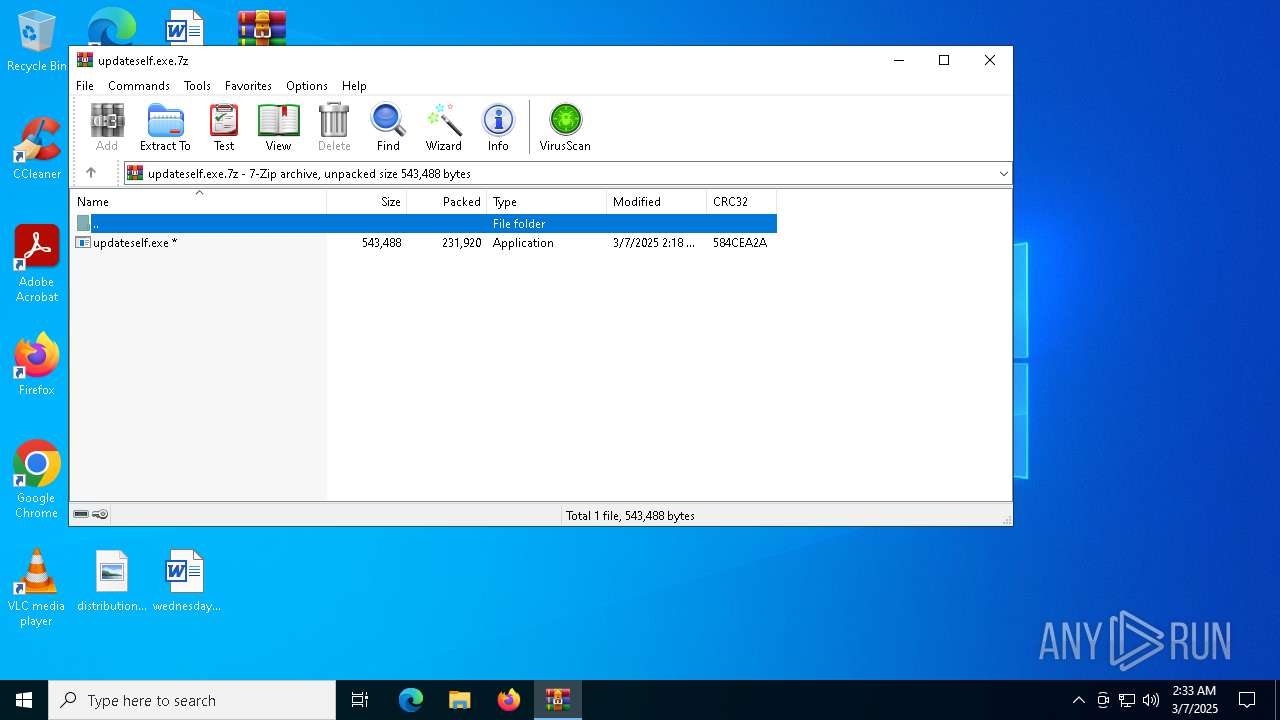
| File name: | updateself.exe.7z |
| Full analysis: | https://app.any.run/tasks/c517c827-ae89-49c8-b86f-695ea28658c3 |
| Verdict: | Malicious activity |
| Analysis date: | March 07, 2025, 02:33:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 7034C7D2A0CEA329109D9EB92C117063 |
| SHA1: | 8C990E06A7A72366D9782B10BE1B86E9A8F0D3AA |
| SHA256: | 399CD01660BF7252DF305DE39F3E6BFA1A524DD9F5AB69CEAA475D3CCE255A0F |
| SSDEEP: | 6144:WmZdkekhD46Vf5nwYSEMfjFysnG0zkwpb1uNYGABjm:Wmpk+6h4EMhzG0zZb12YGABj |
MALICIOUS
Generic archive extractor
- svchost.exe (PID: 456)
Executing a file with an untrusted certificate
- updateself.exe (PID: 2560)
- updateself.exe (PID: 5048)
- updateself.exe (PID: 1168)
SUSPICIOUS
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 7740)
INFO
Reads the software policy settings
- WaaSMedicAgent.exe (PID: 7596)
- BackgroundTransferHost.exe (PID: 3900)
- SIHClient.exe (PID: 7992)
- slui.exe (PID: 7460)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 3900)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 8088)
- BackgroundTransferHost.exe (PID: 3900)
- BackgroundTransferHost.exe (PID: 5508)
- BackgroundTransferHost.exe (PID: 7368)
- BackgroundTransferHost.exe (PID: 6392)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 3900)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 456)
Manual execution by a user
- updateself.exe (PID: 2560)
- updateself.exe (PID: 5048)
- updateself.exe (PID: 1168)
Checks supported languages
- updateself.exe (PID: 2560)
- updateself.exe (PID: 5048)
- ShellExperienceHost.exe (PID: 7740)
- updateself.exe (PID: 1168)
Reads the computer name
- ShellExperienceHost.exe (PID: 7740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2025:03:07 02:18:25+00:00 |
| ArchivedFileName: | updateself.exe |
Total processes
151
Monitored processes
28
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s wuauserv | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 456 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\updateself.exe.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 900 | C:\WINDOWS\System32\Upfc.exe /launchtype periodic /cv 7ZkqF8tB60mXyE10dPpInw.0 | C:\Windows\System32\upfc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Updateability From SCM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | "C:\Users\admin\Desktop\updateself.exe\updateself.exe" | C:\Users\admin\Desktop\updateself.exe\updateself.exe | — | explorer.exe | |||||||||||
User: admin Company: Zhuhai Kingsoft Office Software Co.,Ltd Integrity Level: MEDIUM Description: WPS Office Expansion tool Exit code: 1 Version: 10,2,0,5820 Modules
| |||||||||||||||
| 2104 | C:\WINDOWS\system32\svchost.exe -k wusvcs -p -s WaaSMedicSvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2560 | "C:\Users\admin\Desktop\updateself.exe\updateself.exe" | C:\Users\admin\Desktop\updateself.exe\updateself.exe | — | explorer.exe | |||||||||||
User: admin Company: Zhuhai Kingsoft Office Software Co.,Ltd Integrity Level: MEDIUM Description: WPS Office Expansion tool Exit code: 1 Version: 10,2,0,5820 Modules
| |||||||||||||||
| 2892 | C:\WINDOWS\system32\svchost.exe -k wsappx -p -s AppXSvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 3332 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3868 | C:\WINDOWS\System32\svchost.exe -k wsappx -p -s ClipSVC | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 3900 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 395
Read events
17 217
Write events
164
Delete events
14
Modification events
| (PID) Process: | (2104) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\WaaS\WaaSMedic\TaskStore |
| Operation: | write | Name: | Schedule Wake To Work |
Value: Microsoft\Windows\UpdateOrchestrator | |||
| (PID) Process: | (2104) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\WaaS\WaaSMedic\TaskStore |
| Operation: | write | Name: | Schedule Maintenance Work |
Value: Microsoft\Windows\UpdateOrchestrator | |||
| (PID) Process: | (456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\updateself.exe.7z | |||
| (PID) Process: | (456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
32
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3900 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\10289a37-91bb-478a-b45b-93665aa34b55.down_data | — | |
MD5:— | SHA256:— | |||
| 4944 | sppsvc.exe | C:\Windows\System32\spp\store\2.0\data.dat | binary | |
MD5:1307D5C01ECFFF5EC5B2E77A65D28E22 | SHA256:6D009B12779FAE1C0EDC575418A51BBFB6EB91E51A69A935558513728F12894D | |||
| 3900 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:38989CDC9B939CBF439472EC8FEBE5D7 | SHA256:0188CCDAB61284075618619F99DBB9FC9BA066DF5B1FF02EC5684476CABA0732 | |||
| 2104 | svchost.exe | C:\Windows\Logs\waasmediccapsule\WaasRemediation.002.etl | binary | |
MD5:D5C3C6FF92AB9DC318CD2CEA16B05D13 | SHA256:AD2AC123C272119801B396032898A17A9C6E0ADF6DE2DE218794E31723136DD2 | |||
| 2104 | svchost.exe | C:\Windows\Logs\waasmediccapsule\WaasRemediation.004.etl | binary | |
MD5:A83C439448C1E67E6FFC948FEF1FCE18 | SHA256:9FAA75F166CFDD869D3549B76139DDDDDB6A50790A5C6CC81B2084A432D7D60F | |||
| 4944 | sppsvc.exe | C:\Windows\System32\spp\store\2.0\data.dat.tmp | binary | |
MD5:1307D5C01ECFFF5EC5B2E77A65D28E22 | SHA256:6D009B12779FAE1C0EDC575418A51BBFB6EB91E51A69A935558513728F12894D | |||
| 2104 | svchost.exe | C:\Windows\Logs\waasmediccapsule\WaasRemediation.003.etl | binary | |
MD5:DEDECFD6DDECAA969F2F735761A8363F | SHA256:6D554FD45C5A4651BA508028AF27C5AE6501E3A2E10CFF9A8A925DCB74A68702 | |||
| 7992 | SIHClient.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\51867C3735CFAECCDB556E146BB12C28 | binary | |
MD5:68869FAC2AED8314424C87BB2390D3DB | SHA256:7A309E19D9B3A123A0110AB6B7CC6D9C407EABBEE34207031F33825712FD493B | |||
| 7992 | SIHClient.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9E94643DE99F5621BC288D045BEA85DD | binary | |
MD5:B69C738C71C947FD12B66D6319DF84A5 | SHA256:5582F1CB870F1C1801E659399C2295CB131E180893A6E54FC992B0DCD2FB88A2 | |||
| 3900 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\10289a37-91bb-478a-b45b-93665aa34b55.c96c1b18-a51d-403e-9788-21800c9677a2.down_meta | binary | |
MD5:C3B97A341D6F7742453B70F9691C9A98 | SHA256:02BEEFD3C475D17A1271DDA91DDA507B36C74C41B1507CA81B0573F3342F17C6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
26
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7284 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7992 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3900 | BackgroundTransferHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7992 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2432 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7284 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7284 | backgroundTaskHost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |