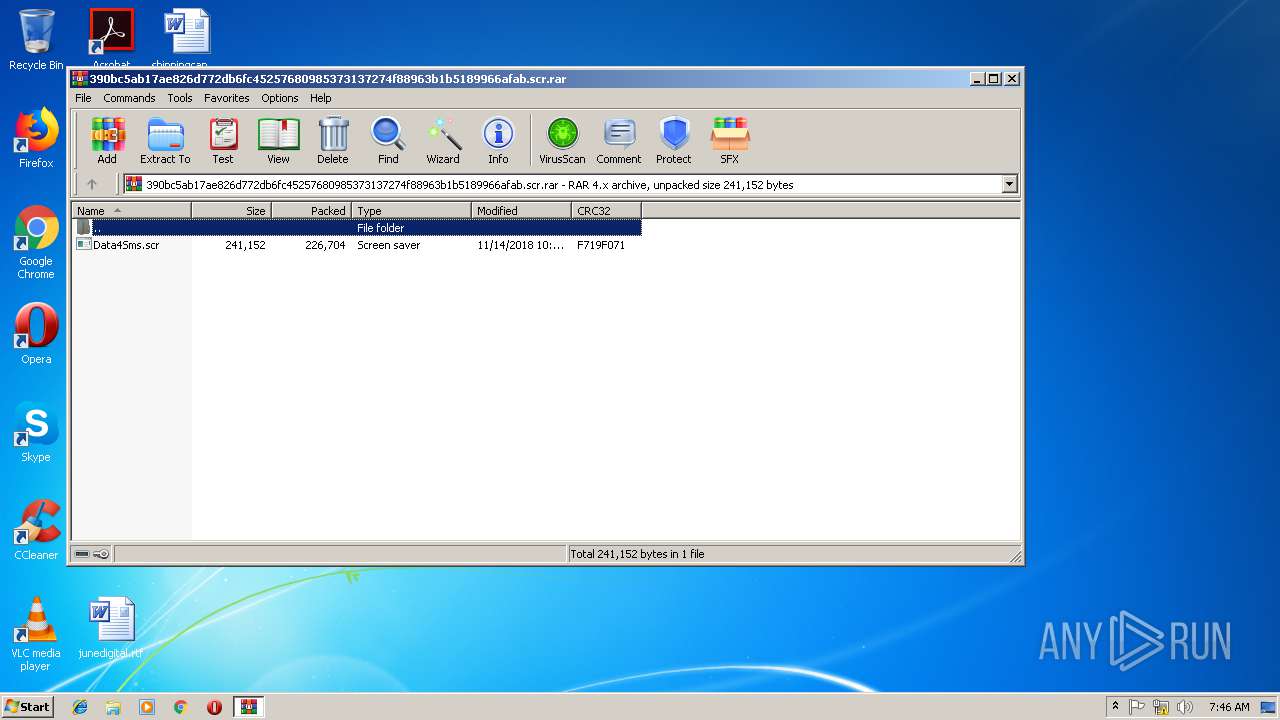
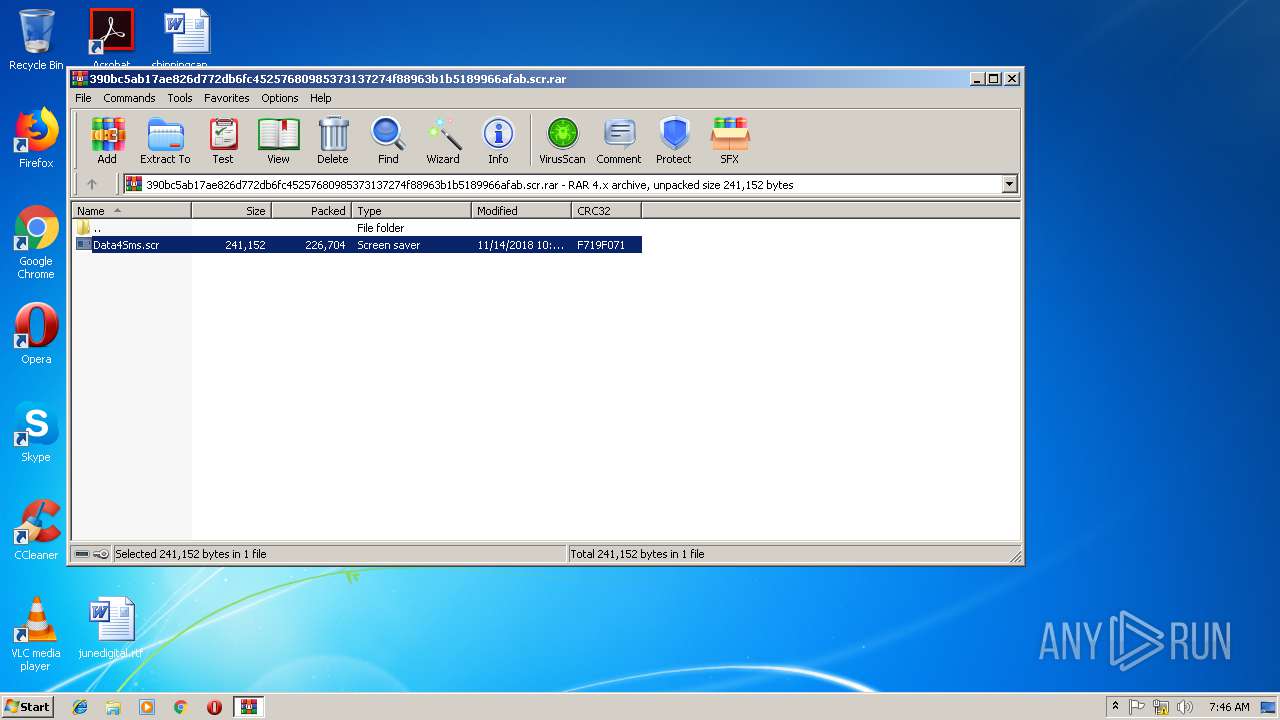
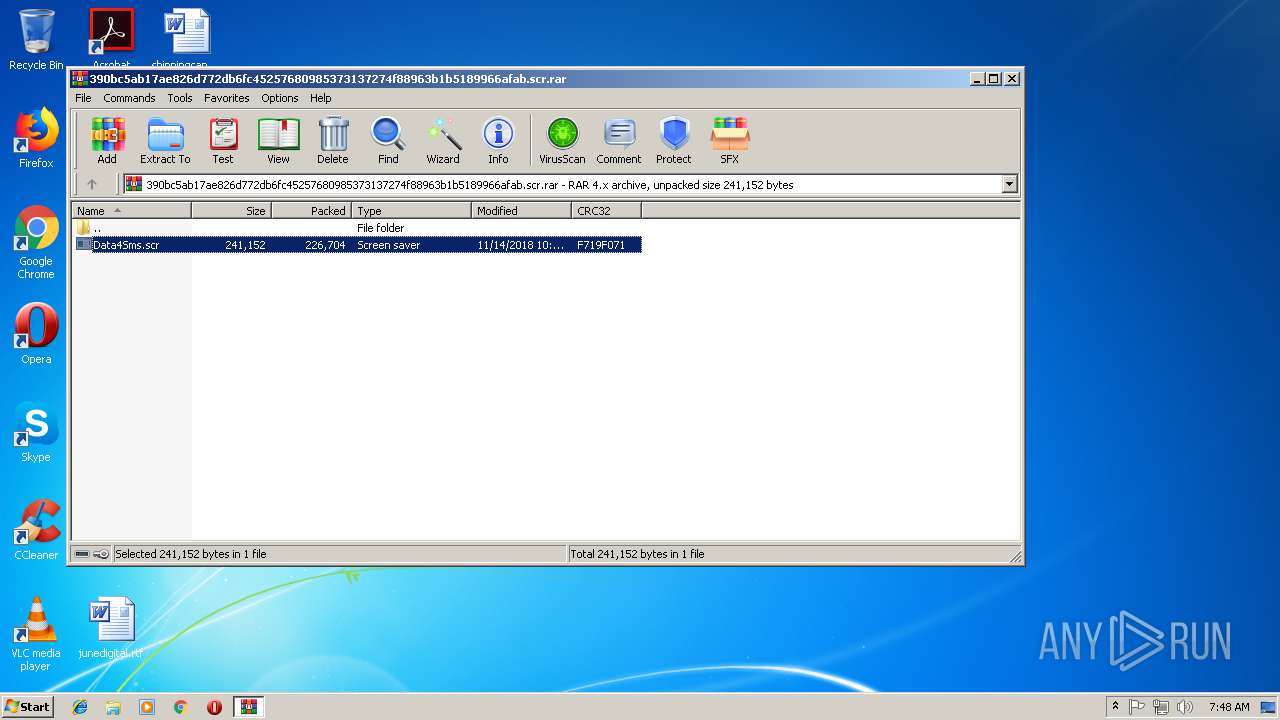
| File name: | 390bc5ab17ae826d772db6fc45257680985373137274f88963b1b5189966afab.scr |
| Full analysis: | https://app.any.run/tasks/b8ad570e-b94f-4012-9b3c-3672719d78da |
| Verdict: | Malicious activity |
| Analysis date: | November 15, 2018, 07:46:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 371DDE8F6DC657247CD5C59C616324B9 |
| SHA1: | B2B4210D3196A52DFC5512DAFB497099C93985B4 |
| SHA256: | 390BC5AB17AE826D772DB6FC45257680985373137274F88963B1B5189966AFAB |
| SSDEEP: | 3072:+J31D8QhMhjjtLzgTOEjP2D+iqQ7P3Z5etpzpgpV94j1peFPRygST0N92X0xDkh4:+J3SIU/WOGP3fQD/26X4JpsMgS5h5HL+ |
MALICIOUS
Application was dropped or rewritten from another process
- Data4Sms.scr (PID: 3384)
- Data4Sms.scr (PID: 2780)
- Data4Sms.scr (PID: 2588)
Changes the login/logoff helper path in the registry
- Data4Sms.scr (PID: 3384)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3208)
- Data4Sms.scr (PID: 3384)
Creates files in the user directory
- Data4Sms.scr (PID: 3384)
- Data4Sms.scr (PID: 2780)
Starts application with an unusual extension
- WinRAR.exe (PID: 3208)
- Data4Sms.scr (PID: 3384)
Application launched itself
- Data4Sms.scr (PID: 3384)
Connects to unusual port
- Data4Sms.scr (PID: 2780)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 226742 |
|---|---|
| UncompressedSize: | 241152 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2018:11:14 10:45:22 |
| PackingMethod: | Normal |
| ArchivedFileName: | Data4Sms.scr |
Total processes
35
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2588 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa3208.13319\Data4Sms.scr" /S | C:\Users\admin\AppData\Local\Temp\Rar$DIa3208.13319\Data4Sms.scr | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: BleIndexer Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2780 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa3208.301\Data4Sms.scr" | C:\Users\admin\AppData\Local\Temp\Rar$DIa3208.301\Data4Sms.scr | Data4Sms.scr | ||||||||||||
User: admin Integrity Level: MEDIUM Description: BleIndexer Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3208 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\390bc5ab17ae826d772db6fc45257680985373137274f88963b1b5189966afab.scr.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3384 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa3208.301\Data4Sms.scr" /S | C:\Users\admin\AppData\Local\Temp\Rar$DIa3208.301\Data4Sms.scr | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: BleIndexer Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
439
Read events
424
Write events
15
Delete events
0
Modification events
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\390bc5ab17ae826d772db6fc45257680985373137274f88963b1b5189966afab.scr.rar | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @shell32,-10162 |
Value: Screen saver | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
3
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3384 | Data4Sms.scr | C:\Users\admin\AppData\Roaming\6ET1QpFY4q8H433K\LKcw0ul08VAd.exe | executable | |
MD5:— | SHA256:— | |||
| 3208 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3208.301\Data4Sms.scr | executable | |
MD5:— | SHA256:— | |||
| 3208 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3208.13319\Data4Sms.scr | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
3
Threats
3
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2780 | Data4Sms.scr | 185.125.205.94:1604 | info1.duckdns.org | — | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
info1.duckdns.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |