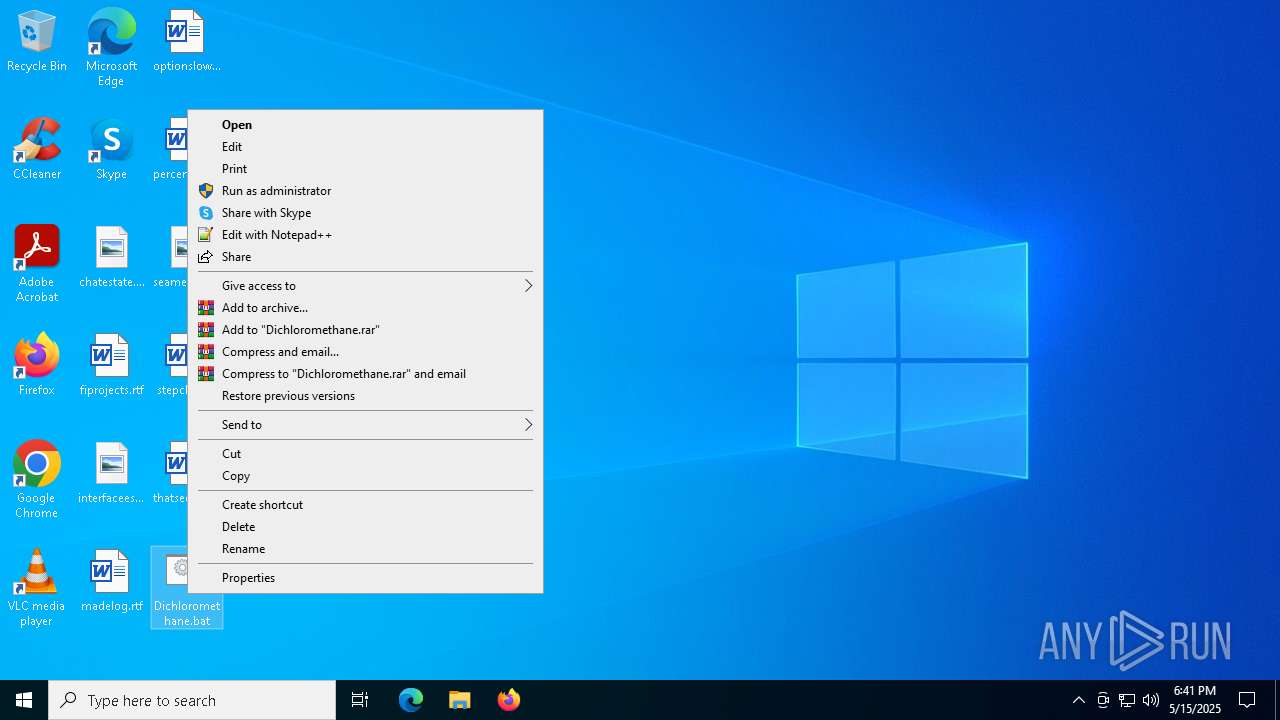
| File name: | Dichloromethane.bat |
| Full analysis: | https://app.any.run/tasks/6a776c27-ff15-4bf0-8b08-13c8d2645d6b |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 18:40:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text, with CRLF line terminators |
| MD5: | 862BE858719402D53E865D17A601B2E3 |
| SHA1: | FC0D5FA20C46785B35C06A4DDCE2C2694A127D9C |
| SHA256: | 38EFC31D5B18C1C9A12DEB1CE0F193C9AE97A15D947E8DC96FEA1A29FA6AD0E8 |
| SSDEEP: | 48:TE20Kt30N390bSOX2FZFZviIDh7+lCLJwmuABF:TEbN390my2DbvhklCLJB1L |
MALICIOUS
Uses Task Scheduler to autorun other applications
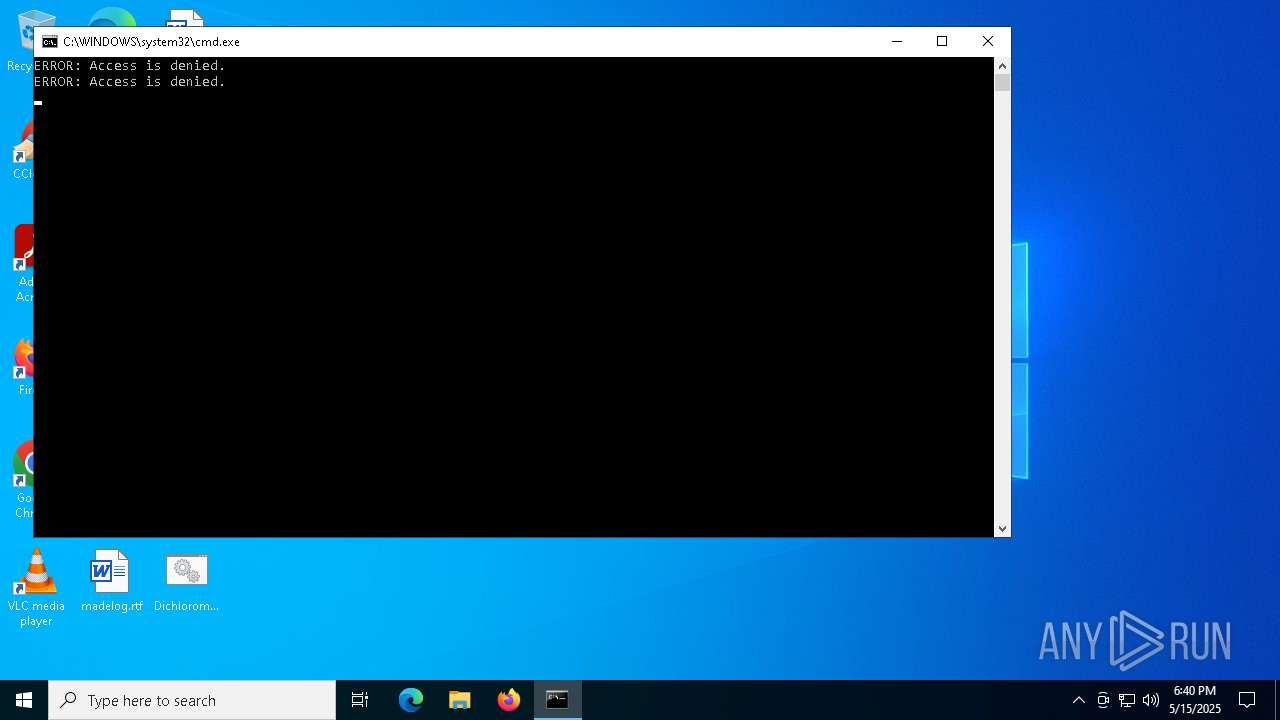
- cmd.exe (PID: 5868)
- cmd.exe (PID: 1184)
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 5868)
- cmd.exe (PID: 1184)
SUSPICIOUS
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5868)
- cmd.exe (PID: 1184)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 5868)
- cmd.exe (PID: 1184)
Starts NET.EXE to map network drives
- cmd.exe (PID: 5868)
- cmd.exe (PID: 1184)
INFO
Manual execution by a user
- cmd.exe (PID: 1184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
159
Monitored processes
30
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
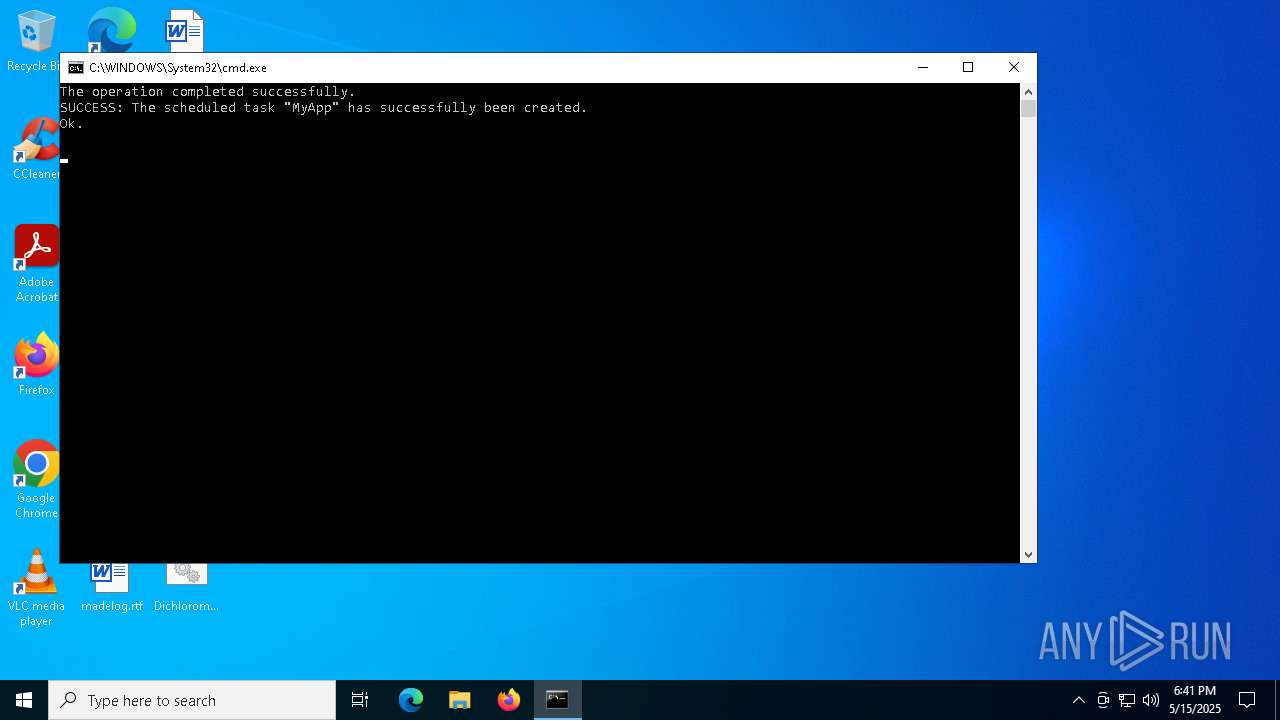
| 300 | schtasks /create /tn "MyApp" /tr "Dichloromethane.exe" /sc onlogon /rl highest /f | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | regsvr32 /s keymgr.dll | C:\Windows\System32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 4 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
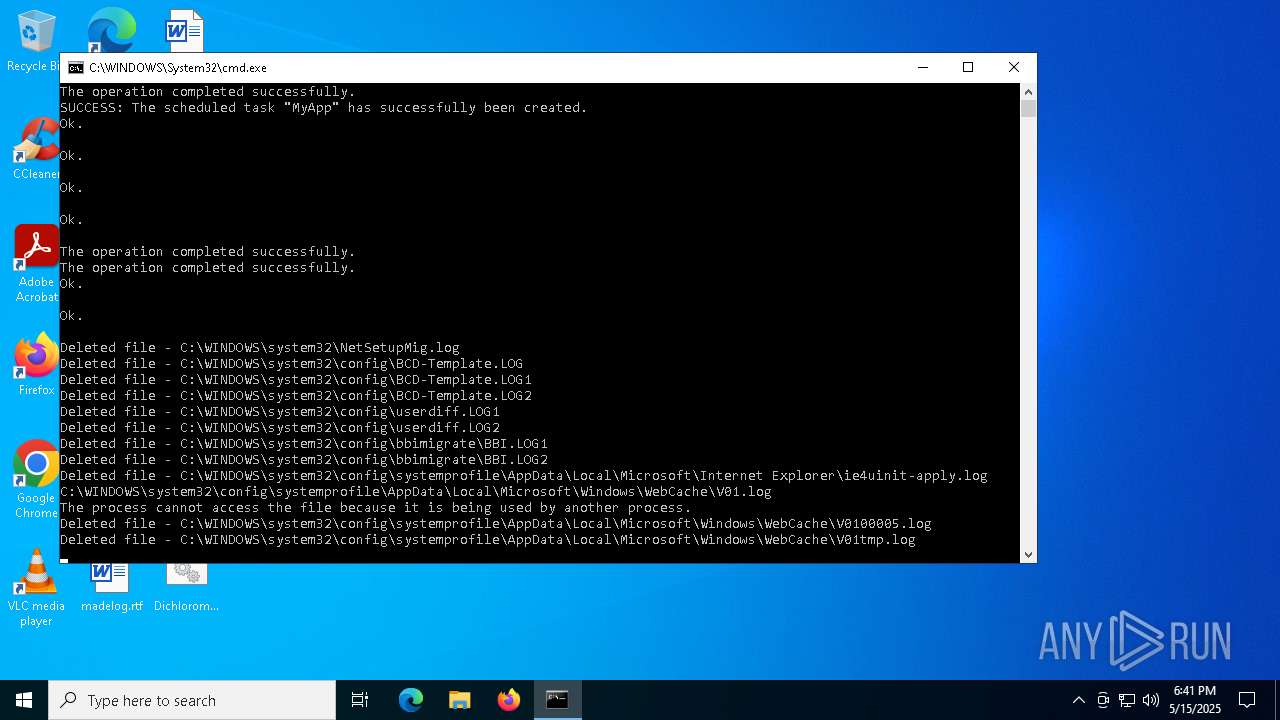
| 896 | reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\DeviceGuard" /v LsaCfgFlags /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\Desktop\Dichloromethane.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | netsh advfirewall firewall add rule name="DHCPv4 Server Port 67" protocol=UDP dir=in localport=67 action=allow | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1672 | netsh advfirewall firewall add rule name="DHCPv4 Client Port 68" protocol=UDP dir=in localport=68 action=allow | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1676 | reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\default\Start" /v HideRestart /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1764 | regsvr32 /s keymgr.dll | C:\Windows\System32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 4 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2152 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | netsh advfirewall firewall add rule name="DHCPv6 Server Port 546" protocol=UDP dir=in localport=546 action=allow | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 693
Read events
4 691
Write events
2
Delete events
0
Modification events
| (PID) Process: | (1676) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\default\Start |
| Operation: | write | Name: | HideRestart |
Value: 1 | |||
| (PID) Process: | (896) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\DeviceGuard |
| Operation: | write | Name: | LsaCfgFlags |
Value: 0 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
19
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 88.221.110.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1672 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1672 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 88.221.110.114:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |