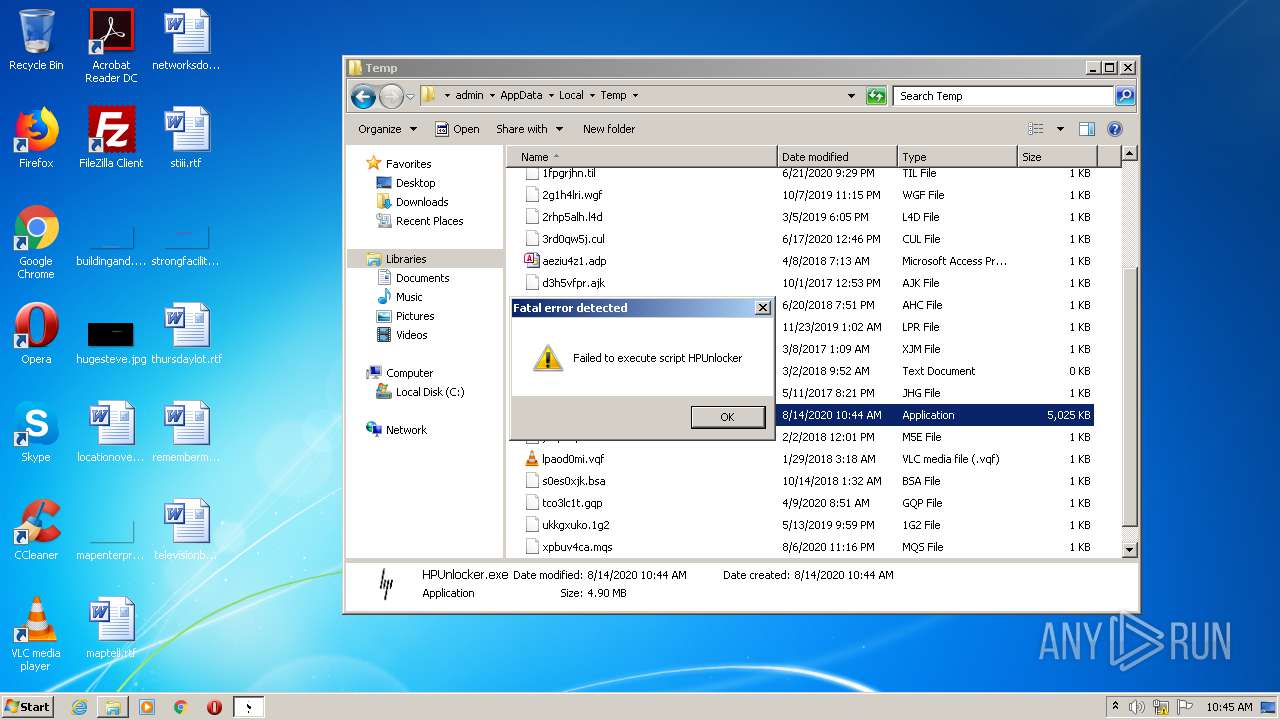
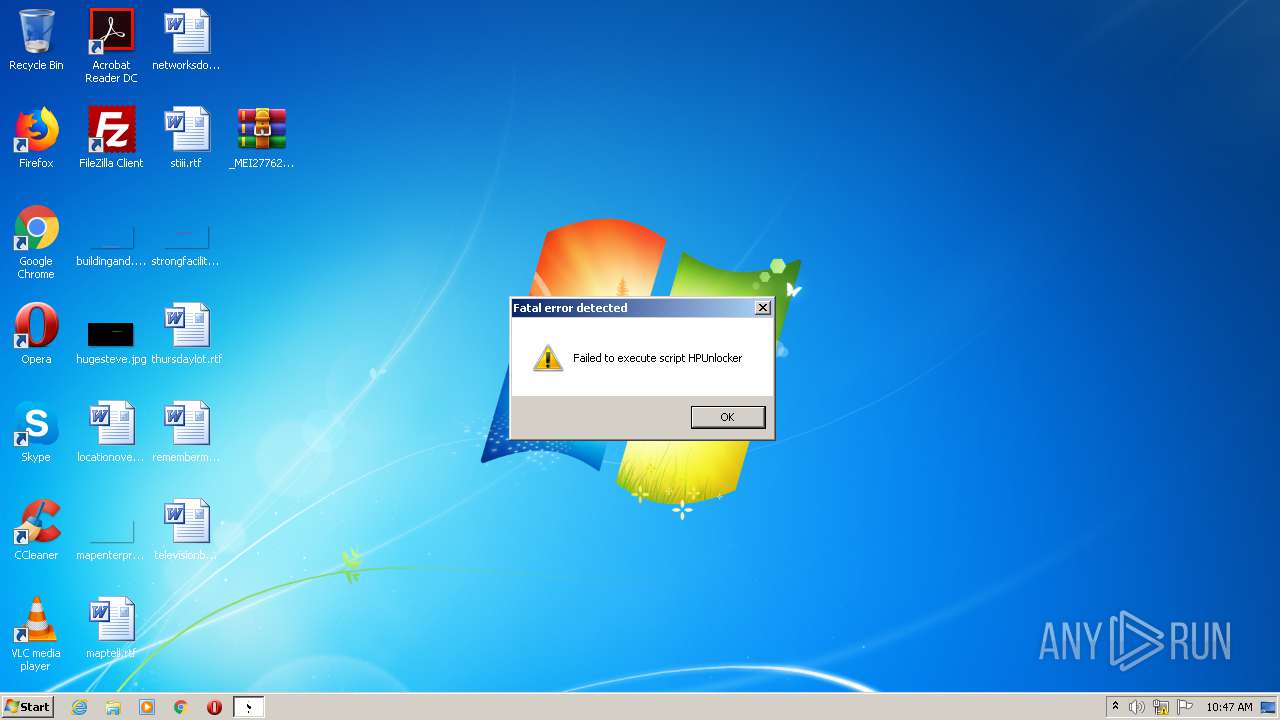
| File name: | HPUnlocker.exe |
| Full analysis: | https://app.any.run/tasks/cce479d3-efdb-431f-998d-ef47e93c0707 |
| Verdict: | Suspicious activity |
| Analysis date: | August 14, 2020, 09:43:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 18CE6A964452CD005B60FB6EF24726CE |
| SHA1: | 4C31A50473DCD88D7D552384E1C5E1C6623910BB |
| SHA256: | 39DA83CAEF2A930CBB64CEB00D2D040B25CC35DA620E233EE0357435C212EC24 |
| SSDEEP: | 98304:Zc7VlKTDbdRGQSxUTZeNEiIK176ykG5pcD7r2lQI4tQ:WVoTDp4QeUpg176K5aDn2/ |
MALICIOUS
Loads dropped or rewritten executable
- HPUnlocker.exe (PID: 3916)
- HPUnlocker.exe (PID: 3040)
SUSPICIOUS
Application launched itself
- HPUnlocker.exe (PID: 2976)
- HPUnlocker.exe (PID: 2776)
Executable content was dropped or overwritten
- HPUnlocker.exe (PID: 2976)
- HPUnlocker.exe (PID: 2776)
Loads Python modules
- HPUnlocker.exe (PID: 3916)
- HPUnlocker.exe (PID: 3040)
INFO
Manual execution by user
- HPUnlocker.exe (PID: 2776)
- explorer.exe (PID: 776)
- iexplore.exe (PID: 3148)
- WinRAR.exe (PID: 1504)
- chrome.exe (PID: 2564)
- explorer.exe (PID: 4036)
- WINWORD.EXE (PID: 2472)
- WINWORD.EXE (PID: 2696)
Reads Internet Cache Settings
- iexplore.exe (PID: 3148)
- iexplore.exe (PID: 2952)
Reads the hosts file
- chrome.exe (PID: 4080)
- chrome.exe (PID: 2564)
Application launched itself
- iexplore.exe (PID: 3148)
- chrome.exe (PID: 2564)
Changes internet zones settings
- iexplore.exe (PID: 3148)
Reads internet explorer settings
- iexplore.exe (PID: 2952)
Reads settings of System Certificates
- iexplore.exe (PID: 3148)
Creates files in the user directory
- iexplore.exe (PID: 2952)
- WINWORD.EXE (PID: 2472)
- WINWORD.EXE (PID: 2696)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3148)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2472)
- WINWORD.EXE (PID: 2696)
Changes settings of System certificates
- iexplore.exe (PID: 3148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:07:09 16:23:33+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 126464 |
| InitializedDataSize: | 265728 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x7b43 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 09-Jul-2019 14:23:33 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000108 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 09-Jul-2019 14:23:33 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0001ECA4 | 0x0001EE00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.64533 |
.rdata | 0x00020000 | 0x0000B164 | 0x0000B200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.10043 |
.data | 0x0002C000 | 0x0000E688 | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.92387 |
.gfids | 0x0003B000 | 0x000000B8 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.85181 |
.rsrc | 0x0003C000 | 0x000336DC | 0x00033800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.18623 |
.reloc | 0x00070000 | 0x000017B8 | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.65903 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
0 | 2.01924 | 20 | Latin 1 / Western European | UNKNOWN | RT_GROUP_ICON |
1 | 5.31683 | 1033 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
2 | 6.44895 | 2216 | Latin 1 / Western European | UNKNOWN | RT_ICON |
3 | 5.77742 | 1384 | Latin 1 / Western European | UNKNOWN | RT_ICON |
4 | 7.95095 | 38188 | Latin 1 / Western European | UNKNOWN | RT_ICON |
5 | 6.0521 | 9640 | Latin 1 / Western European | UNKNOWN | RT_ICON |
6 | 6.15081 | 4264 | Latin 1 / Western European | UNKNOWN | RT_ICON |
7 | 6.39466 | 1128 | Latin 1 / Western European | UNKNOWN | RT_ICON |
101 | 2.71858 | 104 | Latin 1 / Western European | UNKNOWN | RT_GROUP_ICON |
Imports
KERNEL32.dll |
USER32.dll |
WS2_32.dll |
Total processes
82
Monitored processes
32
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 532 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2604 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 772 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,15042761244121354801,7009413782753363202,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17199381728416265831 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2264 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 776 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 872 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1020,15042761244121354801,7009413782753363202,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=625805042083941379 --mojo-platform-channel-handle=3944 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1068 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1020,15042761244121354801,7009413782753363202,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=1727760512980450505 --mojo-platform-channel-handle=3496 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1076 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,15042761244121354801,7009413782753363202,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9853478139404491895 --renderer-client-id=11 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2512 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1348 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1020,15042761244121354801,7009413782753363202,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16353158794905856108 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2444 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1504 | "C:\Program Files\WinRAR\WinRAR.exe" a -ep1 -scul -r0 -iext -- _MEI27762.rar C:\Users\admin\AppData\Local\Temp\_MEI27762 | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1780 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6bf1a9d0,0x6bf1a9e0,0x6bf1a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2092 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1020,15042761244121354801,7009413782753363202,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=17896989769793248063 --mojo-platform-channel-handle=3972 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
3 887
Read events
2 987
Write events
590
Delete events
310
Modification events
| (PID) Process: | (1504) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1504) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1504) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1504) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1504) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1504) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3148) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 3163302243 | |||
| (PID) Process: | (3148) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30831135 | |||
| (PID) Process: | (3148) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3148) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
24
Suspicious files
123
Text files
146
Unknown types
46
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2976 | HPUnlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI29762\_ssl.pyd | executable | |
MD5:CC5C8EB32ACB2261C42A7285D436CCA9 | SHA256:07EA50E536886F68473635FFEFCFCAA7266E63C478EF039BA100DDF02F88CE61 | |||
| 2976 | HPUnlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI29762\unicodedata.pyd | executable | |
MD5:E176F984D22F031098D700B7F1892378 | SHA256:46876FC52F1529C2633372D8E2CEA5B08B5A8582F8645CFAD8F5FF8128A7F575 | |||
| 2976 | HPUnlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI29762\_lzma.pyd | executable | |
MD5:65880A33015AF2030A08987924CA737B | SHA256:A71366B95D89D1539A6EE751D48A969C1BCA1AA75116424CC5F905F32A625EEA | |||
| 2976 | HPUnlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI29762\_bz2.pyd | executable | |
MD5:FF5AC8FB724EDB1635E2AD985F98EE5B | SHA256:B94F64FCB49F40682ED794FA1940A1DC0C8A28F24A1768D3BFE774CF75F59B62 | |||
| 2976 | HPUnlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI29762\pyexpat.pyd | executable | |
MD5:F4AC522E0A04829BBA2B8FCA878F560E | SHA256:87A1D8B94668C55AC0B67E05A9505031E38510CFD2A47979697C05B7C7B375A2 | |||
| 2776 | HPUnlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI27762\_hashlib.pyd | executable | |
MD5:E84E1BA269371E439C2D52024ACA6535 | SHA256:2FCB297733E6080480AC24CF073FF5E239FB02A1CE9694313C5047F9C58D781B | |||
| 2976 | HPUnlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI29762\VCRUNTIME140.dll | executable | |
MD5:AE96651CFBD18991D186A029CBECB30C | SHA256:1B372F064EACB455A0351863706E6326CA31B08E779A70DE5DE986B5BE8069A1 | |||
| 2976 | HPUnlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI29762\libssl-1_1.dll | executable | |
MD5:5ADB49CC84ABD6D3C8F959CA5A146AD7 | SHA256:F4D5DF50BDF3E7304C67C81ACE83263C8D0F0E28087C6104C21150BFEDA86B8D | |||
| 2976 | HPUnlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI29762\_hashlib.pyd | executable | |
MD5:E84E1BA269371E439C2D52024ACA6535 | SHA256:2FCB297733E6080480AC24CF073FF5E239FB02A1CE9694313C5047F9C58D781B | |||
| 2976 | HPUnlocker.exe | C:\Users\admin\AppData\Local\Temp\_MEI29762\base_library.zip | compressed | |
MD5:90544865D020F647A52A766047D87F3E | SHA256:F958D612D9B7A24BB324FDD2202BAB156C808DF069D0D84685C230A414612F9C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
92
DNS requests
63
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
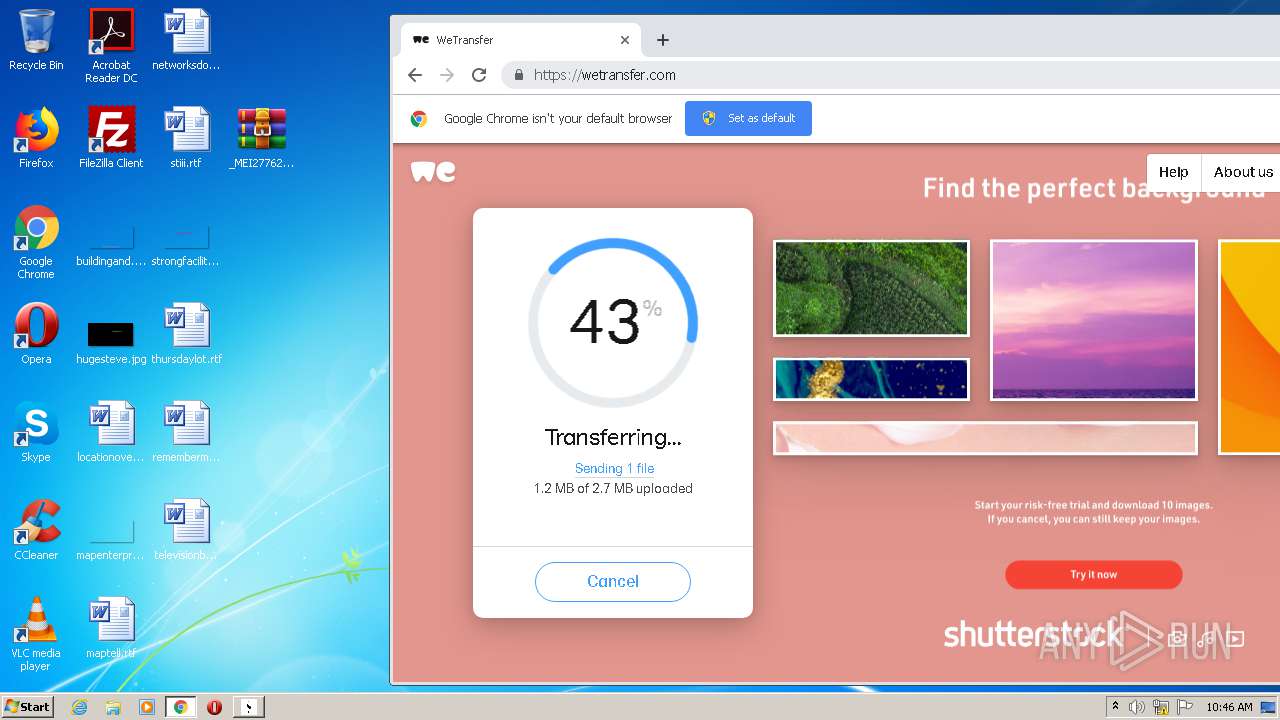
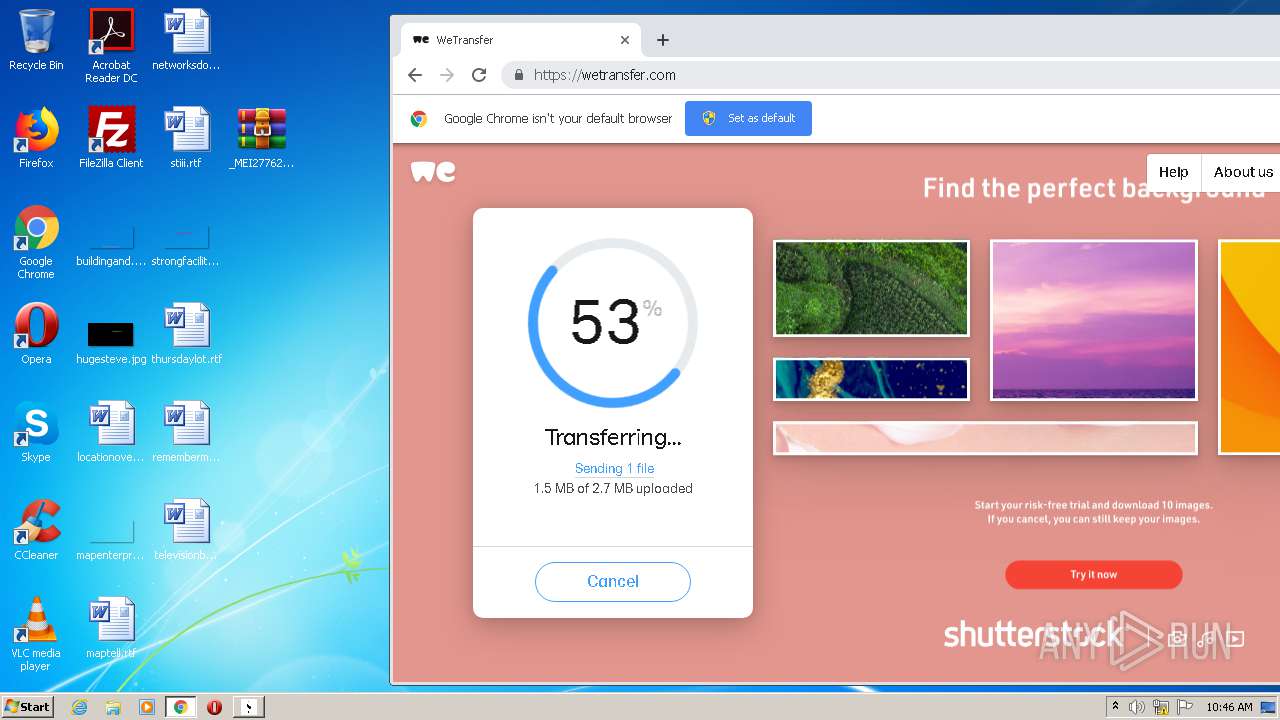
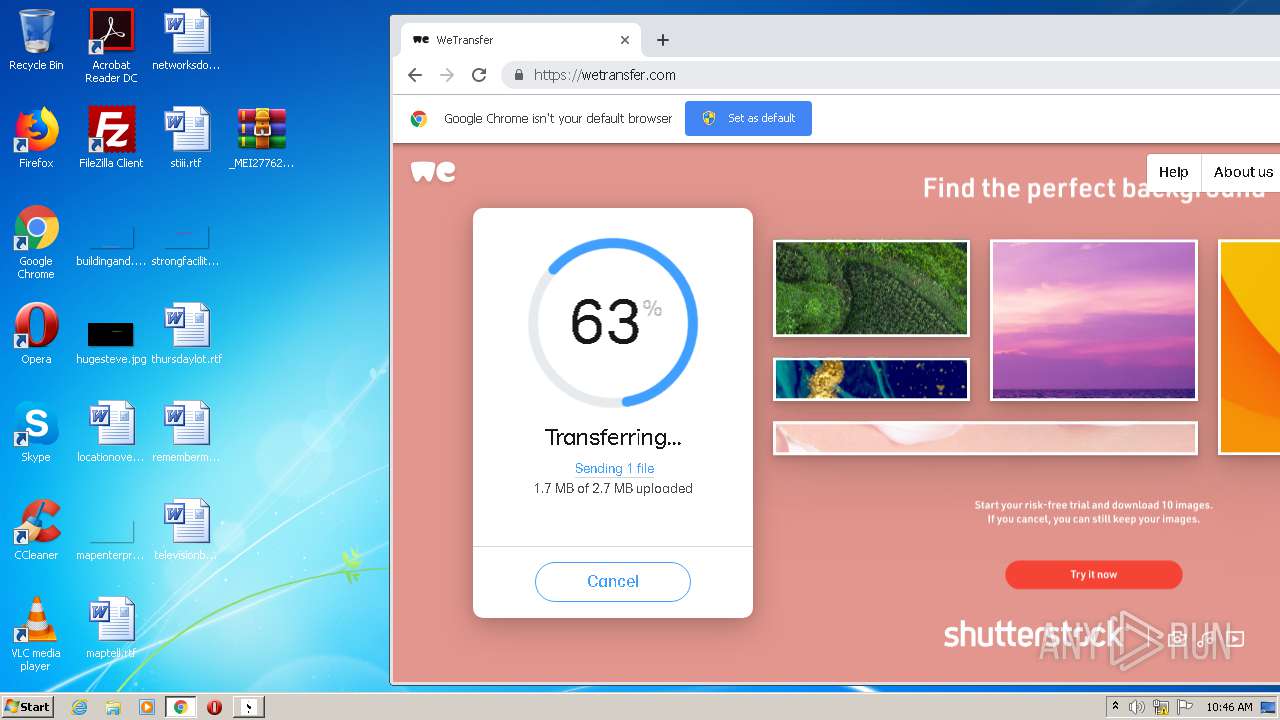
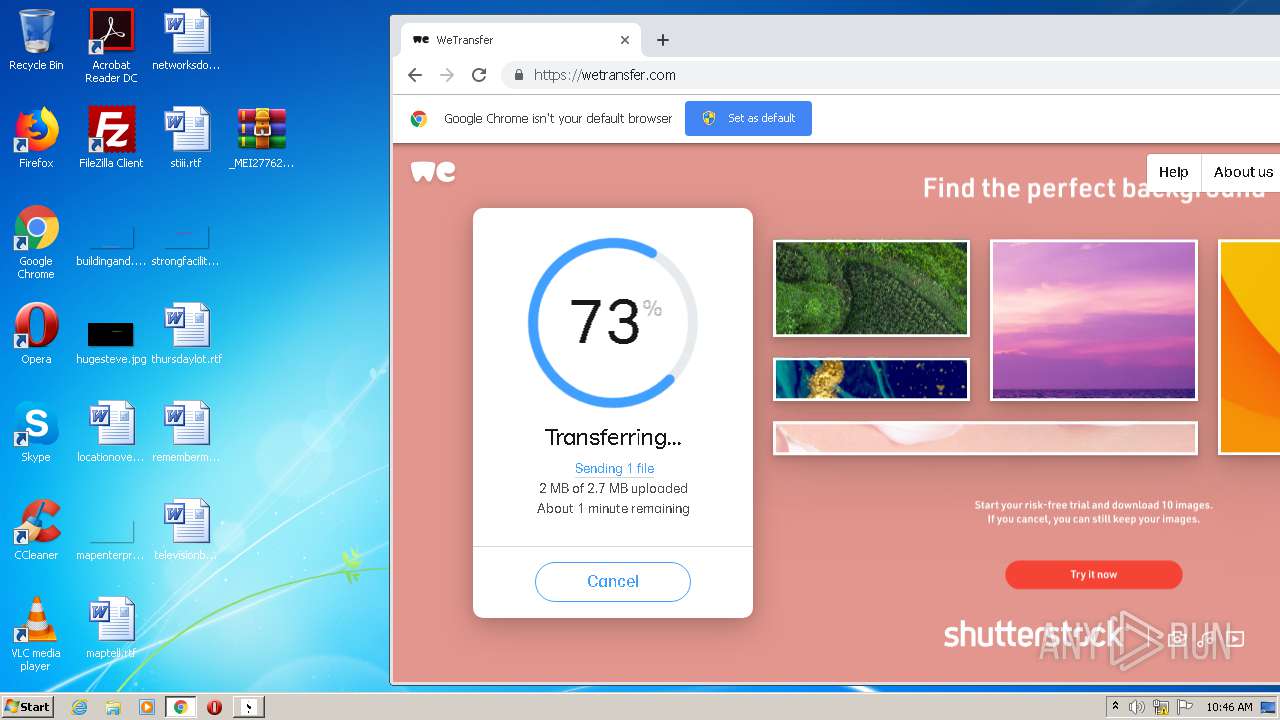
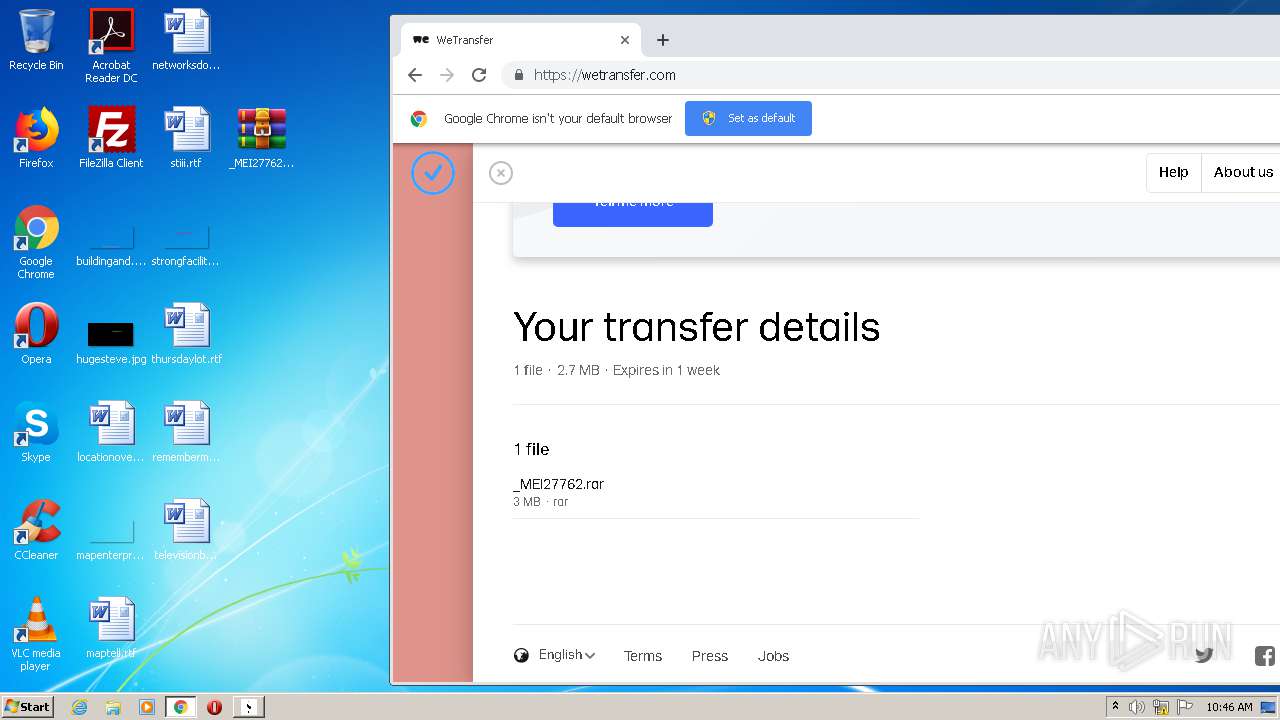
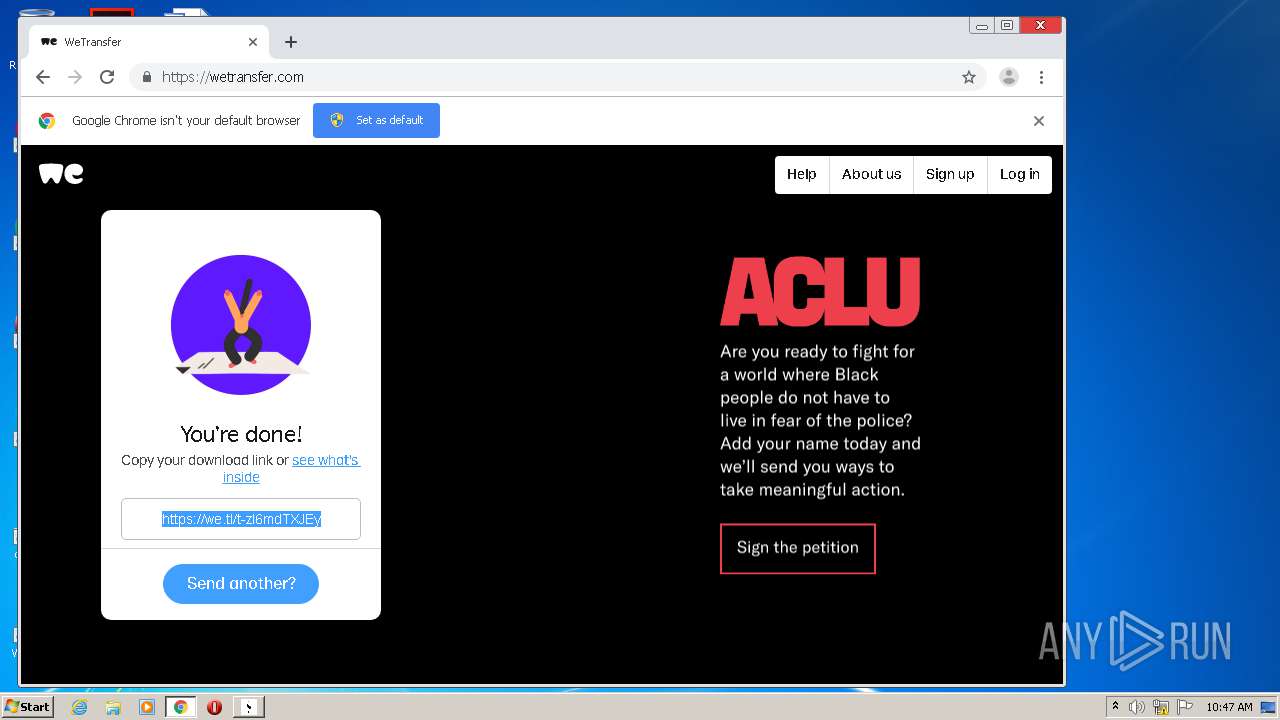
2952 | iexplore.exe | GET | 301 | 52.17.149.98:80 | http://wetransfer.com/ | IE | — | — | shared |
2952 | iexplore.exe | GET | 200 | 23.37.43.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEGMYDTj7gJd4qdA1oxYY%2BEA%3D | NL | der | 1.71 Kb | shared |
2952 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
2952 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr1/ME8wTTBLMEkwRzAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDkbwjNvPLFRm7zMB3V80 | US | der | 1.49 Kb | whitelisted |
2952 | iexplore.exe | GET | 200 | 13.35.253.185:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
2952 | iexplore.exe | GET | 200 | 23.37.43.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEGMYDTj7gJd4qdA1oxYY%2BEA%3D | NL | der | 1.71 Kb | shared |
2952 | iexplore.exe | GET | 200 | 13.35.253.198:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
3148 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2952 | iexplore.exe | GET | 200 | 143.204.208.165:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
2952 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr1/ME8wTTBLMEkwRzAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDkbwjNvPLFRm7zMB3V80 | US | der | 1.49 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2952 | iexplore.exe | 52.17.149.98:80 | wetransfer.com | Amazon.com, Inc. | IE | unknown |
4080 | chrome.exe | 172.217.23.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
4080 | chrome.exe | 172.217.16.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
4080 | chrome.exe | 216.58.207.68:443 | www.google.com | Google Inc. | US | whitelisted |
2952 | iexplore.exe | 143.204.208.165:80 | o.ss2.us | — | US | malicious |
2952 | iexplore.exe | 13.35.253.198:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
2952 | iexplore.exe | 13.35.253.185:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
4080 | chrome.exe | 216.58.207.42:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2952 | iexplore.exe | 143.204.208.79:80 | o.ss2.us | — | US | whitelisted |
4080 | chrome.exe | 172.217.18.99:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wetransfer.com |
| shared |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
o.ss2.us |
| whitelisted |
www.google.com |
| malicious |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.sca1b.amazontrust.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |