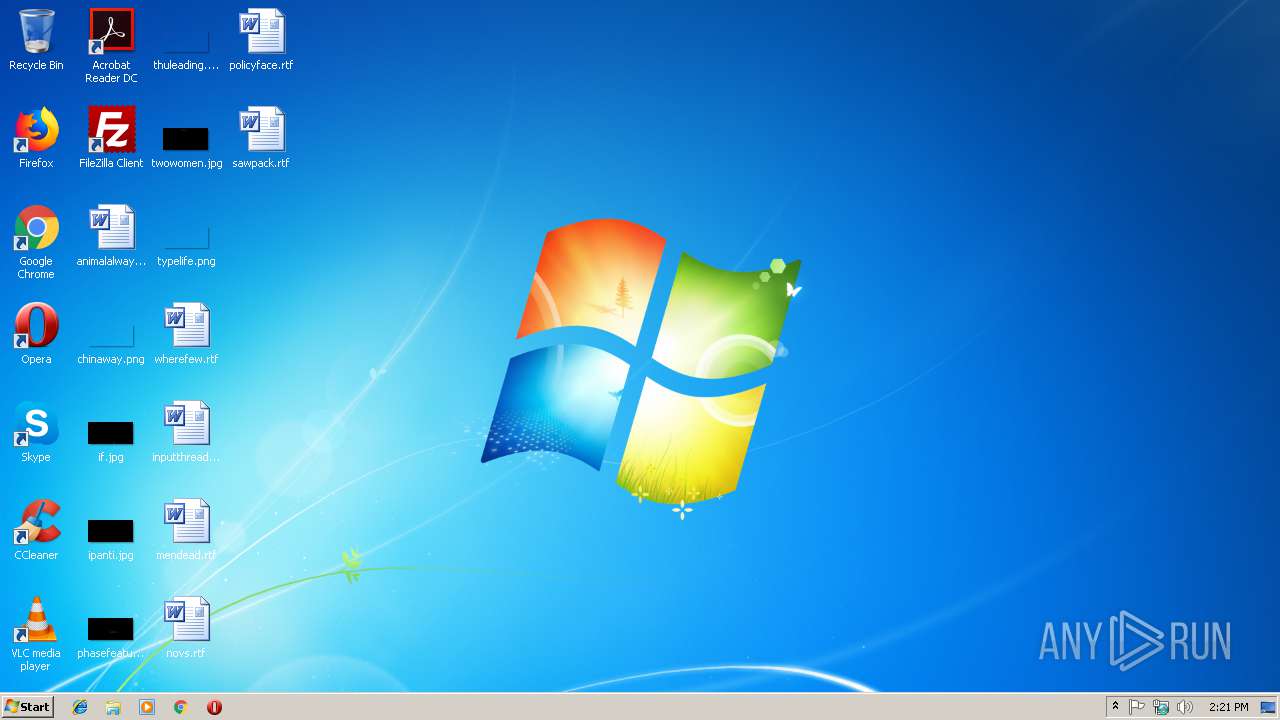
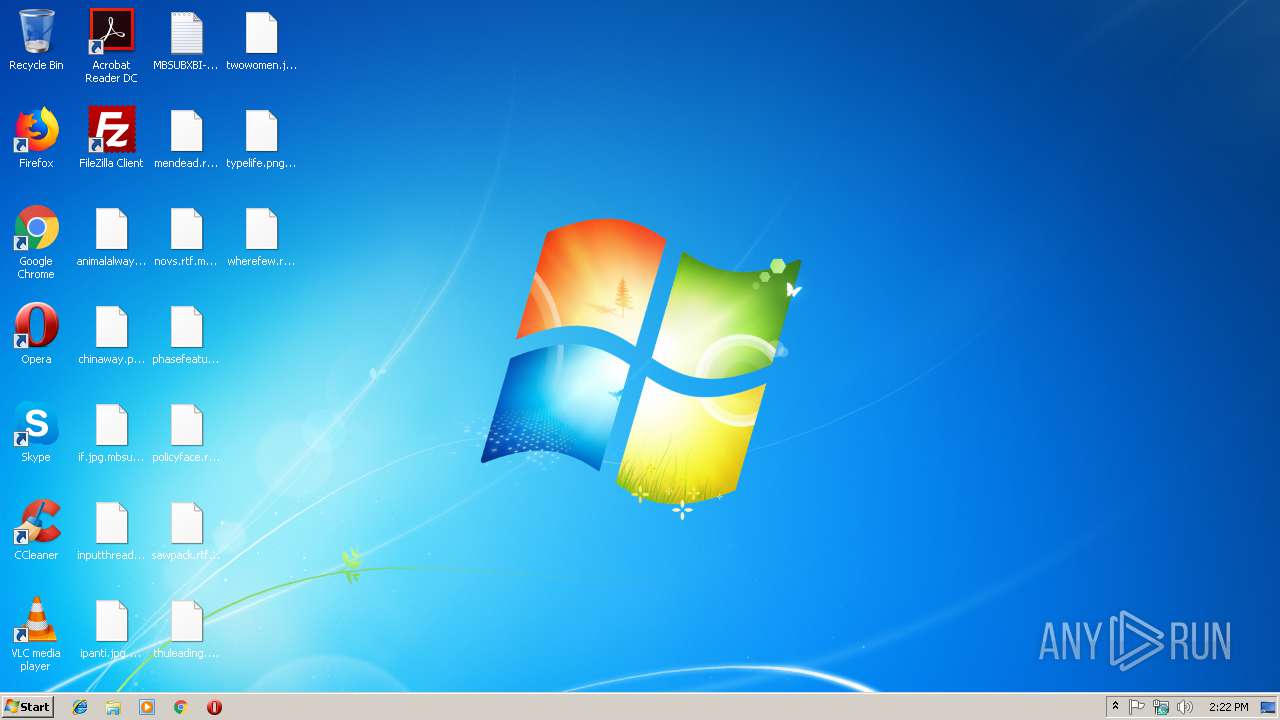
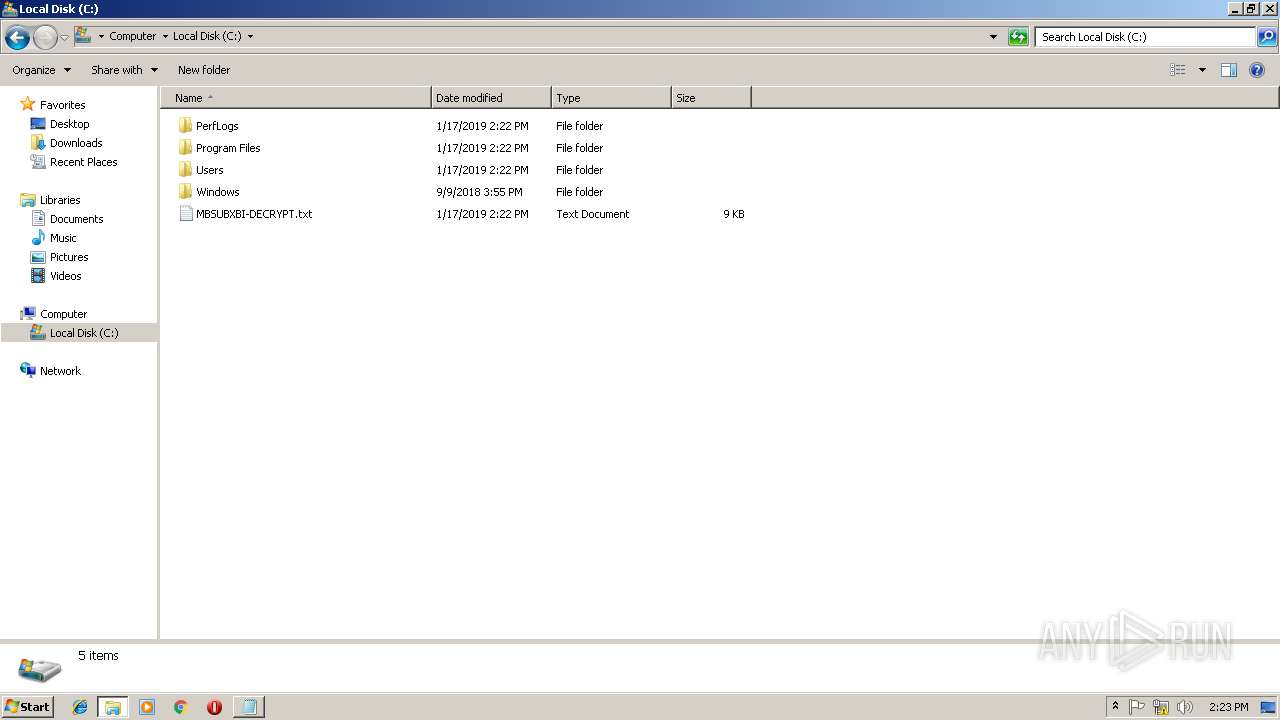
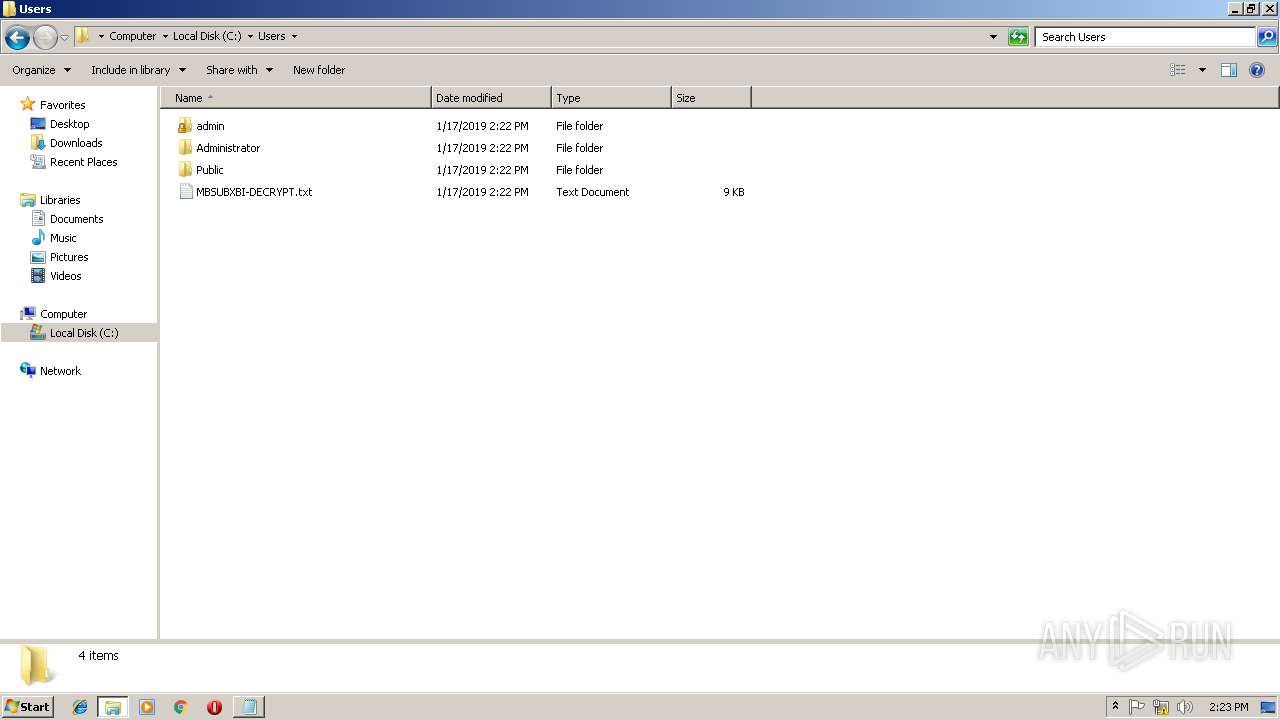
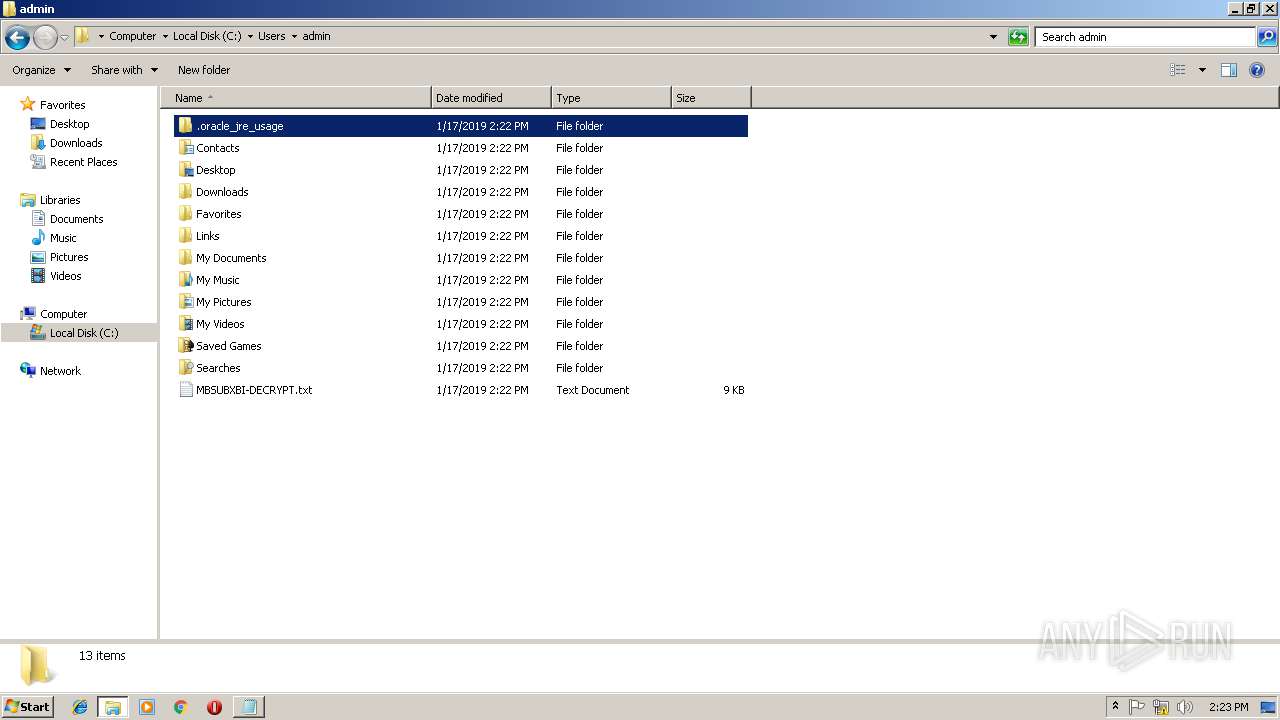
| File name: | 1.exe |
| Full analysis: | https://app.any.run/tasks/0be296a9-a2b0-4cd3-bf0c-bce2637fae9f |
| Verdict: | Malicious activity |
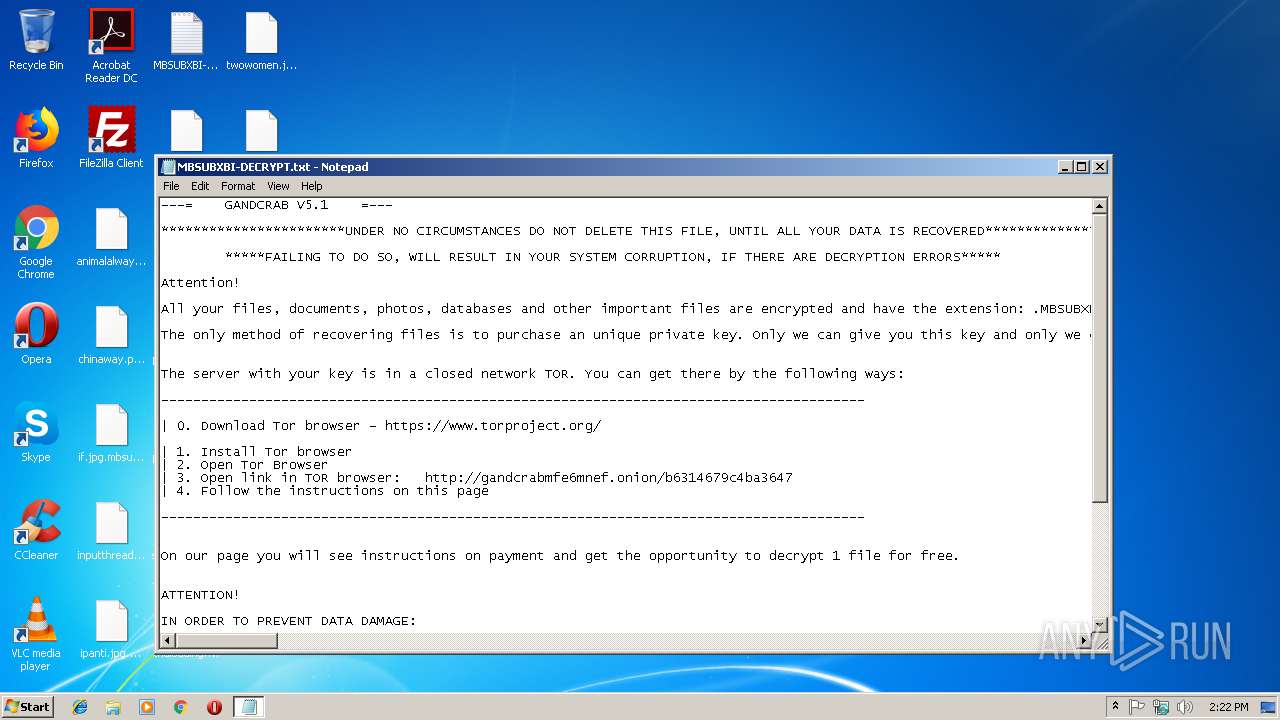
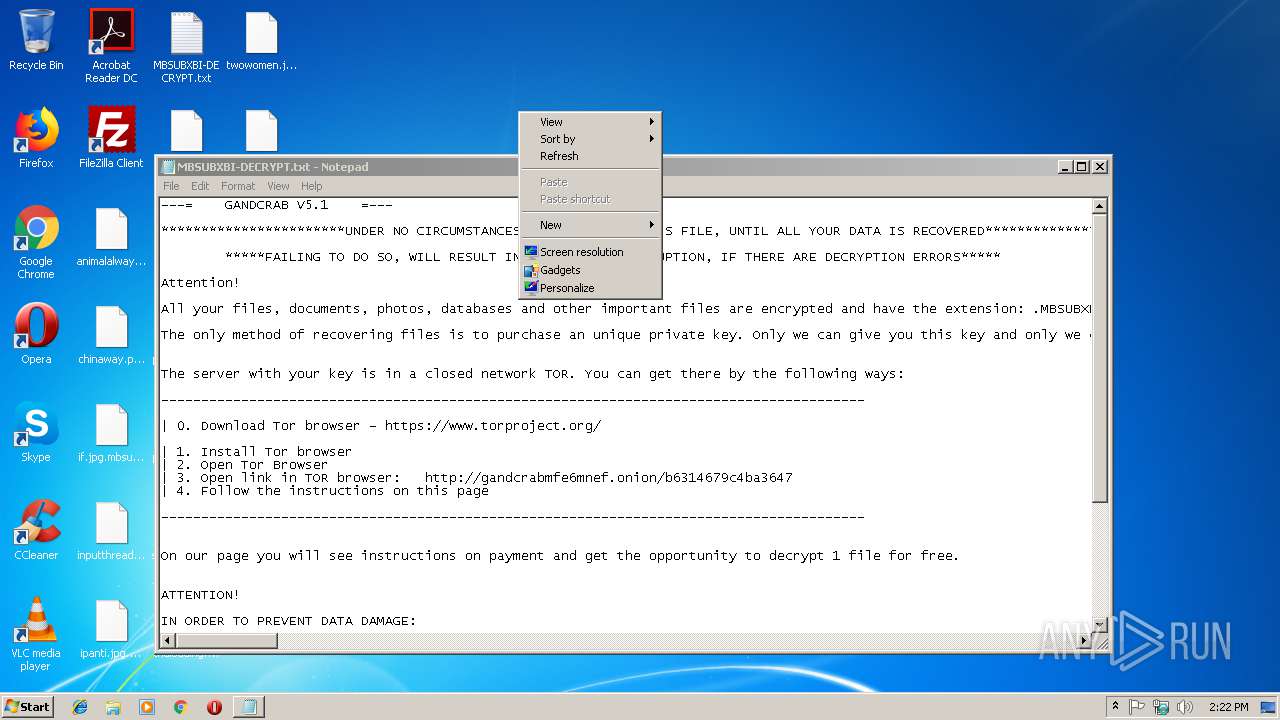
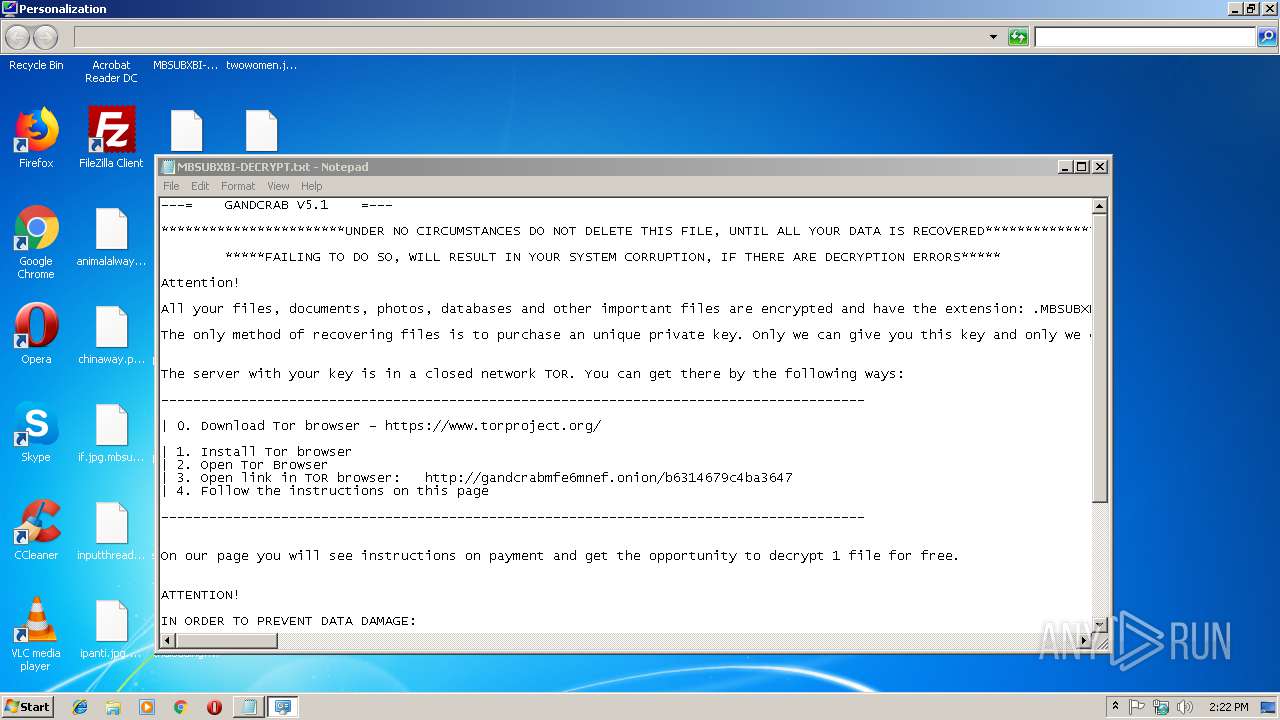
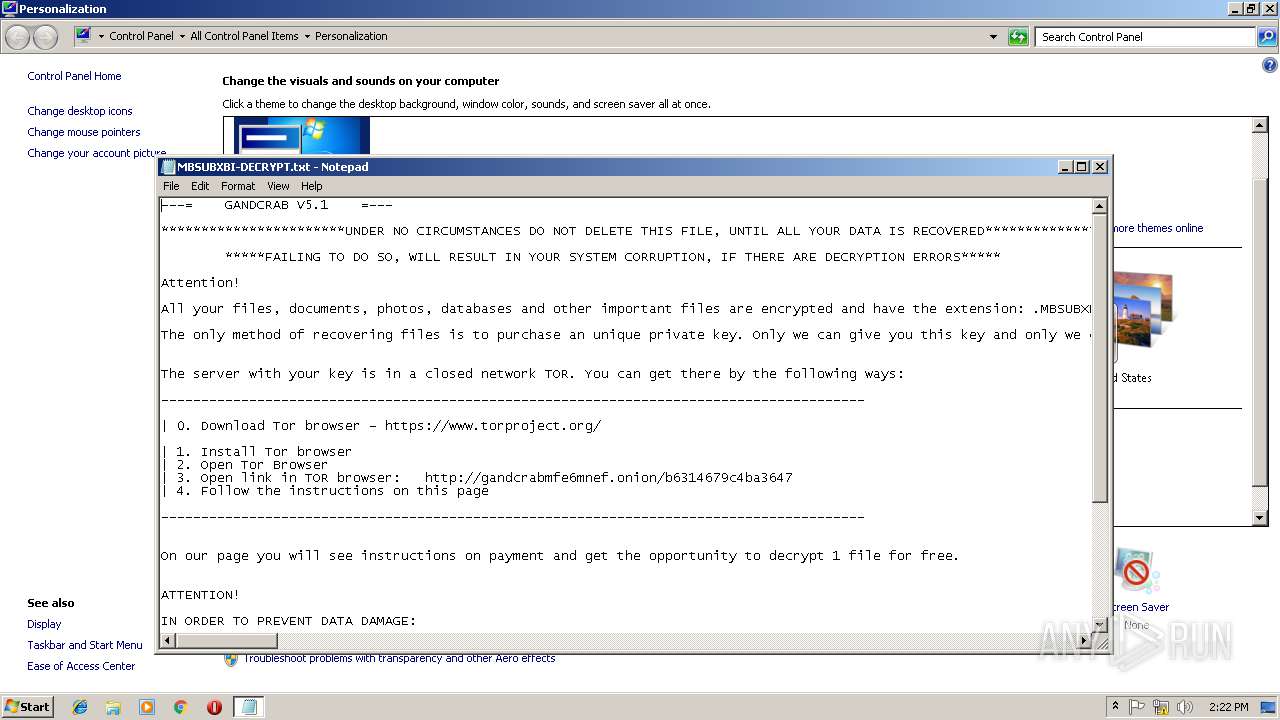
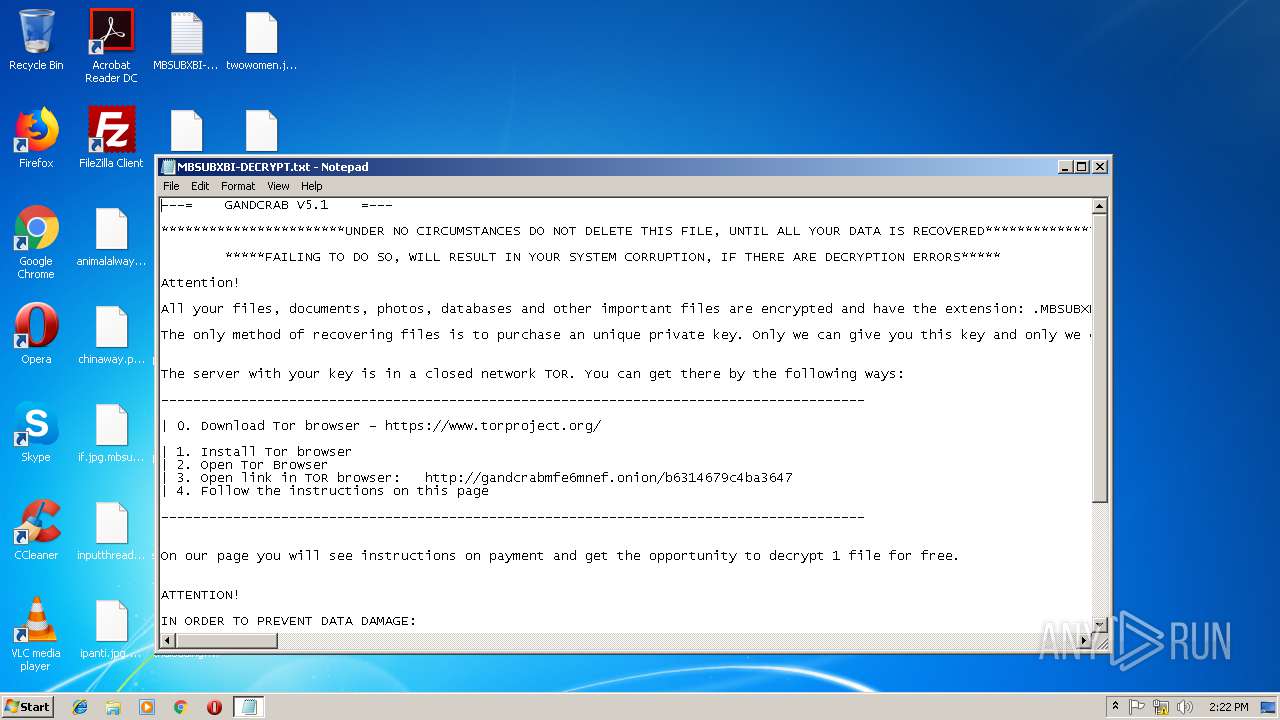
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | January 17, 2019, 14:21:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | E387BD817E9B7F02FA9C2511CC345F12 |
| SHA1: | 98B3EC47B64198E3604C738F8C1F4753E0AFA8C7 |
| SHA256: | 39514226B71AEBBE775AA14627C716973282CBA201532DF3F820A209D87F6DF9 |
| SSDEEP: | 3072:06scOhLLGEdJT5GBQ8eTgeOJnflLfe1ndzo9cLvJkXky6GHBTfFhTWkCvaTdmGlB:0ccLLGEsC7v4c1ndzhe0IdfJC6BtZtb |
MALICIOUS
GandCrab keys found
- 1.exe (PID: 3108)
Actions looks like stealing of personal data
- 1.exe (PID: 3108)
Writes file to Word startup folder
- 1.exe (PID: 3108)
Renames files like Ransomware
- 1.exe (PID: 3108)
Deletes shadow copies
- 1.exe (PID: 3108)
Dropped file may contain instructions of ransomware
- 1.exe (PID: 3108)
SUSPICIOUS
Creates files in the program directory
- 1.exe (PID: 3108)
Reads the cookies of Mozilla Firefox
- 1.exe (PID: 3108)
Creates files like Ransomware instruction
- 1.exe (PID: 3108)
Reads internet explorer settings
- helppane.exe (PID: 3116)
Creates files in the user directory
- 1.exe (PID: 3108)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2628)
Reads Internet Cache Settings
- iexplore.exe (PID: 2848)
Dropped object may contain TOR URL's
- 1.exe (PID: 3108)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:07:26 02:54:11+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 65536 |
| InitializedDataSize: | 307200 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5072 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.45.8.4 |
| ProductVersionNumber: | 7.32.568.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| FileVersion: | 1.0.8.39 |
| ProductVersion: | 1.0.8.39 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 26-Jul-2017 00:54:11 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 26-Jul-2017 00:54:11 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0000FEDB | 0x00010000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.54749 |
.rdata | 0x00011000 | 0x0000411E | 0x00004200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.17141 |
.data | 0x00016000 | 0x0001D2DC | 0x0001B800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.73542 |
.rsrc | 0x00034000 | 0x00028BCA | 0x00028C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.29617 |
.reloc | 0x0005D000 | 0x00001AE0 | 0x00001C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 4.66732 |
Imports
KERNEL32.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
156966 | 0x00000000 |
Total processes
49
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2368 | "C:\Windows\system32\taskmgr.exe" | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2628 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2764 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2848 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2628 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3108 | "C:\Users\admin\AppData\Roaming\1.exe" | C:\Users\admin\AppData\Roaming\1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3116 | C:\Windows\helppane.exe -Embedding | C:\Windows\helppane.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Help and Support Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3704 | "C:\Windows\system32\wbem\wmic.exe" shadowcopy delete | C:\Windows\system32\wbem\wmic.exe | 1.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
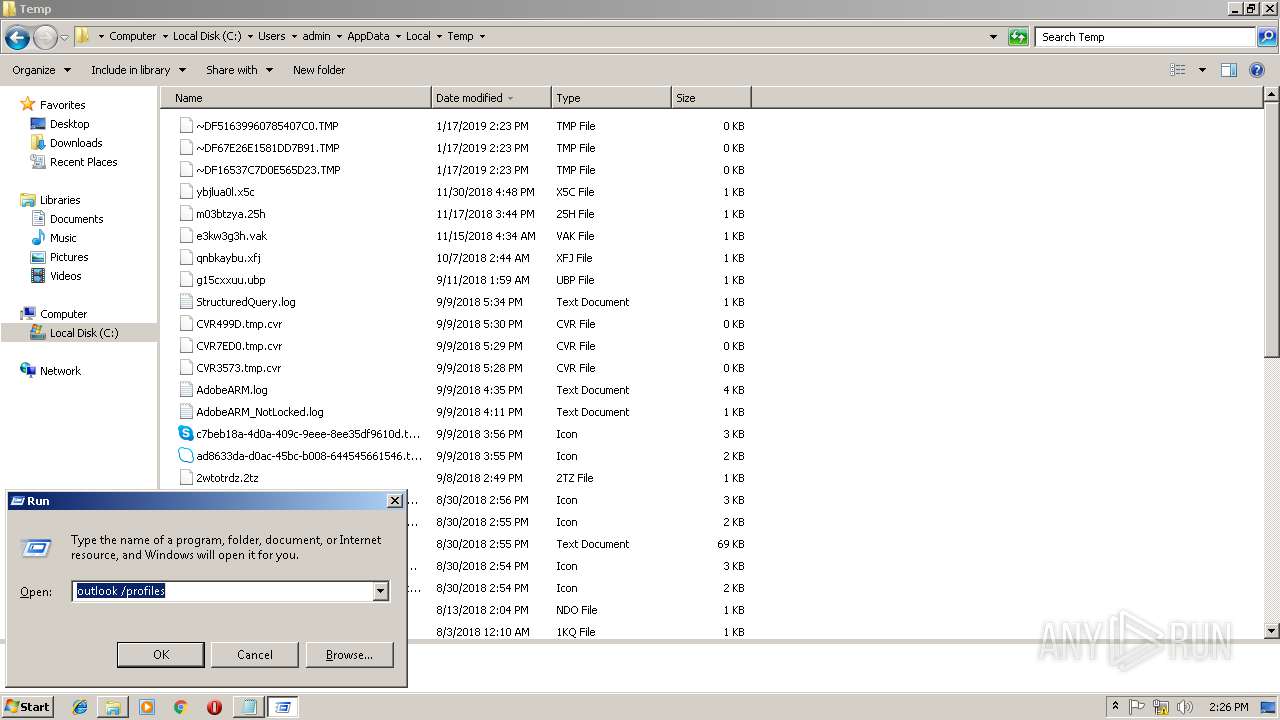
| 3980 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\MBSUBXBI-DECRYPT.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
760
Read events
688
Write events
71
Delete events
1
Modification events
| (PID) Process: | (3108) 1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ex_data\data |
| Operation: | write | Name: | ext |
Value: 2E006D0062007300750062007800620069000000 | |||
| (PID) Process: | (3108) 1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\keys_data\data |
| Operation: | write | Name: | public |
Value: 0602000000A400005253413100080000010001005359828FC66A24F2075095E0631658950EF261E073DC13F01D0A5E1DF4AE041A40DCE3D3D0B4575D0B4DDDE09246E9DEE915F9A621FF89D0CEA43C48A8D3E8A424C9B18918D43FDC089FB8A980D67CE8A6BA38C880C9934B02FC21F3A161E9AE8D27865126F4188775917C07449DF3F9B883F7236BAADD62FB8BA555B8B2FDD070BC14BF1475AE11CAC4CA2BDE22BC29CD0408EB26EEB30F02EFE9F78432FF10FA7E03C916F3158B2819513788373E0E9D0EE14CA5BFCC4422359932C068D025B6EB03E5BB9822280DD535D1B259A6C808BAD6525241A8DACC739A093054D6878C22E95215EF0D83B5CD2F66877B0AFEEC634F30A7DD1DC1512760E7C602D79C | |||
| (PID) Process: | (3108) 1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\keys_data\data |
| Operation: | write | Name: | private |
Value: 94040000F1F9E79D28E02DBFD78CD7755048E7B2ABC284F6350FC2E096E7B1F6E9050BAD8698265BD79B35EDC00FDC086118B4E5D1E12FDA16A4BC01A9F553D6FA476DDFFE77DF5394FC8A4AB1213E0D659E80518BD943032120604BDD81AC82985EAA3F2AD6E1137CC06F3CAB1B46A774DCA05D98257699B268024B44389DC87F57E4BEF976F7D2EA094354826BD618D69701490439A2F78FDF0FB1CA1736234719346D3939491A10FA71B2010F98E863EB8D7F75CE3321DB4527BA5A5BFC8F73BAC228ED8DFBA6640F4EED52689A9C7F318FEF85E23662CD56F032496E6EC24E9B9C51C0E42413FDA83CCE4379DD2CA764E5A9A0B3B2904BD992DB7D2CD0BCC0A87139AADC7D8F3855135502B9C80A2C301AD51C837D2E7E1CCCFDC9640EEB4857DFDFEAE2AEA9F88763F15B6BC6EE0FA36BC32696F34B2159867DE2EC63D02D6582B634E9259552E6CFDC6FC30B011C7A85EF58318DF9564E2DB17517B889AD251096E60DE5880939BDE2E161C3ACF5B0AB885776908C04ECC6AB3B5CBDB2E30C97F477413FB0DC337FAA83923CFC415E1FA7B1BE1C5887EA24C3CA4801C9AA0B61737BF55F75E83CADF91F2EA9D56E56DCD6A3858518E2600FEE0262C1BB0784FD75EEF99B260017BCAF9629A78562DCFF0FD54B5E4FCFB8ED1835D4AB2DAD41BC3B4D00AACDC1070B39EF13D52569C56E48D5B8D52608C61154E1EB402597DC8B896CADABB42CB336D6D94C68373C0620D781080D33E068373AC646CD82867F8DBB24E85BAE47544B78ED41AFAA6529B97B33C2E05FE6BC083CAD44591C0E4EE7023B9AC4013B707E5D51A659A0337E6FA68E662E4040024BDDF7D9B3A9B9990AA0AC671A457C243CA75FF697CA691A7FA541F18417F97EEFC46FF7EA4671937A7D00CA791577267AC4CA6B4EEBF79BF6F3E4785EE8C2DA3E63BDF222AC43735E69E8D334770C3CFEF22BC6CAD1C7A540380BD12D7BAF7F763DE92C34034A60504253E2B3CA7112A43892D371258FFA6993BFB94DCC62BA7CFEF435DCDF79DE676E0B07AF77BE9505E01A27F1022C615D38DA907A221A4C54CD35054E2866ED41DE1866257F379FA46243BE322898952F6D972C3BB4F22DC266D9E3A8BD7815CE0B0247F036CA1CAB176D69651F7EE0970ED1AF23DEACD8DCC05D5C4747746053419865A2276E6A636D3785DDD0467FBD8B6BFF34FB0540AA4F08D1B91E821A4F3998B7746D2F01158EA396B519911EAF237371BD9C33C97DDAAC8A2B6B2EE879A725BDC22597666964717B409F2190252970C02E78B2A9A60640978000BD71FE3151BA105BB93D114EB1BBFF0D5CEBB6328641D6E14928A34D902B1B8F360EB69EE25F7B17C0C1EA54DD8D274012D8EBA9363A9233555E2502D577C032559D75D7E11A0F4248E029E7EB5161B296E20903DC1E163CE6BFB37E6E181FB16DFEA4FC1CC6868DE91C433D0335049F5B8FAEA03307D408ECB2532F3618EB8F0D5A668CA2A5D968380867EFB94AE820B8EE5958B72B2EC9A04D1E82F1E55E0A643F6691AA663E5111BB1AD745F851672DA4E14A9011A145388C0CBE1550ABCBD5093143D5445964B294A7828013AC6619FD3AFD37F859F3D6117F60A5E1DA352A3C6B8C843DCA54B6190034BE7803FA91723B8BA9F711EF0CD94FC8D0B458AC5B2D412CB9910865920FB4D246EAB064985B8E7E5ED47FB53AE2ABF5428B0226CE9F9B7DE6F1752A737D38B63D7A29D1C5CF2BD6577F78DF1E503D455FC784ED5D041C9212F7A64D24176B02C553A0C7888BF5B011CEFAA443D8514DEA546C9F8A01FA2A94F8E2A077073AC00EABF8C7A307B2344D5060913886E819FE2EA9B793A610F320B96004DE44F2C8DD3AFF2001DB561341FDC0050892C5B5699237452F4459E5B26D70FD55B259B23B8F5276EA3BD63813577ABE52ED1FCC7522BF133C2409A80AC11DDF8A1E0ABFF0644A5E1789ED8FBD8AB76BD160ED03CEF7CD578C7FE6E1D03F17A2570334105C15B7259692242F3E705764F23709E2D2B437804CC04A65C0D97D94878DA5BFA7C0417317EBA4D509F6522E1C8CC6A7C1324F1D6D191674D09EB6FD6CA19B7731FF873CA05C324D1B4012237F18D23AF4A6CAC8469E64DB992FCBC75CE4A96457C0FA76C2220892C1E631CC74A6E42A8532FFB5535583480E40E1013B56BB934122FDB559364A84D96528CF8B4FDD0DAEDBE4A83AF389731DB6D93B10D4FECFE70BCC954ACEFE75082FD9009ED041895B71306242E4F7298933ED3635CFDDC9F4FFB5F73929E4C33BAC0F6E54FB1D2F9EEC8F402E7B5E339BA714BBB245C15350E1F92C4CBAD936EF789E816C805DC7B35F152E471B67A90D92F70FF9EDC4D58BD2209363E508C62E2C66EF | |||
| (PID) Process: | (3108) 1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3108) 1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3108) 1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\1_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3108) 1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\1_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3108) 1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\1_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3108) 1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\1_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3108) 1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\1_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
Executable files
0
Suspicious files
429
Text files
320
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3108 | 1.exe | C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\boot.sdi | — | |
MD5:— | SHA256:— | |||
| 3108 | 1.exe | C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\Winre.wim | — | |
MD5:— | SHA256:— | |||
| 3108 | 1.exe | C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\Winre.wim.mbsubxbi | — | |
MD5:— | SHA256:— | |||
| 3108 | 1.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{05ed3515-06b3-48f6-8cf2-bf24b1bf0727}_OnDiskSnapshotProp | — | |
MD5:— | SHA256:— | |||
| 3108 | 1.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{16d74681-6bc3-4c44-97f0-8b8dfefe2355}_OnDiskSnapshotProp | — | |
MD5:— | SHA256:— | |||
| 3108 | 1.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{38e8535f-27d0-4352-aa3a-ce4178930102}_OnDiskSnapshotProp | — | |
MD5:— | SHA256:— | |||
| 3108 | 1.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{3cc0f82b-873a-4e59-b89f-689fbdf88af9}_OnDiskSnapshotProp | — | |
MD5:— | SHA256:— | |||
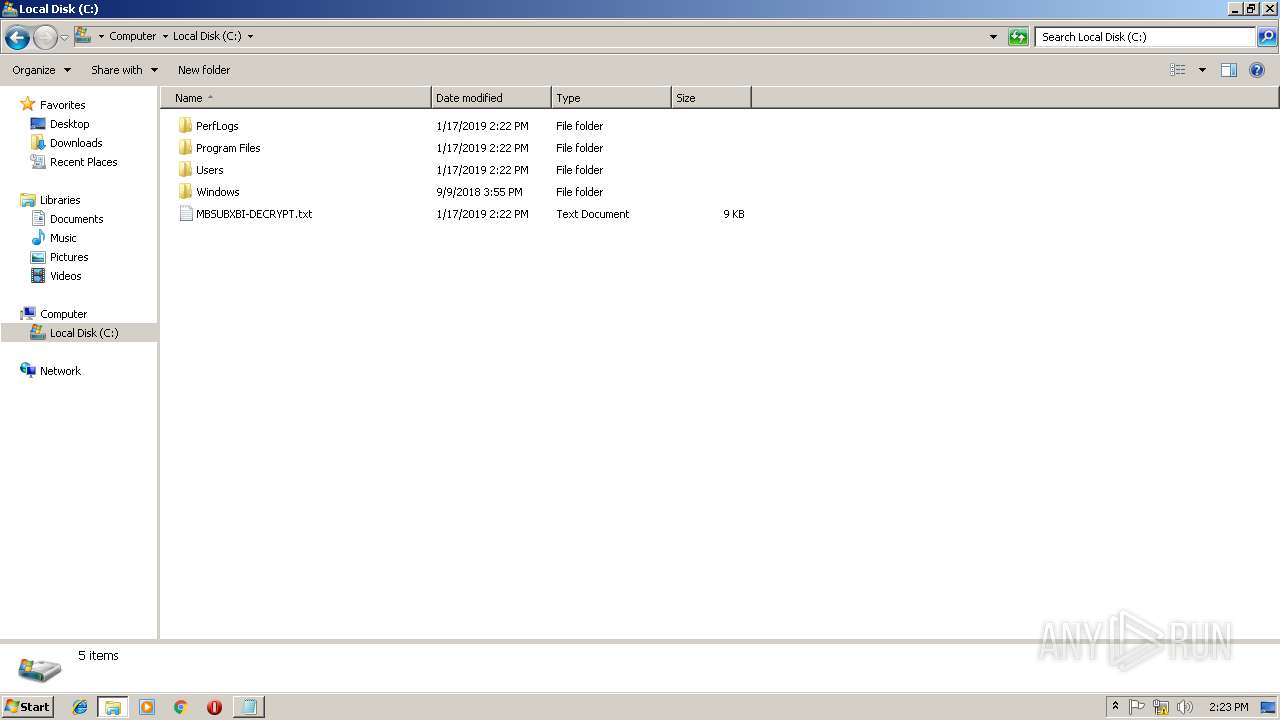
| 3108 | 1.exe | C:\MBSUBXBI-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 3108 | 1.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{5c4beaff-a038-4df7-9b35-072a18f8e3d6}_OnDiskSnapshotProp | — | |
MD5:— | SHA256:— | |||
| 3108 | 1.exe | C:\Recovery\MBSUBXBI-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
2
DNS requests
2
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3108 | 1.exe | GET | 404 | 138.201.162.99:80 | http://www.kakaocorp.link/ | DE | xml | 345 b | malicious |
3108 | 1.exe | POST | 404 | 138.201.162.99:80 | http://www.kakaocorp.link/uploads/pics/sokaamse.jpg | DE | xml | 345 b | malicious |
2628 | iexplore.exe | GET | 404 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | xml | 345 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2628 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3108 | 1.exe | 138.201.162.99:80 | www.kakaocorp.link | Hetzner Online GmbH | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.kakaocorp.link |
| malicious |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3108 | 1.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (jpg) |
3108 | 1.exe | A Network Trojan was detected | MALWARE [PTsecurity] GandCrab Ransomware HTTP |