| File name: | 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4 |
| Full analysis: | https://app.any.run/tasks/5cbed43e-e8a3-41d3-8fab-1fb9ba4ae48c |
| Verdict: | Malicious activity |
| Analysis date: | April 08, 2025, 18:20:54 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | DFB4C34C623ABDF69291746050E17105 |
| SHA1: | 5469A508DBCD0FAC271C9A6363083B98FB0B4F88 |
| SHA256: | 39CF49EA66350706CB9FB8927C24B20BCB175574248BC9FEFDB6475628AF47C4 |
| SSDEEP: | 1572864:ABinBo9VzcASYOSd8gHgGgWaUp/T9oWoyQhi:AknBAVzpP7HgGgWaU3o8Ii |
MALICIOUS
No malicious indicators.SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe (PID: 2504)
The process creates files with name similar to system file names
- 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe (PID: 2504)
Drops 7-zip archiver for unpacking
- 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe (PID: 2504)
Reads security settings of Internet Explorer
- 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe (PID: 2504)
- Installer.exe (PID: 7012)
Process drops legitimate windows executable
- 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe (PID: 2504)
- Installer.exe (PID: 7012)
Creates a software uninstall entry
- 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe (PID: 2504)
There is functionality for taking screenshot (YARA)
- 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe (PID: 2504)
Executable content was dropped or overwritten
- 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe (PID: 2504)
- Installer.exe (PID: 7012)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 2568)
- cmd.exe (PID: 7616)
- cmd.exe (PID: 7724)
- cmd.exe (PID: 616)
- cmd.exe (PID: 8132)
- cmd.exe (PID: 2560)
- cmd.exe (PID: 7704)
- cmd.exe (PID: 7536)
- cmd.exe (PID: 2108)
- cmd.exe (PID: 3192)
- cmd.exe (PID: 3800)
- cmd.exe (PID: 7616)
- cmd.exe (PID: 7712)
- cmd.exe (PID: 8012)
- cmd.exe (PID: 7716)
- cmd.exe (PID: 7484)
- cmd.exe (PID: 4528)
- cmd.exe (PID: 3020)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4300)
- cmd.exe (PID: 7604)
- cmd.exe (PID: 4628)
- cmd.exe (PID: 4228)
- cmd.exe (PID: 5600)
- cmd.exe (PID: 8044)
- cmd.exe (PID: 4172)
- cmd.exe (PID: 8144)
- cmd.exe (PID: 7544)
- cmd.exe (PID: 7352)
- cmd.exe (PID: 6576)
- cmd.exe (PID: 7480)
- cmd.exe (PID: 7808)
- cmd.exe (PID: 7984)
- cmd.exe (PID: 7760)
- cmd.exe (PID: 7508)
- cmd.exe (PID: 7336)
- cmd.exe (PID: 1312)
- cmd.exe (PID: 7852)
- cmd.exe (PID: 3032)
- cmd.exe (PID: 4304)
- cmd.exe (PID: 7412)
- cmd.exe (PID: 1600)
- cmd.exe (PID: 8044)
- cmd.exe (PID: 7744)
- cmd.exe (PID: 7600)
- cmd.exe (PID: 2316)
- cmd.exe (PID: 2108)
- cmd.exe (PID: 1912)
- cmd.exe (PID: 4932)
- cmd.exe (PID: 7344)
- cmd.exe (PID: 8076)
- cmd.exe (PID: 6072)
- cmd.exe (PID: 6048)
- cmd.exe (PID: 7644)
- cmd.exe (PID: 8092)
- cmd.exe (PID: 3760)
- cmd.exe (PID: 7980)
- cmd.exe (PID: 1660)
- cmd.exe (PID: 7476)
- cmd.exe (PID: 1312)
- cmd.exe (PID: 7828)
- cmd.exe (PID: 7816)
- cmd.exe (PID: 6584)
- cmd.exe (PID: 6808)
- cmd.exe (PID: 7340)
- cmd.exe (PID: 3192)
- cmd.exe (PID: 7716)
- cmd.exe (PID: 7552)
- cmd.exe (PID: 7472)
- cmd.exe (PID: 7148)
- cmd.exe (PID: 8104)
- cmd.exe (PID: 8052)
Application launched itself
- Installer.exe (PID: 7012)
- Installer.exe (PID: 7536)
Starts CMD.EXE for commands execution
- Installer.exe (PID: 7012)
- Installer.exe (PID: 7536)
Process drops python dynamic module
- Installer.exe (PID: 7012)
The process drops C-runtime libraries
- Installer.exe (PID: 7012)
Reads the date of Windows installation
- Installer.exe (PID: 7012)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 7724)
- WMIC.exe (PID: 8100)
- WMIC.exe (PID: 1348)
- WMIC.exe (PID: 924)
- WMIC.exe (PID: 8008)
- WMIC.exe (PID: 3024)
- WMIC.exe (PID: 2140)
- WMIC.exe (PID: 7696)
- WMIC.exe (PID: 6184)
- WMIC.exe (PID: 6824)
- WMIC.exe (PID: 7664)
- WMIC.exe (PID: 7552)
- WMIC.exe (PID: 8128)
- WMIC.exe (PID: 7744)
- WMIC.exe (PID: 5328)
- WMIC.exe (PID: 7492)
- WMIC.exe (PID: 132)
- WMIC.exe (PID: 7652)
INFO
The sample compiled with english language support
- 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe (PID: 2504)
- Installer.exe (PID: 7012)
Checks supported languages
- 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe (PID: 2504)
- Installer.exe (PID: 7012)
- Installer.exe (PID: 5260)
- Installer.exe (PID: 6676)
- Installer.exe (PID: 5308)
- Installer.exe (PID: 7360)
- Installer.exe (PID: 7308)
- Installer.exe (PID: 7536)
- Installer.exe (PID: 7780)
- Installer.exe (PID: 7992)
- Installer.exe (PID: 7964)
Reads the computer name
- 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe (PID: 2504)
- Installer.exe (PID: 6676)
- Installer.exe (PID: 7012)
- Installer.exe (PID: 7536)
- Installer.exe (PID: 7780)
- Installer.exe (PID: 5260)
- Installer.exe (PID: 7964)
Create files in a temporary directory
- 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe (PID: 2504)
- Installer.exe (PID: 7012)
- Installer.exe (PID: 7536)
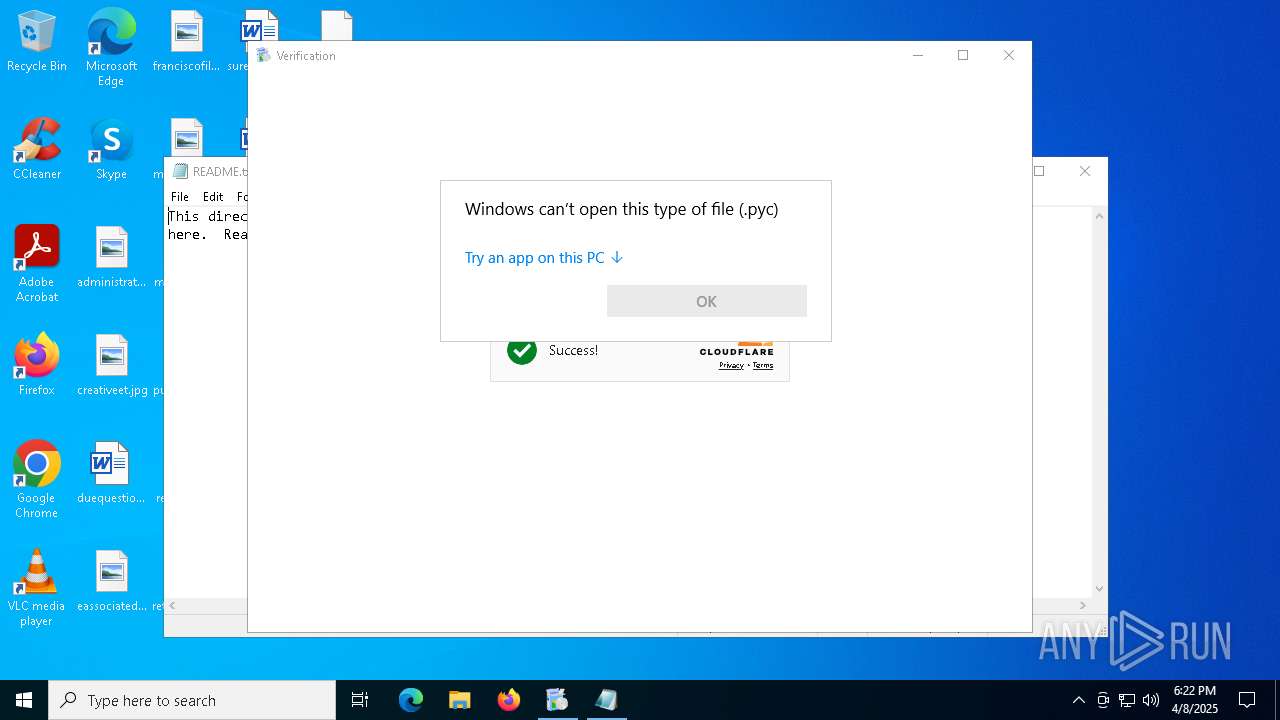
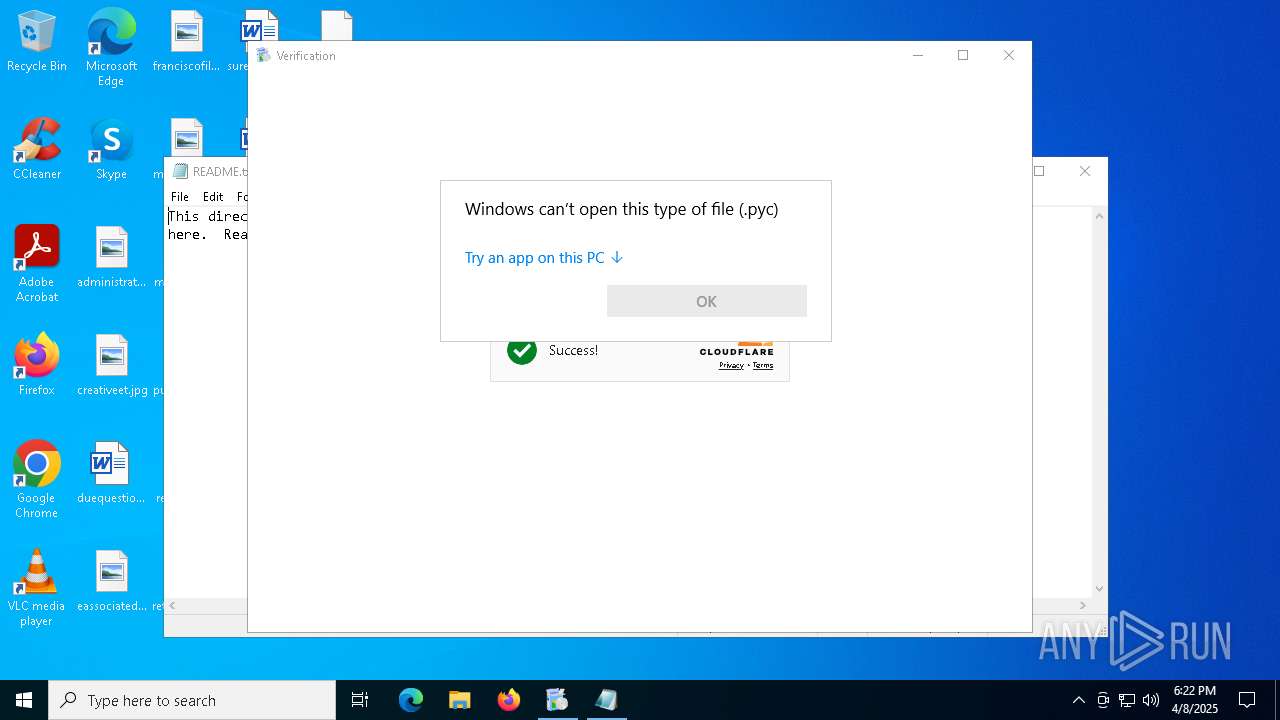
Manual execution by a user
- Installer.exe (PID: 7012)
- Installer.exe (PID: 1188)
- cmd.exe (PID: 5304)
- OpenWith.exe (PID: 6268)
- notepad.exe (PID: 900)
- OpenWith.exe (PID: 7796)
- OpenWith.exe (PID: 7444)
- OpenWith.exe (PID: 5772)
- OpenWith.exe (PID: 2040)
- OpenWith.exe (PID: 7632)
- OpenWith.exe (PID: 3796)
- OpenWith.exe (PID: 7640)
Reads Environment values
- Installer.exe (PID: 7012)
- Installer.exe (PID: 7536)
Reads CPU info
- Installer.exe (PID: 7012)
- Installer.exe (PID: 7536)
Creates files or folders in the user directory
- 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe (PID: 2504)
- Installer.exe (PID: 7012)
- Installer.exe (PID: 6676)
- Installer.exe (PID: 7964)
- Installer.exe (PID: 7536)
Reads product name
- Installer.exe (PID: 7012)
- Installer.exe (PID: 7536)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 1348)
- WMIC.exe (PID: 7724)
- WMIC.exe (PID: 8008)
- WMIC.exe (PID: 924)
- WMIC.exe (PID: 3024)
- WMIC.exe (PID: 2140)
- WMIC.exe (PID: 6184)
- WMIC.exe (PID: 8100)
- WMIC.exe (PID: 7552)
- WMIC.exe (PID: 5328)
Checks proxy server information
- Installer.exe (PID: 7012)
- Installer.exe (PID: 7536)
- slui.exe (PID: 7836)
Reads the machine GUID from the registry
- Installer.exe (PID: 7012)
- Installer.exe (PID: 7536)
Process checks computer location settings
- Installer.exe (PID: 7308)
- Installer.exe (PID: 5308)
- Installer.exe (PID: 7360)
- Installer.exe (PID: 7536)
- Installer.exe (PID: 7012)
- Installer.exe (PID: 7992)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4628)
- powershell.exe (PID: 7736)
Creates files in the program directory
- 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe (PID: 2504)
Reads Windows Product ID
- powershell.exe (PID: 7460)
- powershell.exe (PID: 8188)
- powershell.exe (PID: 4528)
- powershell.exe (PID: 7832)
- powershell.exe (PID: 6264)
- powershell.exe (PID: 7884)
- powershell.exe (PID: 4008)
- powershell.exe (PID: 2416)
- powershell.exe (PID: 4228)
- powershell.exe (PID: 6752)
- powershell.exe (PID: 1348)
- powershell.exe (PID: 7476)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6268)
- OpenWith.exe (PID: 7796)
- OpenWith.exe (PID: 7444)
- OpenWith.exe (PID: 3796)
- OpenWith.exe (PID: 7640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:15 22:26:14+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 473088 |
| UninitializedDataSize: | 16384 |
| EntryPoint: | 0x338f |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.3.41.0 |
| ProductVersionNumber: | 4.3.41.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileDescription: | This is an innovative application developed to the highest security standards. |
| FileVersion: | 4.3.41 |
| LegalCopyright: | Copyright © 2025 Installer |
| ProductName: | Installer |
| ProductVersion: | 4.3.41 |
Total processes
365
Monitored processes
239
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | wmic path win32_VideoController get name | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | powershell.exe -Command "(Get-CimInstance Win32_ComputerSystemProduct).UUID" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | powershell -Command "(Get-WmiObject Win32_OperatingSystem).Caption" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | C:\WINDOWS\system32\cmd.exe /d /s /c "wmic path win32_VideoController get name" | C:\Windows\System32\cmd.exe | — | Installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | powershell -Command "Get-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion' | Select-Object -ExpandProperty InstallDate" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 872 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\README.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 924 | wmic path win32_VideoController get name | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
242 156
Read events
242 084
Write events
18
Delete events
54
Modification events
| (PID) Process: | (2504) 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\f84a1f8f-4350-566d-aebc-bd056217375f |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\Installer | |||
| (PID) Process: | (2504) 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\f84a1f8f-4350-566d-aebc-bd056217375f |
| Operation: | write | Name: | KeepShortcuts |
Value: true | |||
| (PID) Process: | (2504) 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\f84a1f8f-4350-566d-aebc-bd056217375f |
| Operation: | write | Name: | ShortcutName |
Value: Installer | |||
| (PID) Process: | (2504) 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\f84a1f8f-4350-566d-aebc-bd056217375f |
| Operation: | write | Name: | DisplayName |
Value: Installer 4.3.41 | |||
| (PID) Process: | (2504) 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\f84a1f8f-4350-566d-aebc-bd056217375f |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\Installer\Uninstall Installer.exe" /allusers | |||
| (PID) Process: | (2504) 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\f84a1f8f-4350-566d-aebc-bd056217375f |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Program Files\Installer\Uninstall Installer.exe" /allusers /S | |||
| (PID) Process: | (2504) 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\f84a1f8f-4350-566d-aebc-bd056217375f |
| Operation: | write | Name: | DisplayVersion |
Value: 4.3.41 | |||
| (PID) Process: | (2504) 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\f84a1f8f-4350-566d-aebc-bd056217375f |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\Installer\Installer.exe,0 | |||
| (PID) Process: | (2504) 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\f84a1f8f-4350-566d-aebc-bd056217375f |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (2504) 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\f84a1f8f-4350-566d-aebc-bd056217375f |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
Executable files
50
Suspicious files
348
Text files
221
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2504 | 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | C:\Users\admin\AppData\Local\Temp\nslD1CA.tmp\app-64.7z | — | |
MD5:— | SHA256:— | |||
| 2504 | 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | C:\Users\admin\AppData\Local\Temp\nslD1CA.tmp\7z-out\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 2504 | 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | C:\Users\admin\AppData\Local\Temp\nslD1CA.tmp\7z-out\LICENSES.chromium.html | — | |
MD5:— | SHA256:— | |||
| 2504 | 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | C:\Users\admin\AppData\Local\Temp\nslD1CA.tmp\nsis7z.dll | executable | |
MD5:80E44CE4895304C6A3A831310FBF8CD0 | SHA256:B393F05E8FF919EF071181050E1873C9A776E1A0AE8329AEFFF7007D0CADF592 | |||
| 2504 | 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | C:\Users\admin\AppData\Local\Temp\nslD1CA.tmp\SpiderBanner.dll | executable | |
MD5:17309E33B596BA3A5693B4D3E85CF8D7 | SHA256:996A259E53CA18B89EC36D038C40148957C978C0FD600A268497D4C92F882A93 | |||
| 2504 | 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | C:\Users\admin\AppData\Local\Temp\nslD1CA.tmp\7z-out\locales\en-US.pak | binary | |
MD5:9B020E4AF087FECCBC7E243C4094F748 | SHA256:60674D51A66905415250B77168836B2FF7801CAD761C6E186B9831B3BE0CB494 | |||
| 2504 | 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | C:\Users\admin\AppData\Local\Temp\nslD1CA.tmp\7z-out\locales\da.pak | binary | |
MD5:84CBDF1AA0718F1D49D72C632EF4F549 | SHA256:FD63644EAB4E8096CB0DFAC3D861923E7042EF251E6F7DC06E524F22E96DFAF1 | |||
| 2504 | 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | C:\Users\admin\AppData\Local\Temp\nslD1CA.tmp\7z-out\locales\bn.pak | binary | |
MD5:3CA79BFE2A397C6C0A58D9B1D5FFF24E | SHA256:43A0C8BF652288C7A1EFAF19926D25275507FA03E9134CFE5E3A580E8E7CD203 | |||
| 2504 | 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | C:\Users\admin\AppData\Local\Temp\nslD1CA.tmp\7z-out\locales\af.pak | binary | |
MD5:B8F0228434EC80697F573A760A3B9B80 | SHA256:CCF99FA3CD12311291D7D960DEB77347F794217C9494E2A8CFB3338FCA47D91C | |||
| 2504 | 39cf49ea66350706cb9fb8927c24b20bcb175574248bc9fefdb6475628af47c4.exe | C:\Users\admin\AppData\Local\Temp\nslD1CA.tmp\7z-out\locales\el.pak | binary | |
MD5:F3088807630073FE407061702653A279 | SHA256:FF2CD1411E6E1321B0C4ED190CC77706311F28FFCD17B5CA001921752FCEE710 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
29
DNS requests
19
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.22.242.90:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.22.242.90:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1324 | SIHClient.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.22.242.90:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1324 | SIHClient.exe | GET | 200 | 23.200.189.225:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.22.242.90:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 2.22.242.90:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.22.242.90:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1324 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1324 | SIHClient.exe | 23.200.189.225:80 | www.microsoft.com | Moratelindo Internet Exchange Point | ID | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
trouveur.com |
| unknown |
challenges.cloudflare.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6676 | Installer.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
6676 | Installer.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
6676 | Installer.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
6676 | Installer.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
6676 | Installer.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
6676 | Installer.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |