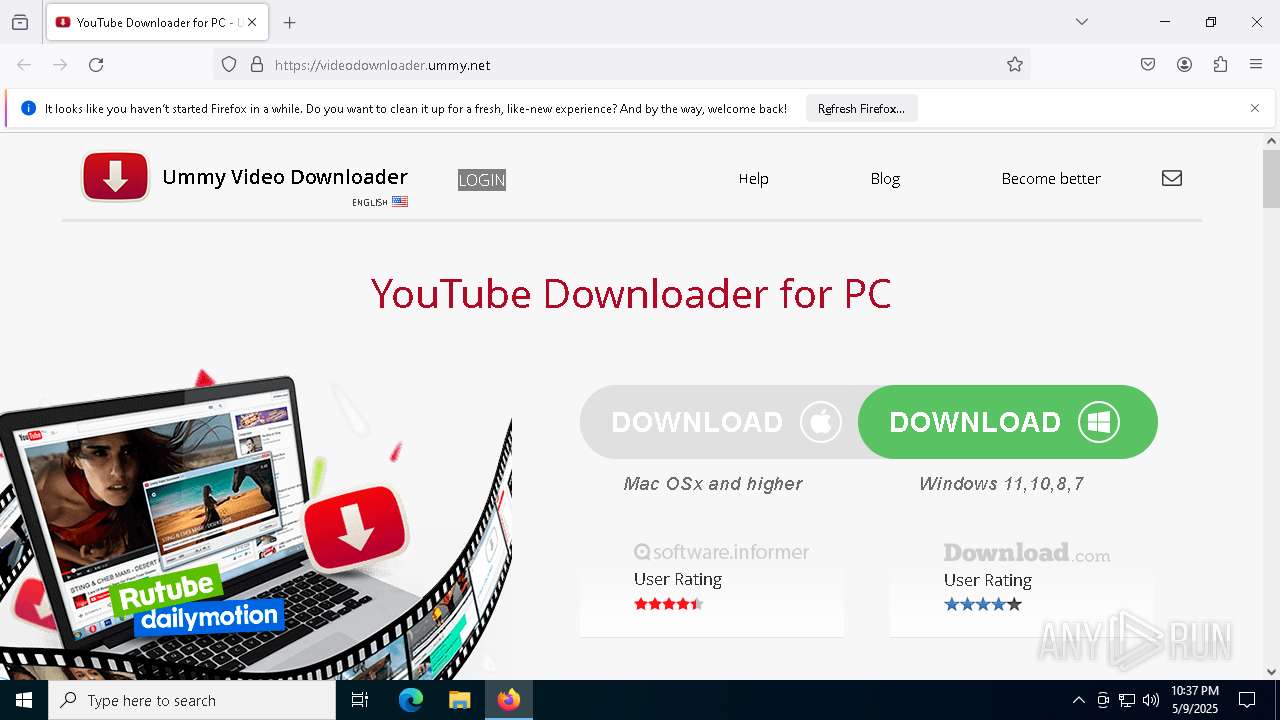
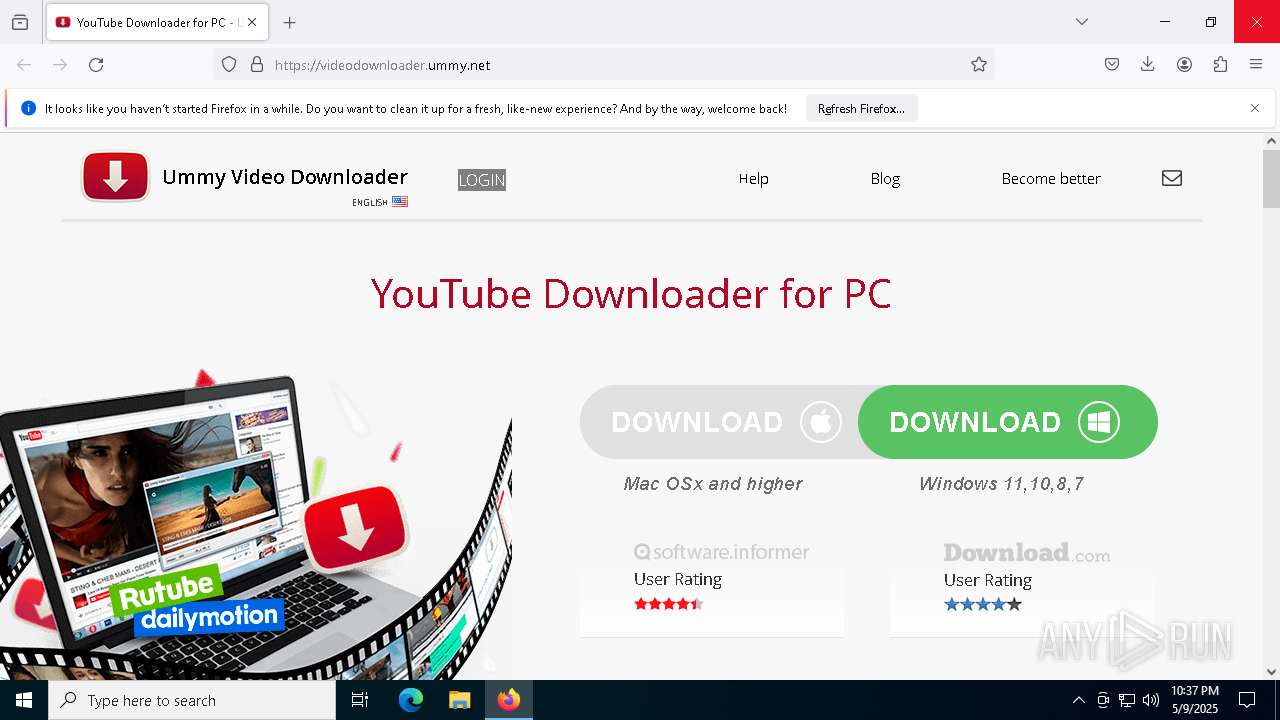
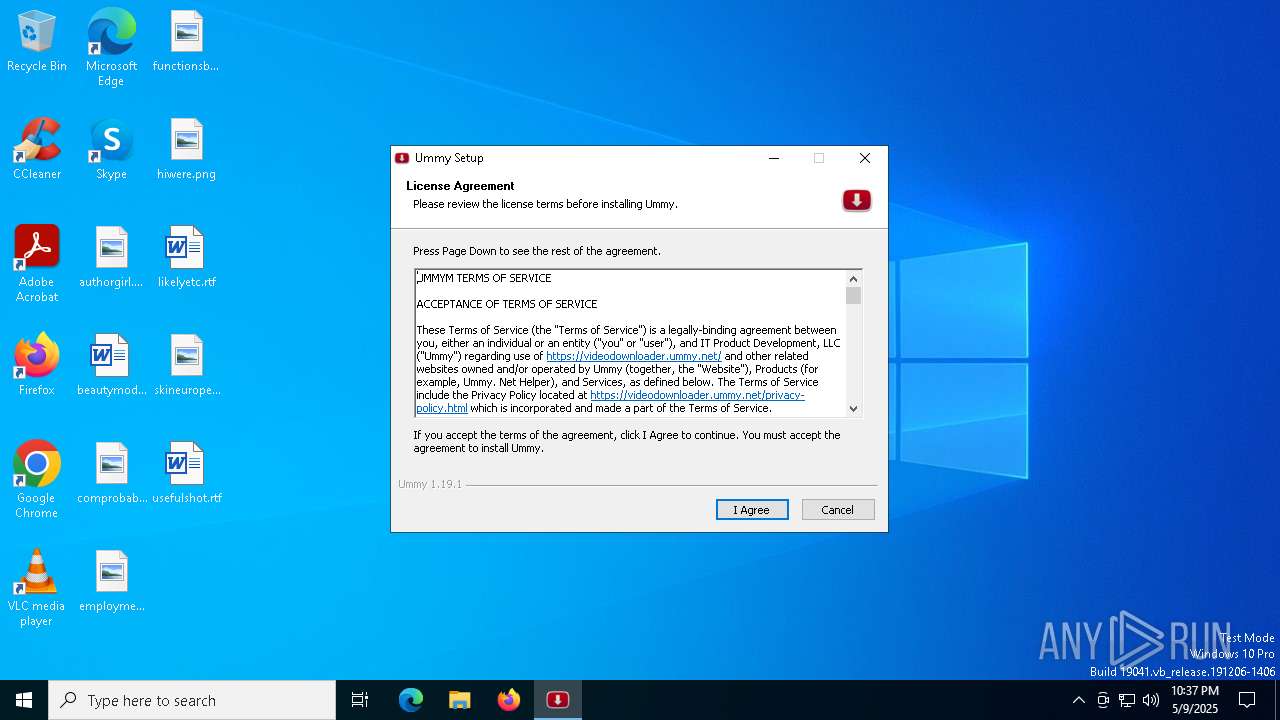
| URL: | https://videodownloader.ummy.net/ |
| Full analysis: | https://app.any.run/tasks/39327c94-2f17-4713-93a0-d158abf029d2 |
| Verdict: | Malicious activity |
| Analysis date: | May 09, 2025, 22:37:20 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 5AC3FA11FCB621B35A9489C7FF4CA7D7 |
| SHA1: | EE51DC7F7648A9041B0A164E52EB46BC8493137F |
| SHA256: | 39682190BF08AD53A3C5564581D4C10FA0F1B770C2A9EDC5250243E57971BC8E |
| SSDEEP: | 3:N8OABEKdXkKz:2ZSA |
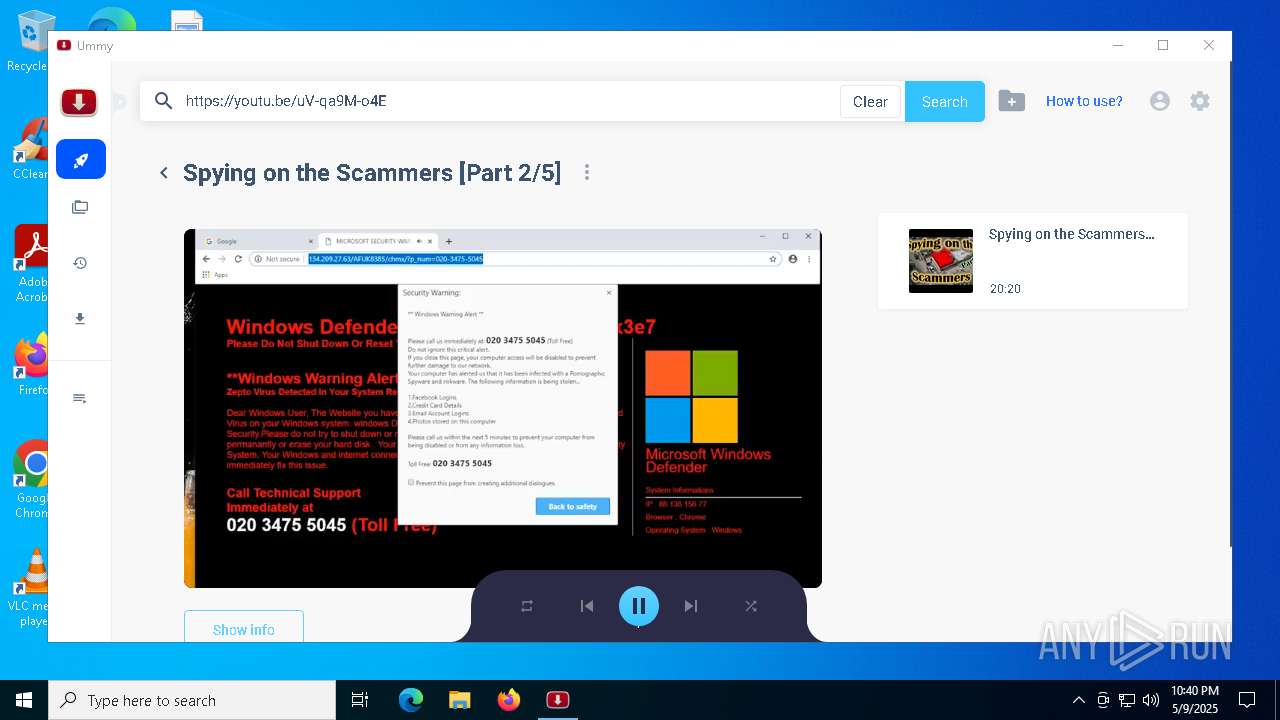
MALICIOUS
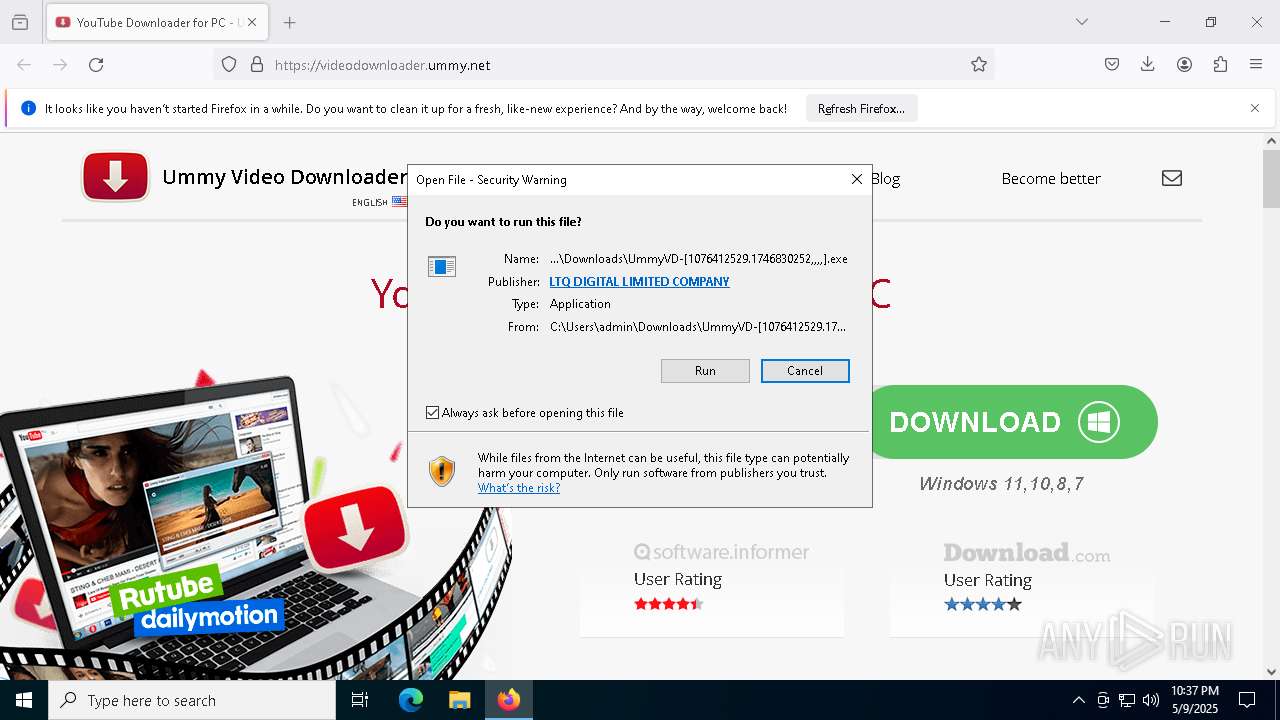
Executing a file with an untrusted certificate
- Setup.exe (PID: 7452)
SUSPICIOUS
Starts application with an unusual extension
- cmd.exe (PID: 8500)
Reads security settings of Internet Explorer
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
- Setup.exe (PID: 7452)
Get information on the list of running processes
- cmd.exe (PID: 8676)
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
The process creates files with name similar to system file names
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
There is functionality for taking screenshot (YARA)
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
- Ummy.exe (PID: 7860)
Starts a Microsoft application from unusual location
- vcredist_x86.exe (PID: 8224)
- vcredist_x86.exe (PID: 7448)
Drops 7-zip archiver for unpacking
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
Creates a software uninstall entry
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
Process drops legitimate windows executable
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
- vcredist_x86.exe (PID: 7448)
- msiexec.exe (PID: 3884)
- yt-dlp.exe (PID: 1276)
- yt-dlp.exe (PID: 7760)
Executable content was dropped or overwritten
- vcredist_x86.exe (PID: 7448)
- yt-dlp.exe (PID: 1276)
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
- yt-dlp.exe (PID: 7760)
- Ummy.exe (PID: 1328)
The process drops C-runtime libraries
- vcredist_x86.exe (PID: 7448)
- msiexec.exe (PID: 3884)
- yt-dlp.exe (PID: 1276)
- yt-dlp.exe (PID: 7760)
Creates file in the systems drive root
- vcredist_x86.exe (PID: 7448)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3884)
Starts CMD.EXE for commands execution
- Ummy.exe (PID: 1328)
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
- yt-dlp.exe (PID: 904)
- yt-dlp.exe (PID: 7564)
Application launched itself
- Ummy.exe (PID: 1328)
- yt-dlp.exe (PID: 1276)
- yt-dlp.exe (PID: 7760)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7660)
- cmd.exe (PID: 2152)
- cmd.exe (PID: 6112)
Process drops python dynamic module
- yt-dlp.exe (PID: 1276)
- yt-dlp.exe (PID: 7760)
Malware-specific behavior (creating "System.dll" in Temp)
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
INFO
Application launched itself
- firefox.exe (PID: 7428)
- firefox.exe (PID: 7384)
Reads the computer name
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
- vcredist_x86.exe (PID: 7448)
- Setup.exe (PID: 7452)
- msiexec.exe (PID: 3884)
- Ummy.exe (PID: 1328)
- Ummy.exe (PID: 7860)
- Ummy.exe (PID: 2392)
Checks supported languages
- more.com (PID: 8552)
- vcredist_x86.exe (PID: 7448)
- Setup.exe (PID: 7452)
- msiexec.exe (PID: 3884)
- Ummy.exe (PID: 1328)
- Ummy.exe (PID: 7860)
- Ummy.exe (PID: 2392)
- Ummy.exe (PID: 7352)
- Ummy.exe (PID: 8612)
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
Creates files or folders in the user directory
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
- msiexec.exe (PID: 3884)
- Ummy.exe (PID: 1328)
- Ummy.exe (PID: 2392)
Checks proxy server information
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
- Ummy.exe (PID: 1328)
Reads the machine GUID from the registry
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
- vcredist_x86.exe (PID: 7448)
- Setup.exe (PID: 7452)
- msiexec.exe (PID: 3884)
- Ummy.exe (PID: 1328)
Reads the software policy settings
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
- slui.exe (PID: 7000)
- Setup.exe (PID: 7452)
- msiexec.exe (PID: 3884)
Executable content was dropped or overwritten
- firefox.exe (PID: 7428)
- msiexec.exe (PID: 3884)
Process checks computer location settings
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
- Ummy.exe (PID: 1328)
- Ummy.exe (PID: 7352)
- Ummy.exe (PID: 8612)
The sample compiled with russian language support
- vcredist_x86.exe (PID: 7448)
- msiexec.exe (PID: 3884)
The sample compiled with spanish language support
- vcredist_x86.exe (PID: 7448)
- msiexec.exe (PID: 3884)
The sample compiled with english language support
- vcredist_x86.exe (PID: 7448)
- msiexec.exe (PID: 3884)
- yt-dlp.exe (PID: 1276)
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
- yt-dlp.exe (PID: 7760)
The sample compiled with korean language support
- vcredist_x86.exe (PID: 7448)
- msiexec.exe (PID: 3884)
The sample compiled with japanese language support
- vcredist_x86.exe (PID: 7448)
- msiexec.exe (PID: 3884)
The sample compiled with Italian language support
- vcredist_x86.exe (PID: 7448)
- msiexec.exe (PID: 3884)
The sample compiled with chinese language support
- vcredist_x86.exe (PID: 7448)
- msiexec.exe (PID: 3884)
The sample compiled with french language support
- vcredist_x86.exe (PID: 7448)
- msiexec.exe (PID: 3884)
The sample compiled with german language support
- vcredist_x86.exe (PID: 7448)
- msiexec.exe (PID: 3884)
Reads CPU info
- Setup.exe (PID: 7452)
Create files in a temporary directory
- Setup.exe (PID: 7452)
- Ummy.exe (PID: 1328)
- UmmyVD-[1076412529.1746830252,,,,].exe (PID: 8468)
Creates a software uninstall entry
- msiexec.exe (PID: 3884)
Manual execution by a user
- Ummy.exe (PID: 1328)
Node.js compiler has been detected
- Ummy.exe (PID: 1328)
- Ummy.exe (PID: 7860)
- Ummy.exe (PID: 2392)
Checks operating system version
- yt-dlp.exe (PID: 904)
- yt-dlp.exe (PID: 7564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
214
Monitored processes
76
Malicious processes
5
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 812 | C:\WINDOWS\system32\reg.exe QUERY "HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.mp4\UserChoice" /v ProgId | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | C:\Users\admin\AppData\Local\ummy\resources\bin_ia32\yt-dlp.exe --no-check-certificates --no-playlist -j -s --cookies "C:\Users\admin\AppData\Roaming\Ummy Desktop\cookies.txt" https://www.youtube.com/watch?v=uV-qa9M-o4E | C:\Users\admin\AppData\Local\ummy\resources\bin_ia32\yt-dlp.exe | yt-dlp.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1012 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | C:\WINDOWS\system32\reg.exe ADD "HKCU\Software\Classes\ummy" /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1276 | C:\Users\admin\AppData\Local\ummy\resources\bin_ia32\yt-dlp.exe --no-check-certificates --no-playlist -j -s --cookies "C:\Users\admin\AppData\Roaming\Ummy Desktop\cookies.txt" https://www.youtube.com/watch?v=uV-qa9M-o4E | C:\Users\admin\AppData\Local\ummy\resources\bin_ia32\yt-dlp.exe | Ummy.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1300 | C:\WINDOWS\explorer.exe /factory,{5BD95610-9434-43C2-886C-57852CC8A120} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | "C:\Users\admin\AppData\Local\ummy\Ummy.exe" | C:\Users\admin\AppData\Local\ummy\Ummy.exe | explorer.exe | ||||||||||||
User: admin Company: LTQ DIGITAL LIMITED COMPANY Integrity Level: MEDIUM Description: Ummy Desktop Version: 1.19.1 Modules
| |||||||||||||||
| 1628 | C:\WINDOWS\system32\reg.exe ADD "HKCU\Software\Classes\ummy\shell\open\command" /ve /t REG_SZ /d "C:\Users\admin\AppData\Local\ummy\Ummy.exe" "%1" /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1672 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
35 765
Read events
35 092
Write events
628
Delete events
45
Modification events
| (PID) Process: | (7428) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (7428) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (8468) UmmyVD-[1076412529.1746830252,,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\589bbc75-bab8-5041-bad3-2b463b503e06 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Local\ummy | |||
| (PID) Process: | (8468) UmmyVD-[1076412529.1746830252,,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (8468) UmmyVD-[1076412529.1746830252,,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (8468) UmmyVD-[1076412529.1746830252,,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (8468) UmmyVD-[1076412529.1746830252,,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\589bbc75-bab8-5041-bad3-2b463b503e06 |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
| (PID) Process: | (8468) UmmyVD-[1076412529.1746830252,,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\589bbc75-bab8-5041-bad3-2b463b503e06 |
| Operation: | write | Name: | KeepShortcuts |
Value: true | |||
| (PID) Process: | (8468) UmmyVD-[1076412529.1746830252,,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\589bbc75-bab8-5041-bad3-2b463b503e06 |
| Operation: | write | Name: | ShortcutName |
Value: Ummy | |||
| (PID) Process: | (8468) UmmyVD-[1076412529.1746830252,,,,].exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\589bbc75-bab8-5041-bad3-2b463b503e06 |
| Operation: | write | Name: | DisplayName |
Value: Ummy | |||
Executable files
222
Suspicious files
427
Text files
116
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7428 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 7428 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7428 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:07FEB6108D35BF674580C026AB2B567F | SHA256:E4059EB6CEF5F48DCF97CE63086D1E71F352379A20619D042B2BF1BAEF67FA54 | |||
| 7428 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 7428 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 7428 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 7428 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.tmp | binary | |
MD5:EF90022DF0735160DD056C0E6670E915 | SHA256:2B663C0B462A437C8DE3D9B95EE157AE181249B78BDD6F7BD73F7EB6D9E03F87 | |||
| 7428 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 7428 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7428 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
113
DNS requests
145
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.163:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7428 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7428 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7428 | firefox.exe | POST | 200 | 184.24.77.62:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7428 | firefox.exe | POST | 200 | 142.250.186.67:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
7428 | firefox.exe | POST | 200 | 142.250.186.67:80 | http://o.pki.goog/s/wr3/3H4 | unknown | — | — | whitelisted |
7428 | firefox.exe | POST | 200 | 142.250.186.67:80 | http://o.pki.goog/s/wr3/3H4 | unknown | — | — | whitelisted |
7428 | firefox.exe | POST | 200 | 184.24.77.52:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
7428 | firefox.exe | POST | 200 | 184.24.77.52:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.163:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7428 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | — | — | whitelisted |
7428 | firefox.exe | 142.250.184.234:443 | safebrowsing.googleapis.com | — | — | whitelisted |
7428 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
7428 | firefox.exe | 34.107.152.202:443 | firefox-settings-attachments.cdn.mozilla.net | GOOGLE | US | whitelisted |
7428 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
videodownloader.ummy.net |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |