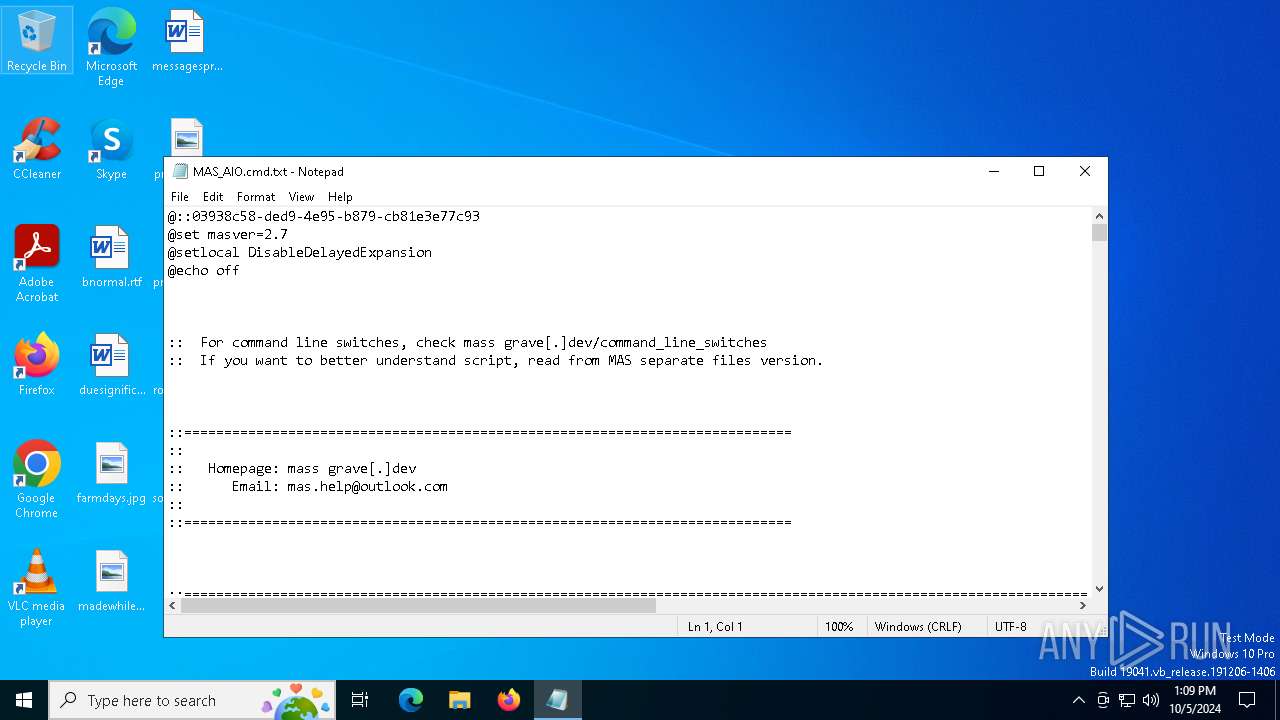
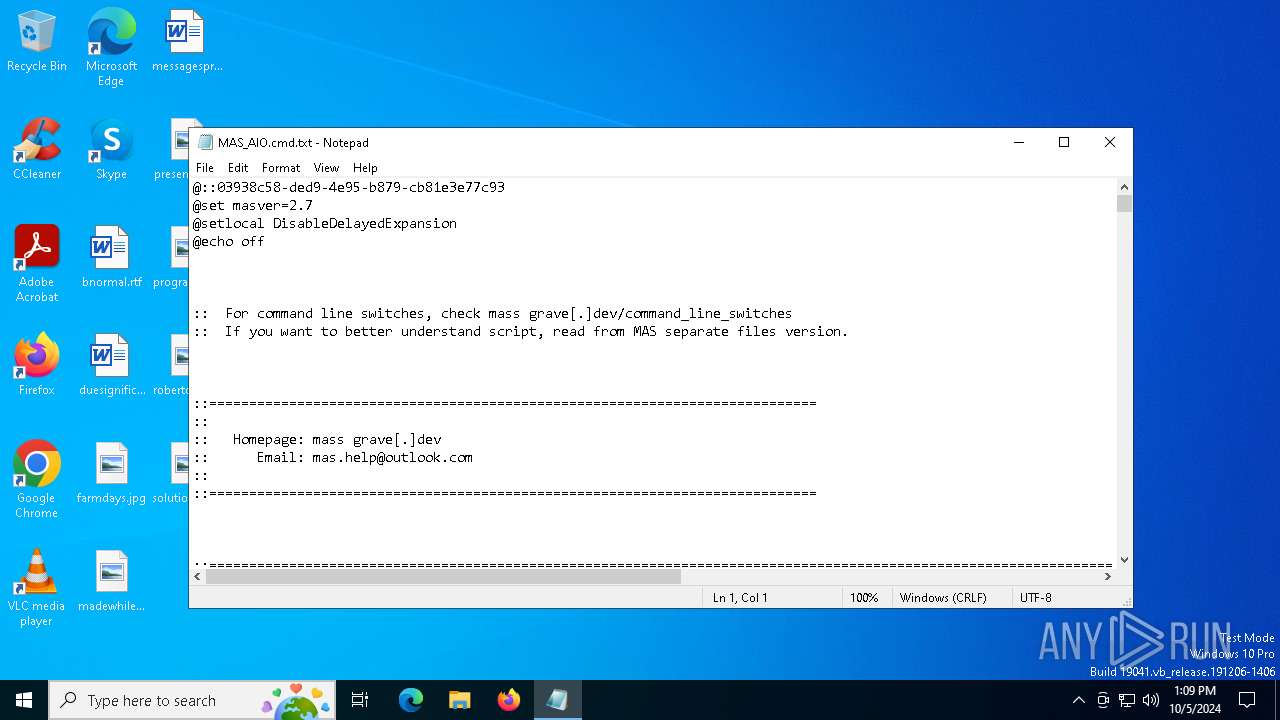
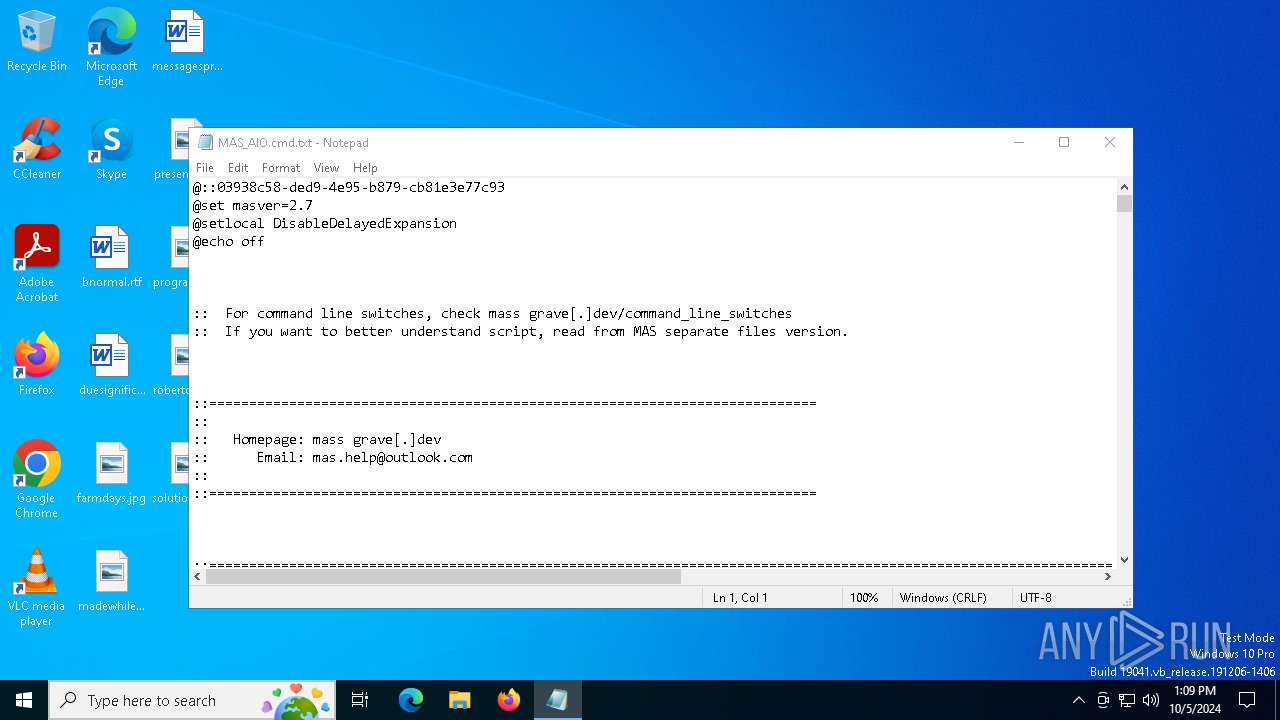
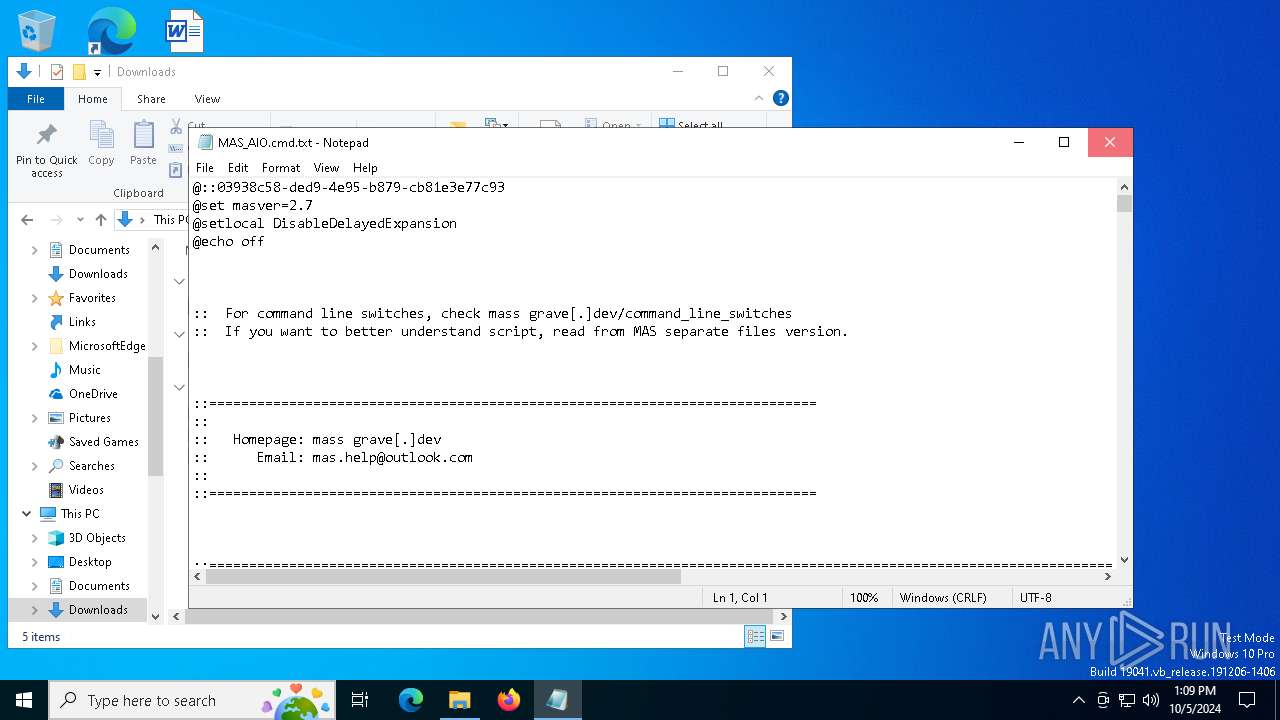
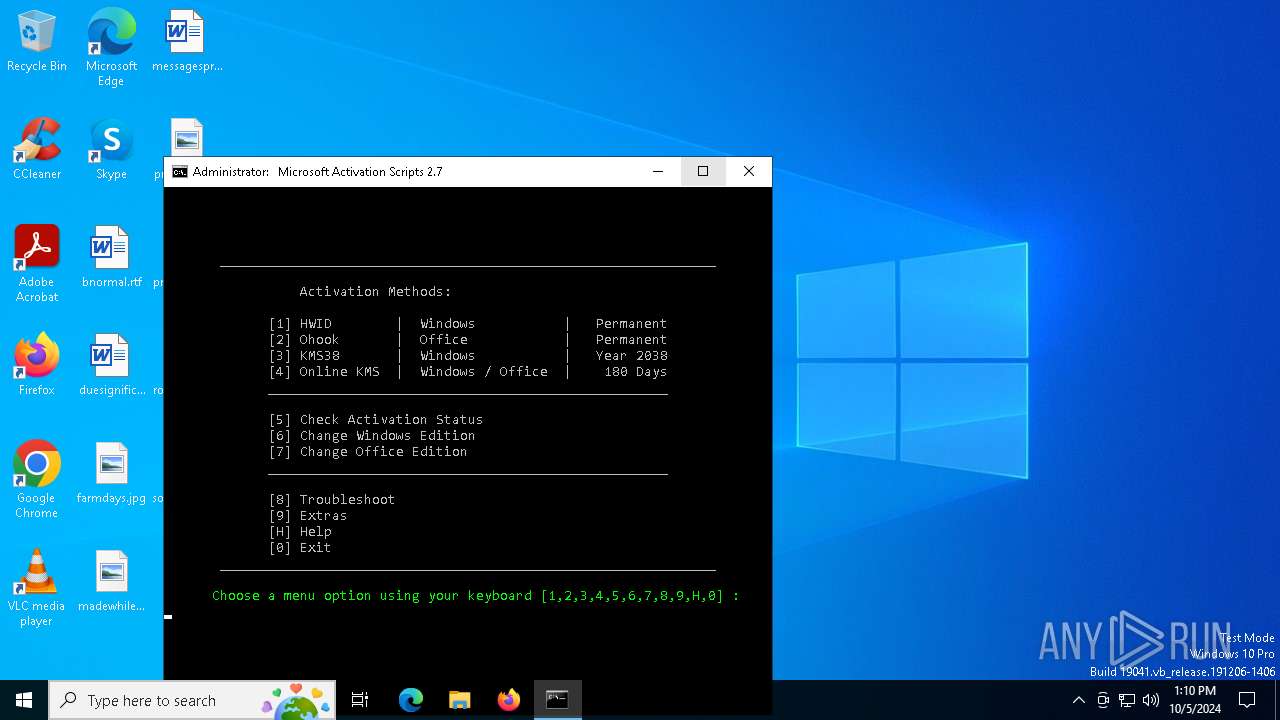
| File name: | MAS_AIO.cmd |
| Full analysis: | https://app.any.run/tasks/93116fdf-be25-42b7-b839-19cbfd21bec5 |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2024, 13:09:41 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (376), with CRLF line terminators |
| MD5: | AA378FAB3084F1BBB2BB73F96ACFDB08 |
| SHA1: | 8DF42A8E5E50763B55A1C79D2F48F81FB4642C08 |
| SHA256: | 39961D29B07D59D54A709AA7B152269ADC6349752660A0C66D627B09DF18B9B6 |
| SSDEEP: | 3072:2IpRnkRVRfRWhFdR9RYI29BKRDA5RFowgJmBMZgnnwBRdDR9RpRDCj4lRaR8Z17n:ViIAkiow6C5ozDTsPBUmU0yknEWuD |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts SC.EXE for service management
- cmd.exe (PID: 6912)
- cmd.exe (PID: 5556)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6912)
- cmd.exe (PID: 5556)
Application launched itself
- cmd.exe (PID: 6912)
- cmd.exe (PID: 5732)
- cmd.exe (PID: 5556)
- cmd.exe (PID: 5280)
- powershell.exe (PID: 6360)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6912)
- cmd.exe (PID: 5732)
- powershell.exe (PID: 6688)
- cmd.exe (PID: 5556)
- cmd.exe (PID: 5280)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 7080)
- cmd.exe (PID: 4596)
- cmd.exe (PID: 4524)
- cmd.exe (PID: 5556)
Executing commands from ".cmd" file
- cmd.exe (PID: 6912)
- powershell.exe (PID: 6688)
- cmd.exe (PID: 5556)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 7080)
- cmd.exe (PID: 4596)
- cmd.exe (PID: 5556)
- cmd.exe (PID: 4524)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7080)
- cmd.exe (PID: 6912)
- cmd.exe (PID: 2816)
- cmd.exe (PID: 5556)
- cmd.exe (PID: 4596)
- cmd.exe (PID: 6712)
- powershell.exe (PID: 6360)
- cmd.exe (PID: 4524)
- cmd.exe (PID: 1184)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 2616)
- cmd.exe (PID: 5556)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5556)
Hides command output
- cmd.exe (PID: 4056)
- cmd.exe (PID: 6032)
- cmd.exe (PID: 3116)
- cmd.exe (PID: 4524)
- cmd.exe (PID: 2488)
- cmd.exe (PID: 1684)
- cmd.exe (PID: 4692)
- cmd.exe (PID: 6712)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 4056)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 5556)
- cmd.exe (PID: 4692)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 6360)
The process hides Powershell's copyright startup banner
- powershell.exe (PID: 6360)
INFO
Reads security settings of Internet Explorer
- notepad.exe (PID: 6568)
Manual execution by a user
- cmd.exe (PID: 6912)
Checks operating system version
- cmd.exe (PID: 6912)
- cmd.exe (PID: 5556)
Starts MODE.COM to configure console settings
- mode.com (PID: 532)
- mode.com (PID: 1972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .bib/bibtex/txt | | | BibTeX references (100) |
|---|
Total processes
373
Monitored processes
241
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | cmd | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8 | reg query HKLM\SYSTEM\CurrentControlSet\Services\wuauserv /v ObjectName | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 240 | find /i "C:\Users\admin\AppData\Local\Temp" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | C:\WINDOWS\System32\cmd.exe /c ping -4 -n 1 updatecheck.massgrave.dev | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | reg query HKLM\SYSTEM\CurrentControlSet\Services\wlidsvc /v ObjectName | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 532 | mode 76, 33 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 532 | find /i "avira.com" C:\WINDOWS\System32\drivers\etc\hosts | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 532 | reg query HKLM\SYSTEM\CurrentControlSet\Services\sppsvc /v ImagePath | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 532 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "0" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | sc query ClipSVC | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
86 575
Read events
86 571
Write events
4
Delete events
0
Modification events
| (PID) Process: | (6568) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosX |
Value: 181 | |||
| (PID) Process: | (6568) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosY |
Value: 127 | |||
| (PID) Process: | (6568) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDX |
Value: 960 | |||
| (PID) Process: | (6568) notepad.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDY |
Value: 489 | |||
Executable files
0
Suspicious files
3
Text files
30
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6100 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:2716EFB49C44DD614CC36FD39E765C9E | SHA256:9E0C59E69A6965BC1F6D125CB4193071D821F39A1FBFBC437BEC2A92CE6F14D2 | |||
| 2032 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ykgjm5zy.nsx.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6776 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xtmulpi0.akj.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2032 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1lzso30x.mqd.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6688 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_g4xurq3v.gc5.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6688 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_dw0g5dec.pcw.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6100 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xj2nq2rx.5gm.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6776 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_t1eutu4r.fdy.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6100 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_skgbjd3i.gpa.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3160 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1klpsecy.suf.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
43
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4004 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6556 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6556 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6744 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3916 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4324 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3916 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4004 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4004 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |