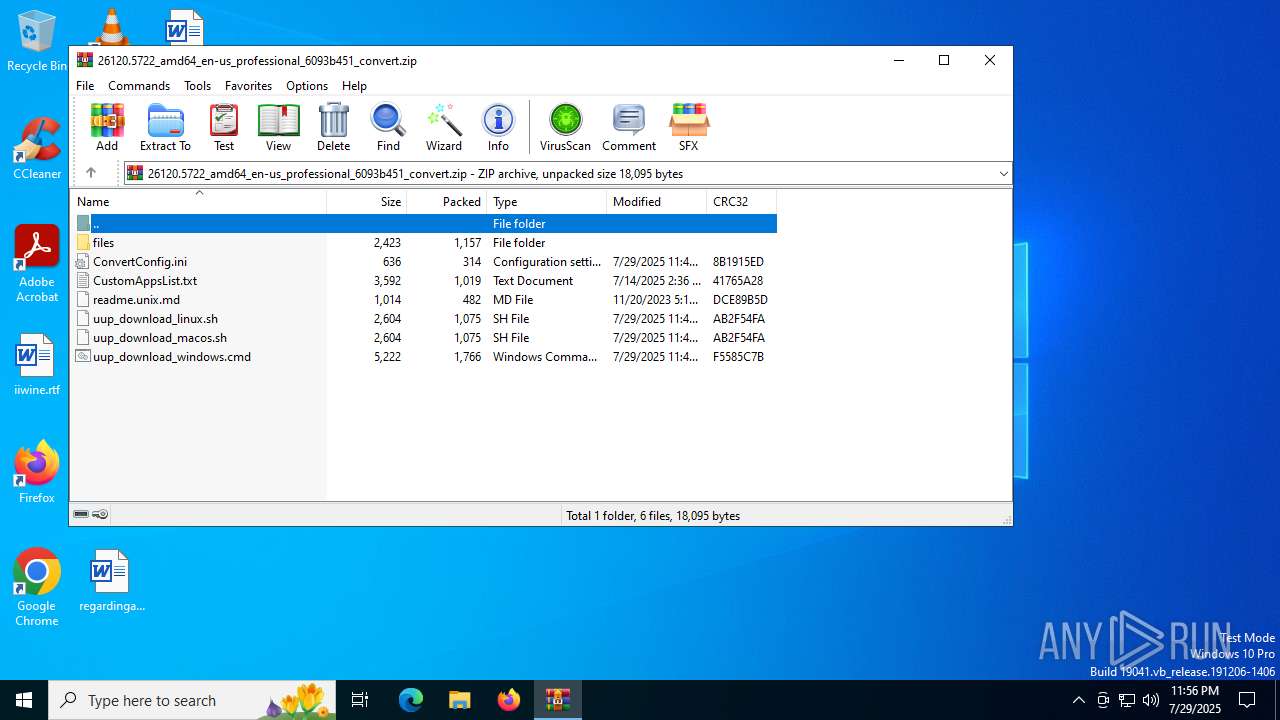
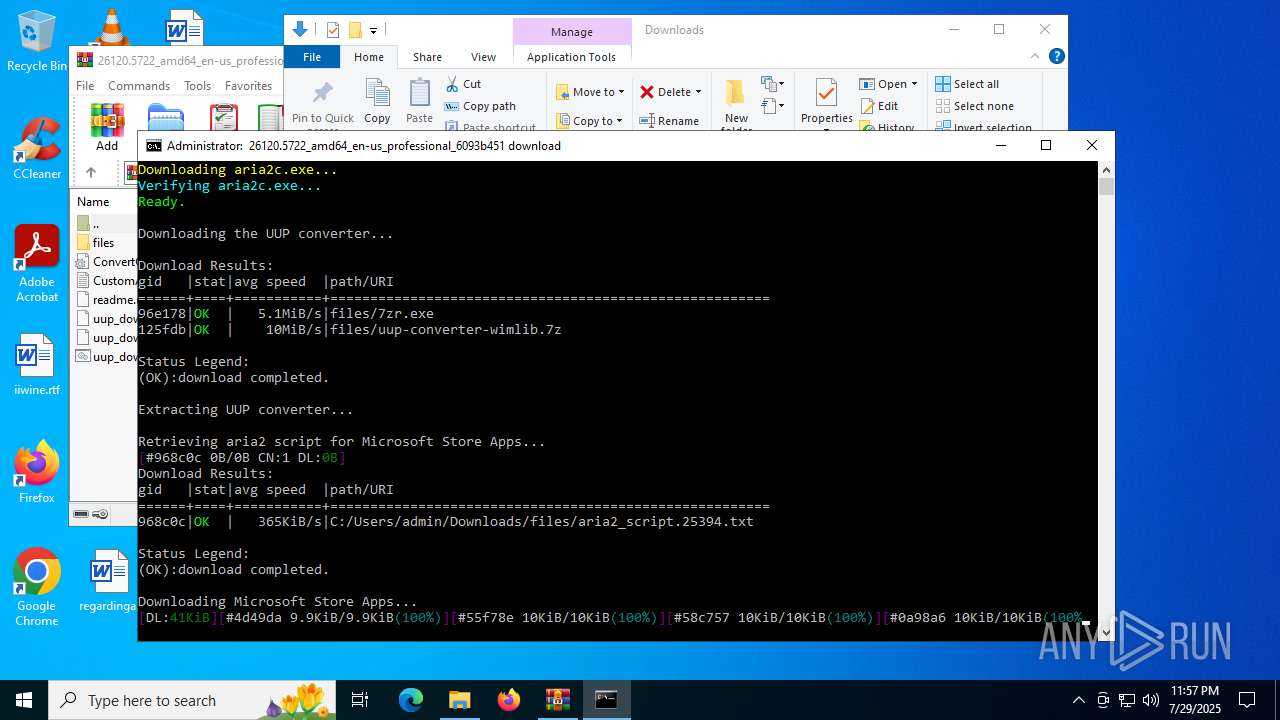
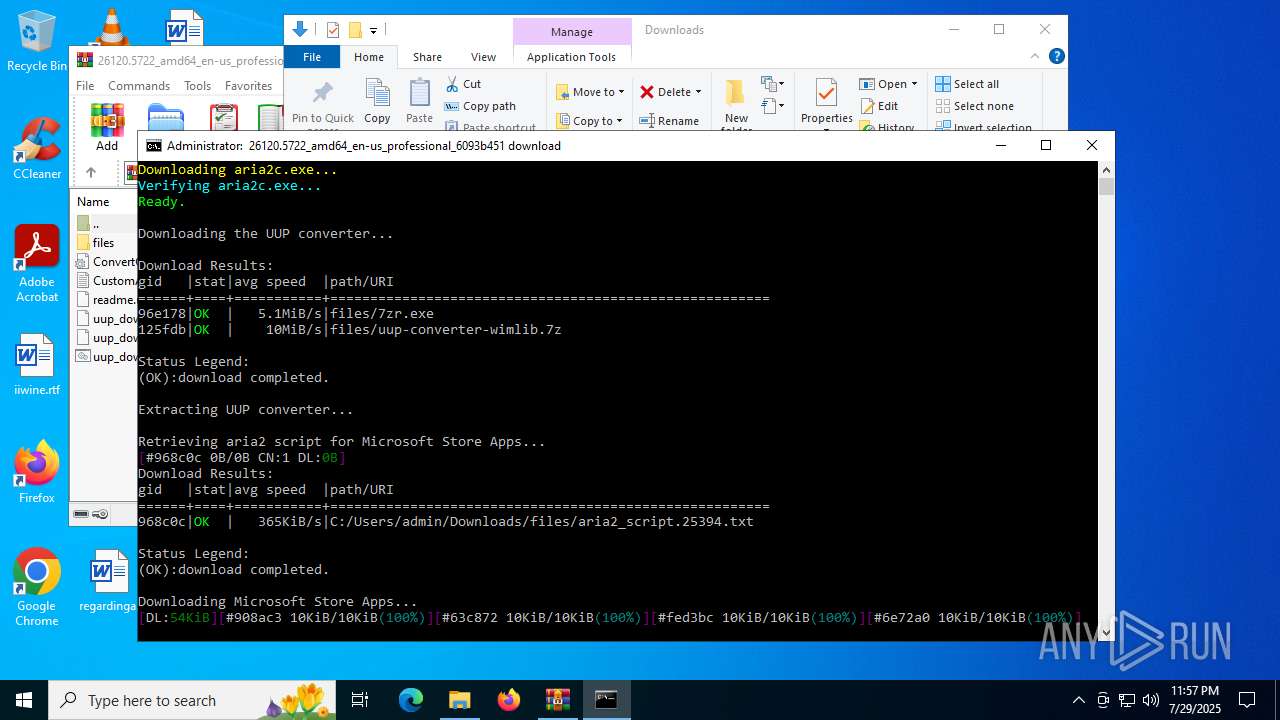
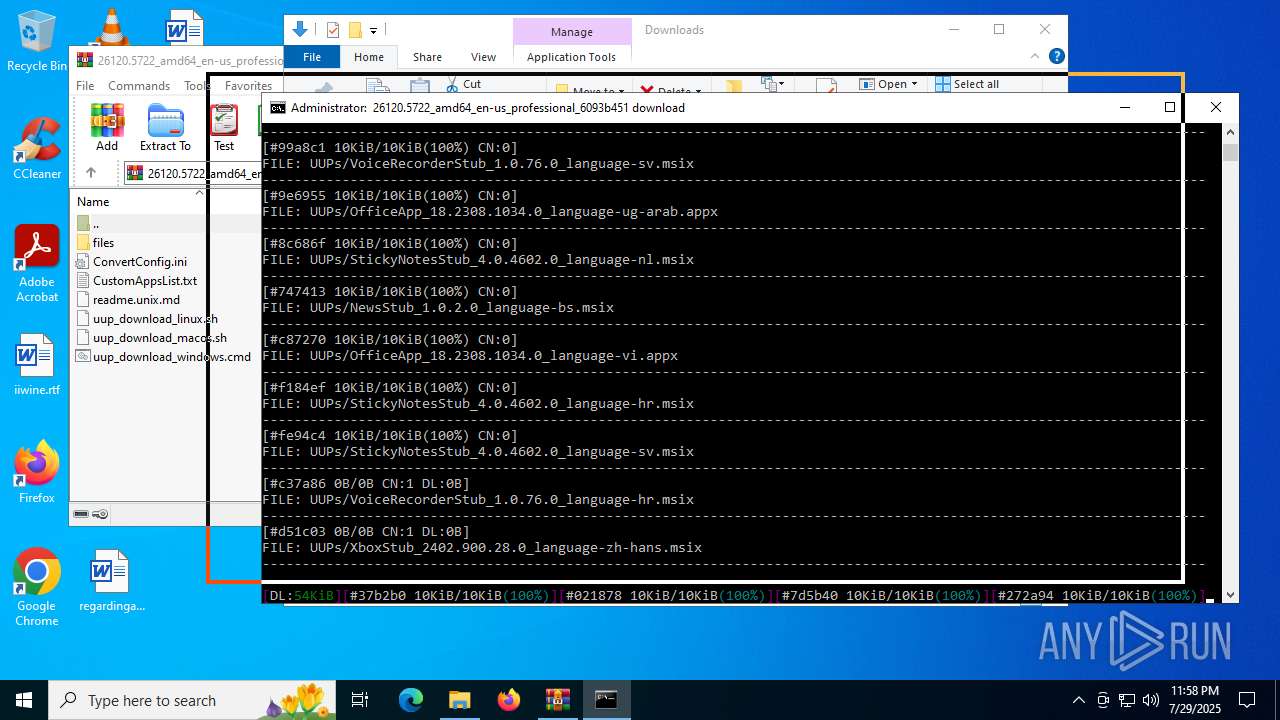
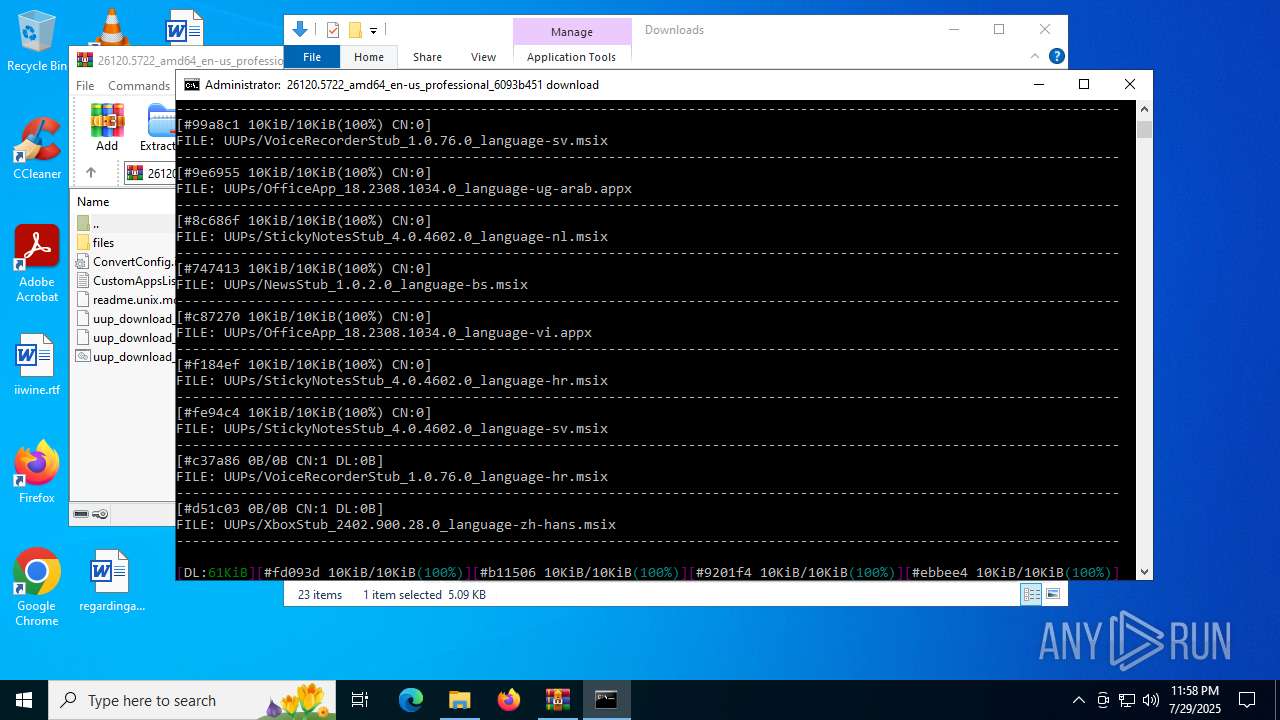
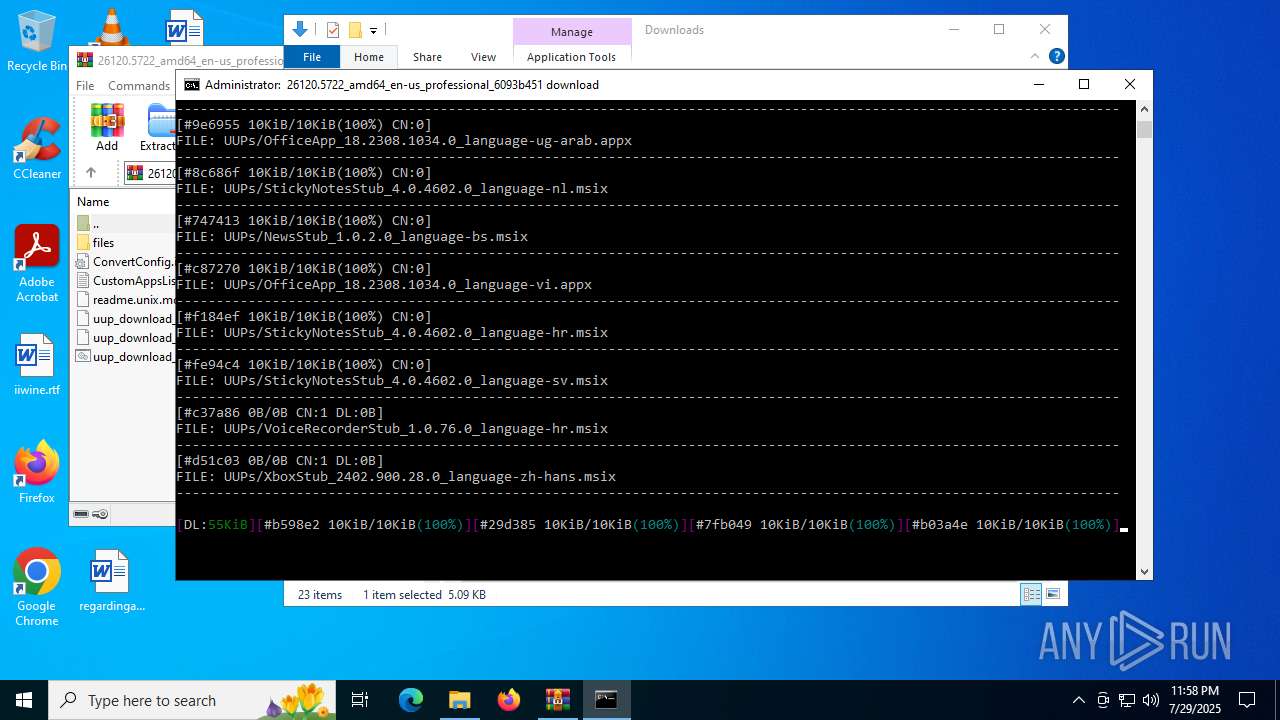
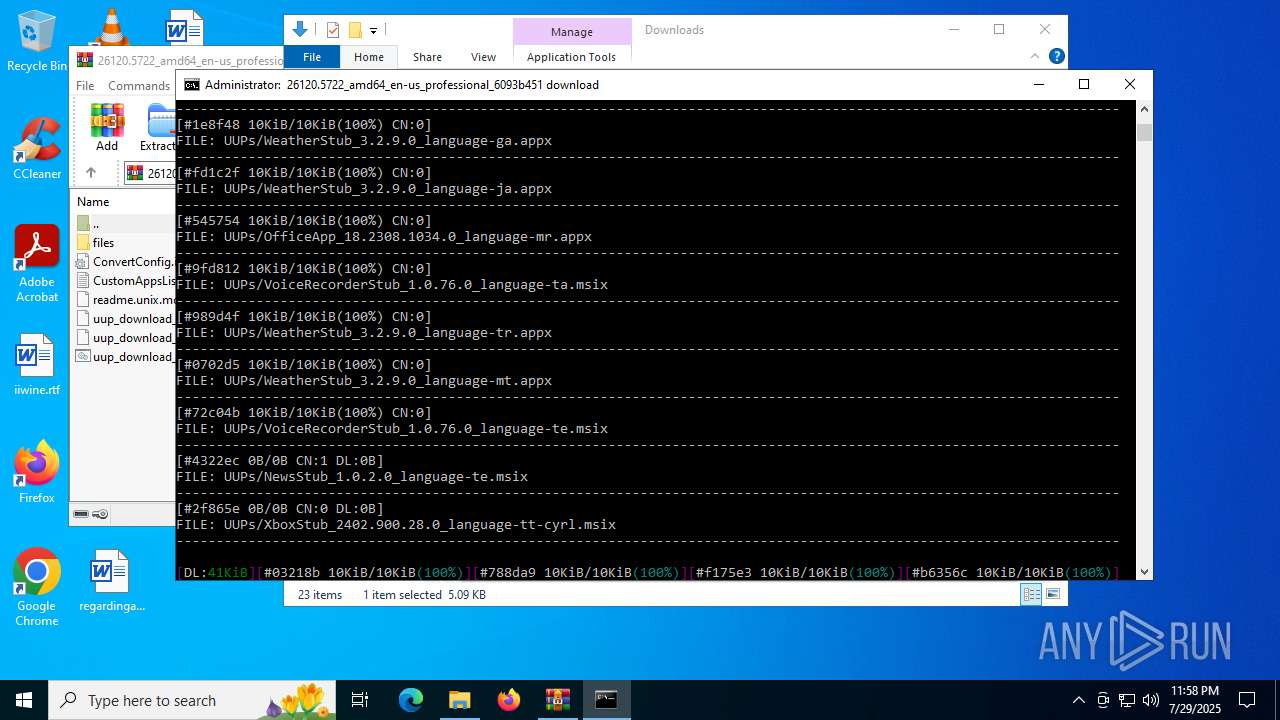
| File name: | 26120.5722_amd64_en-us_professional_6093b451_convert.zip |
| Full analysis: | https://app.any.run/tasks/83485878-bd7d-4c74-9509-9aadaf88b9c7 |
| Verdict: | Malicious activity |
| Analysis date: | July 29, 2025, 23:56:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 56B61EDC44A2968EC481C0AE8962E040 |
| SHA1: | 46793FCF3DD2866C9AECDA0C1287DF63CE1DF9B0 |
| SHA256: | 391BD13EB6CC997F5D4D5611BA24BBC6C0E925435E38294906483D9E3F73BDF4 |
| SSDEEP: | 192:n5BbpolgO1kHqQAOFsO1kHqQAOF1ztpNxtrDPKOLgHOt55RYe1B48NH8vksy:nrbpoqoQsoQ1VxL/DvYe1B48NH8vksy |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5456)
Changes powershell execution policy (Unrestricted)
- cmd.exe (PID: 6868)
SUSPICIOUS
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 1212)
- cmd.exe (PID: 6868)
Starts process via Powershell
- powershell.exe (PID: 1520)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1212)
- cmd.exe (PID: 6868)
Executing commands from ".cmd" file
- powershell.exe (PID: 1520)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 1520)
- cmd.exe (PID: 6868)
The process executes Powershell scripts
- cmd.exe (PID: 6868)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 3556)
The executable file from the user directory is run by the CMD process
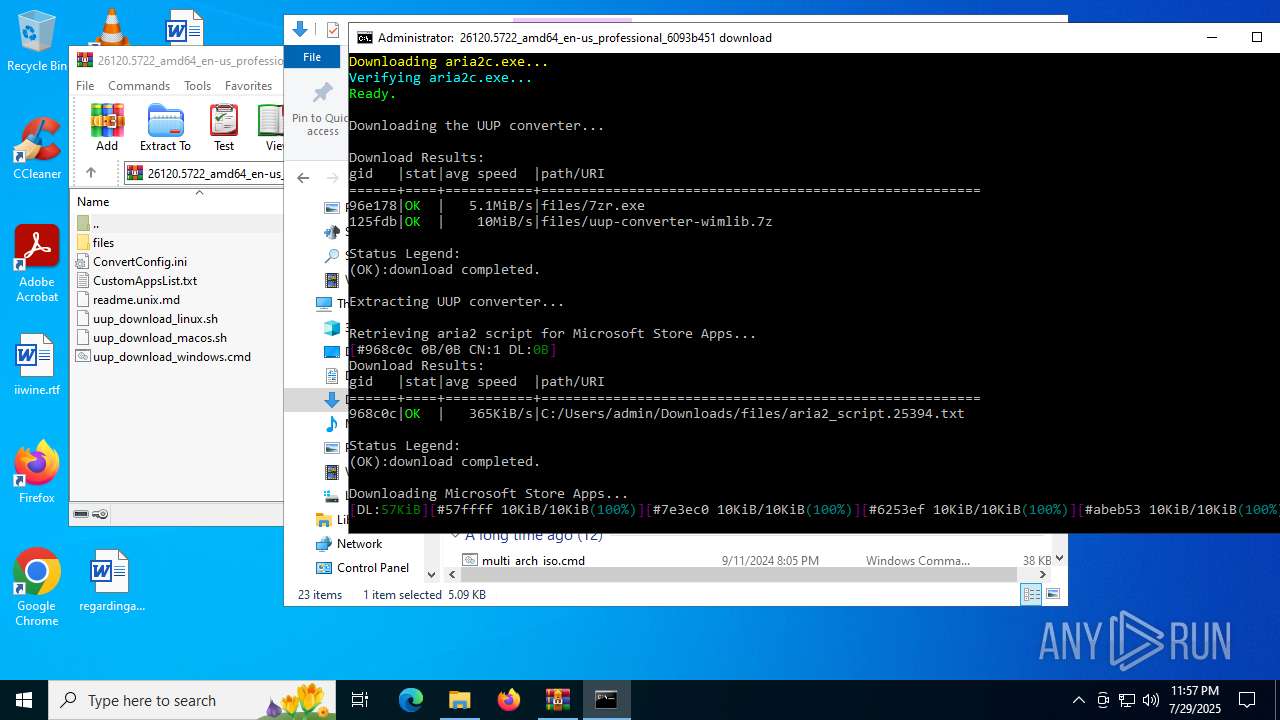
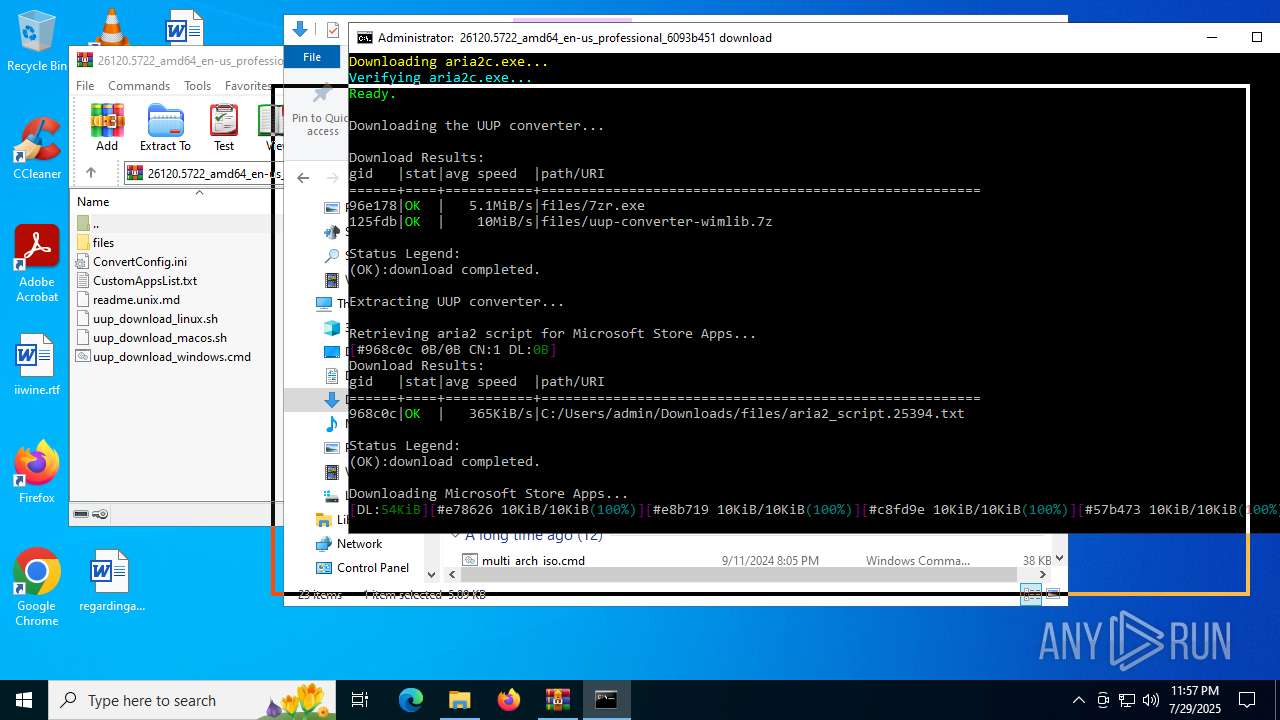
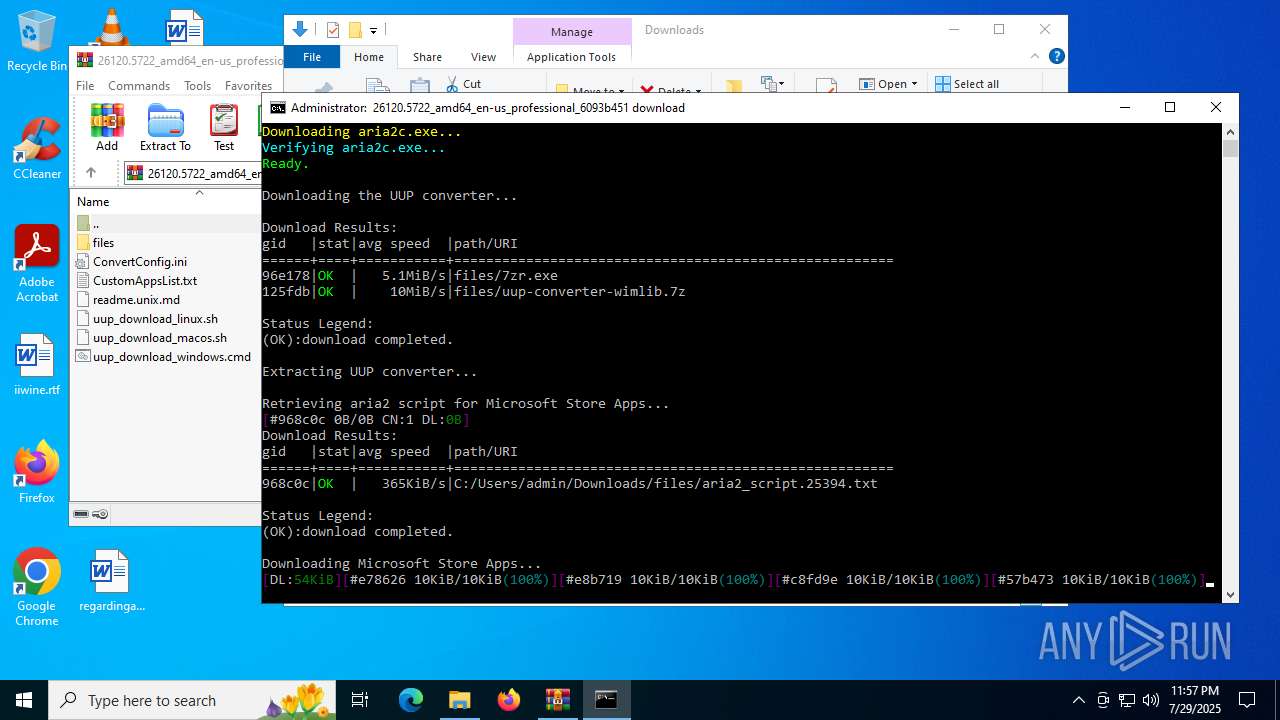
- aria2c.exe (PID: 4580)
- 7zr.exe (PID: 4916)
- aria2c.exe (PID: 7164)
- aria2c.exe (PID: 6504)
Executable content was dropped or overwritten
- powershell.exe (PID: 3556)
- aria2c.exe (PID: 4580)
- 7zr.exe (PID: 4916)
Drops 7-zip archiver for unpacking
- aria2c.exe (PID: 4580)
- 7zr.exe (PID: 4916)
Process drops legitimate windows executable
- aria2c.exe (PID: 4580)
- 7zr.exe (PID: 4916)
Overwriting the PS system utility
- aria2c.exe (PID: 4580)
The process creates files with name similar to system file names
- 7zr.exe (PID: 4916)
Application launched itself
- cmd.exe (PID: 6868)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3480)
INFO
Manual execution by a user
- cmd.exe (PID: 1212)
Checks proxy server information
- powershell.exe (PID: 3556)
- slui.exe (PID: 1612)
Disables trace logs
- powershell.exe (PID: 3556)
Checks supported languages
- aria2c.exe (PID: 4580)
- 7zr.exe (PID: 4916)
- aria2c.exe (PID: 6504)
- aria2c.exe (PID: 7164)
Reads the machine GUID from the registry
- aria2c.exe (PID: 4580)
- aria2c.exe (PID: 6504)
- aria2c.exe (PID: 7164)
Reads the computer name
- aria2c.exe (PID: 4580)
- 7zr.exe (PID: 4916)
- aria2c.exe (PID: 6504)
- aria2c.exe (PID: 7164)
The sample compiled with english language support
- aria2c.exe (PID: 4580)
- 7zr.exe (PID: 4916)
Reads the software policy settings
- slui.exe (PID: 1612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:07:29 23:46:12 |
| ZipCRC: | 0xf5585c7b |
| ZipCompressedSize: | 1766 |
| ZipUncompressedSize: | 5222 |
| ZipFileName: | uup_download_windows.cmd |
Total processes
158
Monitored processes
17
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1212 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Downloads\uup_download_windows.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1520 | powershell -NoProfile Start-Process -FilePath 'C:\WINDOWS\system32\cmd.exe' -ArgumentList '/c """"""C:\Users\admin\Downloads\uup_download_windows.cmd""" 49127c4b-02dc-482e-ac4f-ec4d659b7547"""' -Verb RunAs | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1612 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2120 | REG QUERY HKU\S-1-5-19\Environment | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2532 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3480 | C:\WINDOWS\system32\cmd.exe /c findstr #UUPDUMP_ERROR: "files\aria2_script.25394.txt" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3556 | powershell -NoProfile -ExecutionPolicy Unrestricted .\files\get_aria2.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4580 | "files\aria2c.exe" --no-conf --async-dns=false --console-log-level=warn --log-level=info --log="aria2_download.log" -x16 -s16 -j2 -c -R -d"files" -i"files\converter_windows" | C:\Users\admin\Downloads\files\aria2c.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 4832 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 658
Read events
16 631
Write events
14
Delete events
13
Modification events
| (PID) Process: | (5456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\26120.5722_amd64_en-us_professional_6093b451_convert.zip | |||
| (PID) Process: | (5456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
19
Suspicious files
1 544
Text files
32
Unknown types
3 280
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1520 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_52zk32au.ig2.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5456 | WinRAR.exe | C:\Users\admin\Downloads\readme.unix.md | text | |
MD5:6AC8E0A3282C0B67561AD948DE5F7C2C | SHA256:4A253552B658D0AFFC4E6DAFA55F18FD693FEE333CD5C8B64D1FF9B885CC22A3 | |||
| 5456 | WinRAR.exe | C:\Users\admin\Downloads\uup_download_windows.cmd | text | |
MD5:9A7324C0708F1DF9C1BE3510494BBB22 | SHA256:A86B8A7D5A4EDAC4C953F74355D91278F986479344056BA9BB0DF9E7A5A1D61A | |||
| 5456 | WinRAR.exe | C:\Users\admin\Downloads\uup_download_macos.sh | text | |
MD5:0D51F885D7007A76A54FFC428F593F8A | SHA256:316F0D0BC76223F541354BA93B9674F408C6AE438CB296150EF35D9BB05E4E31 | |||
| 5456 | WinRAR.exe | C:\Users\admin\Downloads\files\converter_multi | text | |
MD5:52547B1827909A2DCD77083F4E31F841 | SHA256:A4EAE7918ED6CE3DD43AD47A39C9D5E0F06AD80C5F2F1CA52FE113D60827DCEF | |||
| 5456 | WinRAR.exe | C:\Users\admin\Downloads\ConvertConfig.ini | ini | |
MD5:06A5D2DAA2E225856DE9FB8D943659DC | SHA256:84A6B66226F3795C4A2C2EC694E6500A704CD156C96261AF3B2BADDD7B41BB85 | |||
| 5456 | WinRAR.exe | C:\Users\admin\Downloads\files\convert_config_linux | text | |
MD5:0F802038B21E07556124EEF30A64DA20 | SHA256:DFD83DF824C5E34B2E402FD176F714D62BB512BE8CB2DD07CF530F5E51F23AE7 | |||
| 5456 | WinRAR.exe | C:\Users\admin\Downloads\files\convert_config_macos | text | |
MD5:0F802038B21E07556124EEF30A64DA20 | SHA256:DFD83DF824C5E34B2E402FD176F714D62BB512BE8CB2DD07CF530F5E51F23AE7 | |||
| 5456 | WinRAR.exe | C:\Users\admin\Downloads\files\get_aria2.ps1 | text | |
MD5:55BD4DCBB931E1592C2E74F426522895 | SHA256:4CB3B3A9149D7DEDFB71796DED682A097DEE2454DC6B40FF95E0B33D022DB4A6 | |||
| 1520 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:B3BE74AE3404BBE59FE4897E73C2EC62 | SHA256:7CC29414BD360FD26C8FE0A7A0314835E092790EA1A79E91CF03D5DF2B3A46A3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1 543
TCP/UDP connections
64
DNS requests
27
Threats
1 558
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 208.89.74.17:80 | http://tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/226423f2-75c1-4af3-b215-5c6550300289?P1=1753833974&P2=404&P3=2&P4=kS7j%2fPUQ727Rq%2fb4ljzS6JZ%2fu9Z9n1e0T%2frx1W2zjxA14cWIYcB5YupSd8u8u0gWm2ojYpASz3geGVddQxRnsA%3d%3d | unknown | — | — | whitelisted |
6936 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7164 | aria2c.exe | GET | 200 | 208.89.74.17:80 | http://tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/04fd8d53-219f-4c5c-b108-fc6b64dcee5d?P1=1753833974&P2=404&P3=2&P4=U3jimQTie63ygLjCF8PTJYn0ZKg3XttqmHBuaNz%2bf1ZUzpx%2fnMvcqXkeWTf%2bK5urHGO9jb%2bsiR1SCRwxztBK3g%3d%3d | unknown | — | — | whitelisted |
7164 | aria2c.exe | GET | 200 | 208.89.74.17:80 | http://tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/58f0382c-02ff-45e6-9684-6aed2d9964c0?P1=1753833974&P2=404&P3=2&P4=UiMjSuwxAb1WMN8mKWYNYsvpEYu4%2b90uQTi%2fe0nTldhmwXrEGQ6Gc%2bEumHCKNRgSwe7l6bRHE%2fqDS4d8JUtEJQ%3d%3d | unknown | — | — | whitelisted |
7164 | aria2c.exe | GET | 200 | 208.89.74.17:80 | http://tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/274e9e9c-02b8-4c64-ad2c-4b7620f2e86a?P1=1753833974&P2=404&P3=2&P4=eJS2vRN5VFXD%2fJtJKRMQ40IGT9RcsRCQvJ4uMZagXifEApinPfuMqzB97HXliyuMBiKJijapt4TyCz9ROeQ0DQ%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 200 | 208.89.74.17:80 | http://tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7a601de3-f3cc-47a0-bc31-b312ae2f105f?P1=1753833974&P2=404&P3=2&P4=isxTqb7tS%2b1eKNHiYpKOUm2%2fvM6xkNHasS5tu6MLZ%2bce%2bJqWkDSCY8ZZ%2bWimuh3n8O8PIkdFndXu3kqUuS6MNg%3d%3d | unknown | — | — | whitelisted |
7164 | aria2c.exe | GET | 200 | 208.89.74.17:80 | http://tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/12b8a935-831c-4d13-a193-90aca98c0c67?P1=1753833974&P2=404&P3=2&P4=aFKDCOKezoQAn2fwXnGIzXxVLweSAgx1nyunGr69Sfhag7vgnUB55f%2fneet6VJA6Yj%2fasXNkzyPmYlO8q5ubCw%3d%3d | unknown | — | — | whitelisted |
7164 | aria2c.exe | GET | 200 | 208.89.74.17:80 | http://tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/35c75b42-6e0a-4ebd-bc3d-2c3e91c9cd89?P1=1753833974&P2=404&P3=2&P4=ZzSk5qQM3vxrMDsSAJVHyf62I9XQHQm7OfjAahM%2bZSo%2bpDB5hMos%2fRwD439nQWQvLbJFmAY6%2b1oGQiVTgpy0NQ%3d%3d | unknown | — | — | whitelisted |
7164 | aria2c.exe | GET | 200 | 208.89.74.17:80 | http://tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/086a2f5c-ccd1-4bae-8418-4ab9aafef202?P1=1753833974&P2=404&P3=2&P4=IPPzZcPNpfWlBuDhg3GlI8jRzzrxRvXq08ZBFSZE362XGClY%2bOq1t7KrhlpzCDgD%2bydr%2bUW7JnU7QGm0LKbvNQ%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 200 | 208.89.74.17:80 | http://tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ec2c466d-ac8e-42fc-87bd-d2a22f9d3bc7?P1=1753833974&P2=404&P3=2&P4=iWeI2VrfIOvRA33AklTjB0x%2bYdbngK%2b331uXJ9cJ8dPjrK17usTPQBmoyEr%2fvySlCLp4EBTiXn%2f2CNGvd%2blkUg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1040 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6936 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6936 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
uupdump.net |
| malicious |
client.wns.windows.com |
| whitelisted |
c.pki.goog |
| whitelisted |
tlu.dl.delivery.mp.microsoft.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7164 | aria2c.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
7164 | aria2c.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
7164 | aria2c.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
7164 | aria2c.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
7164 | aria2c.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
7164 | aria2c.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
7164 | aria2c.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
7164 | aria2c.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
7164 | aria2c.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
7164 | aria2c.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |