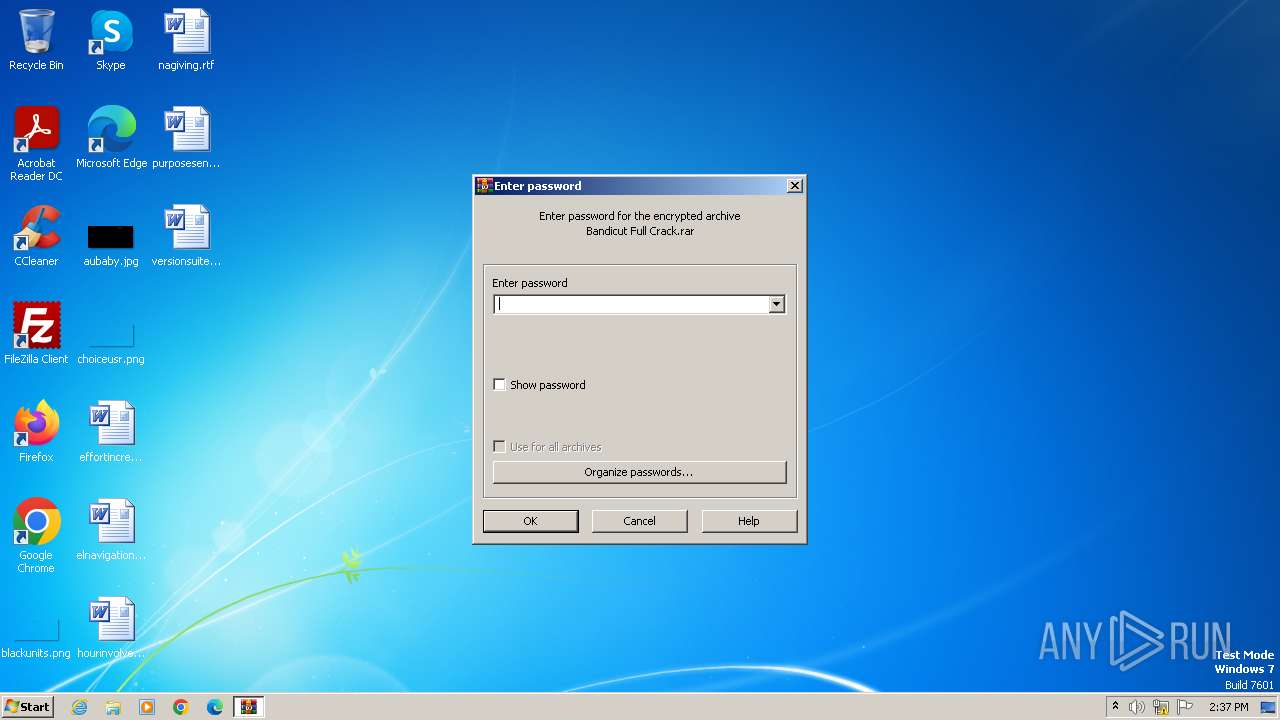
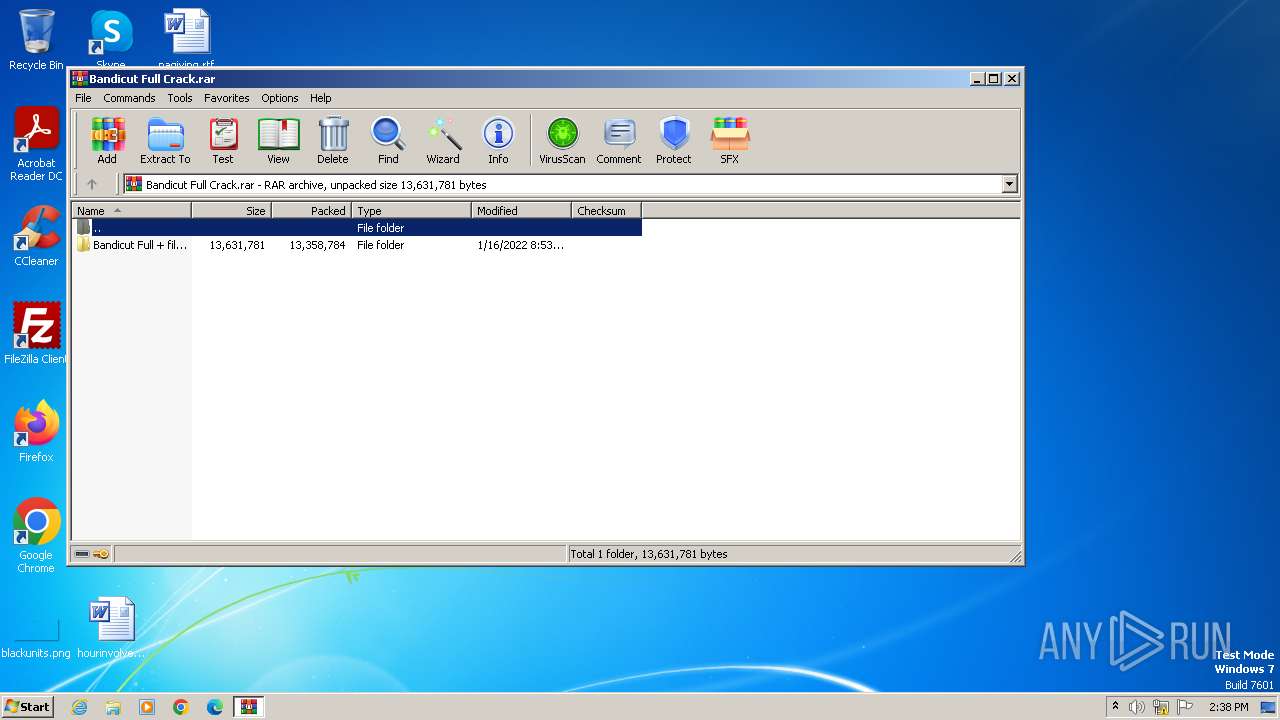
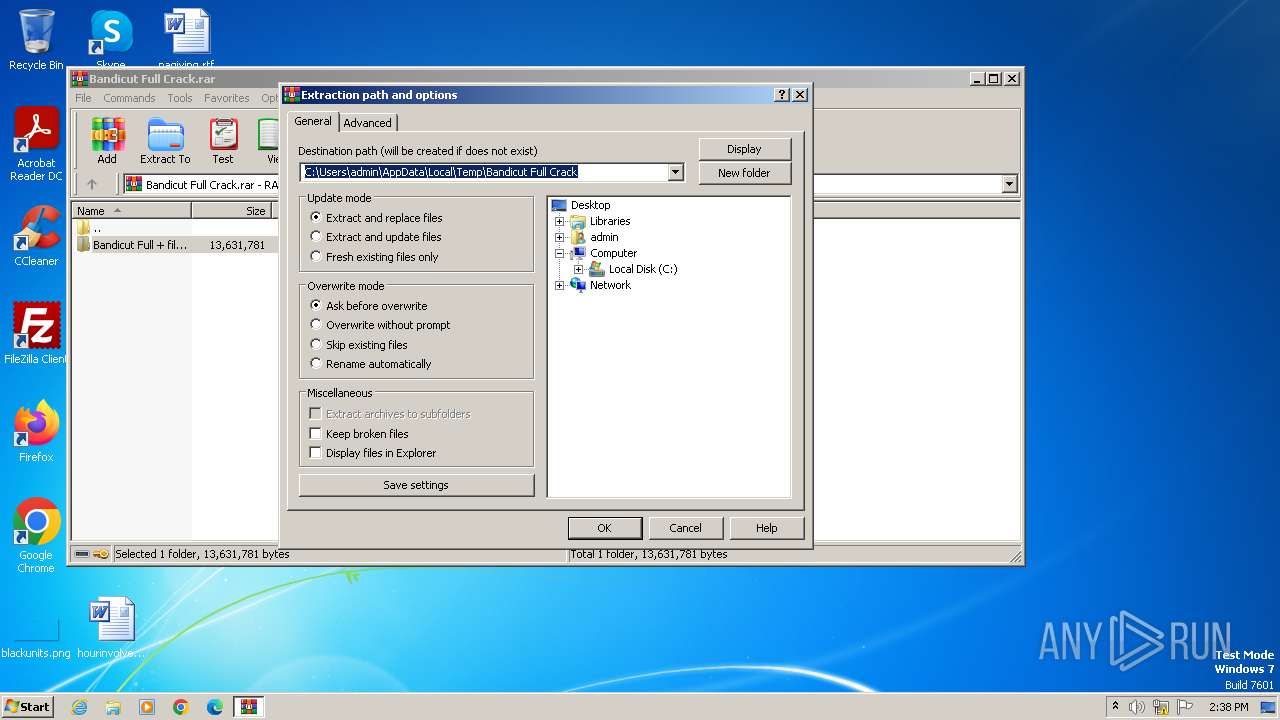
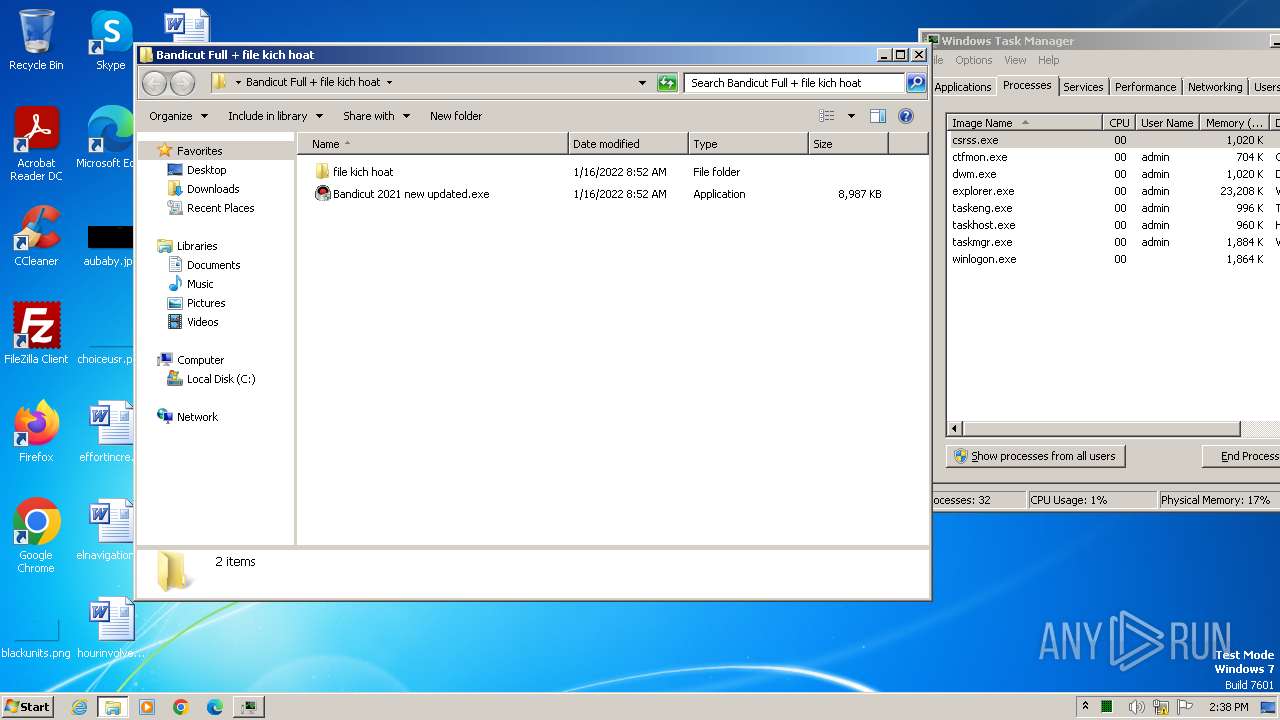
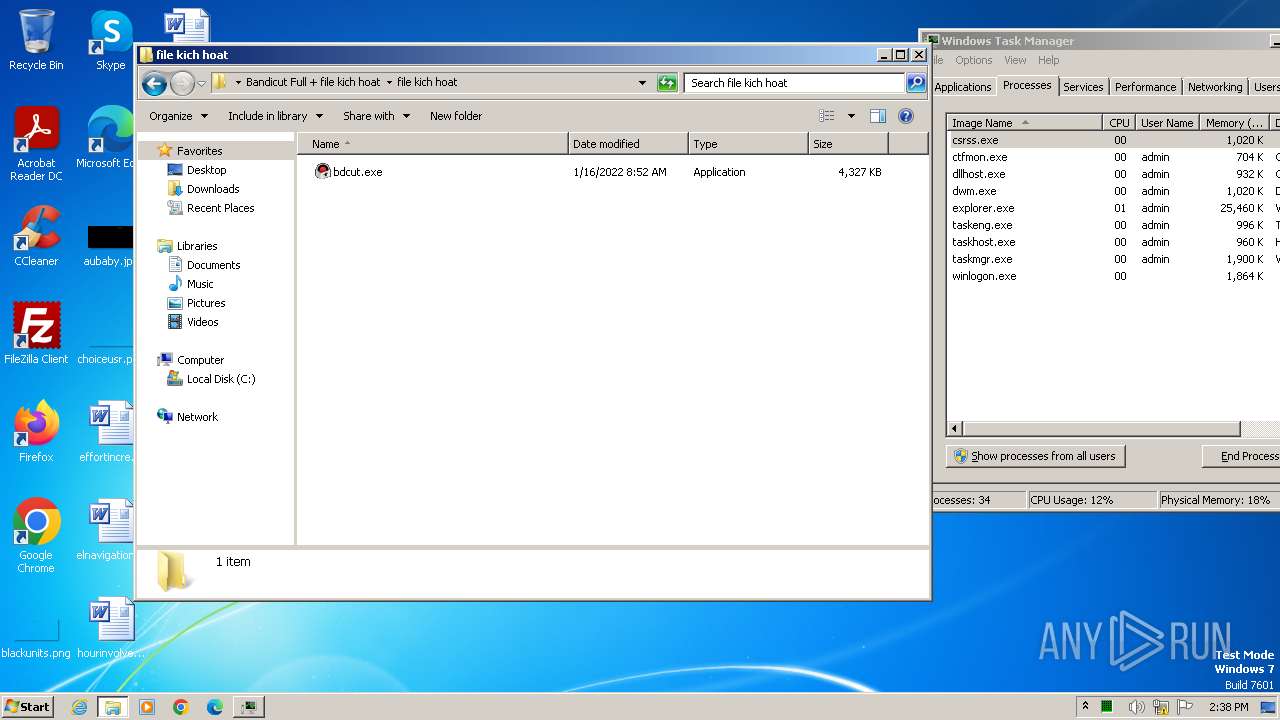
| File name: | Bandicut Full Crack.rar |
| Full analysis: | https://app.any.run/tasks/571845c9-0c5a-4aaf-a1ca-669c8caf2b7d |
| Verdict: | Malicious activity |
| Analysis date: | May 10, 2024, 13:37:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | BD95FD7A845F24172710C3A6962F372C |
| SHA1: | 4CAA945F1FCBB03A0B0D281B7BC77D45ED5167B9 |
| SHA256: | 39313BE32226926A2147369BD9FE7C71539DFBF295F55E4721C44C4993A9DA5E |
| SSDEEP: | 98304:7UUks2Lgi1vEzaD90h/w1F6Ackco4+ZuvS4aSARVsPoPEvK2/2OVoGSV+0GWGc34:uQh4XB9AaKG21qWzmNTKrOXPmHp |
MALICIOUS
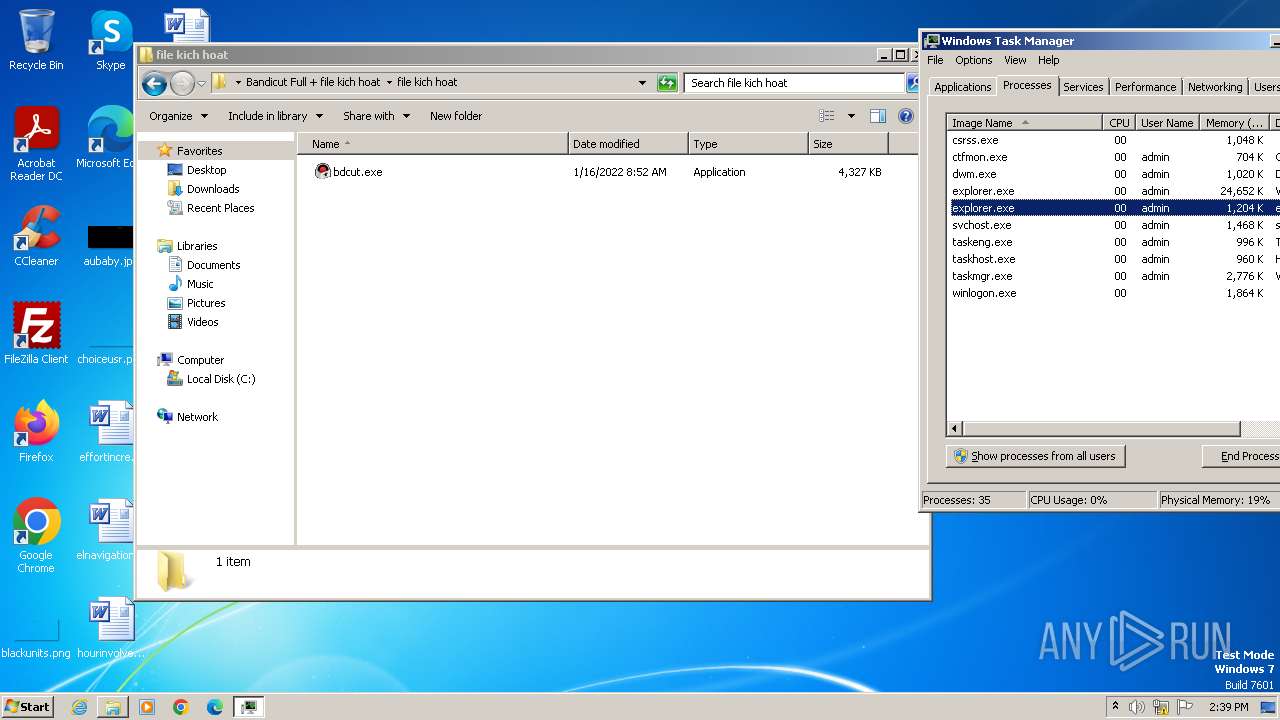
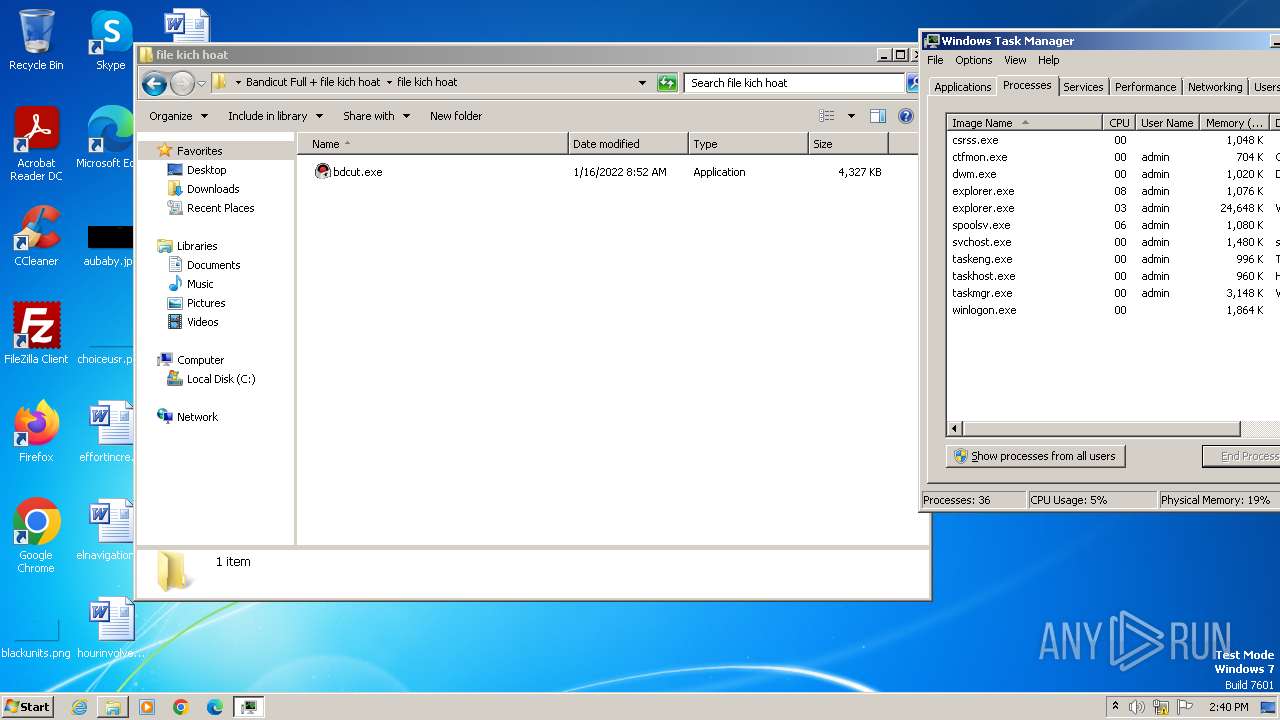
Drops the executable file immediately after the start
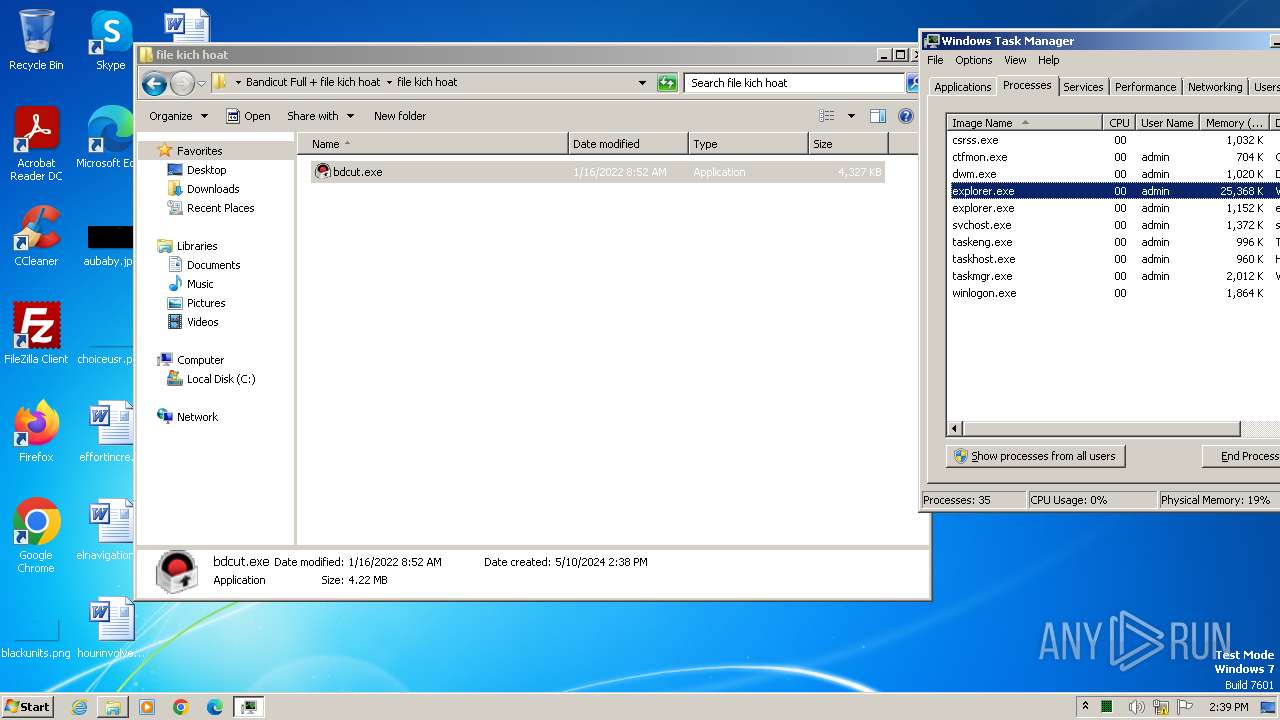
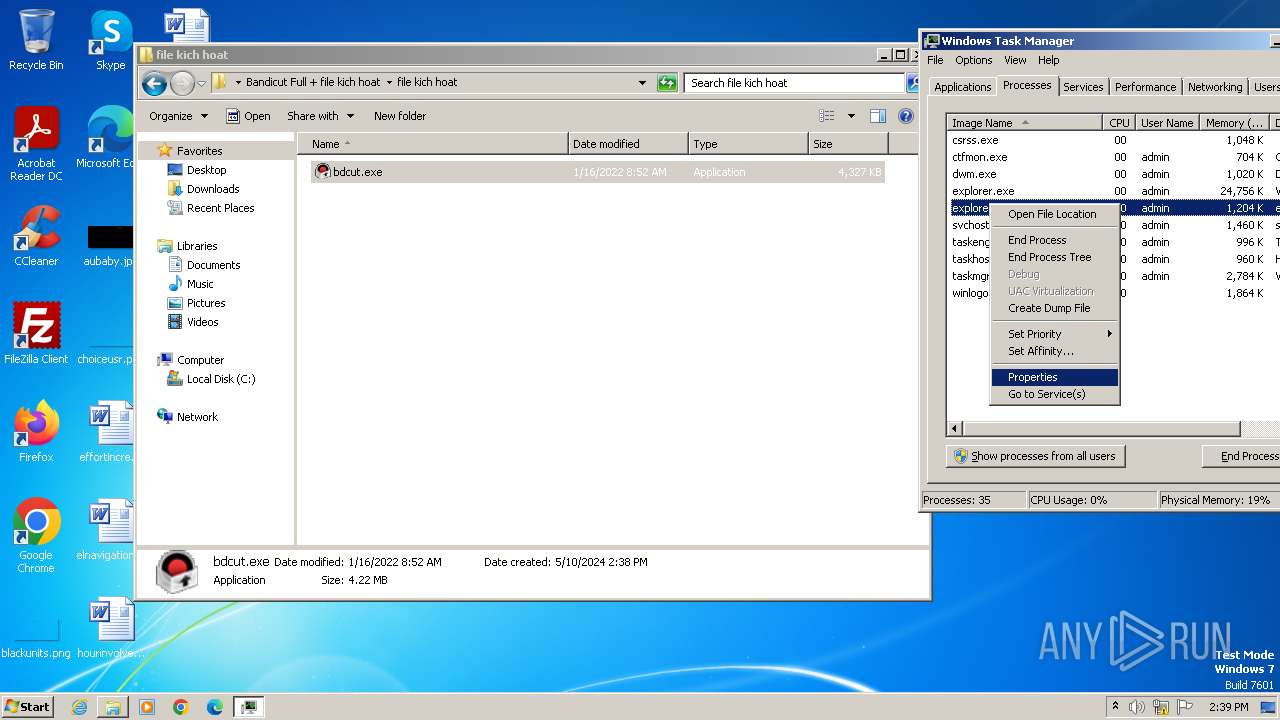
- bdcut.exe (PID: 2240)
- icsys.icn.exe (PID: 2232)
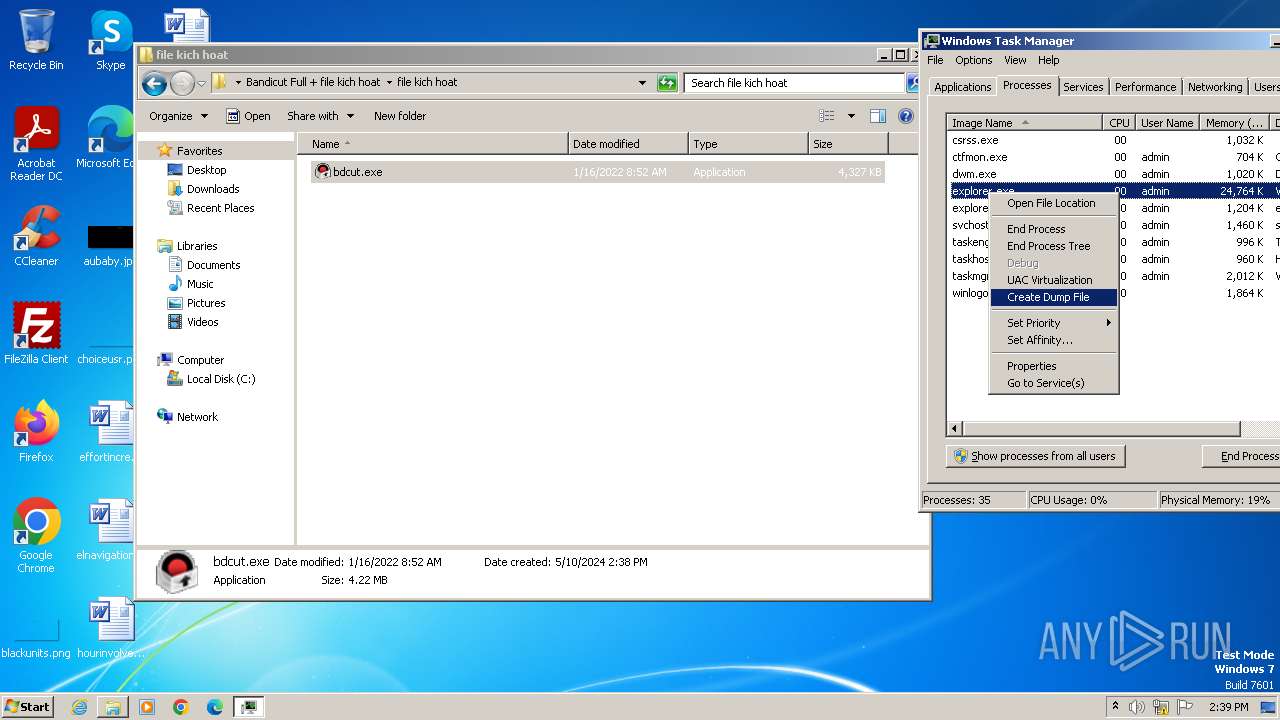
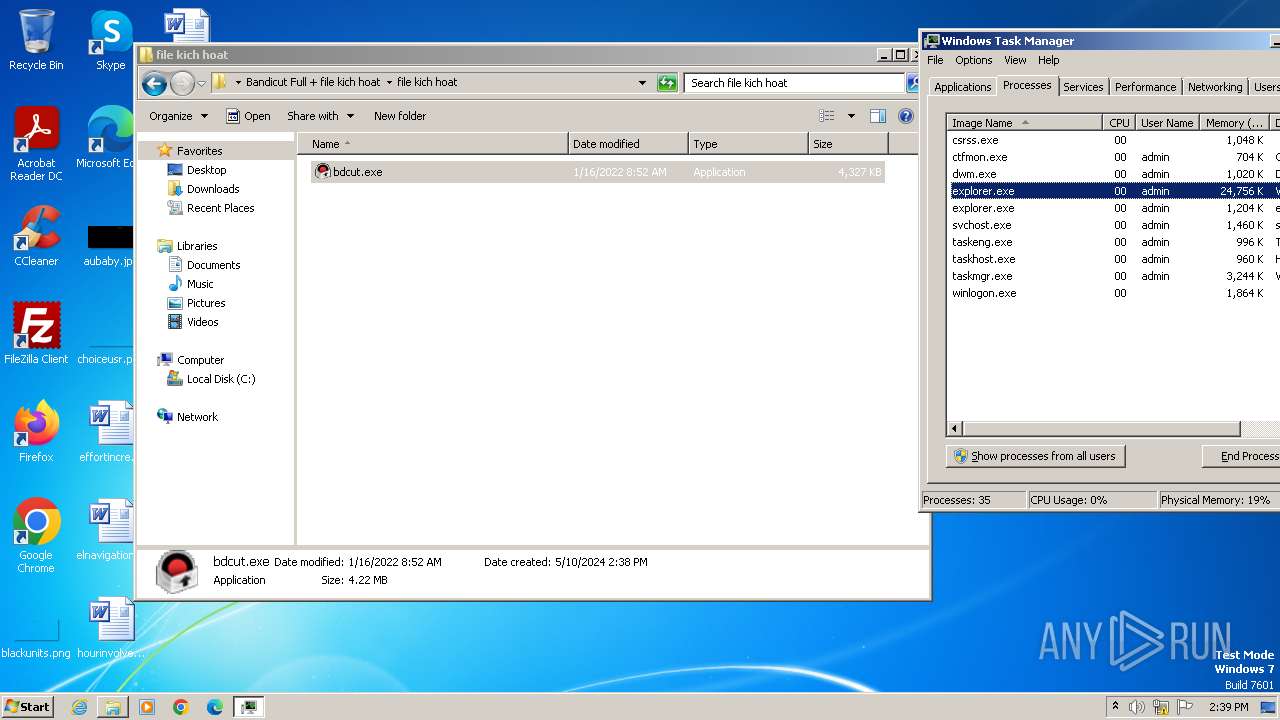
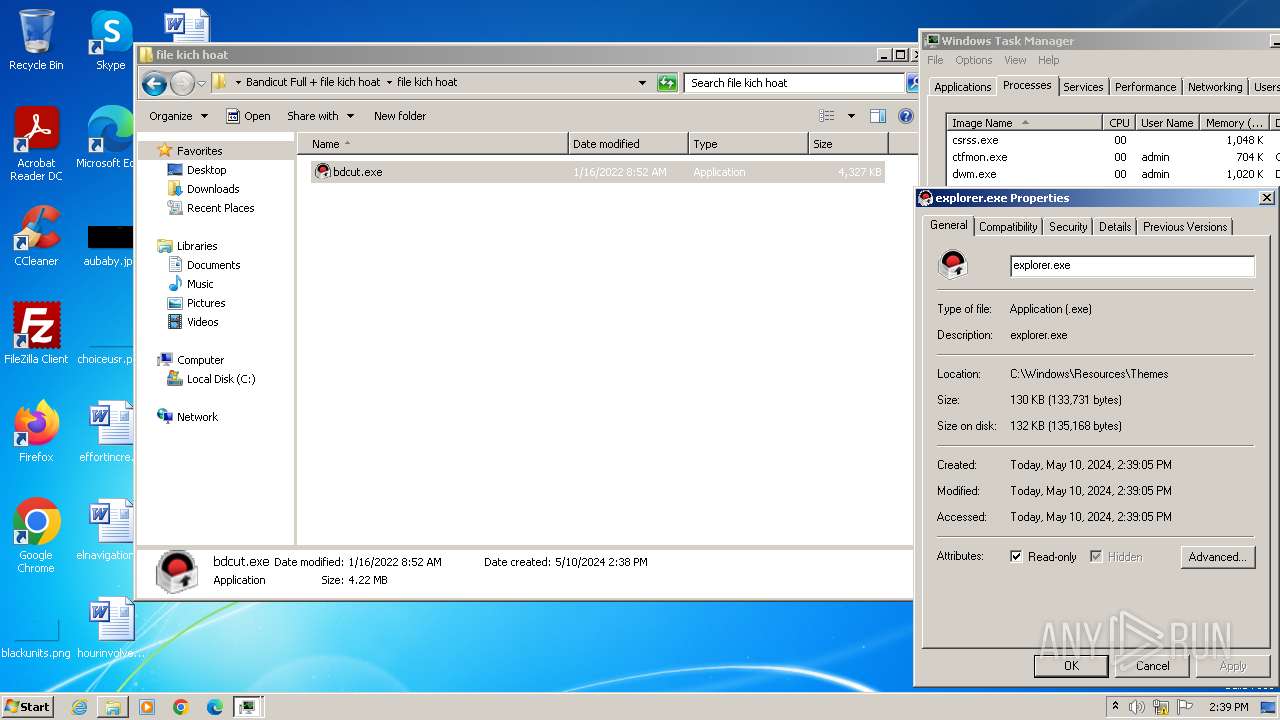
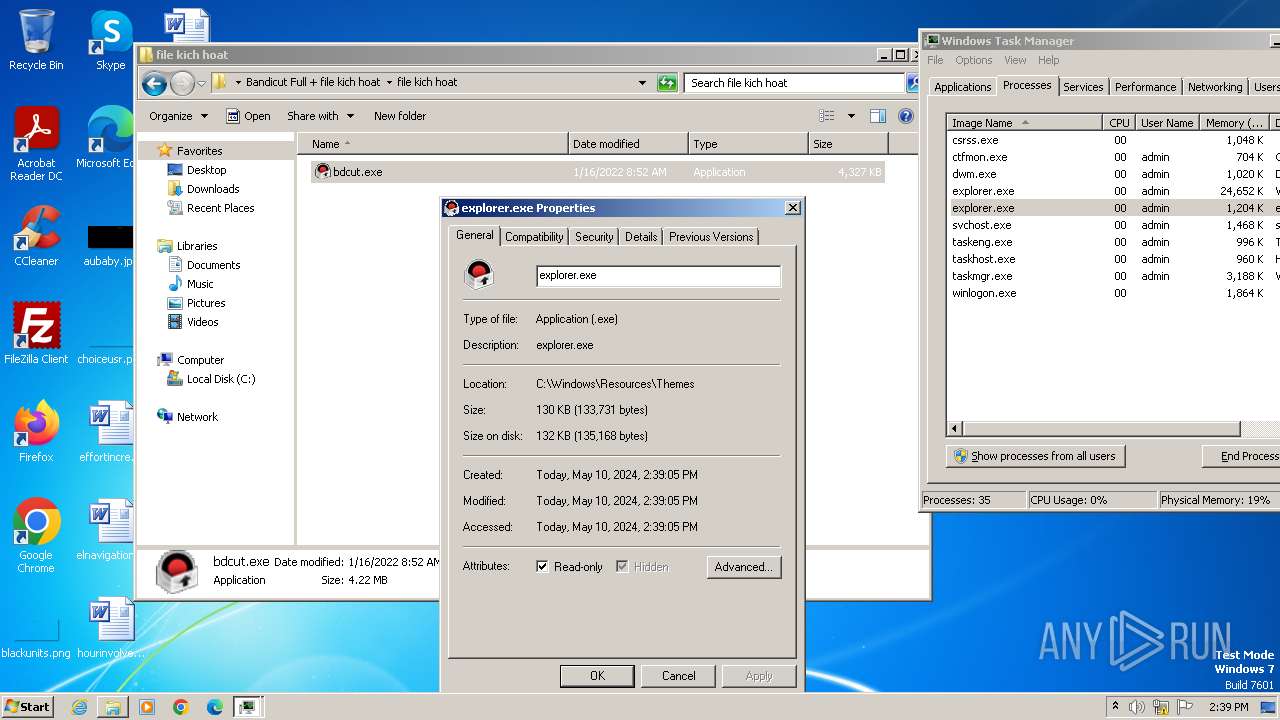
- explorer.exe (PID: 2264)
- spoolsv.exe (PID: 2256)
Changes the autorun value in the registry
- explorer.exe (PID: 2264)
- svchost.exe (PID: 1596)
- explorer.exe (PID: 992)
- explorer.exe (PID: 1344)
Changes appearance of the Explorer extensions
- explorer.exe (PID: 2264)
- svchost.exe (PID: 1596)
- explorer.exe (PID: 992)
- explorer.exe (PID: 1344)
SUSPICIOUS
Executable content was dropped or overwritten
- bdcut.exe (PID: 2240)
- icsys.icn.exe (PID: 2232)
- explorer.exe (PID: 2264)
- spoolsv.exe (PID: 2256)
Starts application with an unusual extension
- bdcut.exe (PID: 2240)
Starts itself from another location
- bdcut.exe (PID: 2240)
- icsys.icn.exe (PID: 2232)
- explorer.exe (PID: 2264)
- spoolsv.exe (PID: 2256)
- spoolsv.exe (PID: 1980)
- explorer.exe (PID: 992)
- svchost.exe (PID: 1596)
- spoolsv.exe (PID: 1964)
- explorer.exe (PID: 1344)
The process creates files with name similar to system file names
- icsys.icn.exe (PID: 2232)
- spoolsv.exe (PID: 2256)
Creates or modifies Windows services
- svchost.exe (PID: 1596)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3984)
Checks supported languages
- bdcut.exe (PID: 2240)
- icsys.icn.exe (PID: 2232)
- explorer.exe (PID: 2264)
- spoolsv.exe (PID: 2256)
- svchost.exe (PID: 1596)
- spoolsv.exe (PID: 736)
- spoolsv.exe (PID: 1980)
- explorer.exe (PID: 992)
- spoolsv.exe (PID: 324)
- spoolsv.exe (PID: 2656)
- spoolsv.exe (PID: 1964)
- explorer.exe (PID: 1344)
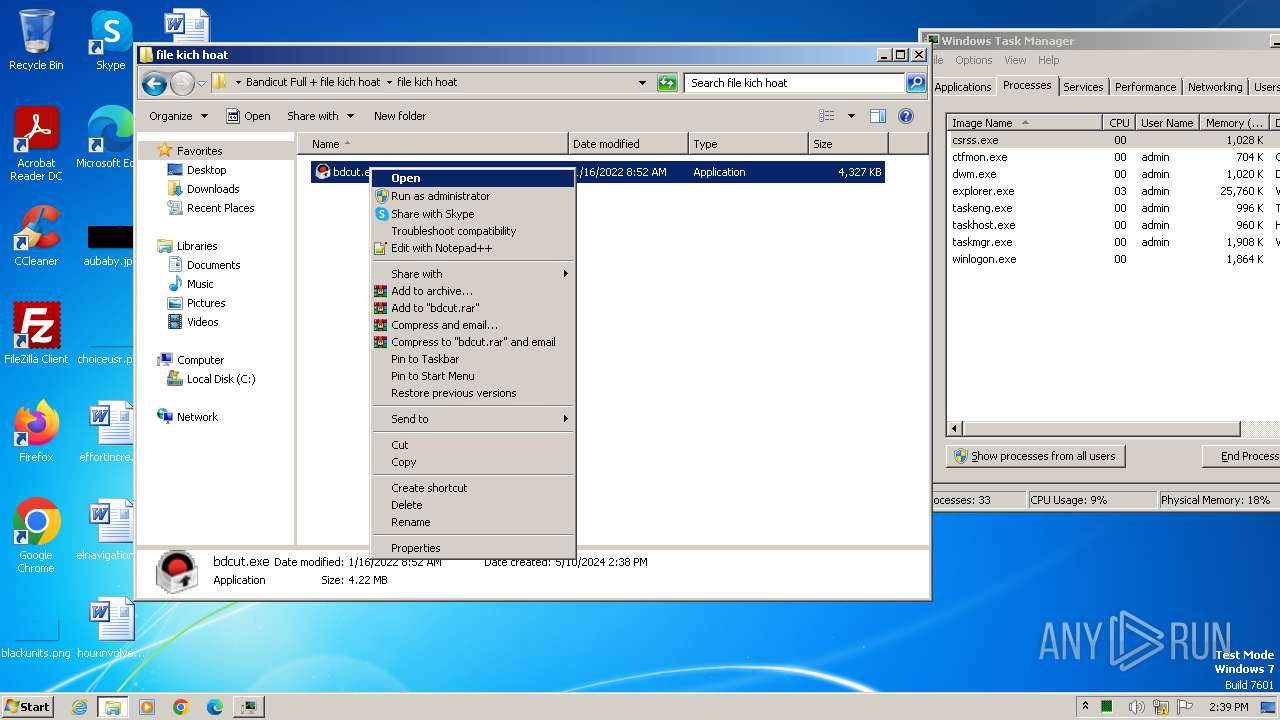
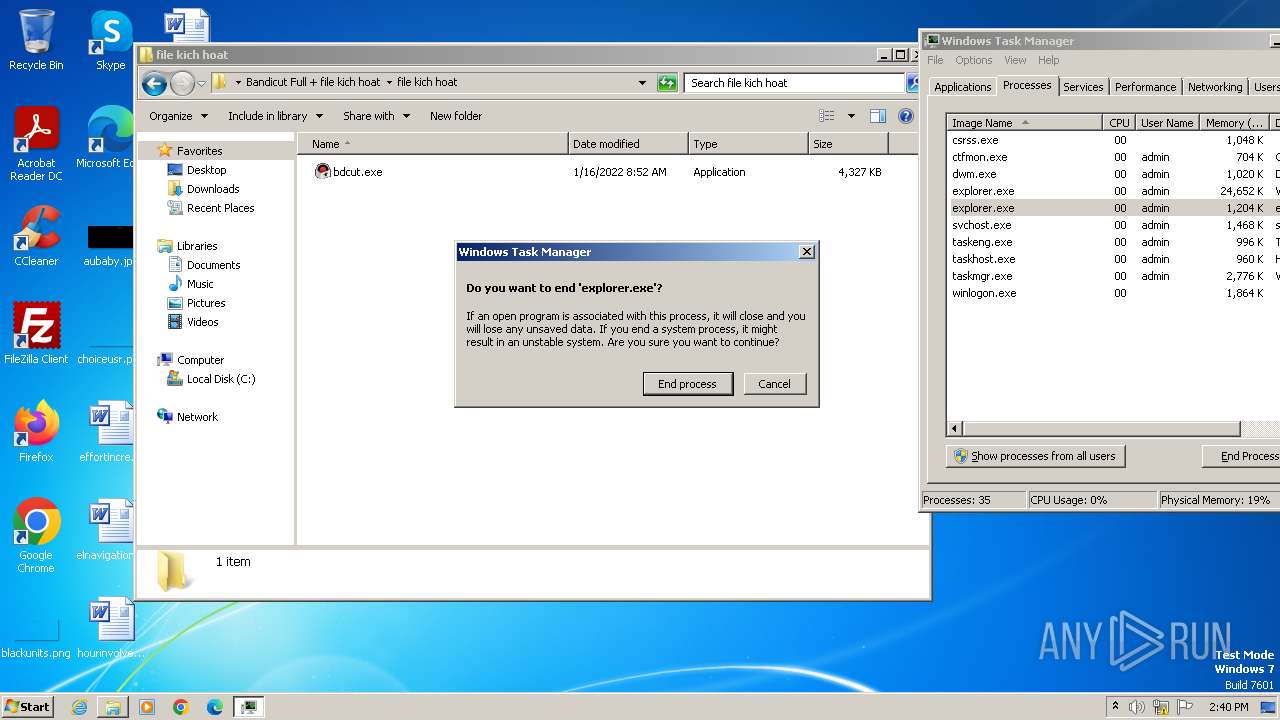
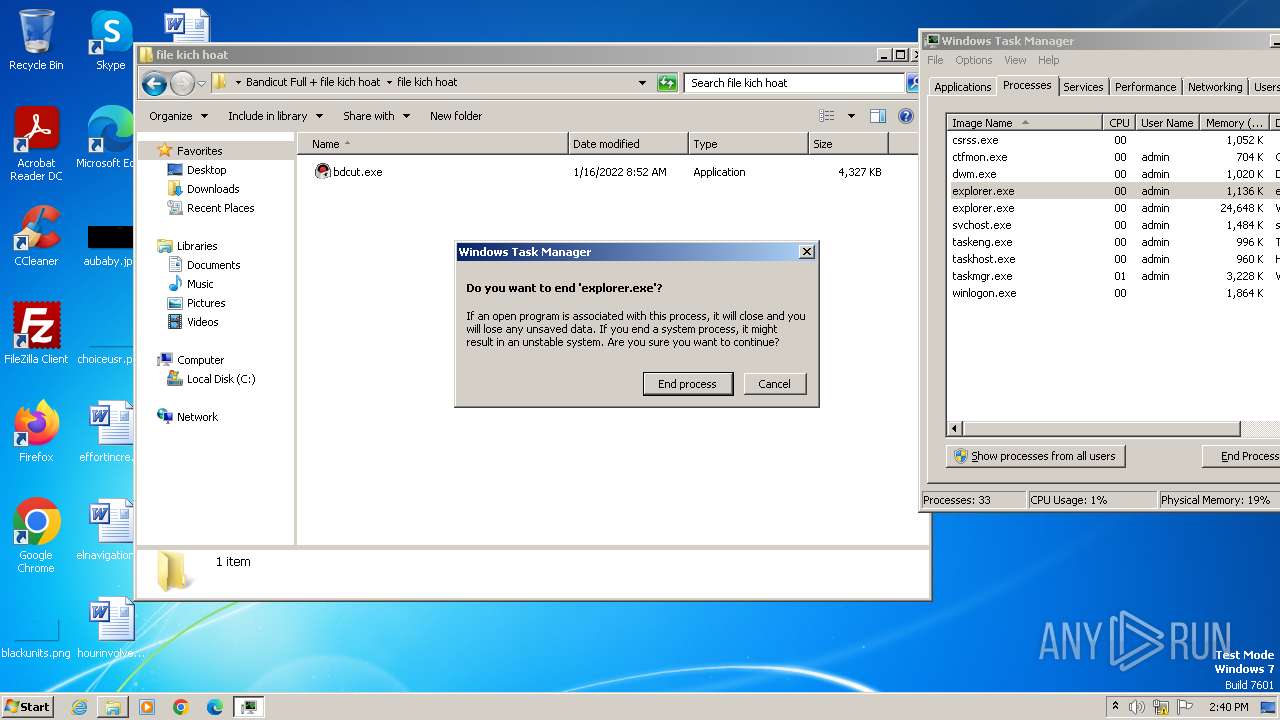
Manual execution by a user
- bdcut.exe (PID: 2240)
- taskmgr.exe (PID: 1432)
Reads the machine GUID from the registry
- bdcut.exe (PID: 2240)
- icsys.icn.exe (PID: 2232)
- spoolsv.exe (PID: 2256)
- svchost.exe (PID: 1596)
- explorer.exe (PID: 2264)
- spoolsv.exe (PID: 1980)
- explorer.exe (PID: 992)
- spoolsv.exe (PID: 736)
- spoolsv.exe (PID: 324)
- spoolsv.exe (PID: 1964)
- explorer.exe (PID: 1344)
- spoolsv.exe (PID: 2656)
Create files in a temporary directory
- bdcut.exe (PID: 2240)
- icsys.icn.exe (PID: 2232)
- spoolsv.exe (PID: 2256)
- svchost.exe (PID: 1596)
- explorer.exe (PID: 2264)
- spoolsv.exe (PID: 324)
- spoolsv.exe (PID: 1980)
- explorer.exe (PID: 992)
- spoolsv.exe (PID: 736)
- spoolsv.exe (PID: 1964)
- explorer.exe (PID: 1344)
- spoolsv.exe (PID: 2656)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3984)
Reads the computer name
- svchost.exe (PID: 1596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
56
Monitored processes
17
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | c:\windows\resources\spoolsv.exe SE | C:\Windows\resources\spoolsv.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 736 | c:\windows\resources\spoolsv.exe PR | C:\Windows\resources\spoolsv.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 860 | schtasks /create /tn "svchost" /tr "c:\windows\resources\svchost.exe" /sc daily /st 14:41 /f | C:\Windows\System32\schtasks.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
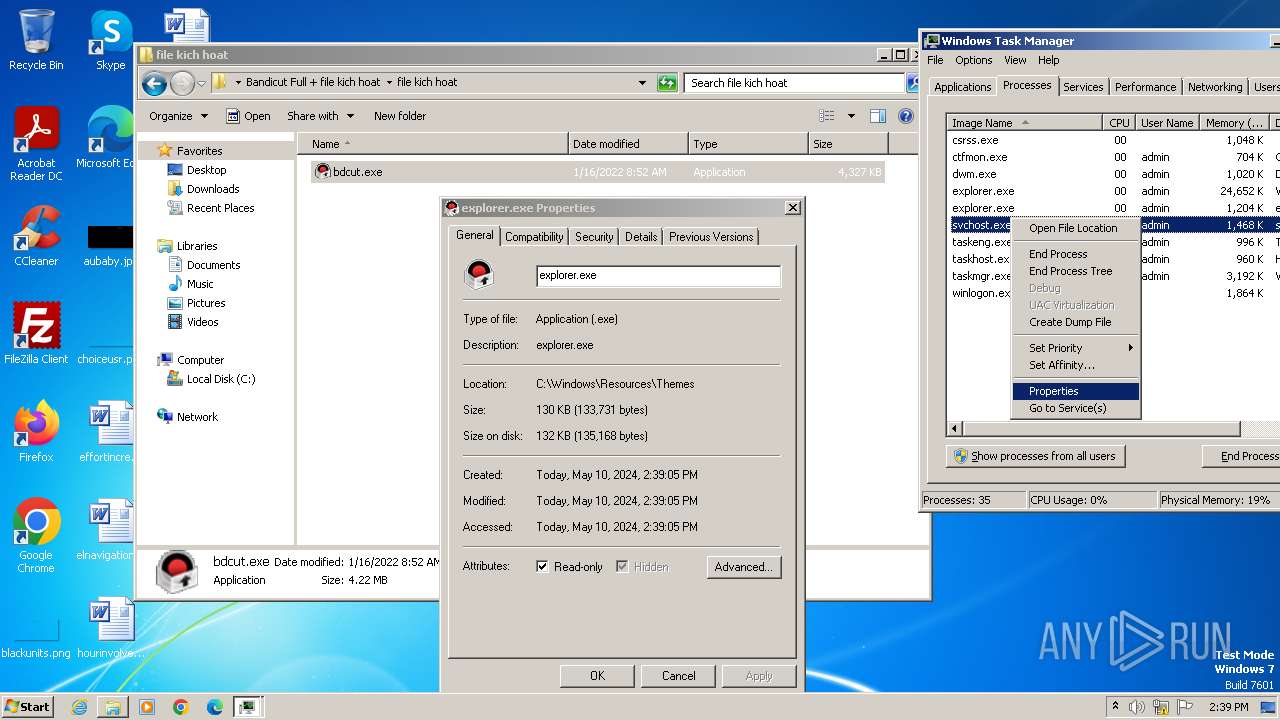
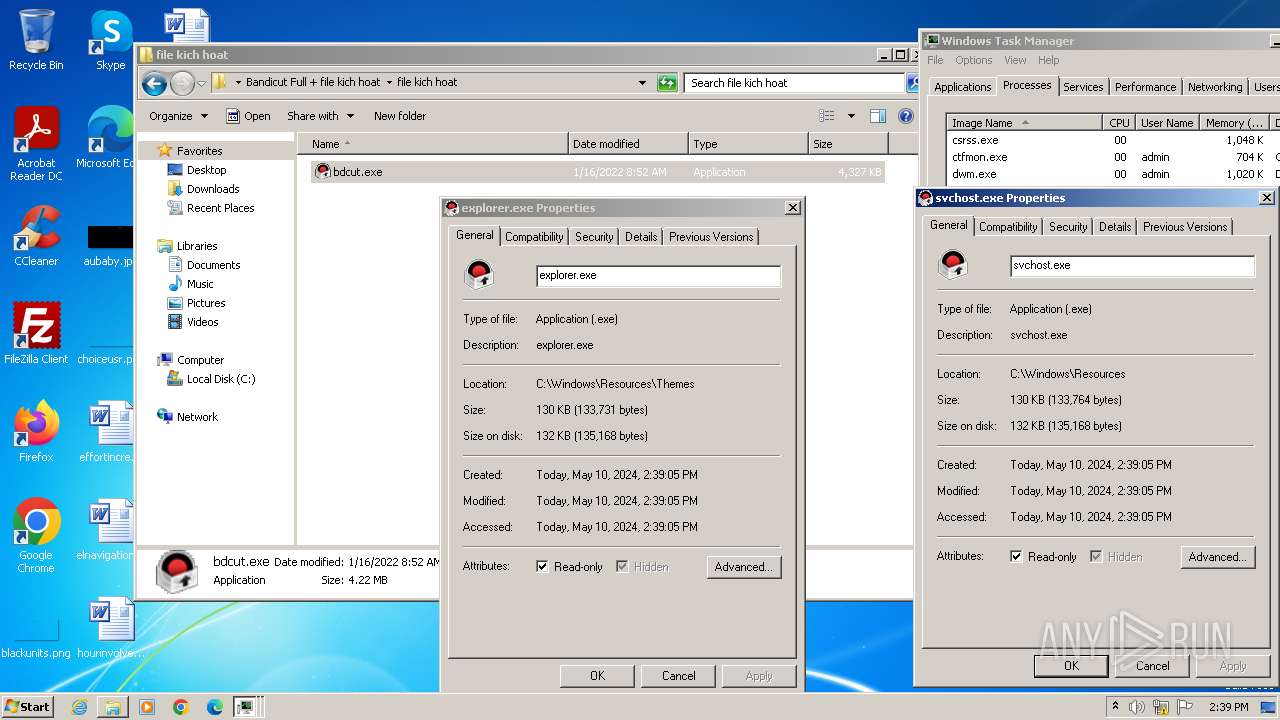
| 992 | c:\windows\resources\themes\explorer.exe | C:\Windows\resources\Themes\explorer.exe | spoolsv.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Version: 1.00 Modules
| |||||||||||||||
| 1344 | c:\windows\resources\themes\explorer.exe | C:\Windows\resources\Themes\explorer.exe | spoolsv.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.00 Modules
| |||||||||||||||
| 1432 | "C:\Windows\system32\taskmgr.exe" | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1596 | c:\windows\resources\svchost.exe | C:\Windows\resources\svchost.exe | spoolsv.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.00 Modules
| |||||||||||||||
| 1964 | c:\windows\resources\spoolsv.exe PR | C:\Windows\resources\spoolsv.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 1980 | c:\windows\resources\spoolsv.exe PR | C:\Windows\resources\spoolsv.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2232 | C:\Windows\Resources\Themes\icsys.icn.exe | C:\Windows\Resources\Themes\icsys.icn.exe | bdcut.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
5 031
Read events
4 940
Write events
83
Delete events
8
Modification events
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Bandicut Full Crack.rar | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
7
Suspicious files
9
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 736 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF4A8E79AC1ACDF3EE.TMP | — | |
MD5:— | SHA256:— | |||
| 2264 | explorer.exe | C:\windows\resources\spoolsv.exe | executable | |
MD5:C970F4A495502229943D90C7F67125C7 | SHA256:05C8452E2DEA7CFAE3668157A9CA9BBA9F258F385DD20195D28777965F913BEF | |||
| 2232 | icsys.icn.exe | C:\windows\resources\themes\explorer.exe | executable | |
MD5:955AAA7C0635F41A7EB2C70F44151687 | SHA256:4316B180B8D3FDA376E8DEF586B20A545F76149C6B88788690A3CC14219141F7 | |||
| 2240 | bdcut.exe | C:\Users\admin\AppData\Local\Temp\~DF82F80B65FF79E284.TMP | binary | |
MD5:D047CD39186E445497E1E070A6B175DA | SHA256:5869A24450D383CAE56F75AA6A5A5489A26BDE6D8A51A46A631663F8AC19F960 | |||
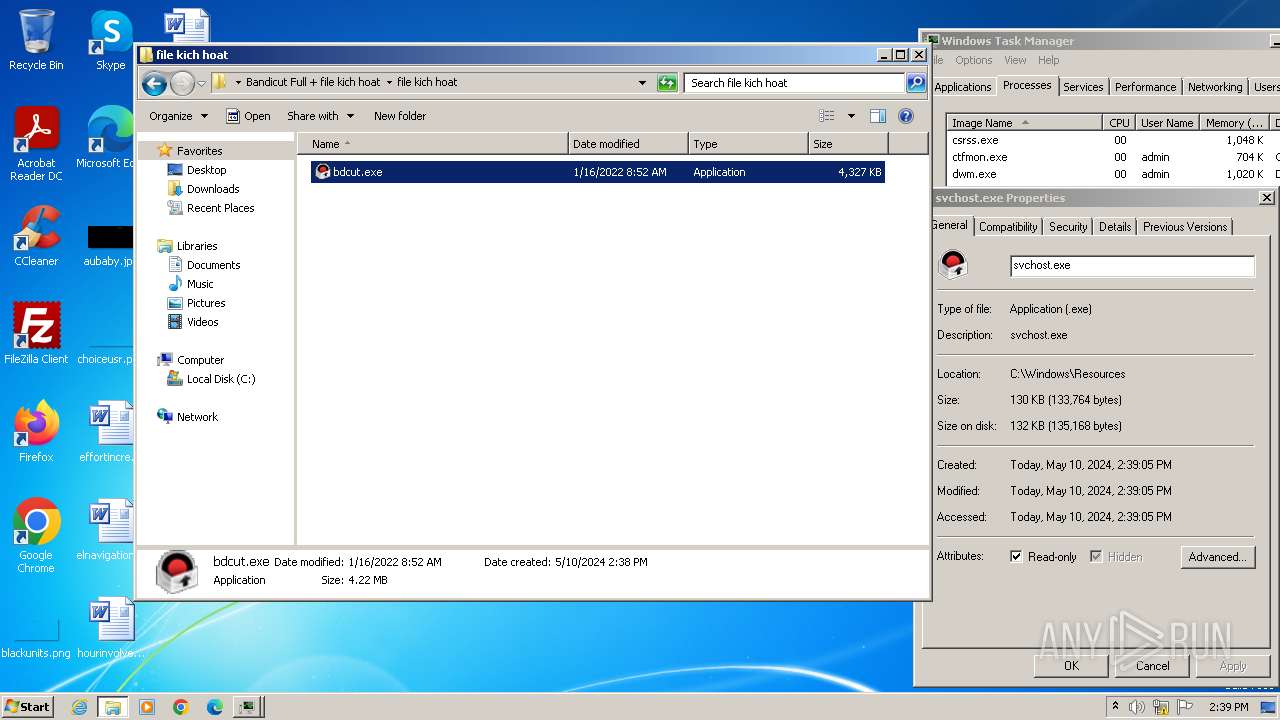
| 2240 | bdcut.exe | C:\users\admin\desktop\bandicut full + file kich hoat\file kich hoat\bdcut.exe | executable | |
MD5:D597126BFBB5B290A3900FF3BD6E1175 | SHA256:B3303F8484DA9D35B37CF961527447C90739B7A3BD60D46C6D41C65C278A657D | |||
| 324 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DFCE422EB127883876.TMP | binary | |
MD5:819041909569F9A81477F6DFA80BFE30 | SHA256:D6B1BF57641F66C94F60DC6DFEE9B2811344DC74747F0A13ABB3AFE79695775F | |||
| 2264 | explorer.exe | C:\Users\admin\AppData\Local\Temp\~DF9782081669CFE6AB.TMP | binary | |
MD5:1E6AF6327736E3508F1C50506326C220 | SHA256:A941B5DA057560690B11153765184E0F92983148611048F3FDADA662054E0EFD | |||
| 2232 | icsys.icn.exe | C:\Users\admin\AppData\Local\Temp\~DFE7B5D8FC61A4D46E.TMP | binary | |
MD5:7EBDDE653172B22E0A2B65C29AE98CF4 | SHA256:9B6F0D09B1859AADB402CE2C9021429411F92AAB62B556B1C5E1921D7AC6ADED | |||
| 2256 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DFF7AC40E1CC6CB266.TMP | binary | |
MD5:7EBDDE653172B22E0A2B65C29AE98CF4 | SHA256:9B6F0D09B1859AADB402CE2C9021429411F92AAB62B556B1C5E1921D7AC6ADED | |||
| 2240 | bdcut.exe | C:\Windows\Resources\Themes\icsys.icn.exe | executable | |
MD5:2C21EA65F781634AFB3166404C5288E5 | SHA256:3ED207FDEEE295835A906244FCD58201BA32D3D0C07A6D06F21F4CD4559EC8A4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |