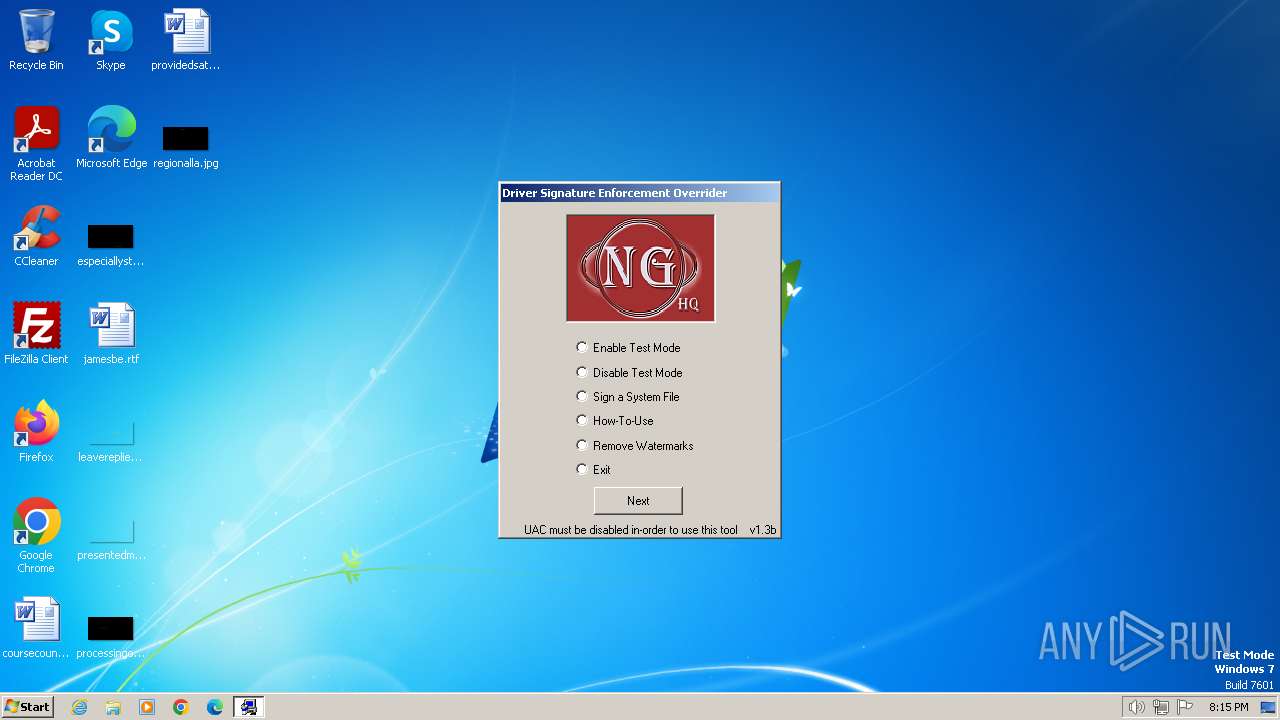
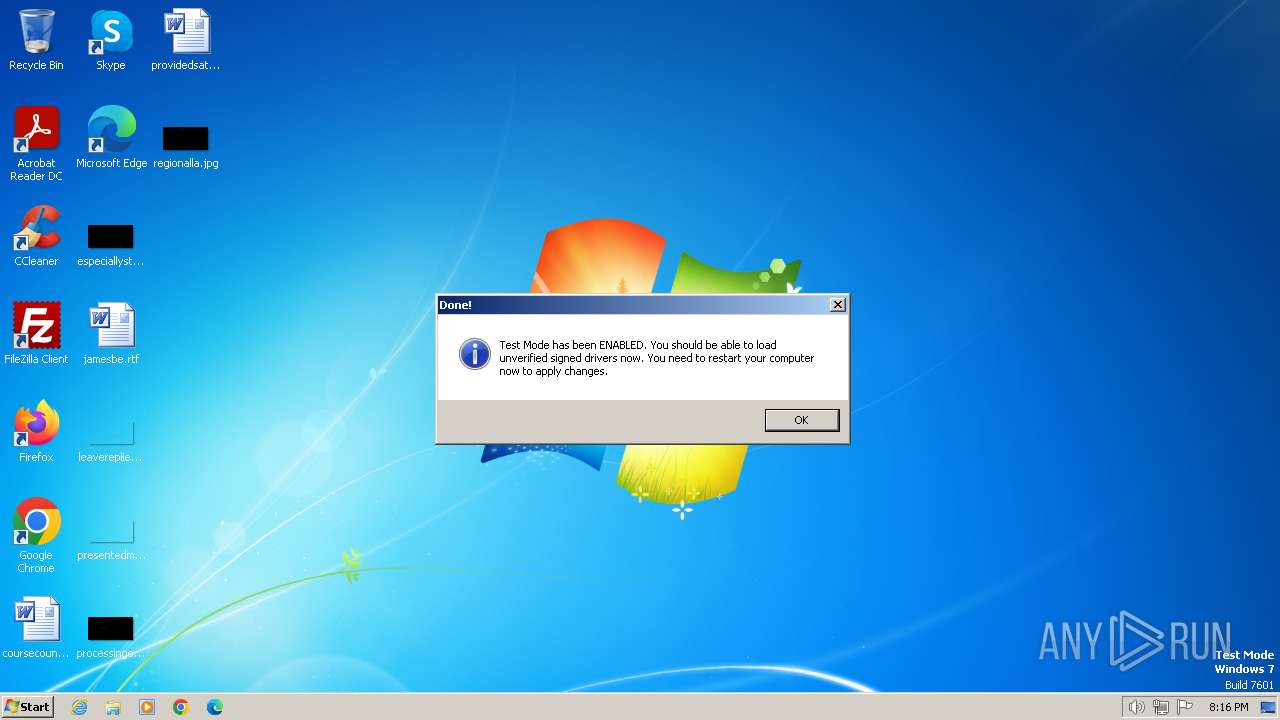
| File name: | dseo13b.exe |
| Full analysis: | https://app.any.run/tasks/b5e469cb-0d25-4f46-85bf-9ccd76b9a3be |
| Verdict: | Malicious activity |
| Analysis date: | February 04, 2024, 20:15:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 6DDEB31C98A188378F0652CD90FC50FF |
| SHA1: | D7922F2DCB47A37CF798DFFB824F840DDEF7FFD5 |
| SHA256: | 39036A8F2CA0430FD57D86563BC783E0F1AD3144540B87CF2EC2DDE9ABB3B8CD |
| SSDEEP: | 24576:2YNh+XEAcdWLg0IsqNqQZpCkPdba7SYLa7SYra7SY0mcrCZ9eeGy71+ltipzc5TS:BNh+UAcdWLzIshQSkPdm7SYW7SY27SYb |
MALICIOUS
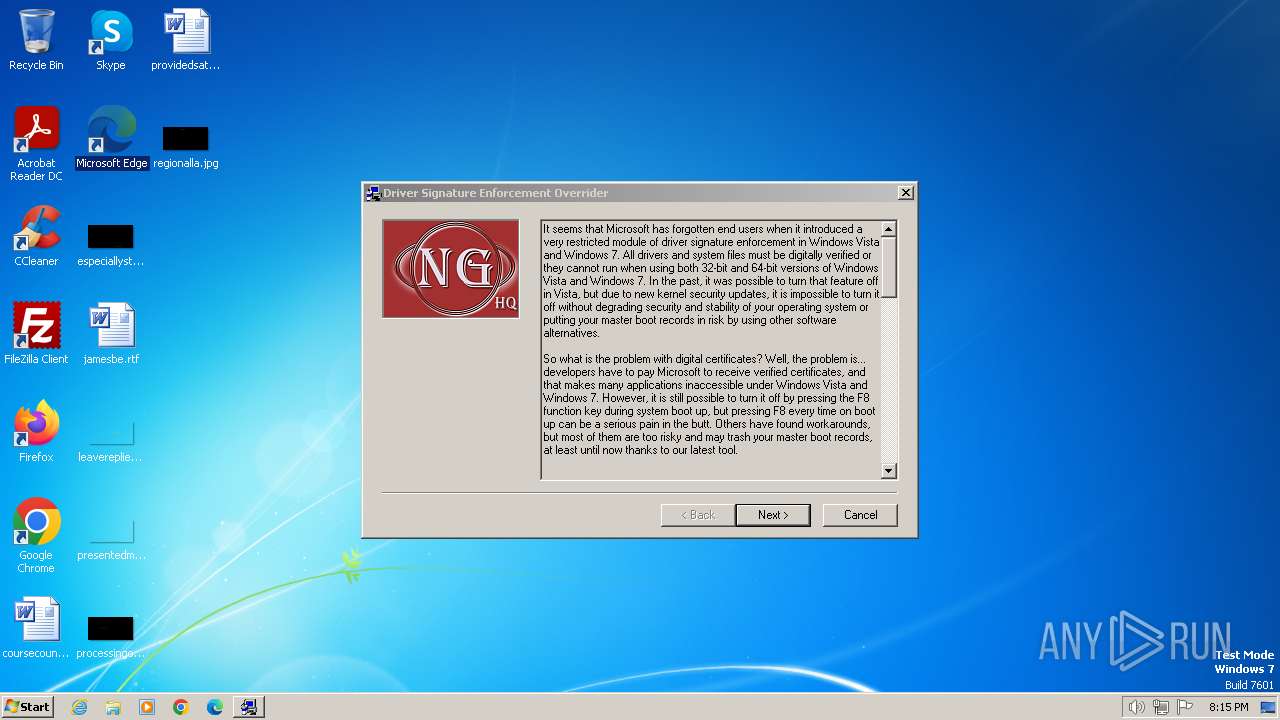
Drops the executable file immediately after the start
- dseo13b.exe (PID: 4092)
SUSPICIOUS
Executable content was dropped or overwritten
- dseo13b.exe (PID: 4092)
The process creates files with name similar to system file names
- dseo13b.exe (PID: 4092)
Process drops legitimate windows executable
- dseo13b.exe (PID: 4092)
Reads the Internet Settings
- dseo13b.exe (PID: 4092)
INFO
Checks supported languages
- dseo13b.exe (PID: 4092)
- bcdedit.exe (PID: 2380)
Reads the computer name
- dseo13b.exe (PID: 4092)
Create files in a temporary directory
- dseo13b.exe (PID: 4092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2003:03:10 18:22:47+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 49152 |
| InitializedDataSize: | 12288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x646b |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
42
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 532 | "C:\Users\admin\AppData\Local\Temp\dseo13b.exe" | C:\Users\admin\AppData\Local\Temp\dseo13b.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2380 | "C:\Windows\bcdedit.exe" /set TESTSIGNING ON | C:\Windows\bcdedit.exe | — | dseo13b.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 4092 | "C:\Users\admin\AppData\Local\Temp\dseo13b.exe" | C:\Users\admin\AppData\Local\Temp\dseo13b.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
252
Read events
243
Write events
9
Delete events
0
Modification events
| (PID) Process: | (4092) dseo13b.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4092) dseo13b.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4092) dseo13b.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4092) dseo13b.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2380) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{345b46fd-a9f9-11e7-a83c-e8a4f72b1d33}\Elements\16000049 |
| Operation: | write | Name: | Element |
Value: 01 | |||
Executable files
5
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4092 | dseo13b.exe | C:\Users\admin\AppData\Local\Temp\~vis0000\English.vlg | text | |
MD5:AA00F72BFC4B20E2EF89A6D705C19345 | SHA256:ADA22EB8E66B404689FABF256E185DD0A9005B7BC7E6C616DB27ED7DBEC080A5 | |||
| 4092 | dseo13b.exe | C:\Users\admin\AppData\Local\Temp\~vis0000\miscdata.xyz | binary | |
MD5:A0064E619964DE638FDCF7EA18319EDB | SHA256:96EA911FB86245D8D57B8AF1F8680A0D531B84FA931CC7E6EAF6FC7AA745F8AE | |||
| 4092 | dseo13b.exe | C:\Windows\bcdedit.exe | executable | |
MD5:C216469F755493B29518B9ECBEE99CBC | SHA256:3D88DD98F488D92F724B1D253C966E92C4B2664A8B0AC03D5850D6D768B5FEB5 | |||
| 4092 | dseo13b.exe | C:\Users\admin\AppData\Local\Temp\~vis0000\v0000005.488 | executable | |
MD5:C216469F755493B29518B9ECBEE99CBC | SHA256:3D88DD98F488D92F724B1D253C966E92C4B2664A8B0AC03D5850D6D768B5FEB5 | |||
| 4092 | dseo13b.exe | C:\Users\admin\AppData\Local\Temp\~vis0000\vise32ex.dll | executable | |
MD5:54925D8AEA245A7BE34EC34402B2865B | SHA256:EE0D08A2B5888B1E127F11FEE8BF91D274E4126D571C62654B97270A11BE7C0F | |||
| 4092 | dseo13b.exe | C:\Users\admin\AppData\Local\Temp\~vis0000\rebootnt.exe | executable | |
MD5:C459E252866435ED8B928D1509C28DE2 | SHA256:4887FF02F8E45F5E03E351CB5156111659CC1B04FDCA9DAE3BD75CB99381DEDE | |||
| 4092 | dseo13b.exe | C:\Users\admin\AppData\Local\Temp\~vis0000\default.bmp | image | |
MD5:4B6AD7D5E4B4F631F7F78DD049E5326B | SHA256:B76620E328E1C40C43965FF65023C995C455B4EC150D55024ABFF46718EA9EC9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |