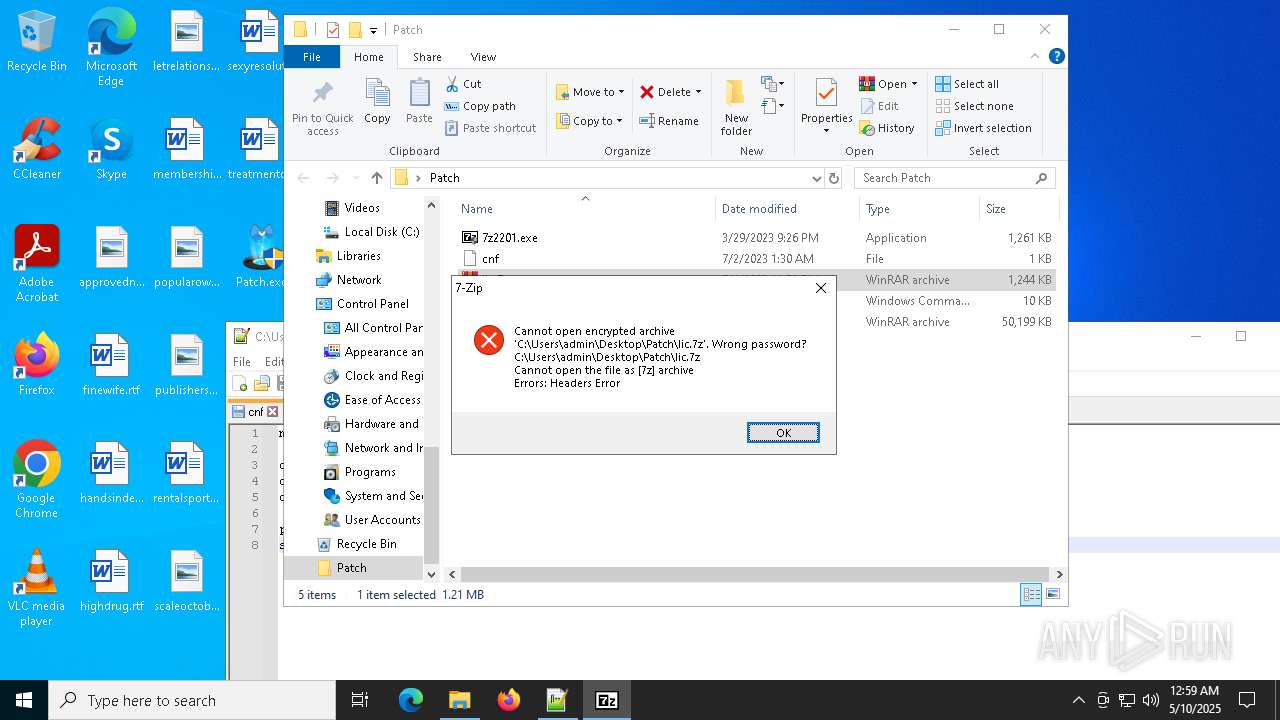
| File name: | Patch.exe |
| Full analysis: | https://app.any.run/tasks/184cb760-e0fe-4845-9787-c4f05f4f1088 |
| Verdict: | Malicious activity |
| Analysis date: | May 10, 2025, 00:54:40 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 10 sections |
| MD5: | 42B302C83A4919AA00C8DDFF40FB7882 |
| SHA1: | 611091779BD7619FC6036F32C440463BB5AB2553 |
| SHA256: | 39EF78D87E3826CB0F772837CF6B9F69E9983E282362434A18615E7977E6AA7E |
| SSDEEP: | 786432:TbHf+UivzrB67McAQ/XEimYXRcWLUxtVA:Tb/+UiJ6DR/XELeRcNxtu |
MALICIOUS
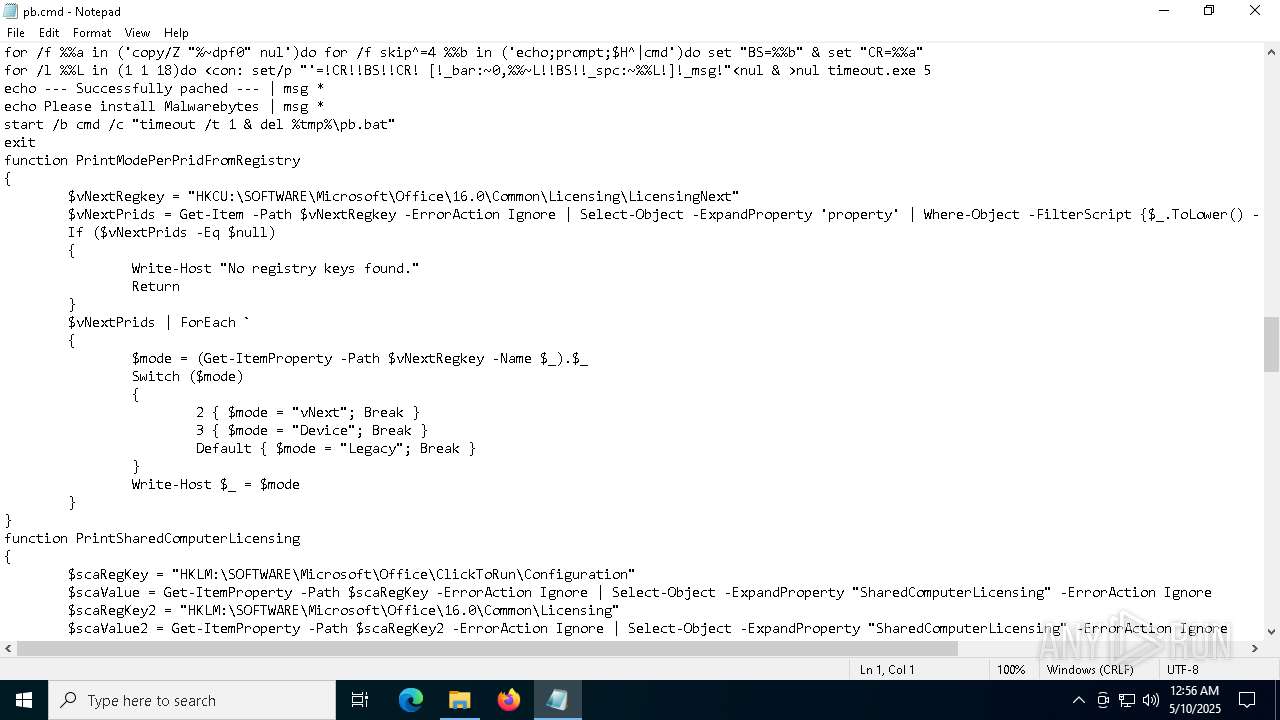
No malicious indicators.SUSPICIOUS
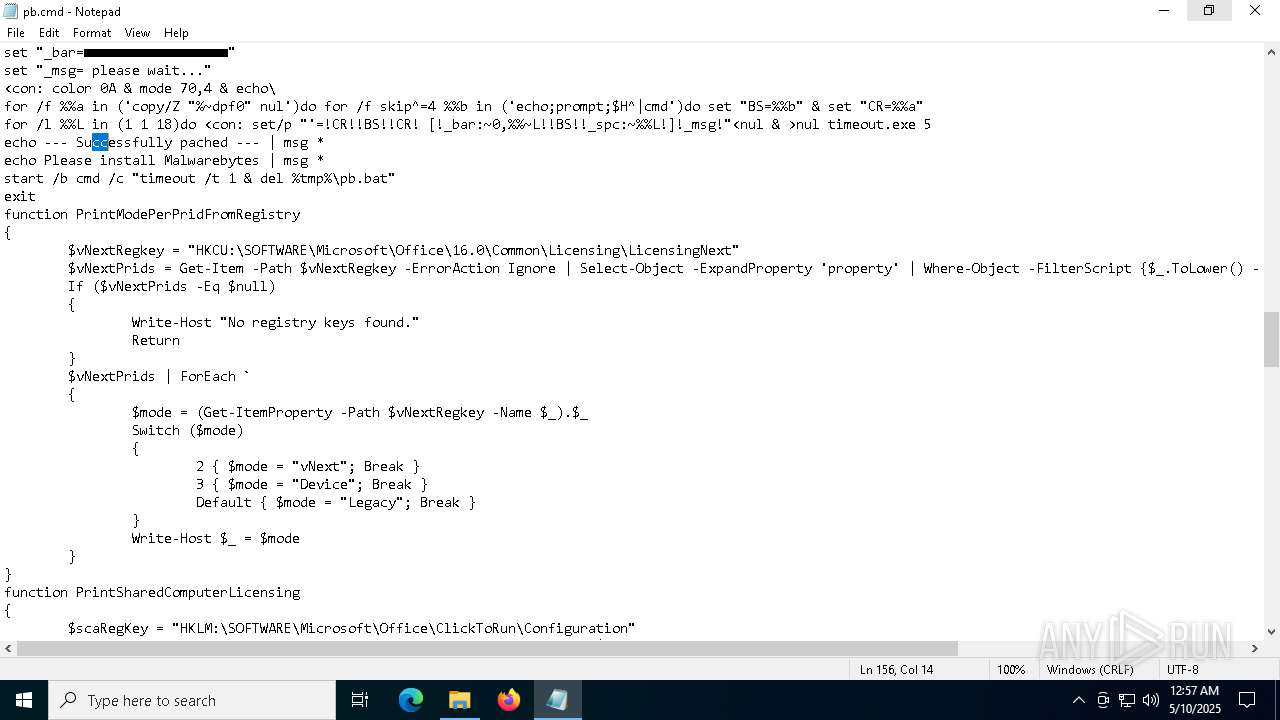
Starts CMD.EXE for commands execution
- Patch.exe (PID: 7592)
- cmd.exe (PID: 7764)
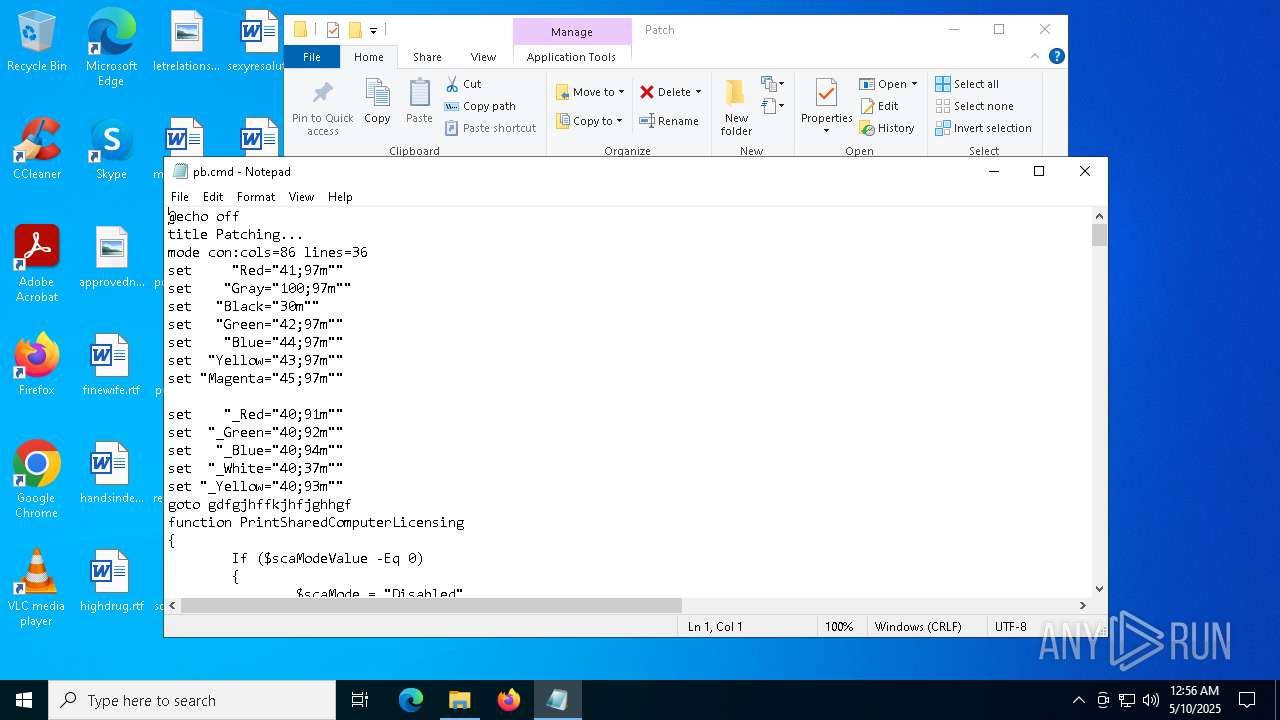
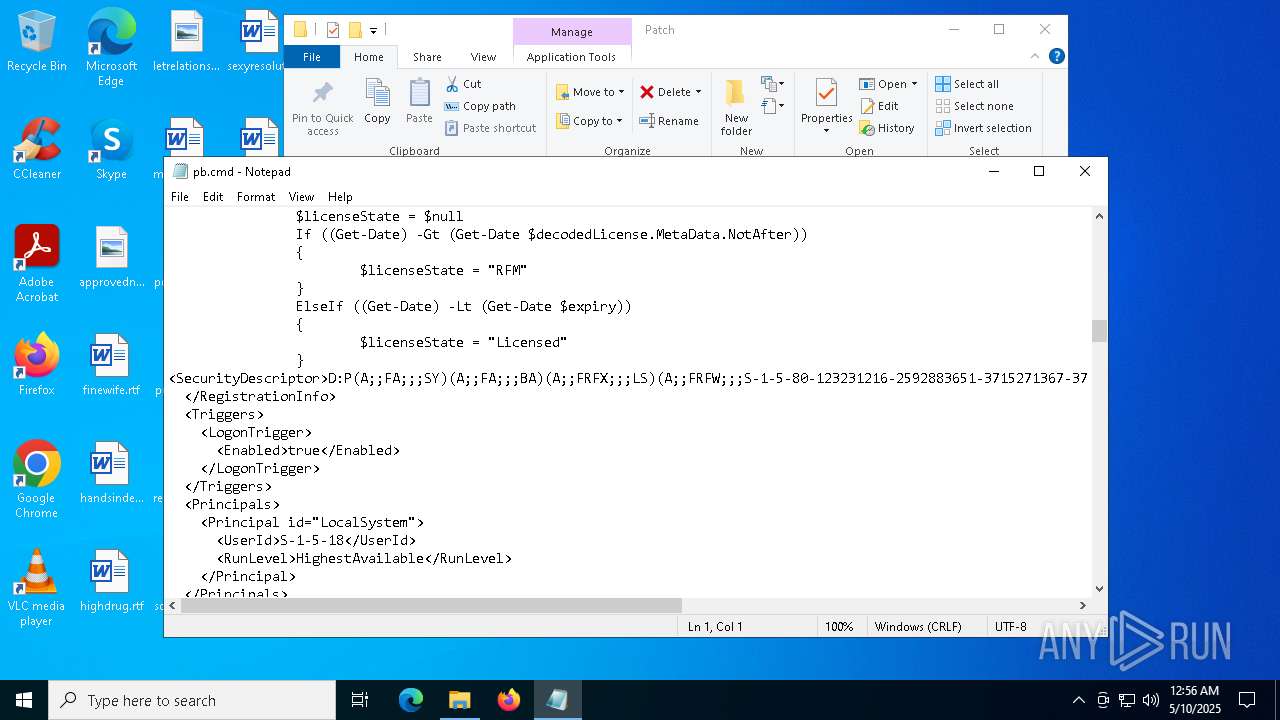
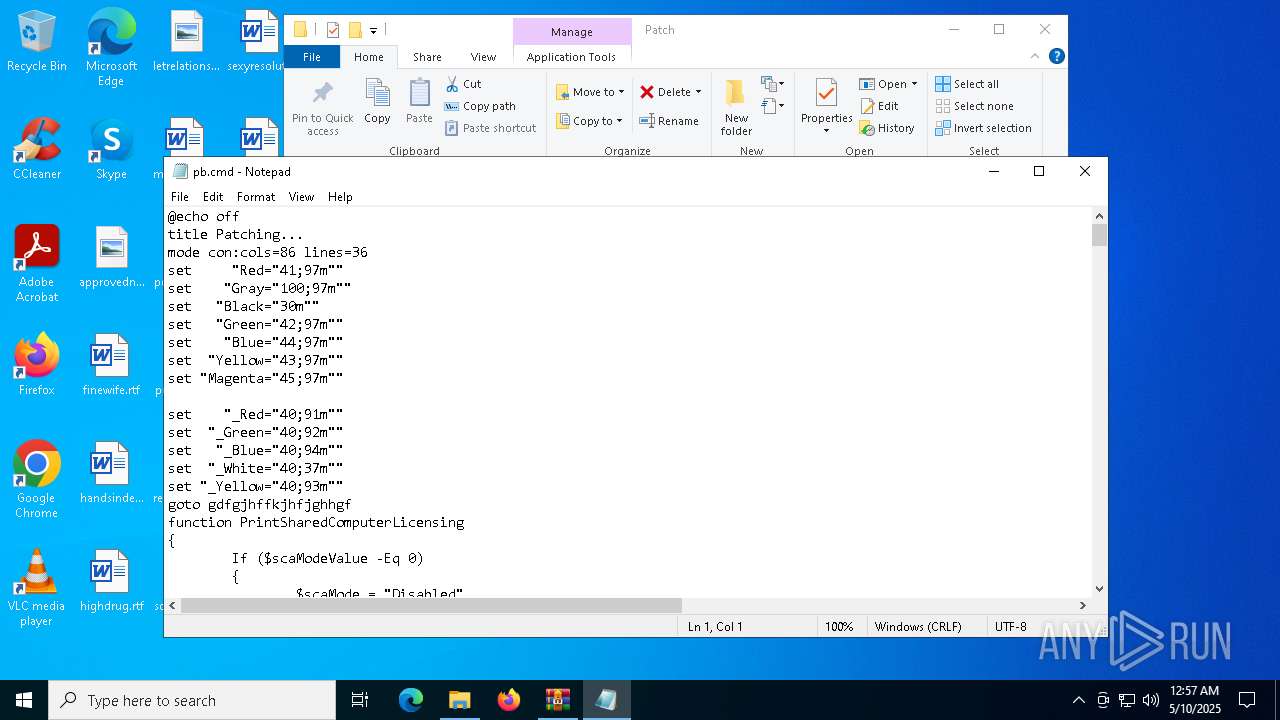
Executing commands from a ".bat" file
- Patch.exe (PID: 7592)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7844)
- cmd.exe (PID: 7888)
- cmd.exe (PID: 7864)
- cmd.exe (PID: 7948)
- cmd.exe (PID: 4200)
- cmd.exe (PID: 5988)
- cmd.exe (PID: 3676)
Modifies hosts file to alter network resolution
- cmd.exe (PID: 7764)
Application launched itself
- cmd.exe (PID: 7764)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7764)
Starts process via Powershell
- powershell.exe (PID: 8128)
- powershell.exe (PID: 4880)
- powershell.exe (PID: 1056)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 7764)
The process verifies whether the antivirus software is installed
- powershell.exe (PID: 8128)
- powershell.exe (PID: 1056)
- cmd.exe (PID: 7764)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7764)
Uses WMIC.EXE
- cmd.exe (PID: 6248)
Get information on the list of running processes
- cmd.exe (PID: 7468)
- cmd.exe (PID: 7764)
- cmd.exe (PID: 2040)
- cmd.exe (PID: 5260)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7764)
Checks for external IP
- svchost.exe (PID: 2196)
- curl.exe (PID: 7788)
- curl.exe (PID: 7704)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 7872)
- WMIC.exe (PID: 7888)
- WMIC.exe (PID: 8008)
- WMIC.exe (PID: 6816)
- WMIC.exe (PID: 7736)
Hides command output
- cmd.exe (PID: 7864)
- cmd.exe (PID: 7948)
- cmd.exe (PID: 4200)
- cmd.exe (PID: 5988)
- cmd.exe (PID: 3676)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 7764)
Execution of CURL command
- cmd.exe (PID: 7764)
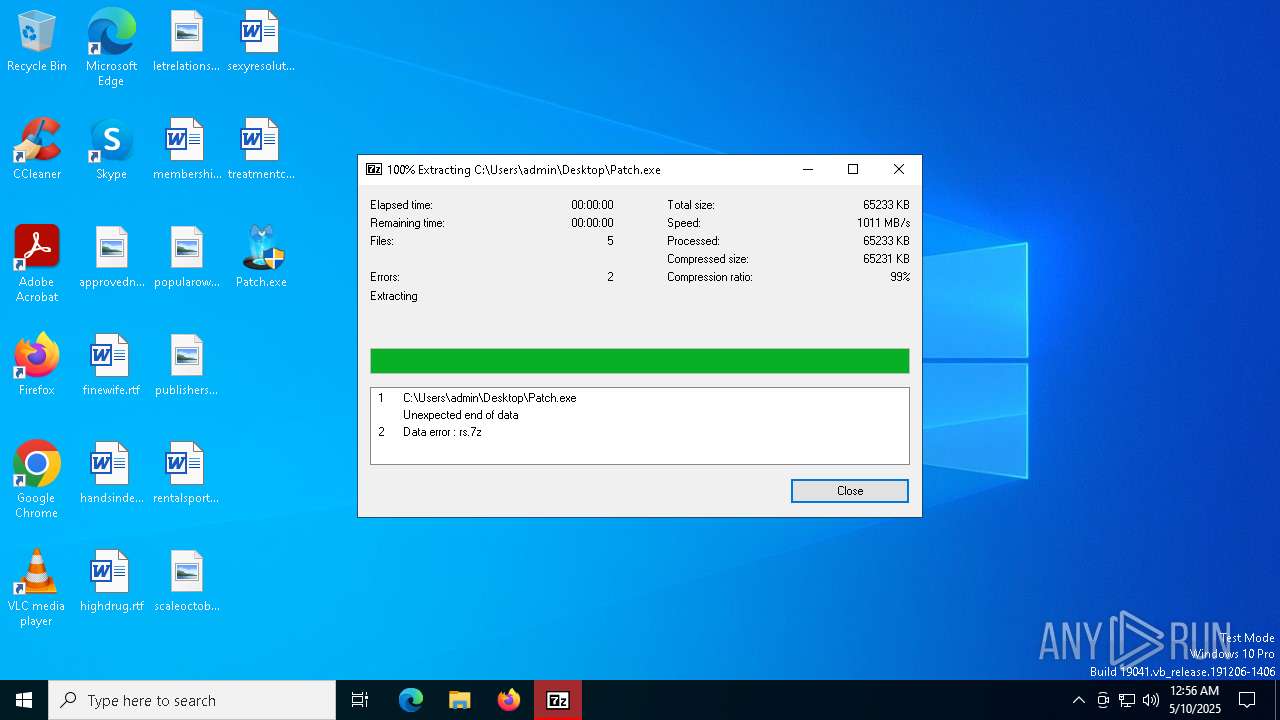
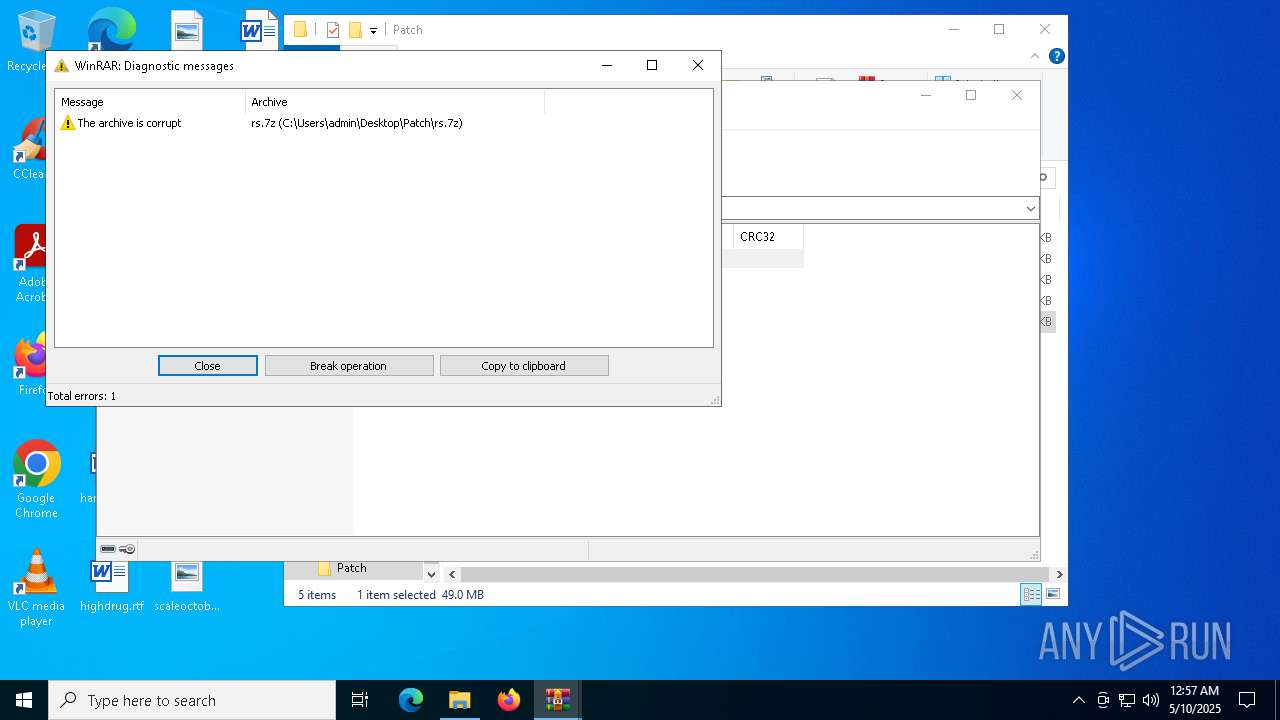
Drops 7-zip archiver for unpacking
- 7z2409-x64.exe (PID: 2332)
- 7zG.exe (PID: 6640)
- firefox.exe (PID: 2344)
Executable content was dropped or overwritten
- 7zG.exe (PID: 6640)
- 7z2409-x64.exe (PID: 2332)
INFO
Create files in a temporary directory
- Patch.exe (PID: 7592)
- curl.exe (PID: 8152)
Checks supported languages
- Patch.exe (PID: 7592)
- curl.exe (PID: 7704)
- curl.exe (PID: 7788)
- curl.exe (PID: 7216)
- curl.exe (PID: 8152)
Reads the computer name
- Patch.exe (PID: 7592)
- curl.exe (PID: 7704)
- curl.exe (PID: 7788)
- curl.exe (PID: 8152)
- curl.exe (PID: 7216)
Manual execution by a user
- WinRAR.exe (PID: 8056)
- WinRAR.exe (PID: 7172)
- firefox.exe (PID: 4880)
- WinRAR.exe (PID: 6640)
- notepad++.exe (PID: 4976)
- 7zG.exe (PID: 6640)
- WinRAR.exe (PID: 2984)
- WinRAR.exe (PID: 3012)
- WinRAR.exe (PID: 4180)
- notepad.exe (PID: 8068)
- WinRAR.exe (PID: 7336)
- notepad.exe (PID: 3124)
- notepad++.exe (PID: 2420)
- 7zFM.exe (PID: 8024)
- 7zFM.exe (PID: 8096)
- WinRAR.exe (PID: 5736)
- 7zG.exe (PID: 8036)
- 7zFM.exe (PID: 6724)
Creates or changes the value of an item property via Powershell
- cmd.exe (PID: 7764)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8128)
- powershell.exe (PID: 4880)
- powershell.exe (PID: 1056)
Creates files in the program directory
- cmd.exe (PID: 7764)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6108)
- WMIC.exe (PID: 7872)
- WMIC.exe (PID: 7888)
- WMIC.exe (PID: 8008)
- WMIC.exe (PID: 6816)
- WMIC.exe (PID: 7736)
Execution of CURL command
- cmd.exe (PID: 7700)
- cmd.exe (PID: 7652)
- cmd.exe (PID: 7764)
- cmd.exe (PID: 3132)
Application launched itself
- firefox.exe (PID: 4880)
- firefox.exe (PID: 2344)
The sample compiled with english language support
- firefox.exe (PID: 2344)
- 7z2409-x64.exe (PID: 2332)
- 7zG.exe (PID: 6640)
Executable content was dropped or overwritten
- firefox.exe (PID: 2344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .scr | | | Windows screen saver (76.4) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (11.6) |
| .exe | | | DOS Executable Generic (11.6) |
| .vxd | | | VXD Driver (0.1) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2021:08:23 03:54:50+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 8 |
| CodeSize: | 379904 |
| InitializedDataSize: | 178688 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5d1a0 |
| OSVersion: | 5.2 |
| ImageVersion: | 5.2 |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
223
Monitored processes
90
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | C:\WINDOWS\system32\cmd.exe /c reg query "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SystemInformation" /v "SystemProductName" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | xcopy /C /H /Q /R /Y "C:\ProgramData\tl\ScanConfig.json" "C:\ProgramData\Malwarebytes\MBAMService\config" | C:\Windows\System32\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Extended Copy Utility Exit code: 4 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | tasklist /fi "imagename eq SbieSvc.exe" /fo csv /nh | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | xcopy /C /H /Q /R /Y "C:\ProgramData\Malwarebytes\MBAMService\config\ScanConfig.json" "C:\ProgramData\tl" | C:\Windows\System32\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Extended Copy Utility Exit code: 4 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | powershell start-process -FilePath 'C:\Program Files\Malwarebytes\Anti-Malware\unins000.exe' -ArgumentList '/VERYSILENT /SUPPRESSMSGBOXES /NORESTART /SP-' -NoNewWindow -Wait | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1244 | findstr /ilc:"Windows 8" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2040 | C:\WINDOWS\system32\cmd.exe /c tasklist /fi "imagename eq QHActiveDefense.exe" /fo csv /nh | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | C:\WINDOWS\system32\cmd.exe /c reg query "HKEY_LOCAL_MACHINE\SYSTEM\HardwareConfig\Current" /v "SystemProductName" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2332 | "C:\Users\admin\Downloads\7z2409-x64.exe" | C:\Users\admin\Downloads\7z2409-x64.exe | firefox.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Installer Exit code: 0 Version: 24.09 Modules
| |||||||||||||||
Total events
37 689
Read events
37 570
Write events
119
Delete events
0
Modification events
| (PID) Process: | (8056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (8056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (8056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (8056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Patch.exe | |||
| (PID) Process: | (7172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
12
Suspicious files
165
Text files
134
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2344 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 8128 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2uv4j4mg.lq5.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 8128 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_dg5ul4wc.jct.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7764 | cmd.exe | C:\Windows\System32\drivers\etc\hosts | text | |
MD5:D7EBF14DEA706776F8C94E21749F3902 | SHA256:D8108FEC76E0948B3784F6628FAF2D417B652B71FDE91F3310E38067424933A7 | |||
| 4880 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4wfqvpst.q3l.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1056 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_uf4qfeb0.2pe.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4880 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_a0jb3htc.2wc.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
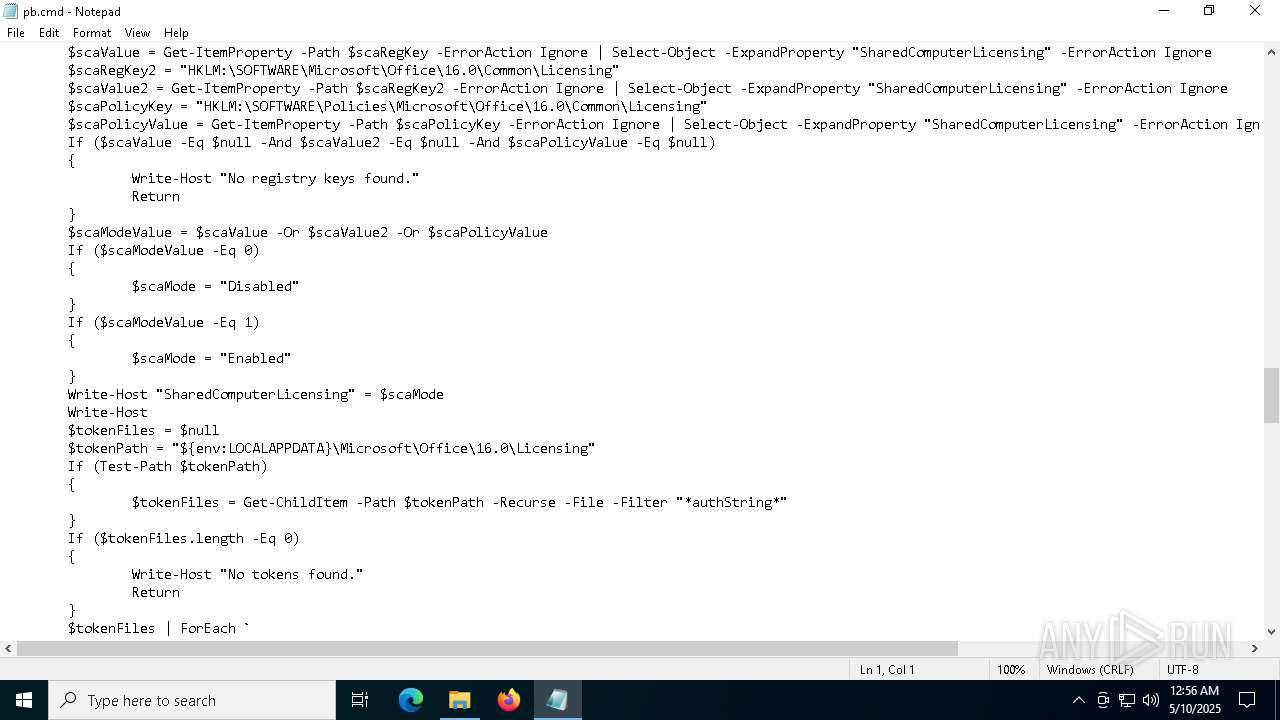
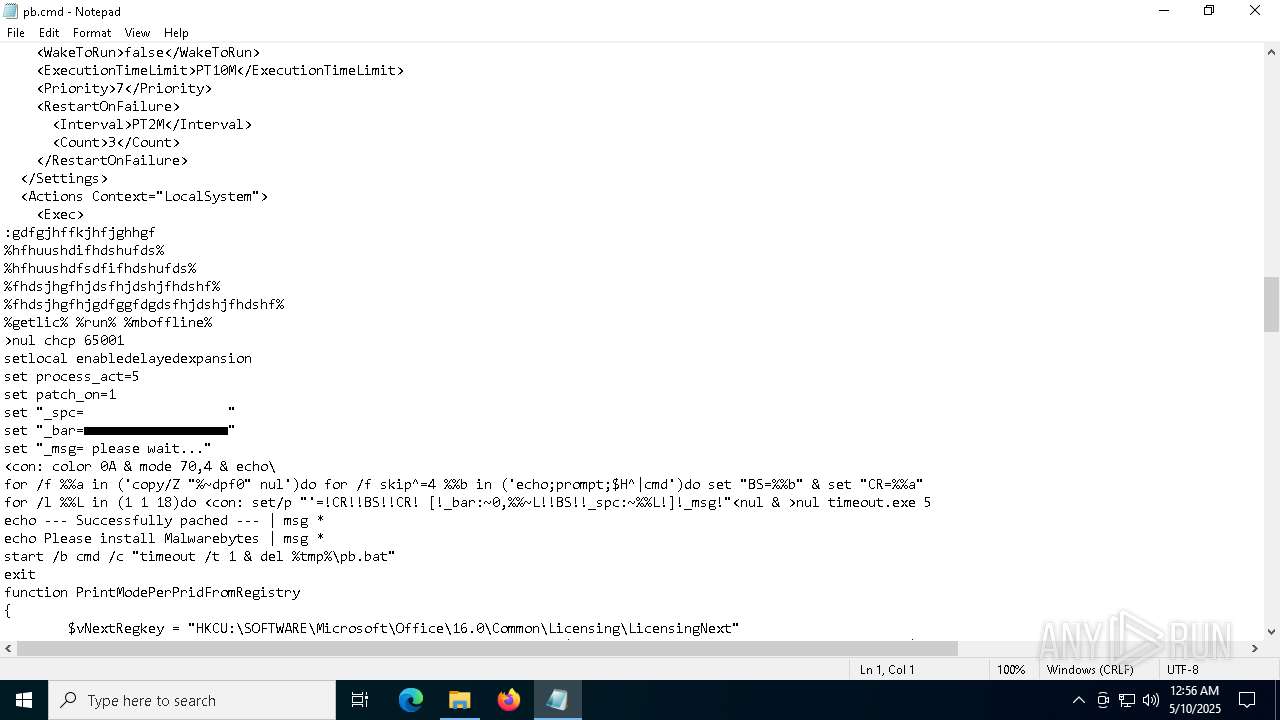
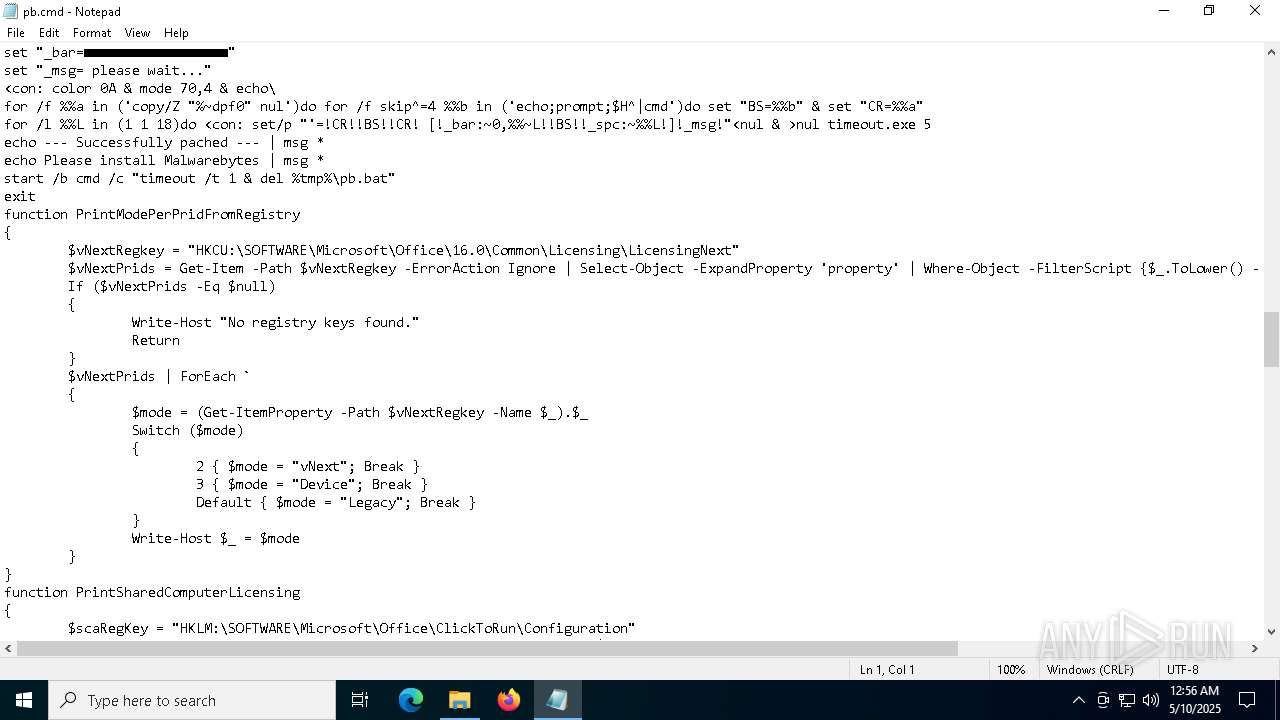
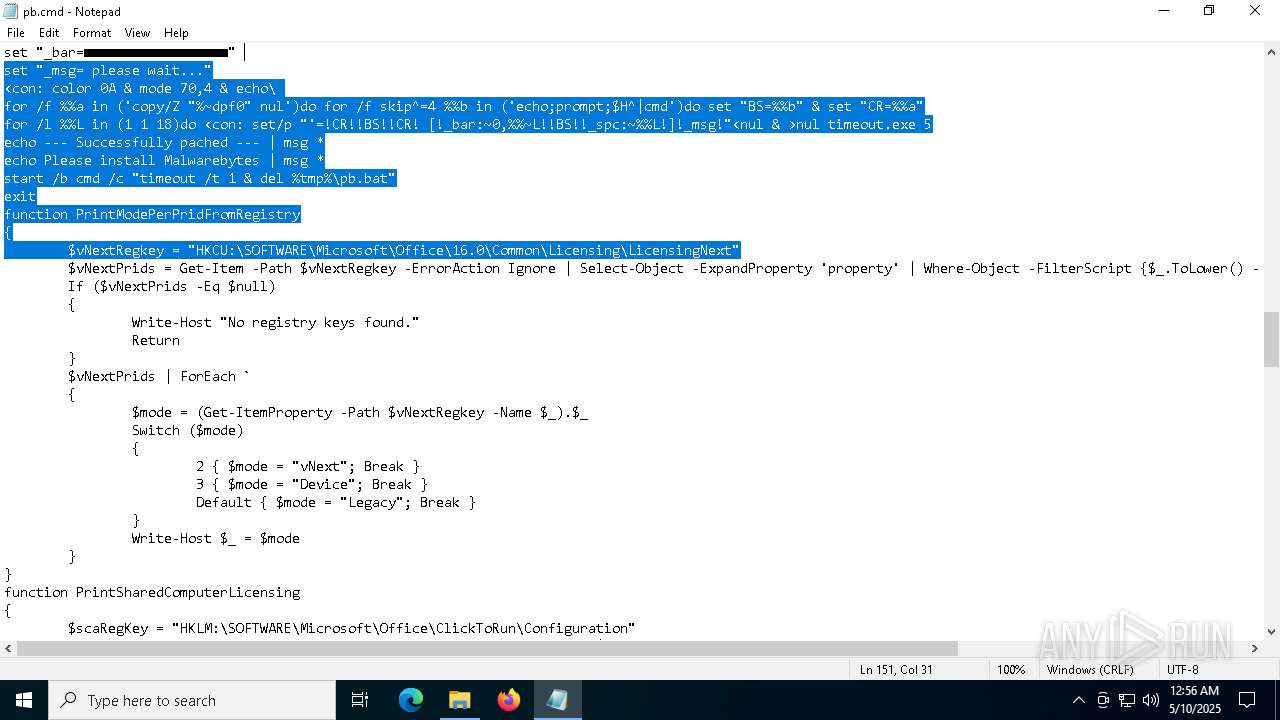
| 7592 | Patch.exe | C:\Users\admin\AppData\Local\Temp\8XYPYO9X.bat | text | |
MD5:7674D583B07DC6B2EB135412DD382AC5 | SHA256:29544D99160D14CCA87B8B9B4DF644A837CC21B0560FED801B868924E1DE3E5B | |||
| 8128 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:1D78EE21E776596613D5FBC439F16D7B | SHA256:4BB9716CDFD99F1A8ED1D70D9367A5EBFAF2D3D910ECB25F80C7EC8AB4362DC4 | |||
| 2344 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
96
DNS requests
132
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2344 | firefox.exe | POST | 200 | 216.58.206.35:80 | http://o.pki.goog/s/we1/rFM | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6652 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6652 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2344 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2344 | firefox.exe | POST | 200 | 2.16.168.113:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
2344 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
2344 | firefox.exe | POST | 200 | 216.58.206.35:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4784 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
ipinfo.io |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
7704 | curl.exe | Device Retrieving External IP Address Detected | ET INFO Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
7704 | curl.exe | Device Retrieving External IP Address Detected | ET INFO Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
7704 | curl.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup SSL Cert Observed (ipinfo .io) |
7788 | curl.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup SSL Cert Observed (ipinfo .io) |