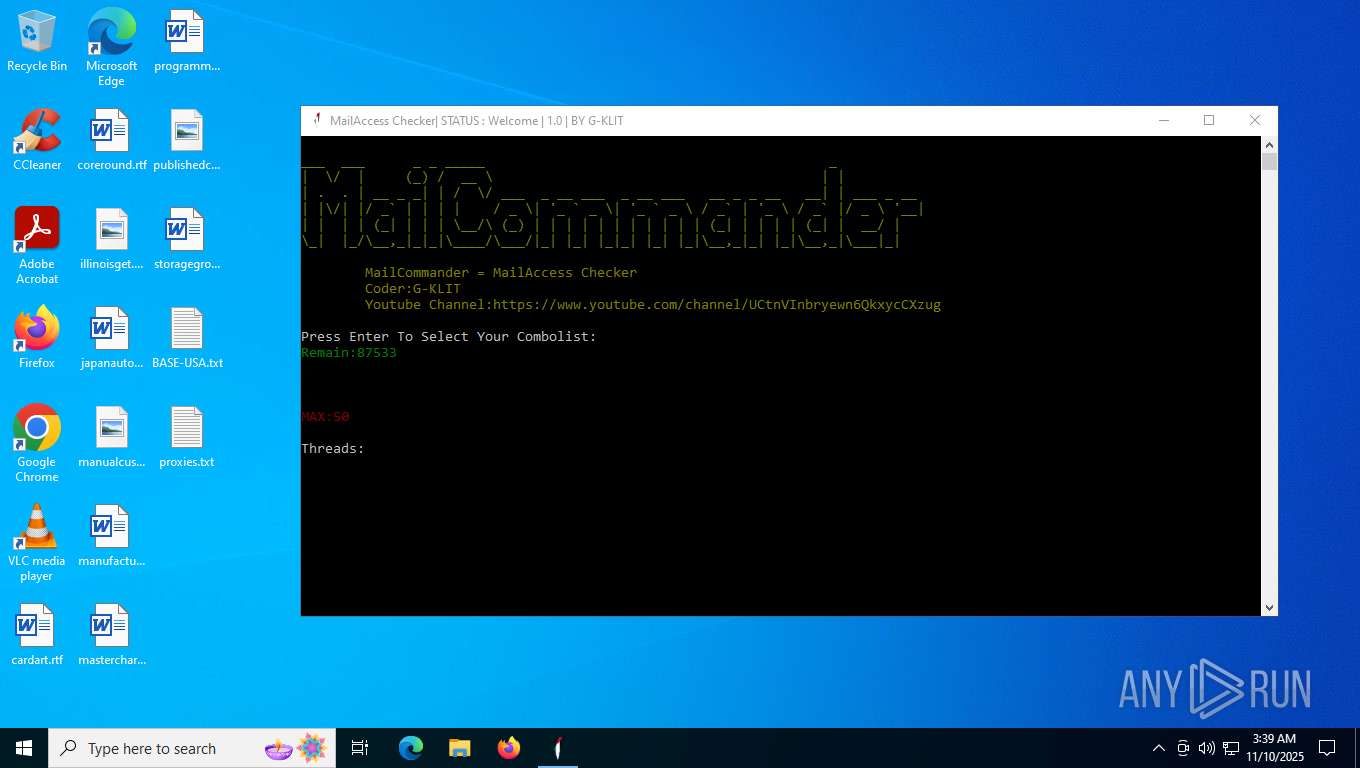
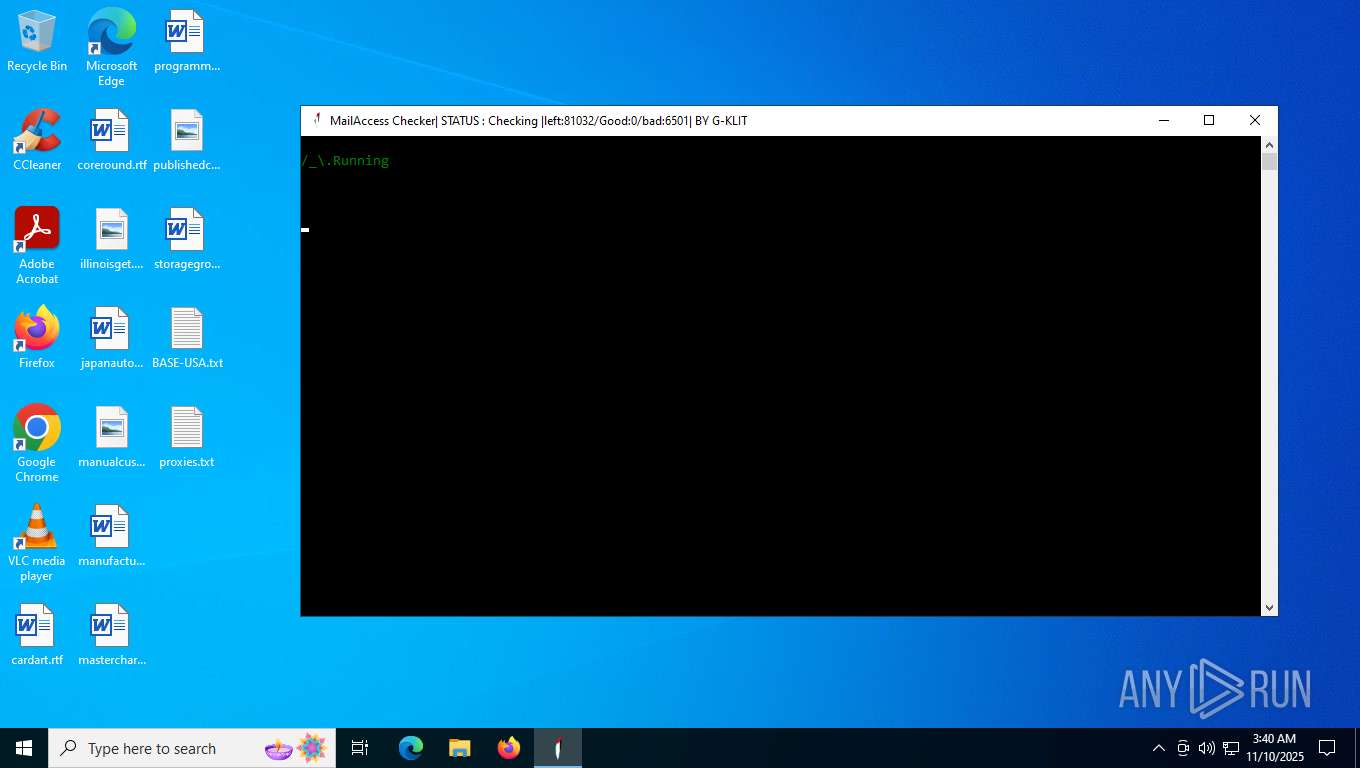
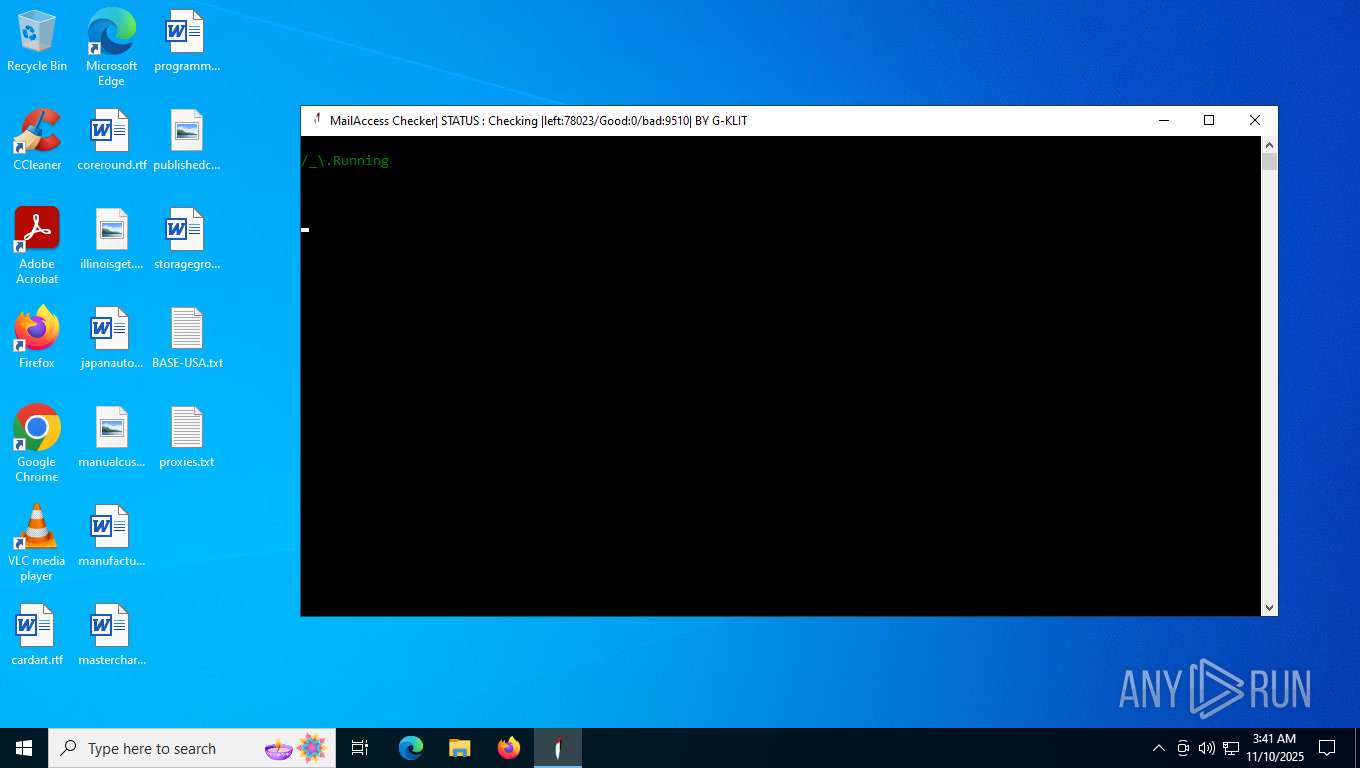
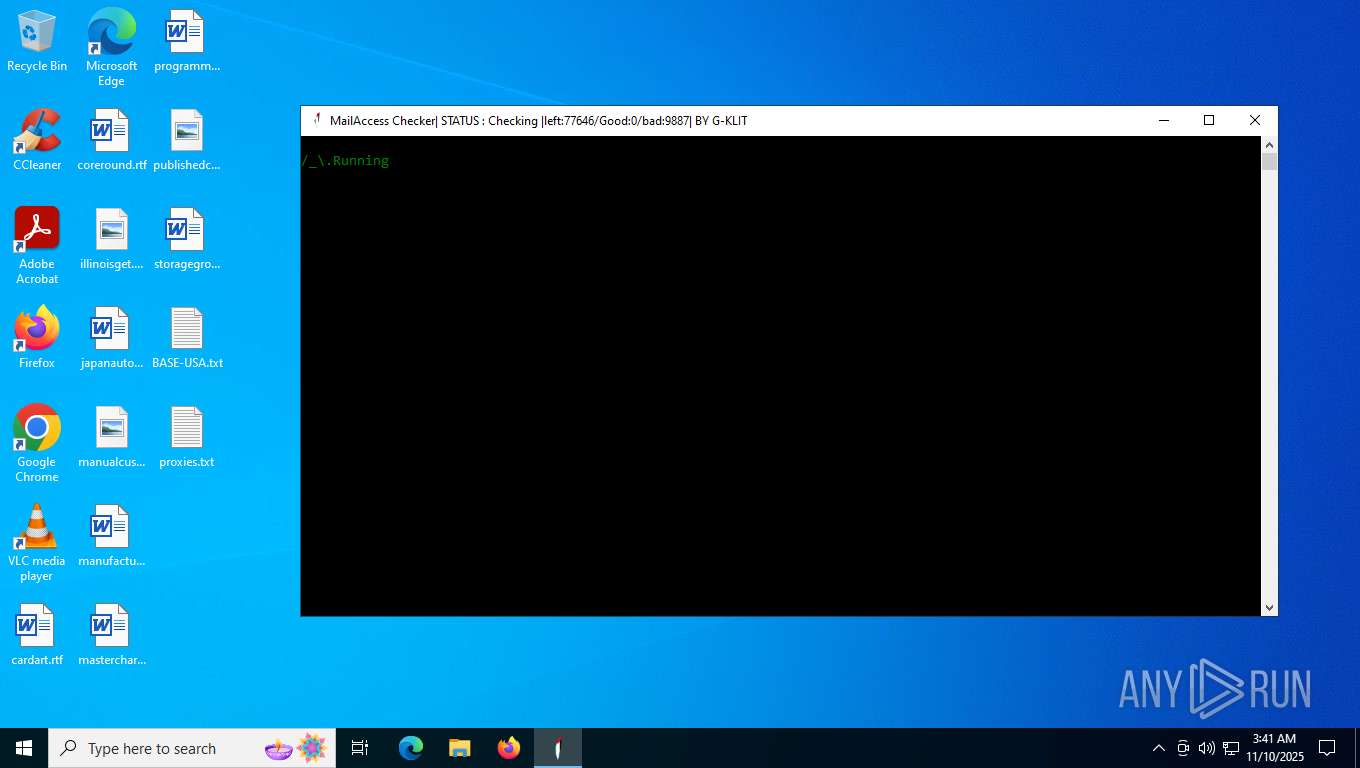
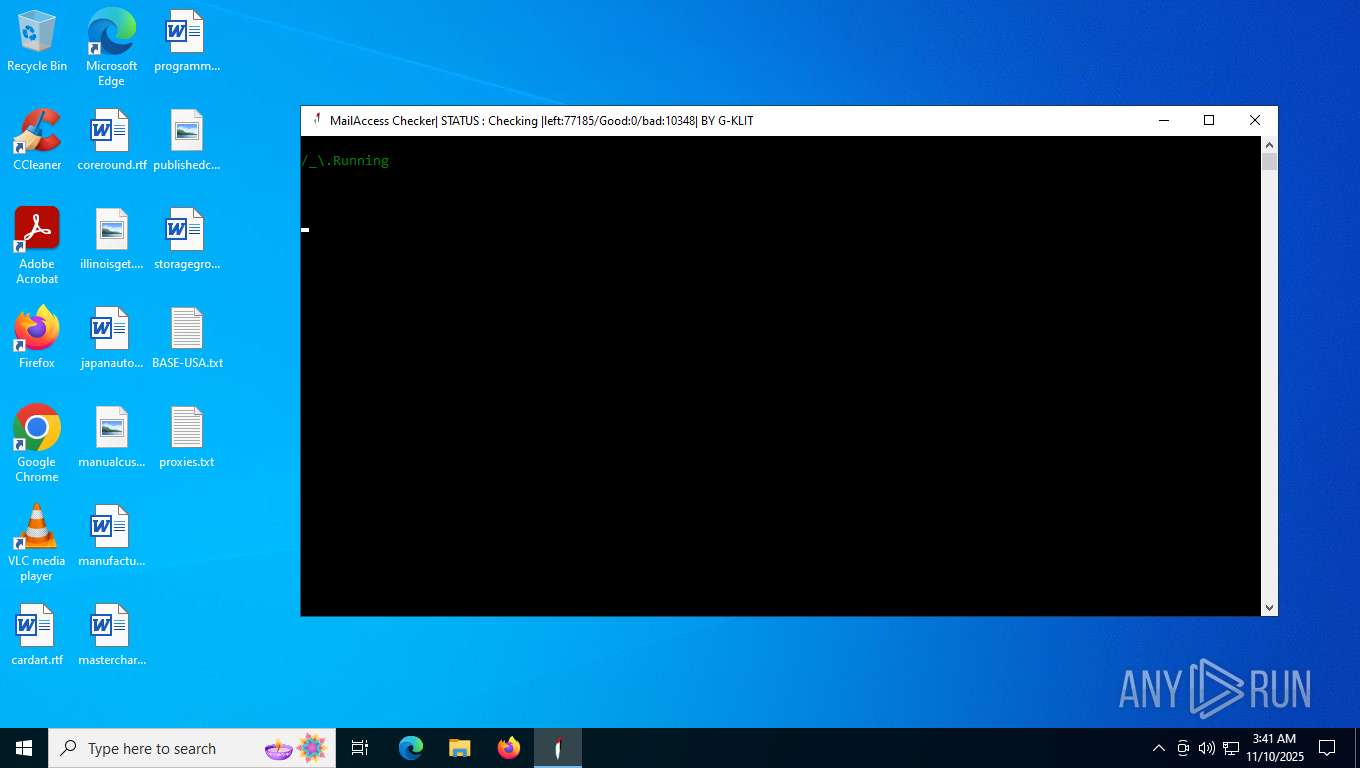
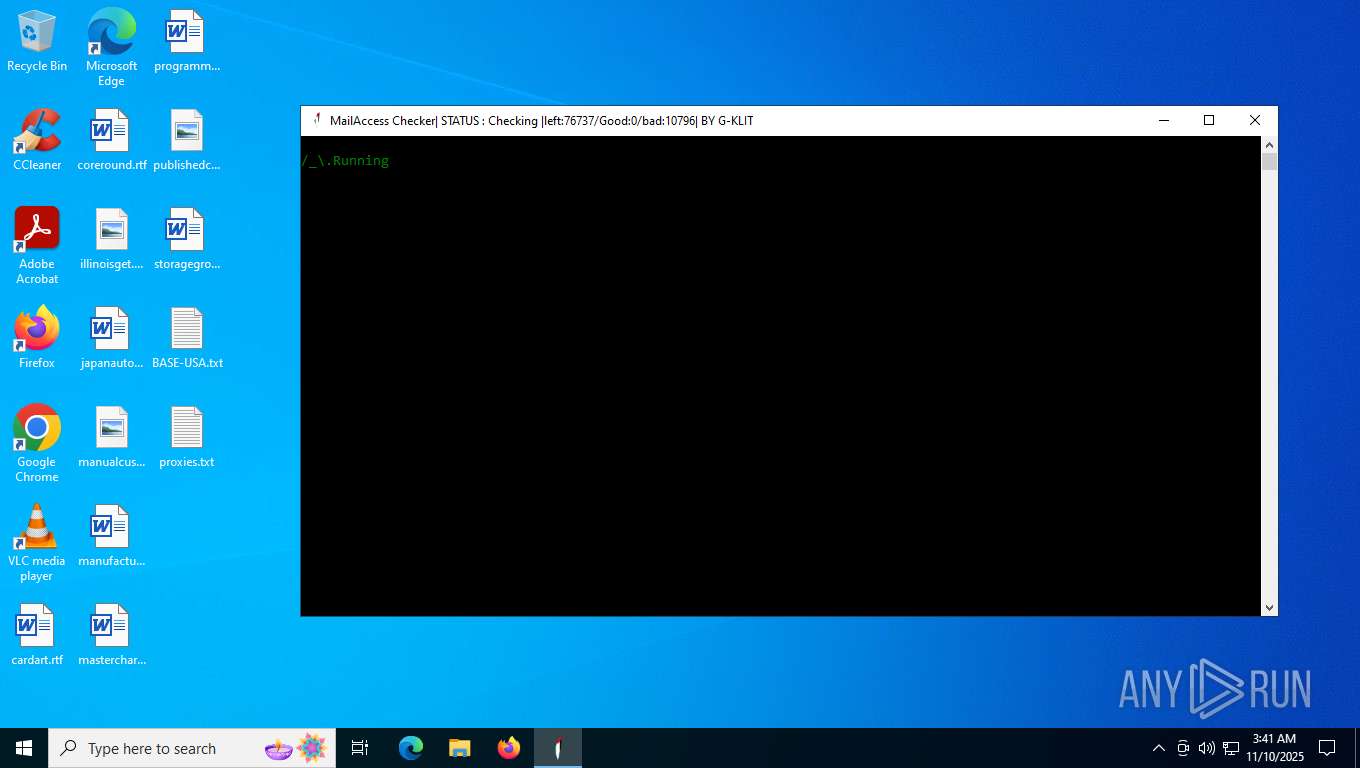
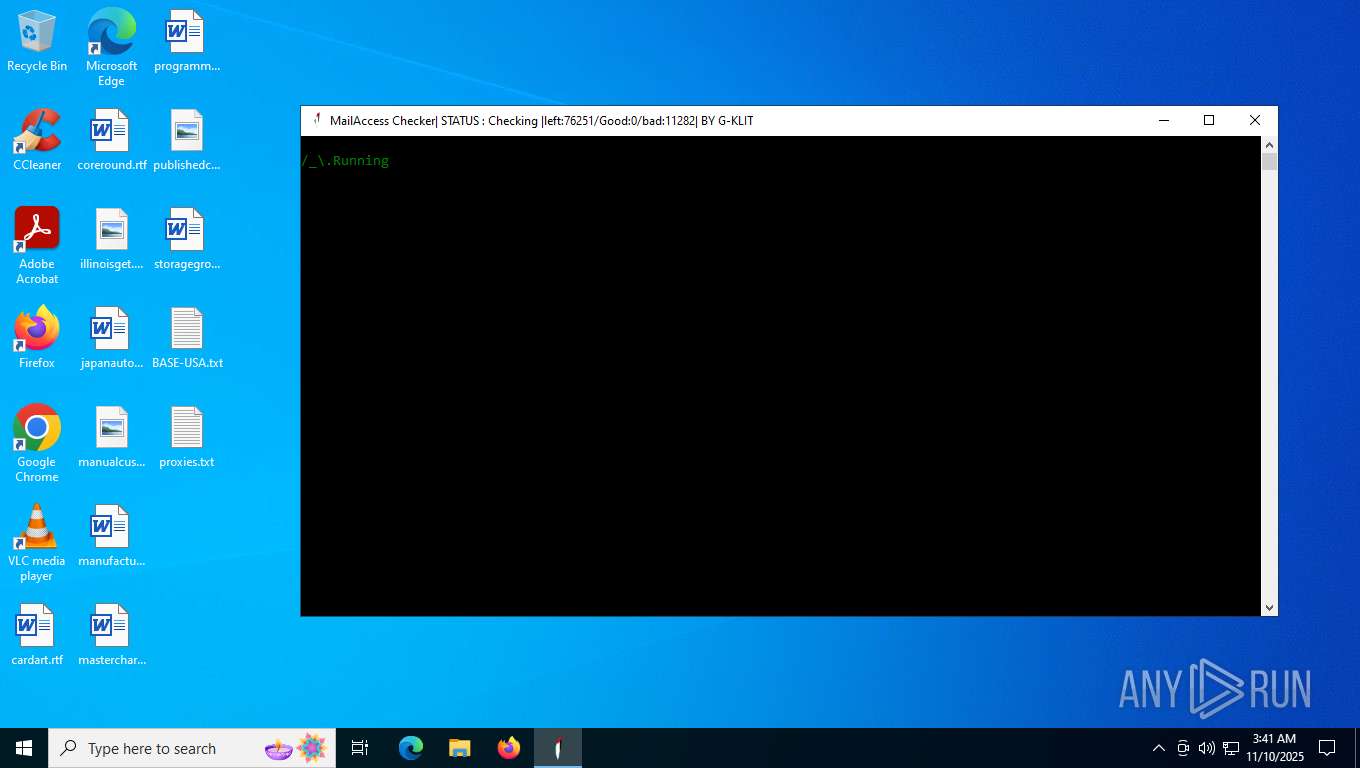
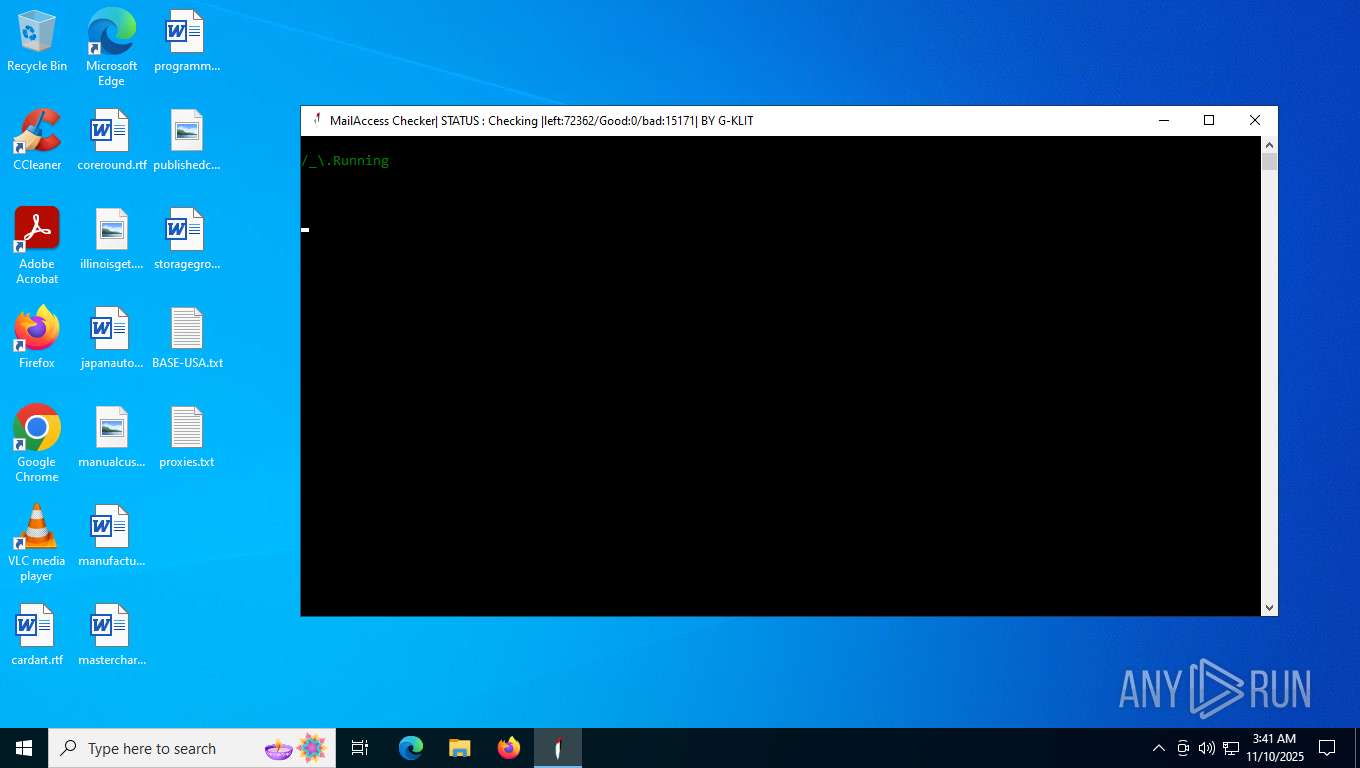
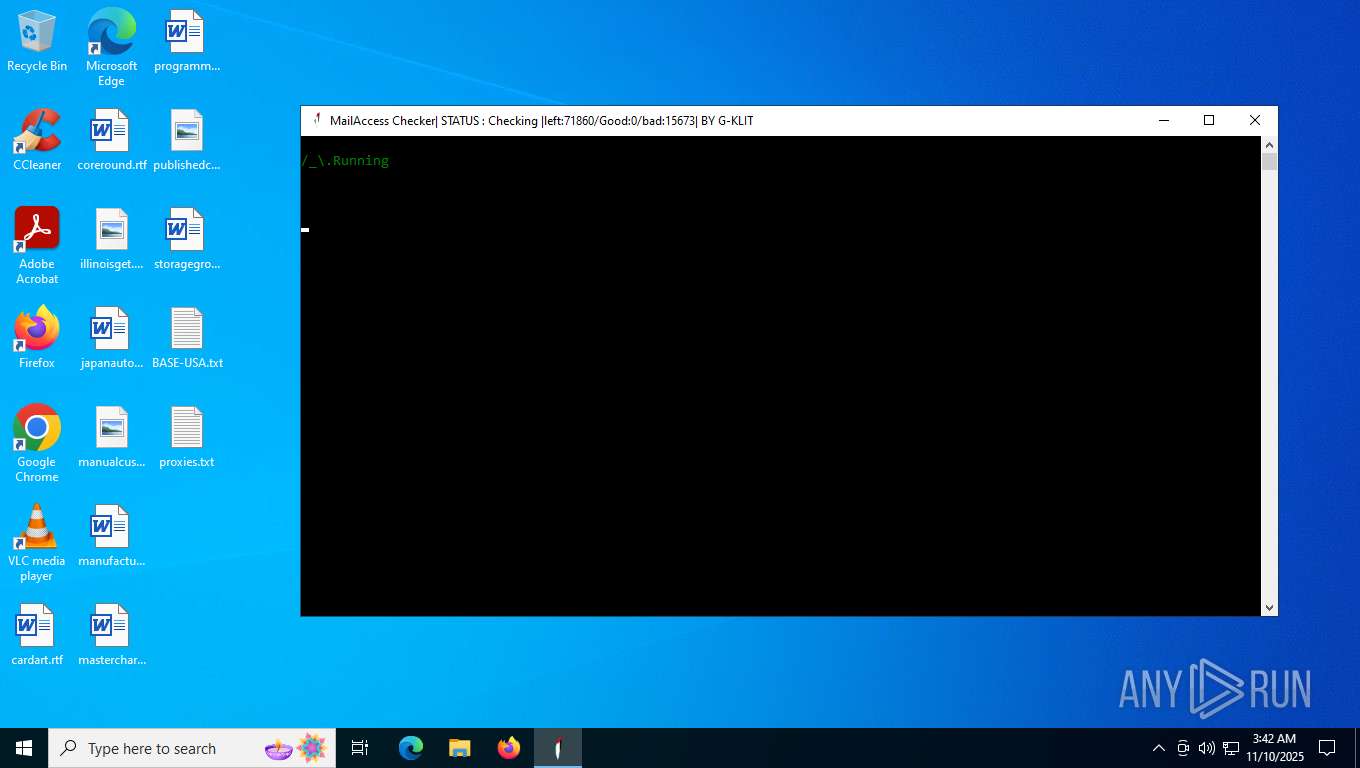
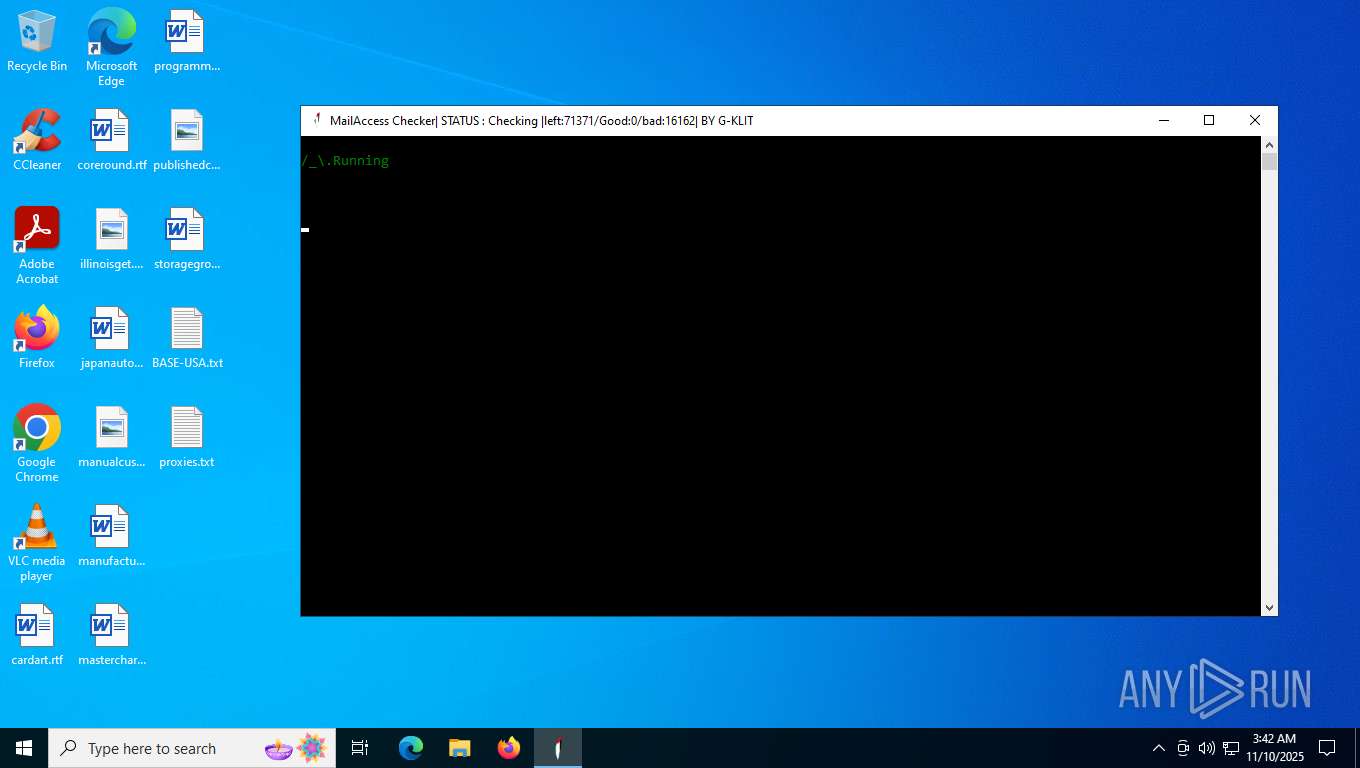
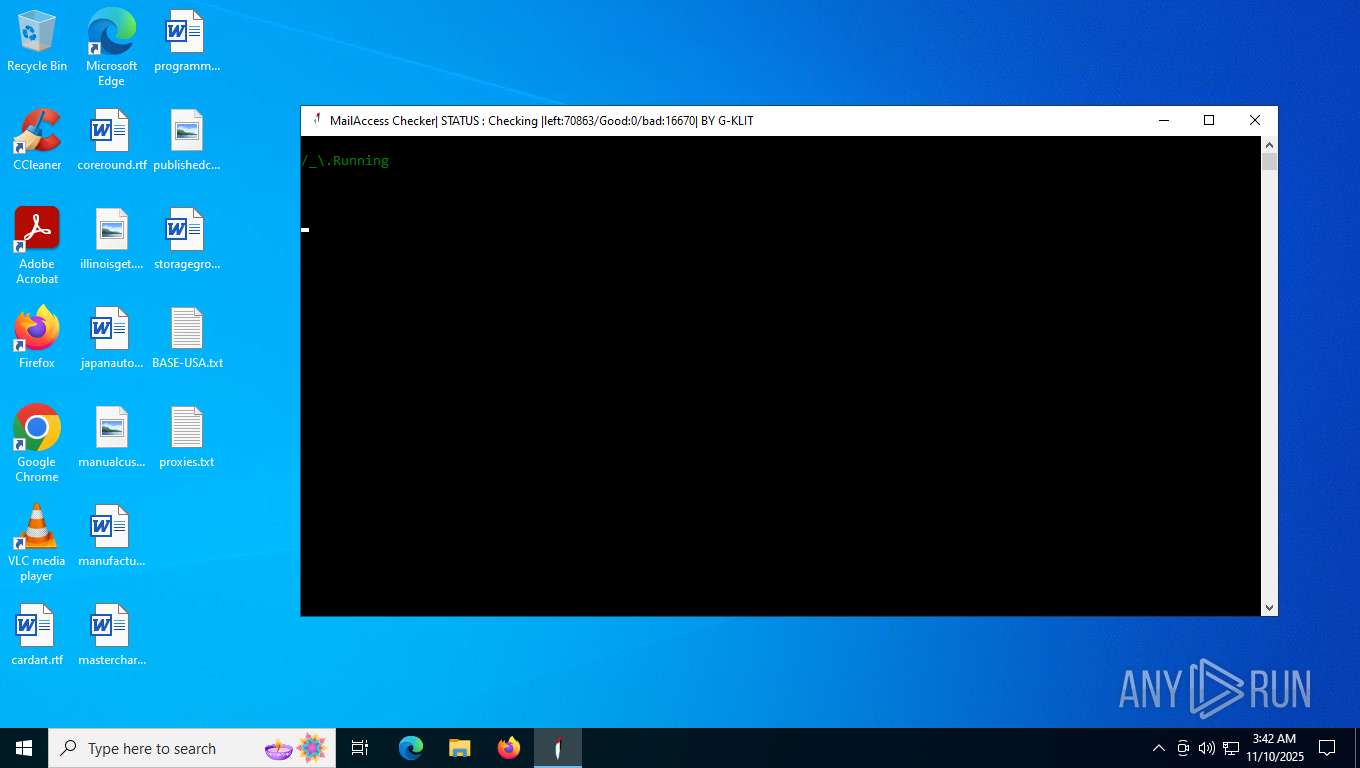
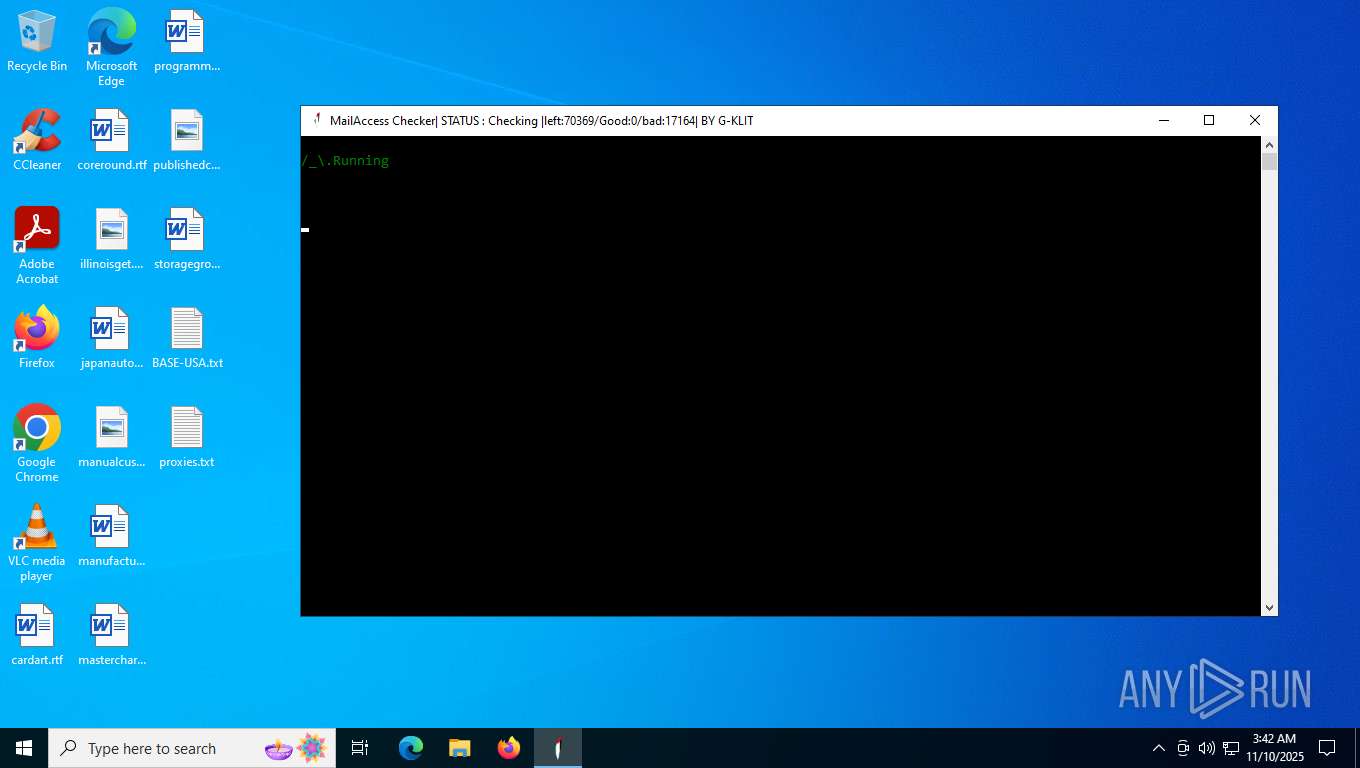
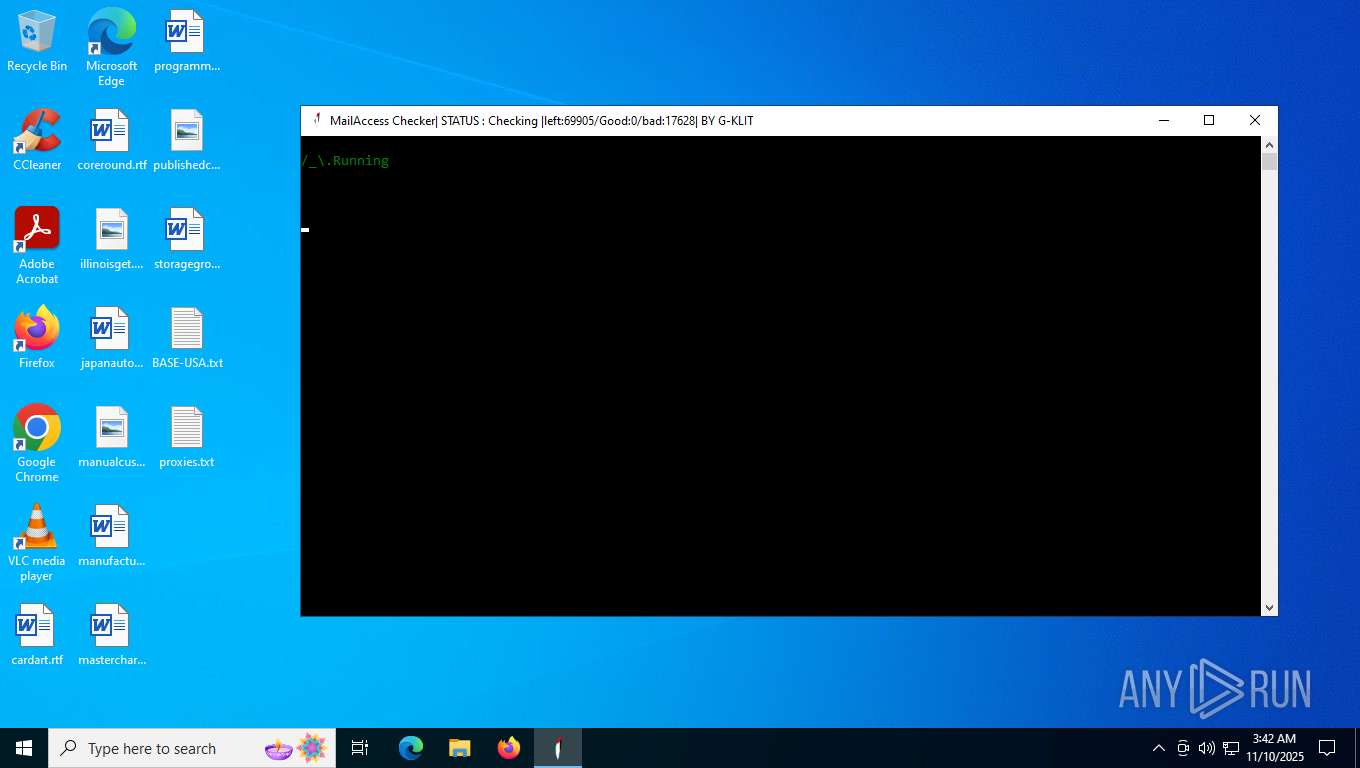
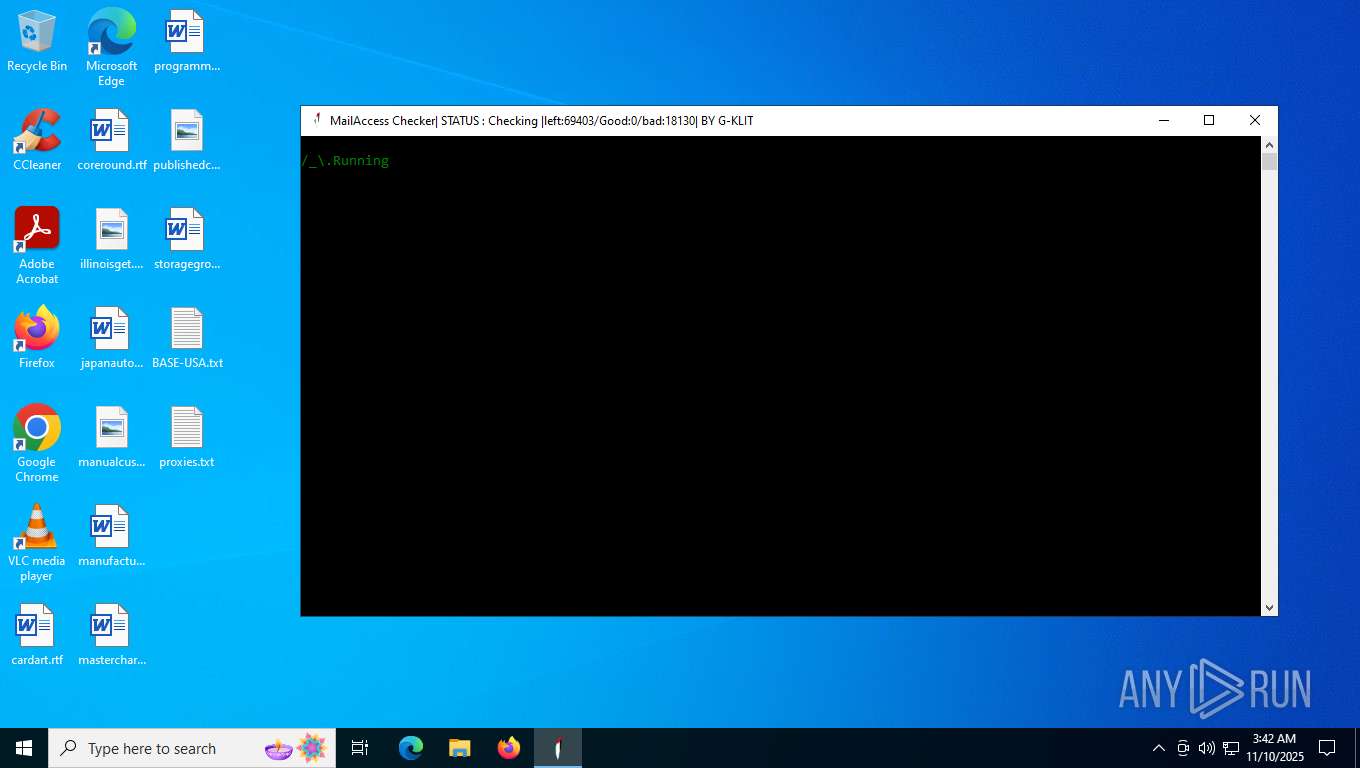
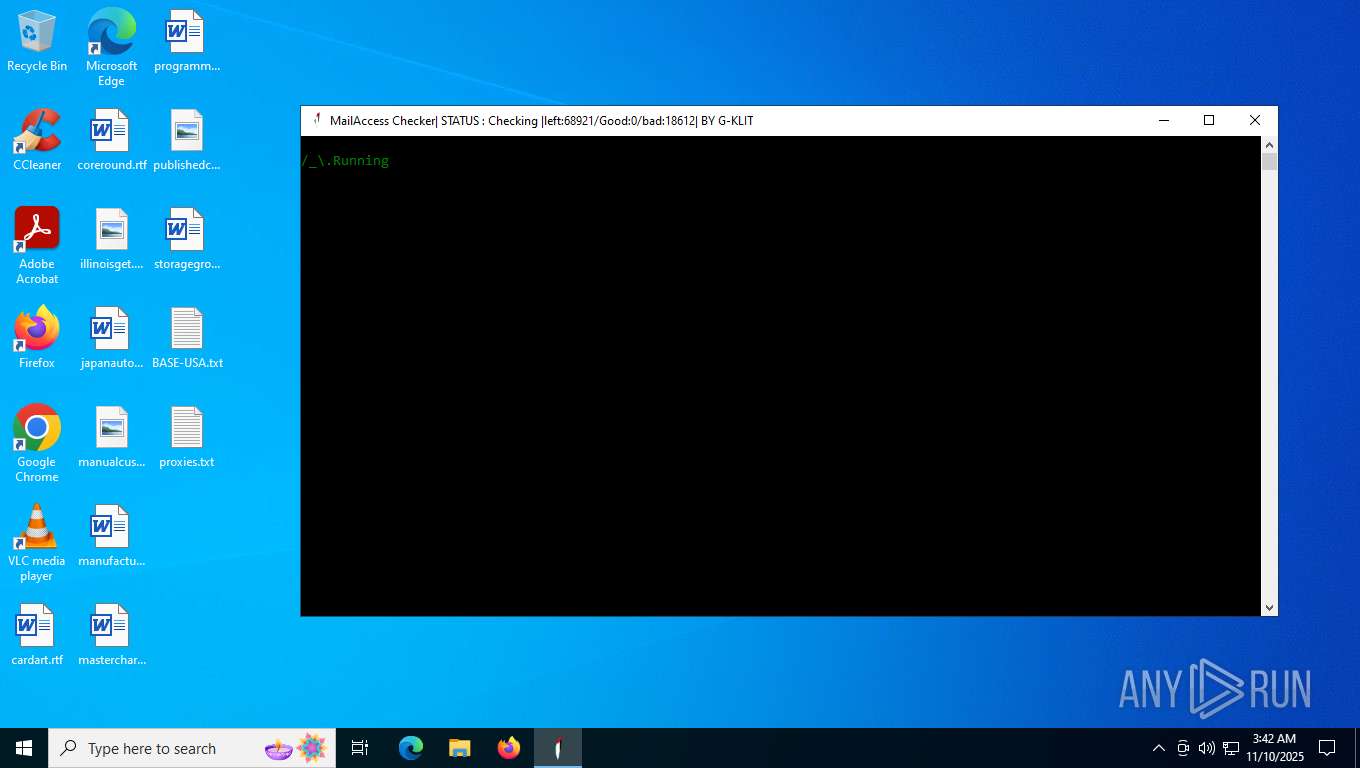
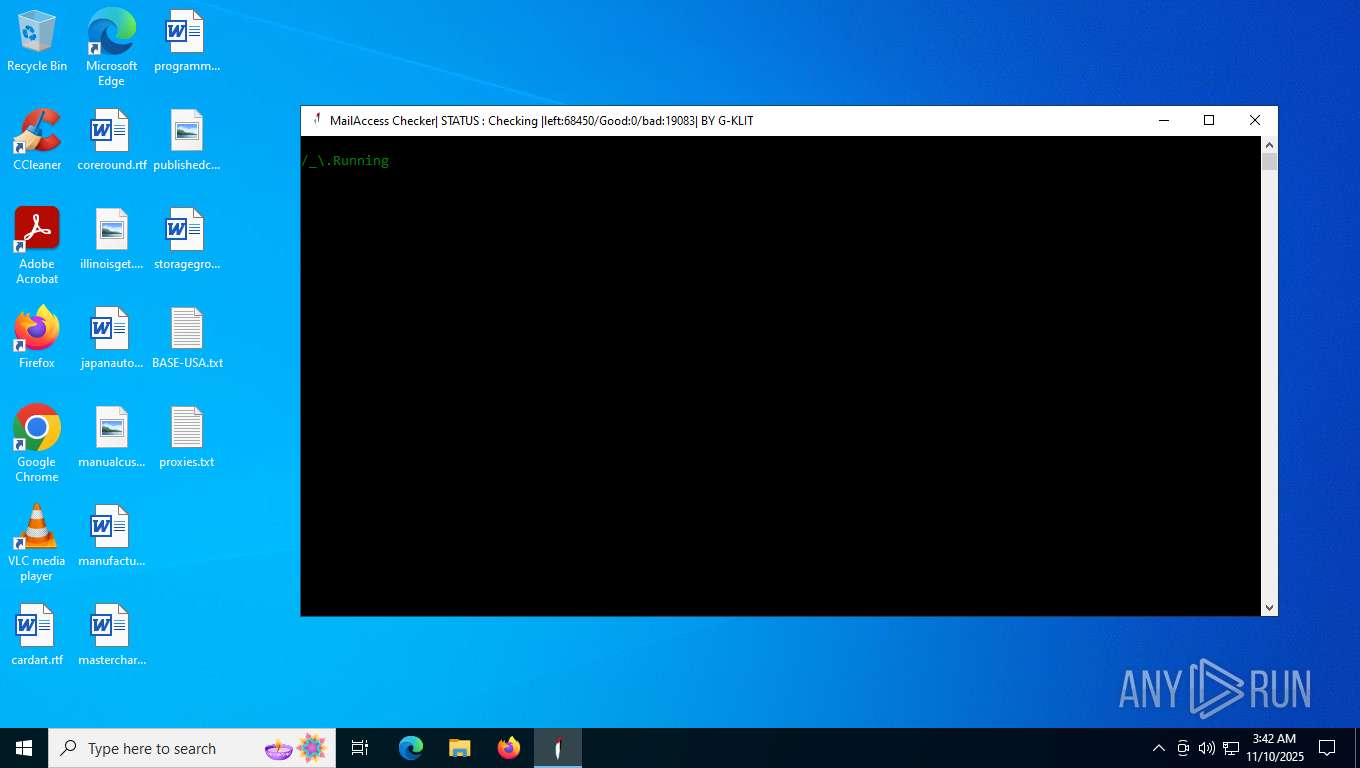
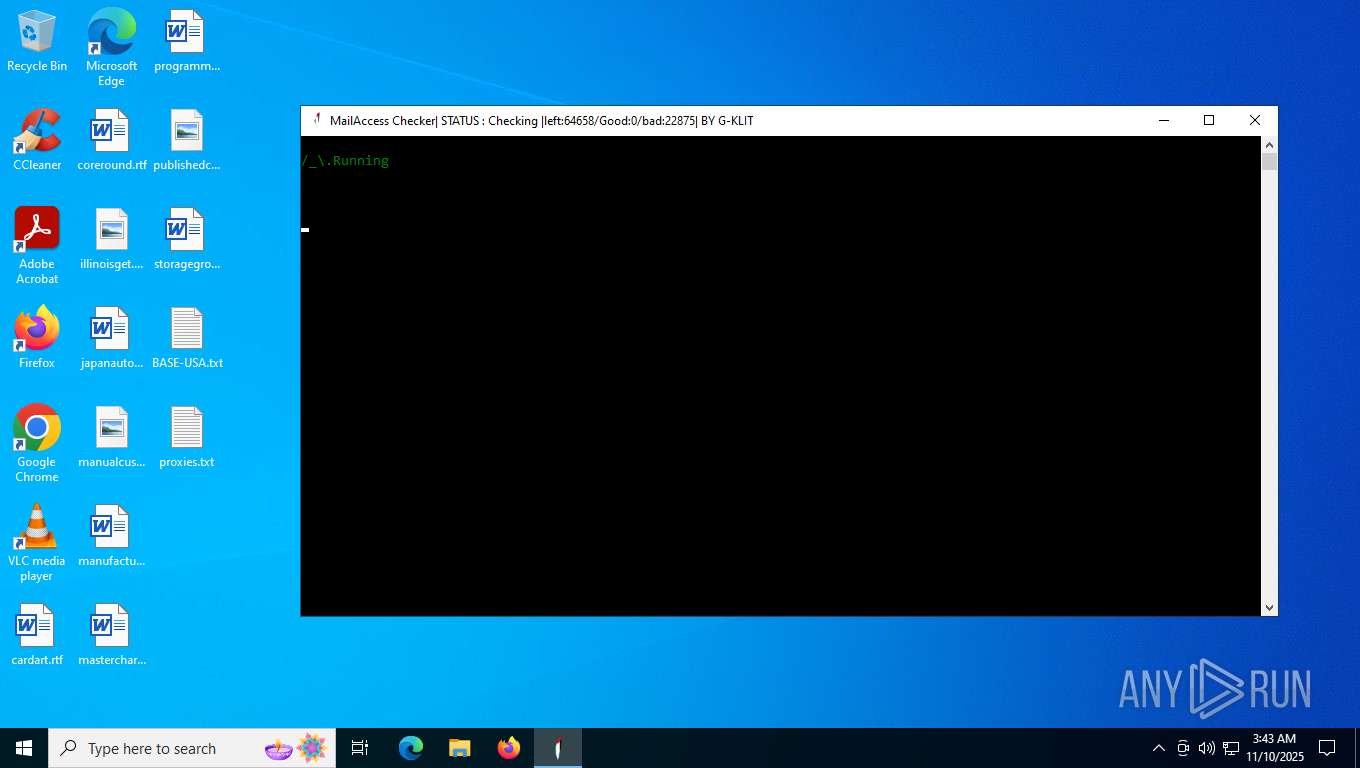
| File name: | Mail Access Checker by G-KLIT.exe |
| Full analysis: | https://app.any.run/tasks/ab8b0790-7722-4d3a-b35e-f55a22f914a7 |
| Verdict: | Malicious activity |
| Analysis date: | November 10, 2025, 03:38:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 6 sections |
| MD5: | 02EADD468D5B5A606F3A73770AE73A41 |
| SHA1: | D639249F959E4BDB2F5C87CF27EE1B5106CE2702 |
| SHA256: | 39063D85E04B6DA2A504FED78BF9B8ADA68EAE7CDD1945D9D2AD1D576F149B31 |
| SSDEEP: | 98304:SXsorR5HrBTifp/VSBc5cI3Xf51rwxeT+fGUGDLWX8rjsdJkkwN25fJ8s9bkf4BT:IgmjOZ/Hugao |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops python dynamic module
- Mail Access Checker by G-KLIT.exe (PID: 7376)
Executable content was dropped or overwritten
- Mail Access Checker by G-KLIT.exe (PID: 7376)
Process drops legitimate windows executable
- Mail Access Checker by G-KLIT.exe (PID: 7376)
The process drops C-runtime libraries
- Mail Access Checker by G-KLIT.exe (PID: 7376)
Application launched itself
- Mail Access Checker by G-KLIT.exe (PID: 7376)
- Mail Access Checker by G-KLIT.exe (PID: 7280)
Reads security settings of Internet Explorer
- Mail Access Checker by G-KLIT.exe (PID: 7280)
Loads Python modules
- Mail Access Checker by G-KLIT.exe (PID: 7280)
- Mail Access Checker by G-KLIT.exe (PID: 4244)
- Mail Access Checker by G-KLIT.exe (PID: 2332)
- Mail Access Checker by G-KLIT.exe (PID: 6376)
- Mail Access Checker by G-KLIT.exe (PID: 4784)
- Mail Access Checker by G-KLIT.exe (PID: 7216)
- Mail Access Checker by G-KLIT.exe (PID: 6404)
- Mail Access Checker by G-KLIT.exe (PID: 3680)
- Mail Access Checker by G-KLIT.exe (PID: 6872)
- Mail Access Checker by G-KLIT.exe (PID: 480)
- Mail Access Checker by G-KLIT.exe (PID: 7336)
- Mail Access Checker by G-KLIT.exe (PID: 2312)
- Mail Access Checker by G-KLIT.exe (PID: 696)
- Mail Access Checker by G-KLIT.exe (PID: 6360)
- Mail Access Checker by G-KLIT.exe (PID: 5956)
- Mail Access Checker by G-KLIT.exe (PID: 7176)
Starts CMD.EXE for commands execution
- Mail Access Checker by G-KLIT.exe (PID: 7280)
There is functionality for taking screenshot (YARA)
- Mail Access Checker by G-KLIT.exe (PID: 7280)
- Mail Access Checker by G-KLIT.exe (PID: 2332)
- Mail Access Checker by G-KLIT.exe (PID: 7336)
- Mail Access Checker by G-KLIT.exe (PID: 7216)
- Mail Access Checker by G-KLIT.exe (PID: 6872)
- Mail Access Checker by G-KLIT.exe (PID: 480)
- Mail Access Checker by G-KLIT.exe (PID: 6376)
- Mail Access Checker by G-KLIT.exe (PID: 6404)
- Mail Access Checker by G-KLIT.exe (PID: 4784)
- Mail Access Checker by G-KLIT.exe (PID: 6360)
- Mail Access Checker by G-KLIT.exe (PID: 2312)
- Mail Access Checker by G-KLIT.exe (PID: 696)
- Mail Access Checker by G-KLIT.exe (PID: 4244)
- Mail Access Checker by G-KLIT.exe (PID: 3680)
- Mail Access Checker by G-KLIT.exe (PID: 7176)
- Mail Access Checker by G-KLIT.exe (PID: 5956)
INFO
PyInstaller has been detected (YARA)
- Mail Access Checker by G-KLIT.exe (PID: 7376)
- Mail Access Checker by G-KLIT.exe (PID: 7280)
- Mail Access Checker by G-KLIT.exe (PID: 2332)
- Mail Access Checker by G-KLIT.exe (PID: 7336)
- Mail Access Checker by G-KLIT.exe (PID: 7216)
- Mail Access Checker by G-KLIT.exe (PID: 6872)
- Mail Access Checker by G-KLIT.exe (PID: 4784)
- Mail Access Checker by G-KLIT.exe (PID: 6376)
- Mail Access Checker by G-KLIT.exe (PID: 6404)
- Mail Access Checker by G-KLIT.exe (PID: 696)
- Mail Access Checker by G-KLIT.exe (PID: 6360)
- Mail Access Checker by G-KLIT.exe (PID: 2312)
- Mail Access Checker by G-KLIT.exe (PID: 480)
- Mail Access Checker by G-KLIT.exe (PID: 3680)
- Mail Access Checker by G-KLIT.exe (PID: 4244)
- Mail Access Checker by G-KLIT.exe (PID: 7176)
- Mail Access Checker by G-KLIT.exe (PID: 5956)
The sample compiled with english language support
- Mail Access Checker by G-KLIT.exe (PID: 7376)
Checks supported languages
- Mail Access Checker by G-KLIT.exe (PID: 7376)
- Mail Access Checker by G-KLIT.exe (PID: 7280)
- Mail Access Checker by G-KLIT.exe (PID: 2332)
- Mail Access Checker by G-KLIT.exe (PID: 7336)
- Mail Access Checker by G-KLIT.exe (PID: 6872)
- Mail Access Checker by G-KLIT.exe (PID: 7216)
- Mail Access Checker by G-KLIT.exe (PID: 480)
- Mail Access Checker by G-KLIT.exe (PID: 6360)
- Mail Access Checker by G-KLIT.exe (PID: 6404)
- Mail Access Checker by G-KLIT.exe (PID: 6376)
- Mail Access Checker by G-KLIT.exe (PID: 4784)
- Mail Access Checker by G-KLIT.exe (PID: 696)
- Mail Access Checker by G-KLIT.exe (PID: 3680)
- Mail Access Checker by G-KLIT.exe (PID: 5956)
- Mail Access Checker by G-KLIT.exe (PID: 2312)
- Mail Access Checker by G-KLIT.exe (PID: 4244)
- Mail Access Checker by G-KLIT.exe (PID: 7176)
Create files in a temporary directory
- Mail Access Checker by G-KLIT.exe (PID: 7376)
Reads the computer name
- Mail Access Checker by G-KLIT.exe (PID: 7280)
- Mail Access Checker by G-KLIT.exe (PID: 2332)
- Mail Access Checker by G-KLIT.exe (PID: 7216)
- Mail Access Checker by G-KLIT.exe (PID: 480)
- Mail Access Checker by G-KLIT.exe (PID: 7336)
- Mail Access Checker by G-KLIT.exe (PID: 6872)
- Mail Access Checker by G-KLIT.exe (PID: 4784)
- Mail Access Checker by G-KLIT.exe (PID: 3680)
- Mail Access Checker by G-KLIT.exe (PID: 2312)
- Mail Access Checker by G-KLIT.exe (PID: 6376)
- Mail Access Checker by G-KLIT.exe (PID: 6404)
- Mail Access Checker by G-KLIT.exe (PID: 6360)
- Mail Access Checker by G-KLIT.exe (PID: 696)
- Mail Access Checker by G-KLIT.exe (PID: 7176)
- Mail Access Checker by G-KLIT.exe (PID: 4244)
- Mail Access Checker by G-KLIT.exe (PID: 5956)
Reads the machine GUID from the registry
- Mail Access Checker by G-KLIT.exe (PID: 7280)
- Mail Access Checker by G-KLIT.exe (PID: 2332)
- Mail Access Checker by G-KLIT.exe (PID: 7216)
- Mail Access Checker by G-KLIT.exe (PID: 7336)
- Mail Access Checker by G-KLIT.exe (PID: 4784)
- Mail Access Checker by G-KLIT.exe (PID: 6872)
- Mail Access Checker by G-KLIT.exe (PID: 6360)
- Mail Access Checker by G-KLIT.exe (PID: 480)
- Mail Access Checker by G-KLIT.exe (PID: 3680)
- Mail Access Checker by G-KLIT.exe (PID: 6376)
- Mail Access Checker by G-KLIT.exe (PID: 5956)
- Mail Access Checker by G-KLIT.exe (PID: 696)
- Mail Access Checker by G-KLIT.exe (PID: 2312)
- Mail Access Checker by G-KLIT.exe (PID: 6404)
- Mail Access Checker by G-KLIT.exe (PID: 7176)
- Mail Access Checker by G-KLIT.exe (PID: 4244)
Checks proxy server information
- slui.exe (PID: 7388)
Reads the software policy settings
- slui.exe (PID: 7388)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:07:09 14:22:19+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 128000 |
| InitializedDataSize: | 218112 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x790a |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows command line |
Total processes
170
Monitored processes
20
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 480 | "C:\Users\admin\AppData\Local\Temp\Mail Access Checker by G-KLIT.exe" "--multiprocessing-fork" "parent_pid=7280" "pipe_handle=2228" | C:\Users\admin\AppData\Local\Temp\Mail Access Checker by G-KLIT.exe | — | Mail Access Checker by G-KLIT.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 696 | "C:\Users\admin\AppData\Local\Temp\Mail Access Checker by G-KLIT.exe" "--multiprocessing-fork" "parent_pid=7280" "pipe_handle=2088" | C:\Users\admin\AppData\Local\Temp\Mail Access Checker by G-KLIT.exe | — | Mail Access Checker by G-KLIT.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2312 | "C:\Users\admin\AppData\Local\Temp\Mail Access Checker by G-KLIT.exe" "--multiprocessing-fork" "parent_pid=7280" "pipe_handle=1940" | C:\Users\admin\AppData\Local\Temp\Mail Access Checker by G-KLIT.exe | — | Mail Access Checker by G-KLIT.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2332 | "C:\Users\admin\AppData\Local\Temp\Mail Access Checker by G-KLIT.exe" "--multiprocessing-fork" "parent_pid=7280" "pipe_handle=1904" | C:\Users\admin\AppData\Local\Temp\Mail Access Checker by G-KLIT.exe | — | Mail Access Checker by G-KLIT.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 3680 | "C:\Users\admin\AppData\Local\Temp\Mail Access Checker by G-KLIT.exe" "--multiprocessing-fork" "parent_pid=7280" "pipe_handle=3184" | C:\Users\admin\AppData\Local\Temp\Mail Access Checker by G-KLIT.exe | — | Mail Access Checker by G-KLIT.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4244 | "C:\Users\admin\AppData\Local\Temp\Mail Access Checker by G-KLIT.exe" "--multiprocessing-fork" "parent_pid=7280" "pipe_handle=3144" | C:\Users\admin\AppData\Local\Temp\Mail Access Checker by G-KLIT.exe | — | Mail Access Checker by G-KLIT.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4784 | "C:\Users\admin\AppData\Local\Temp\Mail Access Checker by G-KLIT.exe" "--multiprocessing-fork" "parent_pid=7280" "pipe_handle=1968" | C:\Users\admin\AppData\Local\Temp\Mail Access Checker by G-KLIT.exe | — | Mail Access Checker by G-KLIT.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5956 | "C:\Users\admin\AppData\Local\Temp\Mail Access Checker by G-KLIT.exe" "--multiprocessing-fork" "parent_pid=7280" "pipe_handle=3796" | C:\Users\admin\AppData\Local\Temp\Mail Access Checker by G-KLIT.exe | — | Mail Access Checker by G-KLIT.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6124 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\SysWOW64\cmd.exe | — | Mail Access Checker by G-KLIT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6360 | "C:\Users\admin\AppData\Local\Temp\Mail Access Checker by G-KLIT.exe" "--multiprocessing-fork" "parent_pid=7280" "pipe_handle=1808" | C:\Users\admin\AppData\Local\Temp\Mail Access Checker by G-KLIT.exe | — | Mail Access Checker by G-KLIT.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
11 495
Read events
11 417
Write events
75
Delete events
3
Modification events
| (PID) Process: | (7280) Mail Access Checker by G-KLIT.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (7280) Mail Access Checker by G-KLIT.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000001200000000000000110000000E000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (7280) Mail Access Checker by G-KLIT.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000005000000030000000200000001000000FFFFFFFF | |||
| (PID) Process: | (7280) Mail Access Checker by G-KLIT.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Documents | |||
| (PID) Process: | (7280) Mail Access Checker by G-KLIT.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 136 | |||
| (PID) Process: | (7280) Mail Access Checker by G-KLIT.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000100000000000000050000000300000002000000FFFFFFFF | |||
| (PID) Process: | (7280) Mail Access Checker by G-KLIT.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (7280) Mail Access Checker by G-KLIT.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (7280) Mail Access Checker by G-KLIT.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | FFlags |
Value: | |||
| (PID) Process: | (7280) Mail Access Checker by G-KLIT.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | IconSize |
Value: 16 | |||
Executable files
19
Suspicious files
3
Text files
908
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7376 | Mail Access Checker by G-KLIT.exe | C:\Users\admin\AppData\Local\Temp\_MEI73762\_lzma.pyd | executable | |
MD5:65880A33015AF2030A08987924CA737B | SHA256:A71366B95D89D1539A6EE751D48A969C1BCA1AA75116424CC5F905F32A625EEA | |||
| 7376 | Mail Access Checker by G-KLIT.exe | C:\Users\admin\AppData\Local\Temp\_MEI73762\_multiprocessing.pyd | executable | |
MD5:42A5EC2E2EC56DCA18E7221C1858A7DE | SHA256:C22D475ADA5E8D7EA37124892B4A3D8315E6E66594A2237DCB0BBDF160B053DE | |||
| 7376 | Mail Access Checker by G-KLIT.exe | C:\Users\admin\AppData\Local\Temp\_MEI73762\_ctypes.pyd | executable | |
MD5:9DB2D9962CBD754E91B40F91CBC49542 | SHA256:6A6DF7D77B7A5552D8443BD1B98F681AD2E6B5A8ACF7ADE542DD369BEAB7E439 | |||
| 7376 | Mail Access Checker by G-KLIT.exe | C:\Users\admin\AppData\Local\Temp\_MEI73762\_bz2.pyd | executable | |
MD5:FF5AC8FB724EDB1635E2AD985F98EE5B | SHA256:B94F64FCB49F40682ED794FA1940A1DC0C8A28F24A1768D3BFE774CF75F59B62 | |||
| 7376 | Mail Access Checker by G-KLIT.exe | C:\Users\admin\AppData\Local\Temp\_MEI73762\_ssl.pyd | executable | |
MD5:CC5C8EB32ACB2261C42A7285D436CCA9 | SHA256:07EA50E536886F68473635FFEFCFCAA7266E63C478EF039BA100DDF02F88CE61 | |||
| 7376 | Mail Access Checker by G-KLIT.exe | C:\Users\admin\AppData\Local\Temp\_MEI73762\_decimal.pyd | executable | |
MD5:E4292AD50769F592F34BC63F62A5E428 | SHA256:0240F15B44E2D3E37EBEFBB221D3D6017BE5EF99806EC4E36C3521F284CB8043 | |||
| 7376 | Mail Access Checker by G-KLIT.exe | C:\Users\admin\AppData\Local\Temp\_MEI73762\_tkinter.pyd | executable | |
MD5:E46970E8EB0061DF01347A3723140E77 | SHA256:71C4545CEE713F26CF2F910A08340DD519C4713B8416479F74B0B9E2683C85D5 | |||
| 7376 | Mail Access Checker by G-KLIT.exe | C:\Users\admin\AppData\Local\Temp\_MEI73762\_queue.pyd | executable | |
MD5:8807DC228BB761439DC6525A2966E27E | SHA256:B7ED6DFB6882E8EC4267D9F80CD5B1DC0A43519382FCB72AB5E74C47875C209D | |||
| 7376 | Mail Access Checker by G-KLIT.exe | C:\Users\admin\AppData\Local\Temp\_MEI73762\_socket.pyd | executable | |
MD5:A4BD8E0C0597A22C3F0601FE798668AA | SHA256:96B0A3CFC16E215F0EF5D1E206F0137B4255005052720E91A58BC98CDE8C898E | |||
| 7376 | Mail Access Checker by G-KLIT.exe | C:\Users\admin\AppData\Local\Temp\_MEI73762\pyexpat.pyd | executable | |
MD5:F4AC522E0A04829BBA2B8FCA878F560E | SHA256:87A1D8B94668C55AC0B67E05A9505031E38510CFD2A47979697C05B7C7B375A2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
29
DNS requests
23
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5040 | svchost.exe | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1376 | svchost.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8056 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.3.crl | unknown | — | — | whitelisted |
8056 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.3.crl | unknown | — | — | whitelisted |
8056 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Time-Stamp%20PCA%202010(1).crl | unknown | — | — | whitelisted |
8056 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
5284 | backgroundTaskHost.exe | GET | 200 | 162.159.142.9:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6680 | svchost.exe | GET | 200 | 162.159.142.9:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5040 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5596 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1284 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7088 | SearchApp.exe | 2.16.204.141:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5040 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5040 | svchost.exe | 2.16.164.72:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5040 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1376 | svchost.exe | 40.126.31.1:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |