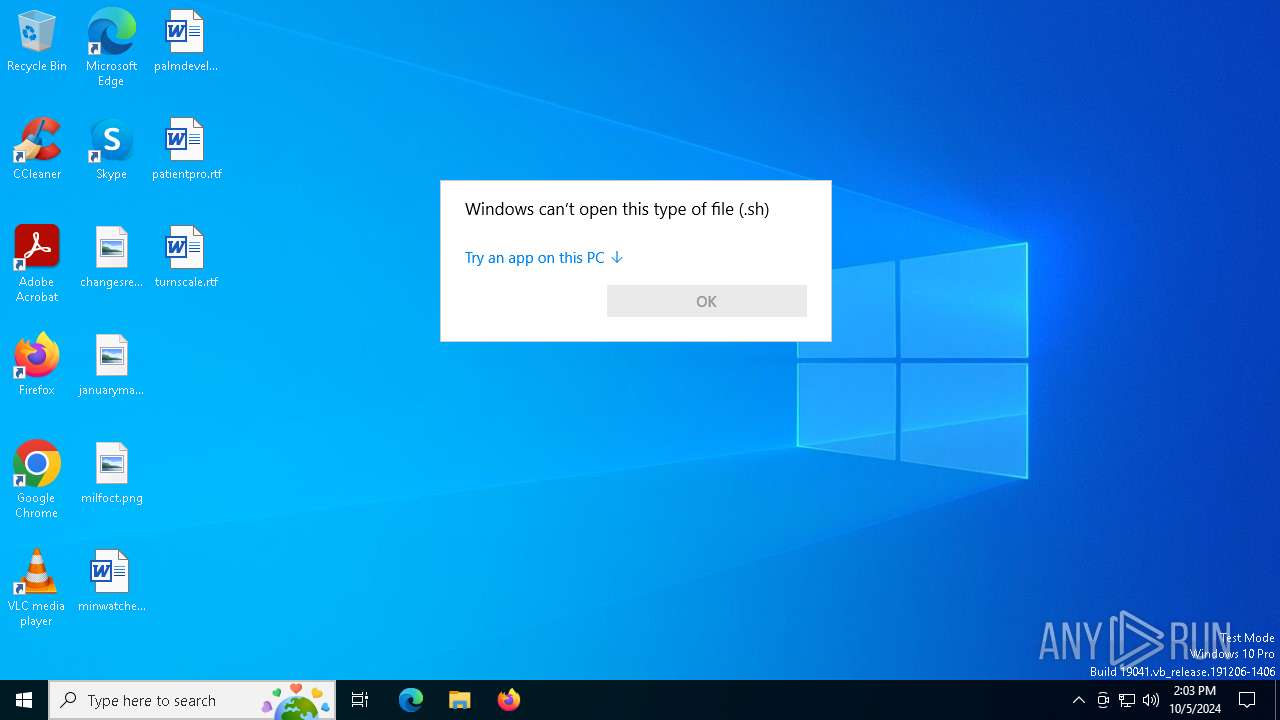
| File name: | pow.sh |
| Full analysis: | https://app.any.run/tasks/661ed1cf-2a1d-4f28-b7ad-f8588c9173bd |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2024, 14:03:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/x-shellscript |
| File info: | Bourne-Again shell script, ASCII text executable |
| MD5: | AA83A878C04F47299E461FA8ECD61F7A |
| SHA1: | 8A9BBA1DDEA5644D10514614FC260ED1A8836BD6 |
| SHA256: | 39C798E508F7A857DDD8746A1ABBE9C30672D5D2AF0D28B7E409E1F459F877A4 |
| SSDEEP: | 24:q0G9CrR5y66Tly/gDwUO+4/rQYHt71CMfnWzLGrNoAkX8nxq/sAyK:q0G9WZVIwUOXrrt7AMfWzO+AksnM/vj |
MALICIOUS
No malicious indicators.SUSPICIOUS
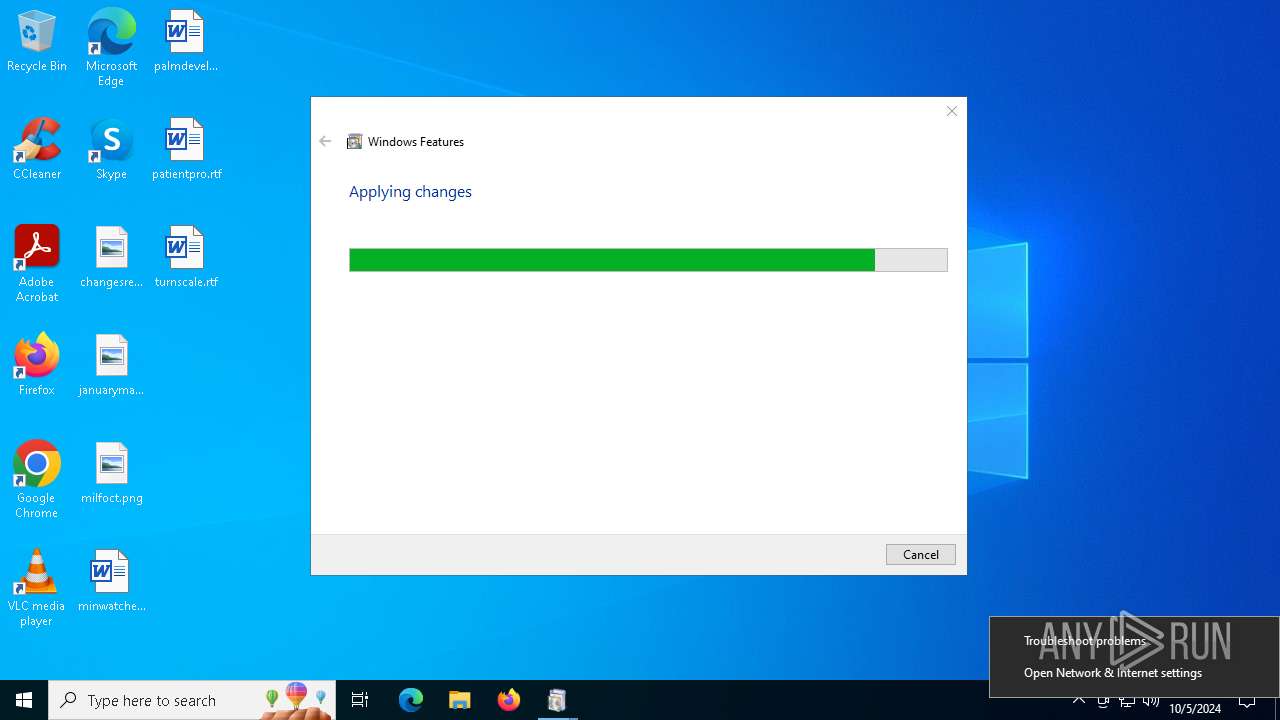
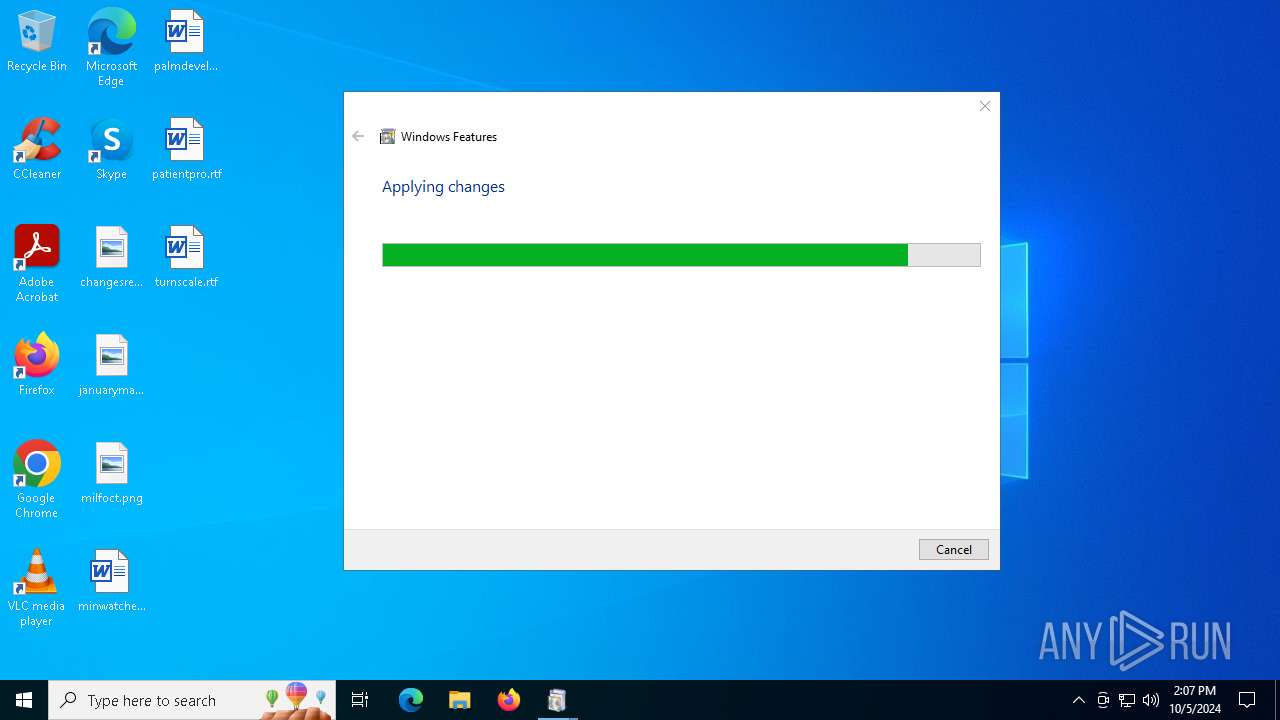
The process executes via Task Scheduler
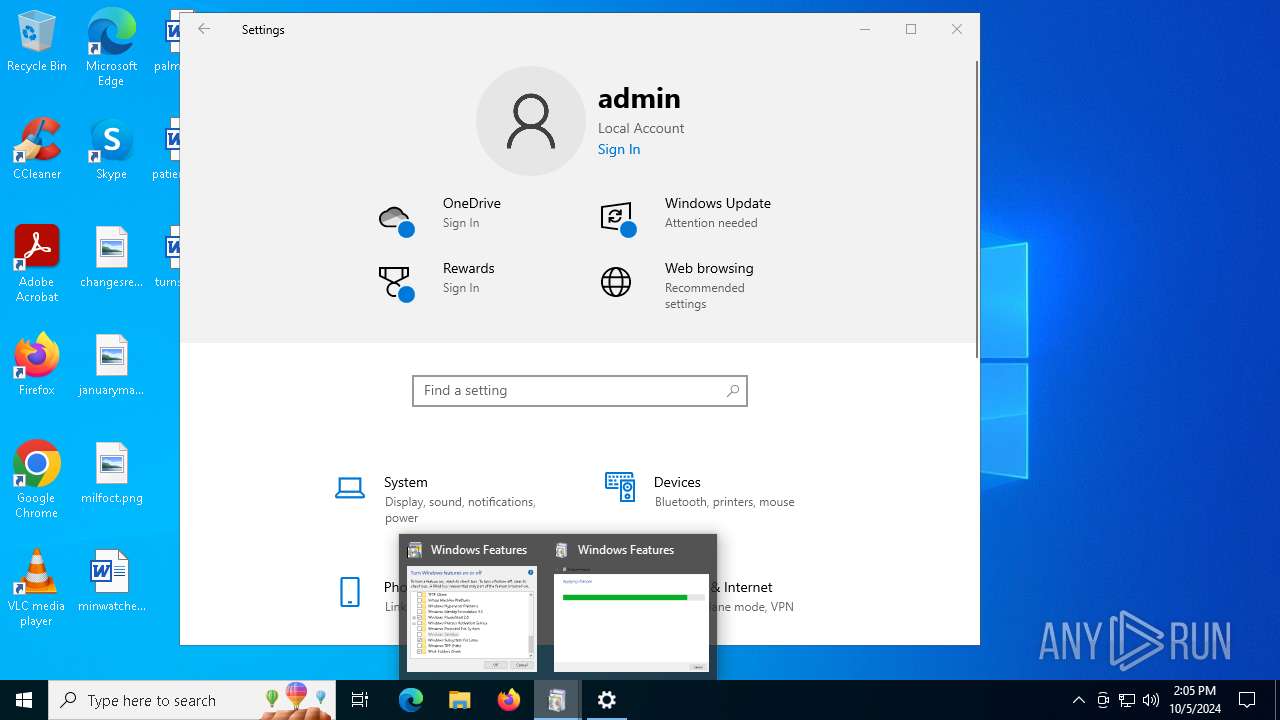
- OptionalFeatures.exe (PID: 3116)
Executes as Windows Service
- VSSVC.exe (PID: 2020)
Process drops legitimate windows executable
- TiWorker.exe (PID: 2448)
Executable content was dropped or overwritten
- TiWorker.exe (PID: 2448)
INFO
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 4108)
Manages system restore points
- SrTasks.exe (PID: 6000)
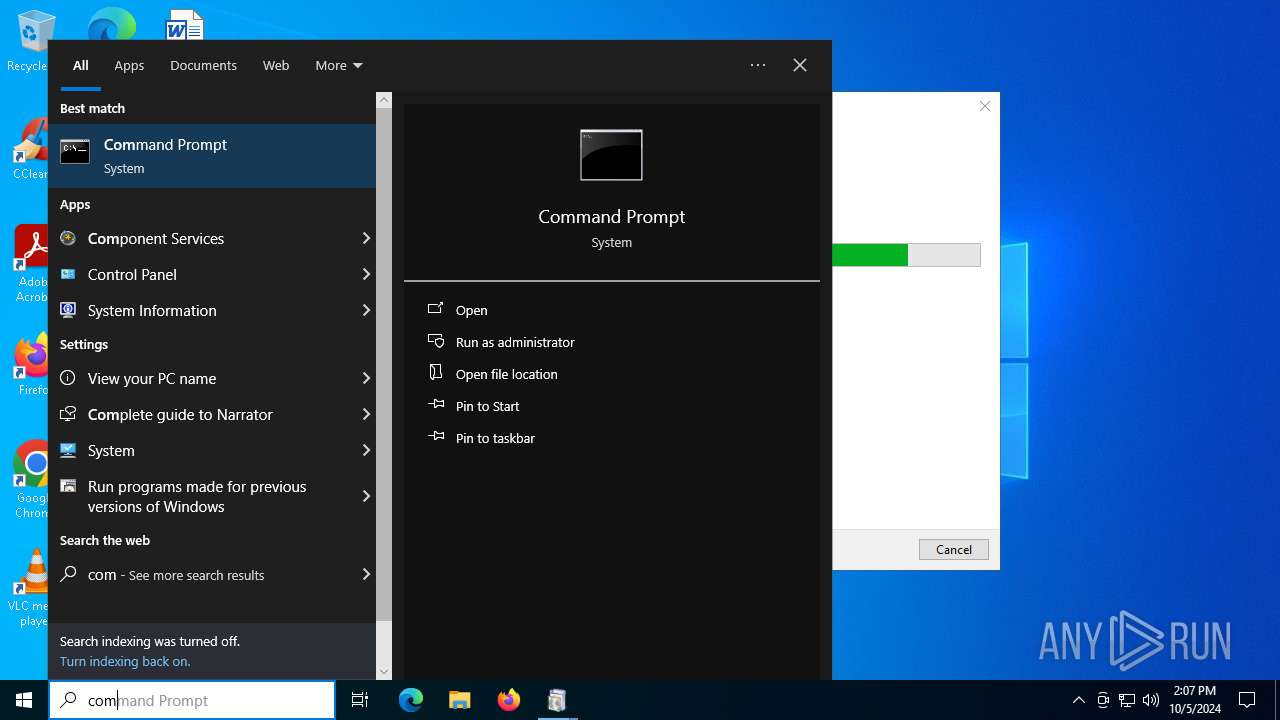
Manual execution by a user
- cmd.exe (PID: 2492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .sh | | | Linux/UNIX shell script (100) |
|---|
Total processes
228
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 240 | C:\WINDOWS\System32\poqexec.exe /noreboot /transaction 836 /display_progress \SystemRoot\WinSxS\pending.xml | C:\Windows\System32\poqexec.exe | — | TiWorker.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Primitive Operations Queue Executor Exit code: 3010 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2020 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2448 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Exit code: 0 Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2492 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3116 | "C:\WINDOWS\system32\OptionalFeatures.exe" | C:\Windows\System32\OptionalFeatures.exe | RuntimeBroker.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Features Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4108 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\AppData\Local\Temp\pow.sh | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6000 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | TiWorker.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6336 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
142 294
Read events
135 898
Write events
4 910
Delete events
1 486
Modification events
| (PID) Process: | (2448) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31135535 | |||
| (PID) Process: | (2448) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: | |||
| (PID) Process: | (2448) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS\ServicingStackVersions |
| Operation: | write | Name: | 10.0.19041.3989 (WinBuild.160101.0800) |
Value: 2024/10/5:14:4:6.295 10.0.19041.3989 (WinBuild.160101.0800) | |||
| (PID) Process: | (2448) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | PendingRequired |
Value: | |||
| (PID) Process: | (2448) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | PendingXmlIdentifier |
Value: | |||
| (PID) Process: | (2448) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | PoqexecFailure |
Value: | |||
| (PID) Process: | (2448) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | ExecutionState |
Value: | |||
| (PID) Process: | (2448) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | RepairTransactionPended |
Value: | |||
| (PID) Process: | (2448) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS\ServicingStackVersions |
| Operation: | write | Name: | 10.0.19041.3989 (WinBuild.160101.0800) |
Value: 2024/10/5:14:4:6.701 10.0.19041.3989 (WinBuild.160101.0800) | |||
| (PID) Process: | (2448) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS\ServicingStackVersions |
| Operation: | write | Name: | 10.0.19041.3989 (WinBuild.160101.0800) |
Value: 2024/10/5:14:4:6.716 10.0.19041.3989 (WinBuild.160101.0800) | |||
Executable files
9
Suspicious files
1 389
Text files
1 377
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2448 | TiWorker.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2448 | TiWorker.exe | C:\Windows\Logs\CBS\CBS.log | text | |
MD5:F46BCCC5FC53E8A5ABD9794C7B3D266B | SHA256:94DB17B87014B073C9F50889A65B42789A7A2D3CC263B0BBF7D7F8C4A4DB3C52 | |||
| 2448 | TiWorker.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{2bd6c2fa-c557-4da4-ab95-8d494e74bccf}_OnDiskSnapshotProp | binary | |
MD5:BF37C9805285ED63F583549AE48A7410 | SHA256:047D1FDF955F784171FC3931042ACA31B7FB1A265912922FEC27A6144A67D2F5 | |||
| 2448 | TiWorker.exe | C:\Windows\servicing\Sessions\31135535_1876358762.xml | xml | |
MD5:2CAF0CC077E56A45801C90900EEF565A | SHA256:DC8F01A35BF0B2E450AA9F68A95D64B6038446DCA28CF0784BEA9EF441E17985 | |||
| 2448 | TiWorker.exe | C:\Windows\WinSxS\Temp\InFlight\5e9e8e832f17db01460000009009f407\amd64_wvms_mp_windows.inf.resources_31bf3856ad364e35_10.0.19041.1_en-us_1110b3d7b2d135d7\wvms_mp_windows.inf_loc | text | |
MD5:62EC93D9FB005BFEB8500FDA1CD5BB33 | SHA256:2051A425C9D81F3ABCD459505BB9D65F2DA2B5158C68713FEA54FF8983982575 | |||
| 2448 | TiWorker.exe | C:\Windows\WinSxS\Temp\PendingDeletes\87ef90832f17db01470000009009f407.wvms_mp_windows.inf_loc | binary | |
MD5:1D9CB367711D070FD8D1CA5A80C0DC6D | SHA256:8041E112362109CC8E1FB6A0FFC988A069AEE87E0B7D0AAE4C14D0B62F378C01 | |||
| 2448 | TiWorker.exe | C:\Windows\WinSxS\Temp\InFlight\e2a7a1832f17db014c0000009009f407\amd64_microsoft-windows-nat-wmiv2provider_31bf3856ad364e35_10.0.19041.1_none_cf396423c0041ea1\NetNat.mof | text | |
MD5:3EBDEC06DEA8A546496AAE1759B3E05C | SHA256:954894878F75751371A4E808B5E66761A0EDFCC6B8FD7362C1B806515A4BF807 | |||
| 2448 | TiWorker.exe | C:\Windows\WinSxS\Temp\InFlight\0f9aad832f17db01520000009009f407\amd64_microsoft-windows-n..2provider.resources_31bf3856ad364e35_10.0.19041.1_en-us_c73624799425a0dc\NetNat.dll.mui | executable | |
MD5:A052415CA833EAB2CE877AE20FC9EA35 | SHA256:3980D86A2D91AFF666BC9AAFD2725786FA722A1151AD78979D66D84379FD061E | |||
| 2448 | TiWorker.exe | C:\Windows\WinSxS\amd64_microsoft-windows-nat-wmiv2provider_31bf3856ad364e35_10.0.19041.1_none_cf396423c0041ea1\NetNat.dll | executable | |
MD5:E4478669DE0BF9E46590A551913196B3 | SHA256:F069C670F676838D728A57EB2376DE40C1F224B83A120A93283C45D4A05D8E2D | |||
| 2448 | TiWorker.exe | C:\Windows\WinSxS\Temp\PendingDeletes\f90aa4832f17db014e0000009009f407.NetNat.mof | binary | |
MD5:3D984D69C604E4D18E99089055117D13 | SHA256:5C6D0F2E645B8DEF1DCD12C2F6081030C8EE473B8DB1E0FA590C45B595381B94 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
53
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
8 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1028 | SystemSettings.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1028 | SystemSettings.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2968 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
8 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
8 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4324 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 20.42.65.85:443 | browser.pipe.aria.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5336 | SearchApp.exe | 2.23.172.122:443 | www.bing.com | Akamai International B.V. | DK | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
r.bing.com |
| whitelisted |
cxcs.microsoft.net |
| whitelisted |
go.microsoft.com |
| whitelisted |