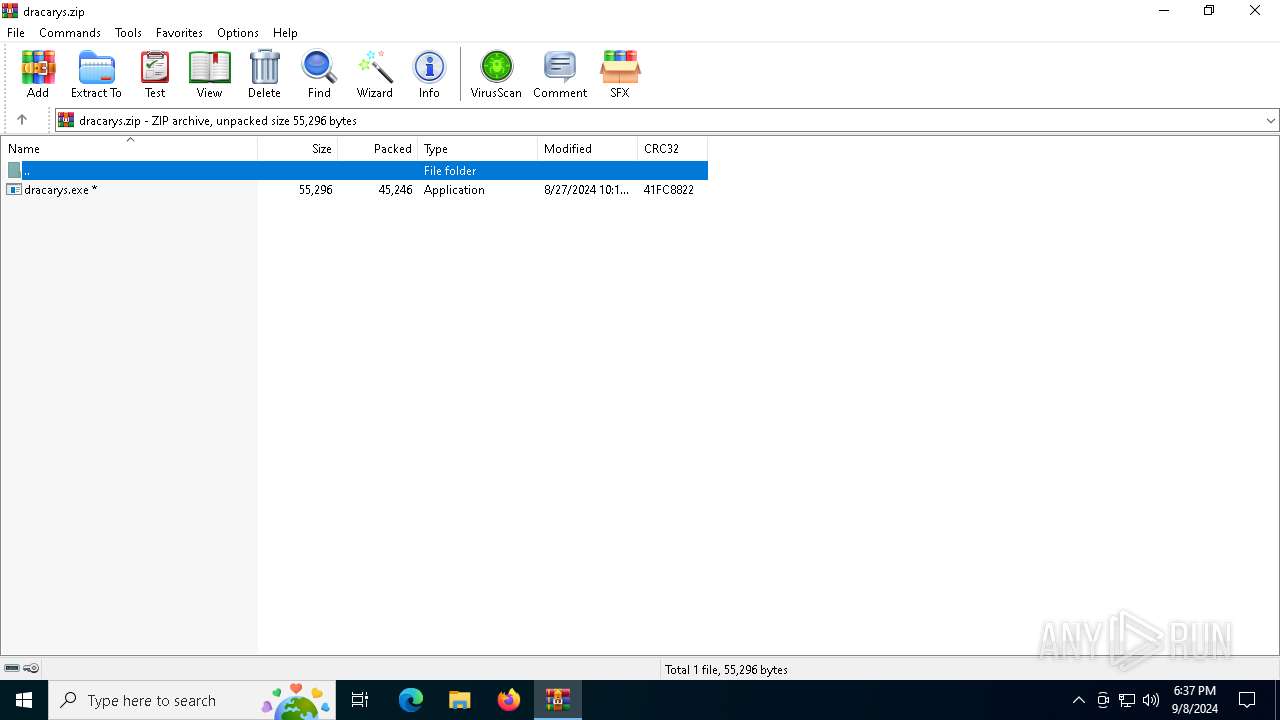
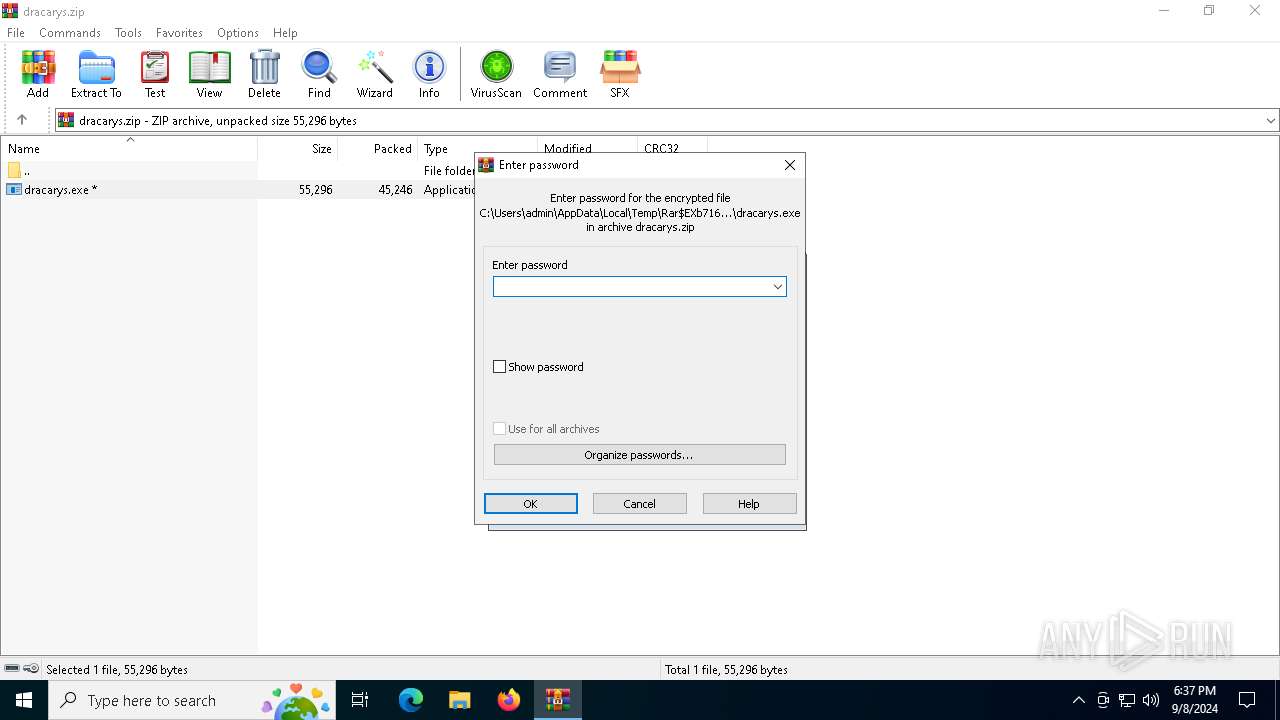
| File name: | dracarys.zip |
| Full analysis: | https://app.any.run/tasks/87720e46-8316-4ec1-8e91-0a5e66754bf0 |
| Verdict: | Malicious activity |
| Analysis date: | September 08, 2024, 18:37:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | D5B4DFFFEB9D4497C8D587DAE338614E |
| SHA1: | 21C211BE81489C32118D52E27052F3E4BC57E55D |
| SHA256: | 392024C66D9604240E6A359CDFD0E3E8C51114B47B4B58FBB4B70E9DC742B64E |
| SSDEEP: | 768:ux/fcEulEmjJgDjLnMtvW/bc+94yGFmzLq3fXQvYIrnI+BzxUQ7q2Zl6764/U6TC:a/ffnmj+jAWw+94yX6PgAIrxtVIp5sfP |
MALICIOUS
Changes the autorun value in the registry
- HdAudio.exe (PID: 780)
SUSPICIOUS
Read disk information to detect sandboxing environments
- AppLaunch.exe (PID: 5160)
- AppLaunch.exe (PID: 5708)
- AppLaunch.exe (PID: 376)
- AppLaunch.exe (PID: 3984)
Executable content was dropped or overwritten
- cmd.exe (PID: 4820)
- svchost.exe (PID: 5096)
- dracarys.exe (PID: 6960)
Process drops legitimate windows executable
- svchost.exe (PID: 5096)
Deletes system .NET executable
- svchost.exe (PID: 5096)
- svchost.exe (PID: 6452)
- svchost.exe (PID: 6752)
Suspicious files were dropped or overwritten
- svchost.exe (PID: 5096)
Reads security settings of Internet Explorer
- HdAudio.exe (PID: 780)
- WinRAR.exe (PID: 7164)
- dracarys.exe (PID: 6960)
Starts CMD.EXE for commands execution
- dracarys.exe (PID: 6960)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7164)
Potential modification of remote process state (Base64 Encoded 'SetThreadContext')
- dracarys.exe (PID: 6960)
The process uses the downloaded file
- WinRAR.exe (PID: 7164)
- dracarys.exe (PID: 6960)
- HdAudio.exe (PID: 780)
Potential remote process memory writing (Base64 Encoded 'WriteProcessMemory')
- dracarys.exe (PID: 6960)
Potential remote process memory interaction (Base64 Encoded 'VirtualAllocEx')
- dracarys.exe (PID: 6960)
Process checks computer location settings
- dracarys.exe (PID: 6960)
- HdAudio.exe (PID: 780)
Reads the computer name
- dracarys.exe (PID: 6960)
- HdAudio.exe (PID: 780)
Checks supported languages
- dracarys.exe (PID: 6960)
- HdAudio.exe (PID: 780)
- AppLaunch.exe (PID: 5160)
- AppLaunch.exe (PID: 5708)
- winhv.exe (PID: 2580)
- AppLaunch.exe (PID: 3984)
- AppLaunch.exe (PID: 376)
Creates files or folders in the user directory
- dracarys.exe (PID: 6960)
Create files in a temporary directory
- svchost.exe (PID: 5096)
Potential remote process memory reading (Base64 Encoded 'ReadProcessMemory')
- dracarys.exe (PID: 6960)
Reads the machine GUID from the registry
- dracarys.exe (PID: 6960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:08:27 03:12:14 |
| ZipCRC: | 0x41fc8822 |
| ZipCompressedSize: | 45246 |
| ZipUncompressedSize: | 55296 |
| ZipFileName: | dracarys.exe |
Total processes
144
Monitored processes
17
Malicious processes
3
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 376 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\AppLaunch.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\AppLaunch.exe | — | dracarys.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET ClickOnce Launch Utility Exit code: 0 Version: 2.0.50727.9149 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
| 780 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\HdAudio.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\HdAudio.exe | dracarys.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: High Definition Audio Function Driver Modules
| |||||||||||||||
| 1748 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2492 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2580 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\winhv.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\winhv.exe | — | HdAudio.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 3984 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\AppLaunch.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\AppLaunch.exe | — | dracarys.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET ClickOnce Launch Utility Exit code: 0 Version: 2.0.50727.9149 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
| 4056 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4820 | "C:\Windows\System32\cmd.exe" /c copy "C:\Users\admin\AppData\Local\Temp\Rar$EXb7164.45011\dracarys.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\winhv.exe" | C:\Windows\SysWOW64\cmd.exe | dracarys.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5096 | C:\WINDOWS\syswow64\svchost.exe | C:\Windows\SysWOW64\svchost.exe | AppLaunch.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 801
Read events
3 717
Write events
84
Delete events
0
Modification events
| (PID) Process: | (7164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (7164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\dracarys.zip | |||
| (PID) Process: | (7164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7164) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (780) HdAudio.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | High Definition Audio Function Driver |
Value: C:\Users\admin\AppData\Roaming\Microsoft\Windows\HdAudio.exe | |||
Executable files
4
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7164 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7164.45011\dracarys.exe | executable | |
MD5:E1CAB624E9D6C4B6E5EF005E3AE7F687 | SHA256:1B7B13C9772E0823736C5A8AC32DAFFDFB6E819C5335077CC81FBD7A42E461A7 | |||
| 4820 | cmd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\winhv.exe | executable | |
MD5:E1CAB624E9D6C4B6E5EF005E3AE7F687 | SHA256:1B7B13C9772E0823736C5A8AC32DAFFDFB6E819C5335077CC81FBD7A42E461A7 | |||
| 6960 | dracarys.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\HdAudio.exe | executable | |
MD5:7B0949E97DF559AC2253B244B9F7A788 | SHA256:C10DA28DC73A4687CB21609F02DF340BD6497CCD236B9891D78BF512A3DE766F | |||
| 5096 | svchost.exe | C:\Users\admin\AppData\Local\Temp\mscrwa.cmd | executable | |
MD5:454501A66AD6E85175A6757573D79F8B | SHA256:7FD4F35AFF4A0D4BFAAE3A5DFB14B94934276DF0E96D1A417A8F3693915E72C8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
27
DNS requests
18
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1776 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6164 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6608 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6608 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6164 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6424 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6164 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6164 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1776 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1776 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.update.microsoft.com |
| whitelisted |
fbconnect.zapto.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.zapto .org |
5096 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.zapto .org |