| download: | /TrotzHD/Windows-Maintenance-Tool/releases/download/v3.0/Windows.Maintenance.Tool.v3.0.zip |
| Full analysis: | https://app.any.run/tasks/1f727872-66aa-48f8-a5b9-dac6517d320f |
| Verdict: | Malicious activity |
| Analysis date: | June 24, 2025, 12:33:55 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
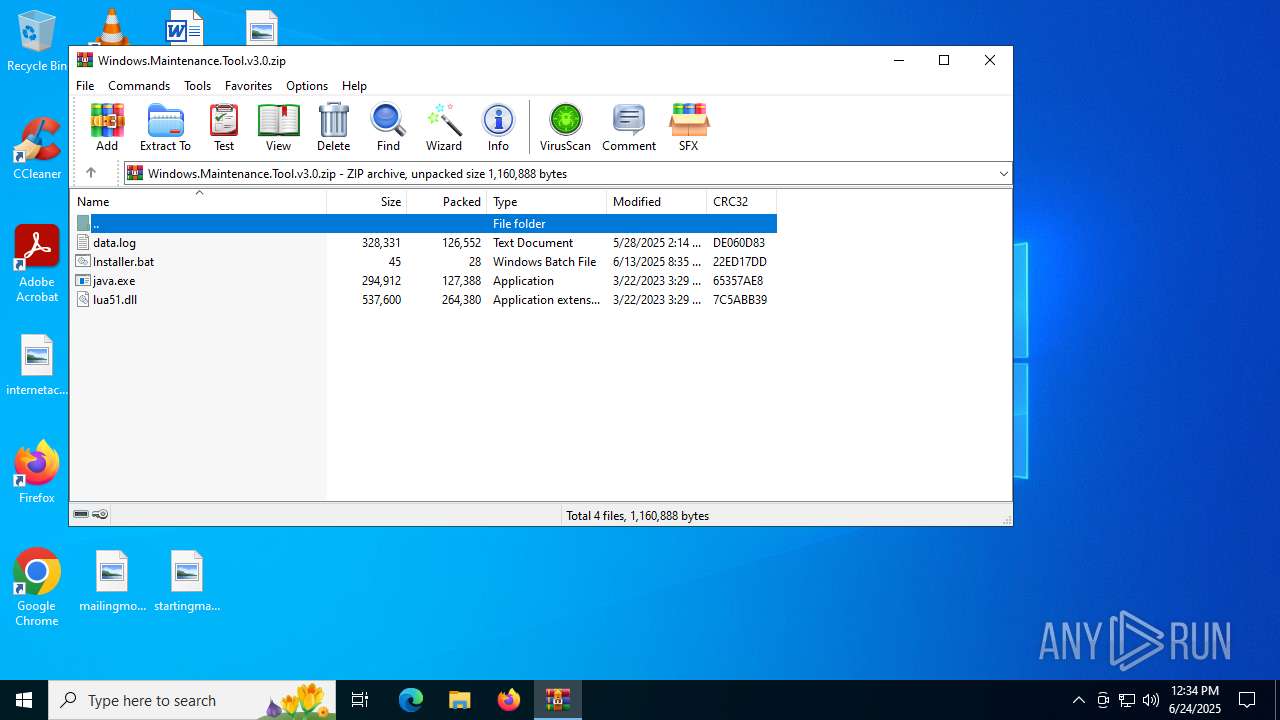
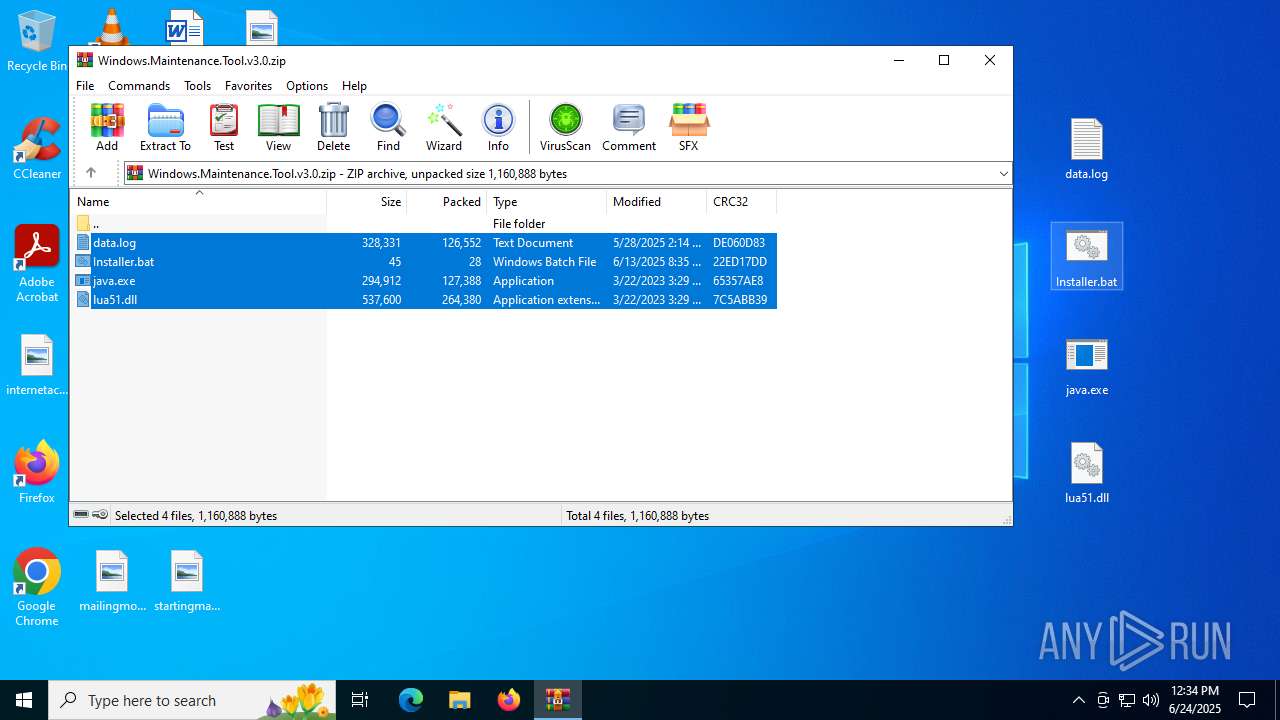
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C928A7C3CBAF0E6D32F06088F0EC1FEB |
| SHA1: | 109671E8F5DBDD20DD419C1019B43D843CBB5C19 |
| SHA256: | 392C9A8527F5A867BBC542479B91ECEE64C9B70EE253AE7DD1A1280A27EC6FB3 |
| SSDEEP: | 24576:WBYHUMOl7C4tvsk8vdRjR+fwwEg65nTiMGwAj:WBY0MOl7C4tvsZvdRjR+fwwEH5nTiMGB |
MALICIOUS
Generic archive extractor
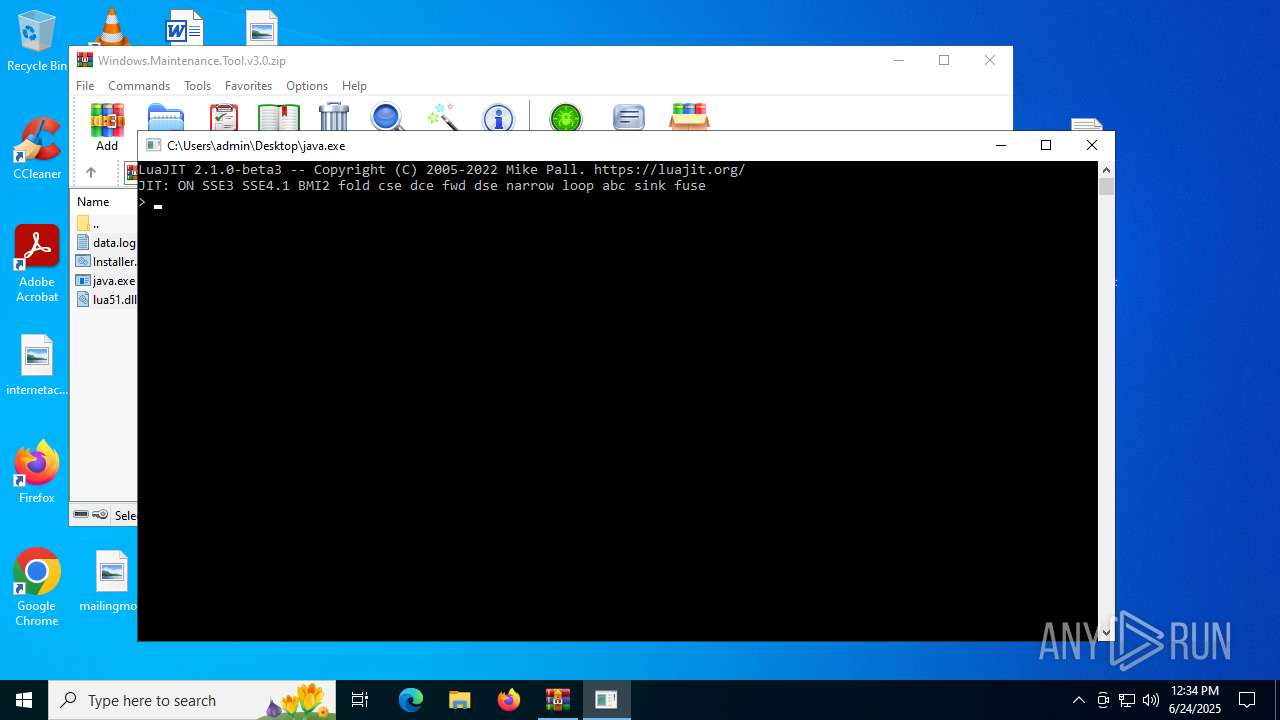
- WinRAR.exe (PID: 440)
SUSPICIOUS
Reads security settings of Internet Explorer
- java.exe (PID: 3392)
Connects to the server without a host name
- java.exe (PID: 3392)
Checks for external IP
- svchost.exe (PID: 2200)
- java.exe (PID: 3392)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 440)
Reads the computer name
- java.exe (PID: 3392)
Checks supported languages
- java.exe (PID: 3392)
- java.exe (PID: 2272)
Manual execution by a user
- cmd.exe (PID: 1328)
- java.exe (PID: 2272)
Creates files or folders in the user directory
- java.exe (PID: 3392)
Checks proxy server information
- java.exe (PID: 3392)
Reads the machine GUID from the registry
- java.exe (PID: 3392)
Reads the software policy settings
- java.exe (PID: 3392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:28 07:14:22 |
| ZipCRC: | 0xde060d83 |
| ZipCompressedSize: | 126552 |
| ZipUncompressedSize: | 328331 |
| ZipFileName: | data.log |
Total processes
144
Monitored processes
9
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Windows.Maintenance.Tool.v3.0.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1328 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Installer.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2272 | "C:\Users\admin\Desktop\java.exe" | C:\Users\admin\Desktop\java.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225786 Modules
| |||||||||||||||
| 3392 | java.exe data.log | C:\Users\admin\Desktop\java.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4264 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4788 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5244 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6724 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 744
Read events
4 730
Write events
14
Delete events
0
Modification events
| (PID) Process: | (440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Windows.Maintenance.Tool.v3.0.zip | |||
| (PID) Process: | (440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (440) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
2
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa440.25679\lua51.dll | executable | |
MD5:FF65A68D6B4266553CAE3E3111F4CFB3 | SHA256:04DC80D84F1452DC76E1962C10DA1420A9D5CEB6E3A03691D274F98043BA74AF | |||
| 440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa440.25679\java.exe | executable | |
MD5:3C366CCD3AC11442F71378E7AB2D266F | SHA256:89C8803CADD3F1D7C423B40C1731B9BA0BAD8A0469F71665C010CB5DA0386241 | |||
| 440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa440.25679\data.log | text | |
MD5:2ED91E48A8A0B731CA3A3F6A7708256D | SHA256:AA75668D43D97C6563EAF94C599FCEB1A11D880806C1269067970A7B1941CE4B | |||
| 3392 | java.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\json[1].json | binary | |
MD5:9EBA77D430D6FD6B7958CF0DD9ADCE95 | SHA256:BDA5C6568139D67A11A0CDBD811C29AFC43151D260992F336380D06242F32D70 | |||
| 440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa440.25679\Installer.bat | text | |
MD5:16416B9212B6547F86A5DF884A8DDADE | SHA256:71735140ADFBE1BB5CE03F549B59F1E225449FD377536A0C3FDACC744C462BA9 | |||
| 3392 | java.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_0FB9553B978E7F00C6B2309507DEB64A | binary | |
MD5:9A932DB4BE34BC4873AEB321F229A36F | SHA256:6080A7C13BBC4832799E81CB412384868A3646B64E006DAEB0F14272F94B8AAE | |||
| 3392 | java.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_0FB9553B978E7F00C6B2309507DEB64A | der | |
MD5:F67F6B9534D9F2130A9BAA302AA65D2F | SHA256:C8350395988594DC13822C0A088E780F99FB162F711B7107FFB14D063AA83E4A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
27
DNS requests
18
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3392 | java.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3392 | java.exe | POST | 200 | 77.105.164.178:80 | http://77.105.164.178/api/YTAsODYsODIsOWQsYTEsODgsOTAsOTUsNjUsN2Qs | unknown | — | — | unknown |
6004 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6004 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3392 | java.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | whitelisted |
5896 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6368 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
1268 | svchost.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
5896 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5896 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ip-api.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3392 | java.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2200 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2200 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |