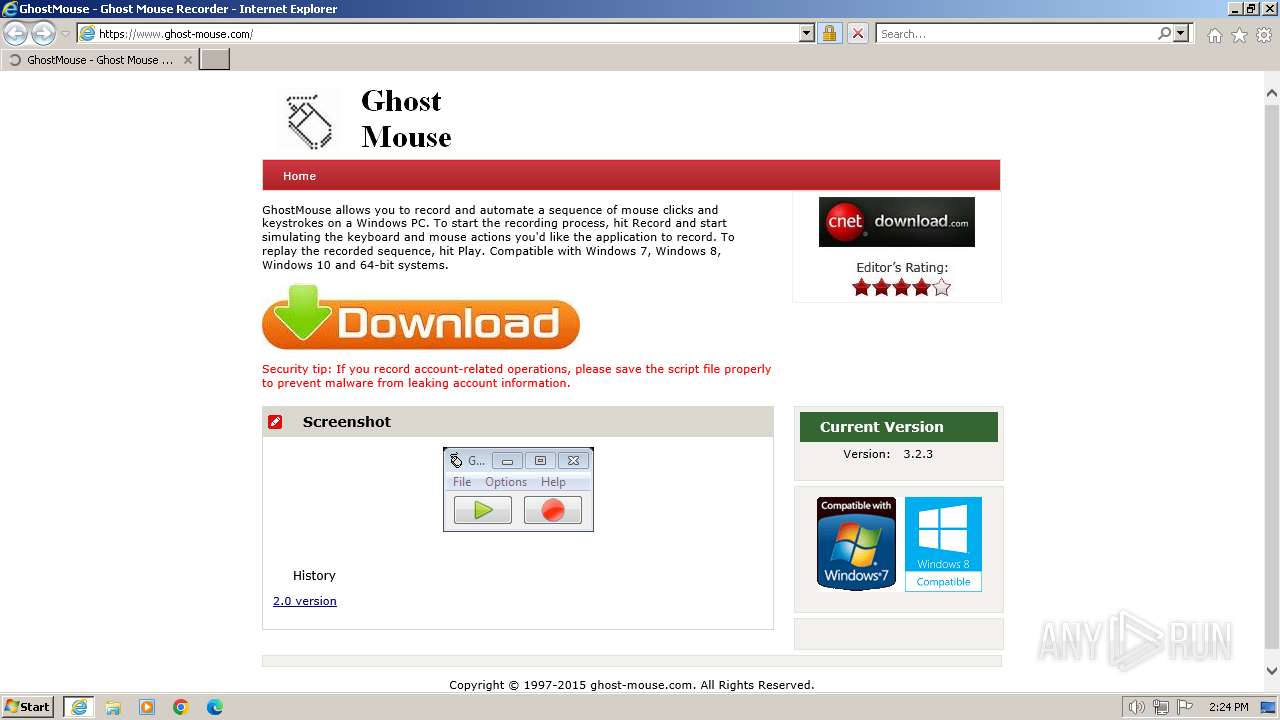
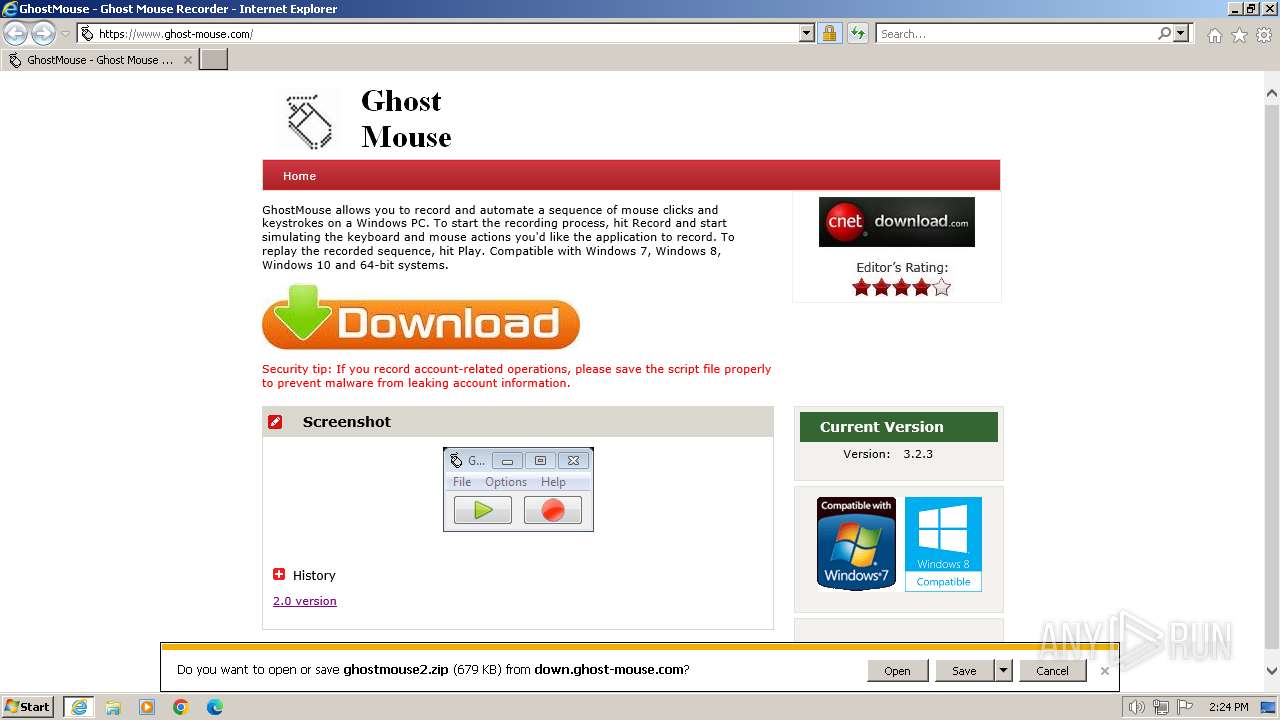
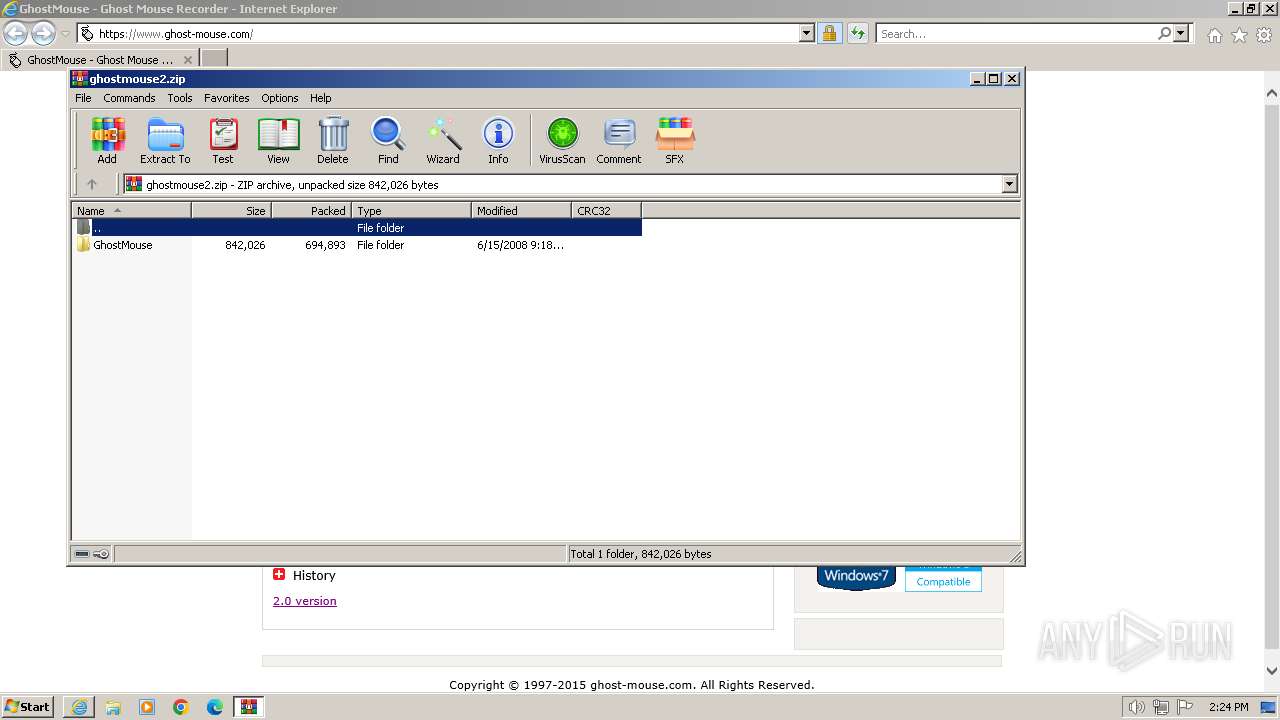
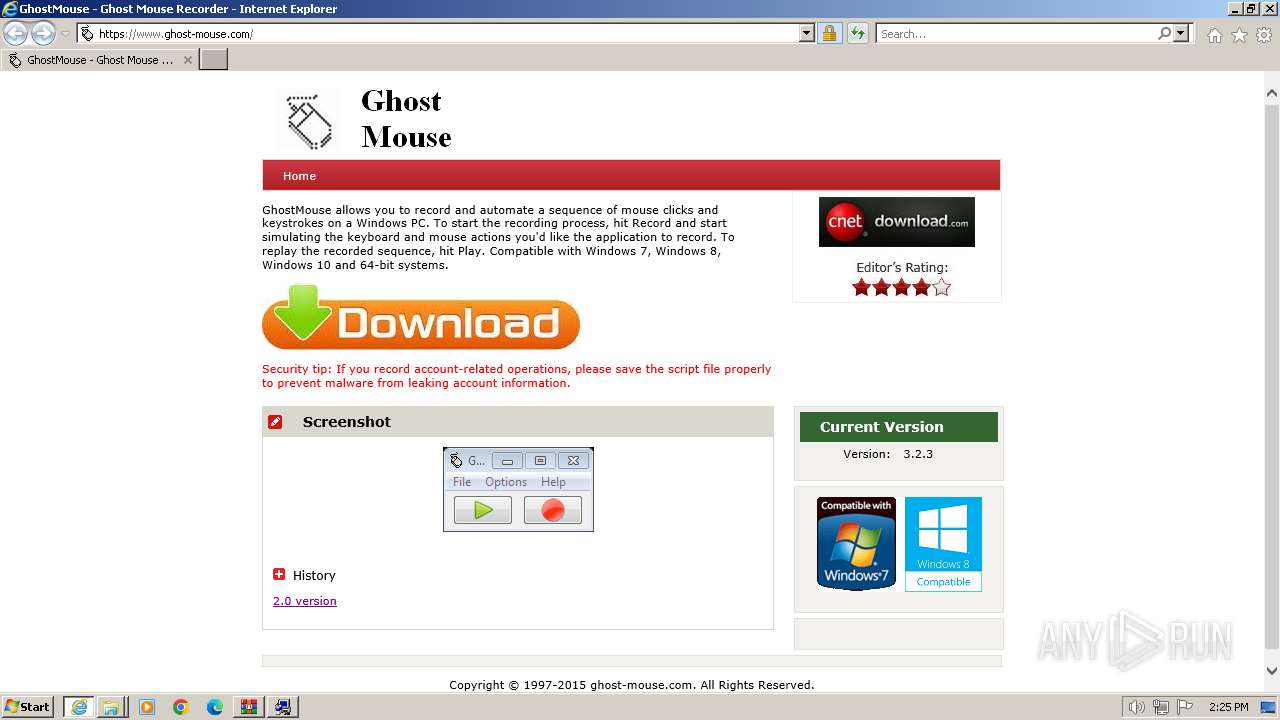
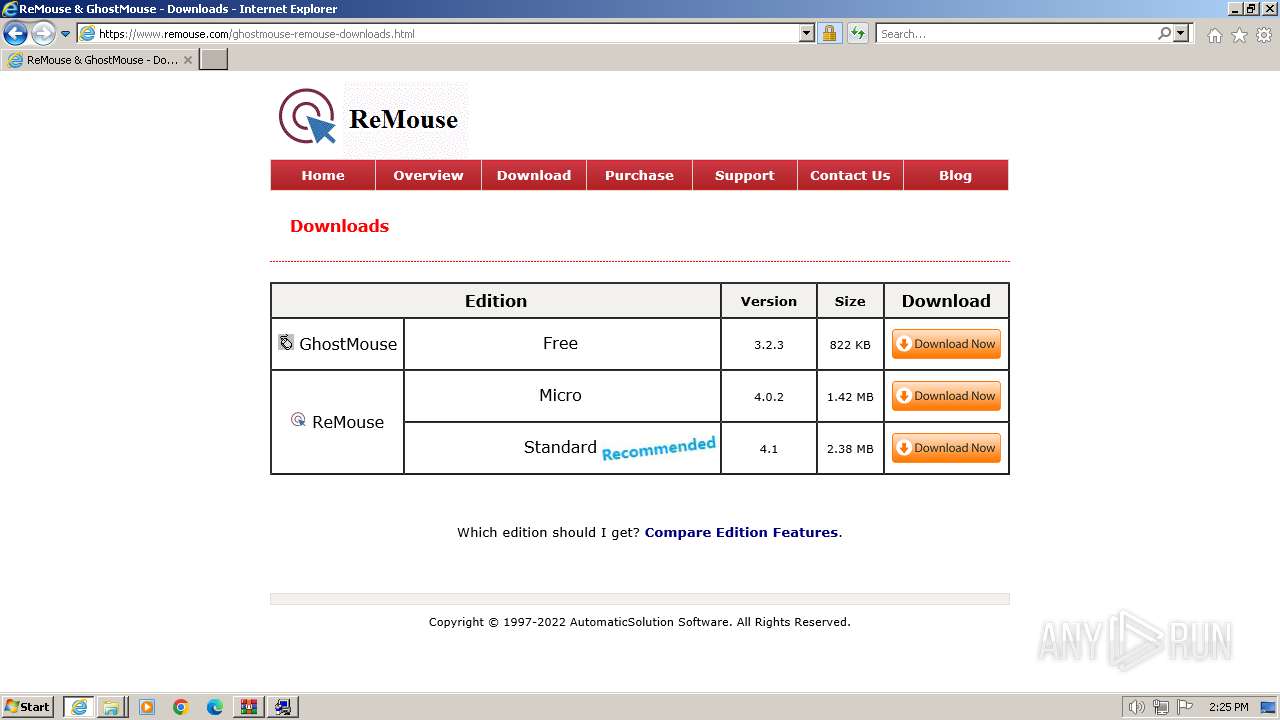
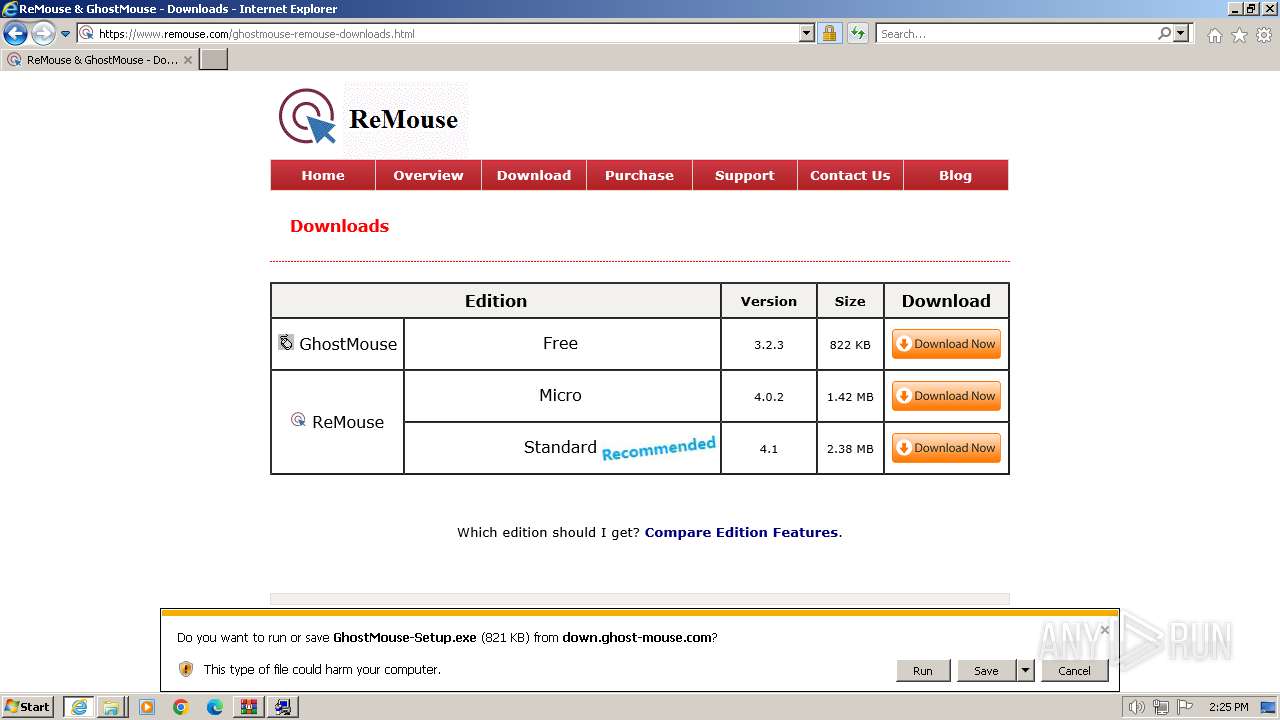
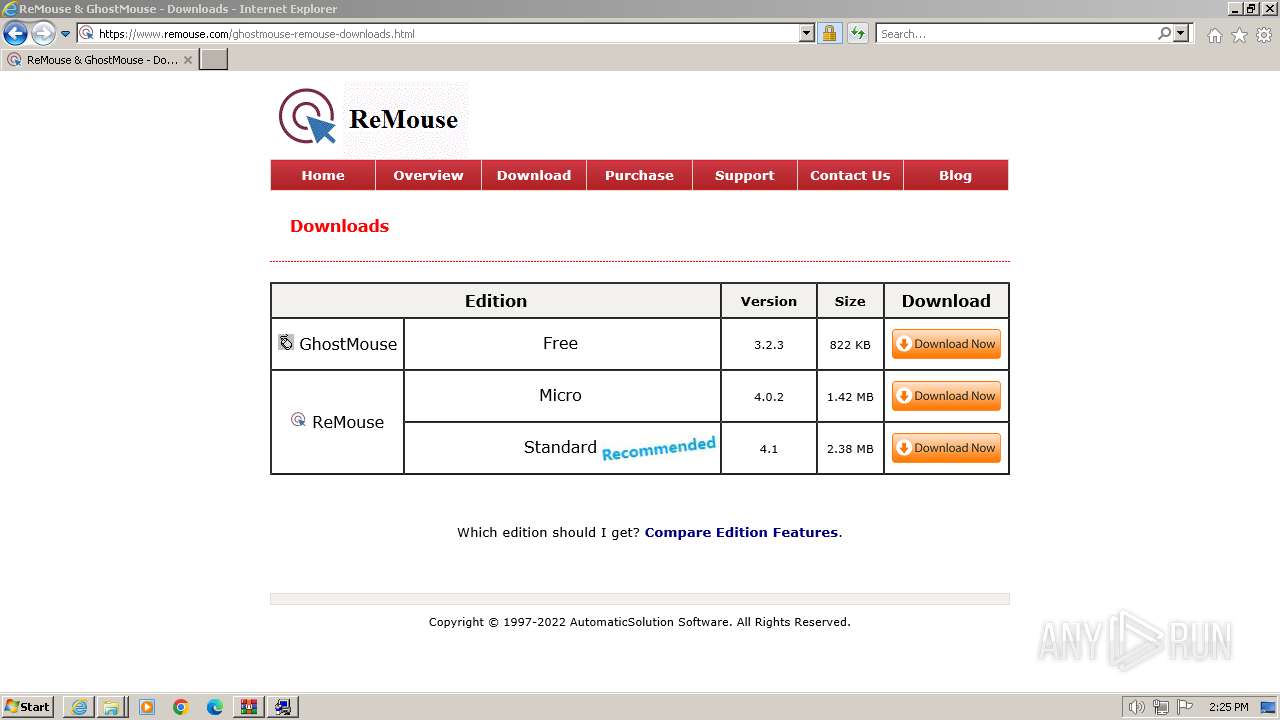
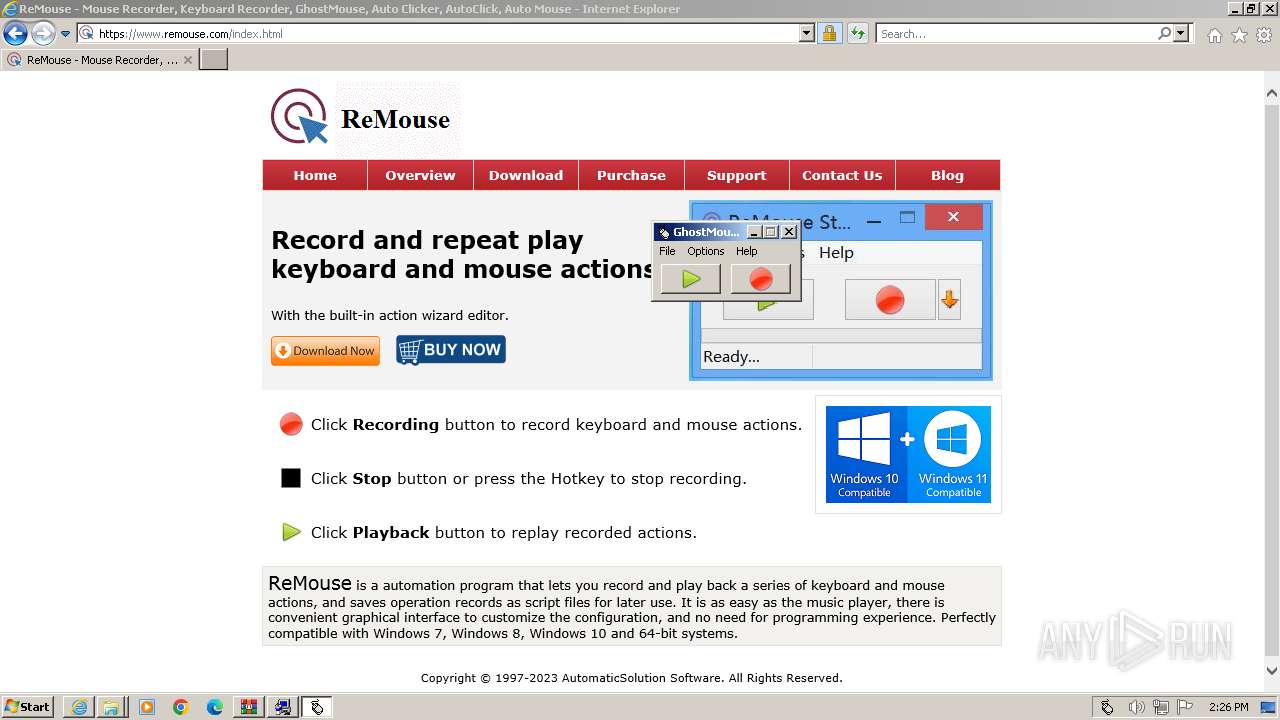
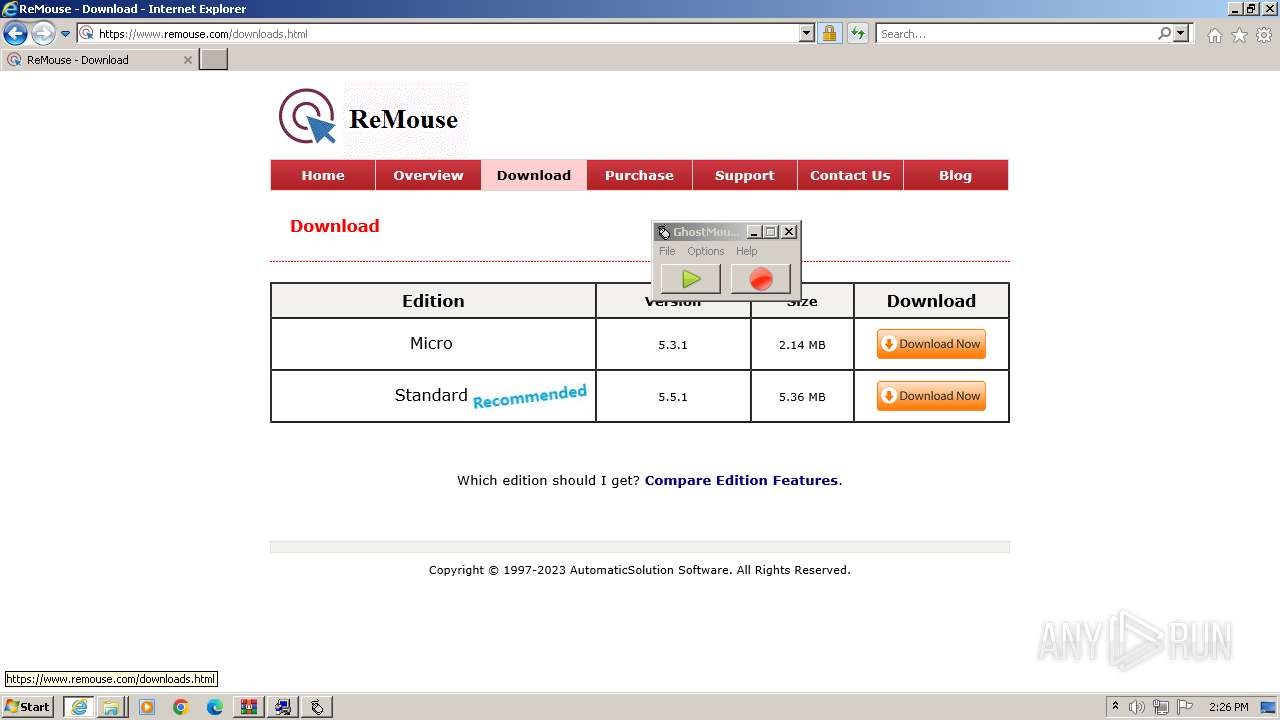
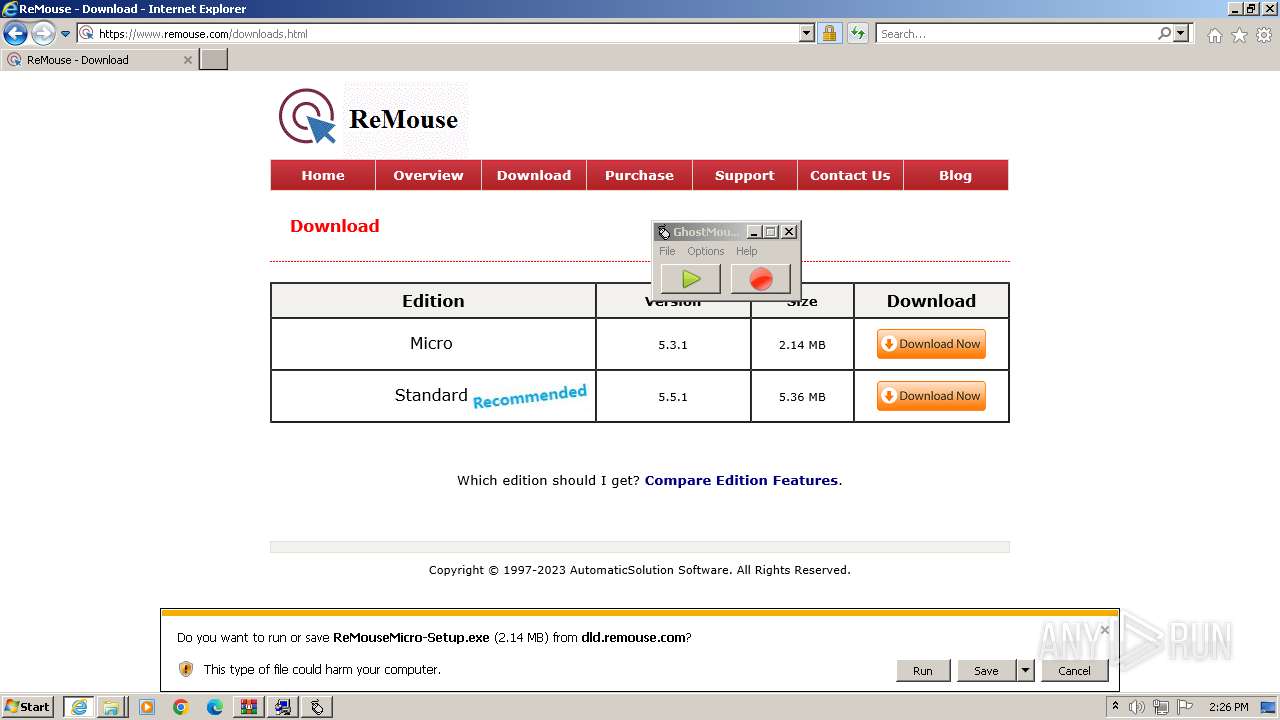
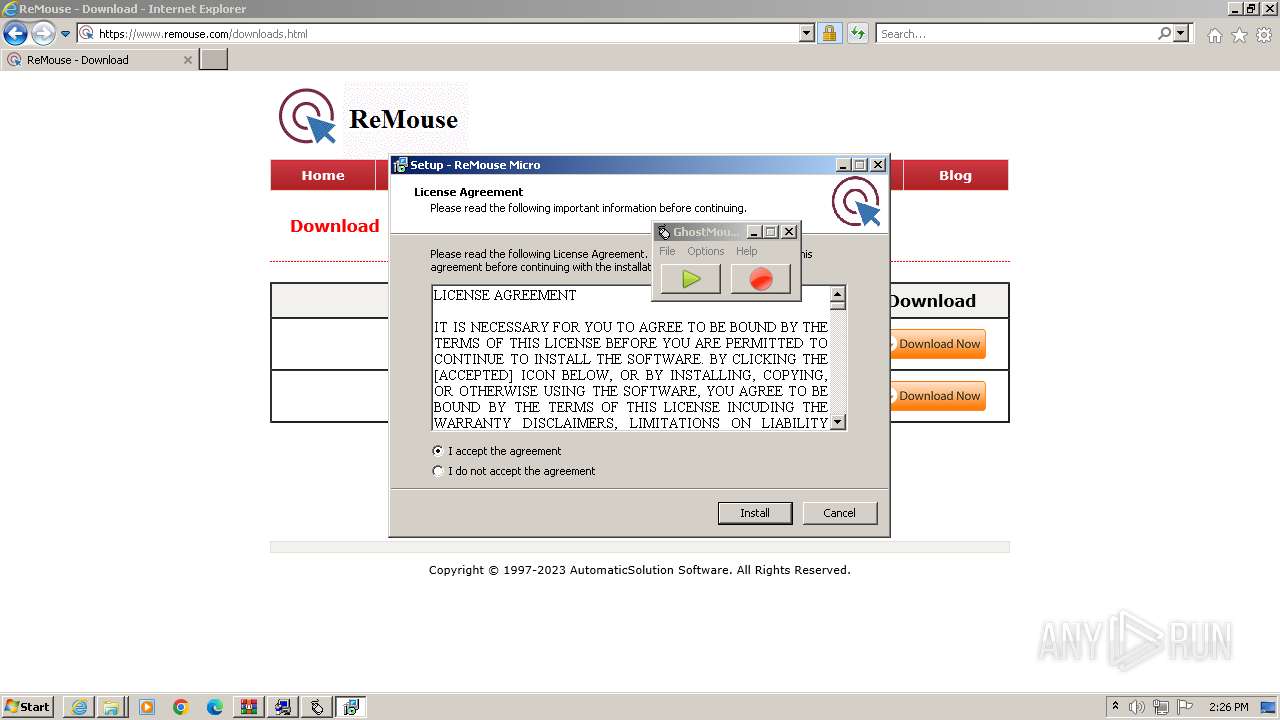
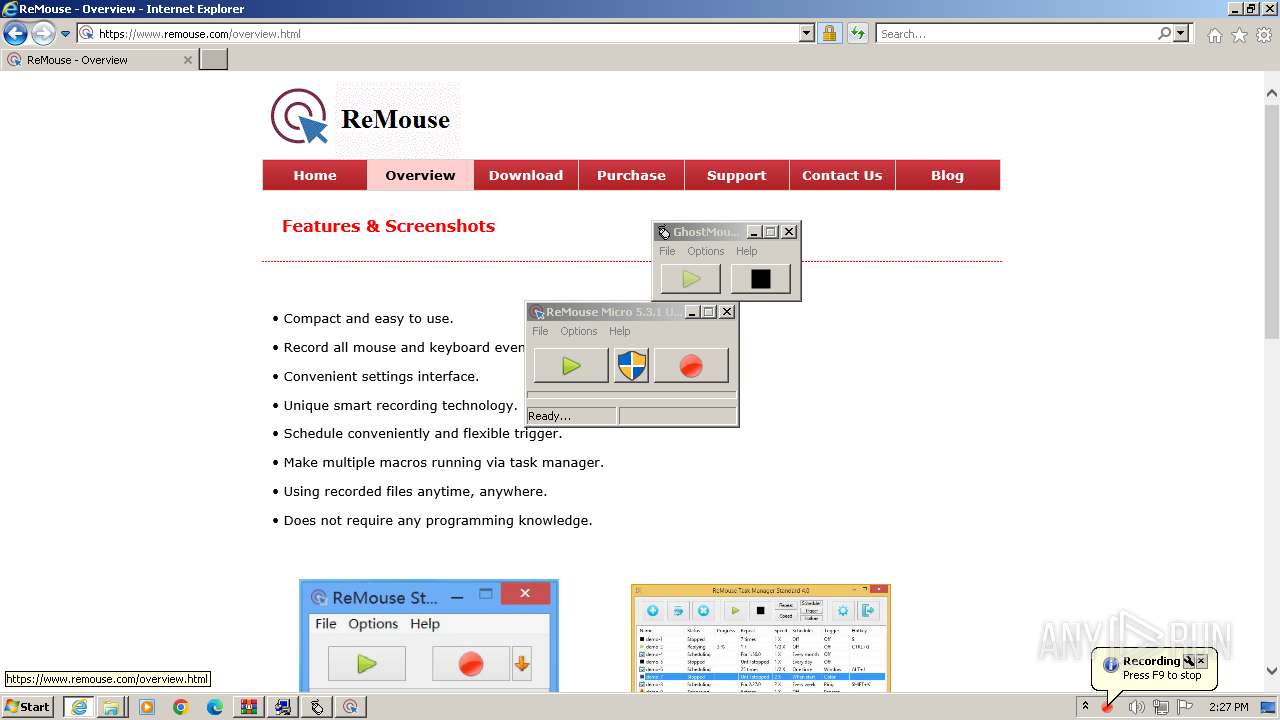
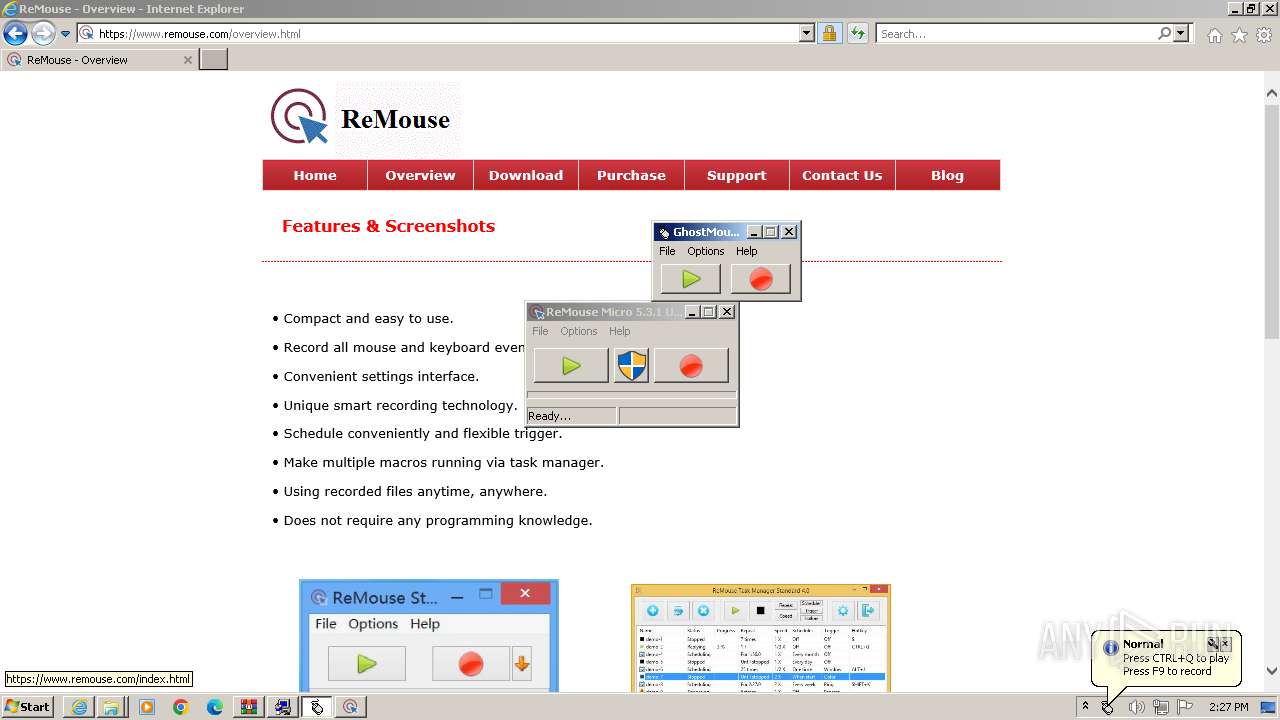
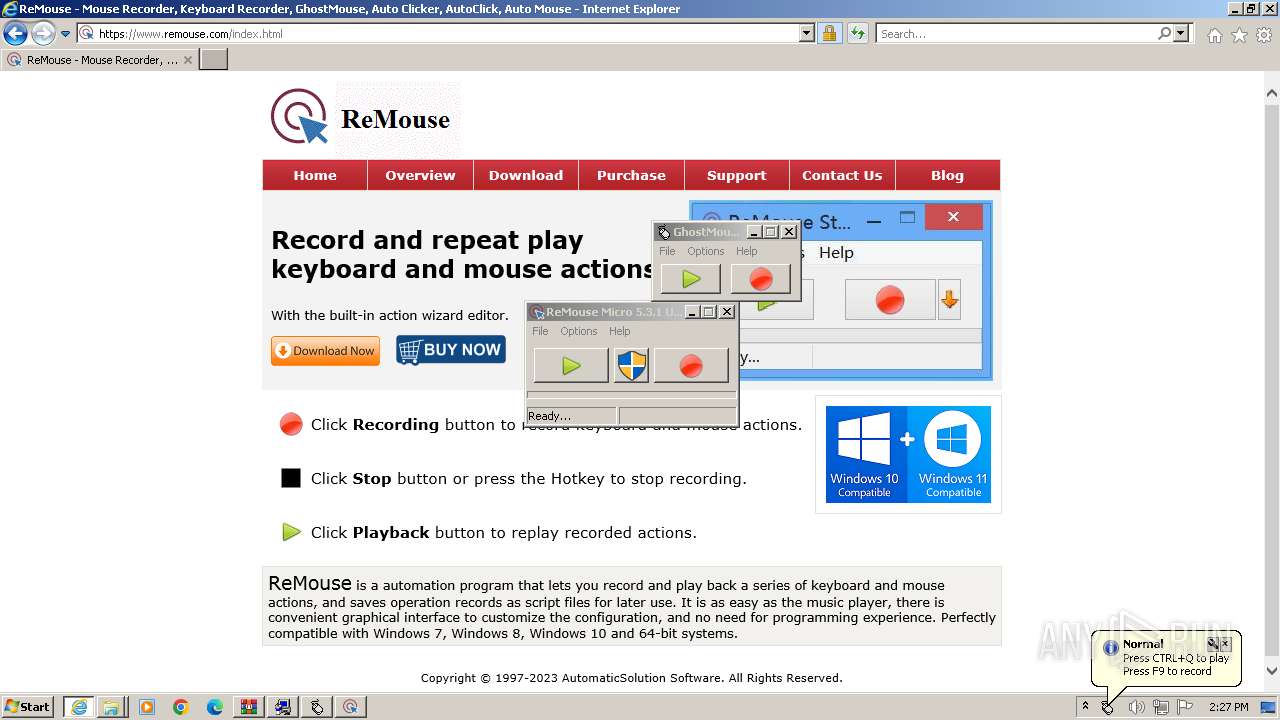
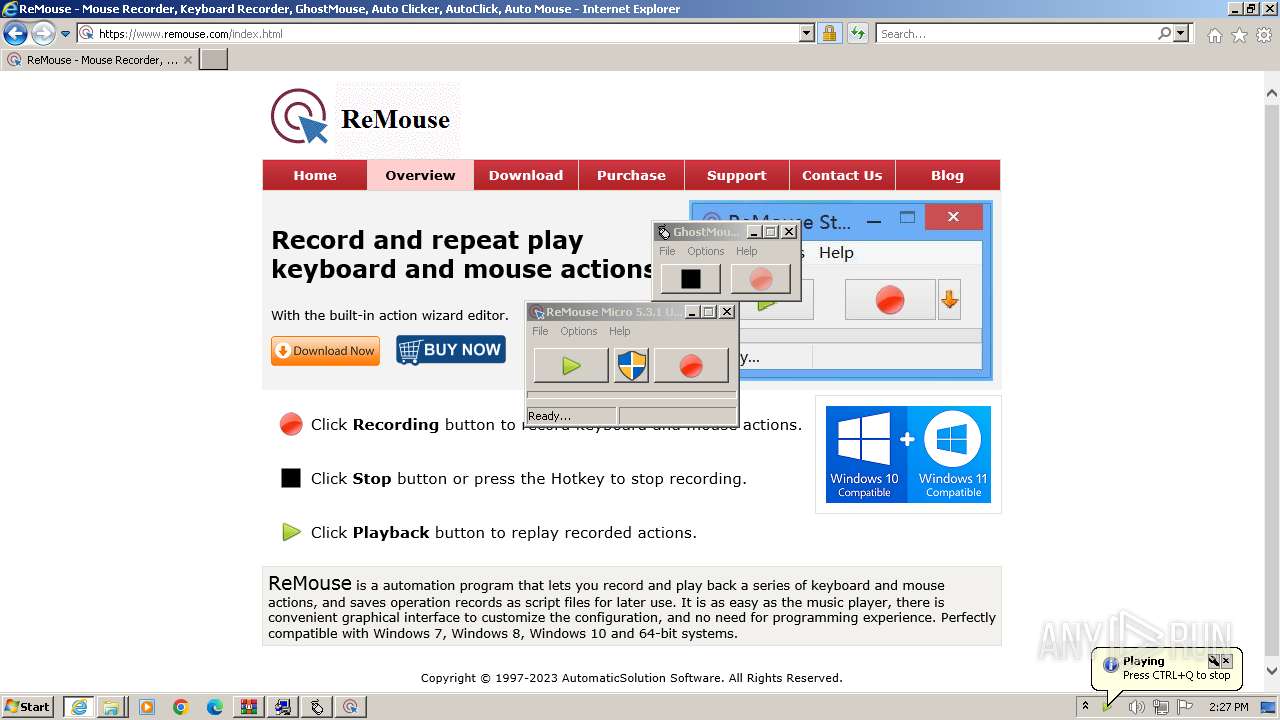
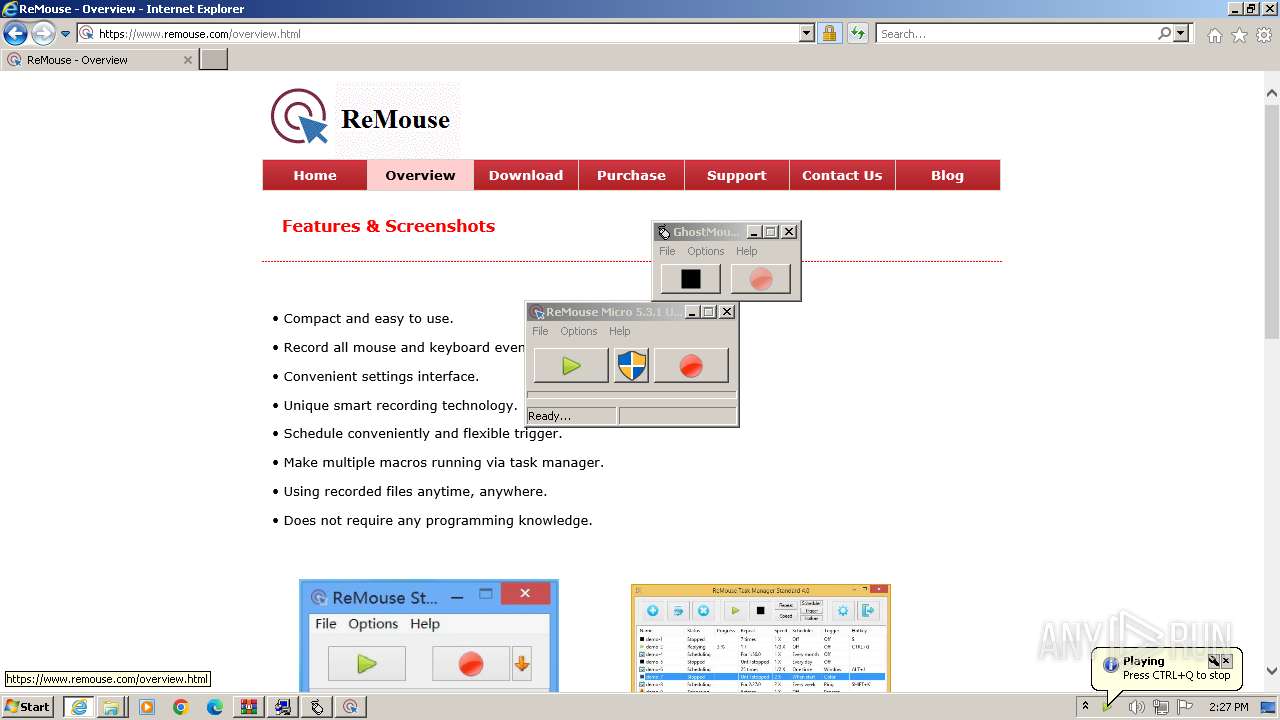
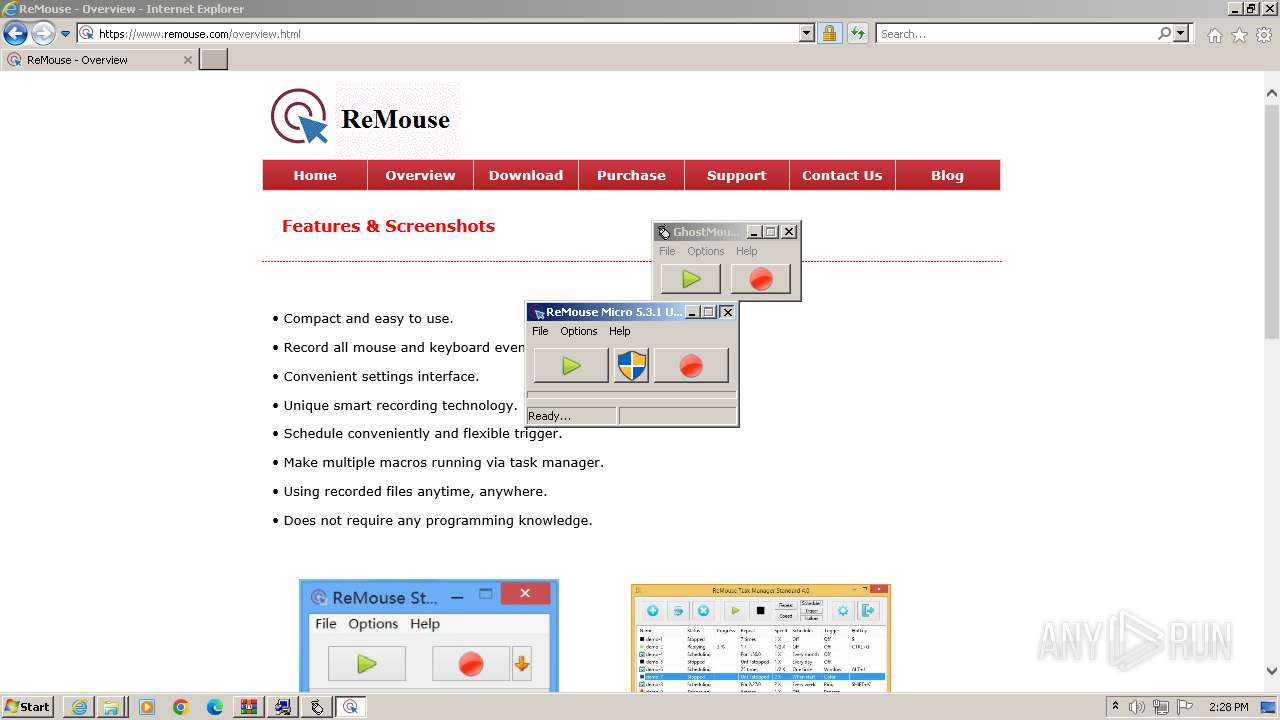
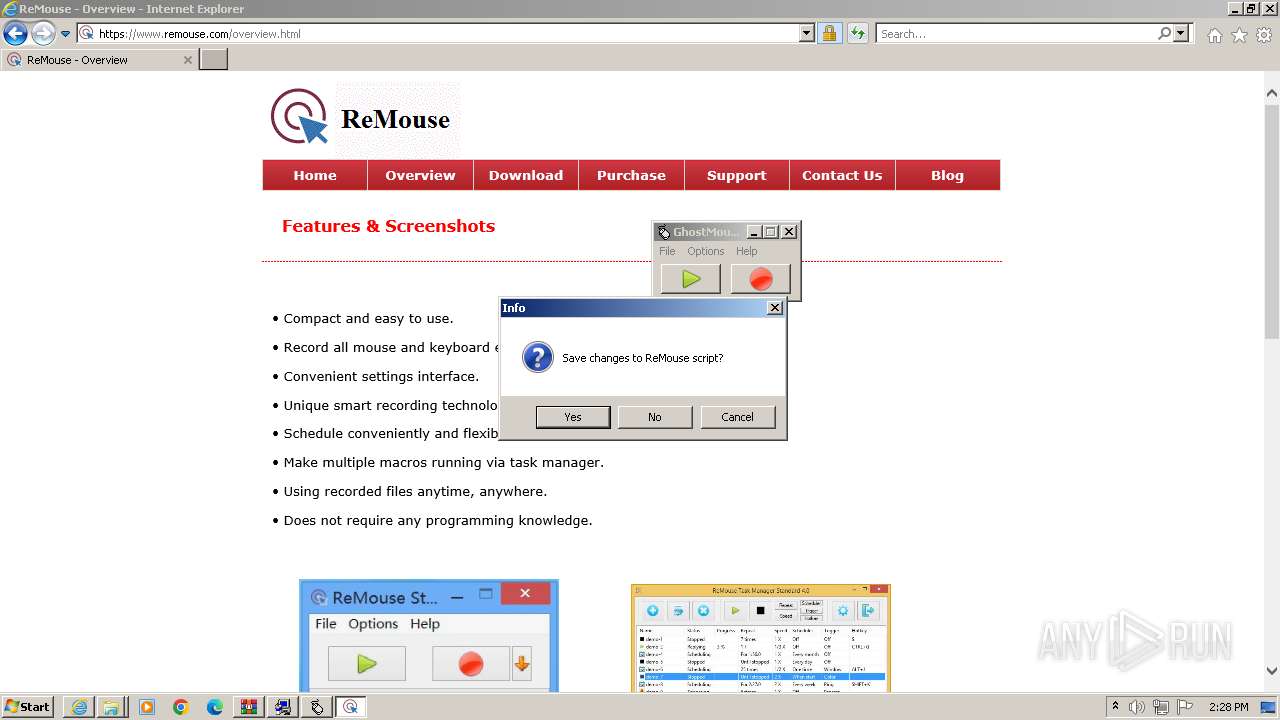
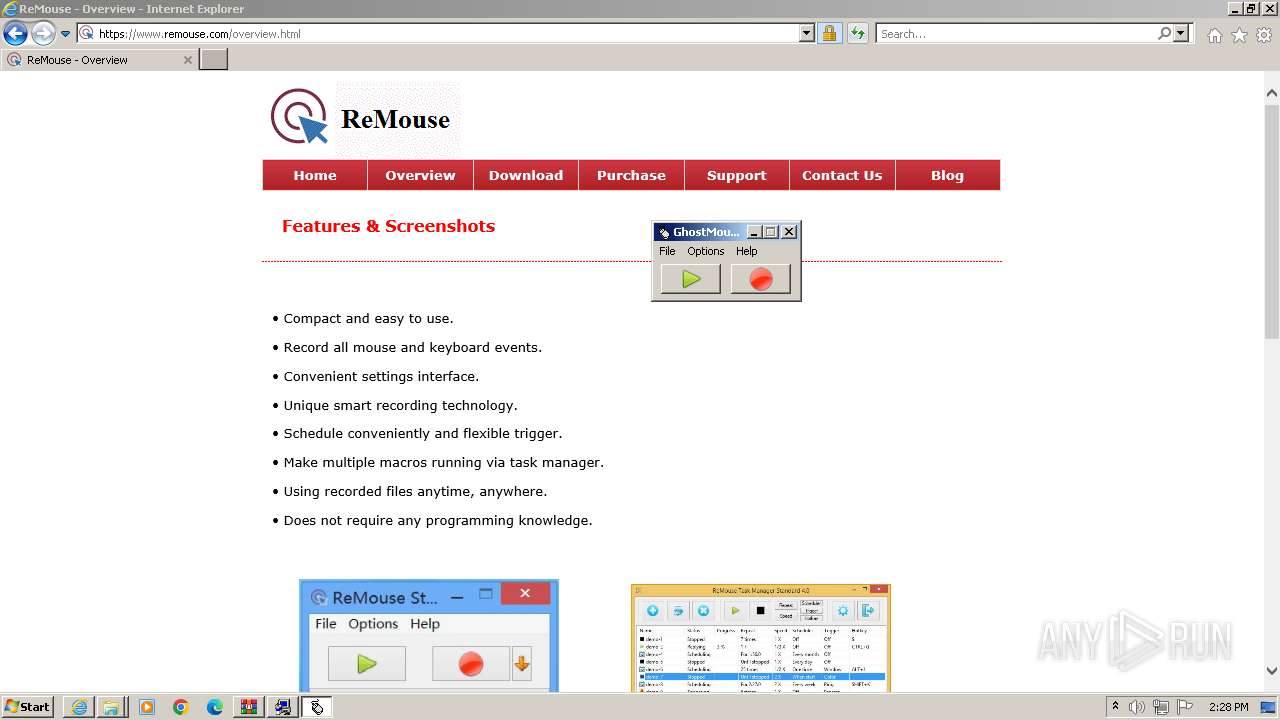
| URL: | https://www.ghost-mouse.com/ |
| Full analysis: | https://app.any.run/tasks/d7f977b4-44be-4e4e-80e0-4427f3ede3c9 |
| Verdict: | Malicious activity |
| Analysis date: | March 12, 2024, 14:23:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 11AFA5825B7799E71FEA4B1B719CBD21 |
| SHA1: | 8E2A813F3217D8628DB48EC0BB4BBB0BE2EACFF2 |
| SHA256: | 38FD6B137170424C247AA0BE900B2FC24259B0DAED00022423A7318F4AB2A6B6 |
| SSDEEP: | 3:N8DSLMHK6dIKn:2OLKK6KK |
MALICIOUS
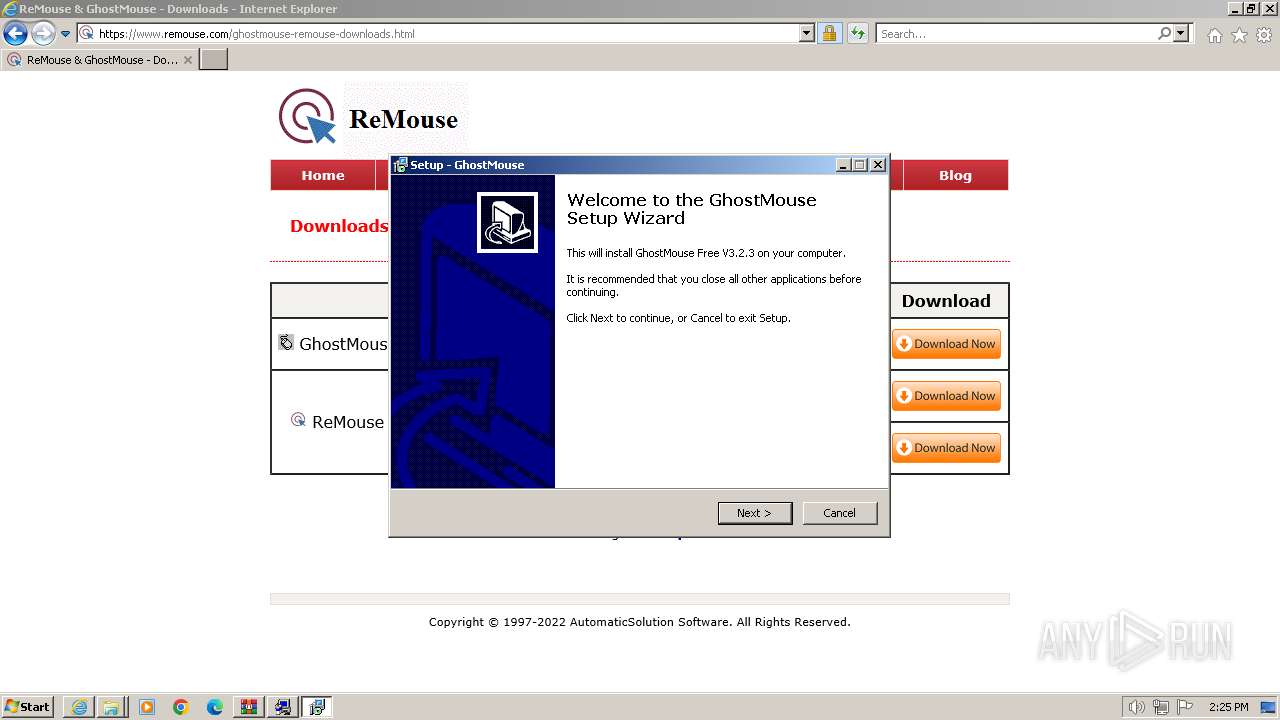
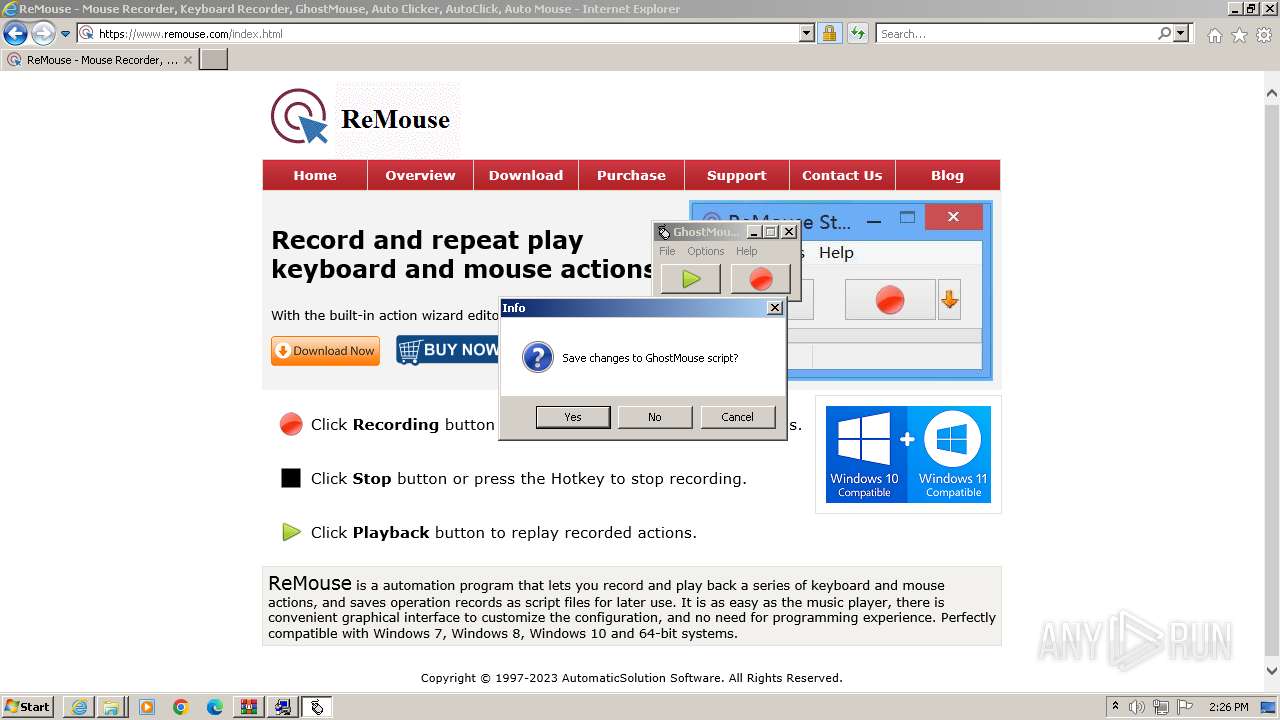
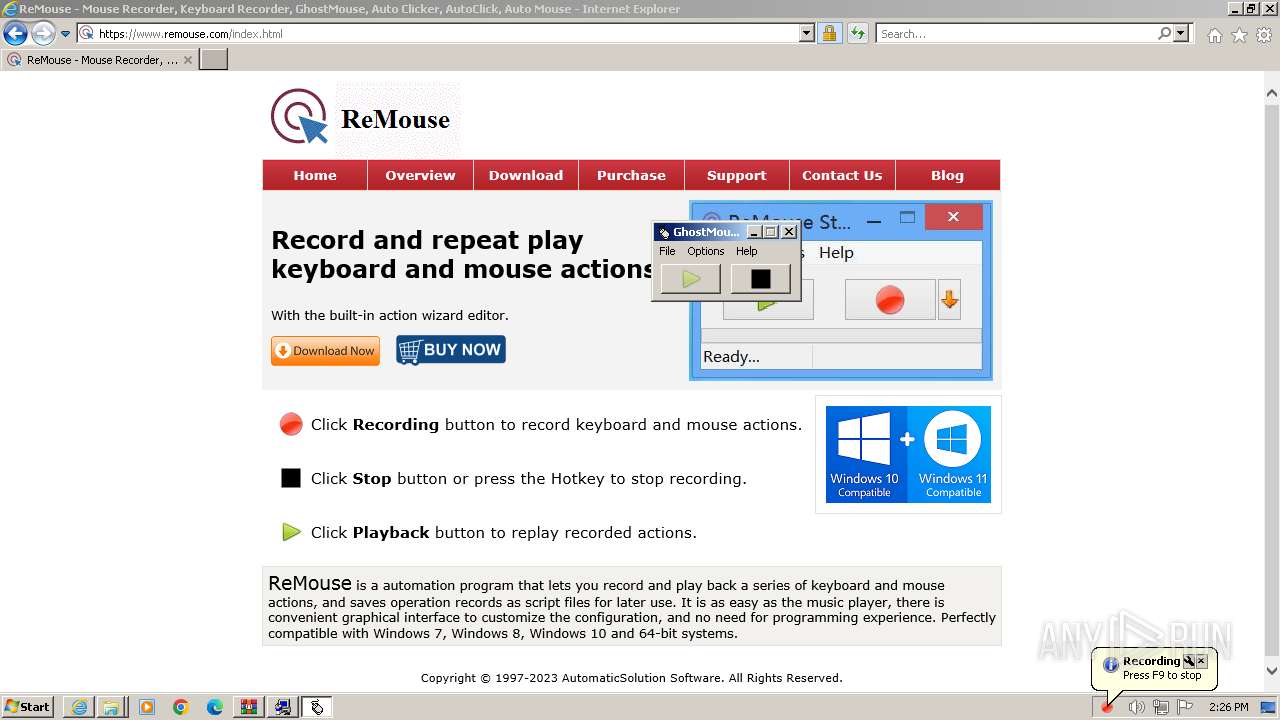
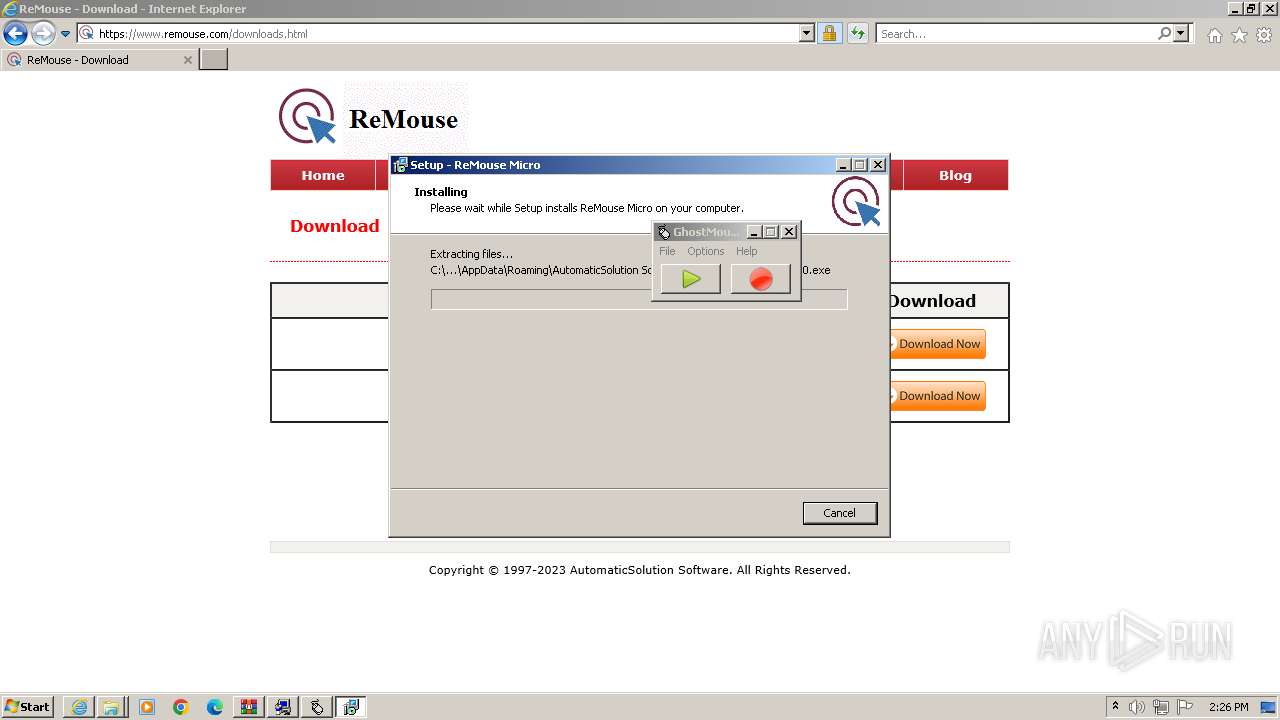
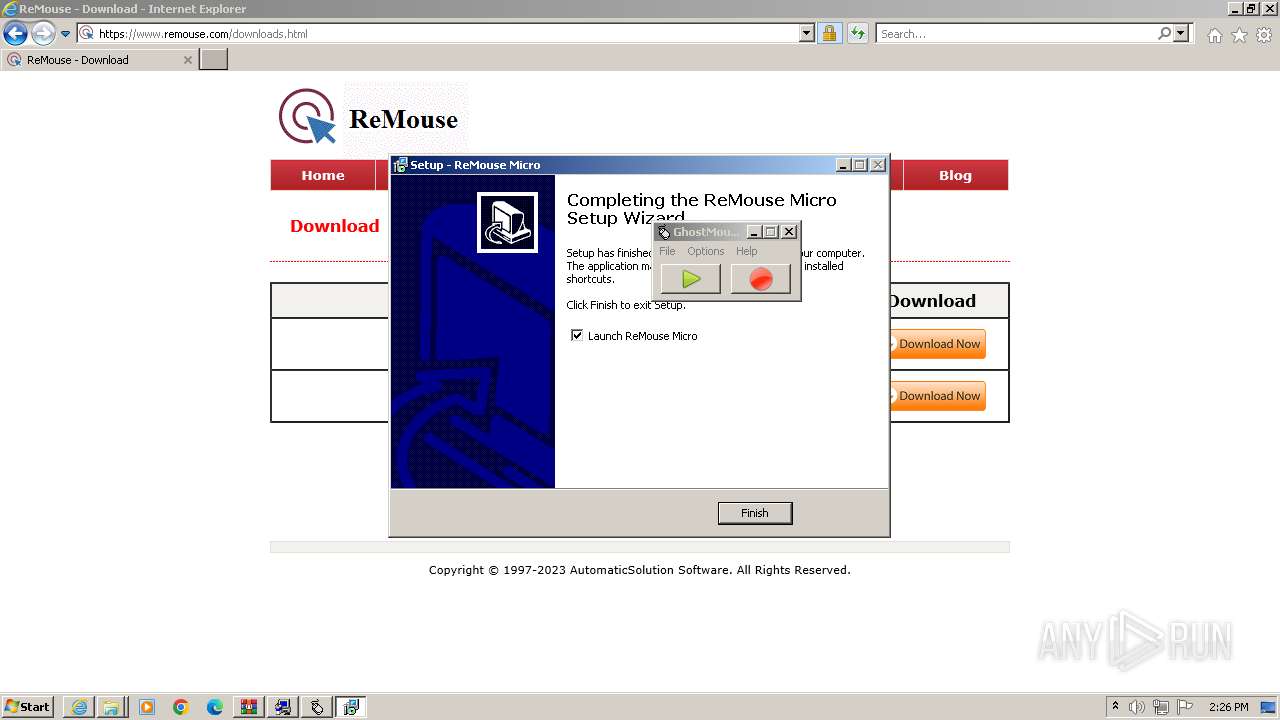
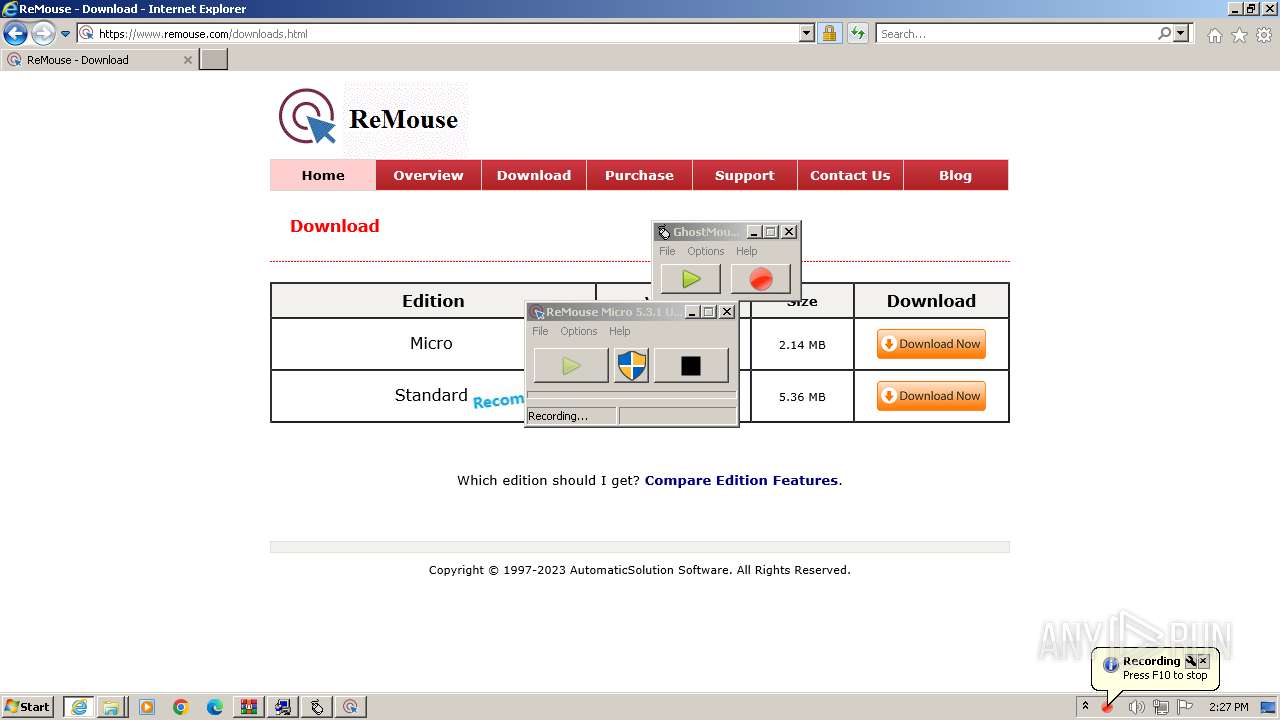
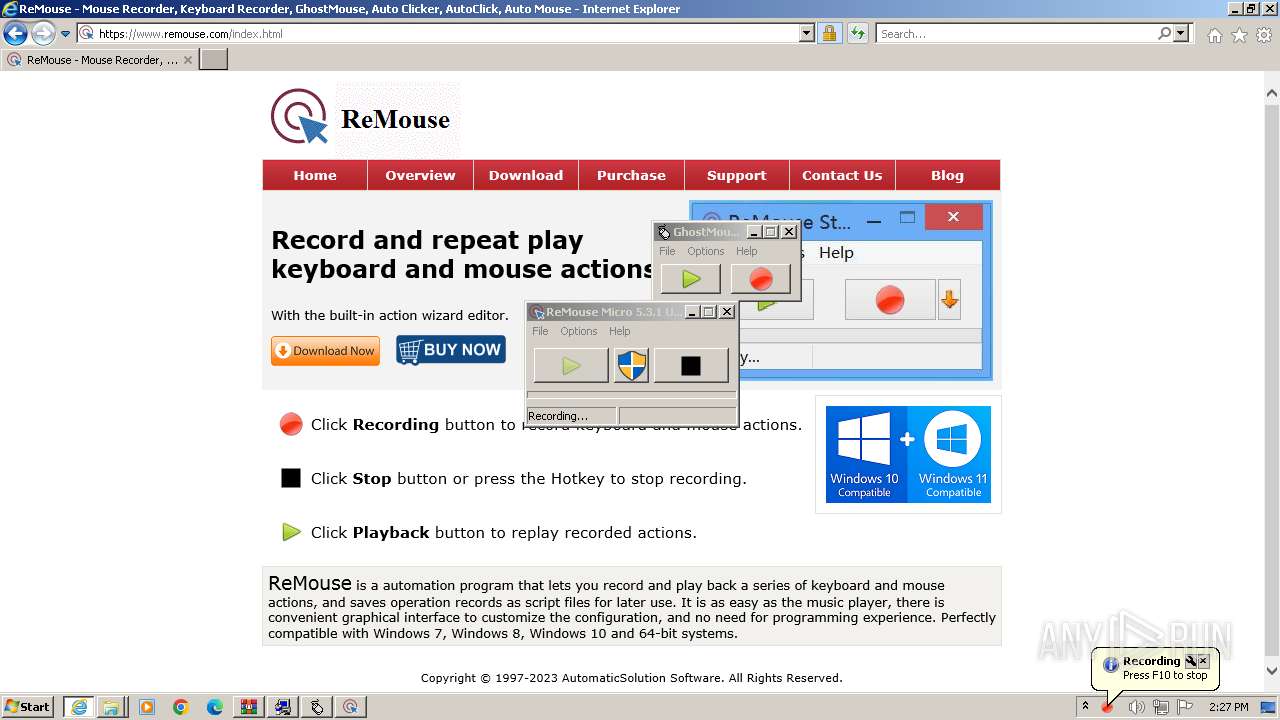
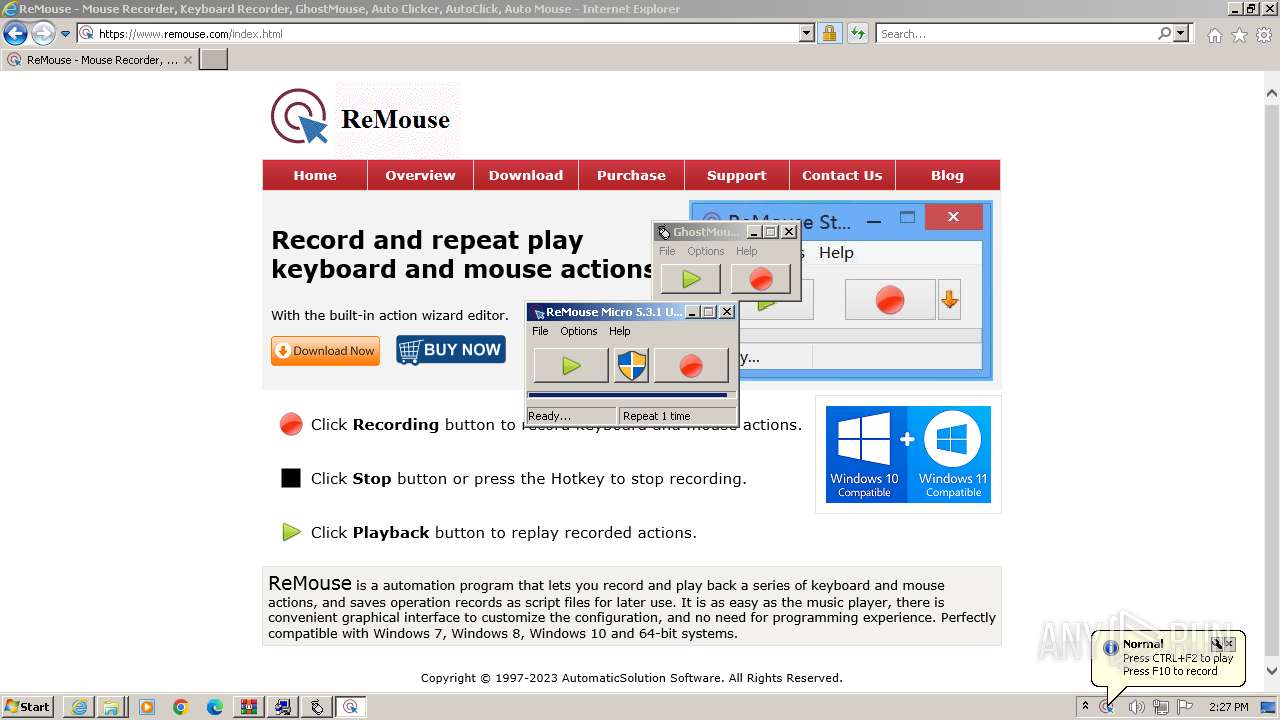
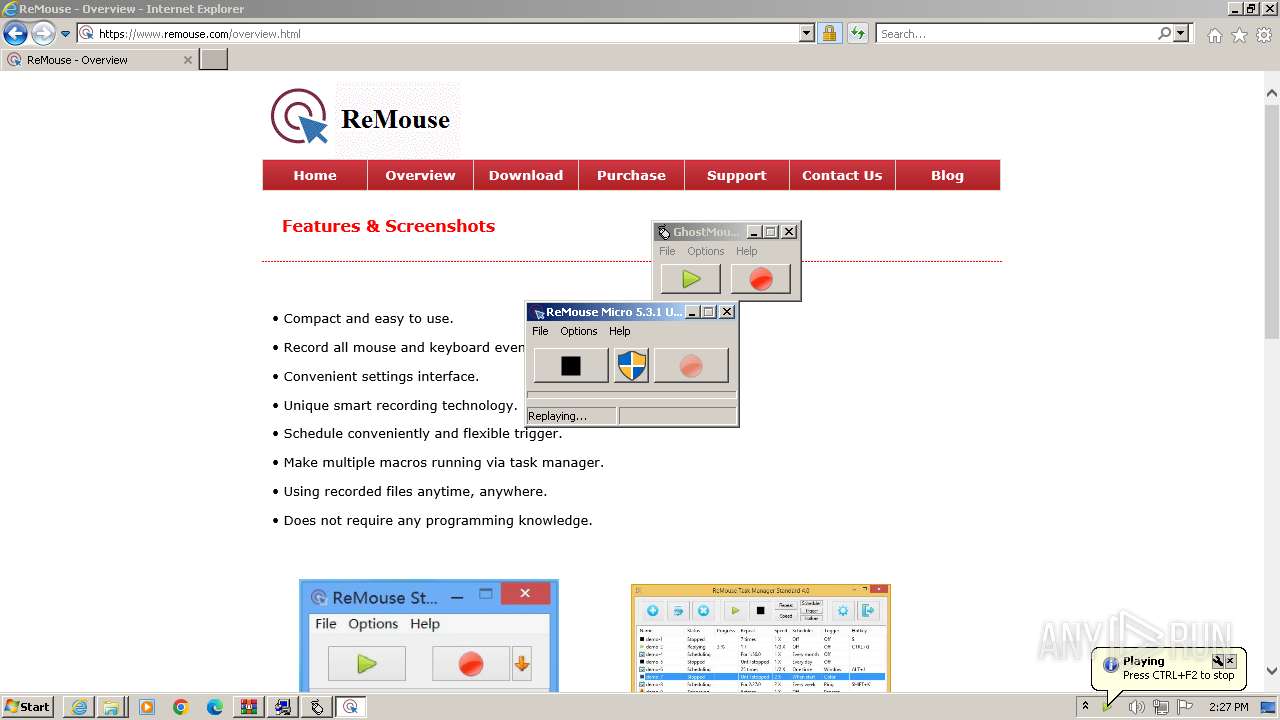
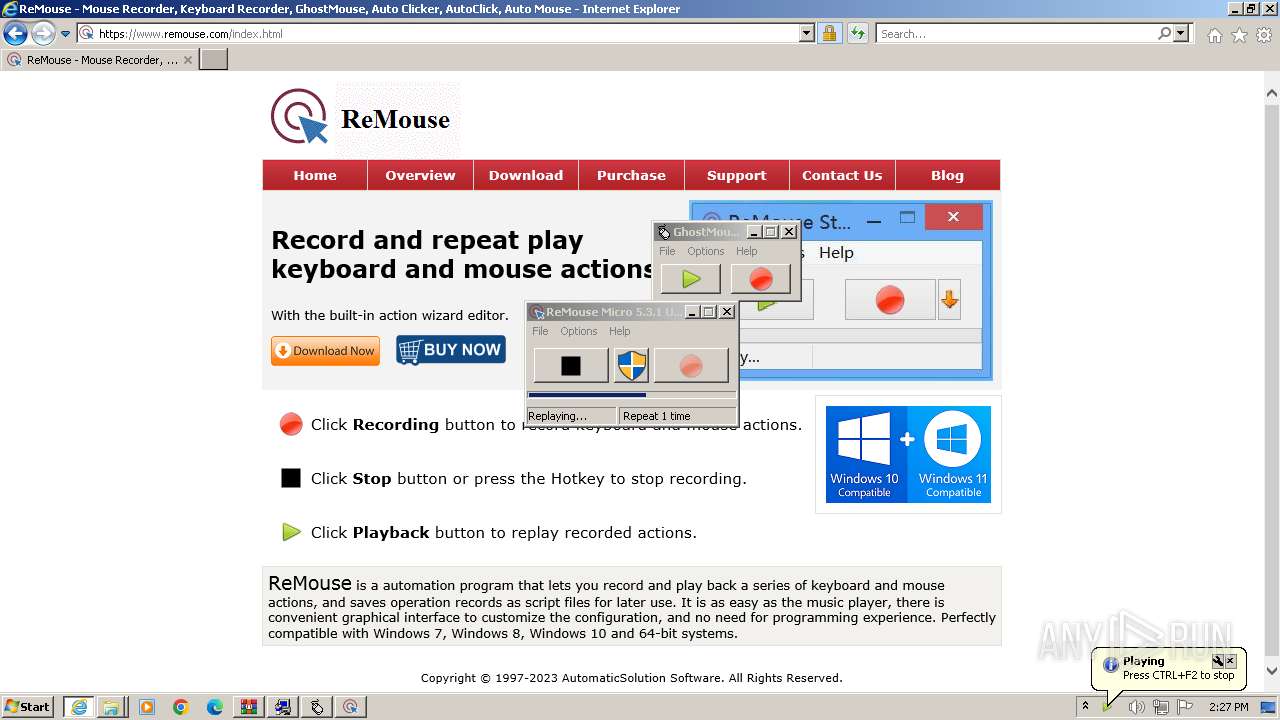
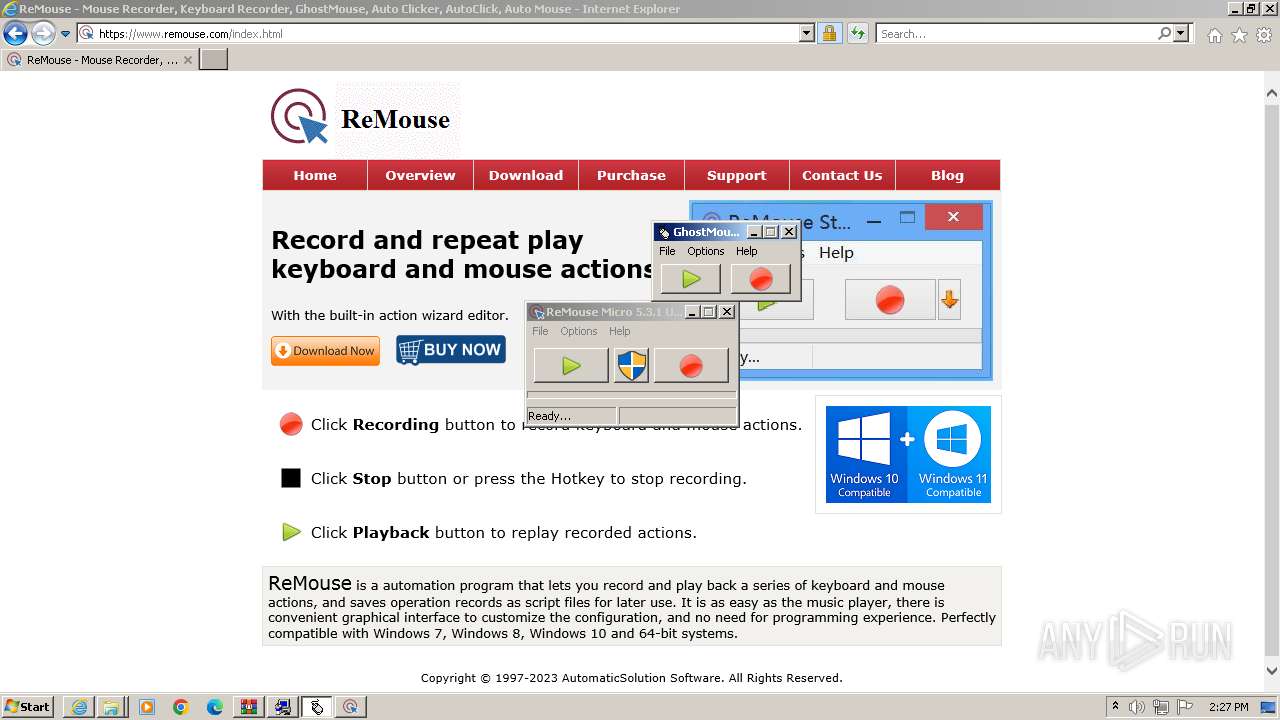
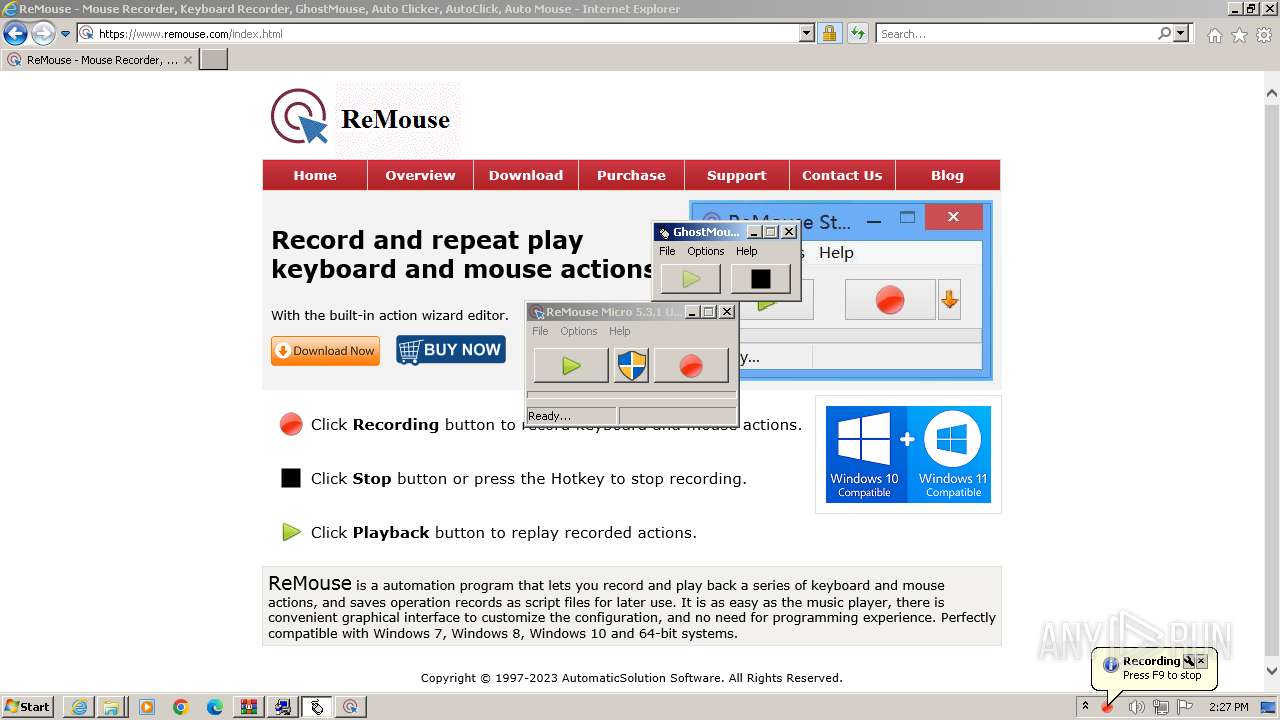
Drops the executable file immediately after the start
- _INS0432._MP (PID: 1608)
- GhostMouse-Setup.exe (PID: 548)
- GhostMouse-Setup.exe (PID: 3524)
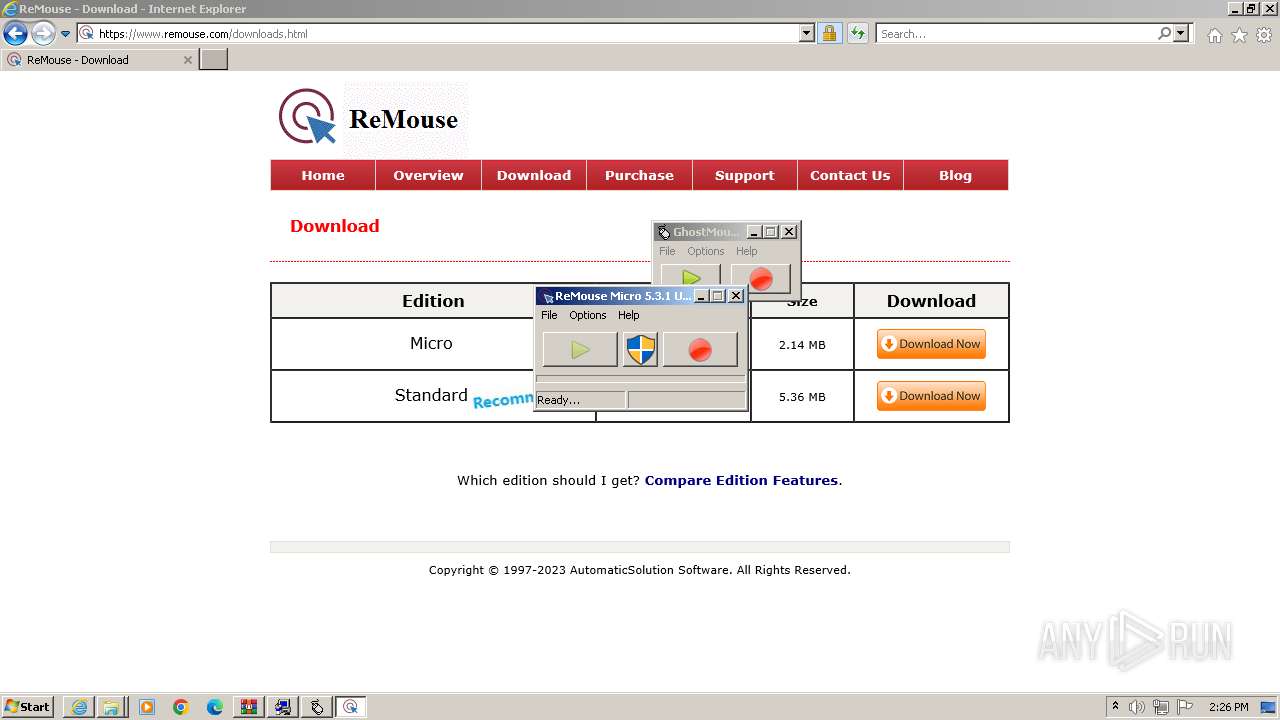
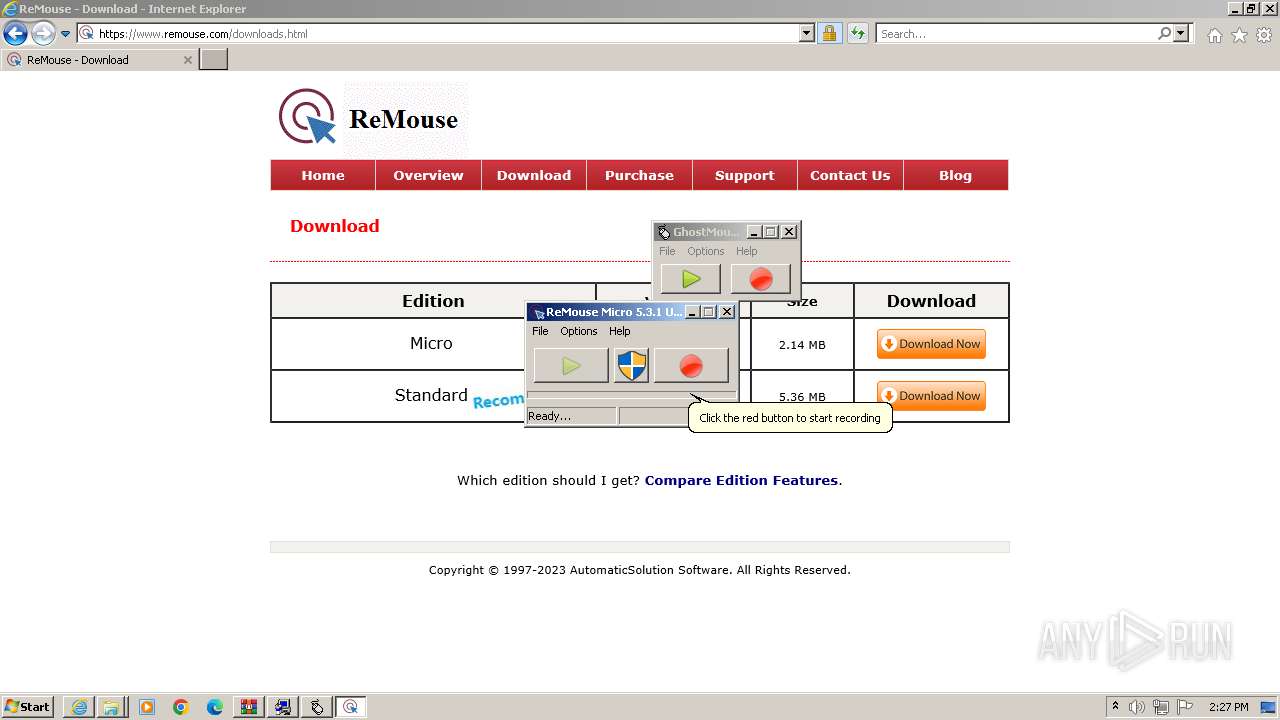
- ReMouseMicro-Setup.exe (PID: 2624)
- GhostMouse-Setup.tmp (PID: 908)
- ReMouseMicro-Setup.tmp (PID: 1880)
SUSPICIOUS
Reads the Windows owner or organization settings
- _INS0432._MP (PID: 1608)
- GhostMouse-Setup.tmp (PID: 908)
- ReMouseMicro-Setup.tmp (PID: 1880)
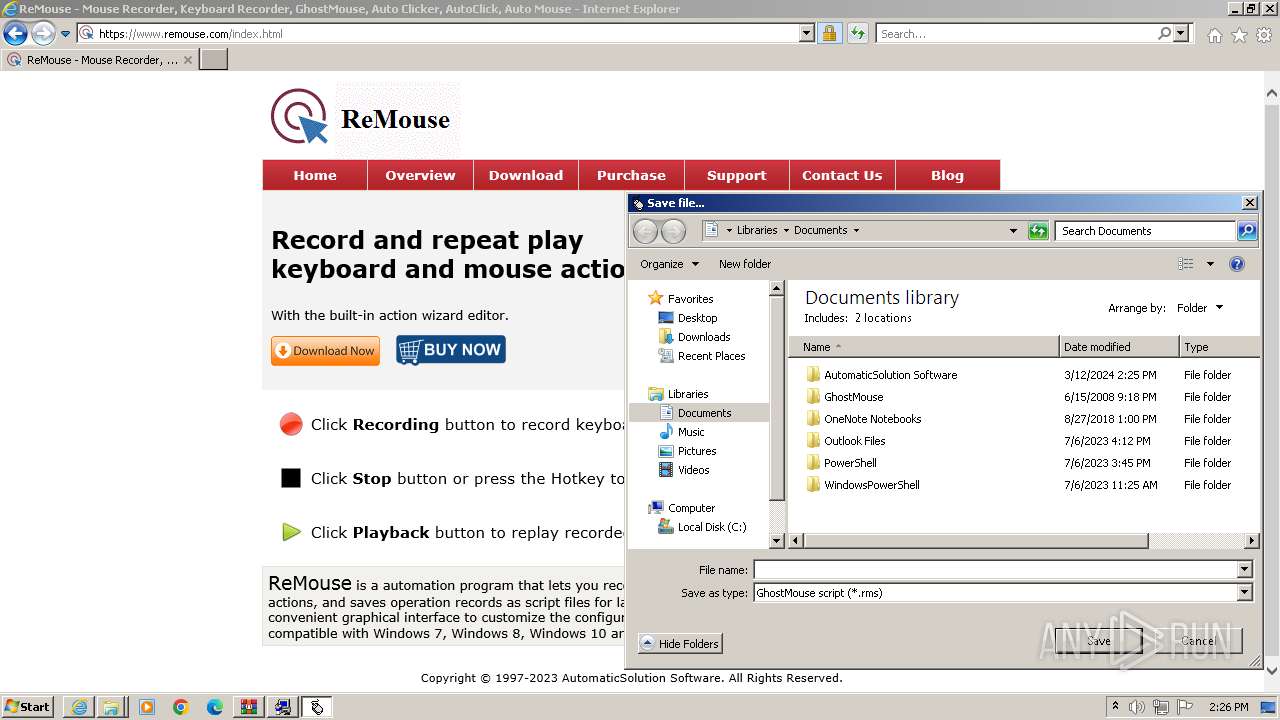
Executable content was dropped or overwritten
- ntvdm.exe (PID: 3444)
- _INS0432._MP (PID: 1608)
- GhostMouse-Setup.exe (PID: 548)
- GhostMouse-Setup.exe (PID: 3524)
- ReMouseMicro-Setup.exe (PID: 2624)
- GhostMouse-Setup.tmp (PID: 908)
- ReMouseMicro-Setup.tmp (PID: 1880)
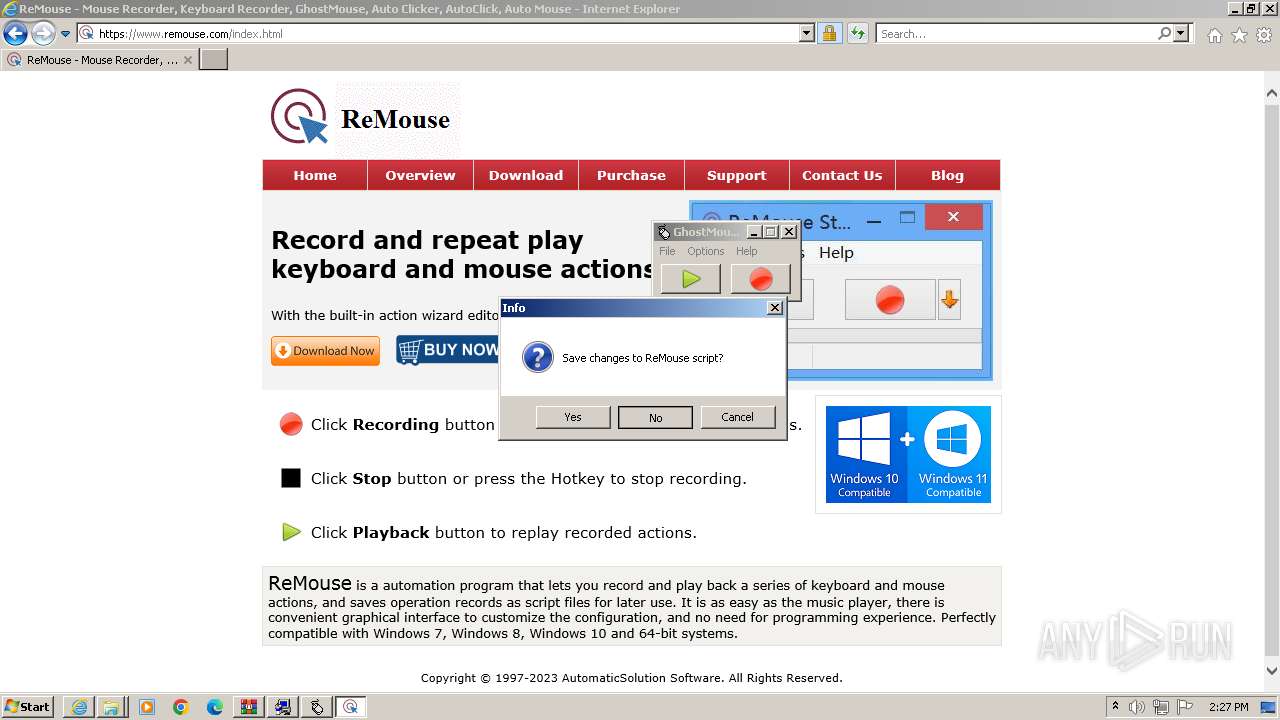
Creates a software uninstall entry
- _INS0432._MP (PID: 1608)
Process drops legitimate windows executable
- _INS0432._MP (PID: 1608)
- GhostMouse-Setup.tmp (PID: 908)
Searches for installed software
- _INS0432._MP (PID: 1608)
Starts application with an unusual extension
- ntvdm.exe (PID: 3444)
Creates file in the systems drive root
- ntvdm.exe (PID: 3444)
Reads the Internet Settings
- GhostMouse.exe (PID: 3860)
Non-standard symbols in registry
- ReMouseMicro-Setup.tmp (PID: 1880)
INFO
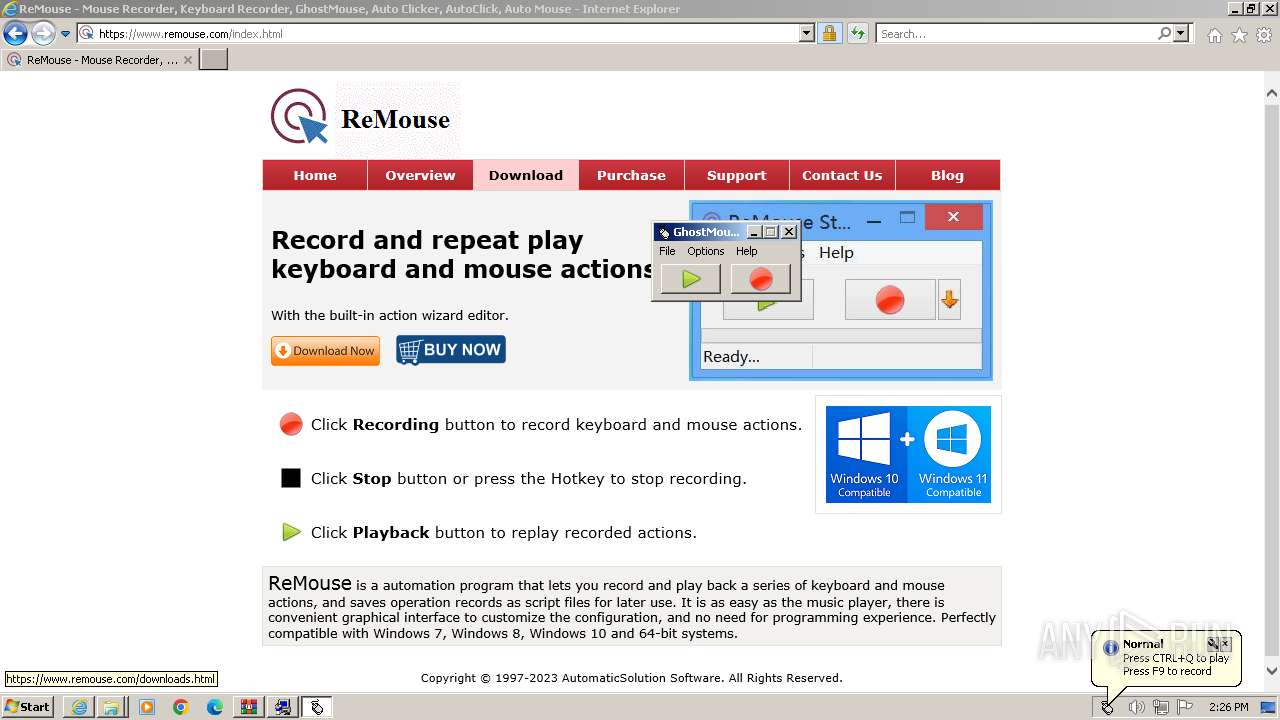
Modifies the phishing filter of IE
- iexplore.exe (PID: 3864)
The process uses the downloaded file
- iexplore.exe (PID: 3864)
- WinRAR.exe (PID: 2156)
Application launched itself
- iexplore.exe (PID: 3864)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2156)
- ntvdm.exe (PID: 3444)
- iexplore.exe (PID: 3952)
- iexplore.exe (PID: 3864)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2156)
- iexplore.exe (PID: 3952)
- iexplore.exe (PID: 3864)
Create files in a temporary directory
- ntvdm.exe (PID: 3444)
- _INS0432._MP (PID: 1608)
- GhostMouse-Setup.exe (PID: 548)
- GhostMouse-Setup.tmp (PID: 908)
- GhostMouse-Setup.exe (PID: 3524)
- GhostMouse.exe (PID: 3860)
- ReMouseMicro-Setup.exe (PID: 2624)
- ReMouse.exe (PID: 1040)
Manual execution by a user
- explorer.exe (PID: 2432)
- csrstub.exe (PID: 2992)
Checks supported languages
- _INS0432._MP (PID: 1608)
- Gmouse.exe (PID: 3260)
- GhostMouse-Setup.exe (PID: 548)
- GhostMouse-Setup.tmp (PID: 1604)
- GhostMouse-Setup.exe (PID: 3524)
- GhostMouse-Setup.tmp (PID: 908)
- GhostMouse.exe (PID: 3860)
- ReMouseMicro-Setup.tmp (PID: 1880)
- ReMouseMicro-Setup.exe (PID: 2624)
- ReMouse.exe (PID: 1040)
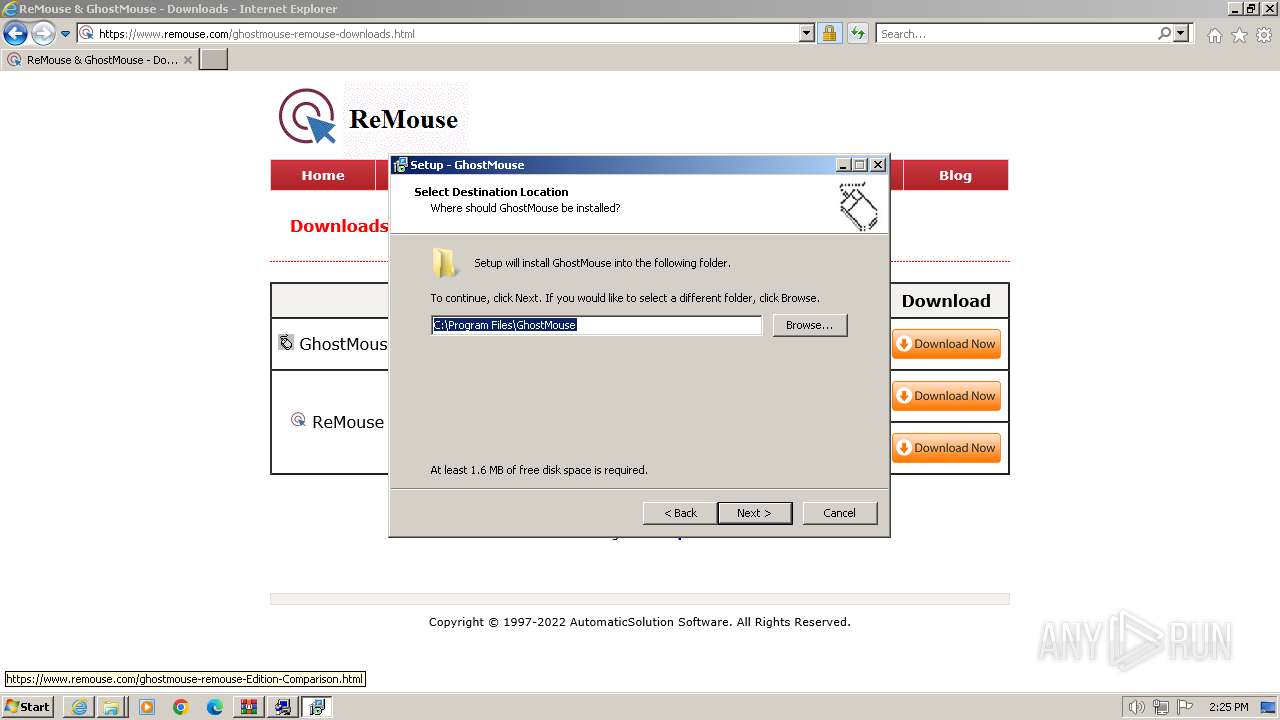
Creates files in the program directory
- _INS0432._MP (PID: 1608)
- GhostMouse-Setup.tmp (PID: 908)
Reads the computer name
- _INS0432._MP (PID: 1608)
- GhostMouse-Setup.tmp (PID: 1604)
- GhostMouse.exe (PID: 3860)
- ReMouseMicro-Setup.tmp (PID: 1880)
- GhostMouse-Setup.tmp (PID: 908)
- ReMouse.exe (PID: 1040)
Reads security settings of Internet Explorer
- explorer.exe (PID: 2052)
- explorer.exe (PID: 3312)
Creates files or folders in the user directory
- Gmouse.exe (PID: 3260)
- ReMouseMicro-Setup.tmp (PID: 1880)
Reads the Internet Settings
- explorer.exe (PID: 2052)
- explorer.exe (PID: 3312)
Reads mouse settings
- GhostMouse.exe (PID: 3860)
- ReMouse.exe (PID: 1040)
Reads the machine GUID from the registry
- GhostMouse.exe (PID: 3860)
Creates a software uninstall entry
- GhostMouse-Setup.tmp (PID: 908)
- ReMouseMicro-Setup.tmp (PID: 1880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
70
Monitored processes
21
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
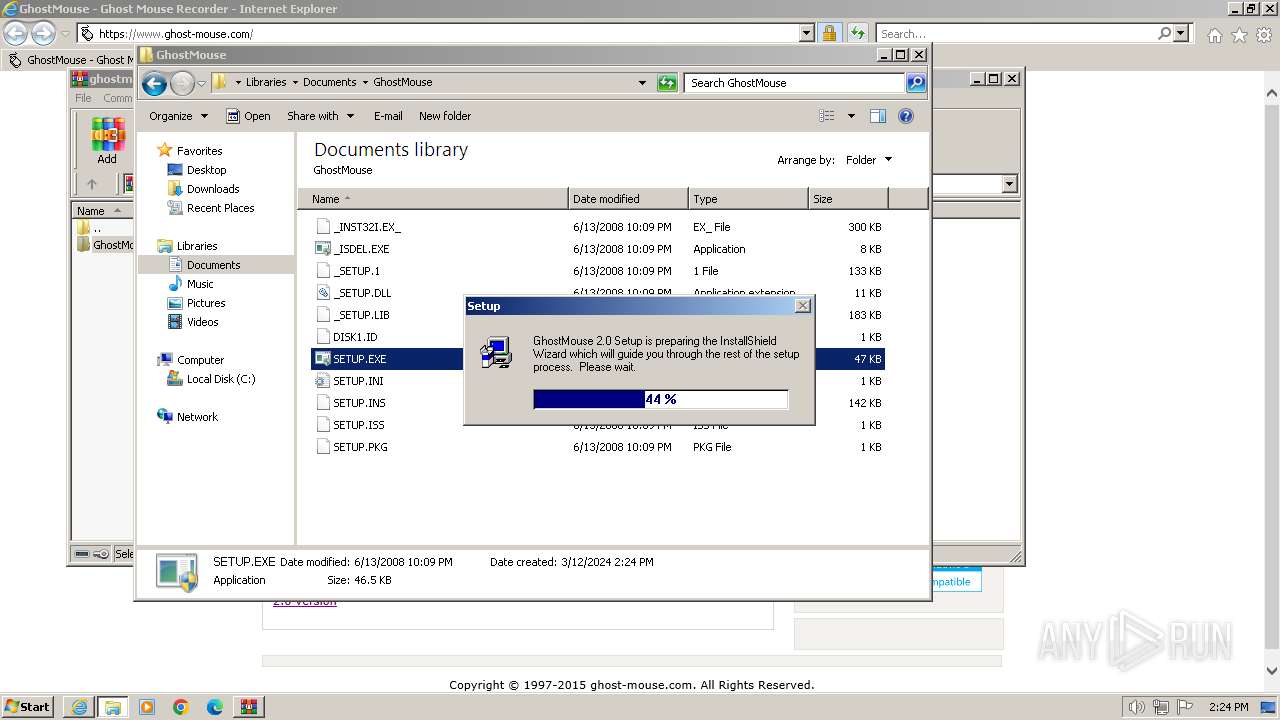
| 548 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\GhostMouse-Setup.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\GhostMouse-Setup.exe | iexplore.exe | ||||||||||||
User: admin Company: ghost-mouse.com Integrity Level: MEDIUM Description: Ghost Mouse Exit code: 0 Version: GhostMouse Free V3.2 Modules
| |||||||||||||||
| 908 | "C:\Users\admin\AppData\Local\Temp\is-5VRKB.tmp\GhostMouse-Setup.tmp" /SL5="$A02E4,589250,54272,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\GhostMouse-Setup.exe" /SPAWNWND=$60338 /NOTIFYWND=$E0250 | C:\Users\admin\AppData\Local\Temp\is-5VRKB.tmp\GhostMouse-Setup.tmp | GhostMouse-Setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 1040 | "C:\Users\admin\AppData\Roaming\AutomaticSolution Software\ReMouse Micro\ReMouse.exe" | C:\Users\admin\AppData\Roaming\AutomaticSolution Software\ReMouse Micro\ReMouse.exe | — | ReMouseMicro-Setup.tmp | |||||||||||
User: admin Integrity Level: MEDIUM Description: ReMouse Micro Exit code: 0 Version: 5.3.1 Modules
| |||||||||||||||
| 1604 | "C:\Users\admin\AppData\Local\Temp\is-U7MQB.tmp\GhostMouse-Setup.tmp" /SL5="$E0250,589250,54272,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\GhostMouse-Setup.exe" | C:\Users\admin\AppData\Local\Temp\is-U7MQB.tmp\GhostMouse-Setup.tmp | — | GhostMouse-Setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 1608 | C:\Users\admin\AppData\Local\Temp\_ins0432._mp -fC:\USERS\ADMIN\DOCUME~1\GHOSTM~1\SETUP.INS -z1 -cx -xC:\Users\admin\AppData\Local\Temp\ | C:\Users\admin\AppData\Local\Temp\_INS0432._MP | ntvdm.exe | ||||||||||||
User: admin Company: Stirling Technologies, Inc. Integrity Level: HIGH Description: InstallShield Engine EXE Exit code: 0 Version: 3.00.095.0 Modules
| |||||||||||||||
| 1796 | explorer.exe C:\GMouse20\GHOSTM~1.0 | C:\Windows\explorer.exe | — | _INS0432._MP | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1880 | "C:\Users\admin\AppData\Local\Temp\is-AI0IT.tmp\ReMouseMicro-Setup.tmp" /SL5="$50402,1983860,57856,C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\ReMouseMicro-Setup.exe" | C:\Users\admin\AppData\Local\Temp\is-AI0IT.tmp\ReMouseMicro-Setup.tmp | ReMouseMicro-Setup.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2052 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2156 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\ghostmouse2.zip" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2292 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3864 CREDAT:4134157 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
66 281
Read events
65 699
Write events
488
Delete events
94
Modification events
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31093896 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 72199988 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31093897 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
48
Suspicious files
42
Text files
85
Unknown types
25
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:FF795F8A318E910F78B1A6C3B93B52FC | SHA256:13624CFE1E8F87157B1BD677159AEBC1F38802B103C3A3F5646C90232DC06E7E | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\1QNN6R31.htm | html | |
MD5:C33CF6A409F50B17EA6B4E4665C1D0CC | SHA256:DB316A76D0896D45E4842388E373C1D9B5054D24B4B5AFBFF2428C80319A4D6B | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:8FB241A6E7426DCAE540662191A7E2DA | SHA256:814410CFED6C8CD92AFBB6FB5C60958EA829C496A9C76DB9AA2C5F2618325171 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:FA3535F092F9397D32AA85B0DDEA751A | SHA256:A17BA59B8BA1538E7E0AD6F0DCCBDEA958FBF3777C97E3BE9CD2FF5CA17CC02A | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\style[1].css | text | |
MD5:0D346D870BFA14652645B5EBFEBEDD17 | SHA256:2AD63B5C9B98DAAE9FD07CA2A4C397EC236E6DA5D132C260D7B5B50CE3B4C1A3 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\dl[1].jpg | image | |
MD5:AF75EC48E7033C6DA3408D1CB5851B14 | SHA256:0FADCE679CC316FB5F0A28519CBF252BE1F9B24AC539A39F2D43CBB29F1CA96C | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\cnet_rating[1].jpg | image | |
MD5:7628F5B8F53A3EA547386CC34F87C7AE | SHA256:960381D25E8F3B8CE2CD145E79C6231C0DEDCD06468A460579B139BED104224E | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\win7-8[1].png | image | |
MD5:0B711F8FBE9E6C7358B0EE818839394E | SHA256:3EE1194DA73D0D3A3EB7BC85518198773FC3BD61BA0E164ADFEB22AFCDFC90C0 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:C2DE2B2A0DB9166283D1F5A3C13A2521 | SHA256:E56769A7D9732C18CD5CD75DFE75769E9B2C2D77C07132900A7B0E429897AF2C | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\logo[1].gif | image | |
MD5:39E8F43EDA4000BD423B0AC77C81AB86 | SHA256:B478253C8EE918ADDDEE873756CED78703AD937BCB9535C8C61ED1CEA159C081 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
60
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3952 | iexplore.exe | GET | 304 | 23.32.238.201:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bd117e088266f0f9 | unknown | — | — | unknown |
3952 | iexplore.exe | GET | 304 | 23.32.238.179:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?545e1839169dd0e6 | unknown | — | — | unknown |
3952 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
3864 | iexplore.exe | GET | 304 | 23.32.238.201:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?18014fff35250a83 | unknown | — | — | unknown |
3864 | iexplore.exe | GET | 304 | 23.32.238.201:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?76ad697231f9b13b | unknown | — | — | unknown |
3952 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
2292 | iexplore.exe | GET | 301 | 188.114.97.3:80 | http://down.ghost-mouse.com/ghostmouse2.zip | unknown | — | — | unknown |
3864 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 312 b | unknown |
1080 | svchost.exe | GET | 200 | 23.32.238.201:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?624d1ab720bef5f8 | unknown | compressed | 67.5 Kb | unknown |
3864 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3952 | iexplore.exe | 188.114.97.3:443 | www.ghost-mouse.com | CLOUDFLARENET | NL | unknown |
3952 | iexplore.exe | 23.32.238.179:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3952 | iexplore.exe | 23.32.238.201:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3952 | iexplore.exe | 142.250.186.35:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3864 | iexplore.exe | 188.114.97.3:443 | www.ghost-mouse.com | CLOUDFLARENET | NL | unknown |
3864 | iexplore.exe | 23.32.238.201:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3864 | iexplore.exe | 92.123.104.36:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.ghost-mouse.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
down.ghost-mouse.com |
| unknown |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |