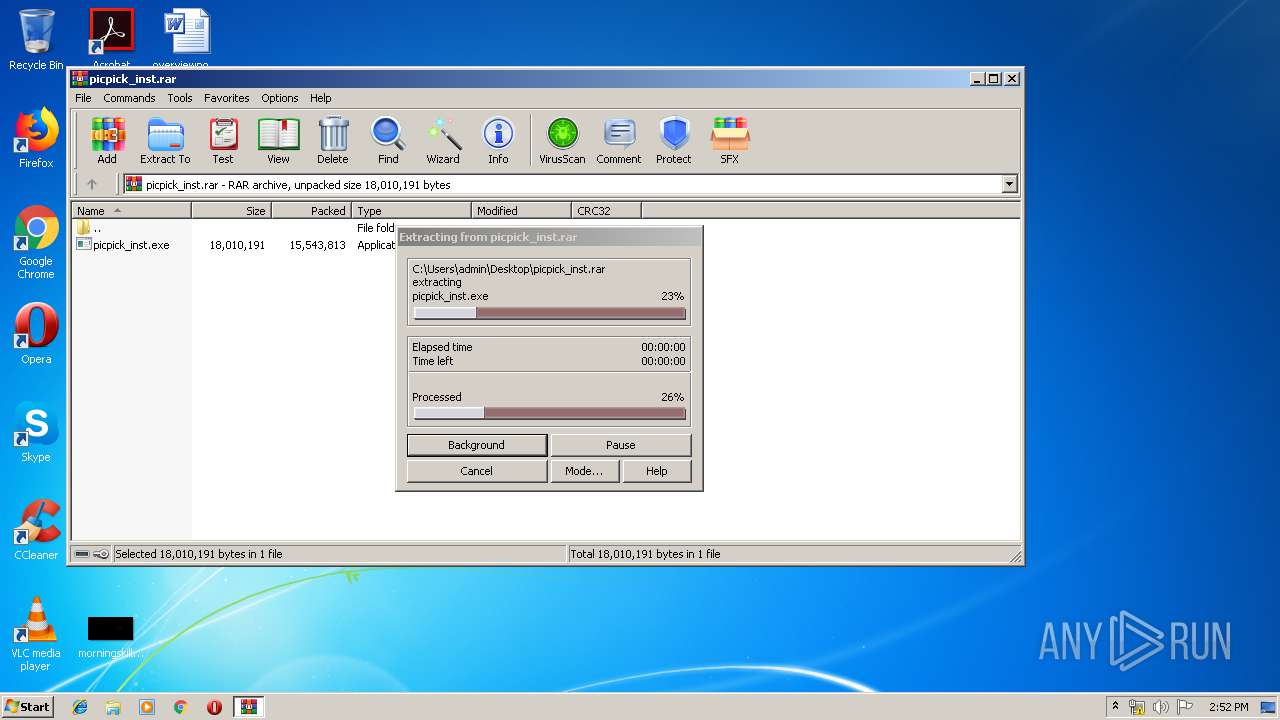
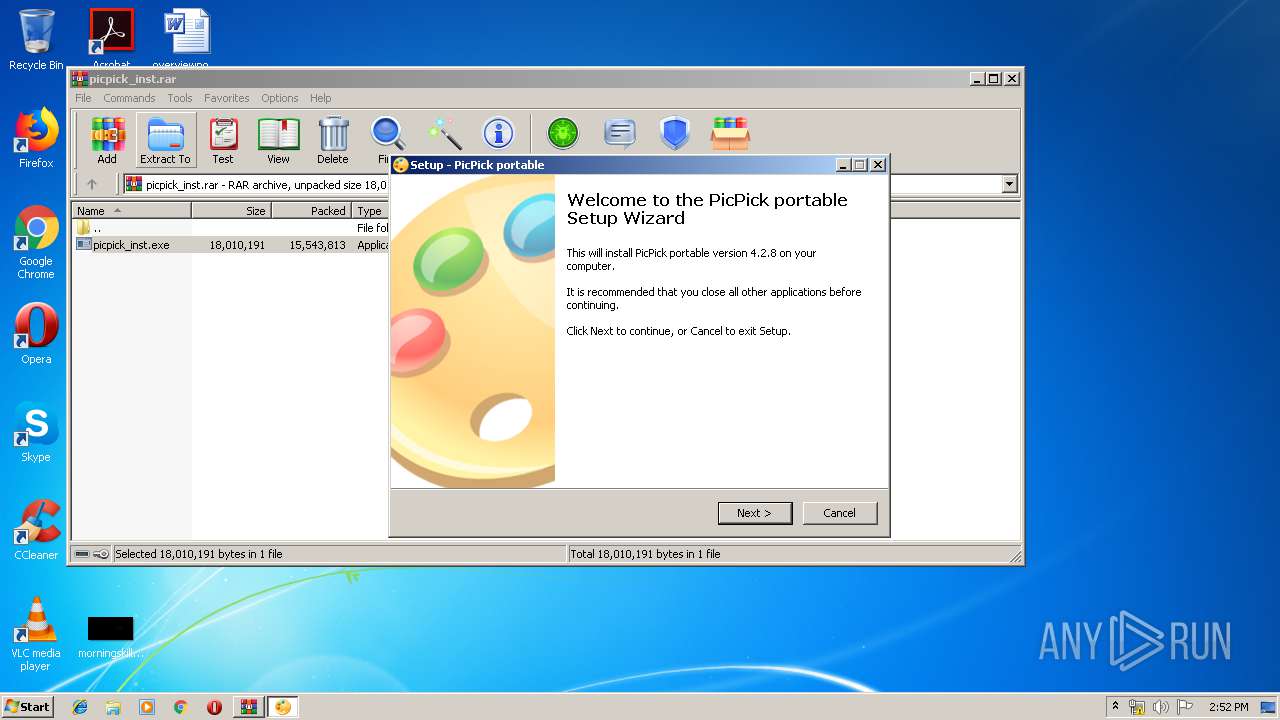
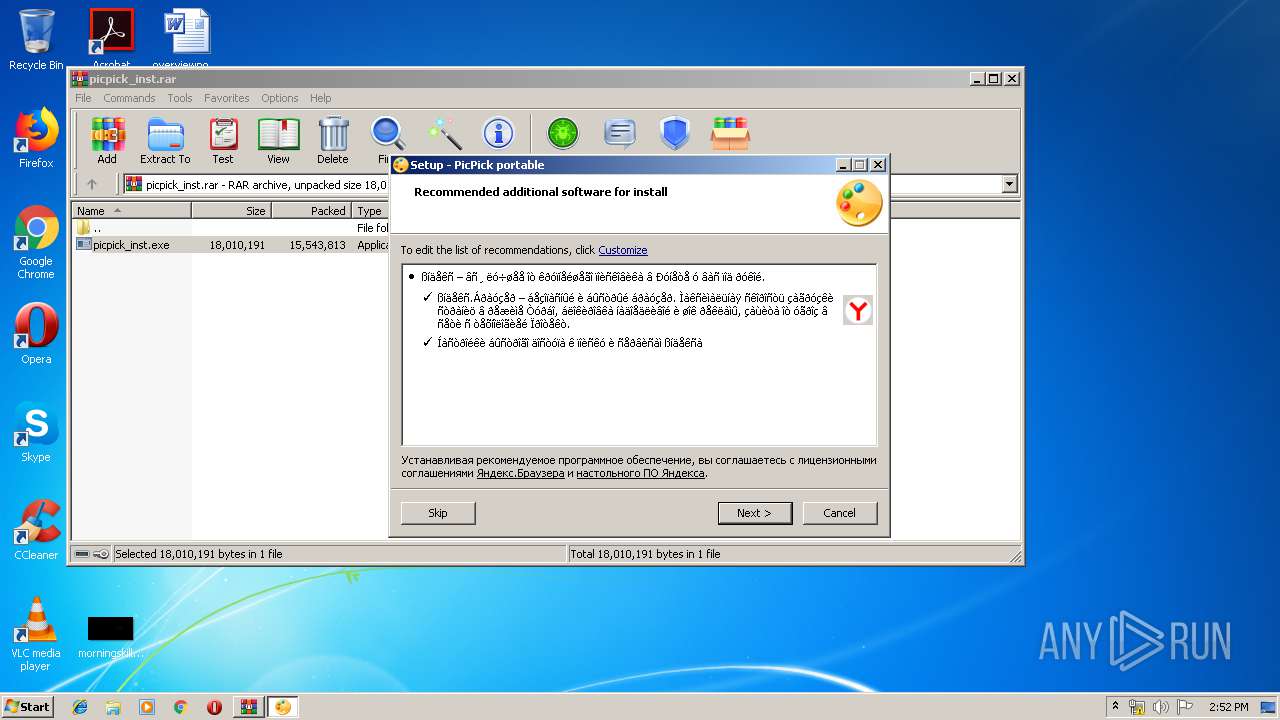
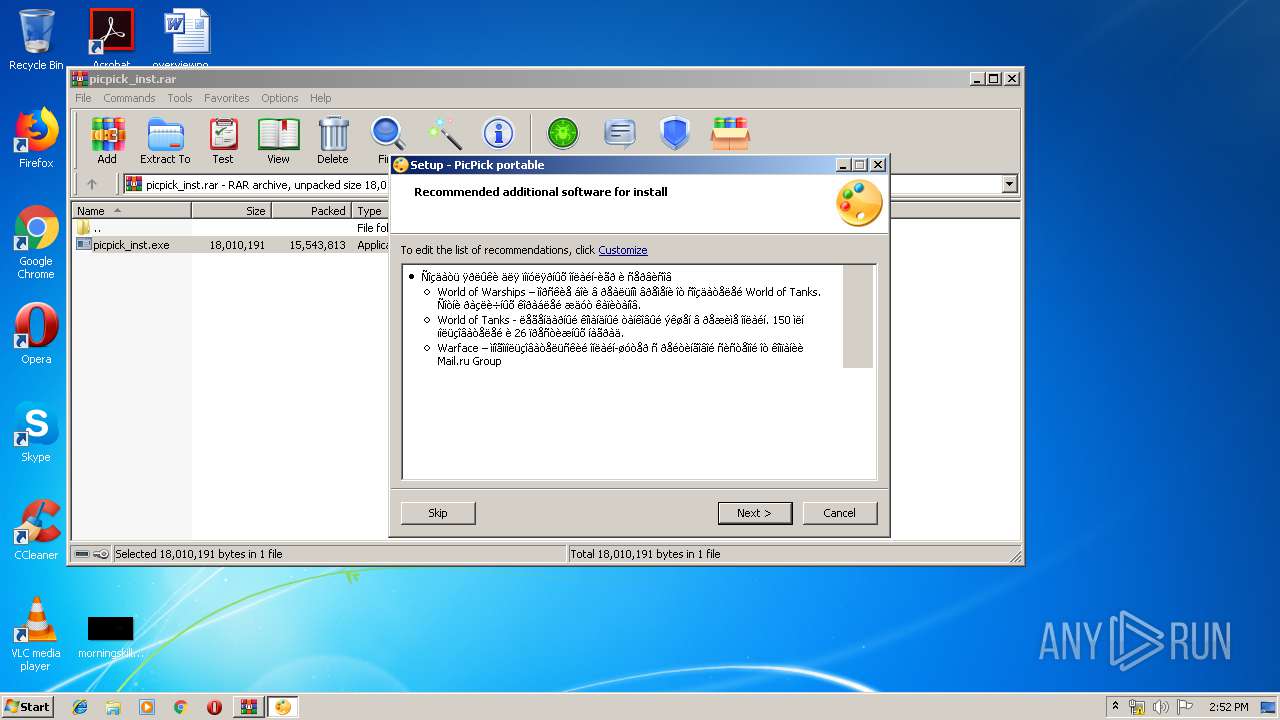
| File name: | picpick_inst.rar |
| Full analysis: | https://app.any.run/tasks/703f4dba-f42b-4baf-ac0a-a8cb4eee08e2 |
| Verdict: | Malicious activity |
| Analysis date: | October 25, 2019, 13:50:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 2BB6AD81A88AA5D9B75C018ABB20AFB3 |
| SHA1: | D7A762ADC497845BDD168FB1AE3EC5C783027CB2 |
| SHA256: | 3930F1F6D3ED8157BD2EB1ECC03383727CB4793E2BACD42891FD5845191DF6D4 |
| SSDEEP: | 393216:ETIsrqDI9UwZoUBNNtPNfVv3KB8BVWUWVCL5Hl+LXN0:CI/IRy8DL5a8rM4+L90 |
MALICIOUS
Application was dropped or rewritten from another process
- picpick_inst.exe (PID: 3580)
- picpick_inst.exe (PID: 3244)
- PicPickPortable.exe (PID: 3660)
Changes settings of System certificates
- picpick_inst.tmp (PID: 3992)
Runs injected code in another process
- shortcut.exe (PID: 2828)
Application was injected by another process
- explorer.exe (PID: 352)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2640)
- explorer.exe (PID: 352)
SUSPICIOUS
Creates files in the user directory
- explorer.exe (PID: 352)
- picpick_inst.tmp (PID: 3992)
Reads Internet Cache Settings
- explorer.exe (PID: 352)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4000)
- picpick_inst.exe (PID: 3580)
- picpick_inst.exe (PID: 3244)
- picpick_inst.tmp (PID: 3992)
- PicPickPortable.exe (PID: 3660)
- PicPickPortable.tmp (PID: 1800)
Reads the Windows organization settings
- picpick_inst.tmp (PID: 3992)
- PicPickPortable.tmp (PID: 1800)
Adds / modifies Windows certificates
- picpick_inst.tmp (PID: 3992)
Reads Windows owner or organization settings
- picpick_inst.tmp (PID: 3992)
- PicPickPortable.tmp (PID: 1800)
INFO
Loads dropped or rewritten executable
- picpick_inst.tmp (PID: 3992)
Application was dropped or rewritten from another process
- picpick_inst.tmp (PID: 3992)
- picpick_inst.tmp (PID: 2764)
- PicPickPortable.tmp (PID: 1800)
- shortcut.exe (PID: 2828)
- shortcut.exe (PID: 2212)
- shortcut.exe (PID: 2120)
Creates a software uninstall entry
- picpick_inst.tmp (PID: 3992)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
52
Monitored processes
12
Malicious processes
3
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 352 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1800 | "C:\Users\admin\AppData\Local\Temp\is-BLITN.tmp\PicPickPortable.tmp" /SL5="$2023E,8814977,401920,C:\Users\admin\AppData\Local\Temp\is-18TNC.tmp\Soft\PicPickPortable.exe" | C:\Users\admin\AppData\Local\Temp\is-BLITN.tmp\PicPickPortable.tmp | PicPickPortable.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2120 | "C:\Users\admin\AppData\Local\Temp\is-18TNC.tmp\shortcut.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Warface.lnk" | C:\Users\admin\AppData\Local\Temp\is-18TNC.tmp\shortcut.exe | — | picpick_inst.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2212 | "C:\Users\admin\AppData\Local\Temp\is-18TNC.tmp\shortcut.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\World of Tanks.lnk" | C:\Users\admin\AppData\Local\Temp\is-18TNC.tmp\shortcut.exe | — | picpick_inst.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2640 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2764 | "C:\Users\admin\AppData\Local\Temp\is-1FD1J.tmp\picpick_inst.tmp" /SL5="$8015C,17179333,401920,C:\Users\admin\AppData\Local\Temp\Rar$EXa4000.5928\picpick_inst.exe" | C:\Users\admin\AppData\Local\Temp\is-1FD1J.tmp\picpick_inst.tmp | — | picpick_inst.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2828 | "C:\Users\admin\AppData\Local\Temp\is-18TNC.tmp\shortcut.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\World of Warships.lnk" | C:\Users\admin\AppData\Local\Temp\is-18TNC.tmp\shortcut.exe | — | picpick_inst.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3244 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4000.5928\picpick_inst.exe" /SPAWNWND=$E01AE /NOTIFYWND=$8015C | C:\Users\admin\AppData\Local\Temp\Rar$EXa4000.5928\picpick_inst.exe | picpick_inst.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: PicPick portable Setup (r17) Exit code: 0 Version: 4.2.8 Modules
| |||||||||||||||
| 3580 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4000.5928\picpick_inst.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4000.5928\picpick_inst.exe | WinRAR.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: PicPick portable Setup (r17) Exit code: 0 Version: 4.2.8 Modules
| |||||||||||||||
| 3660 | "C:\Users\admin\AppData\Local\Temp\is-18TNC.tmp\Soft\PicPickPortable.exe" | C:\Users\admin\AppData\Local\Temp\is-18TNC.tmp\Soft\PicPickPortable.exe | picpick_inst.tmp | ||||||||||||
User: admin Company: PicPick Integrity Level: HIGH Description: PicPick portable Setup Exit code: 0 Version: Modules
| |||||||||||||||
Total events
11 273
Read events
11 117
Write events
146
Delete events
10
Modification events
| (PID) Process: | (4000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4000) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\picpick_inst.rar | |||
| (PID) Process: | (4000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (352) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (352) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
18
Suspicious files
0
Text files
37
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 352 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\290532160612e071.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 4000 | WinRAR.exe | C:\Users\admin\Desktop\picpick_inst.exe | executable | |
MD5:— | SHA256:— | |||
| 3992 | picpick_inst.tmp | C:\Users\admin\AppData\Local\Temp\is-18TNC.tmp\CommonPrechecks.ini | text | |
MD5:— | SHA256:— | |||
| 4000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4000.5928\picpick_inst.exe | executable | |
MD5:— | SHA256:— | |||
| 3992 | picpick_inst.tmp | C:\Users\admin\AppData\Local\Temp\is-18TNC.tmp\CallbackCtrl.dll | executable | |
MD5:F07E819BA2E46A897CFABF816D7557B2 | SHA256:68F42A7823ED7EE88A5C59020AC52D4BBCADF1036611E96E470D986C8FAA172D | |||
| 3244 | picpick_inst.exe | C:\Users\admin\AppData\Local\Temp\is-2SVQL.tmp\picpick_inst.tmp | executable | |
MD5:— | SHA256:— | |||
| 3992 | picpick_inst.tmp | C:\Users\admin\AppData\Local\Temp\is-18TNC.tmp\is-KC55J.ini | text | |
MD5:— | SHA256:— | |||
| 3992 | picpick_inst.tmp | C:\Users\admin\AppData\Local\Temp\is-18TNC.tmp\Yandex\Settings.ini | text | |
MD5:— | SHA256:— | |||
| 352 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 3992 | picpick_inst.tmp | C:\Users\admin\AppData\Local\Temp\is-18TNC.tmp\KIS_tmp1\Settings.ini | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3992 | picpick_inst.tmp | 172.217.16.200:443 | ssl.google-analytics.com | Google Inc. | US | whitelisted |
3992 | picpick_inst.tmp | 79.137.94.254:443 | reqbus.ru | OVH SAS | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
reqbus.ru |
| whitelisted |
ssl.google-analytics.com |
| whitelisted |